Patents
Literature
67results about How to "Make up for loopholes" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
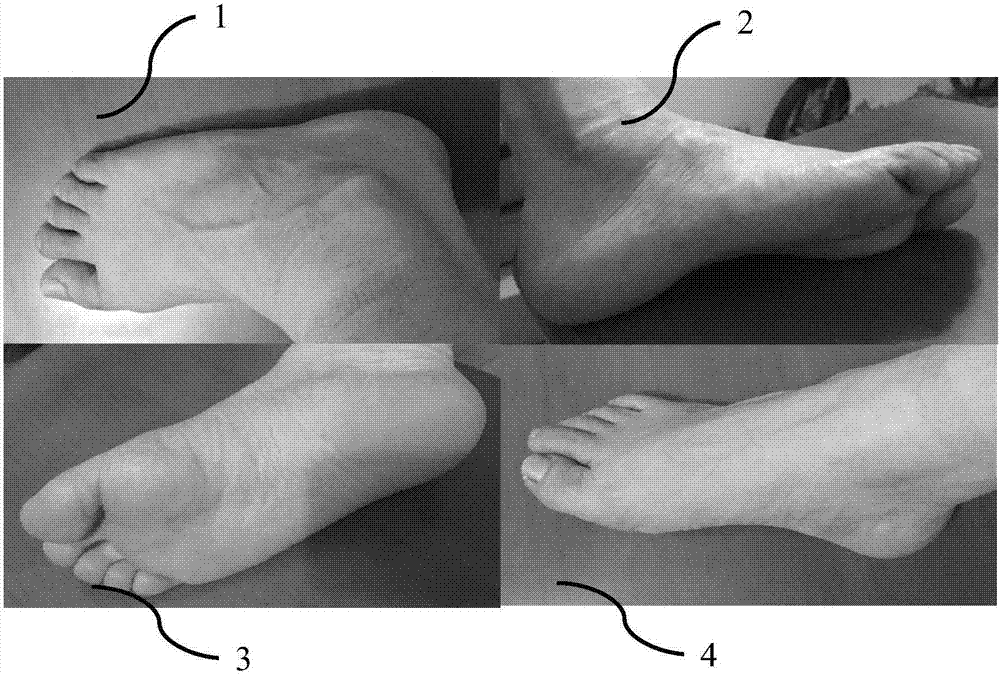
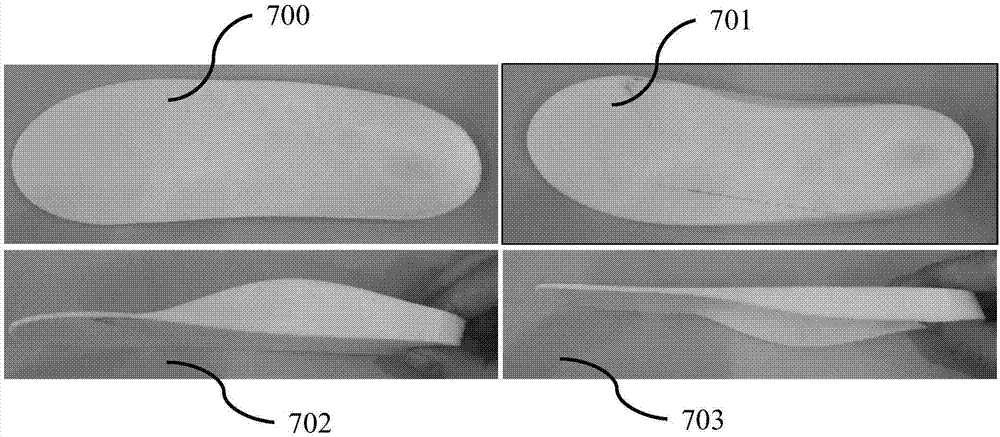
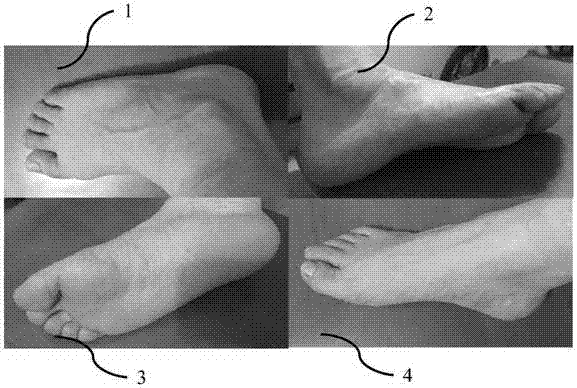
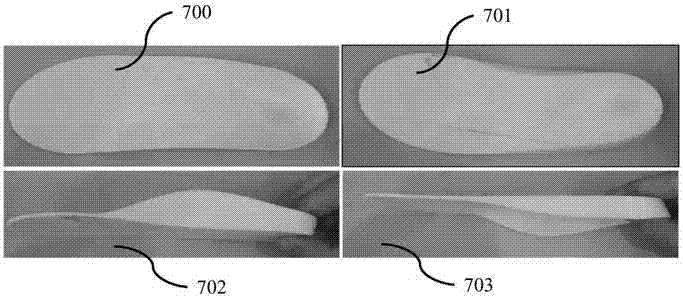
Customized shoe making method and system based on image recognition and three-dimensional modeling technologies
InactiveCN107095393AMeet individual (e.g. aesthetic) needsImprove comfortFoot measurement devicesData acquisitionDimensional modeling
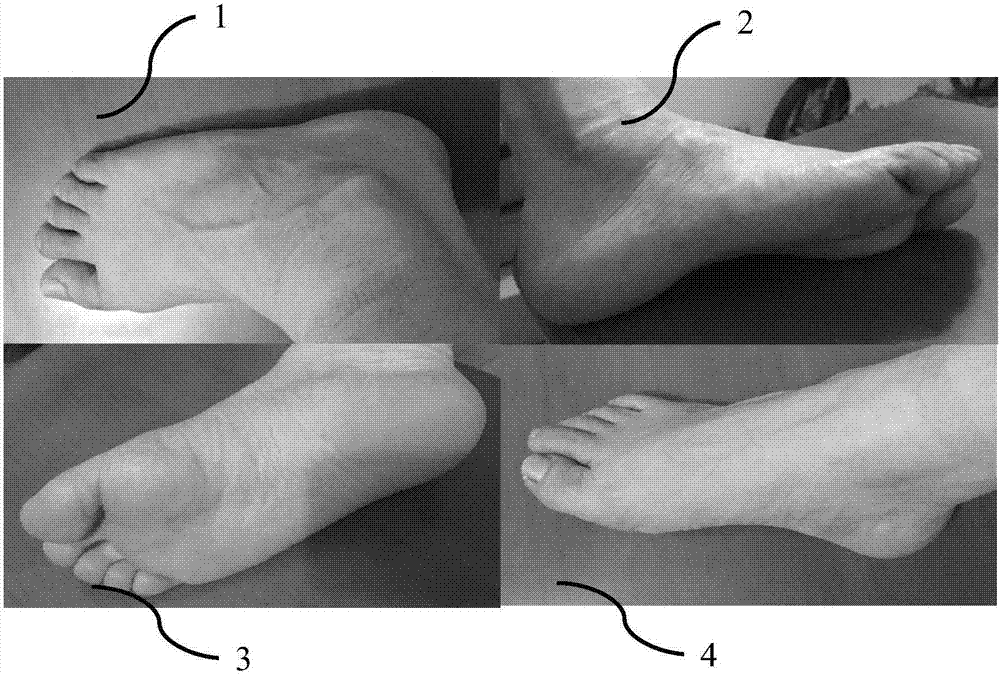
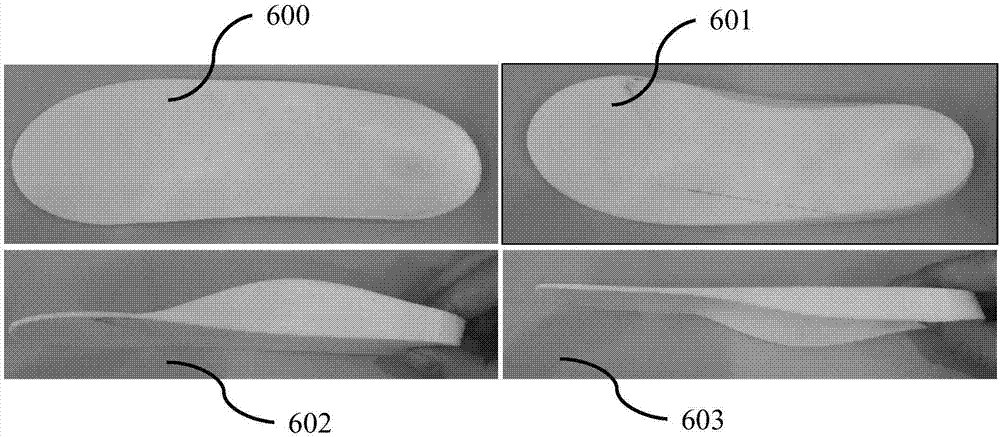
The invention relates to a customized shoe making method and a customized shoe making system based on image recognition and three-dimensional modeling technologies, wherein the customized shoe making method comprises the following steps: acquiring foot images; collecting source data by virtue of a network; conducting image recognition; conducting three-dimensional modeling; and making shoes in accordance with three-dimensional models of feet. The customized shoe making system comprises a data acquisition device, a data collecting and summarizing device, an image recognition device, a three-dimensional modeling device and a shoe making device. According to the customized shoe making method and the customized shoe making system provided by the invention, a user's demand on foot health can be met; user's operations are time-saving and convenient; a shoe making efficiency can be improved; and foot correction can be achieved.
Owner:青岛一小步科技有限公司
Correction shoe making method and system based on image recognition and three-dimensional modeling technique
ActiveCN106942837AMeet individual (e.g. aesthetic) needsImprove comfortFoot measurement devicesComputer graphics (images)Data acquisition
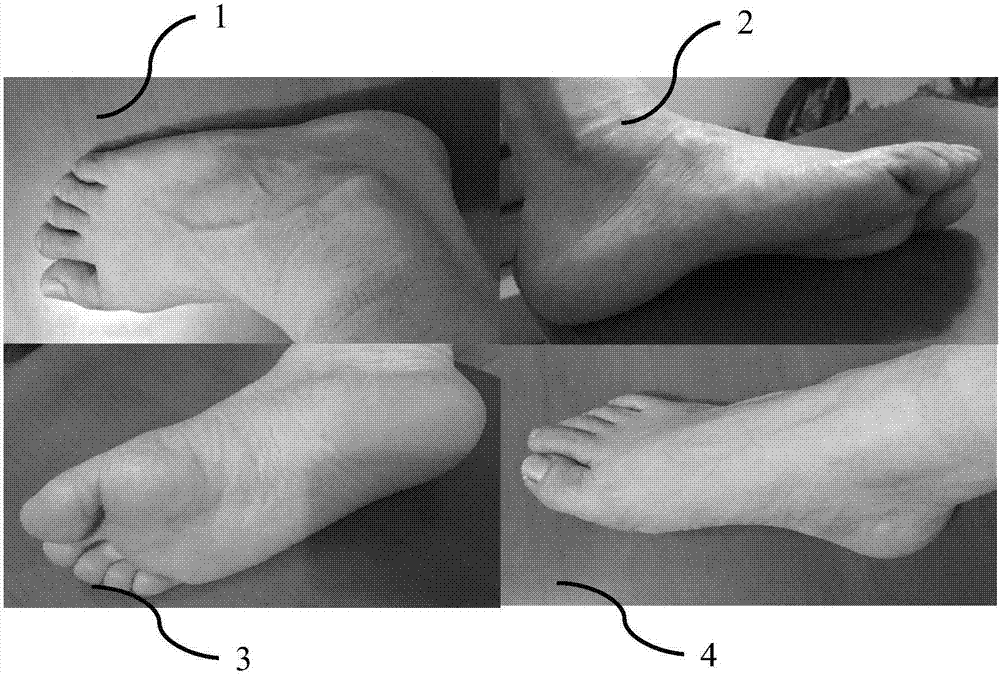
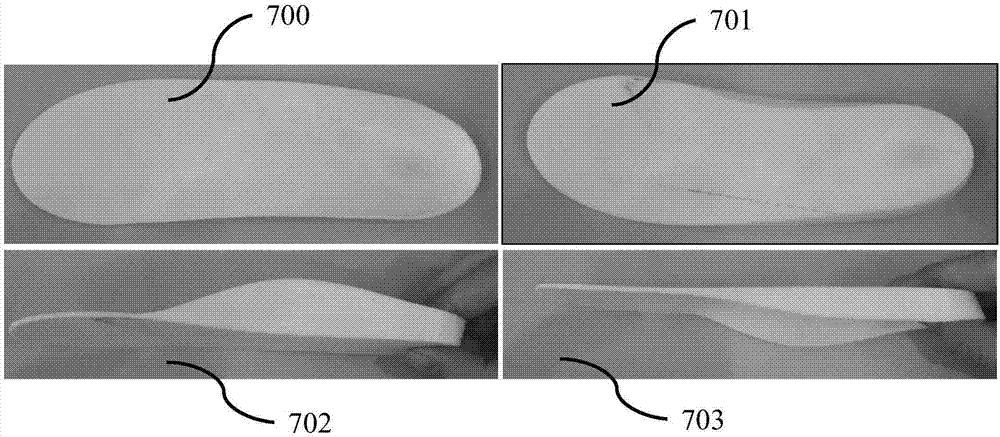
The invention relates to a correction shoe making method and a correction shoe making system based on image recognition and three-dimensional modeling technique, wherein the correction shoe making method comprises the following steps: acquiring a foot image and other health data; collecting source data through network; conducting image recognition; conducting three-dimensional modeling; correcting a three-dimensional model; and making shoes in accordance with the corrected three-dimensional model. The correction shoe making system comprises a data acquisition device, a data collection and summarization device, an image recognition device, a three-dimensional modeling device and a shoe making device. The correction shoe making method and the correction shoe making system provided by the invention can meet users' demands of guaranteeing foot health; users can conduct operations conveniently in a time-saving mode; a shoe making efficiency is improved; and foot correction is achieved.
Owner:青岛一小步科技有限公司
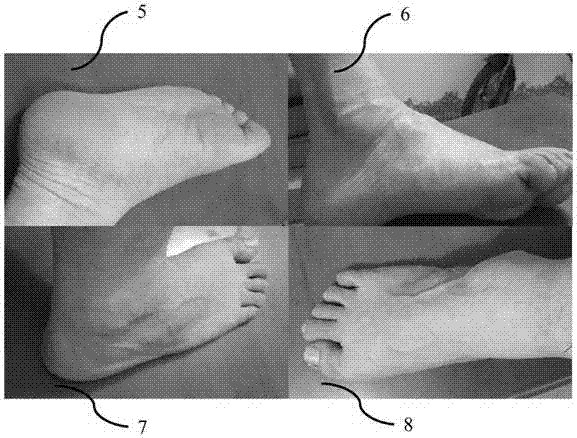
Manufacturing method and system for custom shoes based on pressure imaging and three-dimensional modeling technologies
ActiveCN107114861AMeet individual (e.g. aesthetic) needsImprove comfortFoot measurement devicesData acquisitionDimensional modeling
The invention relates to a manufacturing method and system for custom shoes based on pressure imaging and three-dimensional modeling technologies. The manufacturing method for the custom shoes comprises the steps of collecting foot pressure data; collecting source data by using a network; carrying out three-dimensional modeling; and manufacturing the shoes according to a three-dimensional model of the feet. The manufacturing system for the custom shoes comprises a data collection system, a data collecting and gathering device, a three-dimensional modeling device and a shoe manufacturing device. The manufacturing method and system can meet the foot health requirements of a user, operation of the user is time-saving and convenient, the shoe manufacturing efficiency is high and foot orthopaedics can be achieved.
Owner:青岛一小步科技有限公司
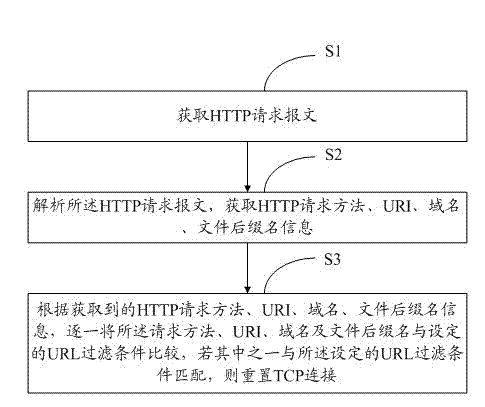
URL (Uniform Resource Locator) filtering method and URL (Uniform Resource Locator) filtering system aiming at HTTP (Hyper Text Transport Protocol) segment request
InactiveCN102868693ARich filter conditionsMake up for loopholesTransmissionDomain nameFilename extension
The invention provides a URL (Uniform Resource Locator) filtering method and a URL filtering system aiming at an HTTP (Hyper Text Transport Protocol) segment request, wherein the method comprises the following steps of: S1, obtaining an HTTP request message; S2, resolving the HTTP request message, and obtaining the HTTP request method, a URI (Uniform Resource Identifier), a domain name and a filename extension information; and S3, according to the obtained HTTP request method, URI, domain name and filename extension information, comparing the request method, the URI, the domain name and the filename extension with a set URL filtering condition one by one, and if one of the request method, the URI, the domain name and the filename extension is matched with the set URL filtering condition, resetting a TCP (Transmission Control Protocol) connection. The URL filtering method and the URL filtering system provided by the invention realize filtering on the segmented HTTP request, make up the vulnerability in the prior art, additionally, the method and the system filter the HTTP request in a manner of gathering multiple information such as the request method, the URI, the domain name and the filename extension, so that the URL filtering conditions are enriched.
