Instruction vulnerability analysis-based SDC error detection method
An error detection and vulnerability technology, applied in the direction of error detection/correction, non-redundancy-based fault handling, response to error generation, etc., to achieve the effect of reducing time overhead, improving accuracy, and ensuring detection rate
Active Publication Date: 2018-09-04
NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
View PDF7 Cites 7 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In the prior art, there is no report on using support vector regression to analyze the vulnerability of instruction SDC and detect SDC errors
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment
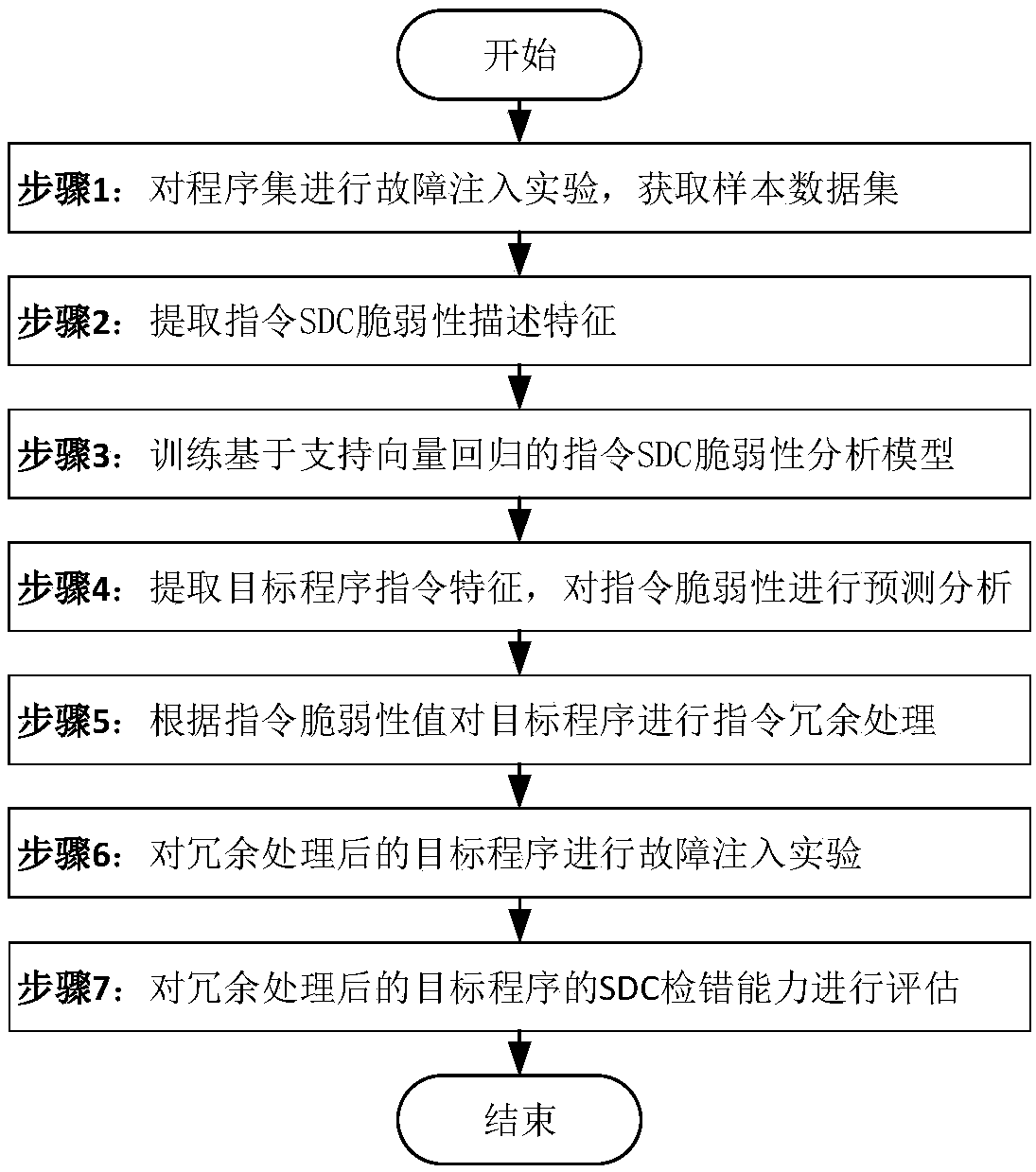
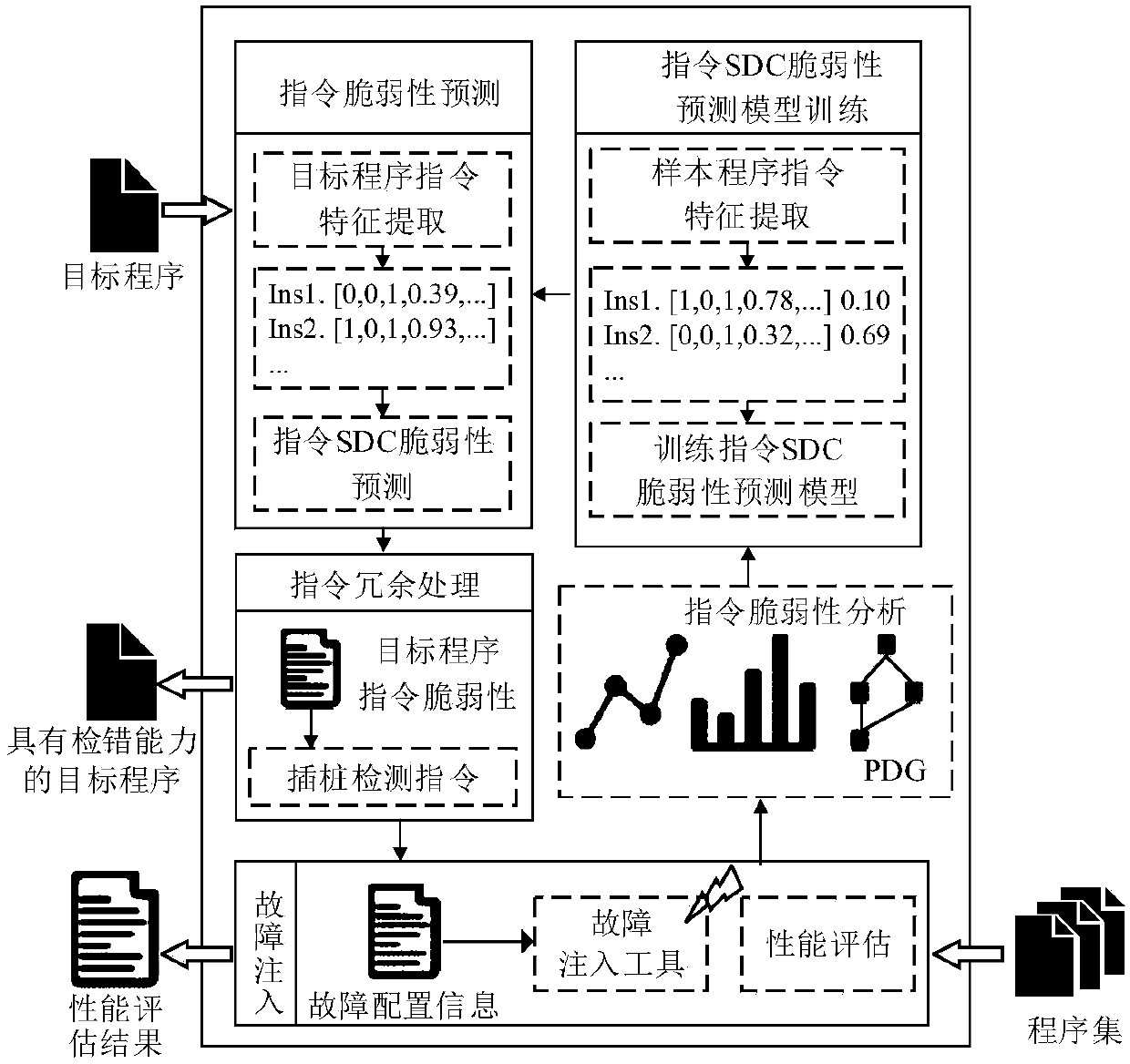
[0048] Combine figure 1 with figure 2 , The present invention is an SDC error detection method based on instruction vulnerability analysis. Including the following steps:
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
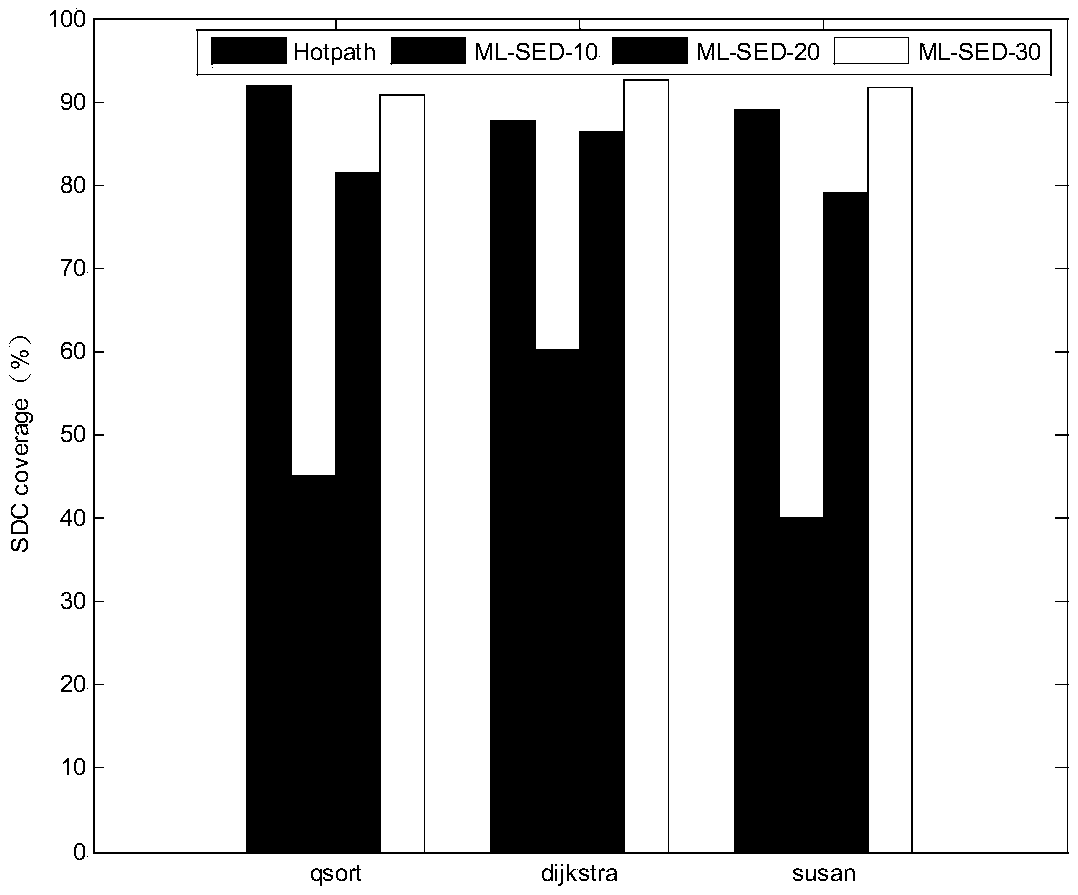
