Novel highly integrated identity recognition and security verification control equipment
A technology of security equipment and security verification, which is applied in the field of new highly integrated identification and security verification control equipment, can solve the problems of improving equipment, waste, not suitable for display, etc., and achieve high security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
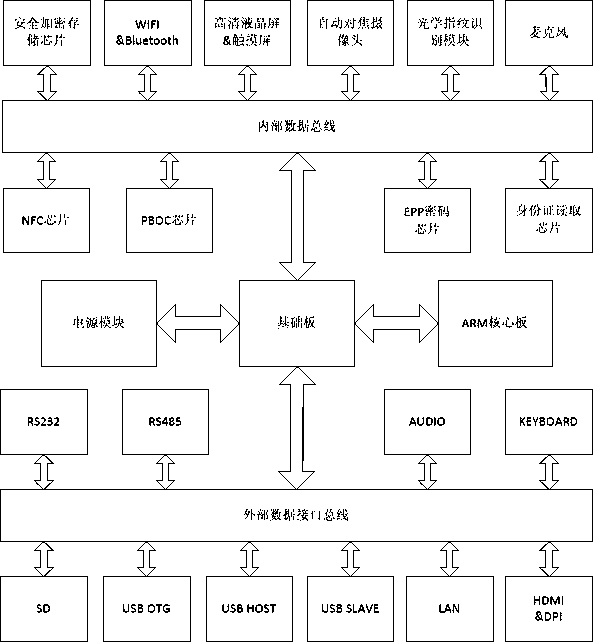
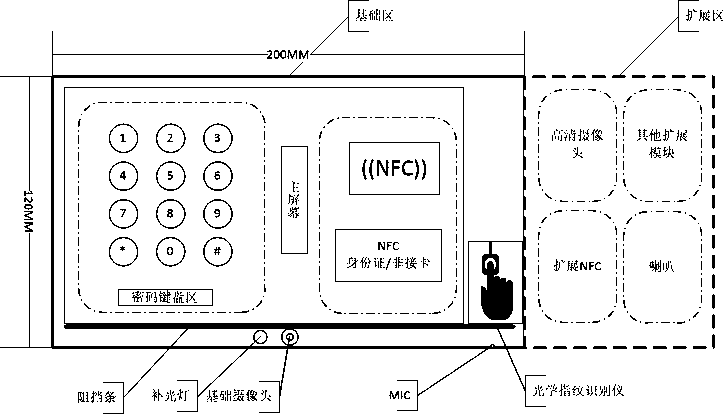
[0032] 1. Dynamic encrypted keyboard: LCD full-touch encrypted keyboard; characters including 0-9, a-z, A-Z, !@#$%&* and space can be input, including special function keys such as back, confirm, and cancel; The buttons can be used to switch between the numeric keyboard and the alphabetic character keyboard. When switching to the character keyboard, the upper and lower case can be switched through the shift key; both the numeric keyboard and the alphabetic keyboard are displayed in a dynamic manner to ensure the order of all inputable characters each time The positions on the screen and on the screen are random; after the password is entered, it will enter a special encryption chip for storage. In addition, you can choose not to dynamically display the password keyboard according to the application requirements.
[0033] 2. Password encrypted storage: load the master encryption key into the encryption chip in plain text; load the communication key into the encryption chip in c...
PUM
| Property | Measurement | Unit |
|---|---|---|
| Thickness | aaaaa | aaaaa |
Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com