Owner:苏州迈科网络安全技术股份有限公司
Orthopedic shoe manufacturing method and system based on pressure imaging and three-dimensional modeling technologies
ActiveCN106901445AMeet individual (e.g. aesthetic) needsImprove comfortFoot measurement devicesModel modificationData acquisition
The invention relates to an orthopedic shoe manufacturing method and system based on pressure imaging and three-dimensional modeling technologies. The orthopedic shoe manufacturing method comprises the steps of collecting foot pressure data and other health data of a patient; collecting source data by using a network; carrying out three-dimensional modeling; carrying out model modification; and manufacturing a shoe according to a modified three-dimensional model. The orthopedic shoe manufacturing system comprises a data collection device, a data collection and summarization device three-dimensional modeling device and a shoe manufacturing device. The orthopedic shoe manufacturing method and system meet the foot heath requirements of a user, operation of the user is time-saving and convenient; the shoe manufacturing efficiency is high and foot orthopedics can be achieved.
Owner:青岛一小步科技有限公司
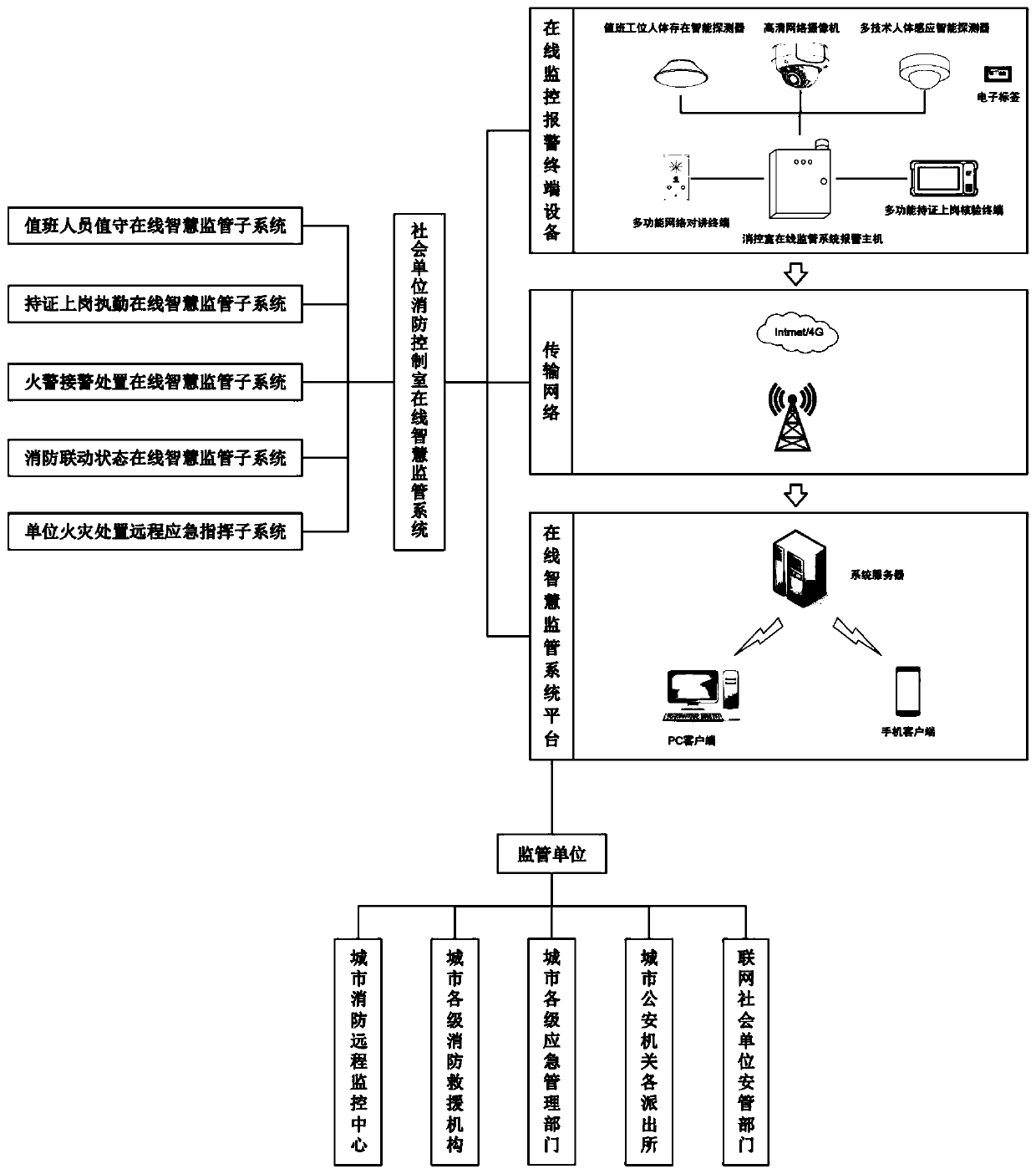
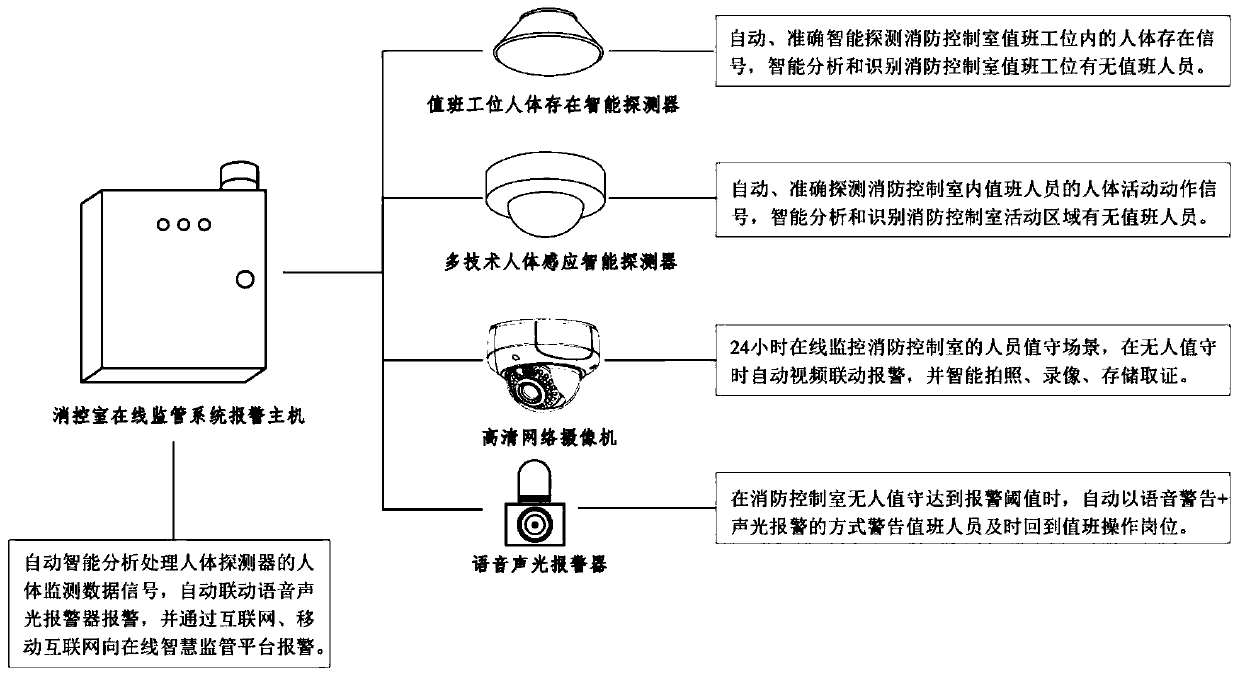
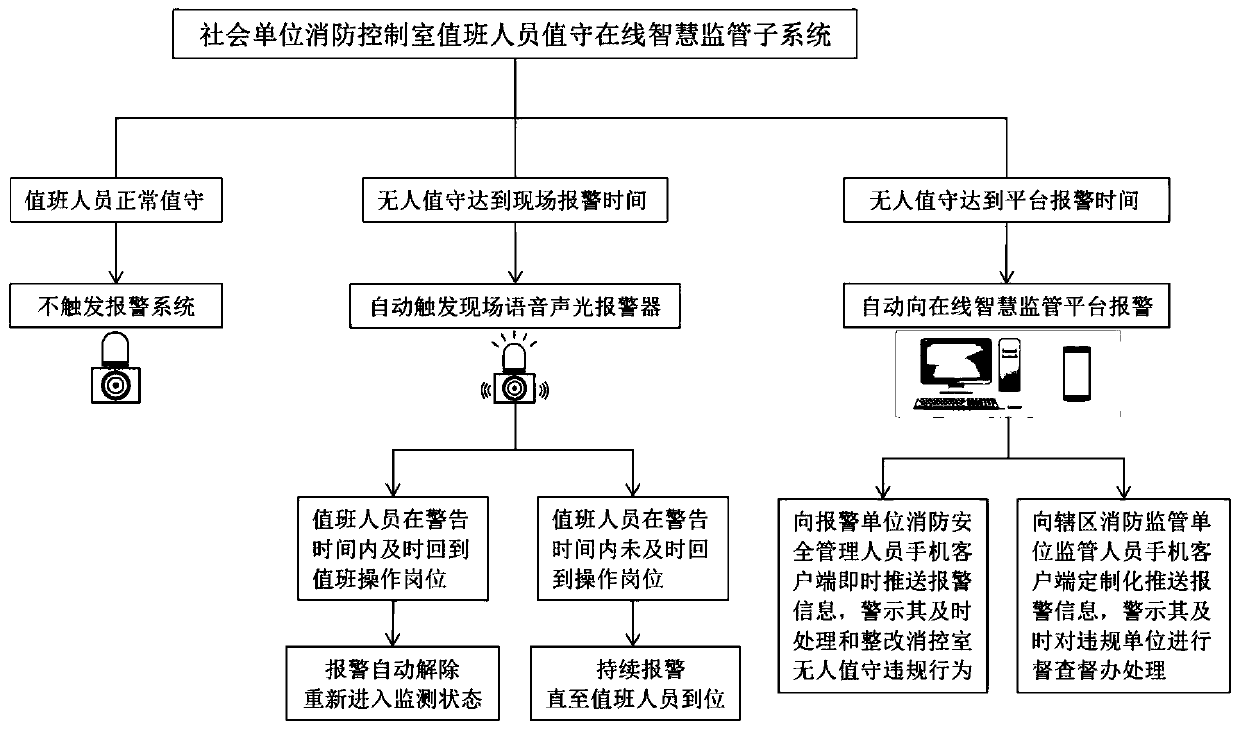
Online smart supervision system of fire protection control room of social unit
PendingCN110689689ASolving Regulatory DifficultiesAddress regulatory needsTelevision system detailsRegistering/indicating time of eventsAlarm messageFire protection
The invention relates to an online smart supervision system of a fire protection control room of a social unit. The online smart supervision system comprises an online supervision and alarm terminal device of the fire protection control room, a transmission network and an online smart supervision platform; the online supervision and alarm terminal device of the fire protection control room comprises an online supervision system alarm host of the fire protection control room, and a personnel on-duty smart detector, a high-definition network camera, a multifunctional certificated employment verification terminal, a multifunctional network intercom terminal and a voice audible and visual alarm, which are connected with the online supervision system alarm host of the fire protection control room; and the online supervision system alarm host of the fire protection control room can transmit supervision / monitoring data and alarm information to the online smart monitoring platform through thetransmission network. The online smart supervision system provided by the invention effectively solves the supervision difficulties of urban fire protection supervision organizations on insufficient staffing, unattended, undocumented employment, fire alarm violation handling, fire protection linkage violation setting and the like of fire protection control rooms of the social units, and realizes refined, normalized an long-lasting online smart supervision of the fire protection control rooms of the social units.
Owner:山东宏成安防科技有限公司
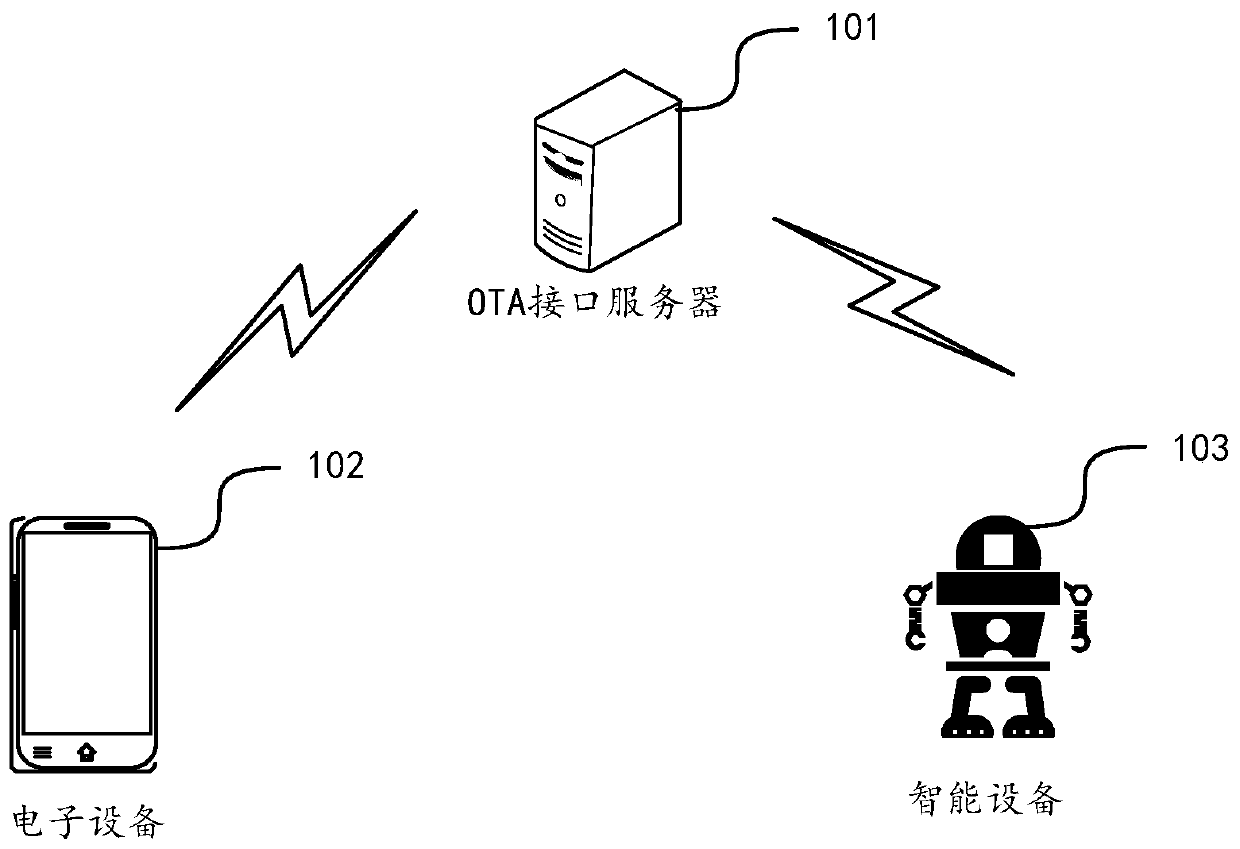
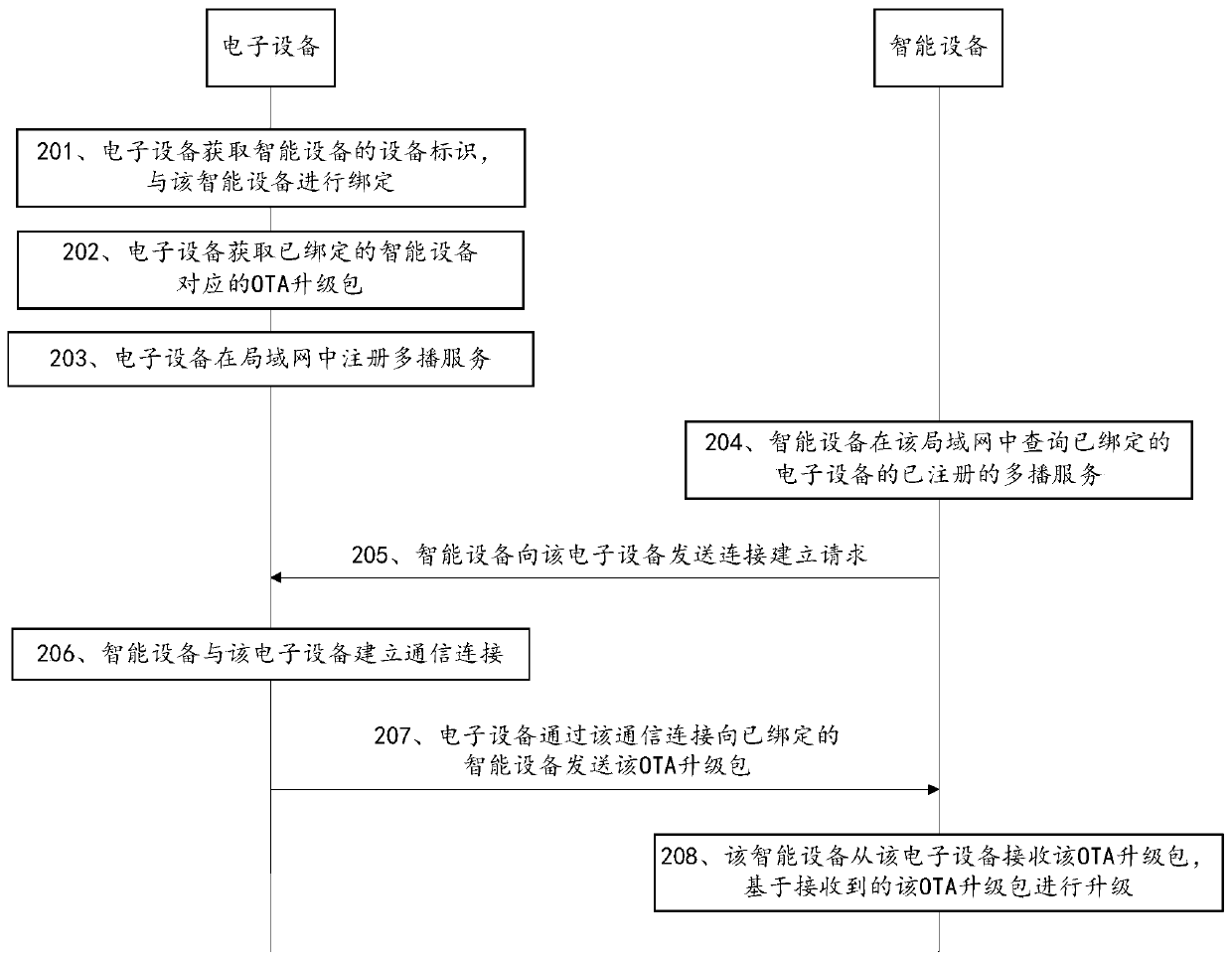
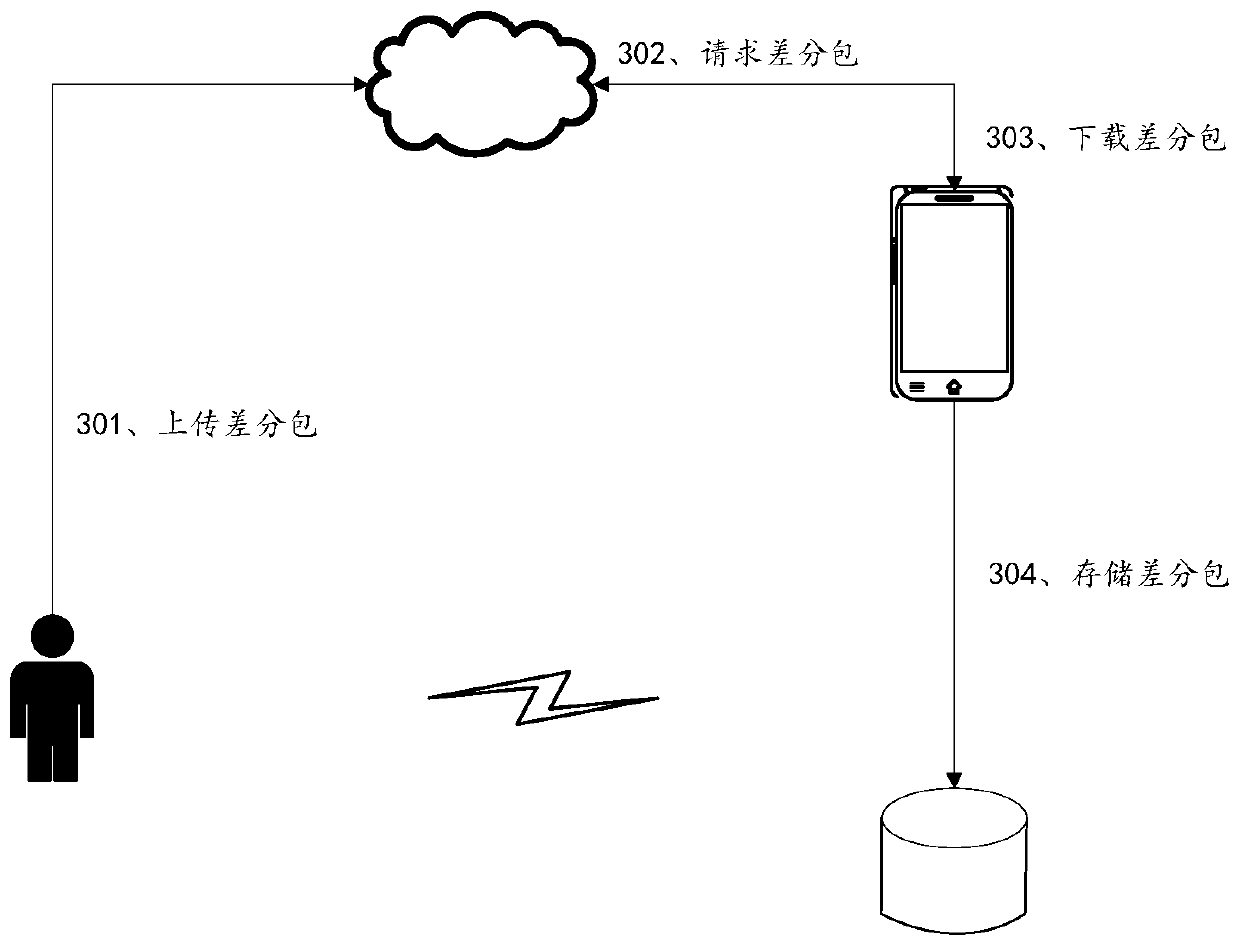
OTA upgrading method, OTA upgrading device and computer equipment
ActiveCN110362328ATroubleshoot upgrade issuesGuaranteed upgrade efficiencySoftware deploymentNetwork data managementService personnelComputer science
