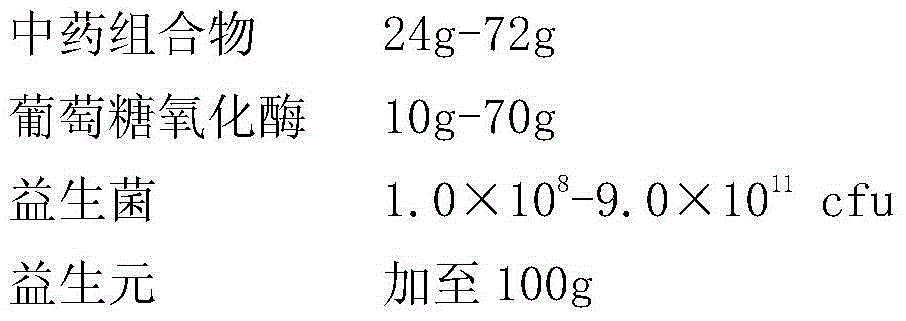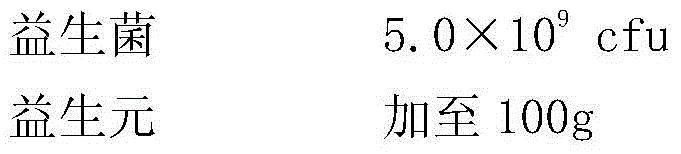Patents
Literature
69results about How to "Protect Integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
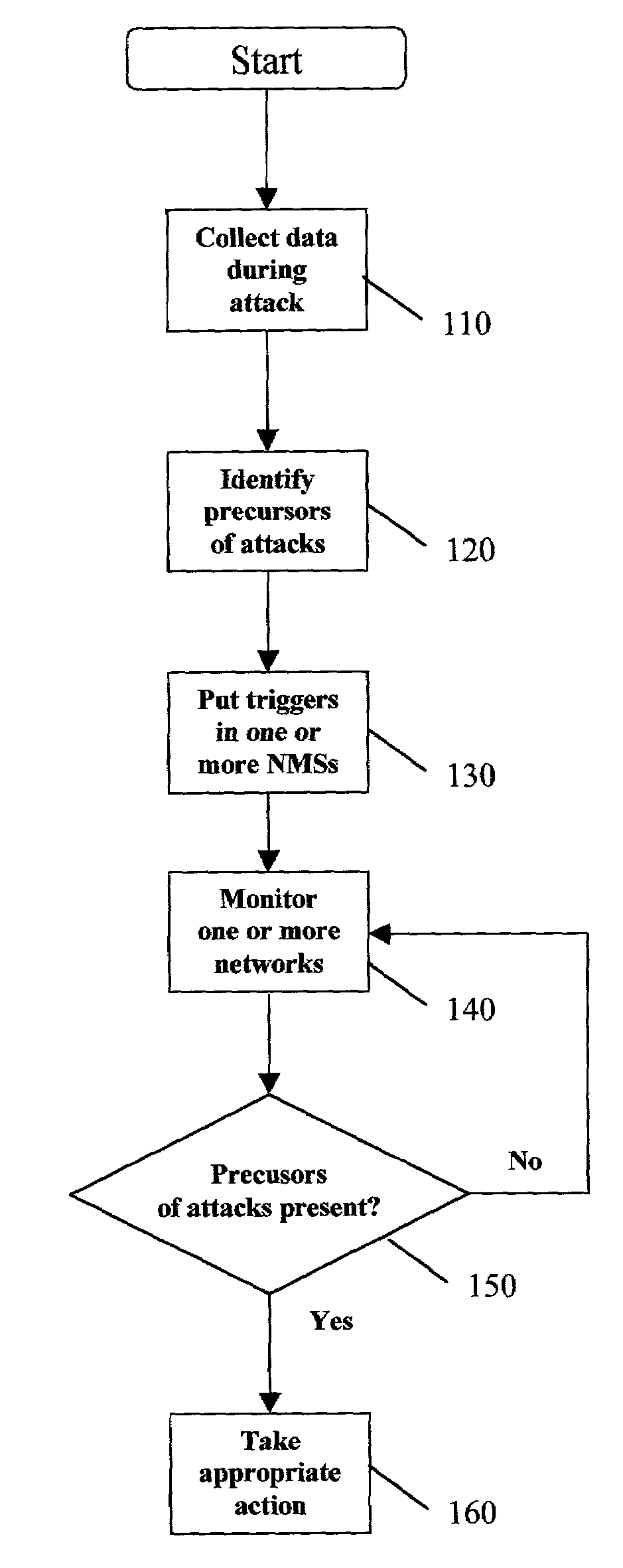
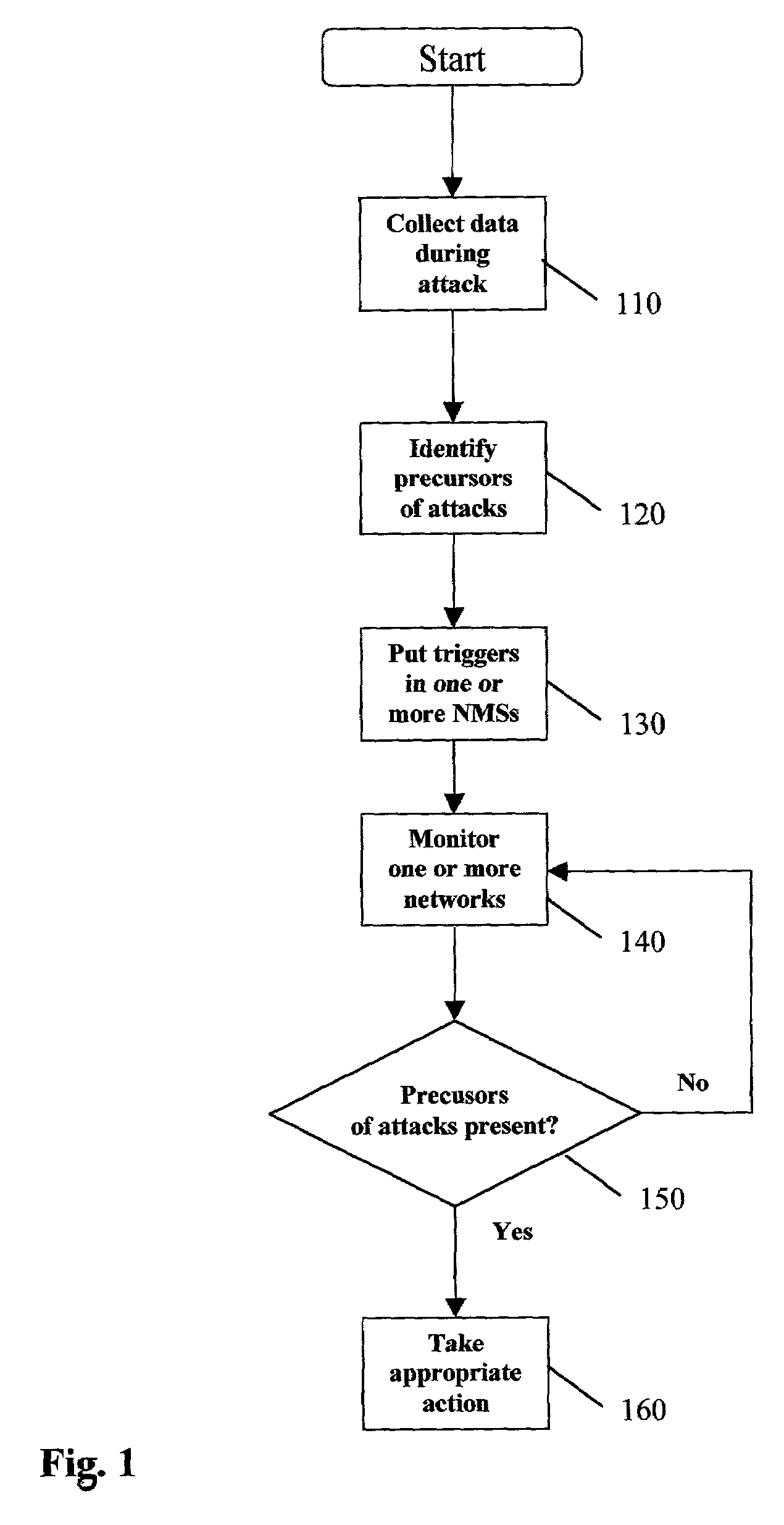
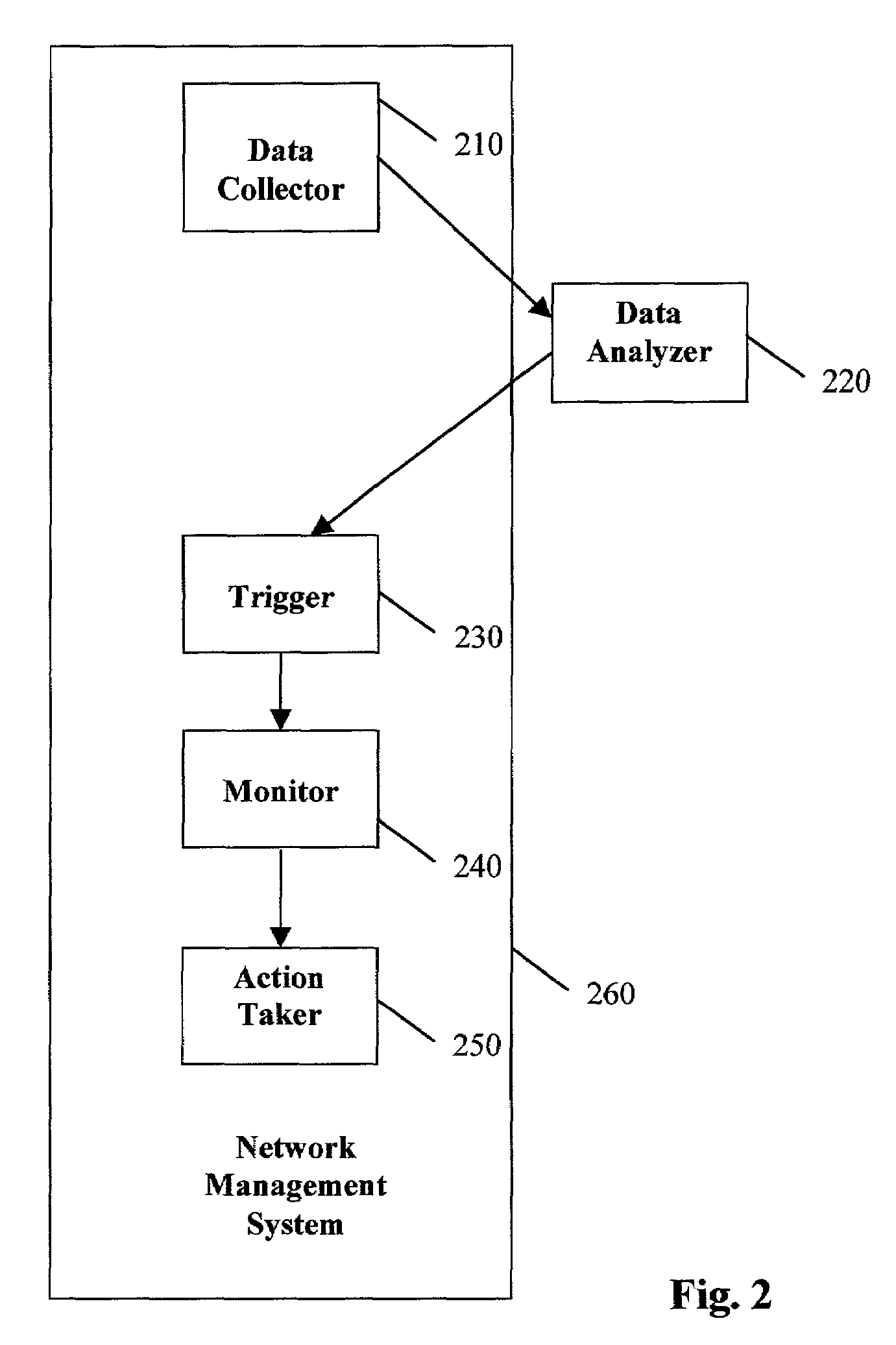
Method and apparatus for predicting and preventing attacks in communications networks
InactiveUS7603709B2Protect integrityImprove integrityMemory loss protectionError detection/correctionIntrusion detection systemSpecific time
In one embodiment of a method and apparatus for predicting and preventing network attacks, data is collected from network devices during an attack. The collected data is analyzed to identify specific temporal precursors of the attack. The future network activity is then monitored for the presence of the identified temporal attack precursors. When the presence of a precursor is detected, appropriate protective action is taken. Preferably, all steps in this process occur automatically. In the preferred embodiment, the process is performed under the control of one or more network or element management systems. The possible network domain includes data, voice, and video networks and multiple, interconnected network technologies. In one embodiment, triggers responsive to the presence of the identified precursors are placed into a network or element management system. The preferred embodiment of the invention utilizes machine-learning algorithms for discovering precursors of attacks, but any suitable algorithm may be used. The invention may be used in “attack autopsy” mode only, monitoring mode only, or both. Among other uses, the invention allows integration of Intrusion Detection Systems with Network Management Systems.
