Attack link based website backdoor use event identifying method
An identification method and website technology, applied in electrical components, transmission systems, etc., can solve the problems of inability to determine the attack stage, difficult to determine website intrusion events, and inability to attack correlation analysis, and achieve the effect of improving the ability of security response.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
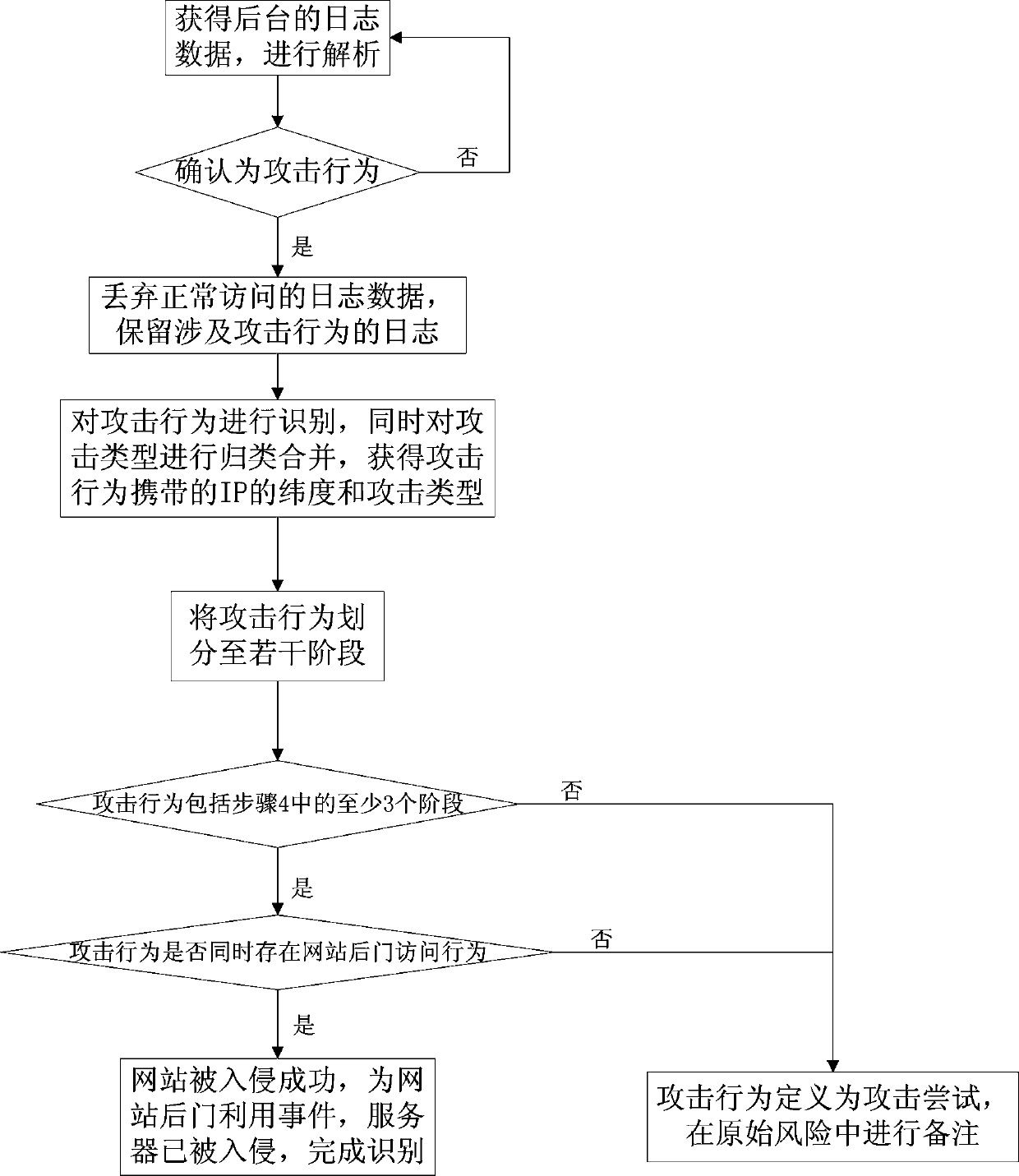
[0022] The invention relates to a method for identifying events of website backdoor utilization based on an attack chain, and the method includes the following steps.
[0023] Step 1: Obtain the log data in the background and analyze it.
[0024] Step 2: If it is confirmed as an attack behavior, discard the log data of normal access, keep the log related to the attack behavior, and proceed to the next step; otherwise, return to step 1.
[0025] In the step 2, if a false positive is found, the log data is discarded directly, and the step 1 is returned.
[0026] Step 3: Identify the attack behavior, classify and merge the attack types at the same time, and obtain the IP latitude and attack type carried by the attack behavior.
[0027] Step 4: Divide the attack behavior into several stages according ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com