The invention discloses an OTA upgrading method, an OTA upgrading equipment and computer equipment, and belongs to the technical field of networks. The method comprises the steps of obtaining an OTA upgrade package corresponding to bound intelligent equipment by electronic equipment, sending the OTA upgrade package to intelligent equipment through communication connection with the intelligent equipment, and carrying out upgrading operation by the intelligent equipment upon receiving the OTA upgrade package. According to the invention, the OTA upgrade package is downloaded through the electronic equipment and the OTA upgrade package does not need to be actively downloaded by intelligent equipment. Therefore, the intelligent equipment cannot be connected to the wide area network. The OTA upgrading can still be carried out. The advantages of upgrading the system without loss, repairing system bugs and optimizing system functions of OTA upgrading are ensured; and moreover. The OTA upgrading problem when the intelligent equipment is abnormal and cannot access the network is solved. The defect that an existing upgrading mode is very inconvenient for after-sales service personnel and users far away from the location is overcome, and the upgrading efficiency is ensured.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Image encryption system, image decryption system, image encryption method and image decryption method
ActiveCN106100819AHigh strengthImprove protectionEncryption apparatus with shift registers/memoriesPlaintextComputer hardware
The invention provides an image encryption system, an image decryption system, an image encryption method and an image decryption method. The image encryption system comprises a cellular automaton, a first encryption module connected with the cellular automation, a scrambling mapping table generation module connected with the cellular automation, and a second encryption module connected with the first encryption module and the scrambling mapping table generation table. Reversible information mixing is carried out at paintext of pseudorandom chaos sequences and image data, thereby, after a numerical value of the image data is encrypted, the data encrypted at the first time is divided into a plurality of data blocks, and the data blocks are recombined according to a scrambling mapping table so as to scramble positions of the data encrypted at the first time, thus, intensity of information chaord is greater, and ciphertext digital sequences are more irregular; that attackers cannot calculate the pseudorandom sequences for the first time encryption through public algorithm details is ensured, technical bugs of the existing algorithm technology are remedied, and long-term information protection for users used to encrypting multiple sets of data with the same key is realized.
Owner:SHANGHAI IRAY TECH
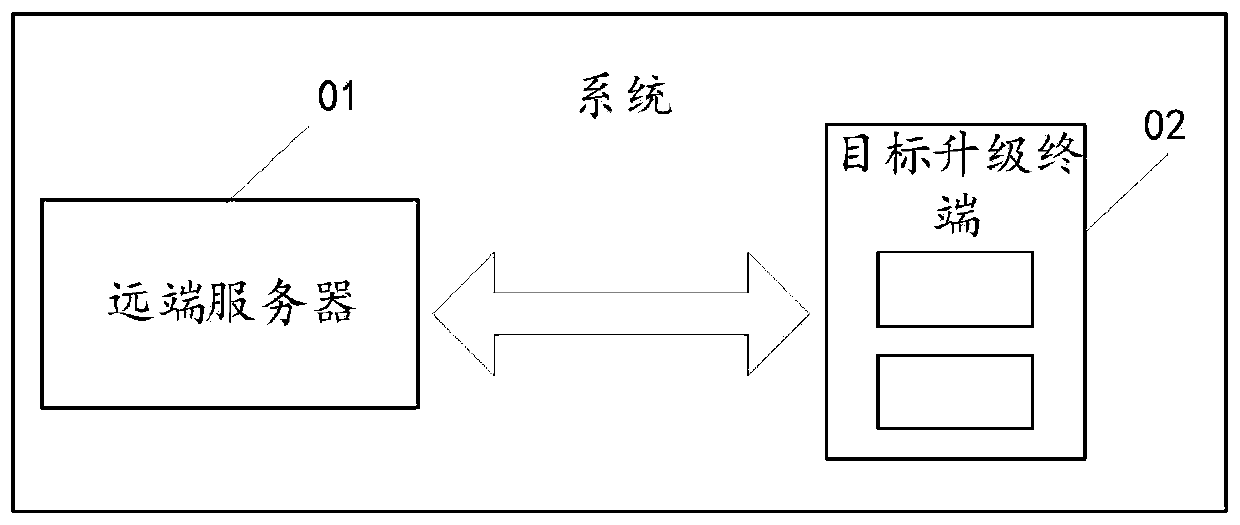
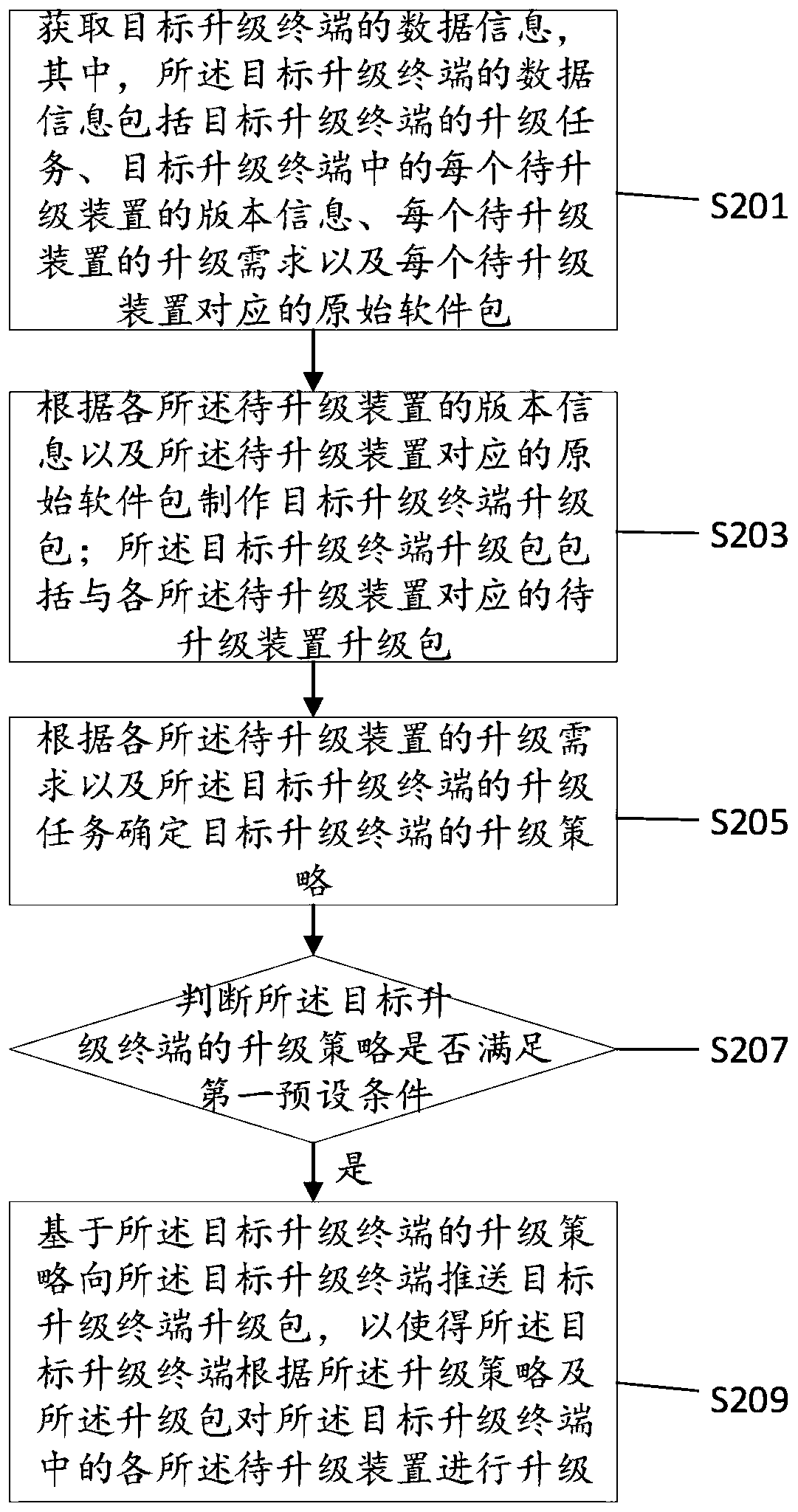
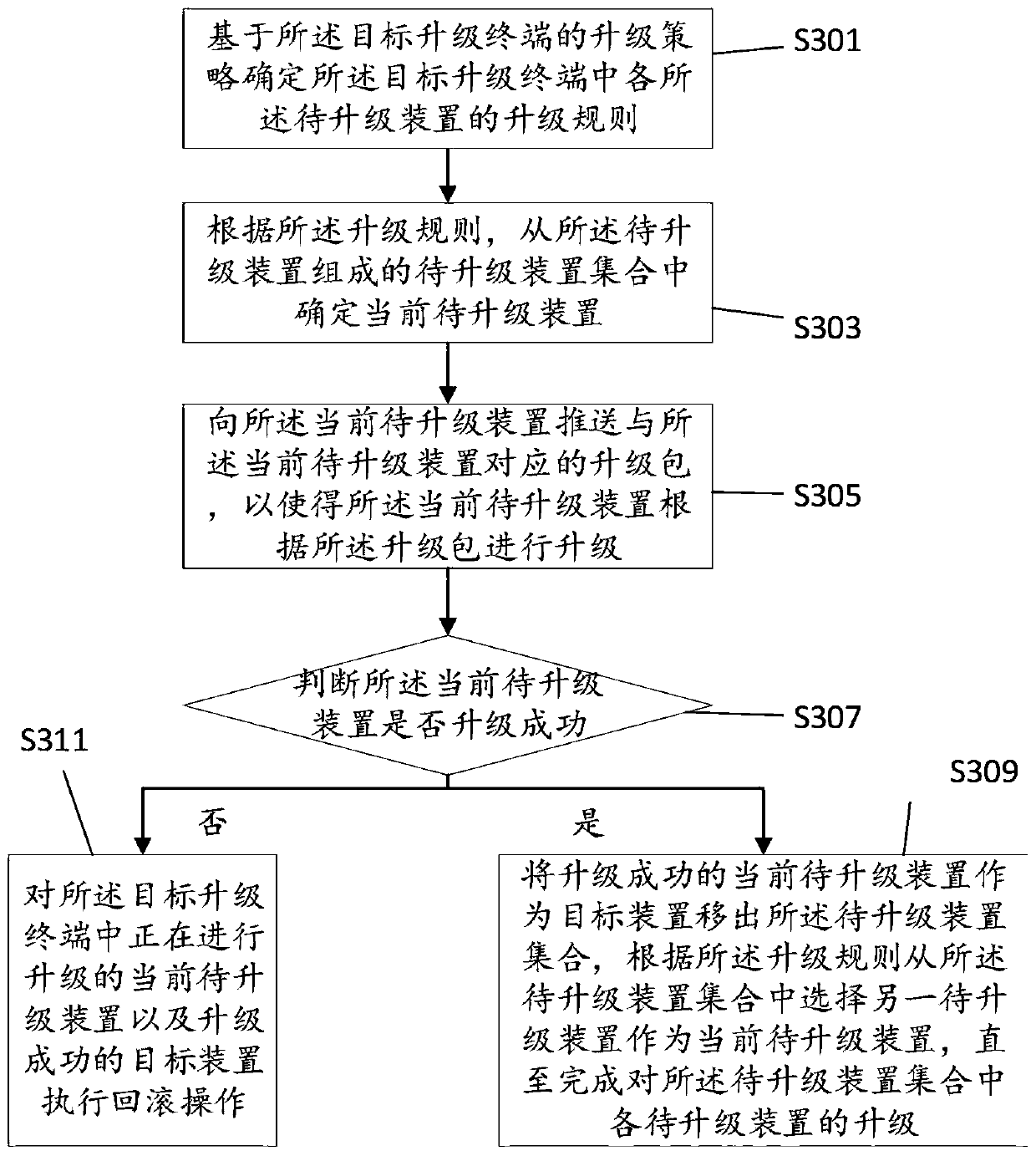
Terminal upgrading method and device, terminal and storage medium
The invention discloses a terminal upgrading method and device, a terminal and a storage medium. The method comprises: obtaining an upgrading task of a target upgrading terminal, version information of each to-be-upgraded device in the target upgrading terminal, an upgrading demand of each to-be-upgraded device and an original software package corresponding to each to-be-upgraded device; making atarget upgrading terminal upgrading package according to the version information of each to-be-upgraded device and the original software package corresponding to the to-be-upgraded device; determiningan upgrading strategy of the target upgrading terminal according to the upgrading requirement of each to-be-upgraded device and the upgrading task of the target upgrading terminal; and when the upgrading strategy of the target upgrading terminal meets a first preset condition, pushing the target upgrade terminal upgrade package to the target upgrade terminal based on the upgrade strategy of the target upgrade terminal, so that the target upgrade terminal upgrades each to-be-upgraded device in the target upgrade terminal according to the upgrade strategy and the upgrade package, and the security risk and vulnerability of the target upgrade device information can be quickly solved from the far end.
