Method for carrying out vulnerability early warning aiming at large-scale target
A large-scale, loophole technology, applied in the direction of instrumentation, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as insufficient performance, excessive system scheduling overhead, etc., and achieve the effect of improving the speed of early warning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0077] A new vulnerability has recently emerged online, which is assumed to be a "Heartbleed vulnerability."
[0078] https: / / baike.baidu.com / item / Heartbleed / 13580882? fr=aladdin&fromid=13579697&fromtitle=Heartbleed
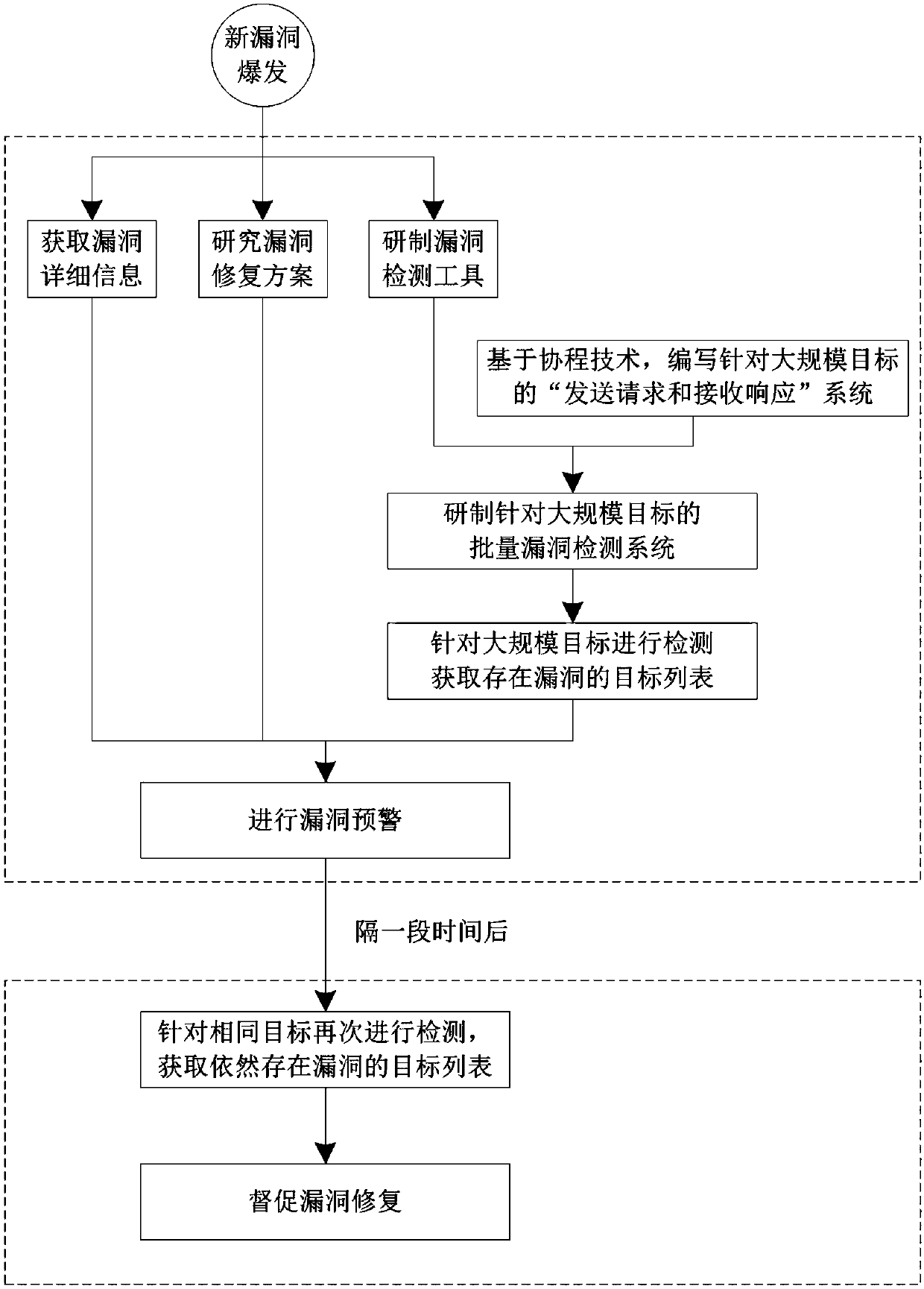
[0079] First, obtain the detailed information of the vulnerability, study the repair scheme of the vulnerability, and develop the detection tool for the vulnerability.
