Security operation and maintenance architecture of industrial control system
An industrial control system and security technology, which is applied in the framework of the cloud platform of security operation and maintenance services, can solve problems such as the limitation of storage session computing resources, and achieve the effect of enhancing information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Below is further detailed description of the present invention according to accompanying drawing and example:
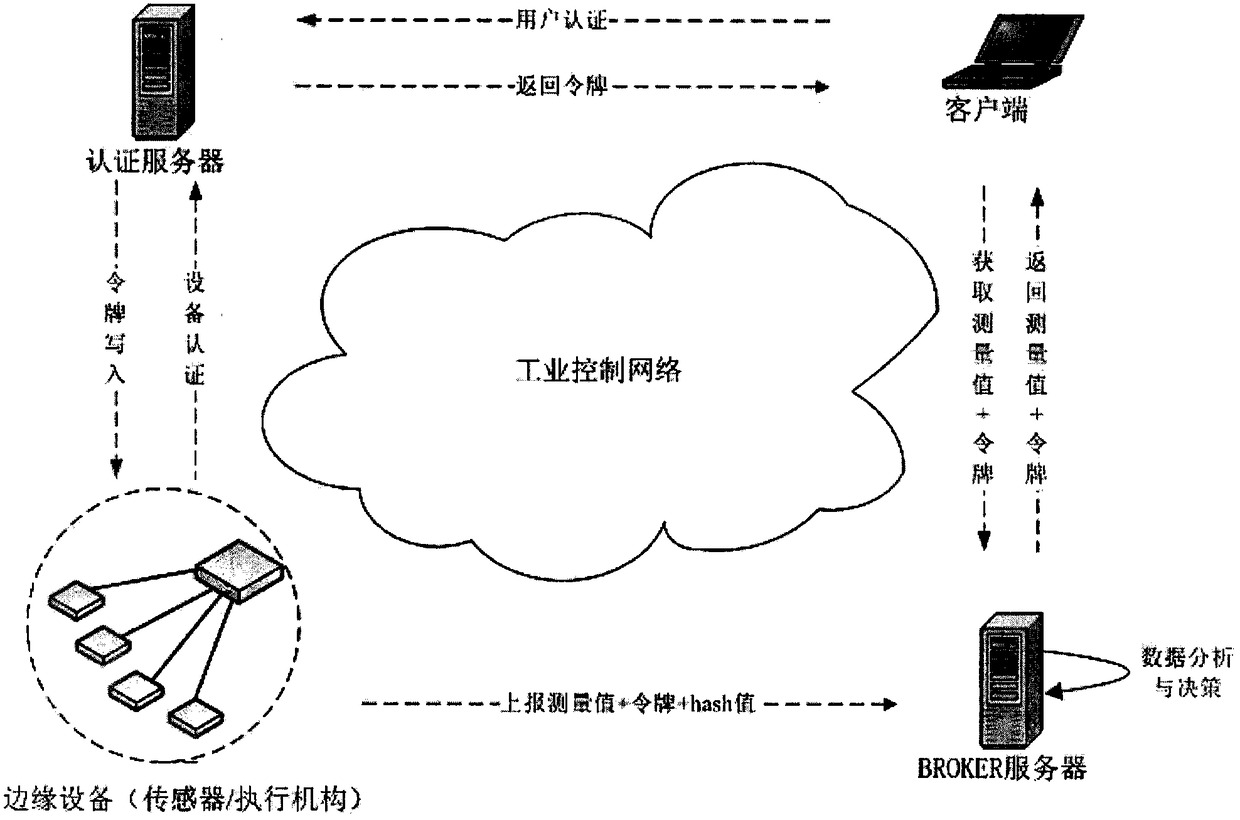
[0023] figure 1 It is a schematic structural diagram of a security operation and maintenance architecture of an industrial control system according to the present invention. The architecture includes an authentication server and a BROKER server.
[0024] Further, the main functions of the authentication server are as follows:
[0025] (1) Responsible for user authentication, when the user needs to access the security operation and maintenance service cloud platform, first access the authentication server to perform user authentication, and if the authentication is successful, then feed back the token of the IoT device.
[0026] (2) Responsible for the certification of edge devices (sensors / actuators) newly deployed in industrial control systems. The edge device will report the ID number created by using blockchain technology to the authentication server. If...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com