Owner:COMP ASSOC THINK INC +1
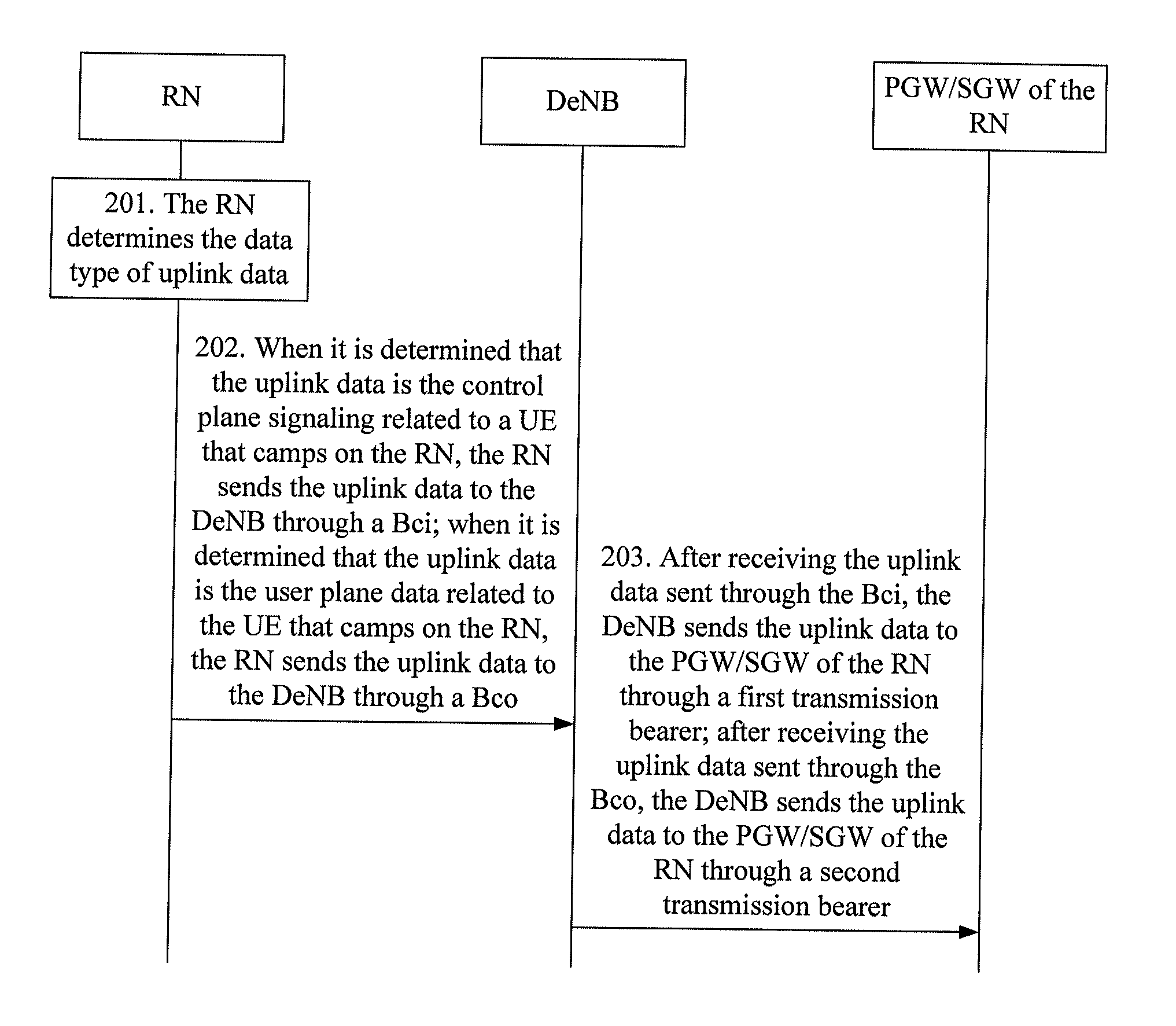
Method, apparatus, and system for data transmission
ActiveUS20120182929A1Protect IntegrityImprove protectionFrequency-division multiplex detailsNetwork topologiesData transmissionUser equipment
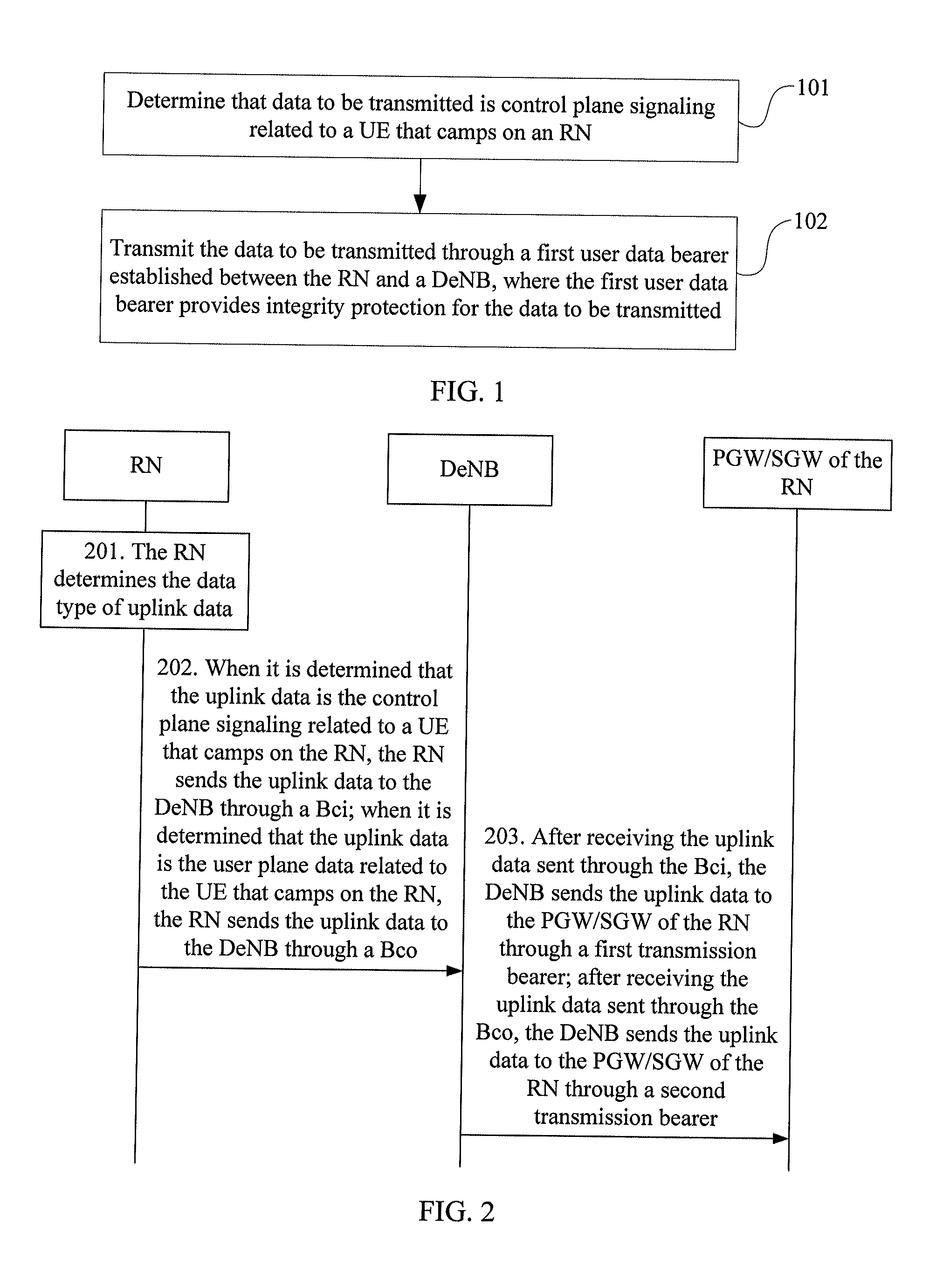
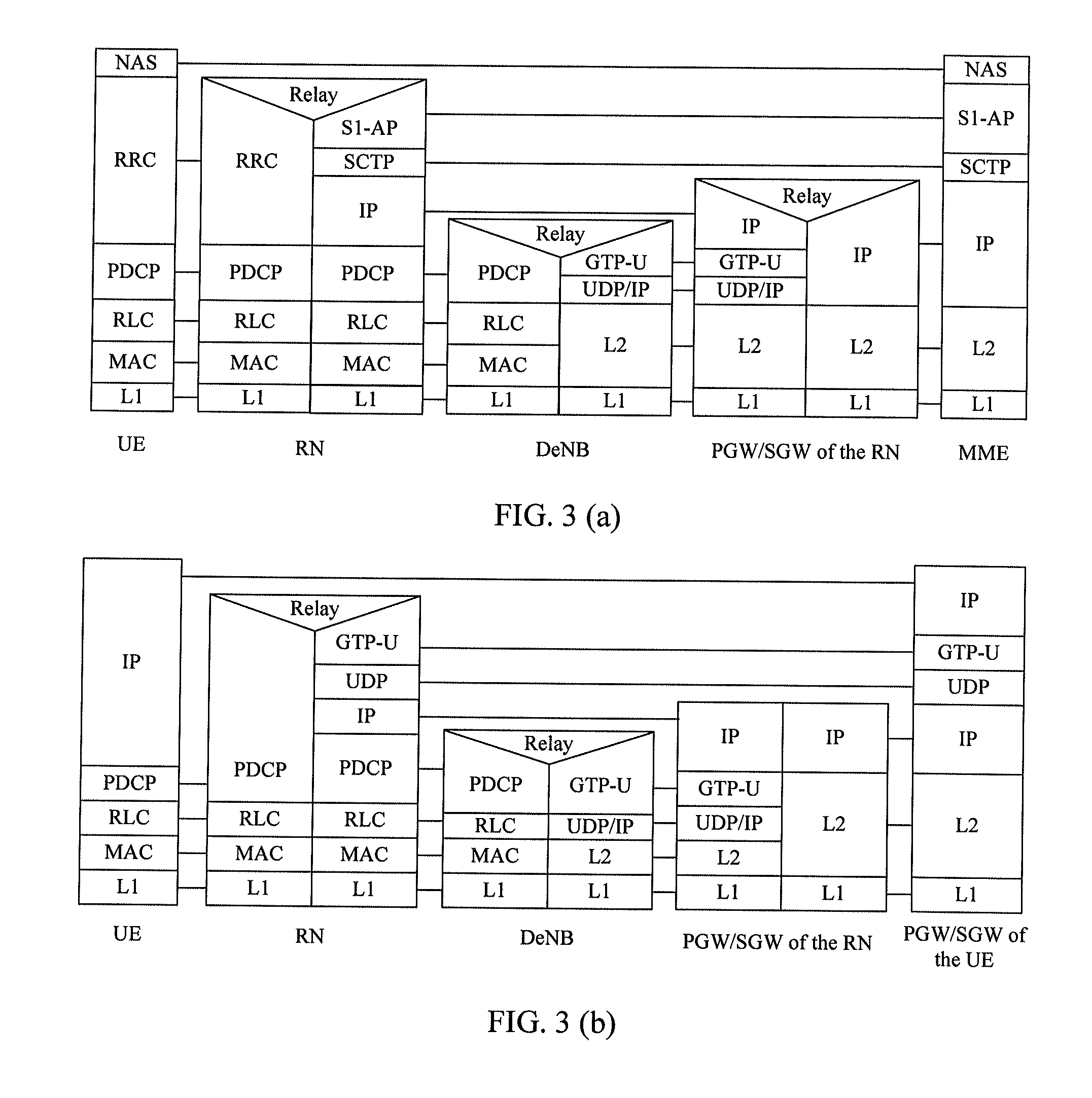
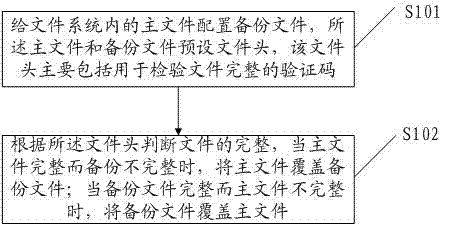
Embodiments of the present invention disclose a method, an apparatus, and a system for data transmission. The method for data transmission includes: determining that data to be transmitted is control plane signaling related to a user equipment that camps on a relay node; and transmitting the data through a first user data bearer established between the relay node and a donor base station, where the first user data bearer provides integrity protection for the data. According to the embodiments of the present invention, when the control plane signaling related to the user equipment that camps on the relay node is transmitted between the relay node and the donor base station, integrity protection is provided for the control plane signaling, and therefore attacks such as the denial of a service attack are prevented.
Owner:HUAWEI TECH CO LTD
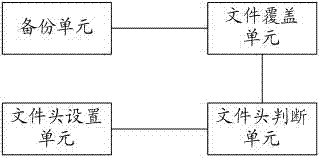
Method and device for storing file backups and backup method for file systems
ActiveCN102411523AProtect IntegrityGuaranteed integrityRedundant operation error correctionSpecial data processing applicationsFile systemBackup
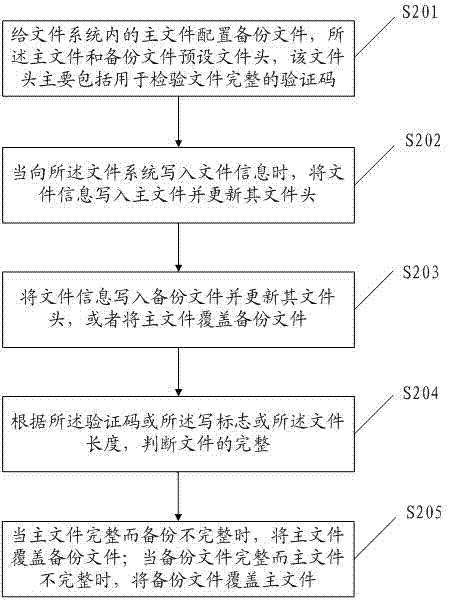
The invention discloses a method and a device for storing file backups and a backup method for file systems. The storing method comprises the following steps that: the main file in the file system is configured with backup files; the main file and the backup file are pre-set with file headers; the file header mainly comprises verification codes for detecting the completeness of files; the completeness of the file is judged according to the file header; when the main file is complete while the backup file is incomplete, the main file covers the backup file; when the backup file is complete while the main file is incomplete, the backup file covers the main file. Incompleteness of files can be judged according to the file header by adopting the invention and the incomplete file is restored by another file (main / backup file) so as to guarantee the completeness of main / backup files.
