Image encryption system, image decryption system, image encryption method and image decryption method
An encryption system and image technology, applied in transmission systems, digital transmission systems, encryption devices with shift registers/memory, etc., can solve problems such as being easily cracked, and achieve long-term information protection effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
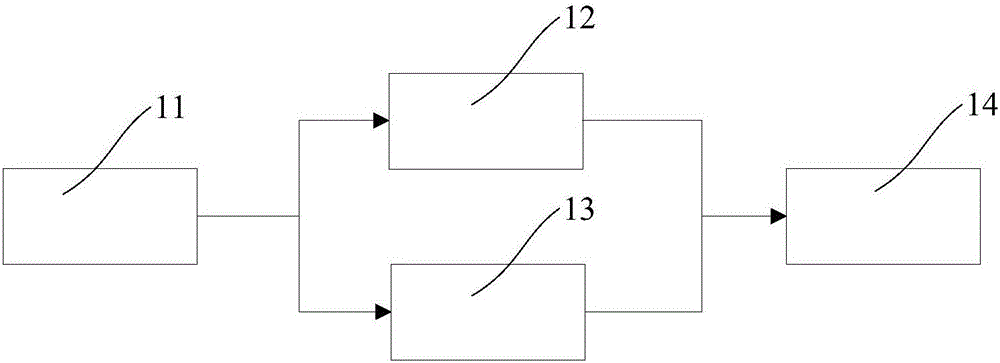
[0061] see figure 1 , the present invention provides a kind of image encryption system, described image encryption system comprises: cellular automaton 11, and described cellular automaton 11 is suitable for generating the pseudo-random chaotic sequence that is equal to image data with key as seed; The automaton 11 produces complex structures and processes by the simple interaction of a large number of basic constituent units; the pseudo-random chaotic sequence is a digital sequence that has good randomness and can be repeated according to certain rules; the first encryption module 12, The first encryption module 12 is connected to the cellular automaton 11, and is adapted to reversibly mix the pseudo-random chaotic sequence with the corresponding bits of the plaintext of the image data to obtain first encrypted data; The first encryption module 12 is to encrypt the value of the image data itself; the scrambling mapping table generating module 13, the scrambling mapping table ...
Embodiment 2
[0066] see image 3 , the present invention also provides an image encryption method, the image encryption method comprising:
[0067] S20: using the cellular automaton to generate a pseudo-random chaotic sequence with the same length as the image data with the key as the seed;
[0068] S21: Perform reversible information mixing of the pseudo-random chaotic sequence and the plaintext of the image data to obtain first encrypted data;
[0069] S22: Generate a scrambling mapping table according to the pseudo-random chaotic sequence;
[0070] S33: Divide the first encrypted data into multiple data blocks according to the key length, and reorganize the data blocks according to the scramble mapping table to obtain scrambled second encrypted data.
[0071] As an example, reversible information mixing is performed on the pseudo-random chaotic sequence and corresponding bits of the plaintext of the image data to obtain the first encrypted data.
[0072] As an example, in the step S2...
Embodiment 3
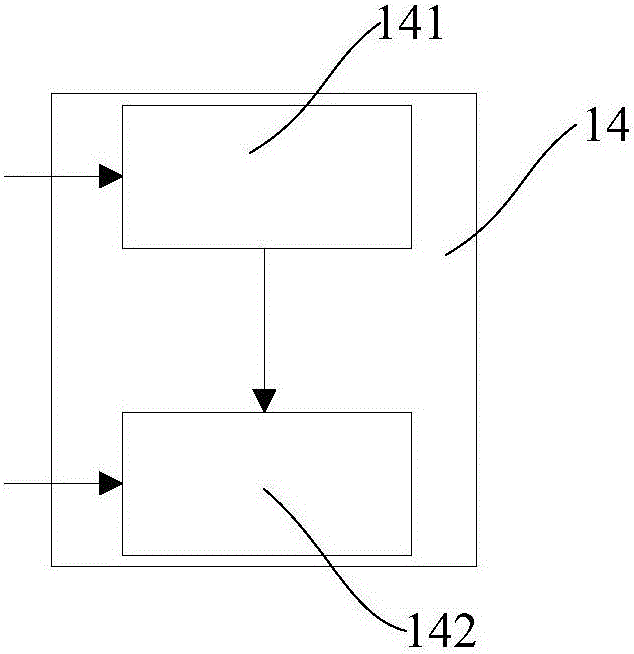
[0078] see Figure 4 , the present invention also provides an image decryption system, the image decryption system is connected to the image encryption system described in Embodiment 1, and is suitable for performing the first encryption data and the second encryption data obtained by the image encryption system Decryption, the image decryption system includes: a cellular automaton 31, the cellular automaton 31 is suitable for using a key as a seed to generate a pseudo-random chaotic sequence equal in length to the image data; a scrambling mapping table generation module 32, the setting The random mapping table generation module 32 is connected with the cellular automaton 31, and is adapted to generate a random mapping table according to the pseudo-random chaotic sequence; the first decryption module 33, the first decryption module is connected with the image encryption system and The scrambling mapping table generating modules are connected and adapted to divide the second en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com