Owner:ZHEJIANG GEELY NEW ENERGY COMML VEHICLES CO LTD +3
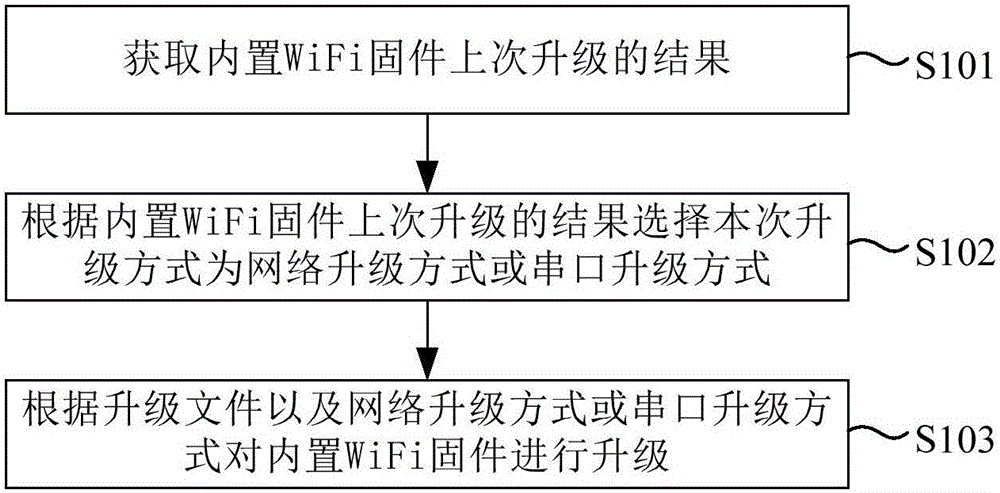
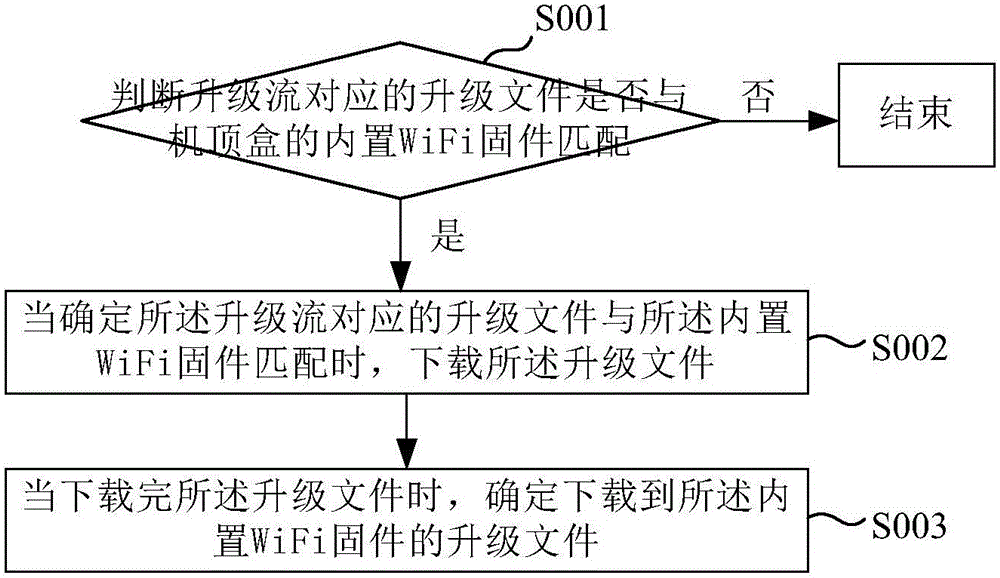
Method and device for upgrading built-in WiFi firmware of set top box, and set top box
ActiveCN106131682AImprove performanceMake up for loopholesProgram loading/initiatingSelective content distributionSet top boxError state
The invention relates to a method and a device for upgrading built-in WiFi firmware of a set top box, and the set top box. The method comprises the steps of when an upgrade file of the built-in WiFi firmware is downloaded, acquiring a result of a previous upgrade of the built-in WiFi firmware, selecting a network upgrade mode or a serial port upgrade mode as a current upgrade mode according to the result of the previous upgrade of the built-in WiFi firmware, and upgrading the built-in WiFi firmware according to the upgrade file and the network upgrade mode or the serial port upgrade mode. According to the method provided by the embodiment of the invention, the situation that the built-in WiFi firmware cannot be upgraded due to the fact that the power of the built-in WiFi firmware is failed unexpectedly, an upgrade program is damaged or the built-in WiFi firmware is in an error state is avoided, a possibility that the firmware cannot be upgraded can be prevented in advance, and thus bugs in the built-in WiFi firmware can be effectively remedied, and the whole performance of the set top box can be greatly improved.
Owner:HISENSE BROADBAND MULTIMEDIA TECH
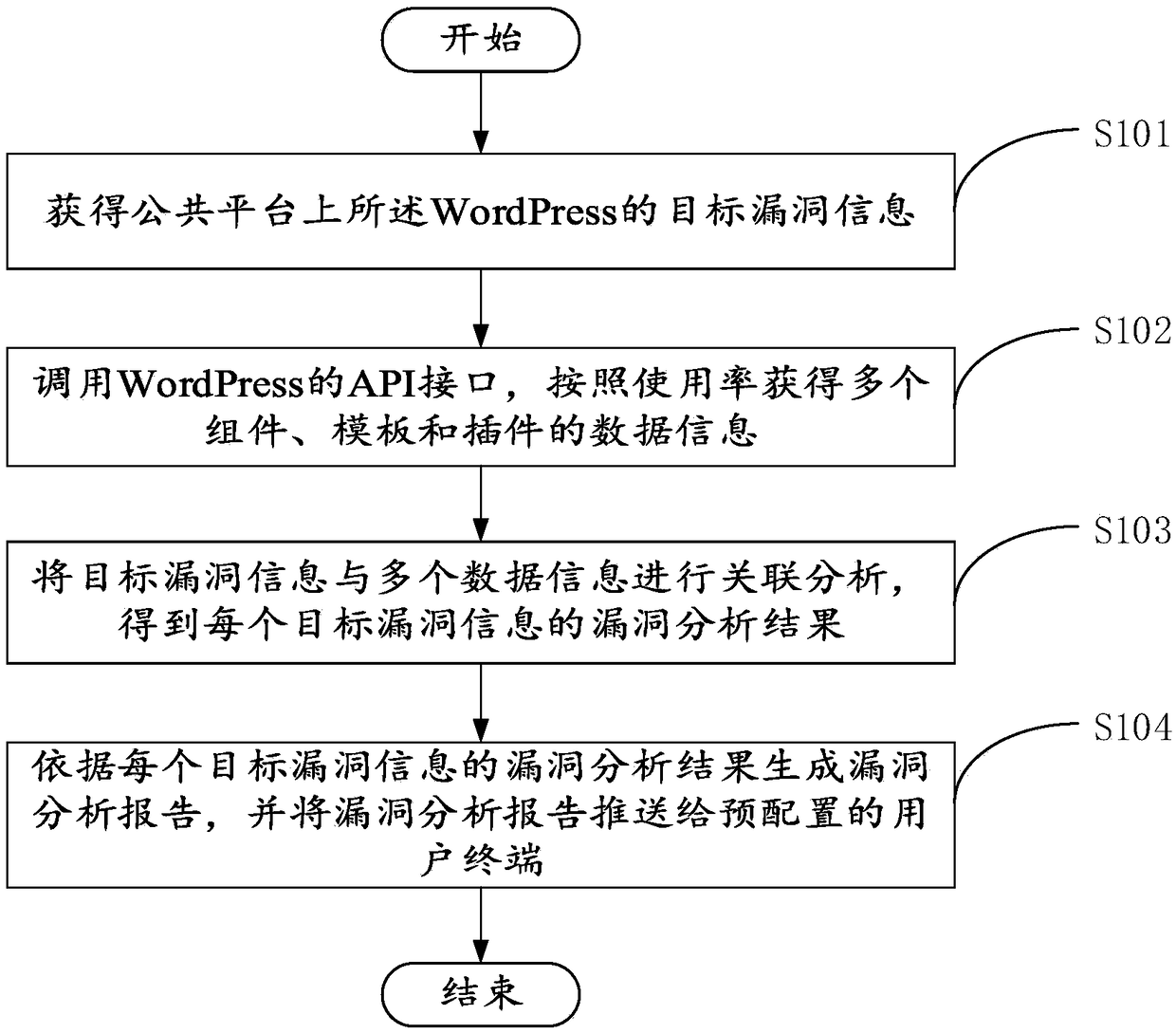
Method and device for vulnerability analysis based on WordPress
The invention provides a method and device for vulnerability analysis based on WordPress, and relates to the field of vulnerability detection. The method for vulnerability analysis based on WordPressis applied to servers, and comprises the steps that target vulnerability information of WordPress on a public platform is obtained; an API interface of WordPress is called, the data information of multiple assembles, templates and plug-ins is obtained according to the usage rate; the target vulnerability information and multiple data information are correlated and analyzed, and a vulnerability analysis result of each target vulnerability information is obtained; a vulnerability analysis report is generated according to the vulnerability analysis result of each piece of target vulnerability information, and the vulnerability analysis report is pushed to a pre-configured user terminal. The method and device for vulnerability analysis based on WordPress can comprehensively collect vulnerability information about WordPress in the Internet, and remind the user to update patches or update versions to fix the vulnerability.
Owner:BEIJING KNOWNSEC INFORMATION TECH
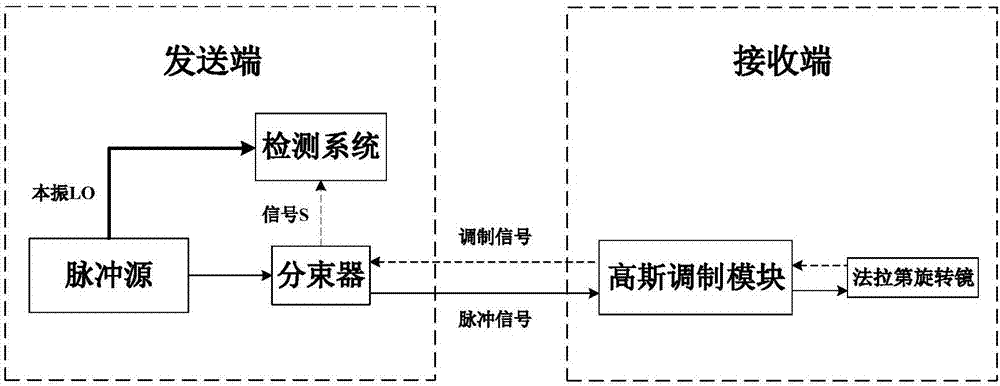
Reciprocating Gauss modulated continuous variable quantum key distribution method and device
InactiveCN107453867AStrong implementability and securityAvoid transmissionKey distribution for secure communicationPhase jitterTransfer procedure
The invention discloses a reciprocating Gauss modulated continuous variable quantum key distribution method and device. The method comprises the following steps: S1, pulse source generation; S2, local oscillation light and signal light separation; S3, quantum signal Gauss modulation; S4, quantum signal reversal; and S5, quantum signal detection. The method and the device are of very high safety and practicability. By generating local oscillation light at an emitting end and detecting signals at the emitting end, the transmission of local oscillation light is avoided, and eavesdroppers can no longer take advantage of the transmission of local oscillation light. As the local oscillation light and the signal light are from the same light source, the frequency difference is small, the phase jitter is low, and therefore, the phase noise is greatly reduced. Because of the adoption of a reciprocating structure, compensation can be automatically made for polarization drift in the transmission process, and degradation of the system performance caused by polarization drift is avoided. Thus, the scheme improves the long-time stability of the system.
Owner:SHANGHAI JIAO TONG UNIV
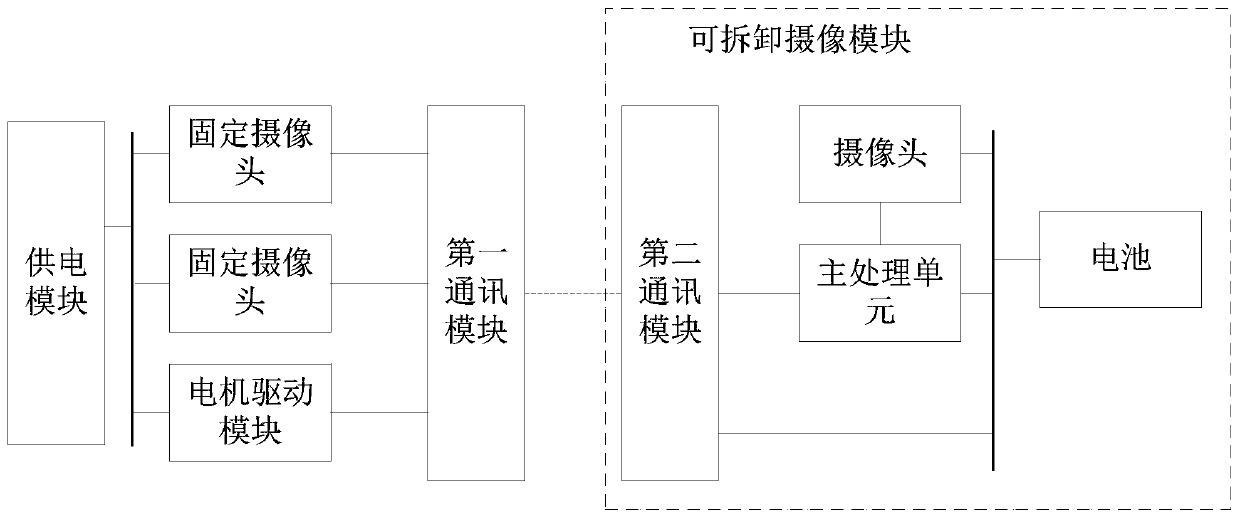
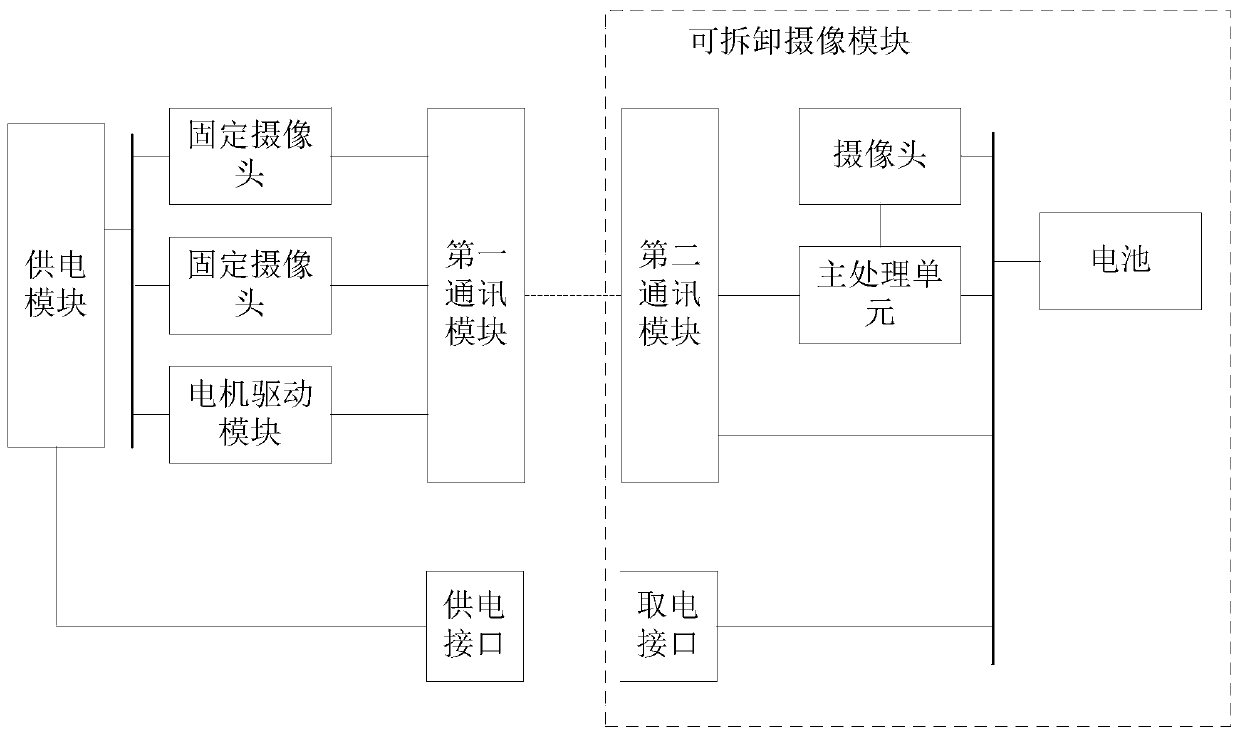
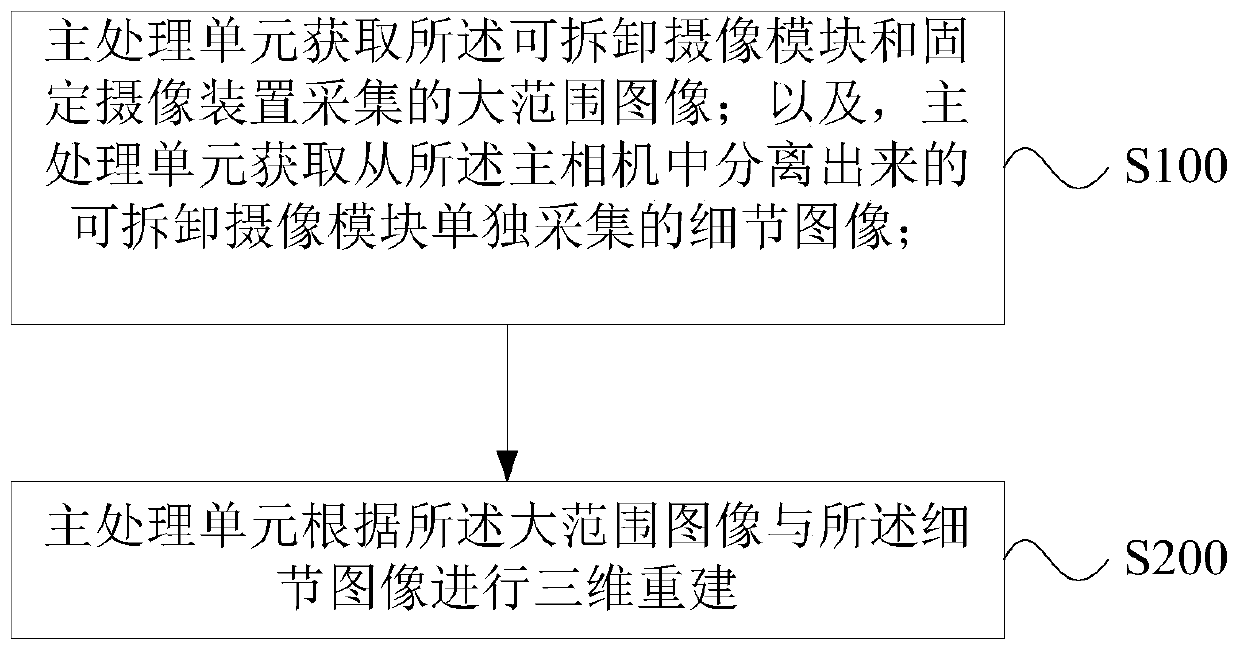
Three-dimensional reconstruction system and method
PendingCN110070607AMake up for loopholesImage enhancementImage analysisMain processing unitSerial scanning
The invention discloses a three-dimensional reconstruction system and method. The system comprises a main camera. The main camera comprises a detachable camera module and a fixed camera device which are used for collecting large-range images together, and the detachable camera module can be separated from the main camera and can independently collect detail images. The detachable camera module comprises a main processing unit. The main processing unit is used for acquiring a large-range image and carrying out three-dimensional reconstruction according to the large-range image and the detail image. The overall space is required to be roughly reconstructed; the detachable camera module of the main camera and the fixed camera device can be used for jointly acquiring a large-range image. Whena small object needs to be continuously scanned, the detachable camera module can be directly separated from the main camera for use, the detachable camera module is independently used for collectingdetail images, and finally the main processing unit in the detachable camera module carries out three-dimensional reconstruction according to the large-range images and the detail images, so that after normal indoor scanning, the detachable camera module is used for scanning details, and vulnerabilities are filled.
