FPGA-based key index negotiation device, system and method
A key index and key technology, which is applied in the transmission system, digital transmission system, secure communication device, etc., can solve the problems of high cost, heavy workload of modifying the mapping table, and inflexibility of the prefabricated mapping table, so as to improve flexibility , the effect of small address conflict cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
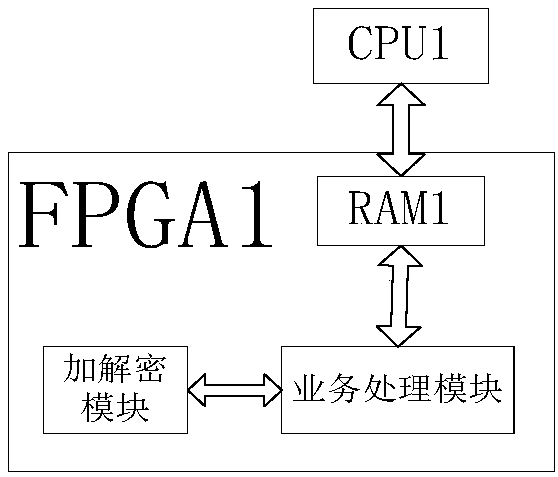
[0059] Such as figure 1 As shown, this embodiment relates to the key agreement device at the terminal 1, which is the communication initiator. FPGA1 and CPU1 are set at terminal 1; FPGA1 includes on-chip RAM1.
[0060] FPGA1 is used to search the table entry whose peer address is IP2 in the mapping table when receiving the data packet to be sent. If it is not found, notify CPU1 to create a new key index; it is also used to obtain the second frame sent by terminal 2, and Save in the on-chip RAM1 data area, and notify CPU1 to process;
[0061] CPU1 is used to execute: after creating a new key index, send the first frame to Terminal 2, the first frame includes the key index value, frame count, IP1 and IP2 of Terminal 1; when receiving the processing notification, read out the first frame In the second frame, add or update the state of the entry whose peer address is IP2 to FIN, and at the same time update the key index field of the entry to the key index value in the second fra...
Embodiment 2
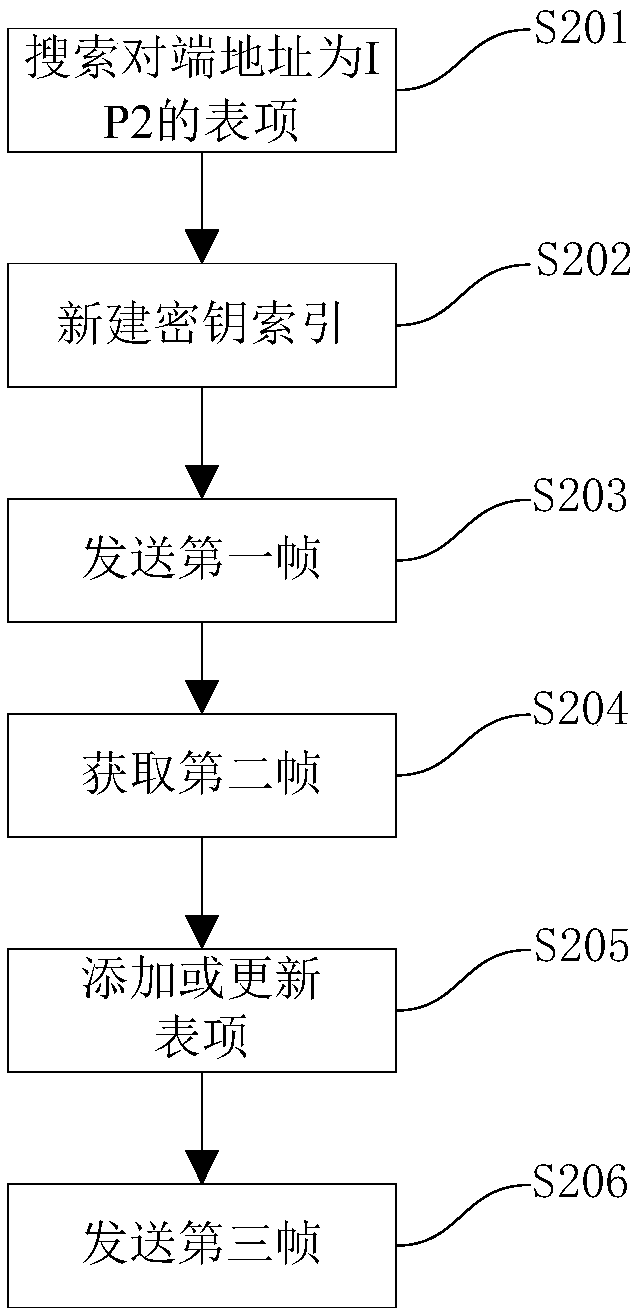
[0084] Such as figure 2 As shown, this embodiment relates to the key agreement method implemented at the communication sending end, that is, the terminal 1 .
