A real-time monitoring threat analysis method and system based on deep learning
A technology for threat analysis and real-time monitoring, applied in neural learning methods, transmission systems, closed-circuit television systems, etc. The effect of pressure, reducing labor cost and improving security efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] A real-time monitoring threat analysis method based on deep learning, comprising the following steps:
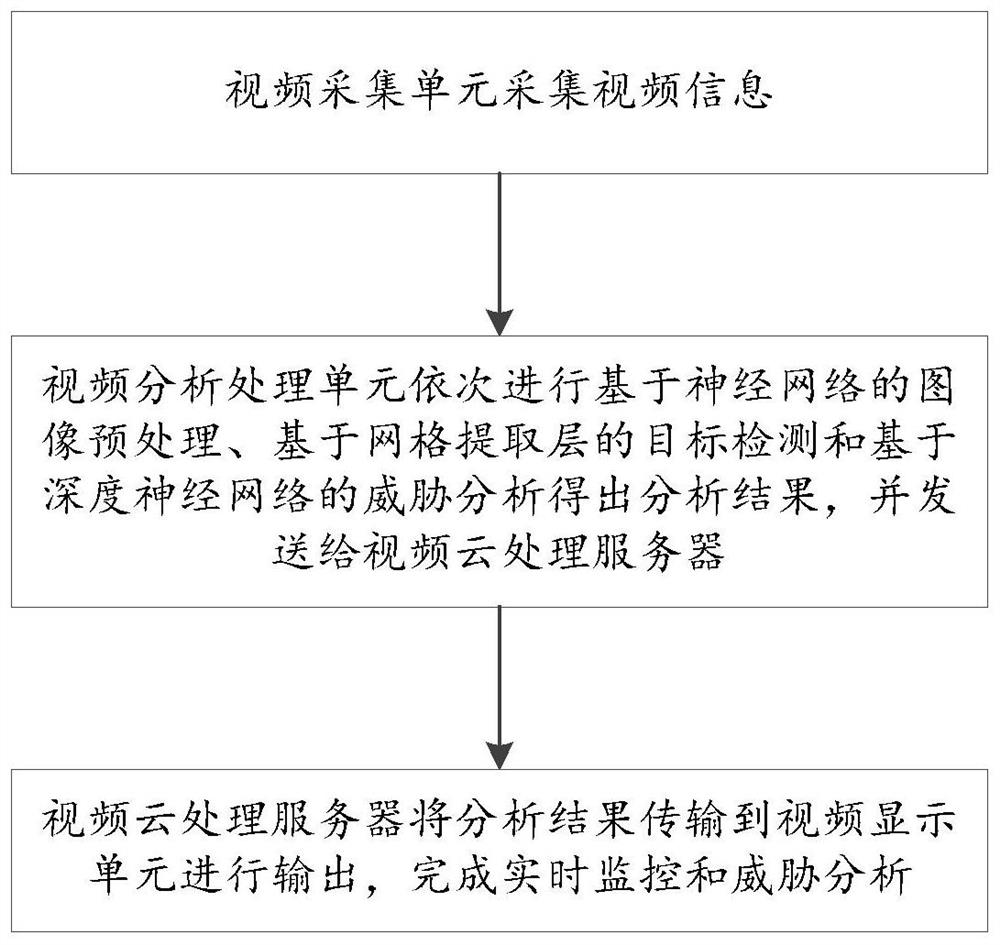
[0040] Step 1: the video acquisition unit collects video information;
[0041] Step 2: The video analysis and processing unit sequentially performs image preprocessing based on the neural network, target detection based on the grid extraction layer, and threat analysis based on the deep neural network to obtain analysis results and send them to the video cloud processing server;
[0042] Step 2 includes the following steps:
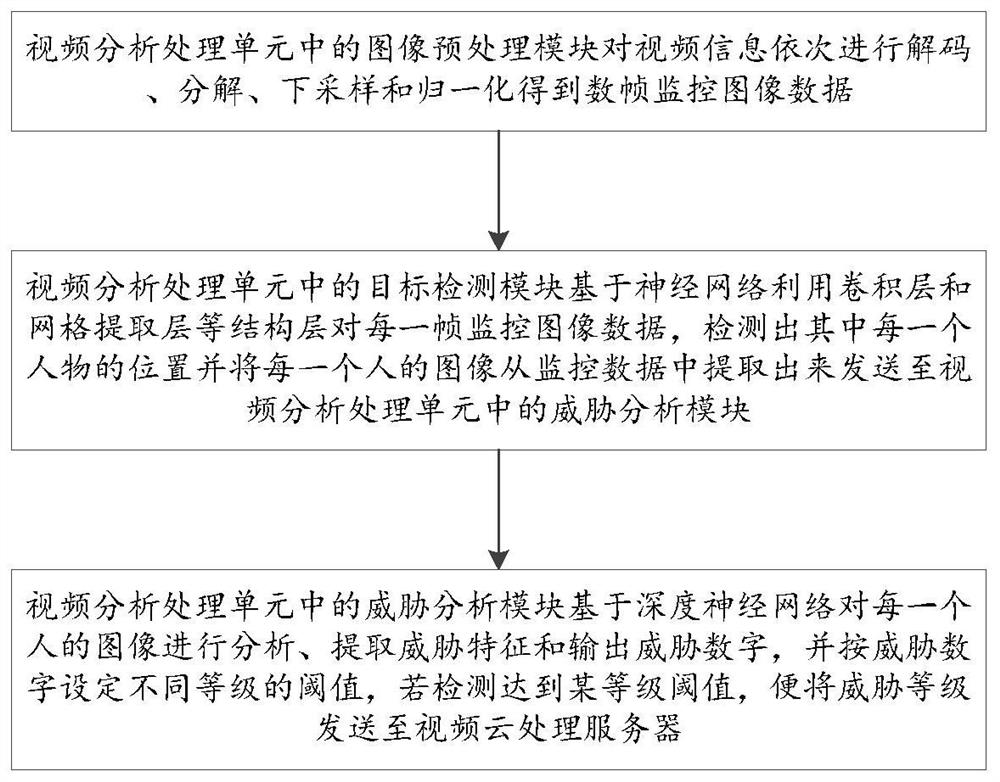
[0043] Step 2.1: The image preprocessing module in the video analysis and processing unit sequentially decodes, decomposes, down-samples and normalizes the video information to obtain several frames of monitoring image data;
