Working method and device of intelligent key device
A technology of smart key device and working method, which is applied in the field of smart key device work, can solve problems such as excessive storage overhead, complex logical structure, and poor user experience, and achieve improved user experience, simple logical structure, and low storage overhead Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
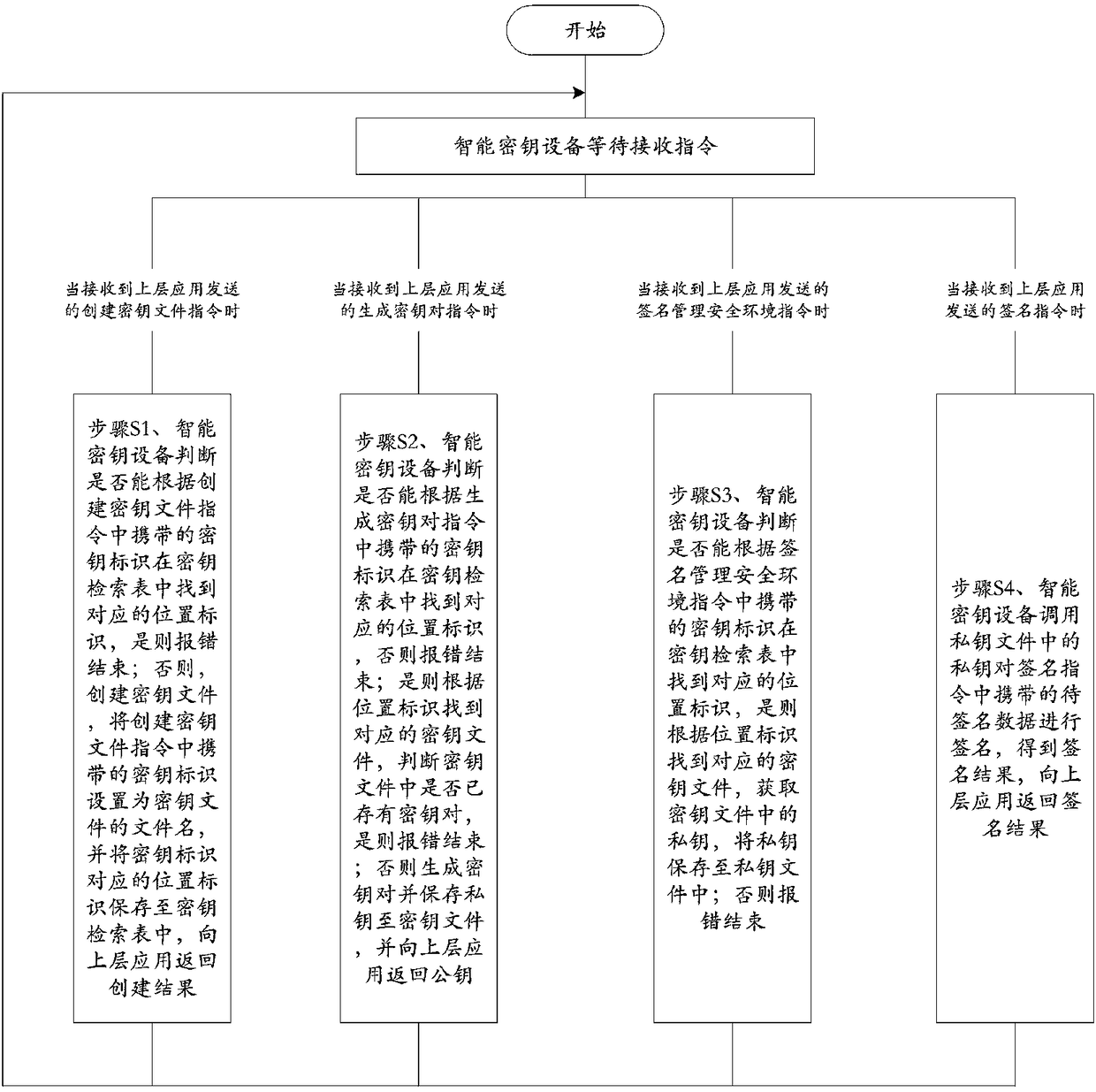
[0043] This embodiment provides a working method of a smart key device, such as figure 1 shown, including:
[0044] The smart key device waits for the instruction to be received. When receiving the instruction to create a key file sent by the upper-layer application, execute step S1; when receiving the instruction to generate a key pair sent by the upper-layer application, execute step S2; When the signature management security environment command is executed, step S3 is executed; when the signature instruction sent by the upper layer application is received, step S4 is executed;
[0045] Step S1, the smart key device judges whether the corresponding location identifier can be found in the key retrieval table according to the key identifier carried in the instruction to create a key file, and if yes, an error will be reported; otherwise, the key file will be created and the key will be created The key identifier carried in the file instruction is set as the file name of the k...
