Secure coding and decoding method of railway transponder messages based on lightweight chaotic authentication encryption
A transponder message, encoding and decoding method technology, applied in the direction of railway signal and security, secure communication through chaotic signal, railway signal, etc., can solve the problems of on-board ATP calculation, not proposed, wrong speed curve, etc., and achieve enhanced security protection effect of ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
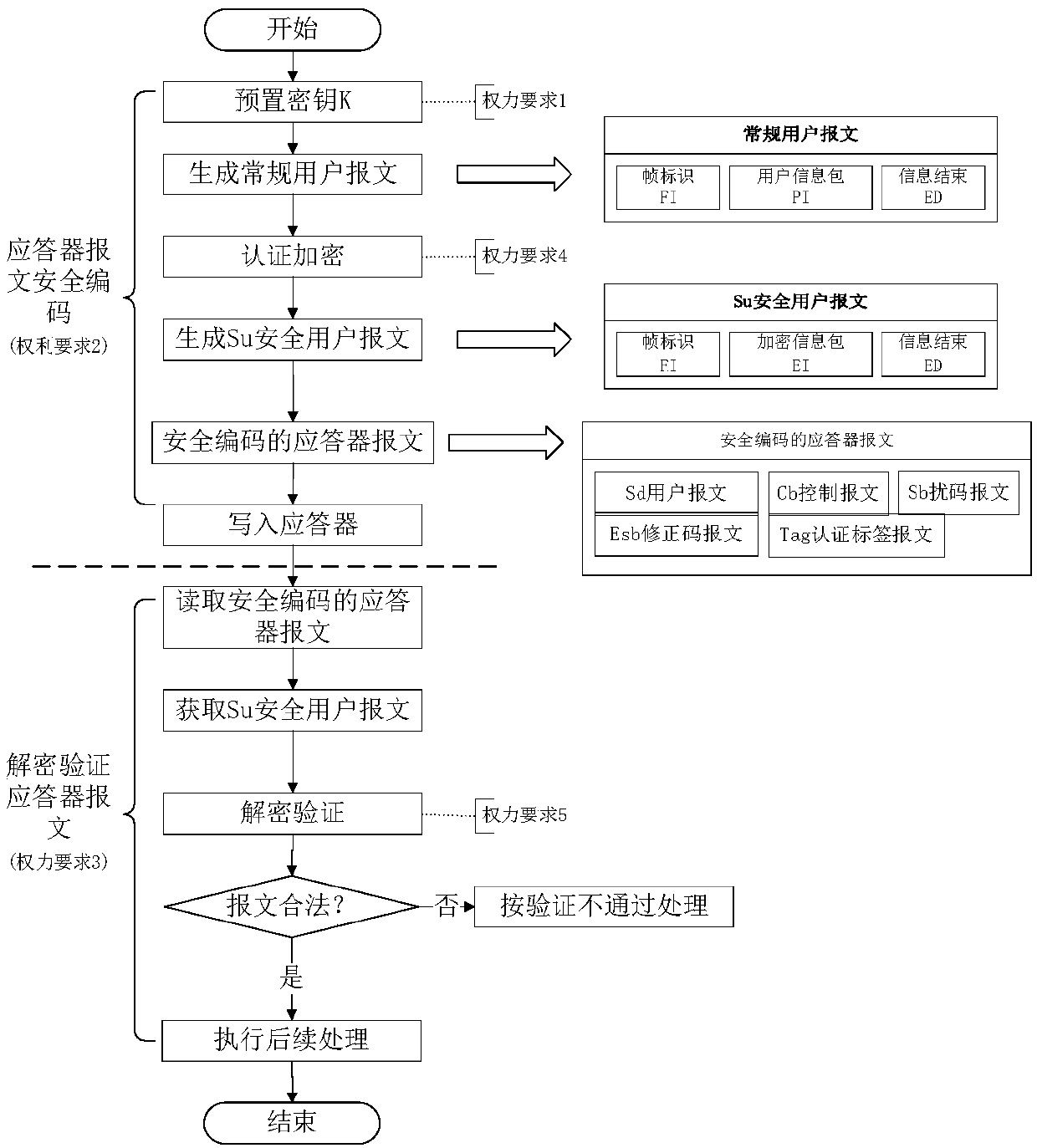
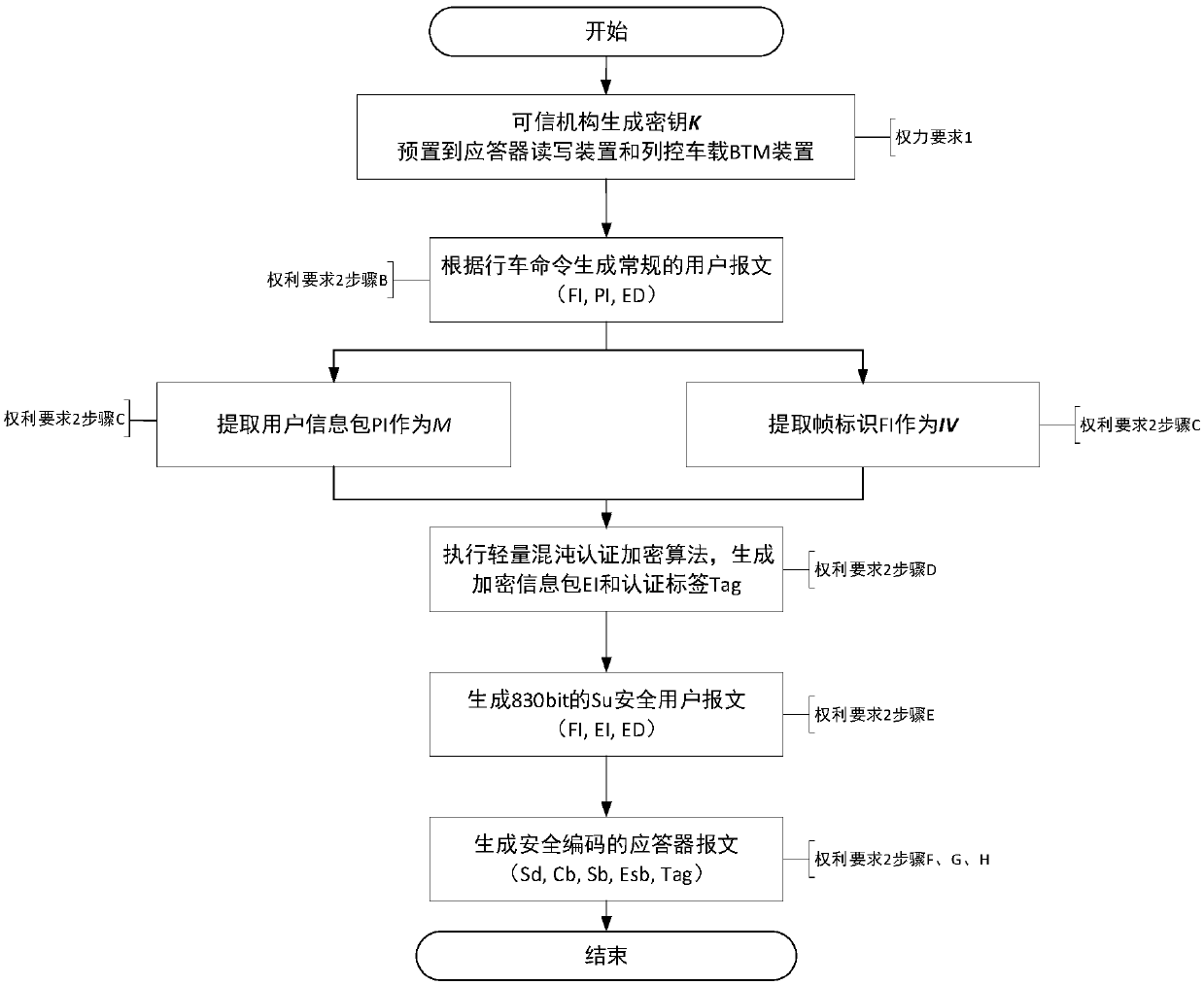
[0060] figure 2 It shows the security encoding process of the transponder message, and the specific steps are as follows:
[0061] 1. First, assign a 772-bit legal key K∈G(2 772 );
[0062] 2. The authorized party generates regular user messages (FI, PI, ED) according to the ETCS / CTCS responder standard;
[0063] 3. The read-write device of the transponder relies on the special lightweight chaos authentication encryption algorithm (such as Figure 4 Shown), generate encrypted information package EI and authentication label Tag, the steps are as follows:
[0064] a) Generate a 4×4 S box according to the key K, denoted as S(·), as an example, its content is as follows:
[0065] x
0
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
S(x)
12
7
15
0
13
11
3
1
10
2
6
14
9
5
8
4
[0066] b) Use the S-box to construct an integer chaotic coupled mapping lattice;
[0067] 1) Gener...