Owner:GUANGDONG VTRON TECH CO LTD
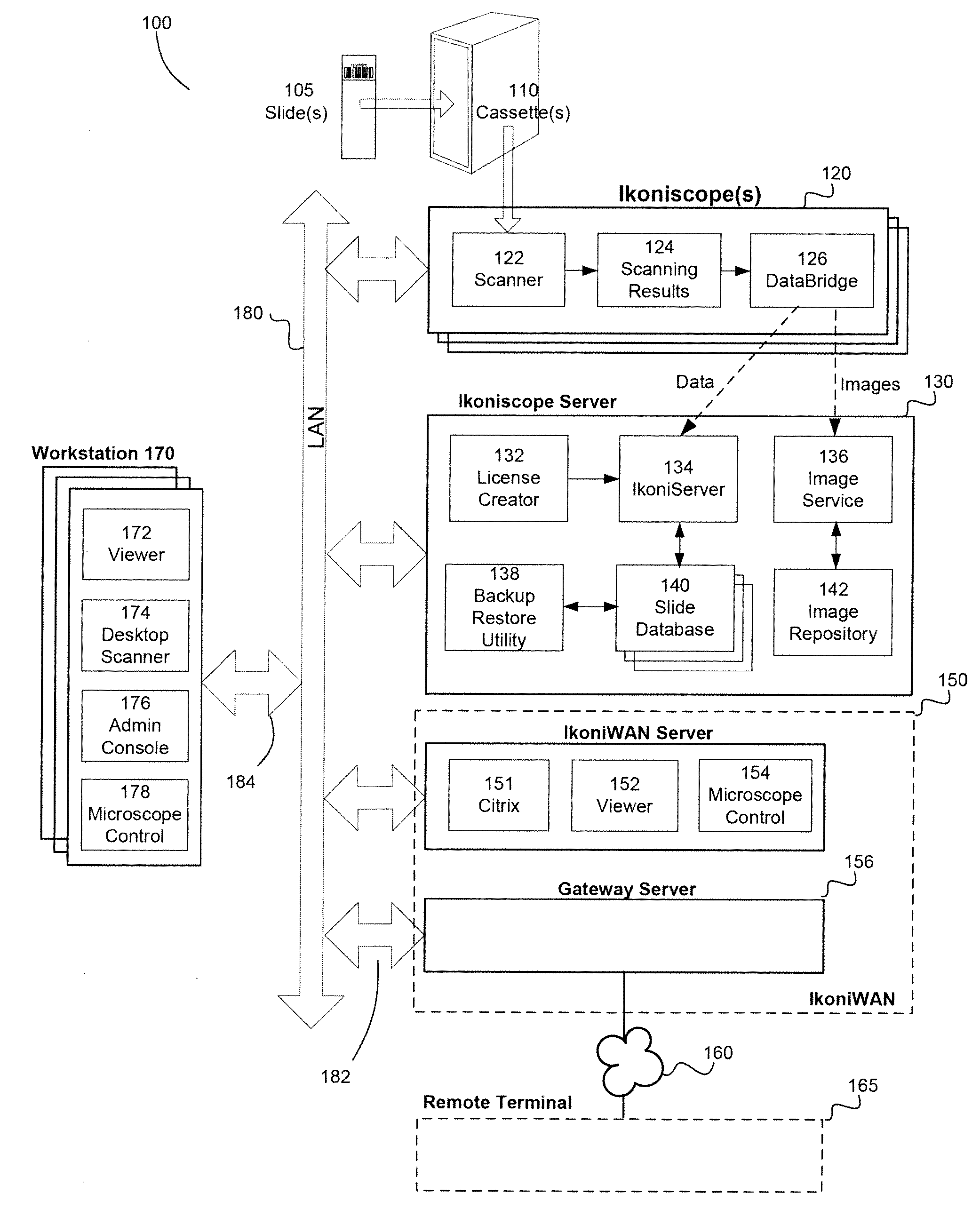
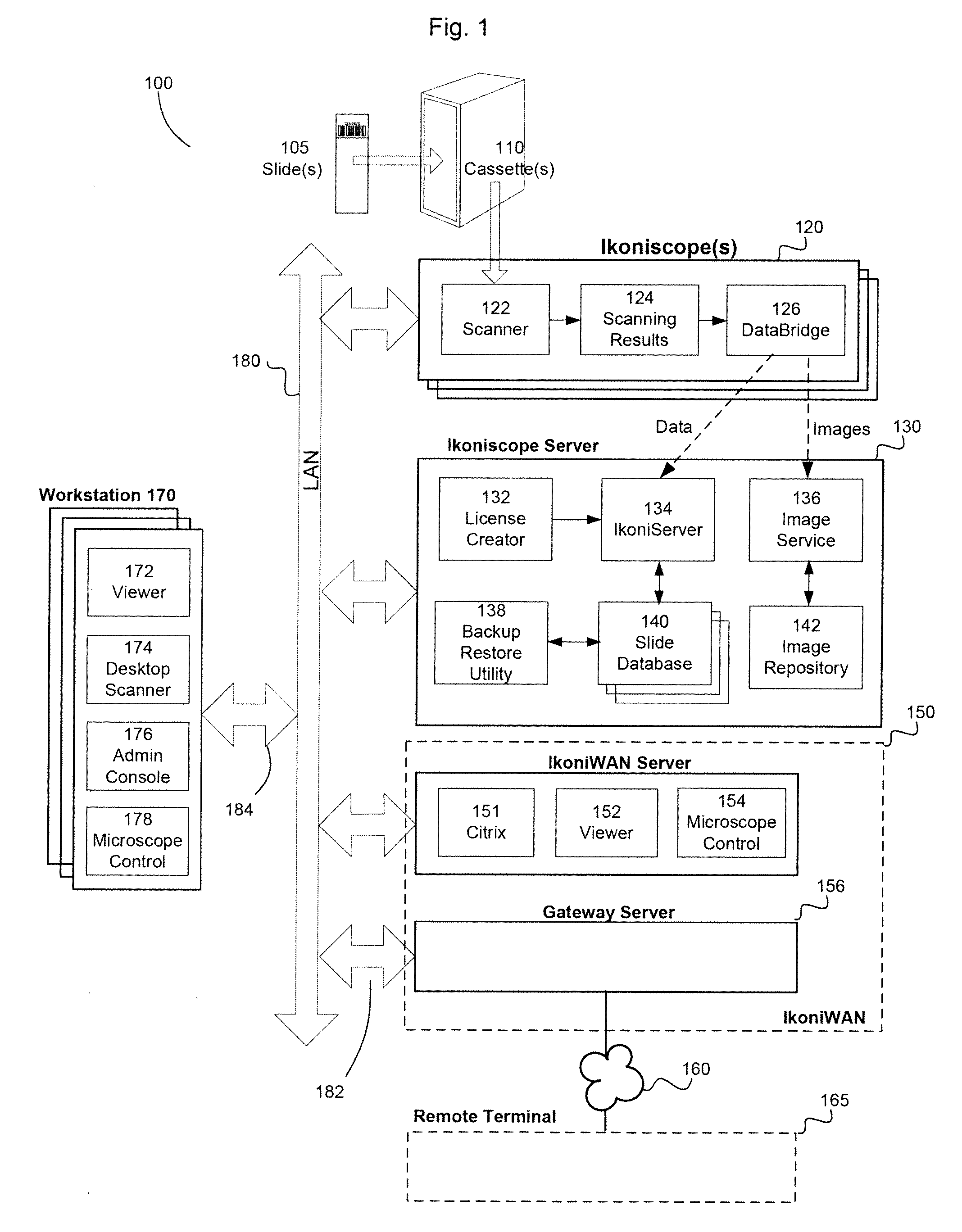
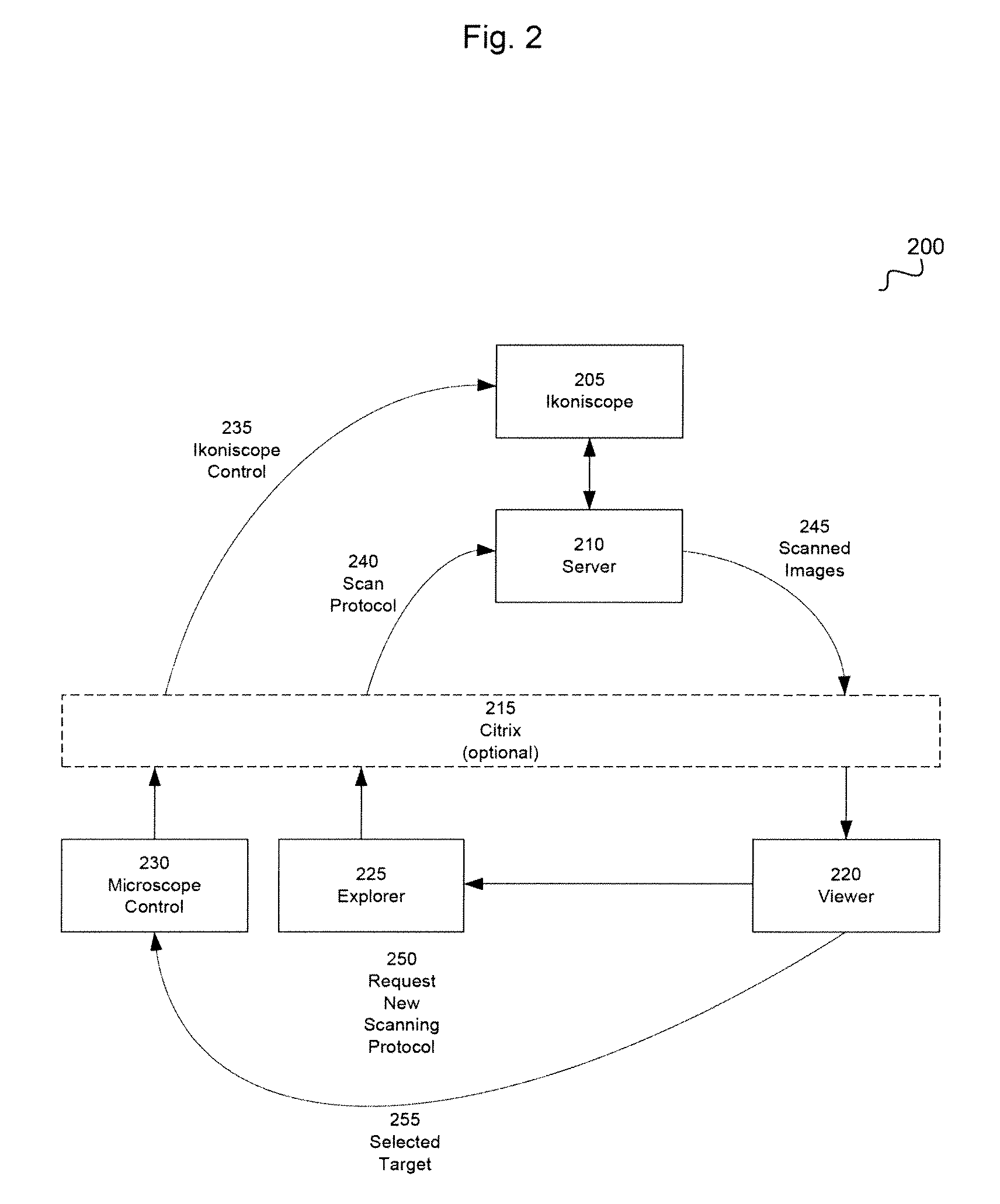
System and method for remote control of a microscope
InactiveUS20100315502A1Protect integrityImprove integrityTelevision system detailsColor television detailsAutomated microscopyMicroscope
Owner:IKONISYS INC
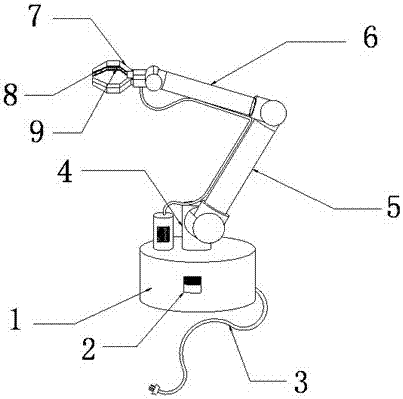
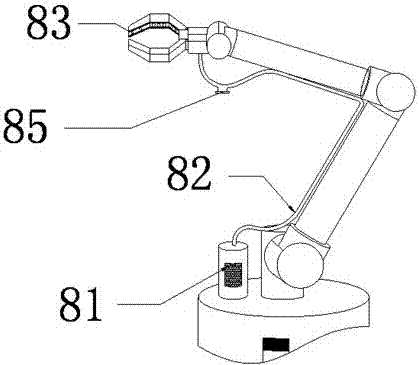
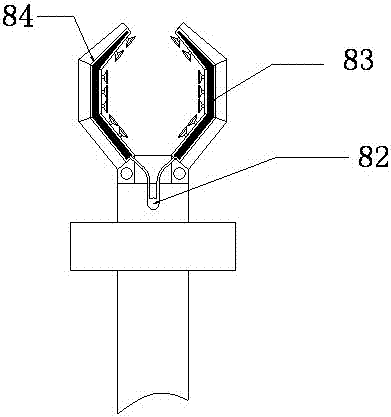
Automatic equipment part clamping mechanism
InactiveCN107139201AAvoid indentationProtect IntegrityProgramme-controlled manipulatorGripping headsSmooth surfaceEngineering
The invention provides a clamping mechanism for automatic equipment parts, which includes an inflator, a rubber hose, a strip air bag, a rubber suction cup and a spring. The upper end of the pipe is connected with the bar-shaped air bag, the bar-shaped air bag is installed in the air bag groove, the lower end of the rubber suction cup is connected with the rubber pad one, the spring upper end is connected with the rubber pad one, and the spring bottom is connected with the rubber pad two. The clamping mechanism produces indentations when clamping the parts, which is beneficial to protect the integrity of the clamped parts, facilitates the clamping of parts with smooth surfaces, and makes the clamping mechanism more powerful in clamping functions.