Improved train control system security data interaction method
ActiveCN110267266AIncrease the lengthMake up for loopholesNetwork traffic/resource managementEncryption apparatus with shift registers/memoriesOccupancy rateTransceiver
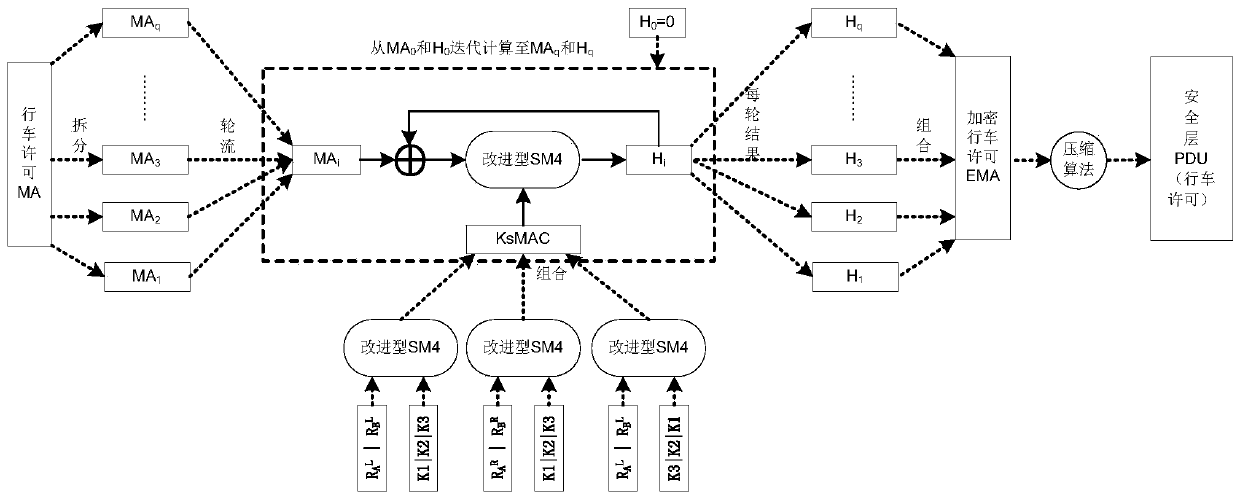
The invention discloses an improved train control system secure data interaction method, which comprises the following steps of: expanding the shared key of a data transceiver and the length of a random number generated and shared by the transceiver, and calculating a session key with an increased key length by matching with a corresponding SM4 algorithm; dividing the security data X of the train control system into blocks according to N bits, using a data block and a full text of a session key as input in each round, performing iterative computation by using a corresponding SM4 algorithm, and generating an N-bit operation result Hi corresponding to the corresponding data block; regarding the operation result Hi as encrypted data of the corresponding data block, and covering the corresponding data block, so that the security encryption of the security data X of the train control system is realized; and selecting a corresponding lossless compression algorithm according to the type of the train control system security data, performing data lossless compression on the full-text encrypted train control system security data X, and sending the compressed data X to a receiver. According to the method, the data security is greatly improved, and meanwhile, the occupancy rate of wireless resources is reduced.
Owner:CHINA RAILWAYS CORPORATION +2
Implementation method of business process automatic supervision aid decision making
InactiveCN105631579AImprove audit qualityStrengthen early warning information managementResourcesBusiness dataSafe system
The invention discloses an implementation method of business process automatic supervision aid decision making. According to the method, based on mass information comparison, a data model is established; a comprehensive real-time decision role which acts as an aid decision making system and a data security system is provided; the method can go deep into a business system; the business process of the business system is analyzed; the loopholes of the business system are filled; the operation logs of the business system are recorded in a whole process; data identification is carried out with a absolutely neutral standing point; logic judgment is clear; feedback results are sent to a user terminal according to needs; illegal operation in the business system can be avoided; supervision standards are unified; audit quality after business handling can be improved; the early warning information management of the business data of the business system is strengthened; as for some systems, with an aid function well provided, the quality of services can be improved, and people's satisfaction can be improved; the image of the user can be enhanced; through system classified statistic modeling, decision-making data can be provided for the promotion of the healthy development of work; and business handling quality and efficiency can be further improved, and the business handling efficiency can be increased by more than 50%.
Owner:尚德软件股份有限公司
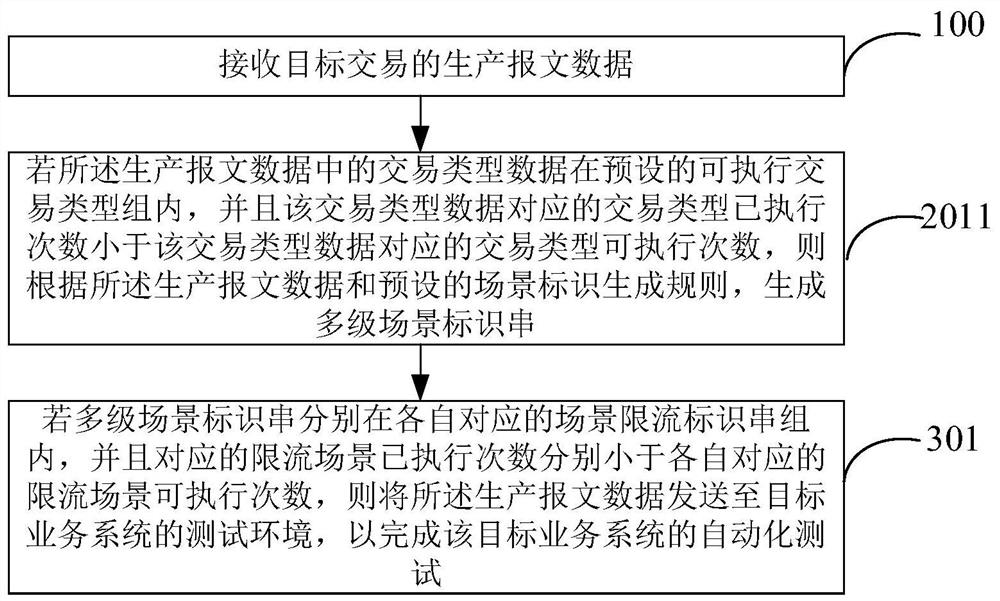
Automatic test method and device for service system
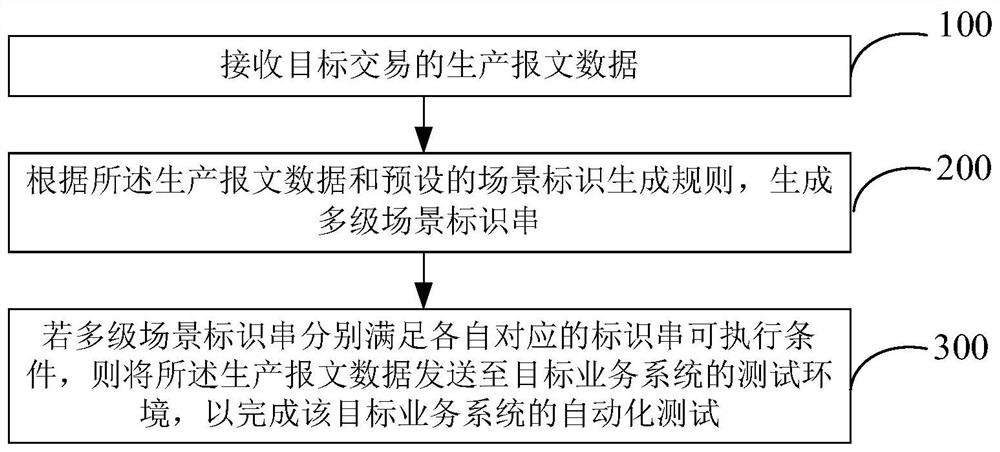
PendingCN112799943AImprove automated testing efficiencySecurity Scenario CoverageSoftware testing/debuggingManufacturing computing systemsFinancial transactionAutomatic testing
The invention provides an automatic test method and device for a service system, which can be used in the financial field or other fields, and the method comprises the following steps: receiving production message data of a target transaction; generating a multi-stage scene identification string according to the production message data and a preset scene identification generation rule; and if the multiple stages of scene identification strings respectively meet respective corresponding identification string executable conditions, sending the production message data to a test environment of a target service system to complete the automatic test of the target service system. According to the method and device, repeated scene testing can be avoided, the efficiency of automatic testing of the service system can be improved, and then the safety of system operation can be improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
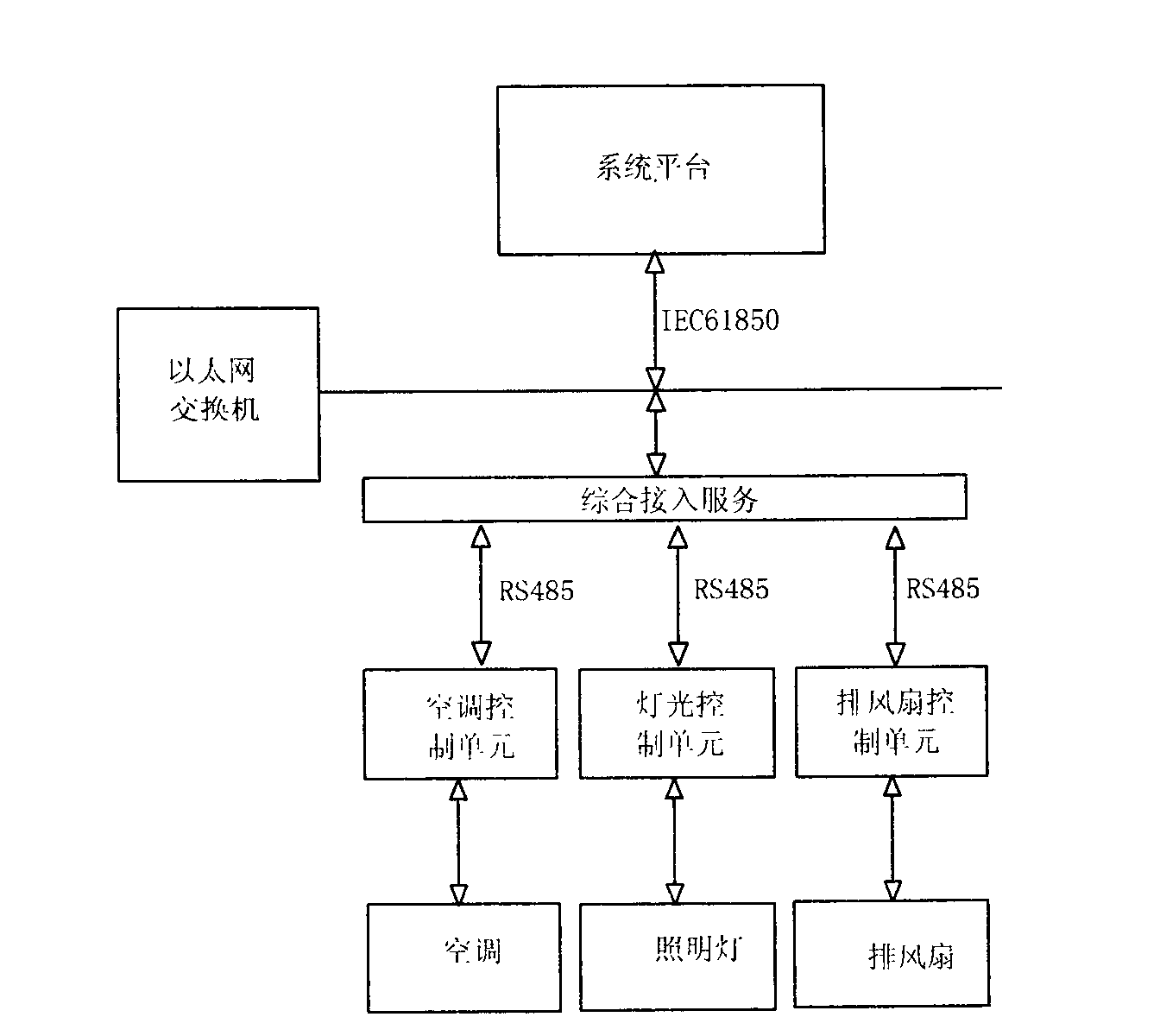
Remote intelligent regulation and control system for operating environment of unmanned substation
InactiveCN102122840AImprove safety and reliabilityAdd smart adjustmentsPower network operation systems integrationCircuit arrangementsOperating environmentControllability
The invention discloses a remote intelligent regulation and control system for an operating environment of an unmanned substation. In the system, remote control and real-time state monitoring of air conditioning, exhaust fans and lamplights in the substation are realized through integrated, low-carbon and intelligent control equipment. The operating environment of the unmanned substation can be effectively and remotely regulated and controlled through an environmental control unit, the comprehensive control, controllability and in-control of the operating environment of the unmanned substation are realized, and the safety and stability of operating the substation are improved.