The invention discloses an instruction vulnerability analysis-based SDC error detection method. The method comprises the following steps of: 1, carrying out a fault injection test on a program set soas to obtain a sample data set; 2, extracting instruction SDC vulnerability description features; 3, training a support vector regression-based instruction SDC vulnerability analysis model; 4, extracting instruction features of a target program, and predicting and analyzing instruction vulnerability; 5, carrying out instruction redundancy processing on the target program according to an instruction vulnerability value; 6, carrying out fault injection test on the target program after the redundancy processing, and detecting SDC errors during the operation of the program; and 7, assessing an SDCerror detection ability of the target program after the redundancy processing. The method is high in SDC error detection rate and low in performance overhead, and can be applied to detection of program SDC errors caused by transient faults under severe environment.
Description
Technical field [0001] The invention belongs to the field of soft reinforcement and trusted software, and specifically relates to an SDC error detection method based on instruction vulnerability analysis. Background technique [0002] With the development of integrated circuit technology, while the performance of computers is greatly improved, chips are also more susceptible to space radiation. In the space environment, single event effects caused by high-energy particle irradiation or electromagnetic pulse interference are one of the main reasons for the failure of computer systems. Single event upset (Single Event Upset, SEU) is the most important form of single event effect. The system hardware failure caused by single event flip is called soft error, which is a transient failure. The impact of soft errors on system reliability is that it will propagate to the program, causing the program's state to be abnormal or functional. In the field of spaceborne computer research, th...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06F11/36G06F11/07
CPCG06F11/079G06F11/0793G06F11/3644
Inventor 庄毅张倩雯顾晶晶宴祖佳
Owner NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com