Embodiment 2
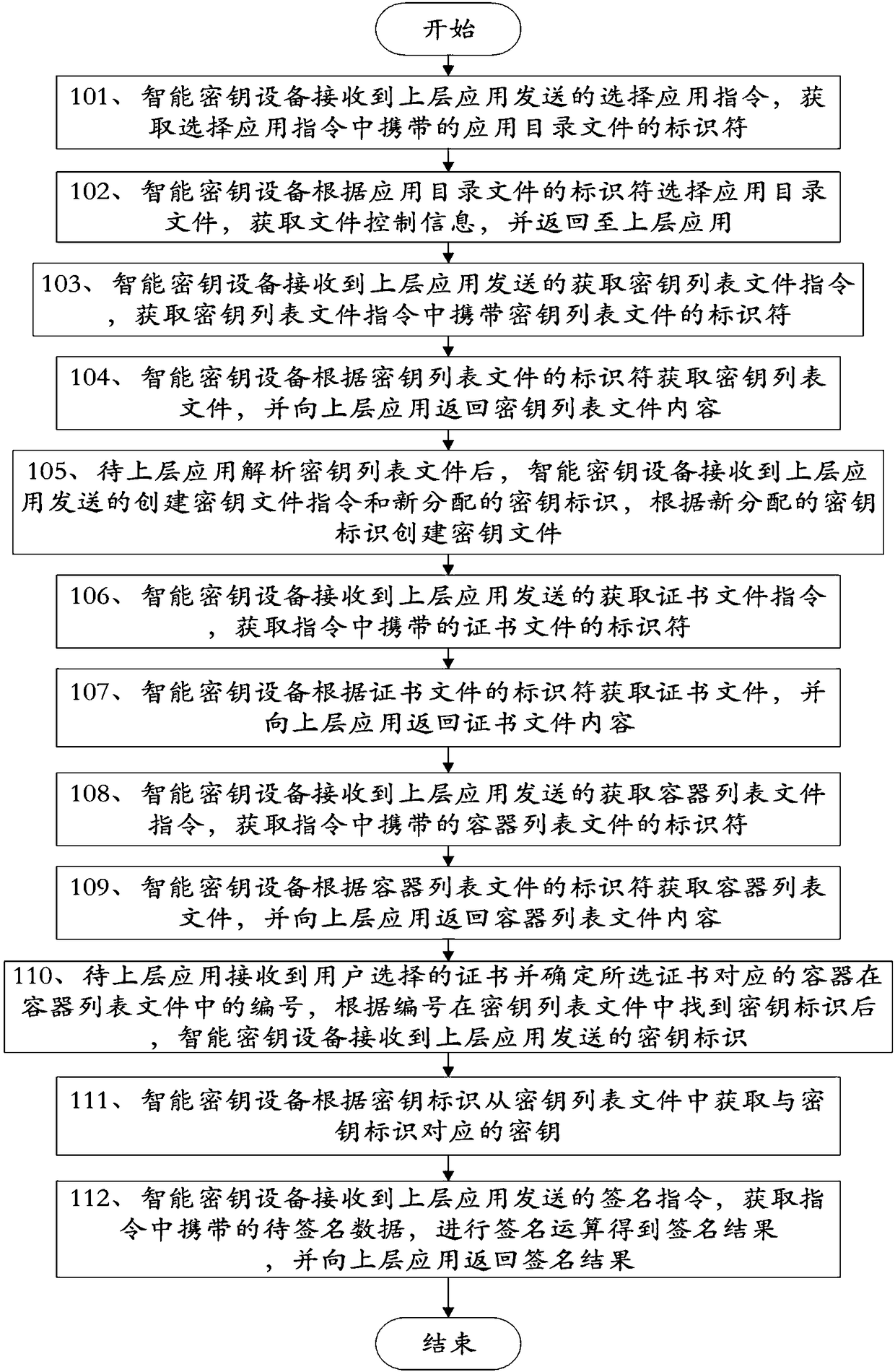
[0076] This embodiment discloses a working method of a smart key device, such as figure 2 As shown, the method specifically includes:
[0077] Step 101, the smart key device receives the application selection instruction sent by the upper application, and obtains the identifier of the application directory file carried in the application selection instruction;
[0078] Specifically, the instruction for selecting an application may specifically be: 00a4040009a00000039742544659. These include selection header: 00a40400 and application number: a00000039742544659;
[0079] Step 102, the smart key device selects the application directory file according to the identifier of the application directory file, obtains file control information, and returns to the upper application;
[0080] Specifically, when the smart key device receives the application selection instruction sent by the upper layer application, the java virtual machine in the device matches each application program in...