Owner:SUZHOU FUTENG INTELLIGENT TECH CO LTD
Tire monitoring device with coupled power source
InactiveUS7082818B2Protect integrityImprove integrityAntenna supports/mountingsTyre measurementsElectricityElectrical connection
A method and apparatus for connecting an electronic monitoring device to a pneumatic tire includes mounting the monitoring package of the monitoring device within the body of the tire or the body of a patch and subsequently connecting the power source to the monitoring package through electrical coupling. The method allows the monitoring package to be cured within the tire or the patch at relatively high temperatures while protecting the sensitive power source from the high temperatures. The use of electrical coupling to achieve the power transfer prevents the material surrounding the monitoring package from being pierced by an element that would form the direct electrical connection. The method allows the monitoring package and its antenna to be positioned in a variety of positions on or within the pneumatic tire.
Owner:BRIDGESTONE FIRESTONE NORTH AMERICAN TIRE
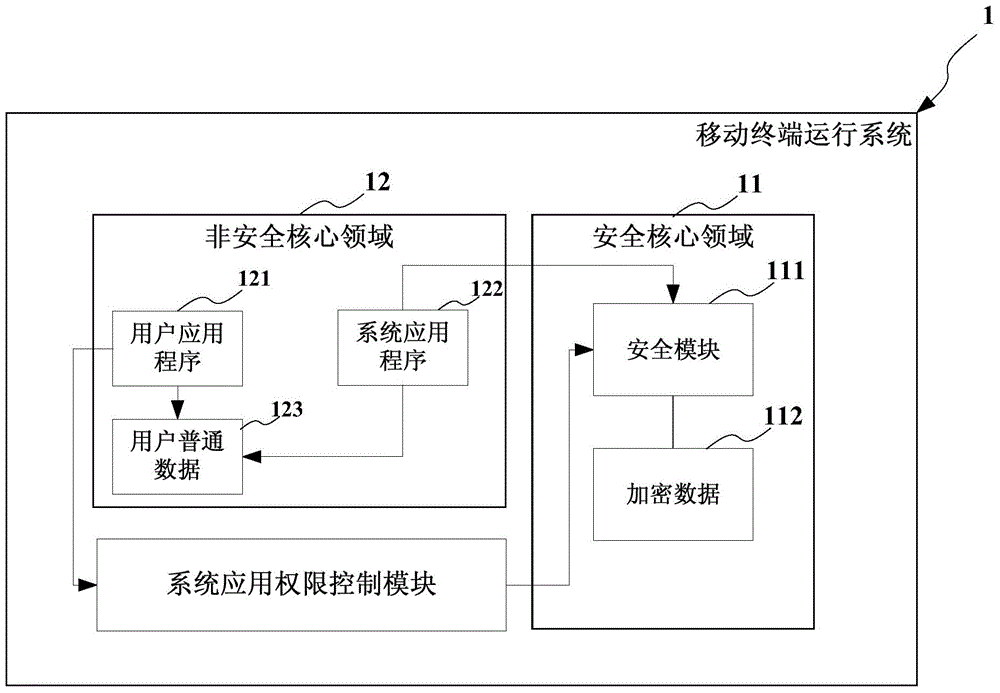
Mobile terminal and data encryption method thereof
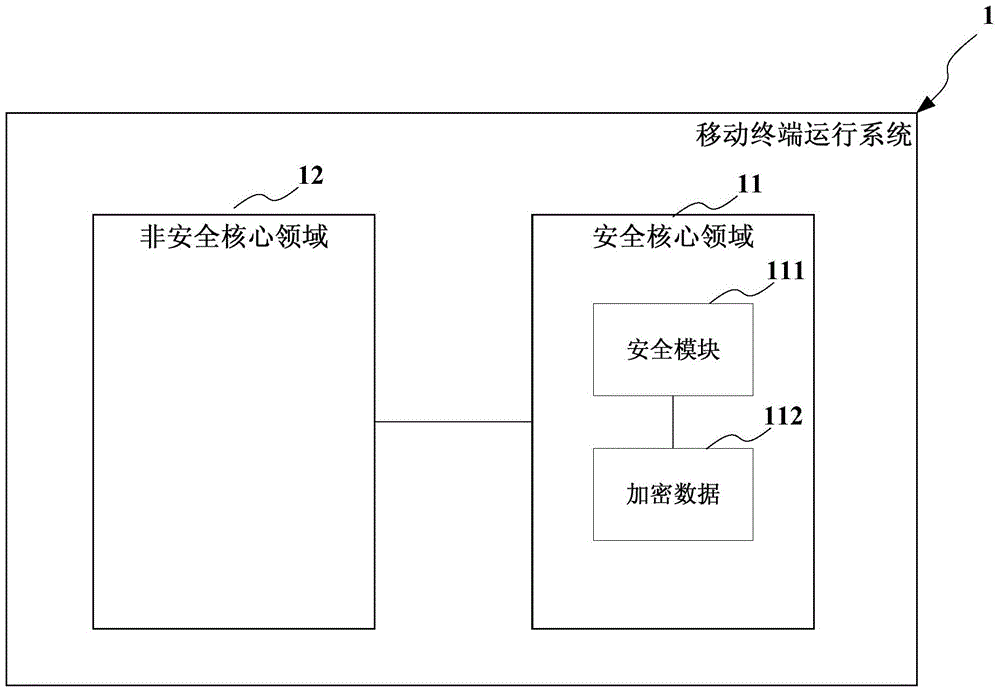
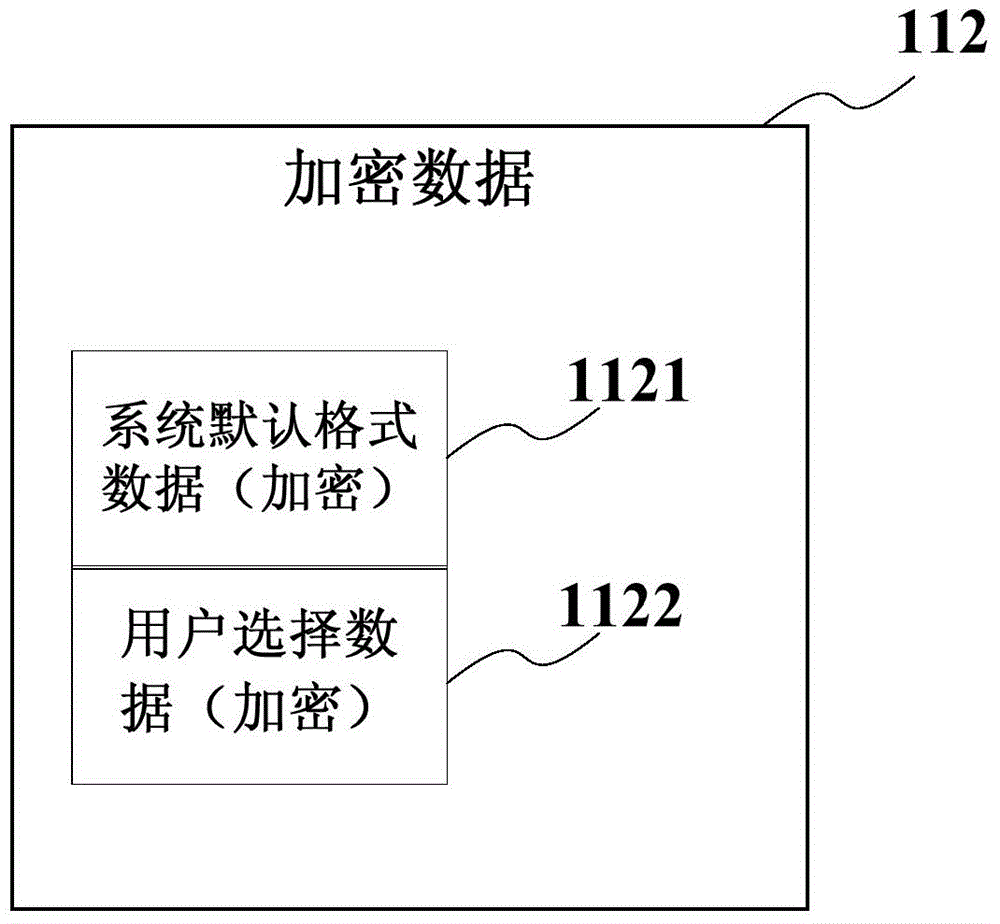
InactiveCN104463013AProtect IntegrityImprove securityDigital data protectionApplication softwareTerminal system
The invention provides a mobile terminal and the data encryption method thereof. The method comprises the following steps: setting up a security core domain in the system run by the mobile terminal, and setting up a security module in the security core domain for encrypting user sensitive data and saving the encrypted data in the security core domain, wherein the security module is used for verifying the access behavior to the encrypted data, so that only the decrypted user can access the user sensitive data, and only the application program given the security access right can access the decoded data. The mobile terminal and the data encryption method protect the integrity of the system from software and hardware levels, and improve the security of a mobile terminal system.
Owner:PHICOMM (SHANGHAI) CO LTD
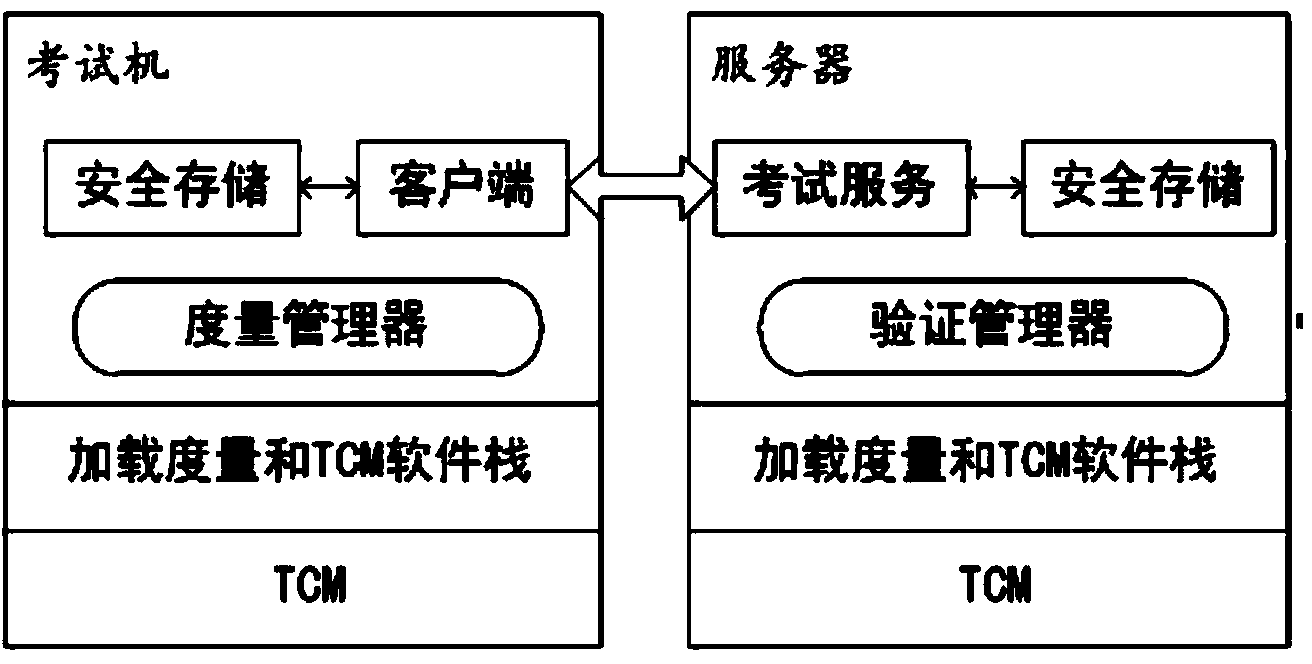
Method and system for preventing cheating during examination based on trusted computing
InactiveCN103916246AProtect IntegrityImprove integrityData processing applicationsUser identity/authority verificationClient-sideMalware
The invention discloses a method and system for preventing cheating during an examination based on trusted computing. The method and system are achieved based on a TCM credible encryption module, and security mechanisms such as credible guidance, dynamic integrality measurement, credible network connection, asymmetric encryption and decryption and digital signature verification are used. Security guarantees provided by the method and system for an examination scene include the platform security before the examination, the network connection security between a client side and a server, the security of the system environment during the examination and the like, the integrity of an examination operation system and the integrity of an examination system are protected in real time, and cheating behaviors achieved by running malicious software and the like are prevented. By the adoption of the method and system for preventing cheating during the examination based on trusted computing, answers of an examinee are prevented from being tampered on the server side due to collusion between a server administrator and the examinee.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
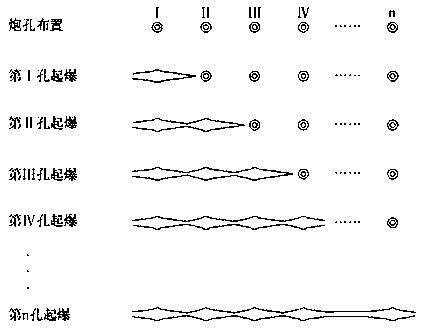
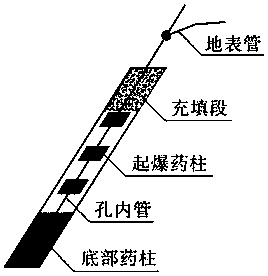
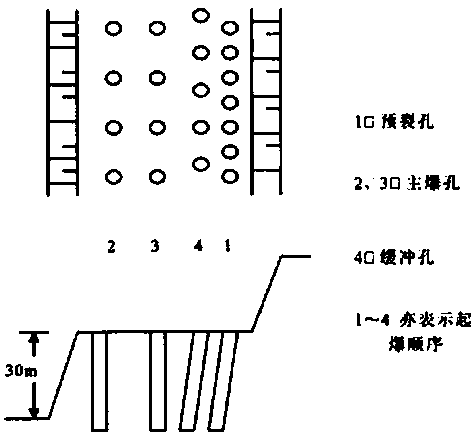
Method for open-air deep-hole bench pre-cracking hole hole-by-hole detonation pre-cracking blasting cracking in complex environment
The invention relates to a method for open-air deep-hole step pre-cracking hole hole-by-hole detonation pre-cracking blasting cracking in a complex environment, and belongs to the technical field of blasting. According to the method, pre-cracking blasting is carried out along a final boundary line and namely a design contour line of bench blasting, a pre-crack hole should be ahead of a main explosion hole for 100 ms or above to be detonated, a crack is formed through blasting in advance between the main explosion hole and a protected rock mass, after the pre-cracking crack is formed, a bufferhole explosion group and a main hole explosion group are detonated, the pre-cracking crack can reduce the blasting seismic effect of the main hole explosion group, the damage of the surrounding rock mass is slight, the integrity of the rock mass is protected, the workload is reduced, the vibration on surrounding civil houses, cultural relics and other surrounding structures is small, the disturbance on the reserved rock mass is small, the stability is good, the crack forming effect is good, a flat and smooth rock wall surface can be obtained, the overexcavation is greatly reduced, and the stability of surrounding rock is maintained.
