MQTT connection method and system of low-end limited equipment, terminal and server
A connection method and server technology, applied in transmission systems, electrical components, etc., can solve problems such as unsupportable, increased equipment power consumption, increased manufacturing costs, etc., and achieve the effect of expanding the range of choices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
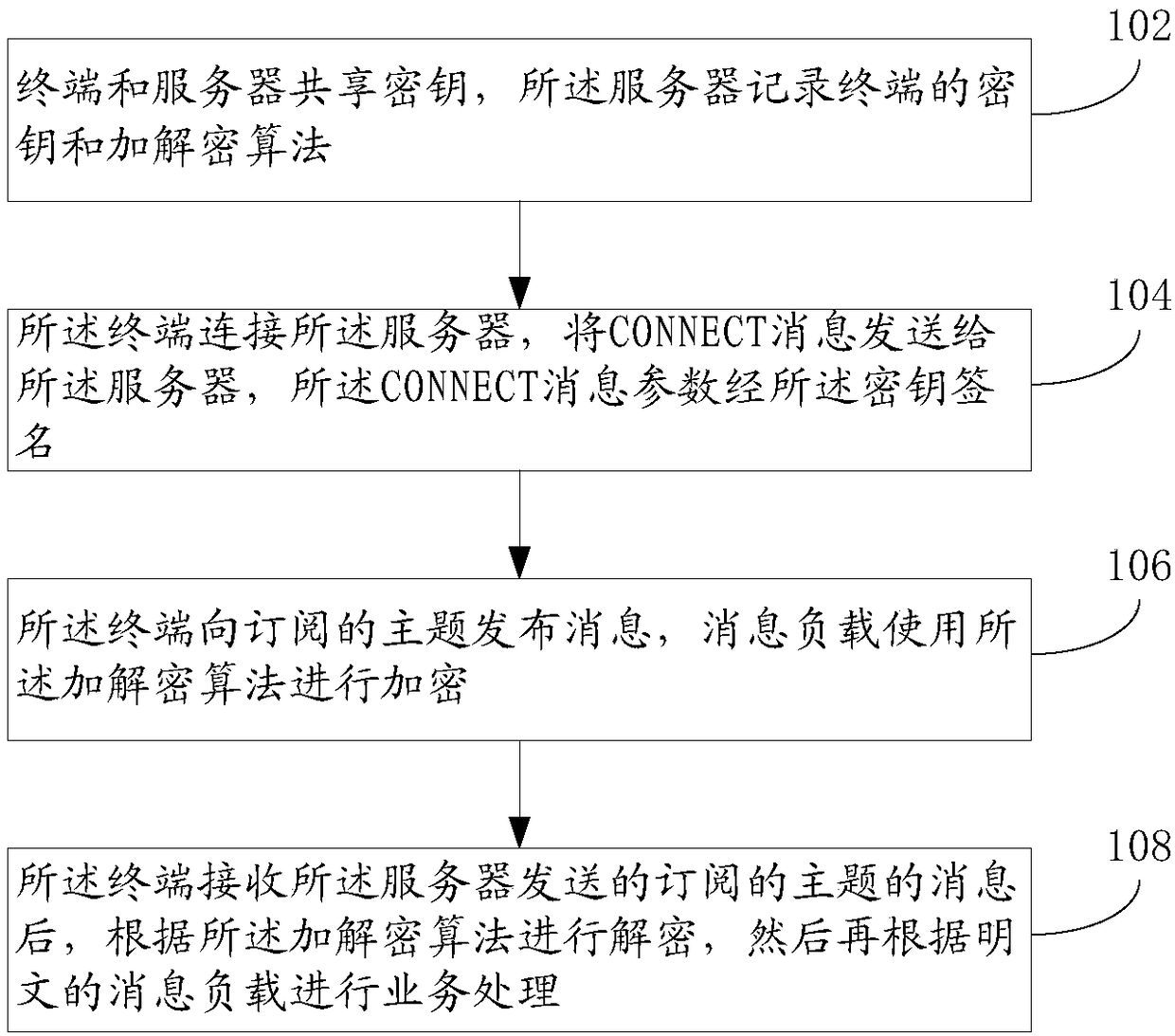
[0055] Such as figure 1As shown, the MQTT connection method of the low-end limited device of the present application, an implementation thereof, includes the following steps:
[0056] Step 102: The terminal and the server share a key, and the server records the key of the terminal and the encryption and decryption algorithm matching the computing capability of the terminal; the server in this application is a server supporting the MQTT protocol.
[0057] Step 104: The terminal connects to the server, and sends an MQTT CONNECT message to the server, and the parameters of the MQTT CONNECT message are signed by a key.
[0058] Step 106: The terminal publishes a message to the subscribed topic, and the message payload is encrypted using an encryption and decryption algorithm.