[0085] Including the following steps:
[0086] Step S201, after receiving the data packet to be sent, search for the entry whose peer address is IP2 in the mapping table;
[0087] Step S202, if not found, create a new key index; otherwise, end.
[0088] Step S203, sending a first frame to terminal 2, the first frame including key index value, frame count, IP1 and IP2 of terminal 1;
[0089] Step S204, obtaining the second frame sent by the terminal 2, and saving it;
[0090] Step S205, read the second frame, add or update the state of the entry whose peer address is IP2 to FIN, and update the key index field of the entry to the key index value in the second frame;
[0091] Step S206, sending a third frame to Terminal 2, where the third frame includes the key index value of Terminal 1, frame count, IP1 and IP2.
[...
Embodiment 3
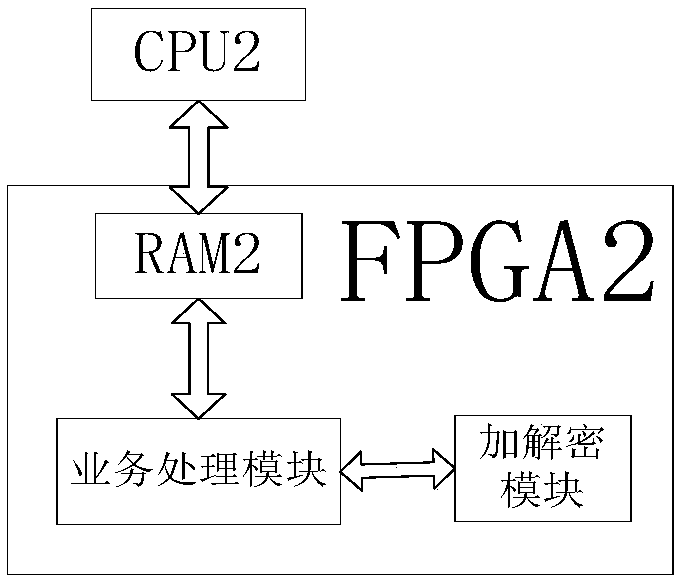
[0094] This embodiment relates to the key agreement device at the terminal 2 which is the receiving end of the communication. FPGA2 and CPU2 are set at the terminal 2, and FPGA2 includes an on-chip RAM2 data area.
[0095] specifically,
[0096] FPGA2 is used to capture the first frame sent by terminal 1 and save it in the on-chip RAM2 data area; it is also used to capture the third frame sent by terminal 1 and save it in the on-chip RAM2 data area;
[0097] CPU2, to execute:
[0098] Read the first frame, find the entry whose peer address is IP1, add or update the state of the entry to ACK, and update the key index field of the entry to the key index value in the first frame;
[0099] sending a second frame to terminal 1, the second frame including key index value, frame count, IP1 and IP2 of terminal 2;
[0100] Read the third frame, add or update the state of the entry whose peer address is IP1 to FIN, and update the key index field of the entry to the key index value in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com