Network intrusion detection method based on transfer learning and integrated learning
A network intrusion detection and integrated learning technology, applied in the field of network security, can solve the problems of complex network traffic, difficult generation of detection sample data sets, and huge workload of labeling data sets, so as to speed up convergence, save training time, and improve detection. The effect of accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
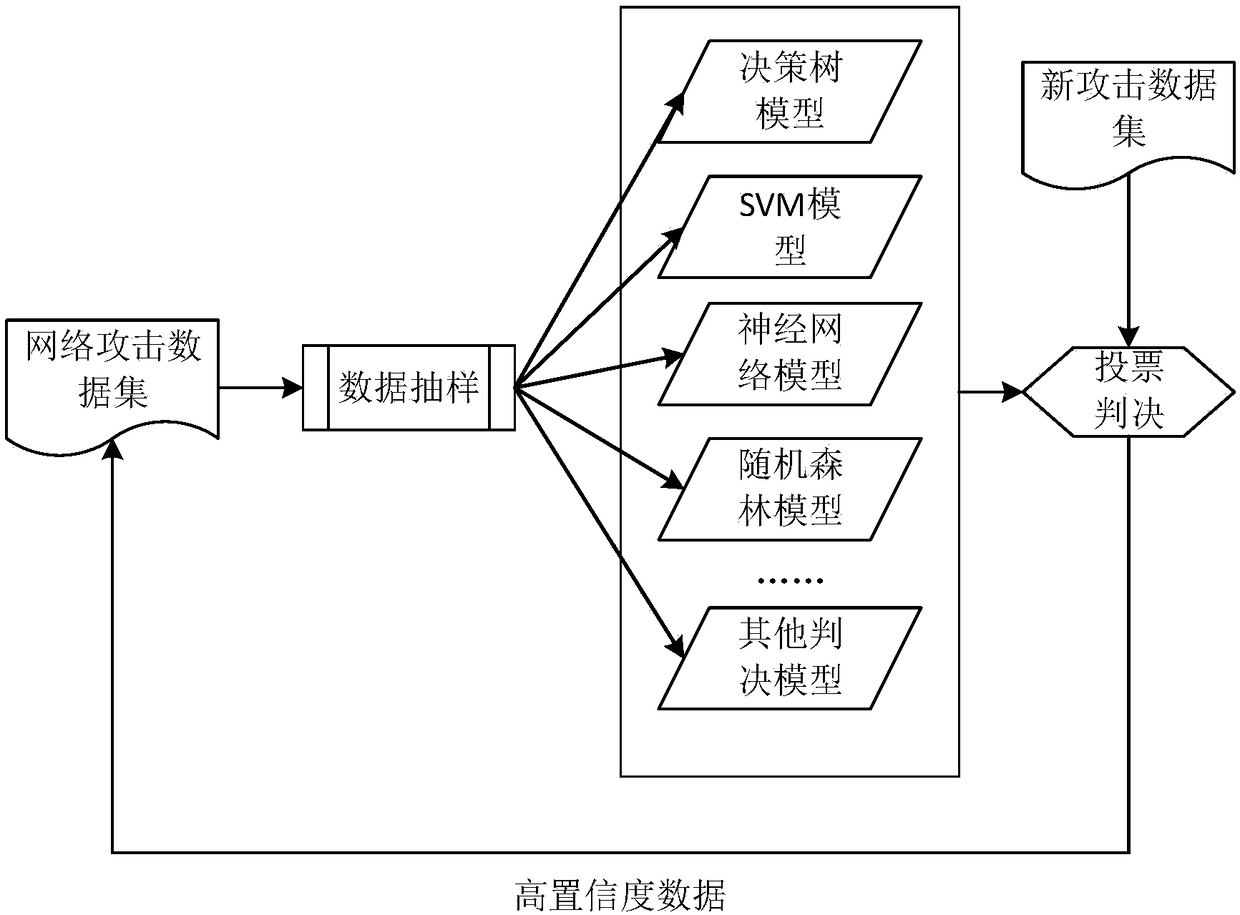
Image
Examples
Embodiment
[0031] Existing network intrusion detection methods include:
[0032] 1. Intrusion detection based on pattern matching
[0033] The research on intrusion detection began in the 1980s, and after the rise of the Internet, it received high attention and developed rapidly. As early as 1980, J Anderson and others made a technical report entitled "Computer Security Threat Monitoring and Surveillance" for the U.S. Air Force. This report is recognized as the pioneering achievement of intrusion detection. This report proposes the concept of intrusion detection for the first time, proposes to use audit messages to track suspicious behaviors of users, and simply divides intrusion behaviors. In 1985, Denning proposed an intrusion detection technology based on statistical analysis, real-time and user behavior profiles in Oakland, and made the first real-time intrusion detection system model, which is a milestone in the field of intrusion detection research. Since then, a large number of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com