Owner:KUNMING UNIV OF SCI & TECH +1
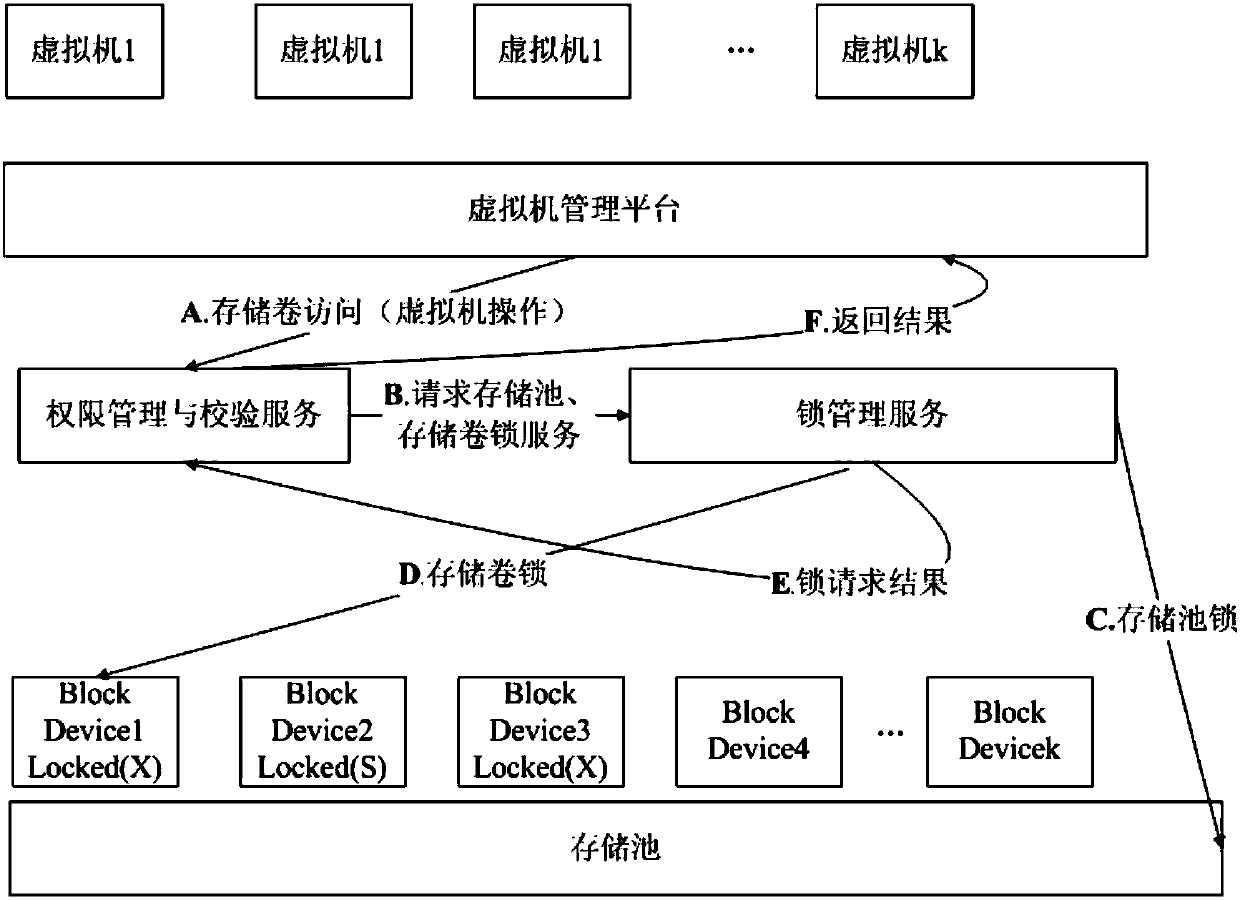
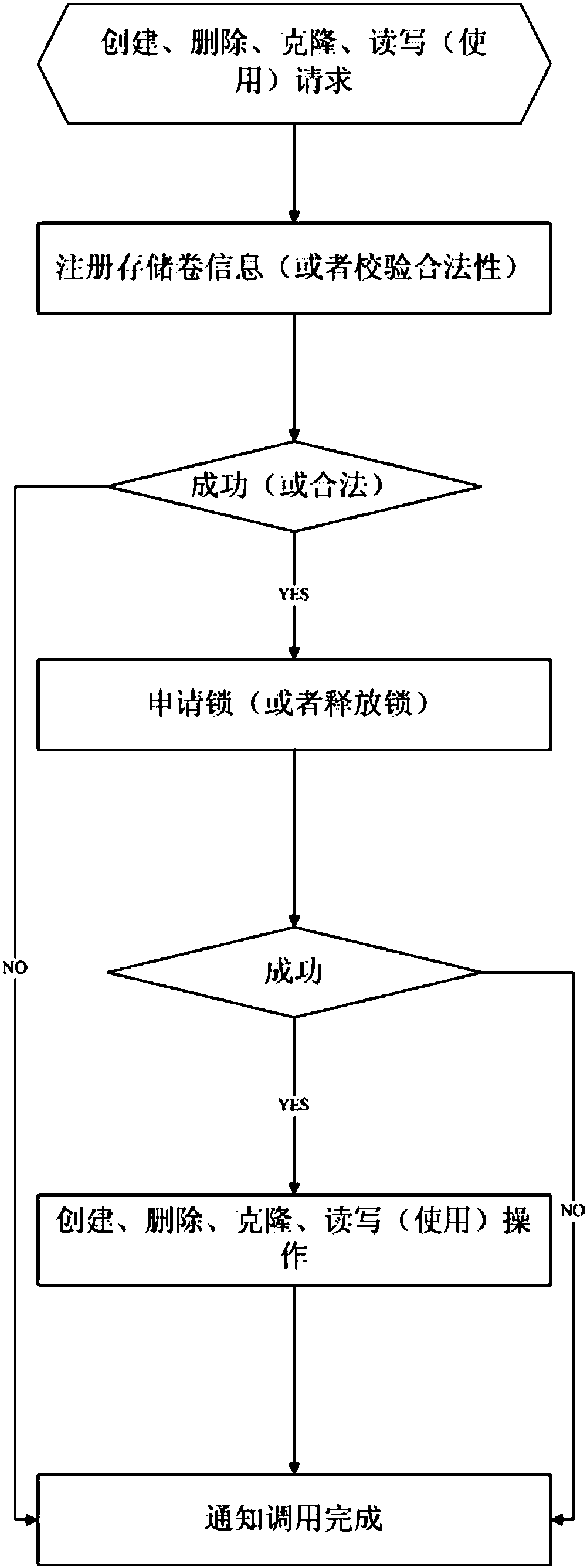
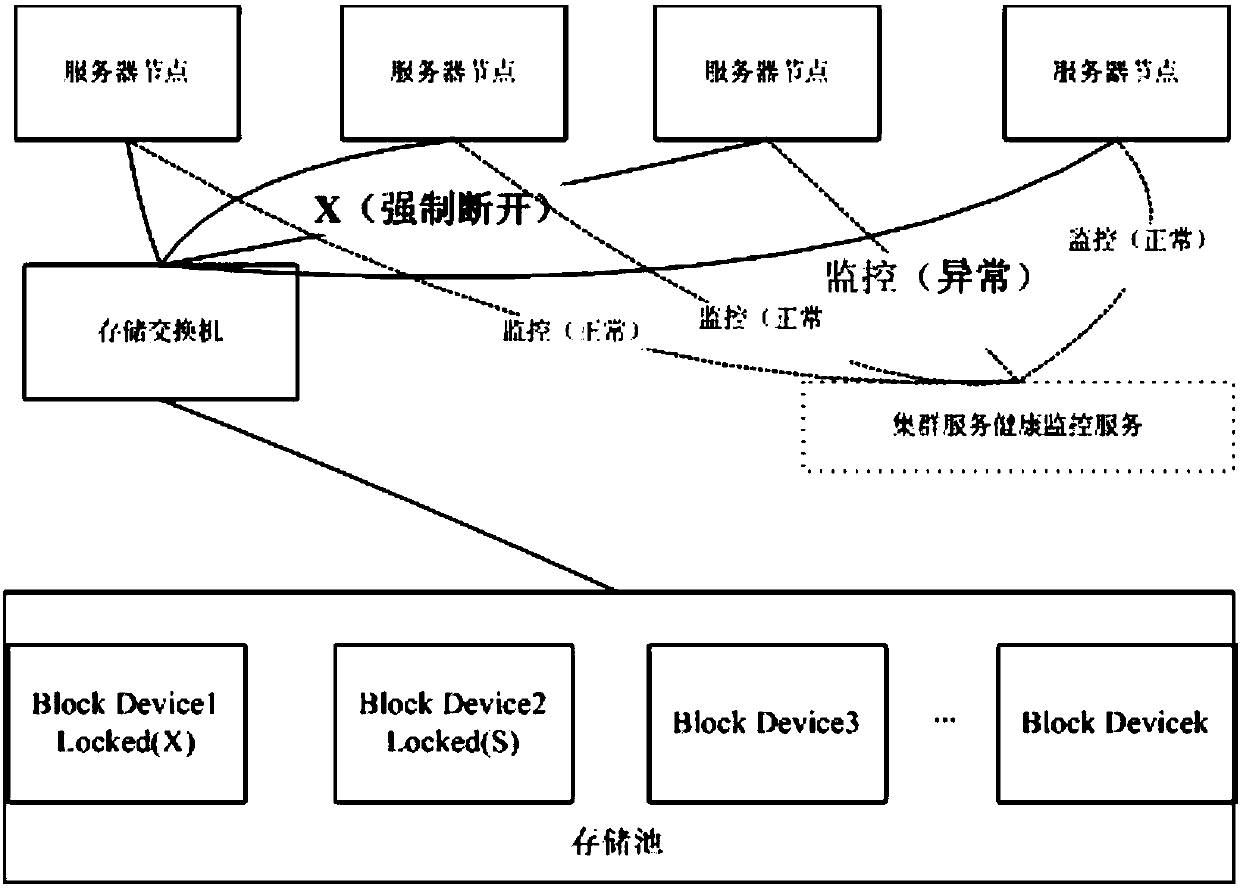
High-safety cluster sharing storage virtualization method
ActiveCN108038384APrevent unauthorized accessProtect IntegrityDigital data protectionData switching networksCluster NodeStorage security
The invention belongs to the field of virtualization and cloud computing, and particularly relates to a high-safety cluster sharing storage virtualization method. The method comprises two sub-links including the storage security access control sub-link and the storage service integrity monitoring sub-link. According to the method, through a high-safety management and monitoring mechanism, a systemcarries out virtualization management on cluster shared storage in a cluster mode; in the cluster environment, the functions of reading and writing access of shared storage data, cluster node state real-time monitoring, data protection under the conditions of faults and abnormal conditions and the like are achieved.