Embodiment 2
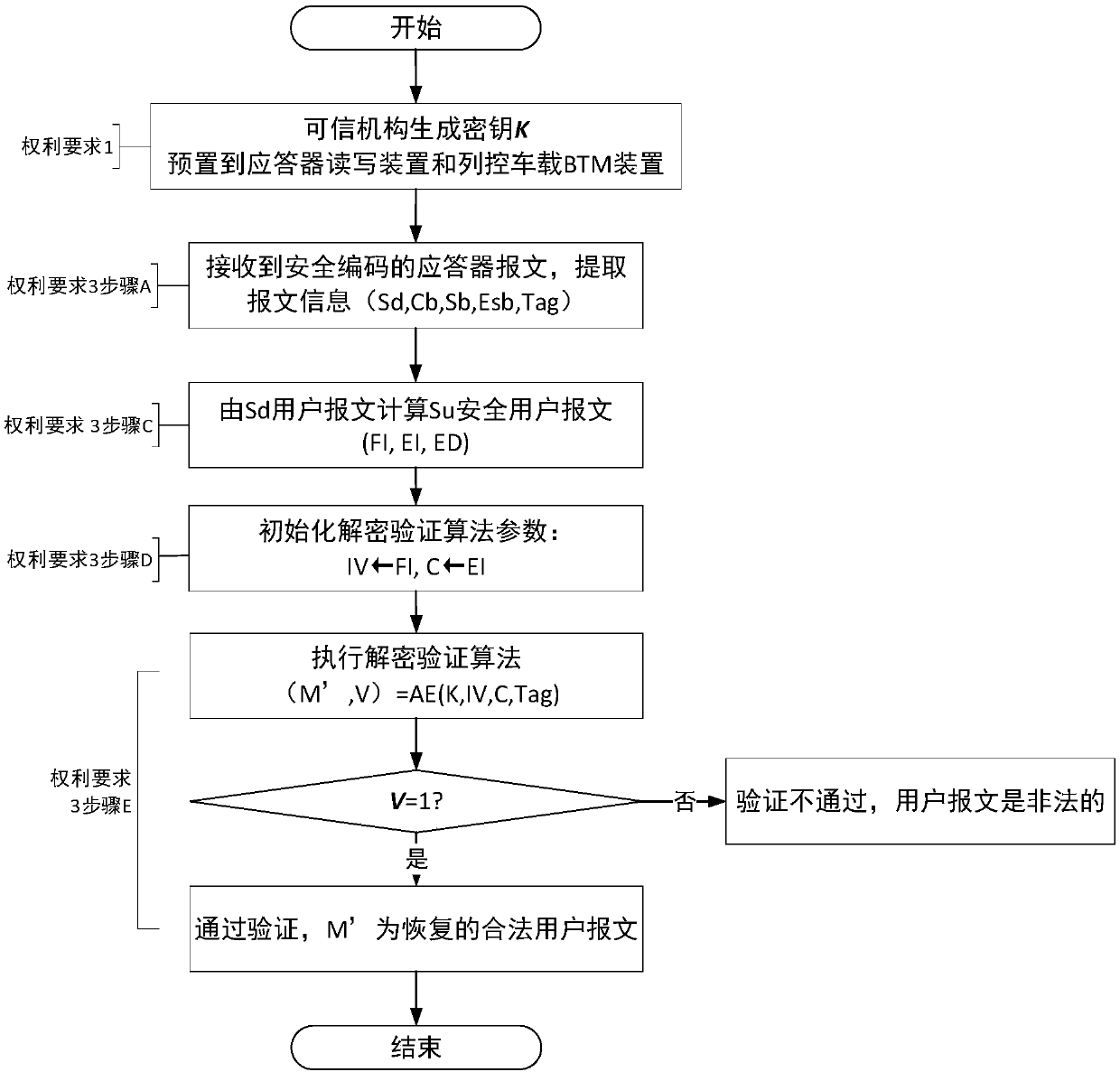
[0084] The transponder security encoding message format is shown in Table 1, in which the 913-bit Sd user message is obtained by extending the 830-bit Su security user message from 10 bits to 11 bits, and the extension method adopts the ETCS transponder standard; the Tag authentication label message is obtained by the authentication The 85-bit authentication label generated by the encryption algorithm is obtained; the generation method of the Cb control message, the Sb scrambling code message and the Esb correction code message is the same as the ETCS transponder standard;
[0085] Table 1 Transponder Security Coded Message Format
[0086] 1
2
3
4
5
Sd user message
Cb control message
Sb scrambled message
Esb correction code message
Tag authentication label message
83*11=913bit
3bit
12bit
10bit
85bit
[0087] Table 2 Su security user message structure (information frame)
[0088] serial number
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com