Dynamic password acquisition method and device, terminal and storage medium
A technology of dynamic password and acquisition method, which is applied to secure communication devices and key distribution, can solve the problems of user loss and easy acquisition of dynamic passwords by others, and achieve the effect of ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
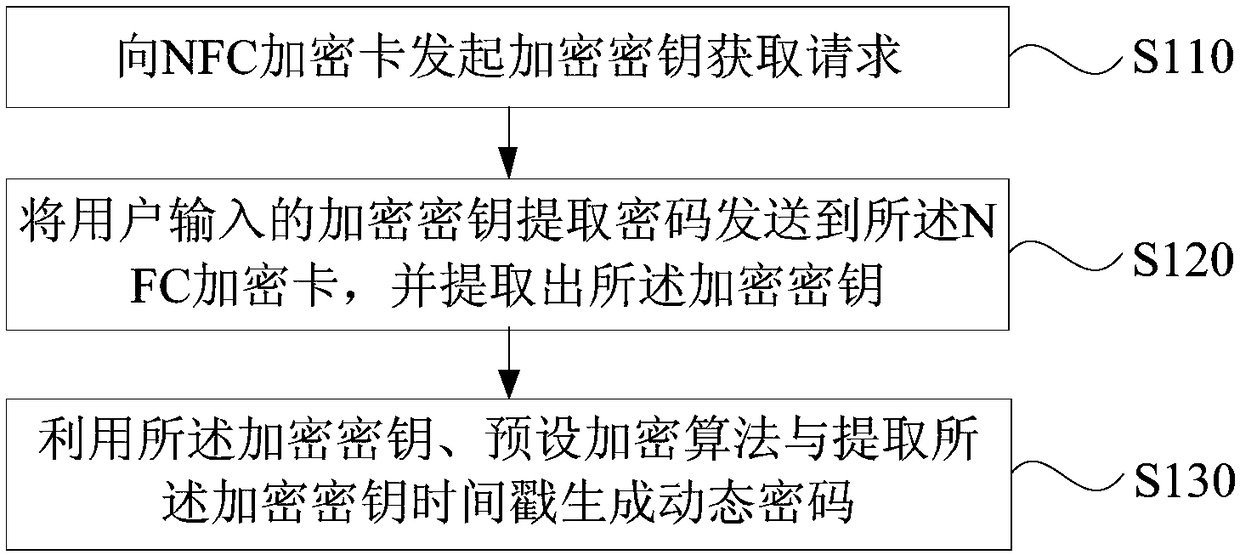
[0025] figure 1 It is a flowchart of a method for obtaining a dynamic password provided by Embodiment 1 of the present invention. This embodiment is applicable to the case where a terminal generates a dynamic password. The method can be executed by a device for obtaining a dynamic password, which can be configured in a terminal, for example. Such as figure 1 As shown, the method specifically includes:
[0026] S110. Initiate an encryption key acquisition request to the NFC encryption card.
[0027] Among them, the NFC encryption card is an NFC medium independent of the terminal, which is equivalent to an IC card using RFID technology, which can replace a large number of IC cards (including credit cards) in shopping malls, bus cards, access control, tickets, tickets, etc. Wait. The unique encryption key of its corresponding terminal is stored in the NFC encryption card.
[0028] Further, when the user initiates an identity authentication or a transaction operation, an encry...
Embodiment 2
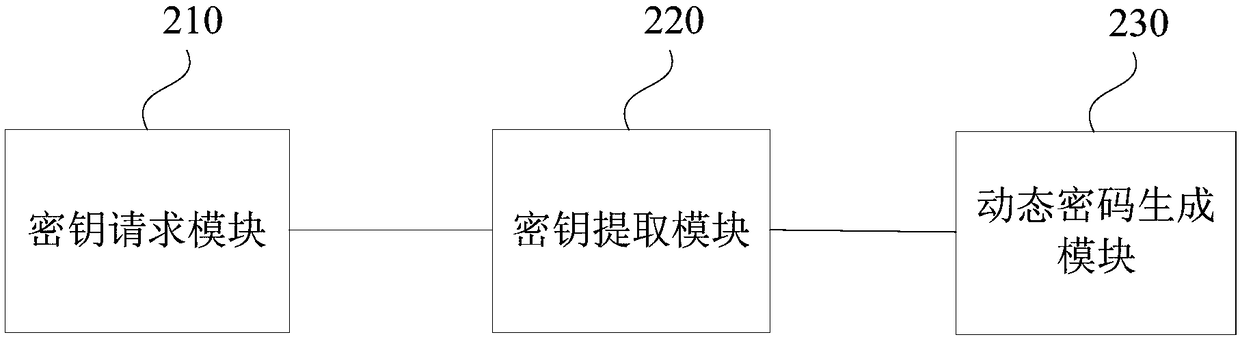
[0037] figure 2 It is a schematic structural diagram of a device for obtaining a dynamic password provided by Embodiment 2 of the present invention. Such as figure 2 As shown, the device includes: a key request module 210 , a key extraction module 220 and a dynamic password generation module 230 .