[0059] Step 108: After receiving the message of the subscribed topic sent by the server, the terminal decrypts it according to the encryption and decryption algorithm, and then performs business processing...
Embodiment 2
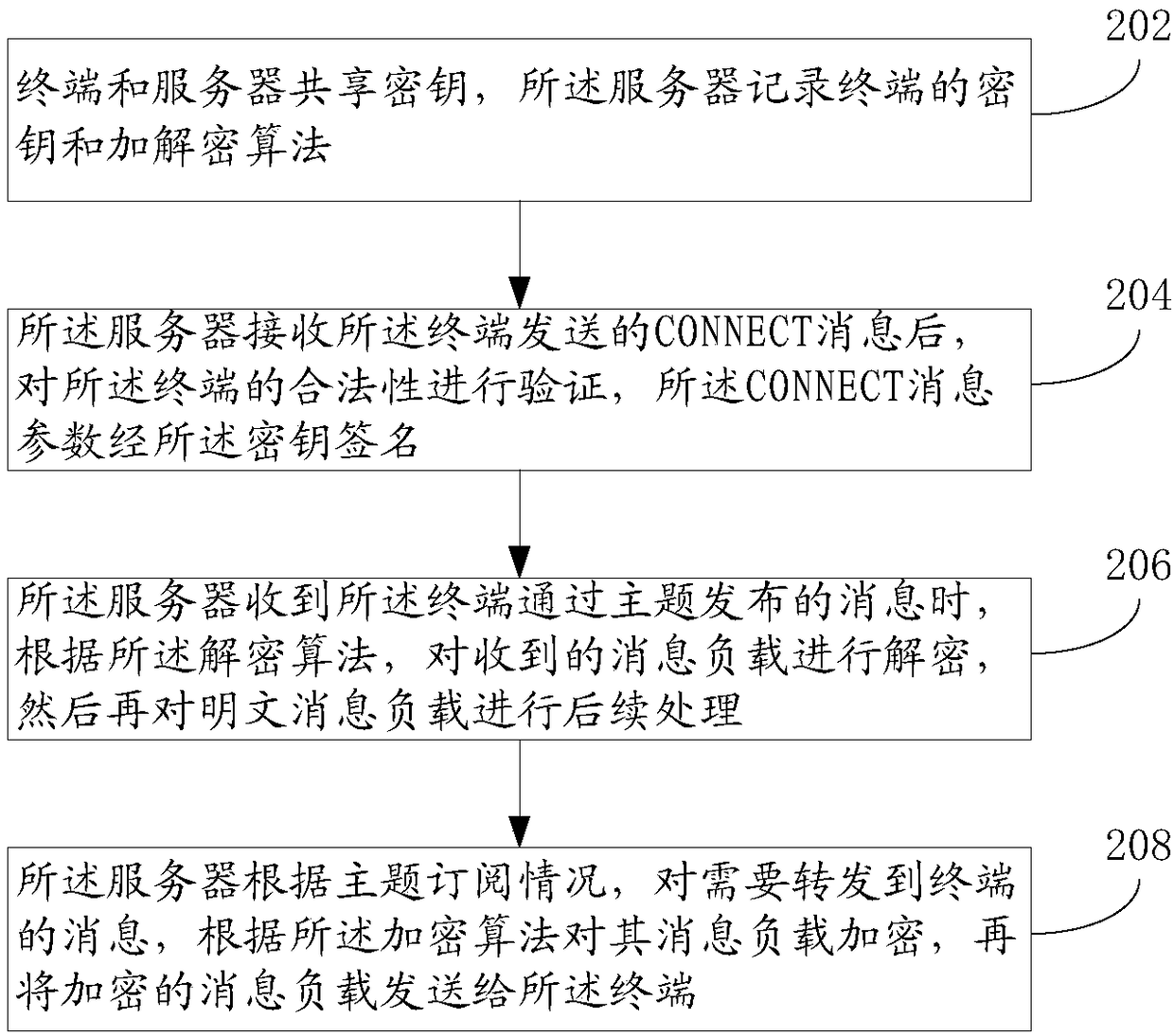
[0067] Such as figure 2 As shown, another embodiment of the MQTT connection method of the low-end limited device of the present application includes the following steps:
[0068] Step 202: The terminal and the server share a key, and the server records the key of the terminal and the encryption and decryption algorithm matching the computing capability of the terminal.
[0069] Step 204: After receiving the MQTT CONNECT message sent by the terminal, the server verifies the legitimacy of the terminal, and the parameters of the MQTT CONNECT message are signed by the key.
[0070] Step 206: When the server receives the message published by the terminal through the topic, it decrypts the received message payload according to the decryption algorithm, and then performs subsequent processing on the plaintext message payload.
[0071] Step 208: The server encrypts the message payload of the message to be forwarded to the terminal according to the encryption algorithm according to t...