Owner:ZAOZHUANG POWER SUPPLY COMPANY OF STATE GRID SHANDONG ELECTRIC POWER
Voice recognition character string processing comparison method based on Pinyin
PendingCN108874872AMake up for loopholesAccurate identificationNatural language data processingSpecial data processing applicationsUTF-8Recognition algorithm
The invention relates to a voice recognition character string processing comparison method based on Pinyin. For application of an existing voice recognition technology to certain special occasions ofperson name recognition, equipment name recognition and the like, errors are generated easily due to incorrect comparison. The method is "secondary processing" based on a general Chinese character recognition algorithm; and recognized Chinese character strings are converted into Pinyin strings, and then the Pinyin strings are compared with target Pinyin strings. The method comprises the followingsteps of 1, performing Pinyin coding: performing coding on all Chinese character Pinyin, wherein the coding is similar to coding of unicode; and enumerating all Chinese character Pinyin combinations;2, performing code conversion: converting the character strings, with coding modes of GBK, Unicode, UTF-8 and the like, for expressing Chinese characters converted into the Pinyin strings; and 3, performing polyphone processing: enumerating polyphones of all family names; performing special processing; and distributing the same Pinyin codes. According to the method, accurate recognition can be rapidly realized, so that misjudgment is avoided.
Owner:深圳市艾塔文化科技有限公司
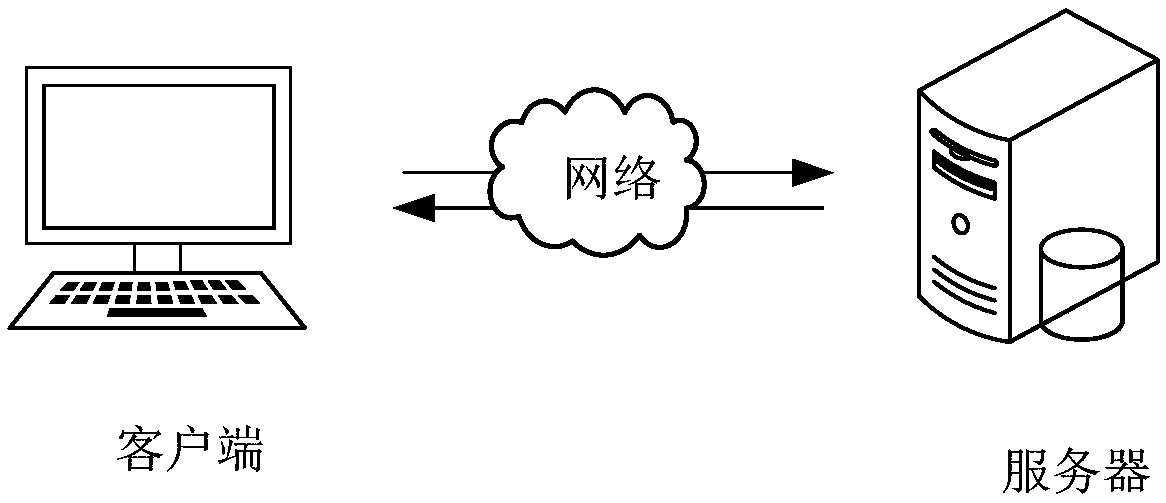
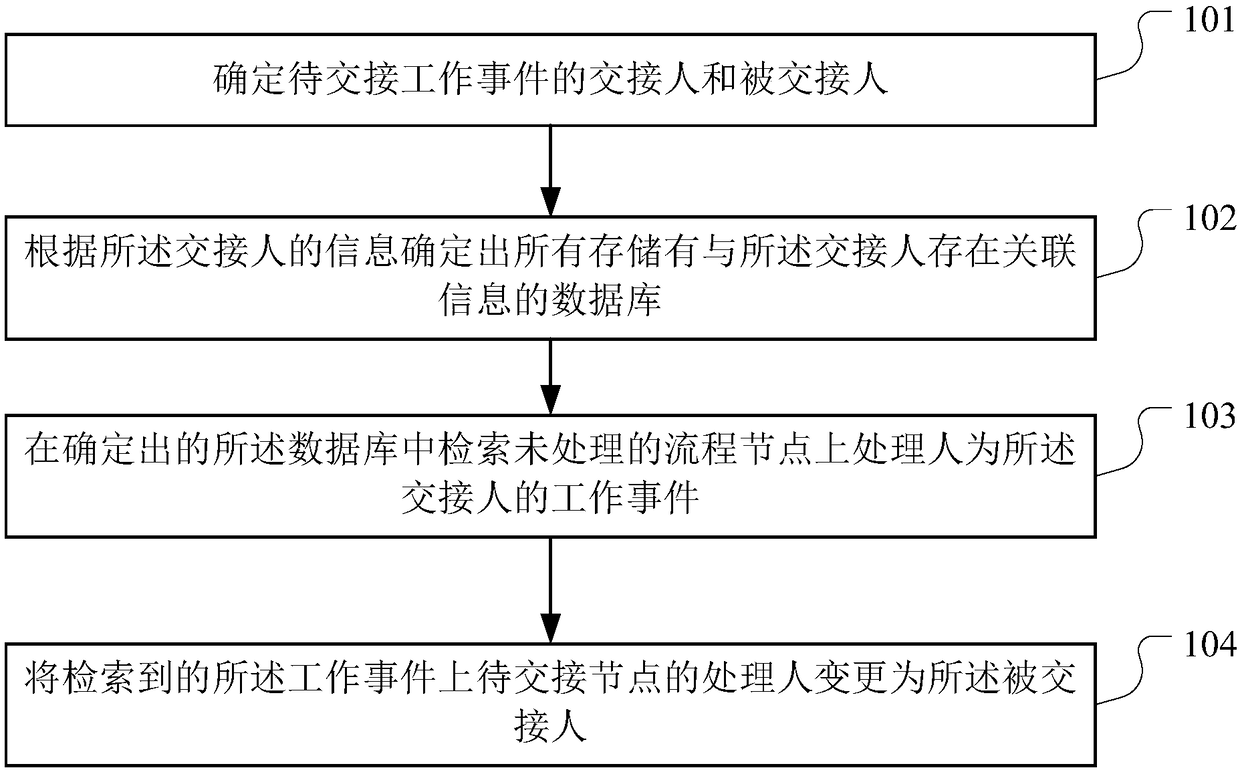
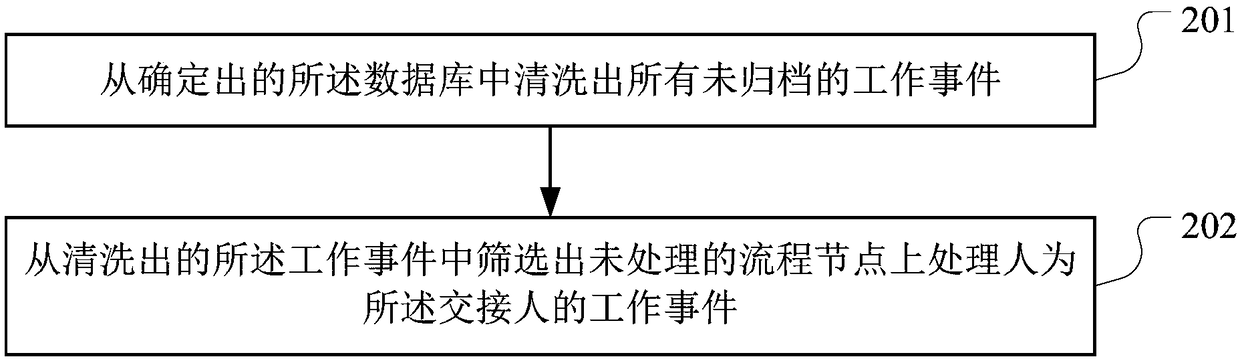
Work event intelligent handover method and device, computer device and storage medium
PendingCN109325727AFill in the holesFull Coverage GuaranteedDigital data information retrievalOffice automationComputer deviceHandover
The invention discloses a work event intelligent handover method, which is used for solving the problem that the prior work handover is easy to be omitted. The method provided by the invention comprises the following steps of: determining the handover person and the handover person of the work event to be handled; determining all databases storing information associated with the existence of the handover person according to the information of the handover person; ;processing the work event for the handover person on retrieving an unprocessed flow node in the determined database; changing the handler of the node to be handled on the retrieved work event to the handled person, wherein the node to be handled refers to an unhandled flow node for which the handler is the handler. The inventionalso provides a work event intelligent handover device, a computer device and a storage medium.
Owner:PING AN TECH (SHENZHEN) CO LTD
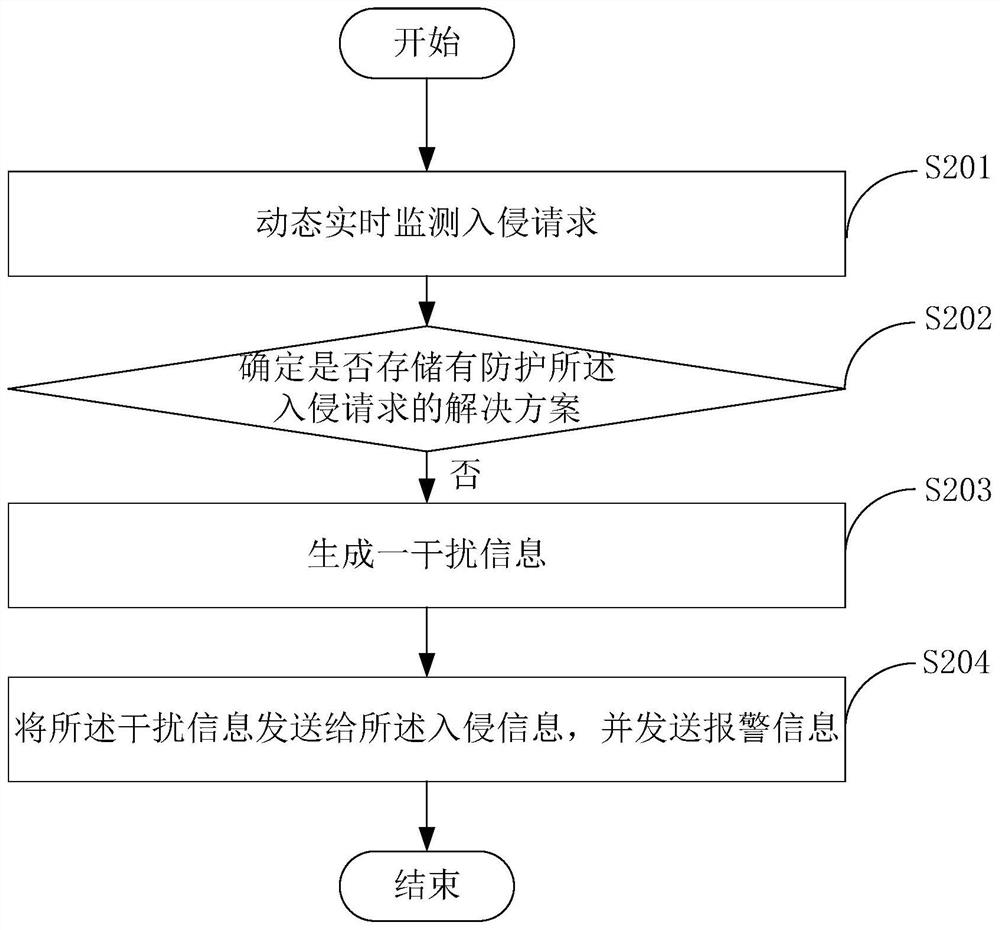
Dynamic security protection method and system for industrial Internet
The embodiment of the invention provides a dynamic security protection method and system for an industrial Internet, and belongs to the technical field of the Internet. The method comprises the following steps: dynamically monitoring an intrusion request in real time, wherein an intrusion event comprises all access requests which cannot be identified by a server; determining whether a solution forprotecting the intrusion request is stored or not, wherein a plurality of solutions for coping with multiple types of intrusion requests are pre-stored in the server, and the solution is one of the plurality of solutions; if not, generating a piece of interference information, wherein the interference information comprises an empty IP address; and sending the interference information to the intrusion information, and sending alarm information. According to the method, the probability of being intruded can be effectively reduced, and human resources can be saved at the same time.
Owner:唐琪林
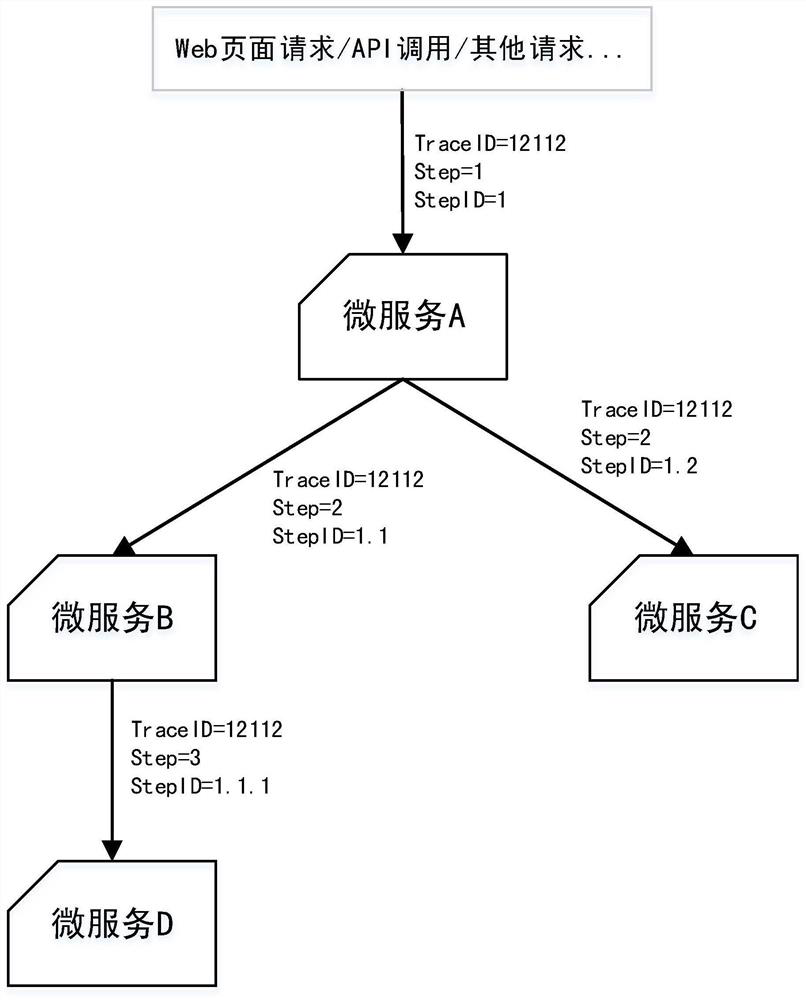
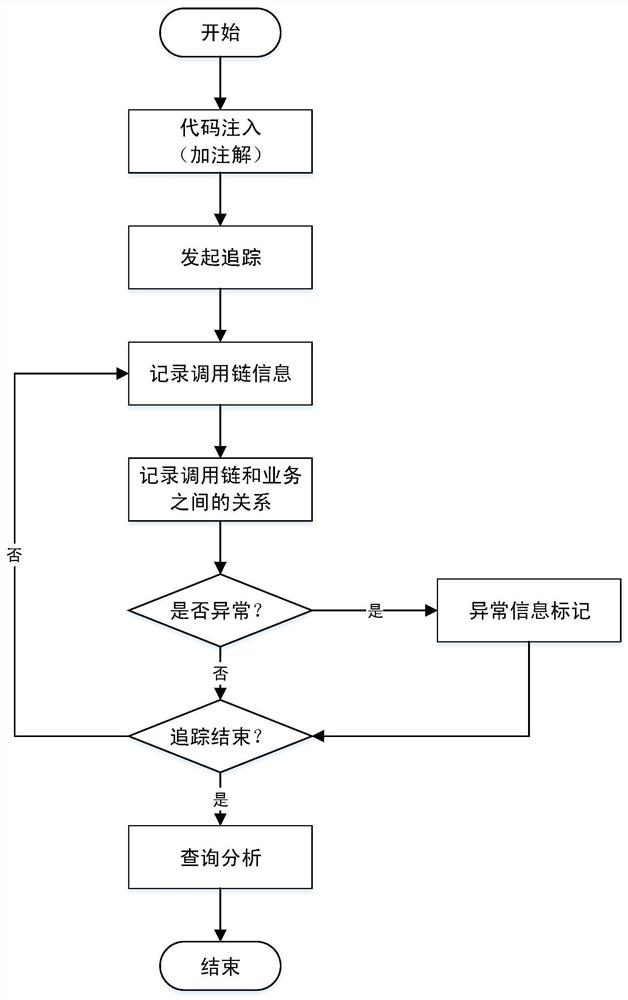
AOP annotation-based call chain tracking and service analysis method
PendingCN113986669AOptimizerTo achieve the purpose of buryingCode refactoringHardware monitoringMicro servicesEngineering
The invention discloses an AOP annotation-based call chain tracking and service analysis method, which comprises the following steps of: adding an annotation during development, and initiating call chain tracking; recording the calling chain information by using a log, and connecting the micro-service and the calling relationship in series by using the TraceID; adding StepID between micro-service calling chains, and identifying the nested relation of service calling in the calling chains; performing bidirectional association, establishing a relationship between the call chain and the business, and recording the relationship between the call chain TraceID and the business ID by using a log; judging whether the system is abnormal or not, and if not, judging whether tracking is ended or not; if so, positioning and marking abnormal information by using a log, and judging whether tracking is ended or not; and finally, enabling a developer to query logs and exception information from different dimensions to optimize codes to solve exceptions. According to the method, the micro-service calling chain and service analysis function is achieved by recording the relation between the calling chain and the service, when the program is abnormal, checking is conducted from the two aspects of the calling chain and the service, and developers are helped to rapidly position the abnormity and repair vulnerabilities.
