Secured execution context data
A technology of execution context and data, applied in secure communication devices, digital data protection, computer security devices, etc., to achieve the effect of protecting integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
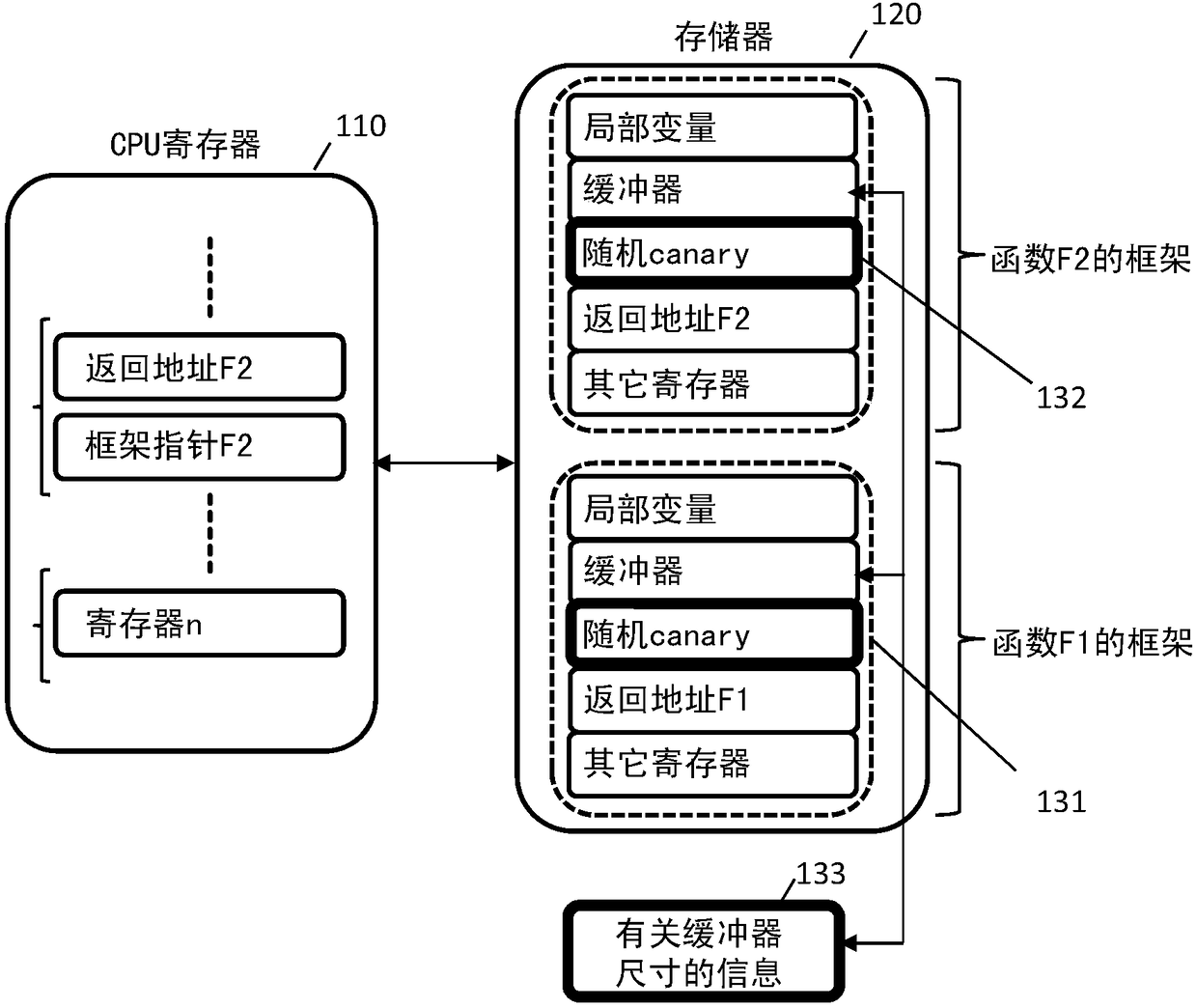
[0030] figure 1 Some protection mechanisms are shown.