Owner:北京京航计算通讯研究所
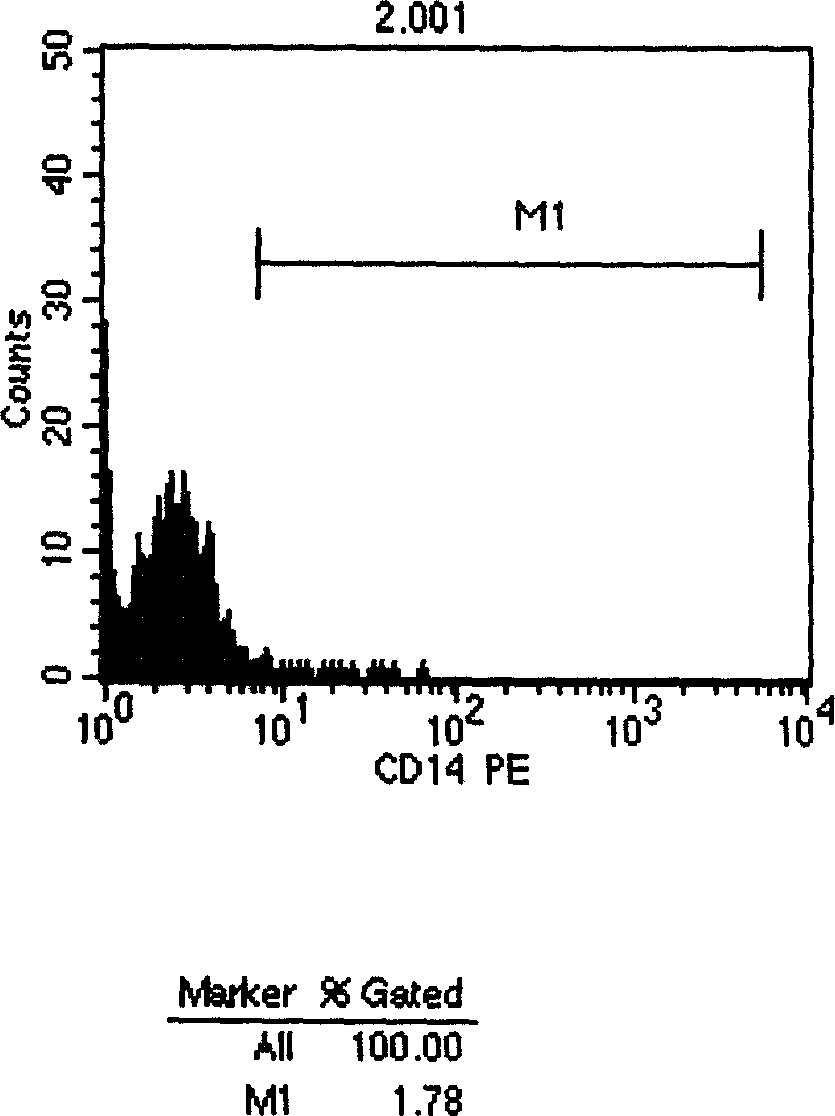
Dedicated Hemolysin for flow cytometer and preparing method and application thereof
InactiveCN1632576AProtect integrityProtection from infectionPreparing sample for investigationBiological testingBlood testWhite blood cell number
It is a process method of hemolysin in special cell device and its application, which belongs to medical test agent technique field. The hemolysin is composed of NaCI, Na#-[2] HPO#-[4]íñ12H#-[2] O, KH#-[2] PO#-[4], cavaform and double stilled water. Each component is mixed and is put in the water for four to five hours and is shaken every thirty to forty minutes and to be filtered to get the agent. The hemolysin in this invention is used as surface marks of leucocyte in blood tested by the flow cell device.
Owner:JINAN CENTER HOSPITAL
Slim hole explosion crack generation assisted hydraulic fracturing method
The invention discloses a slim hole explosion crack generation assisted hydraulic fracturing method. The method includes the following steps: firstly, windowing is carried out to side-drill a horizontal drilling well to form a long open slim hole, an explosive is put, and after the explosive explodes to impact rock, a large number of microcracks and micro-gaps are formed; secondly, perforation operation is carried out on the crack growing gaps formed by the impact of explosion pulse, slick-water is injected into perforation holes to form a main crack, the radial cracks and activated natural cracks are further opened to communicate with the main crack to form a complex crack network of main crack-branch crack, a glue solution or slick-water fracturing fluid mixed with a proppant is pumped for sanding to further extend and expand the main crack and the explosion cracks, the cracks are filled with the proppant, continuous sanding is carried out until designed sand volume is reached and then the operation is stopped. The method of the invention is simple in operation and mature in technology and can effectively improve the transformation efficiency of a deep shale gas reservoir.
Owner:CHINA PETROLEUM & CHEM CORP +1
Fail-safe control rod drive system for nuclear reactor
InactiveUS20150325318A1Protect integrityEliminate problemNuclear energy generationEmergency protection arrangementsNuclear reactorScram
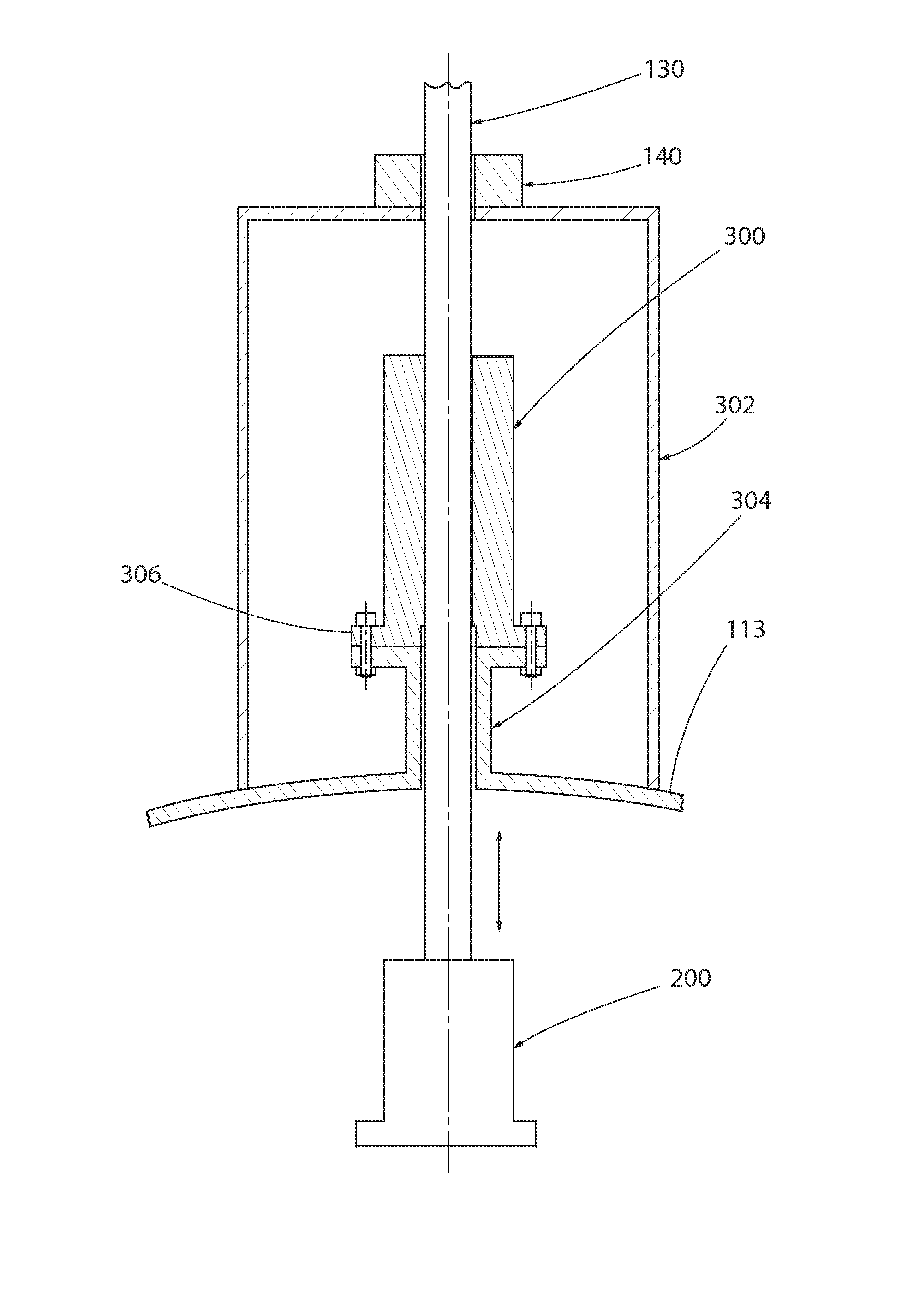
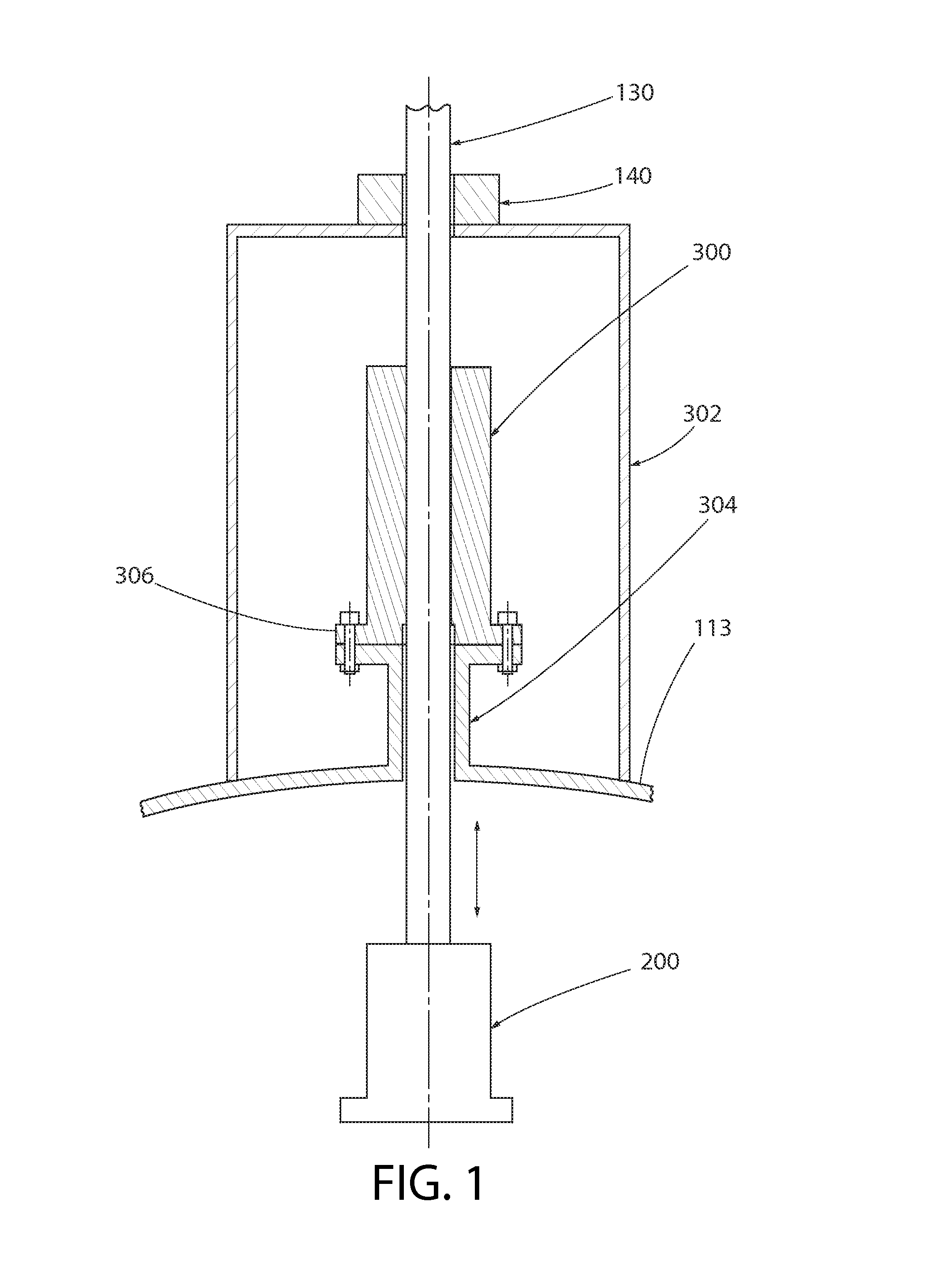
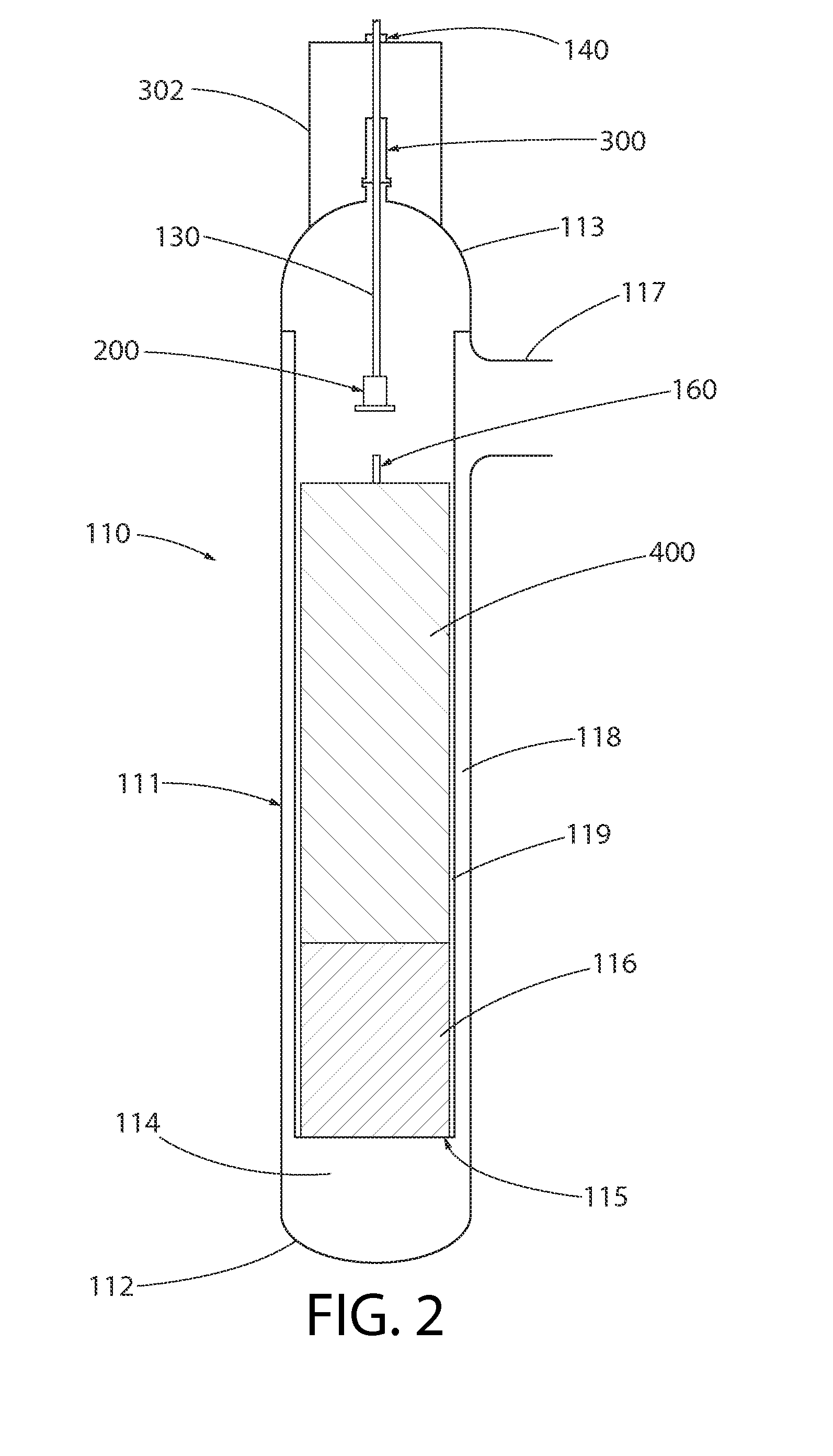
A control rod drive system (CRDS) for use in a nuclear reactor. In one embodiment, the system generally includes a drive rod mechanically coupled to a control rod drive mechanism (CRDM) operable to linearly raise and lower the drive rod along a vertical axis, a rod cluster control assembly (RCCA) comprising a plurality of control rods insertable into a nuclear fuel core, and a drive rod extension (DRE) releasably coupled at opposing ends to the drive rod and RCCA. The CRDM includes an electromagnet which operates to couple the CRDM to DRE. In the event of a power loss or SCRAM, the CRDM may be configured to remotely uncouple the RCCA from the DRE without releasing or dropping the drive rod which remains engaged with, the CRDM and in position.