Owner:北京航天云路有限公司
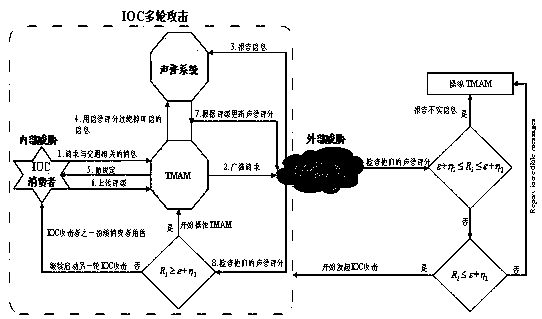
System and method for safely defending collusion attacks under Internet of Vehicles
ActiveCN110139278AImprove securityPrevent overloadParticular environment based servicesAnti-theft devicesInternet privacyAttack
The invention discloses a system and a method for safely defending collusion attacks under the Internet of Vehicles. The system and the method improve the reputation score of the system in an internalcollusion mode and an external collusion mode to manipulate a TMAM. The IOC attack can be rapidly detected, and the safety of the Internet of Vehicles is improved. Through recursion, suspicious providers and proposed reputation fluctuation association rules are eliminated, and overload of the TMAM is avoided. An IOC attacker can be deprived to prompt its reputation scoring opportunity and ensuretrusted information in the Internet of Vehicles. The fairness and the availability of the TMAM are ensured under the condition that the TMAM is not interfered by an IOC attacker. The defect that in the prior art, a reputation system can be utilized by an IOC attacker to improve the reputation score of the attacker so as to manipulate the TMAM is effectively avoided.
Owner:XIAN ANMENG INTELLIGENT TECH CO LTD
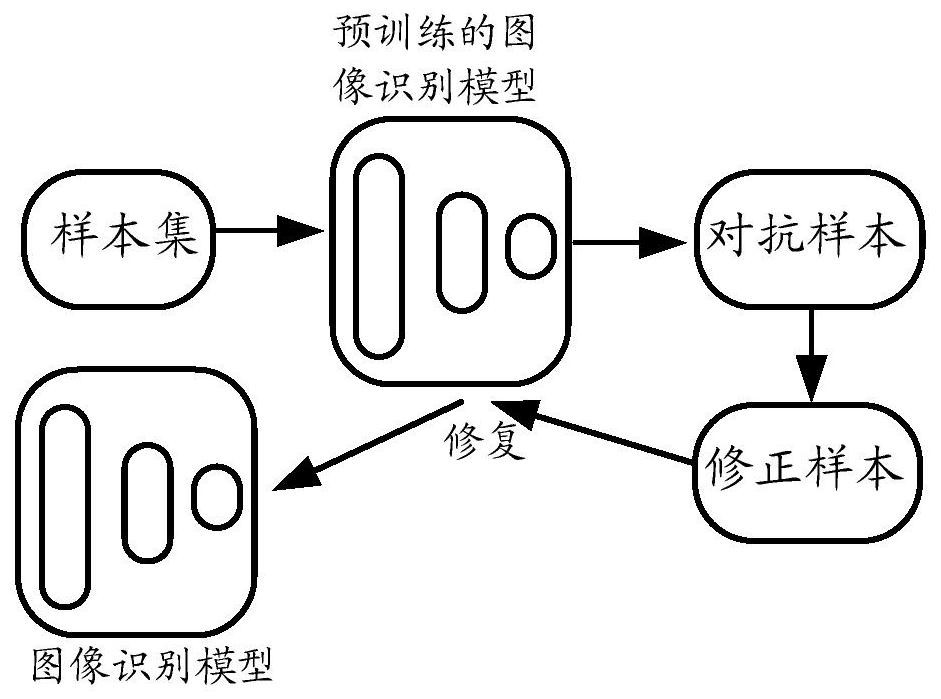
Processing method and device for image recognition model
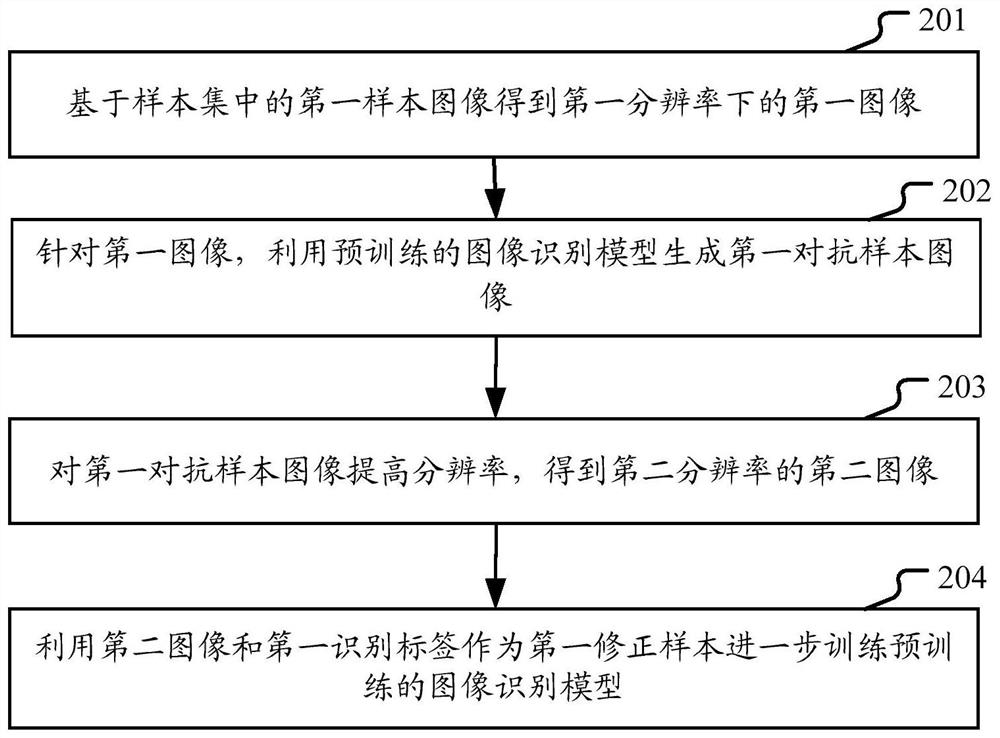
ActiveCN113379001AMake up for loopholesImprove robustnessCharacter and pattern recognitionNeural architecturesImage resolutionSample image
The embodiment of the invention provides a processing method and device for an image recognition model. Through the method and device provided by the embodiment of the invention, for the image recognition model pre-trained by using a sample set, a first image under a relatively small first resolution is obtained based on a first sample image in the sample set, then, for the first image, a first adversarial sample image is generated by using a pre-trained image recognition model, and then the resolution of the first adversarial sample image is improved to obtain a second image under a larger second resolution, and the pre-trained image recognition model is further trained by using the second image and the first recognition tag corresponding to the first sample image as a first correction sample, so that the corrected image recognition model is used for image recognition. According to the embodiment, the model vulnerability is found through the low-resolution image, and the model vulnerability is repaired through the high-resolution image, so that the robustness of the image recognition model is improved.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Method for repairing written document
InactiveCN102797196ARepair wrinklesMake up for loopholesOld paper after-treatmentWrinkleVulnerability
The invention discloses a method for repairing a written document, which is characterized by comprising the following steps: firstly, clearing up dust and stains on the surface of the written document; secondly, ironing wrinkles of the written document treated in the first step by using an electric iron; thirdly, treating breakage and holes of the written document treated in the second step by using a sticker repairing process; fourthly, sticking deckle edges to four sides of the written document treated in the third step; and fifthly, naturally airing the written document treated in the fourth step at a shade, and then, filing and preserving. The technical scheme of the invention is simple in flow and simple and convenient for working procedure; not only can the wrinkles and the holes of the written document be repaired, but also the whole strength of the document is enhanced by sticking the deckle edges to the four sides of the written document; and the method is beneficial to the preservation and retreatment of the written document.
Owner:ANHUI BAOHULU INFORMATION TECH GRP
MySQL-based real-estate sales management system
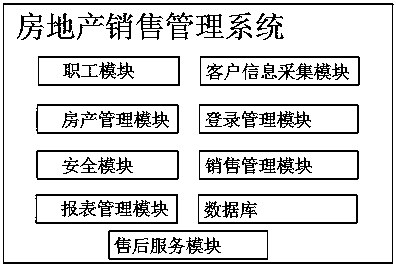
InactiveCN108133435AEasy to follow upUnderstand the reflected situationOffice automationBuying/selling/leasing transactionsProgram planningSecurity Measure
The invention discloses a MySQL-based real-estate sales management system. The system comprises an employee module, a client information collection module, a real-estate management module, a logging-in management module, a safety module, a sales management module, a report management module, a database and an after-sale service module. The system enables the main line of sales to be clear, so thatthe work of salesman is orderly, the timely follow-up of multiple business main lines is facilitated, the system has a sales prompt function, helps an enterprise to find out a business opportunity and to formulate a development plan and a marketing strategy, real-time statistics and sales and analysis can be performed, rapid exchange with a client is implemented, multi-level safety measures are taken, encrypted files of a user are protected in a safer manner, the bug of an existing secrecy system is made up, the situation reflected by the user can be understood conveniently so as to improve acorresponding technology in time, and the system can also help the client to solve problems as soon as possible, and is simple, convenient and easy to operate.
Owner:广州微房团网络科技有限公司
Intelligent building with intelligent community property management device
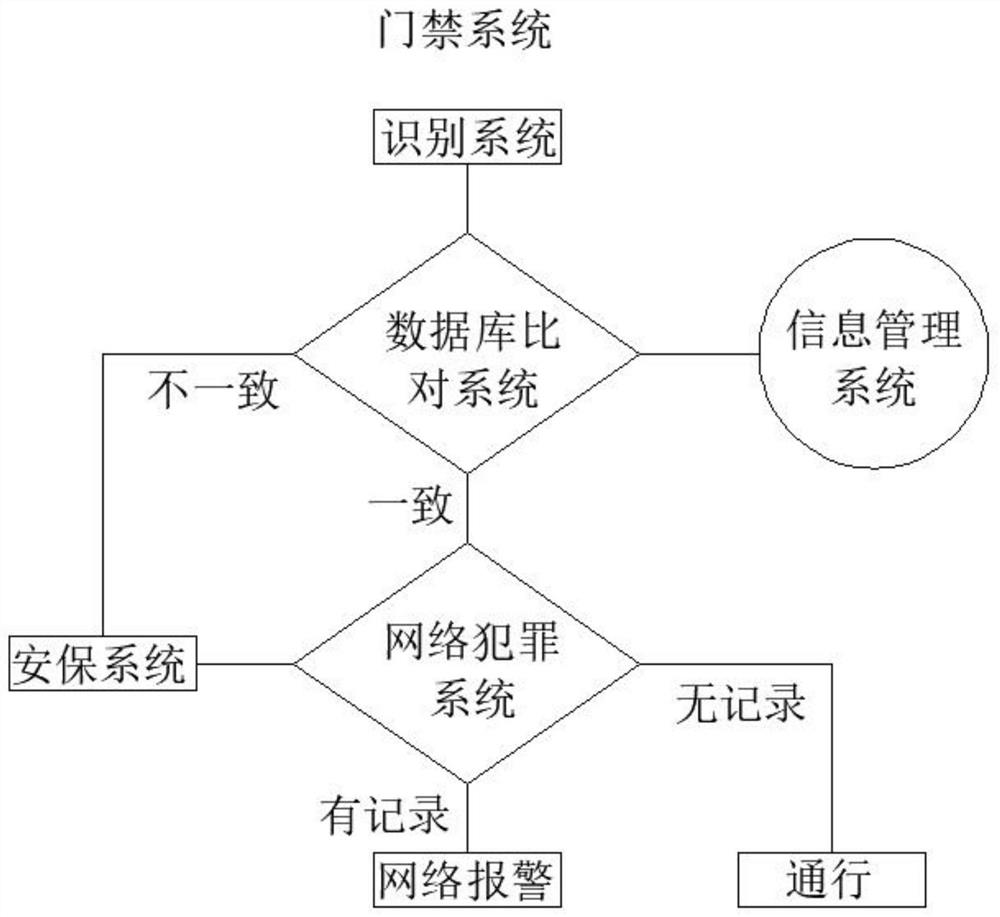
InactiveCN112037385AKeep your identity safeFunction increaseIndividual entry/exit registersCyber crimeNetwork on
The invention discloses an intelligent building with an intelligent community property management device, which comprises an identification system, a database comparison system, a network crime system, a security system and an information management system, and is characterized in that the identification system is used for performing safety identification on personnel entering the intelligent building; wherein the database comparison system is used for comparing identities of identification personnel with background data, the network crime system is used for comparing identity information of the identification personnel with crime information published on a network, the security system is used for field check, and the information management system is used for carrying out corresponding management operation on existing personnel information in a database. The identification system comprises an access control mechanism. The corresponding mechanism is additionally arranged in a property access control system, so that the functions of the access control system are increased, the access control system is safer and more reliable to use, free access of illegal criminals is avoided, the loophole of property management is made up, and therefore, the safety of an intelligent building can be ensured.
Owner:嘉兴新博信息科技有限公司
Dynamic application program updating method for vehicle-mounted embedded equipment
PendingCN113204356AResolving Function Semantic AmbiguitySolve multi-thread resource deadlockVersion controlSoftware deploymentIn vehicleEmbedded system
The invention relates to a dynamic application program updating method for vehicle-mounted embedded equipment, and belongs to the technical field of ECU dynamic updating. The remote server compares the program information reported by the automobile ECU with the existing latest program version of the ECU and sends an instruction that the ECU of the automobile is about to be updated to the TBOX of the automobile where the ECU needing to be updated is located, the TBOX sends the updating packet to the ECU through the CAN bus after receiving the updating packet, the ECU waits for the TBOX to send an updating instruction after receiving the updating packet, and the ECU starts to perform dynamic updating after receiving the updating instruction of the TBOX, and the updating is completed. The method has the advantages that software updating can be completed under the condition that operation of an original program is not affected, original data are protected from being lost, and the problems of function semantic ambiguity and multi-thread resource deadlock are solved.