[0044] Step 2.2: The target detection module in the video analysis processing unit monitors the image data for each frame based on the neural network using structural layers such as the convolutional layer and the grid ext...
Embodiment 2
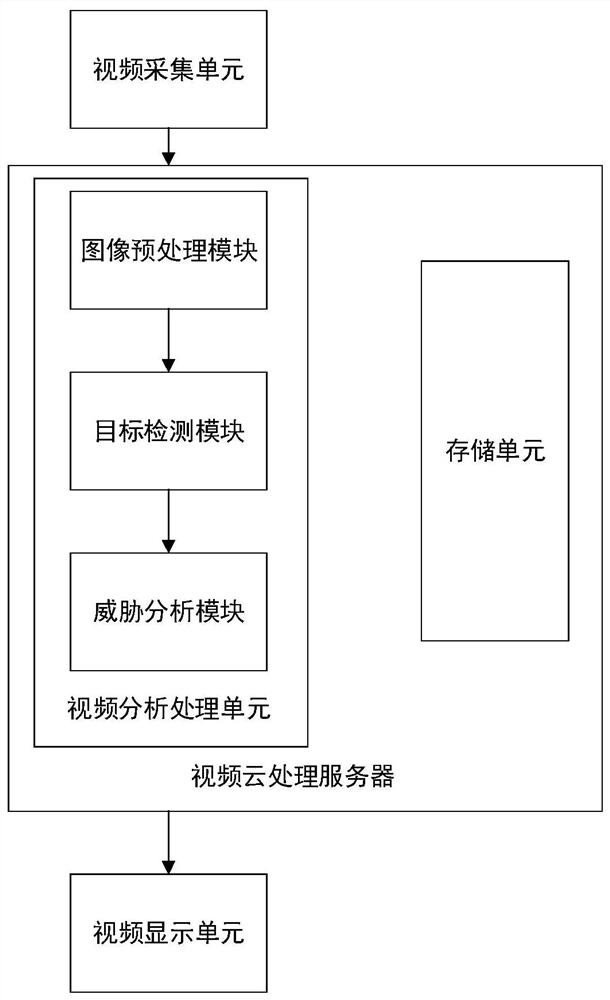
[0057] First, the video acquisition unit performs image acquisition on the monitoring area, and the acquisition device adopts a high-definition surveillance camera or a camera on a wearable device or a camera of a mobile phone.
[0058] The image data collected by the video acquisition unit is encoded by the video encoder and then transmitted to the video cloud processing server through a wireless network or an optical fiber cable network. The video cloud processing server stores the obtained data in the video cloud processing server before processing the data. backup, and then send the data to the video analysis and processing unit for processing.
[0059] The video analysis and processing unit preprocesses the monitoring video data.
[0060] The preprocessing steps are:
[0061] S101: Decoding the surveillance video, and then decomposing the video into images frame by frame;
[0062] S102: Downsampling each frame of image to change the image to a resolution of 448*448, so ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com