Owner:SMR INVENTEC
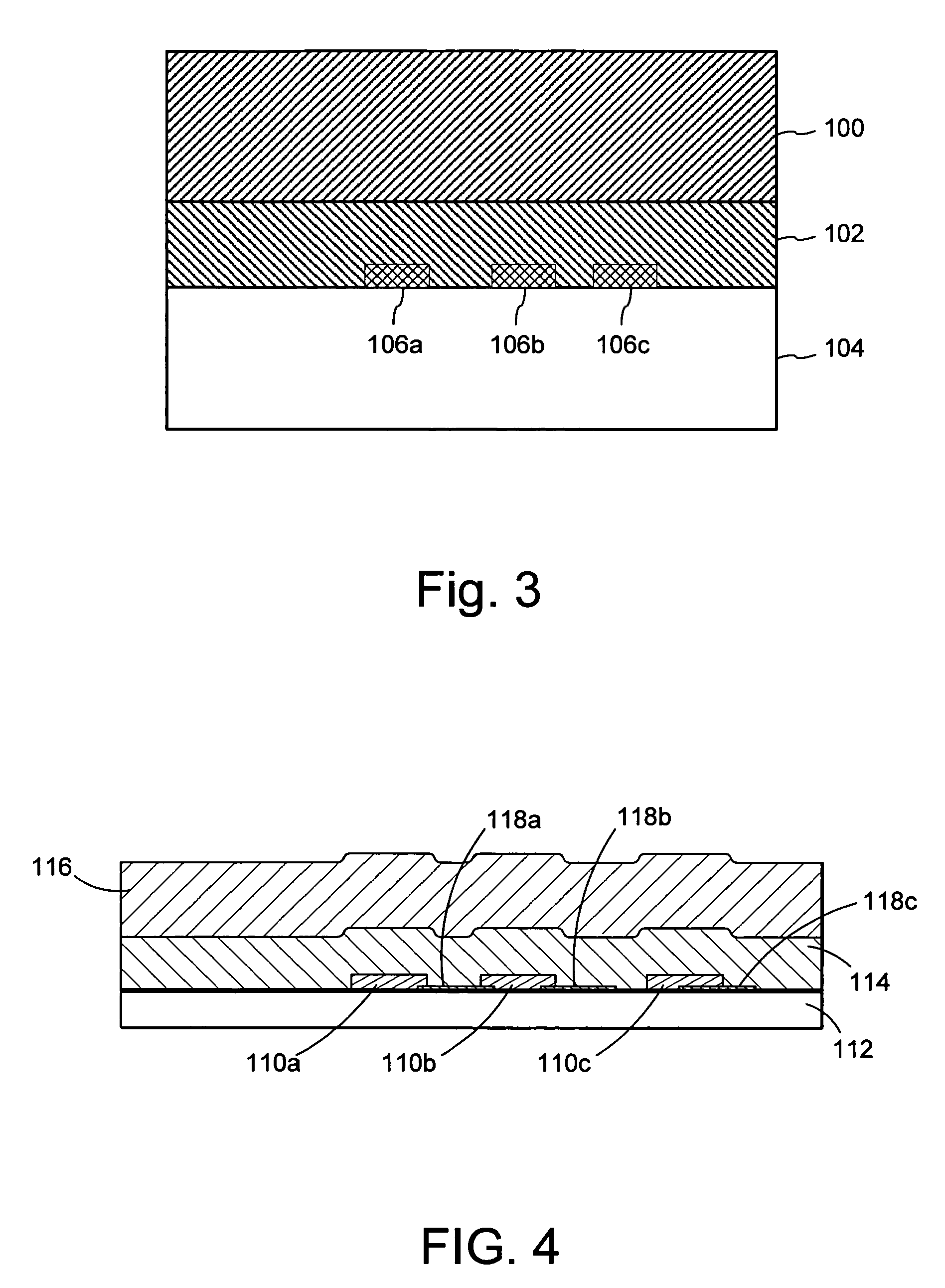
Image destruct feature used with image receiving layers in secure documents
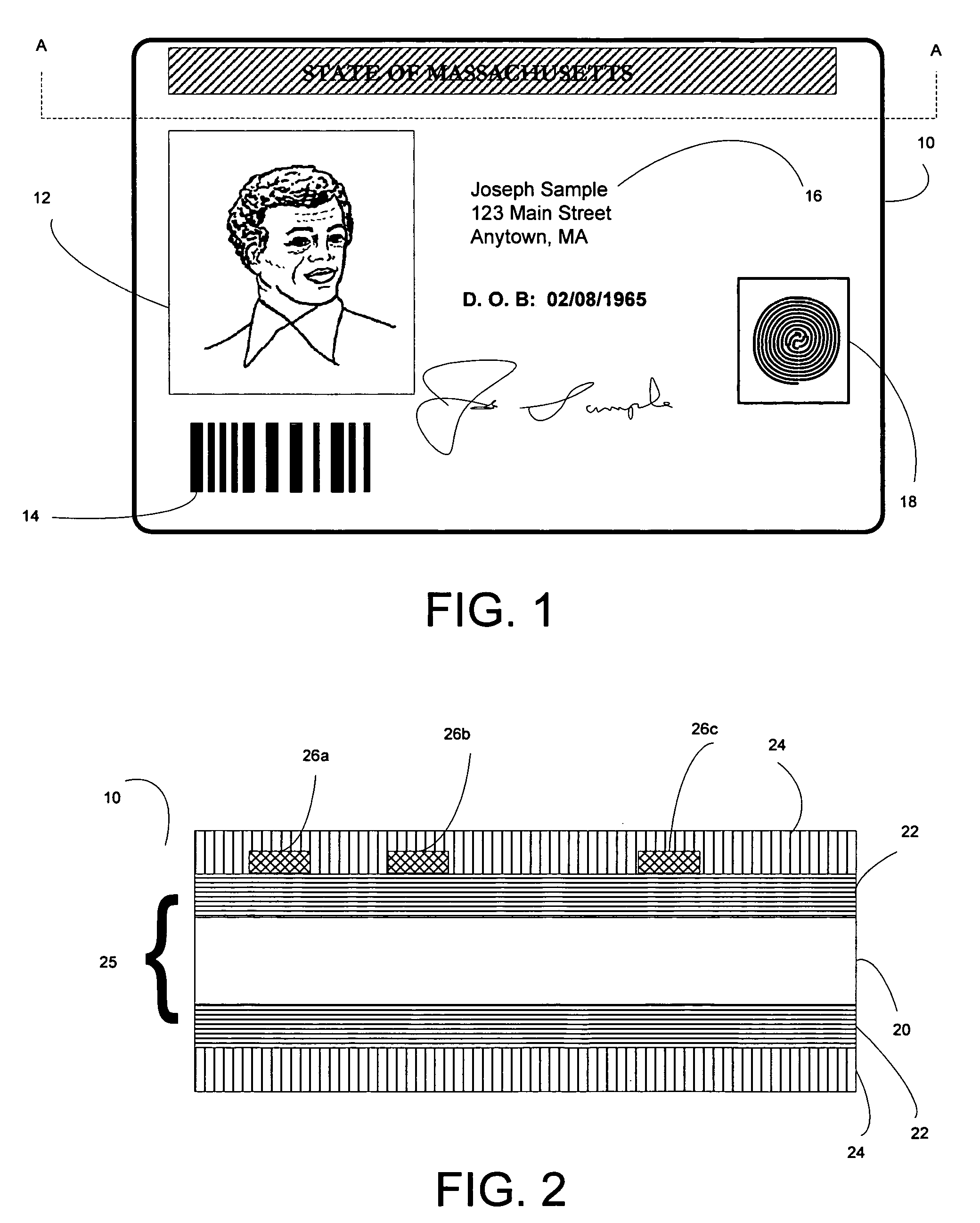
ActiveUS20060222830A1Protect integrityDifficult to separateOther printing matterDecorative surface effectsPaper documentDocument preparation
An image destruct material comprises a release layer positioned between an image receiving layer and a base layer. The adhesion between the release layer and the base layer is greater than adhesion between the release layer and the image receiving layer. The release layer material can be used in secure documents that have an image receiving layer, such as used for dye diffusion, mass transfer, ink jet, and xerographic printing. For example, particular implementations are designed for identification documents with a D2T2 image receiving layer. In these implementations, for example, the release layer is in the form of a patterned coating under the image receiving layer. After information is printed on the image receiving layer, an overlaminate is applied over it. Removal of the overlaminate destroys the printed image on the receiving layer because the relative adhesive properties of the image receiving layer, overlaminate and release layer cause the image to release with the overlaminate at the locations of the coating whereas the remainder of the image remains with the base layer.
Owner:L 1 SECURE CREDENTIALING
Rock-like sample discharging device for conventional triaxial test and use method
InactiveCN106769402AProtect IntegrityEasy to operateMaterial strength using tensile/compressive forcesSteel platesSteel columns
The invention provides a rock-like sample discharging device for a conventional triaxial test and a use method, and belongs to the field of geotechnical engineering tests. The rock-like sample discharging device comprises a vertical frame, a pressing column, a protection barrel, a base plate and fixers, wherein the vertical frame comprises a steel ring, a fixed frame and a supporting rod; the vertical frame is inserted into an insertion slot of the base plate; the pressing column is a steel column with a hard rubber pressing pad at the front end; the protection barrel is a rubber protection barrel with a closed bottom end; the base plate is a steel plate with the insertion slot; the fixers are plugged into screw holes of the fixed frame. Furthermore, the invention further provides the use method of the device. The device disclosed by the invention is simple in structure and convenient to use; the device can effectively protect the extraction intactness of a broken test sample.