Owner:JILIN UNIV
ETC card anti-mis-swiping mechanism and system for highway vehicle departure
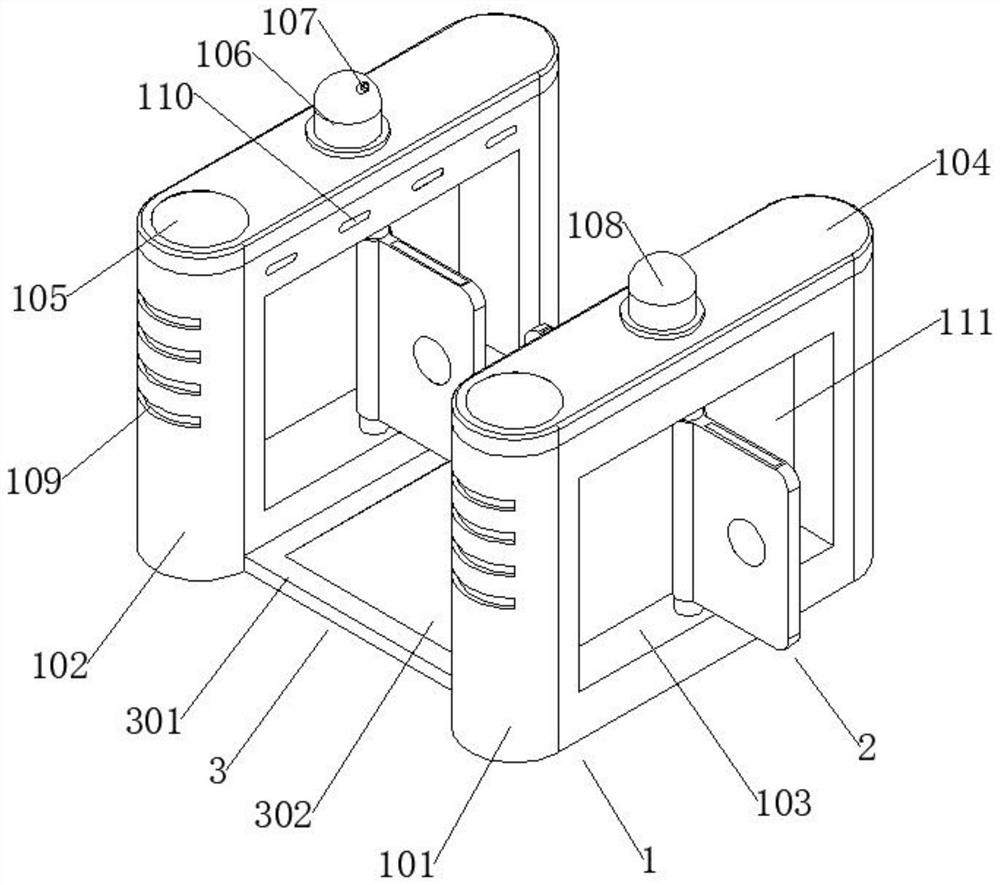
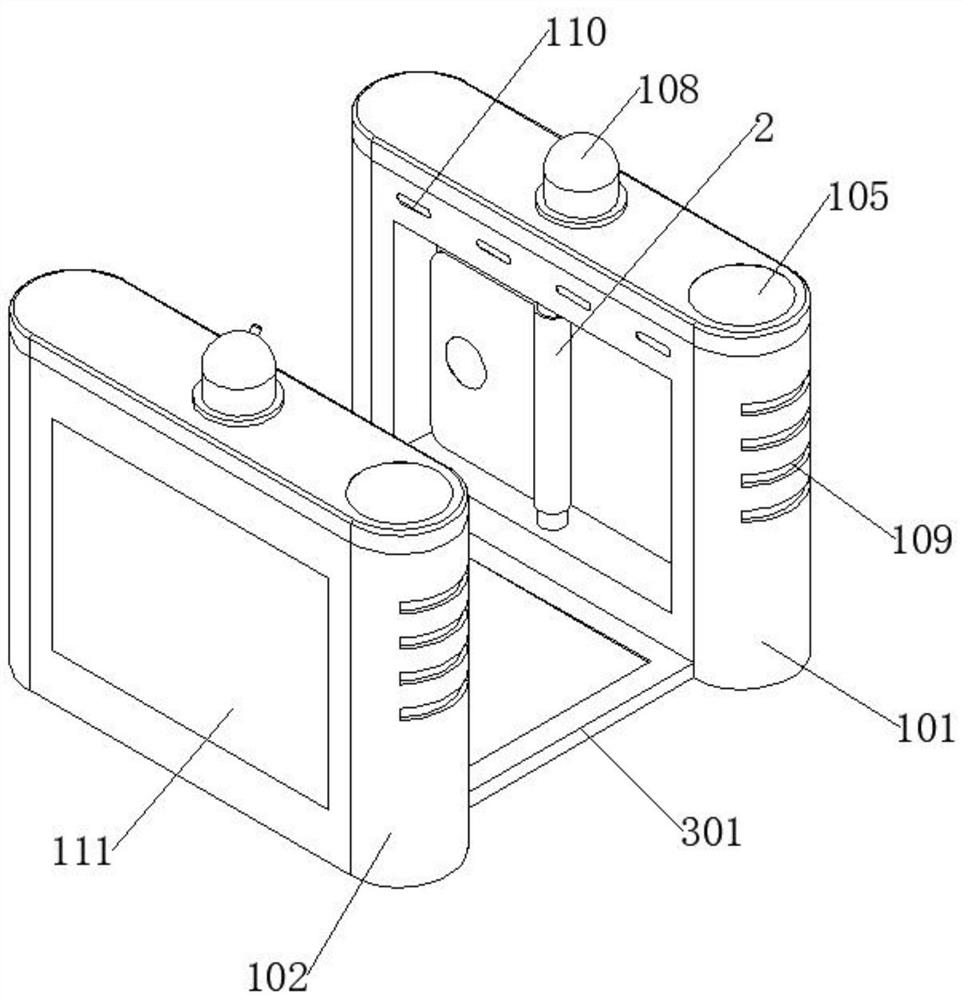
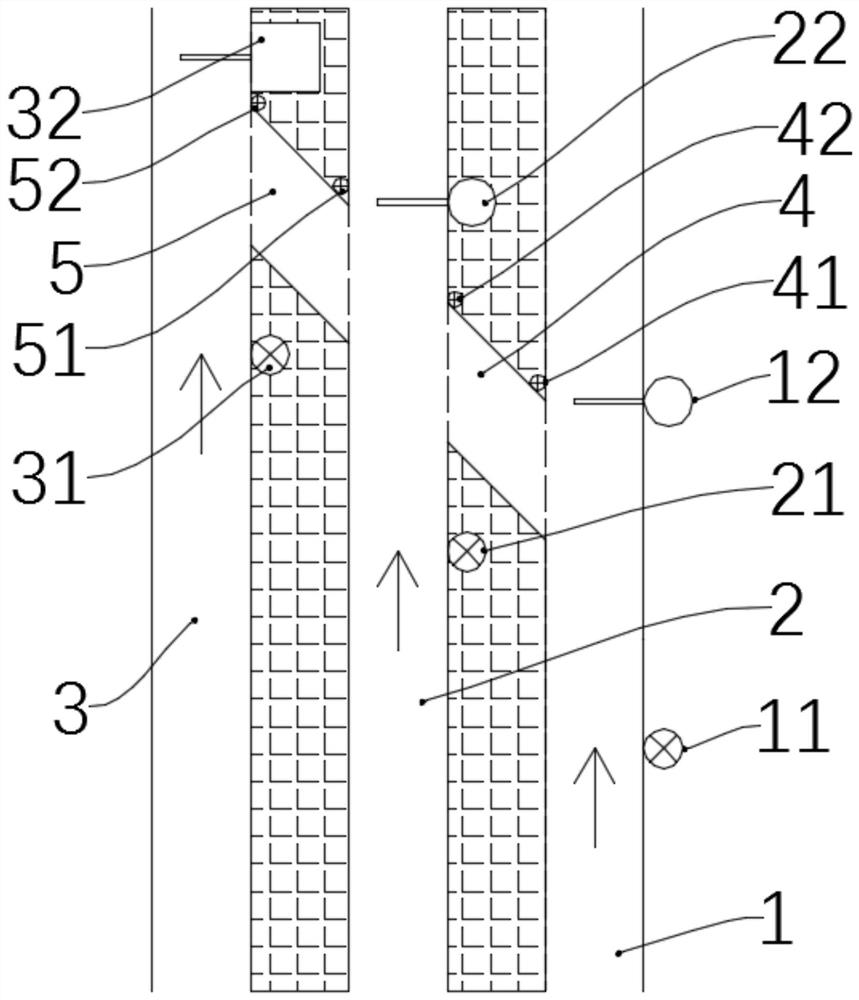
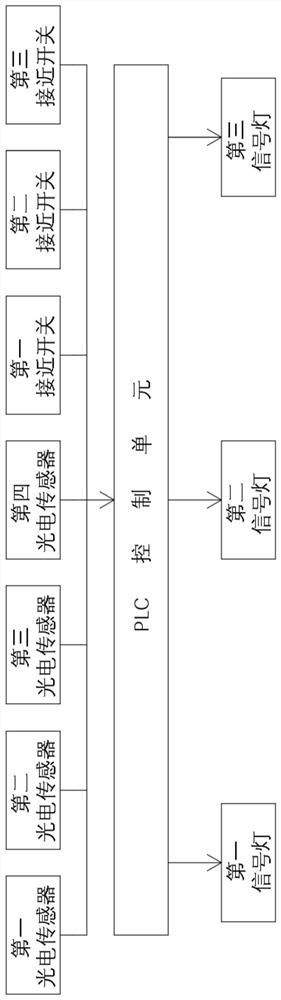
PendingCN111899446AMake up for loopholesQuick fixTicket-issuing apparatusVisible signalling systemsControl cellComputer science
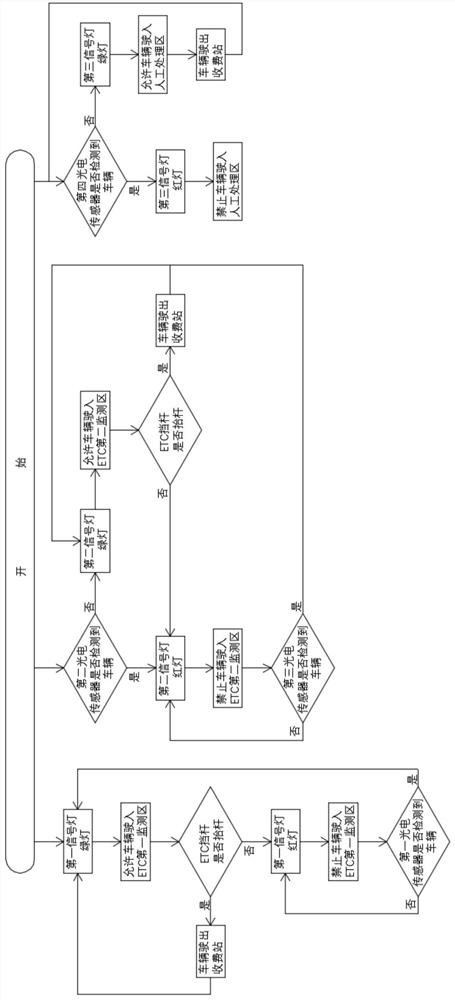
The invention relates to an ETC card anti-mis-swiping mechanism and system for highway vehicle departure. The ETC card anti-mis-swiping mechanism comprises a highway vehicle departure mechanism and ahighway vehicle ETC card anti-mis-swiping system. The highway vehicle departure mechanism sequentially comprises a first ETC channel, a second ETC channel, a manual channel, a first channel and a second channel from right to left. The highway vehicle ETC card anti-mis-swiping system comprises a PLC control unit, a first proximity switch, a third proximity switch, a first photoelectric sensor, a second photoelectric sensor, a third photoelectric sensor, a fourth photoelectric sensor, a first signal lamp, a second signal lamp and a third signal lamp. According to the ETC card anti-mis-swiping mechanism and system for the highway vehicle departure, the situation where a front vehicle leaves out of the station by swiping the ETC card of a rear vehicle can be avoided; and vehicles which cannotnormally pass through the ETC lane can be driven into the manual handling channel through a special channel, so that vehicles involved in accidents can be rapidly solved, time and labor are saved, andtraffic jam cannot be caused.
Owner:侯春叶 +4
Open cultivation type online vocational education course system
InactiveCN113327468AImprove comprehensivenessImprove collaborationData processing applicationsElectrical appliancesOnline testEngineering
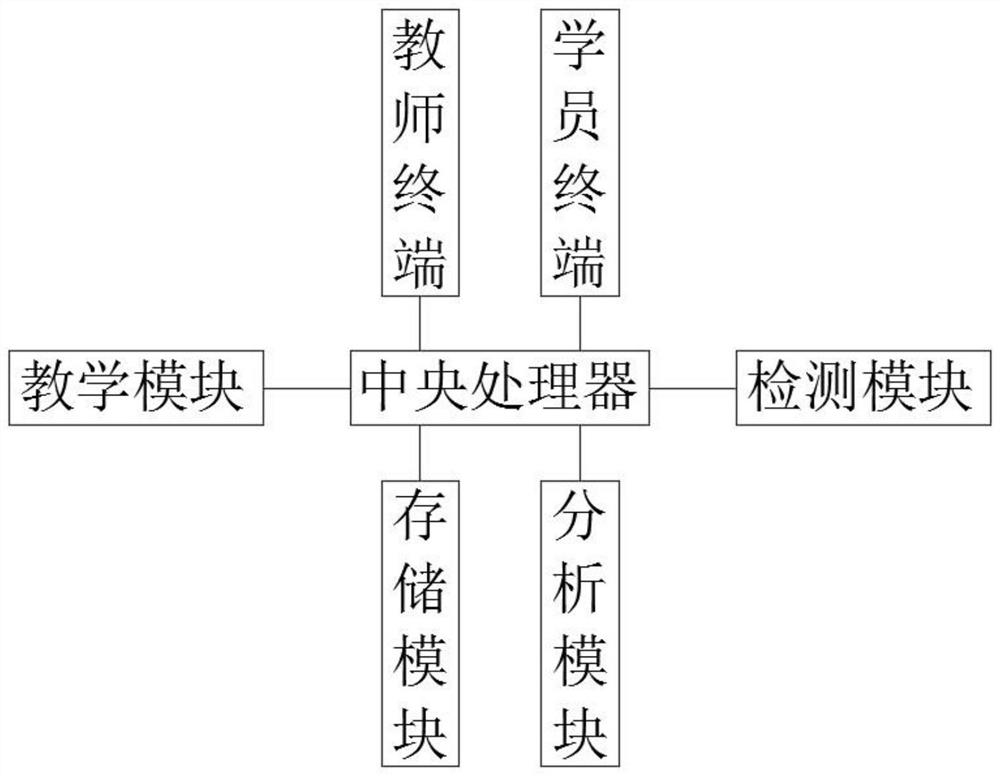
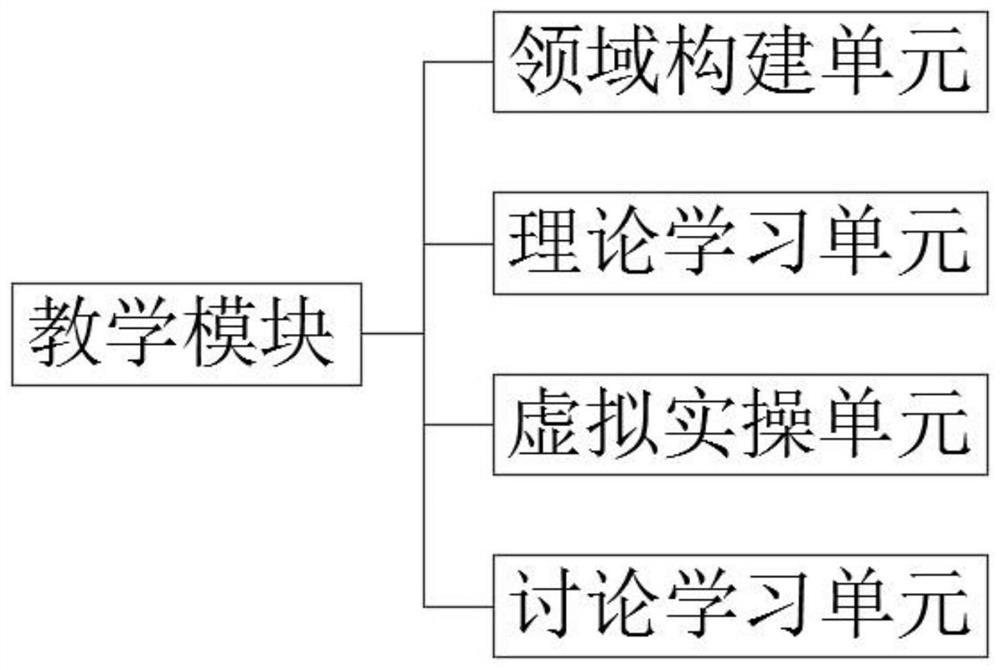
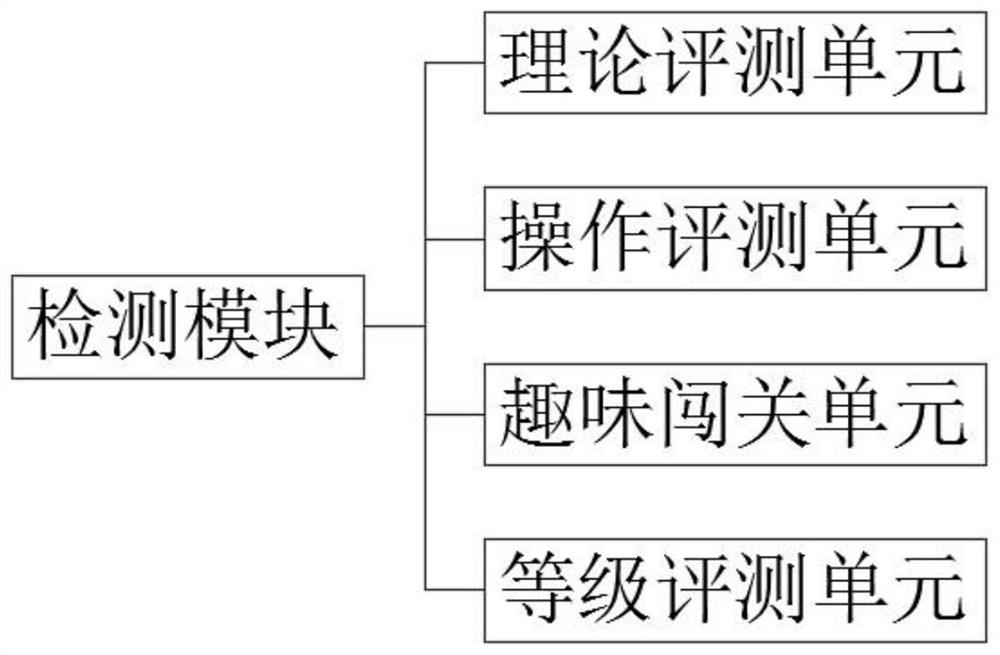
The invention discloses an open cultivation type online vocational education course system. The system comprises a teacher terminal which is used for a teacher to log in the system, carry out online teaching, and upload teaching data; a student terminal which is used for enabling a student to log in the system, and carrying out knowledge learning, actual operation, online testing and communication and interpretation; a teaching module which is used for providing knowledge field division and constructing a virtual scene for online teaching of teachers and students; a detection module which is used for testing theoretical knowledge and actual operation of students; an analysis module which is used for analyzing the theoretical knowledge mastering condition and the practical operation ability of the students, finding out error-prone points of each student through big data analysis and AI data mining, and performing targeted education; and a central processing unit which is used for coordinating the above modules to work, calling corresponding data in each database within the authority of the data calling command by using the data calling command, and sending the control commands to the corresponding modules.
Owner:ARMY ENG UNIV OF PLA
Large power transformer application field capacity verification method
InactiveCN104808081AFill gaps in capacity managementMake up for loopholesElectrical testingValidation methodsTransformer
The invention relates to a power transformer capacity verification method, particularly relates to a large power transformer application field capacity verification method, and solves a problem of lacking the large power transformer capacity verification method at present. The technical scheme is that transformer capacity is estimated by applying the corresponding relation of transformer model numbers and no-load loss numerical values specified in the GB / T6451-2008 "three-phase oil immersed power transformer technical parameters and requirements"; and transformer capacity is verified by no-load current, and finally transformer capacity is proved by comparison of calculation of the sum of DC resistance loss and no-load loss at temperature of 75 DEG C and load loss. The GB50150 "electrical equipment handover testing standard" is supplemented and improved by the method, and vulnerability in large transformer capacity management is compensated.
Owner:STATE GRID CORP OF CHINA +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com