Embodiment 3
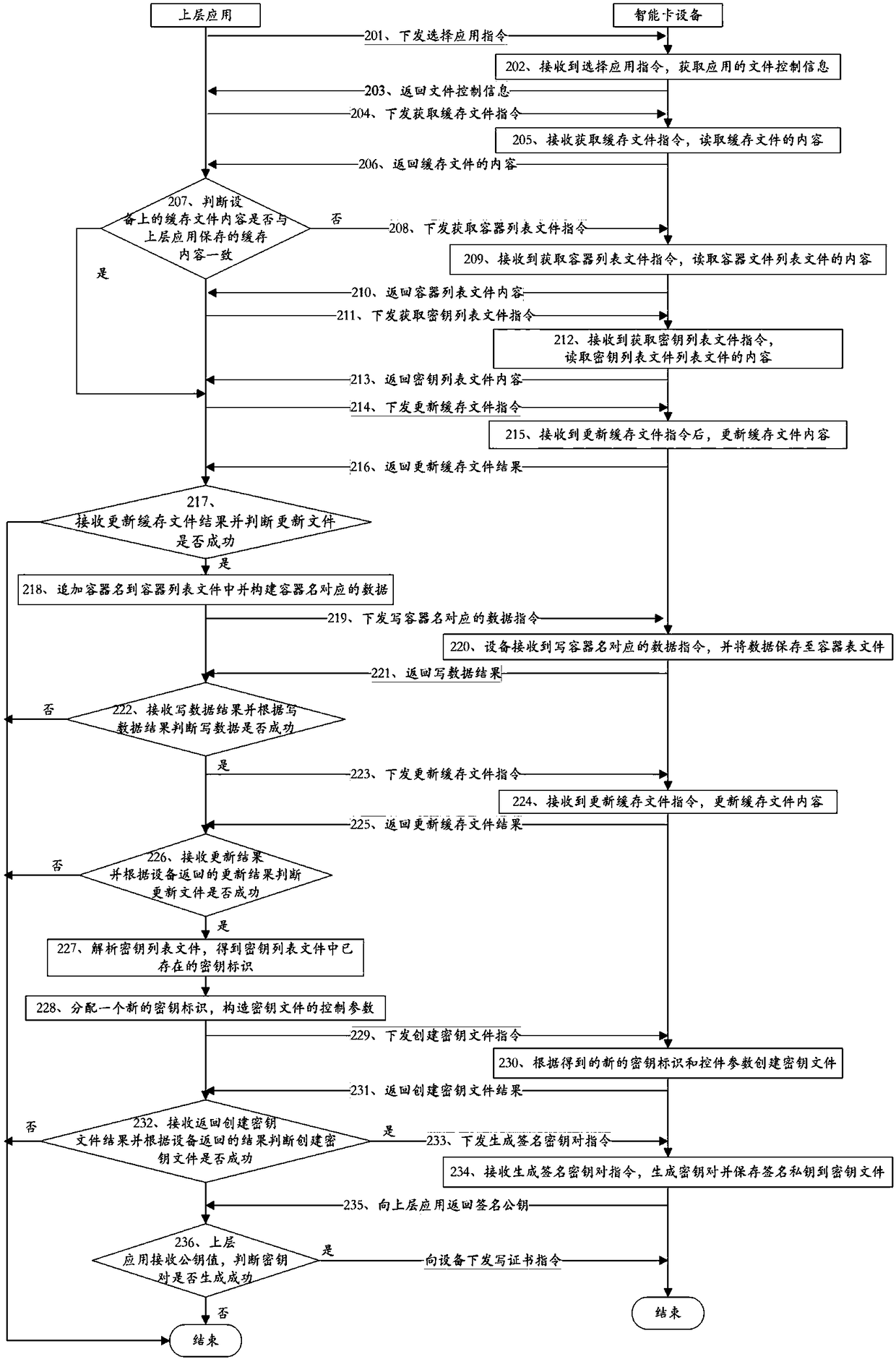
[0118] This embodiment discloses a working method of a smart key device, which is applied to a system including an upper-layer application and a smart key device. The upper-layer application communicates with the smart key device (hereinafter referred to as the device) directly or through other devices. or media, etc., which are not specifically limited in the present invention. The methods specifically include:
[0119] Generate a key pair process, such as image 3 shown, including:
[0120] Step 201, the upper layer application sends an instruction to select an application to the device;
[0121] In this embodiment, the upper-layer application sends an instruction to select an application to the device. After the device receives the instruction, the java virtual machine in the device matches each application program in the device according to the AID (Application Identifie) in the instruction, and then Send the command to the matching application.
[0122] Specifically, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com