Embodiment 3
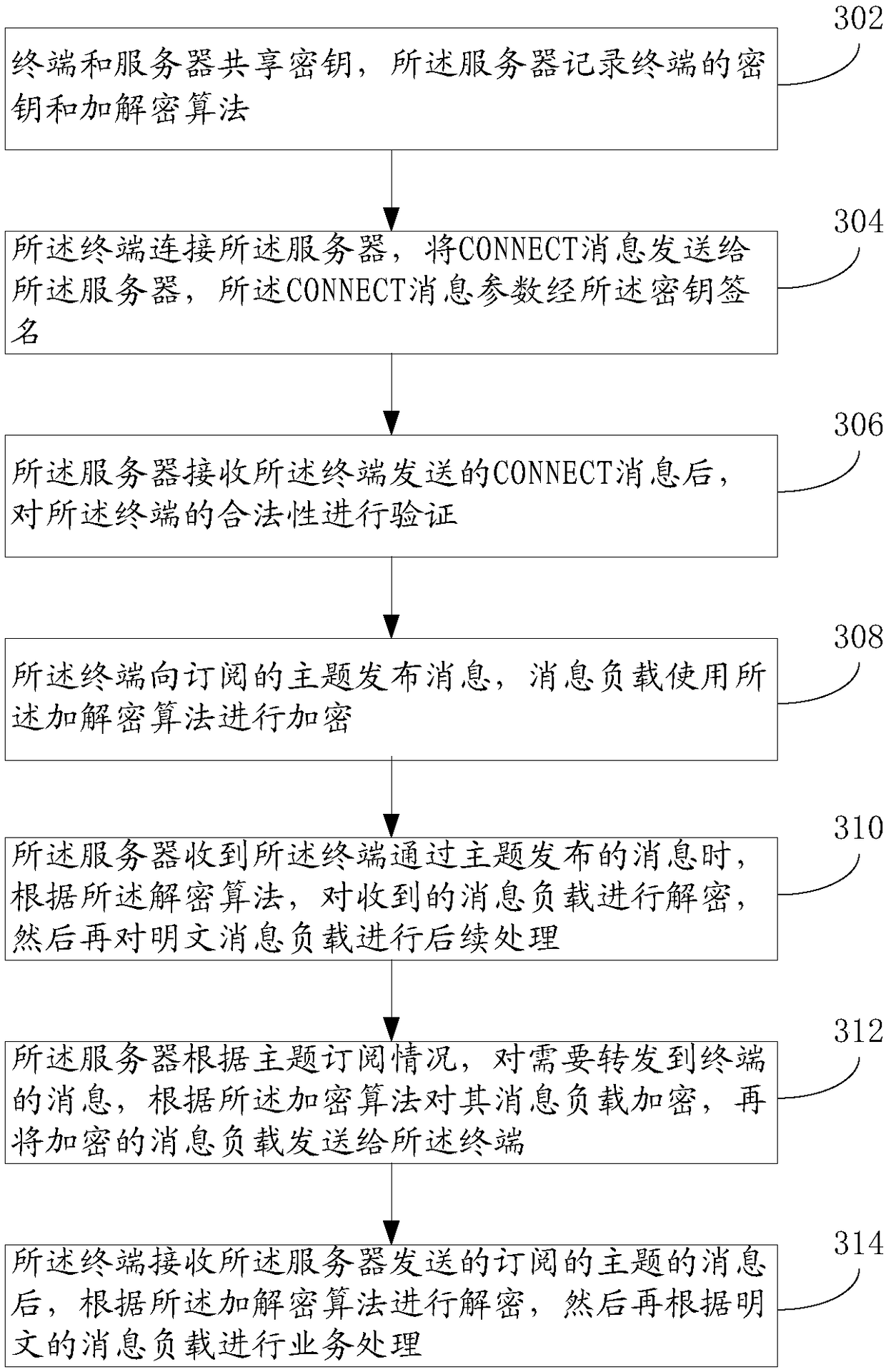
[0086] Such as image 3 As shown, the MQTT connection method of the low-end limited device of the present application, an implementation thereof, includes the following steps:
[0087] Step 302: The terminal and the server share a key, and the server records the key of the terminal and the encryption and decryption algorithm matching the computing capability of the terminal.
[0088] Step 304: The terminal connects to the server, and sends an MQTT CONNECT message to the server, and the parameters of the MQTT CONNECT message are signed by the key.
[0089] Step 306: After receiving the CONNECT message sent by the terminal, the server verifies the legitimacy of the terminal.
[0090] Step 308: The terminal publishes a message to the subscribed topic, and the message payload is encrypted using an encryption and decryption algorithm.
[0091] Step 310: When the server receives the message published by the terminal through the topic, it decrypts the received message payload accor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com