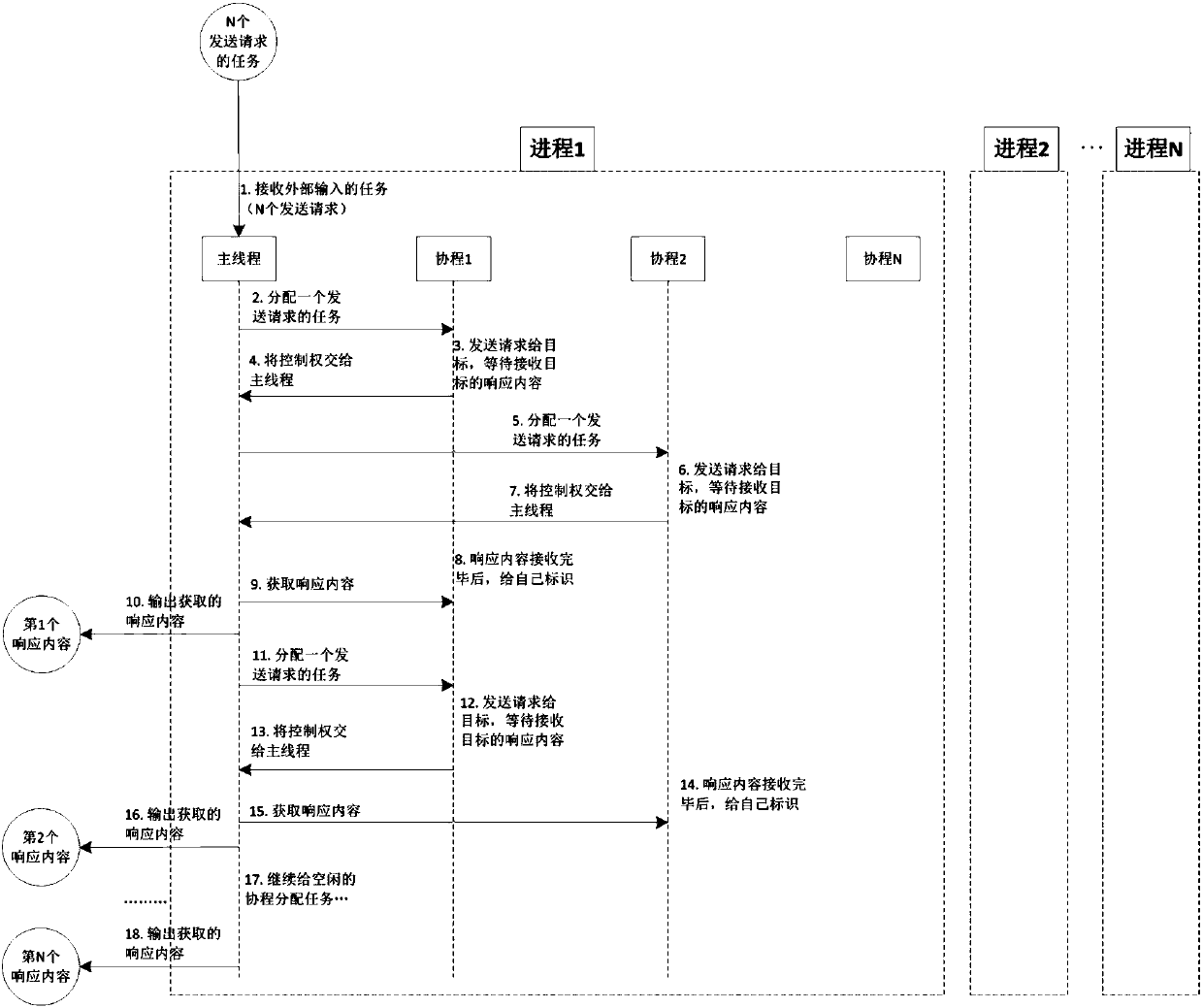
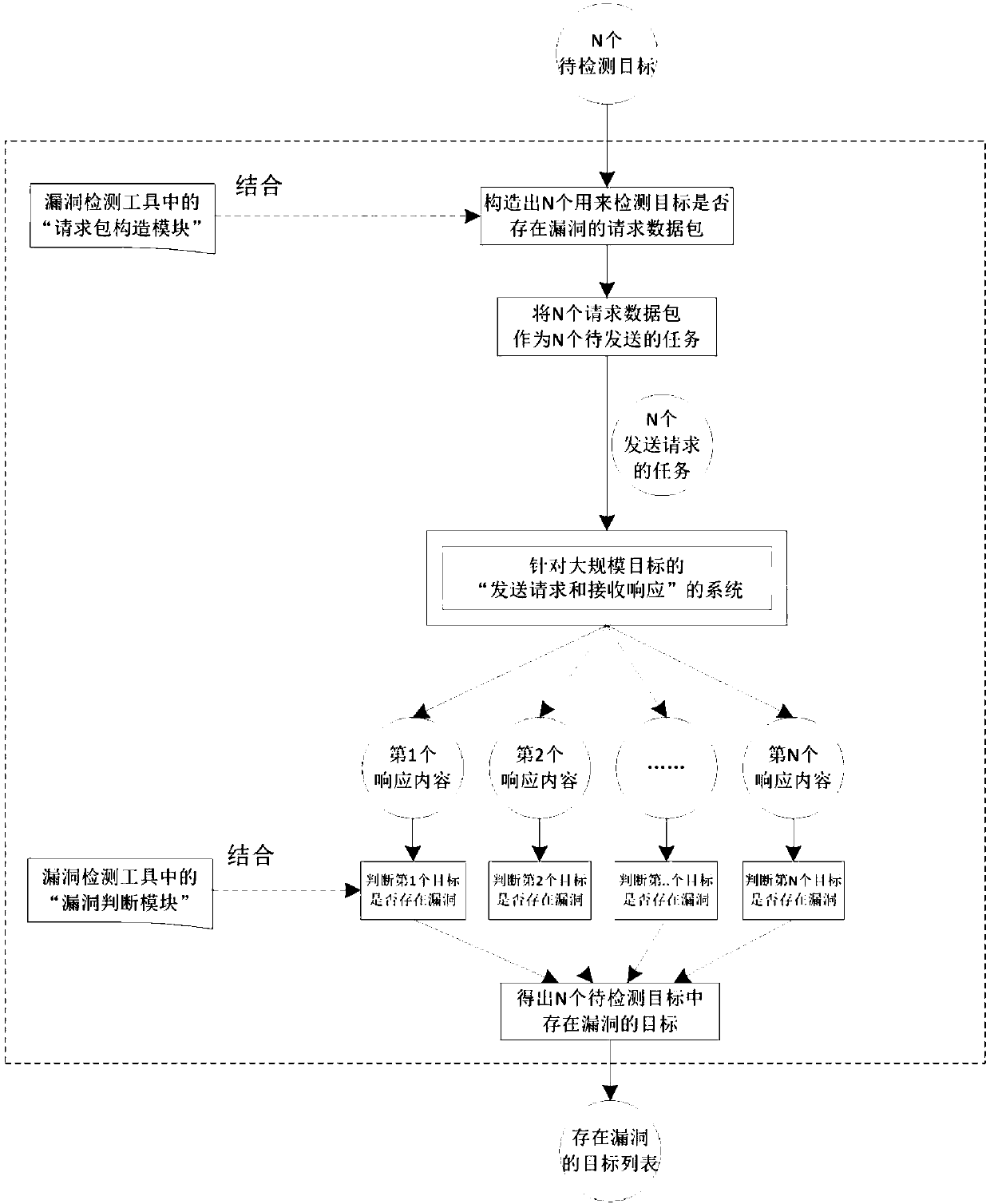
[0080] The "Send Request and Receive Response" system for large-scale targets, combined with the "Heartbleed Vulnerability" vulnerability detection tool, develops a batch "Heartbleed Vulnerability" detection system for large-scale targets.
[0081] It is assumed that the target to be detected is the Internet network equipment in the whole of Beijing, that is, the IP addresses on the Internet in the whole of Beijing are the targets to be detected. There are more than 50 million IP addresses in Beijing, and these more than 50 million IP addresses are all targets to be detected.
[0082] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com