[0038] Among them, the key request module 210 is used to initiate an encryption key acquisition request to the NFC encryption card; the key extraction module 220 is used to send the encryption key extraction password input by the user to the NFC encryption card, and extract all The encryption key; the dynamic password generation module 230, configured to generate a dynamic password by using the encryption key, a preset encryption algorithm and extracting the encryption key time stamp.
[0039] In the technical solution of this embodiment, by storing the encryption key in the NFC encryption card, the encryption algorithm stored in the mobile terminal is stored in a different med...
Embodiment 3
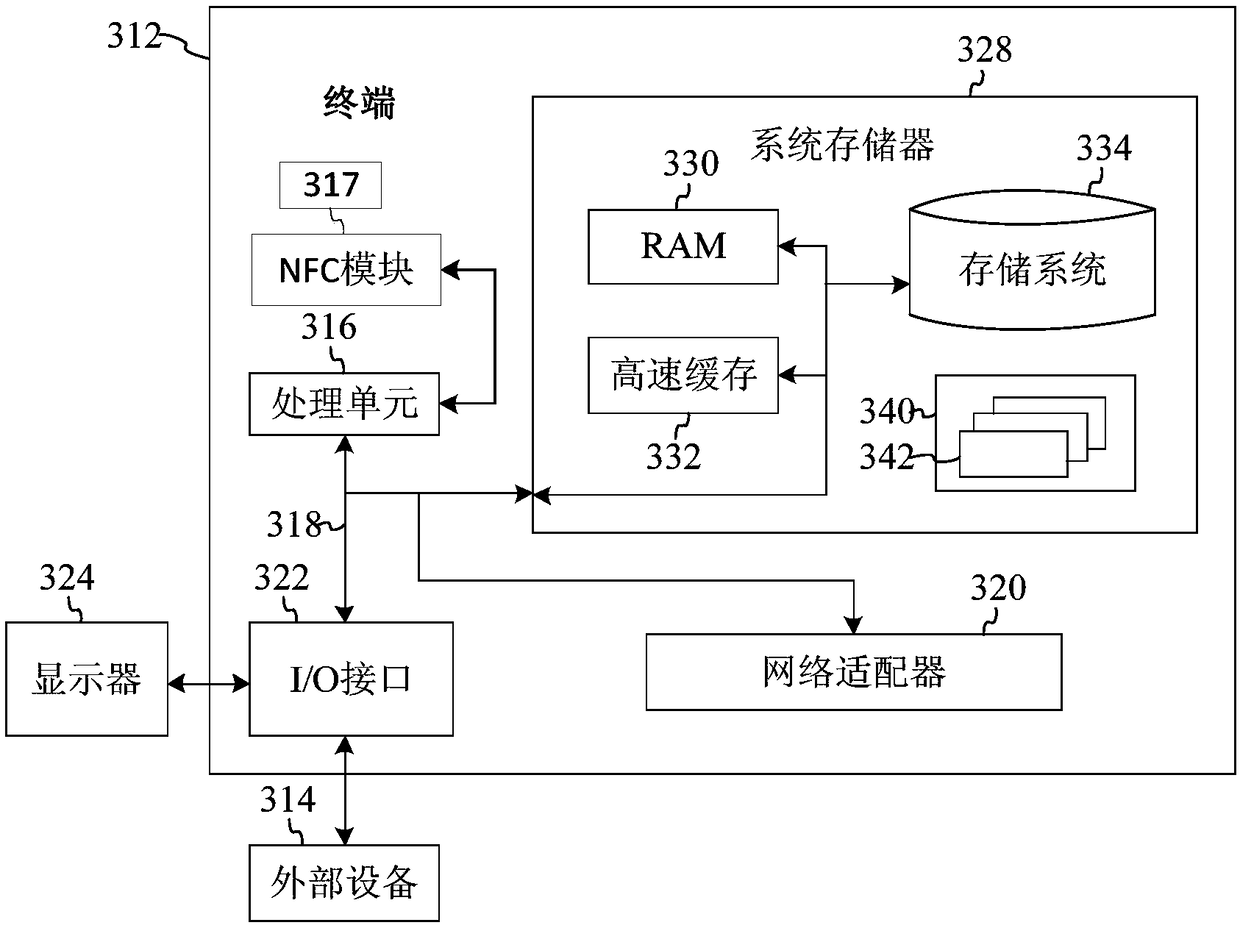
[0045] image 3 is a schematic structural diagram of a terminal in Embodiment 3 of the present invention. image 3 A block diagram of an exemplary terminal 312 suitable for use in implementing embodiments of the invention is shown. image 3 The displayed terminal 312 is only an example, and should not limit the functions and scope of use of this embodiment of the present invention.
[0046] Such as image 3 As shown, terminal 312 takes the form of a general purpose computing device. Components of terminal 312 may include, but are not limited to: one or more processors or processing units 316, system memory 328, NFC module 317, bus 318 connecting different system components (including system memory 328 and processing unit 316).
[0047] Bus 318 represents one or more of several types of bus structures, including a memory bus or memory controller, a peripheral bus, an accelerated graphics port, a processor, or a local bus using any of a variety of bus structures. These archi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com