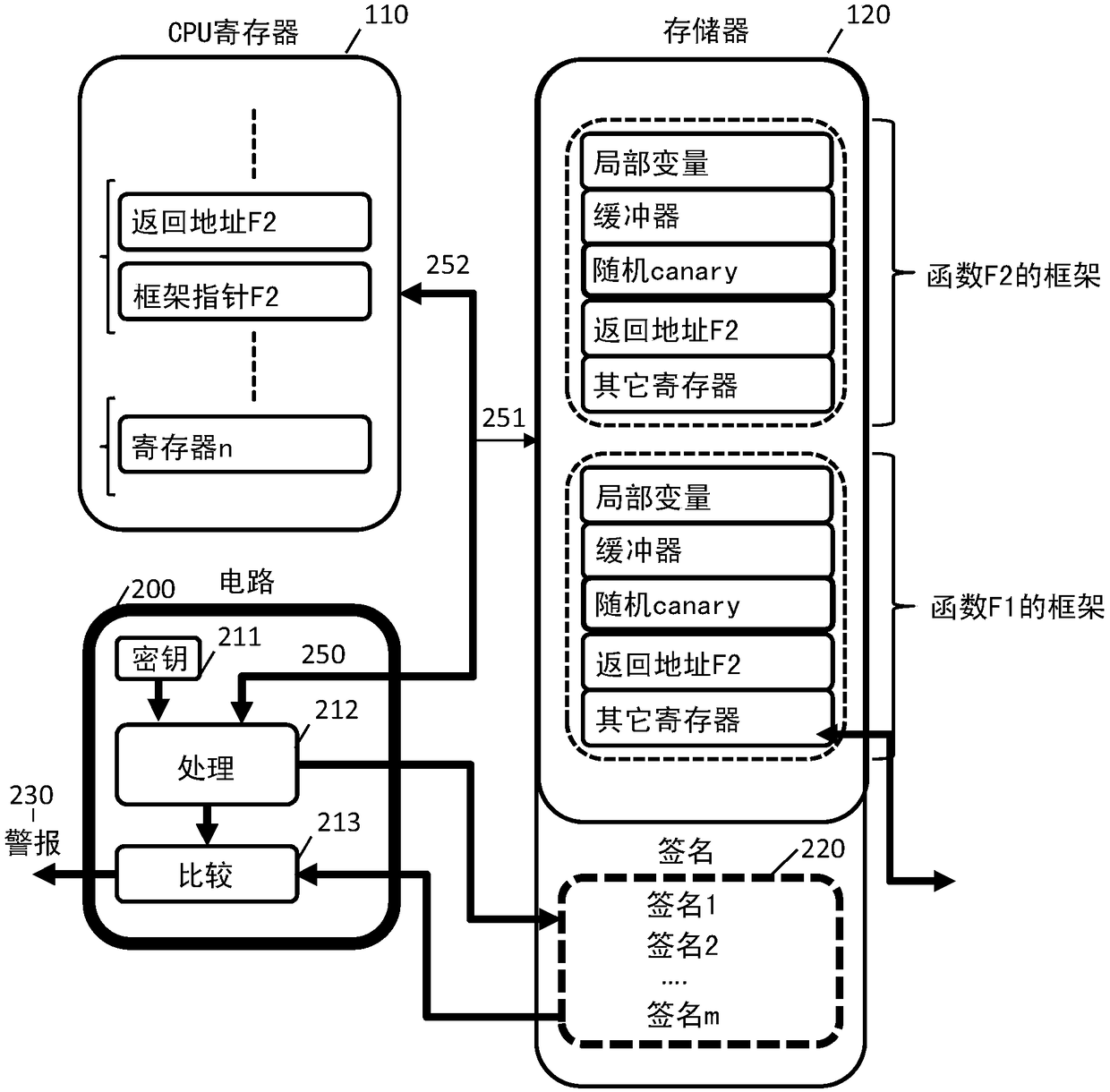
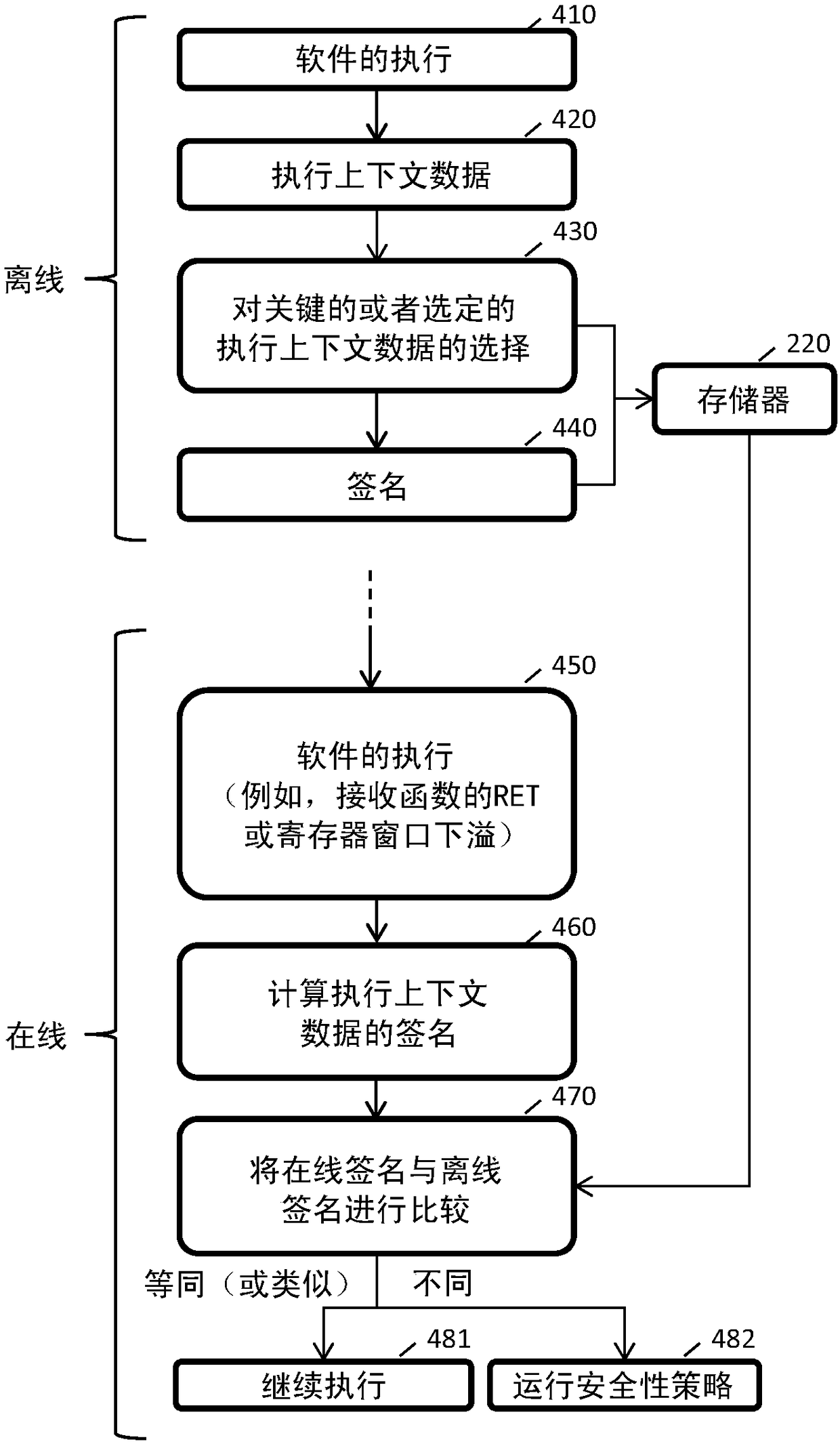
[0031] A register 100 of a processor or a central processing unit (CPU) 100 communicates with a memory 120 . The executed software program is associated with different frames for different functions (eg frame 131 calling function F1 of frame F2 132 ). To protect these frames (execution context data), so-called "canaries" are used to protect critical or sensitive data, including execution context data. The canary word is a known value placed between the buffer and control data on the stack to monitor for buffer overflow 133 . On a buffer overflow, the first data to be corrupted is usually the canary, and thus a failure to validate the canary data is an alarm of overflow, which can then be handled, for example, by invalidating the corrupted data. In this example, a random canary (131, 132) is incremented just before the address is returned to the stack to detect overflow. Raises a security exception if the canary is ove...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com