Owner:HOHAI UNIV
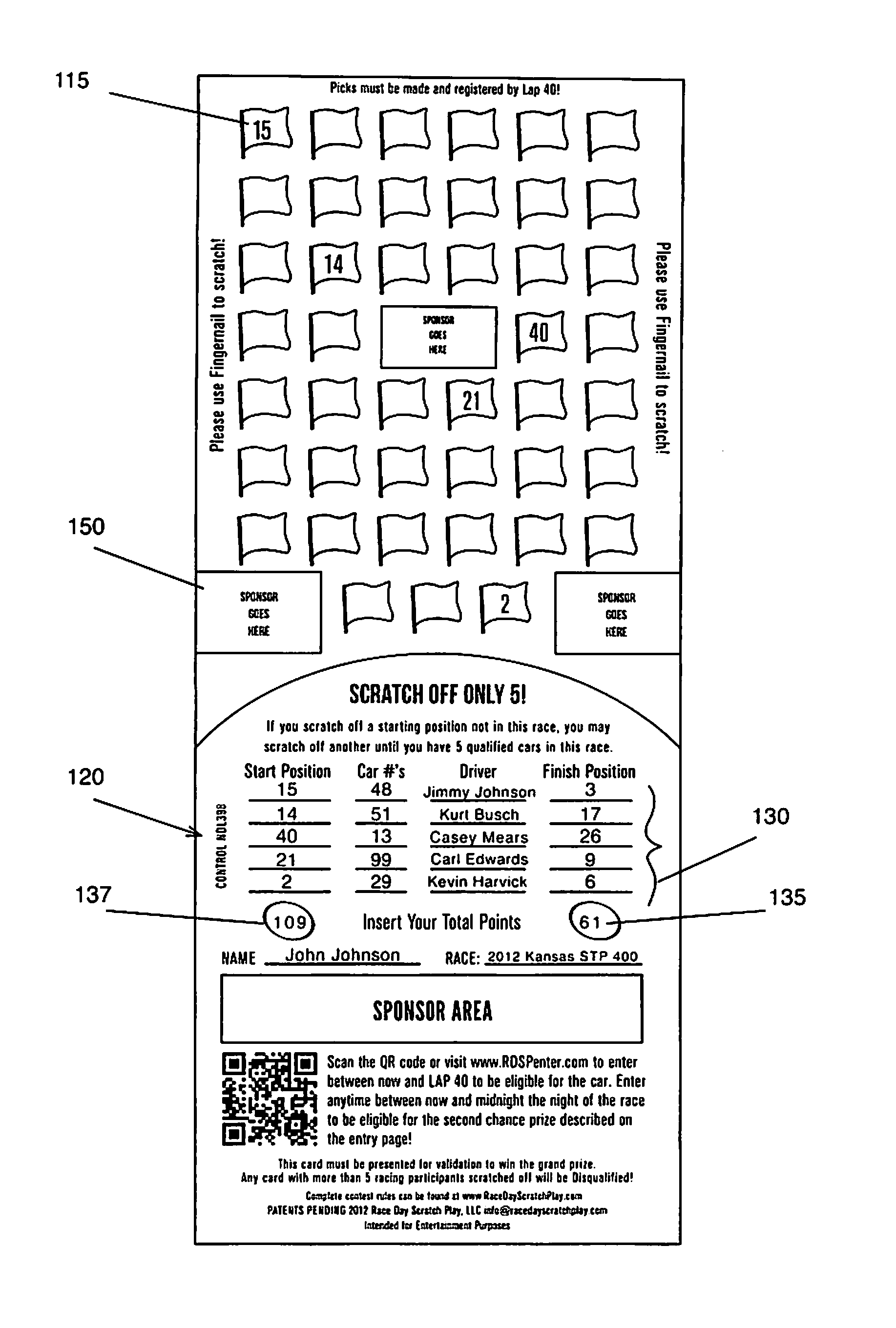
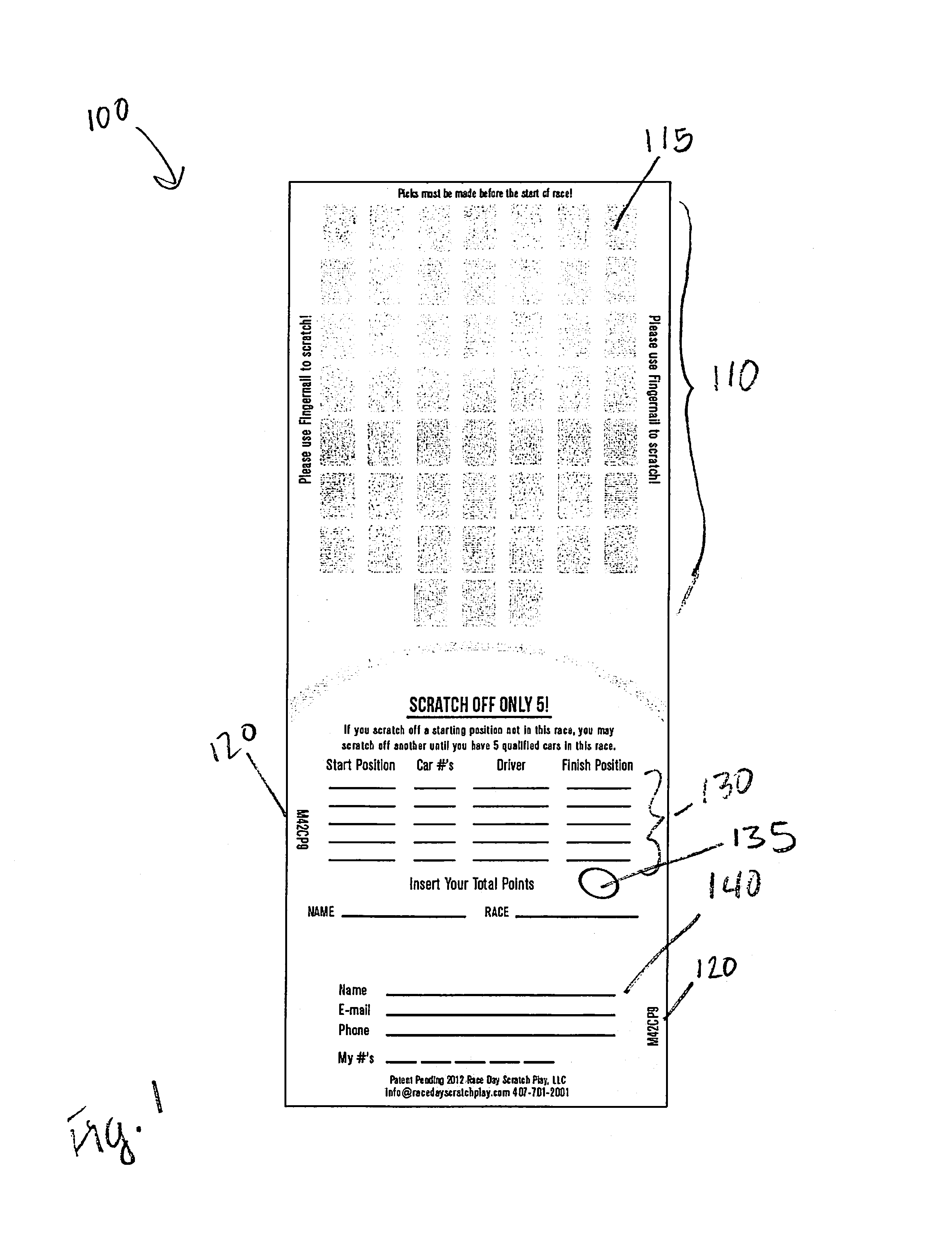
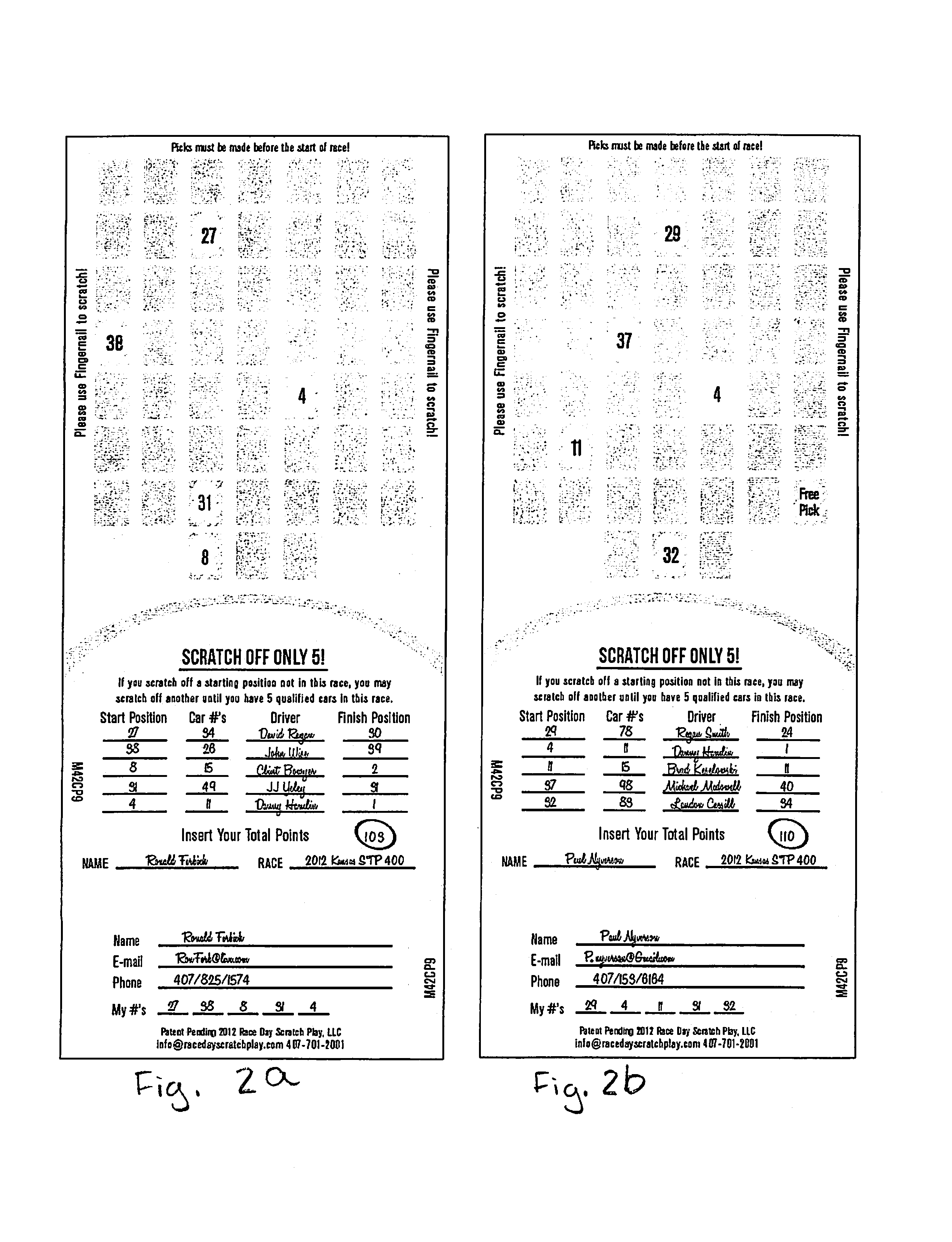
Race day scratch play game, game card and method of playing
InactiveUS8820744B1Protect integrityIncrease opportunitiesBoard gamesCard gamesOperations researchPosition Number
Scratch-off game cards, systems and methods of play for pre-picking winners of real-time sporting events before events take place. Each player scratches off a number of scratch-off portions from scratch off sheets to determine teams picked before the sporting event begins. Players list selected racing teams and start positions on cards before events begin. After the event concludes, players list final position numbers for the teams. Players sum up their initial position numbers to determine initial position sum scores, and players sum up their finish position numbers to determine finish position scores. The player with the lowest initial and or final position sum score wins game. Optionally, the player with the winner of the race on the player's game card wins another portion of the game. In the case of a sponsored race, the rules and method of play can vary.
Owner:RACE DAY SCRATCH PLAY
Compound aloe health-care tablet
InactiveCN1559605AImprove human immunityProtect integrityMetabolism disorderDigestive systemDetoxicationUlcer care
A health-care compound aloe tablet for moistening intastine, detoxication, decreasing blood fat, regulating immunity, and reducing the influence from radiation, smoking, wine, etc contains aloe extract, glutathion, VC and auxiliary.
Owner:方芳
Method and system for protecting integrity of host based on self-checking mechanism
InactiveCN110197073AProtect IntegrityImprove securityPlatform integrity maintainanceSelf checkingComputer hardware
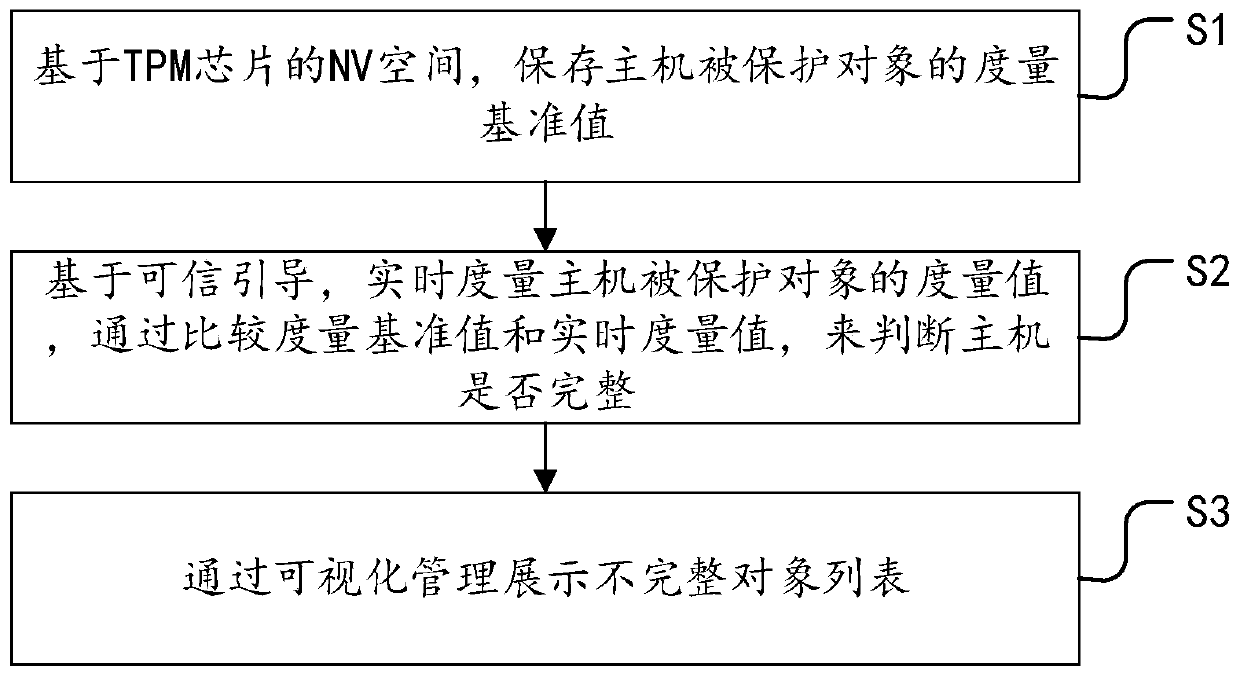
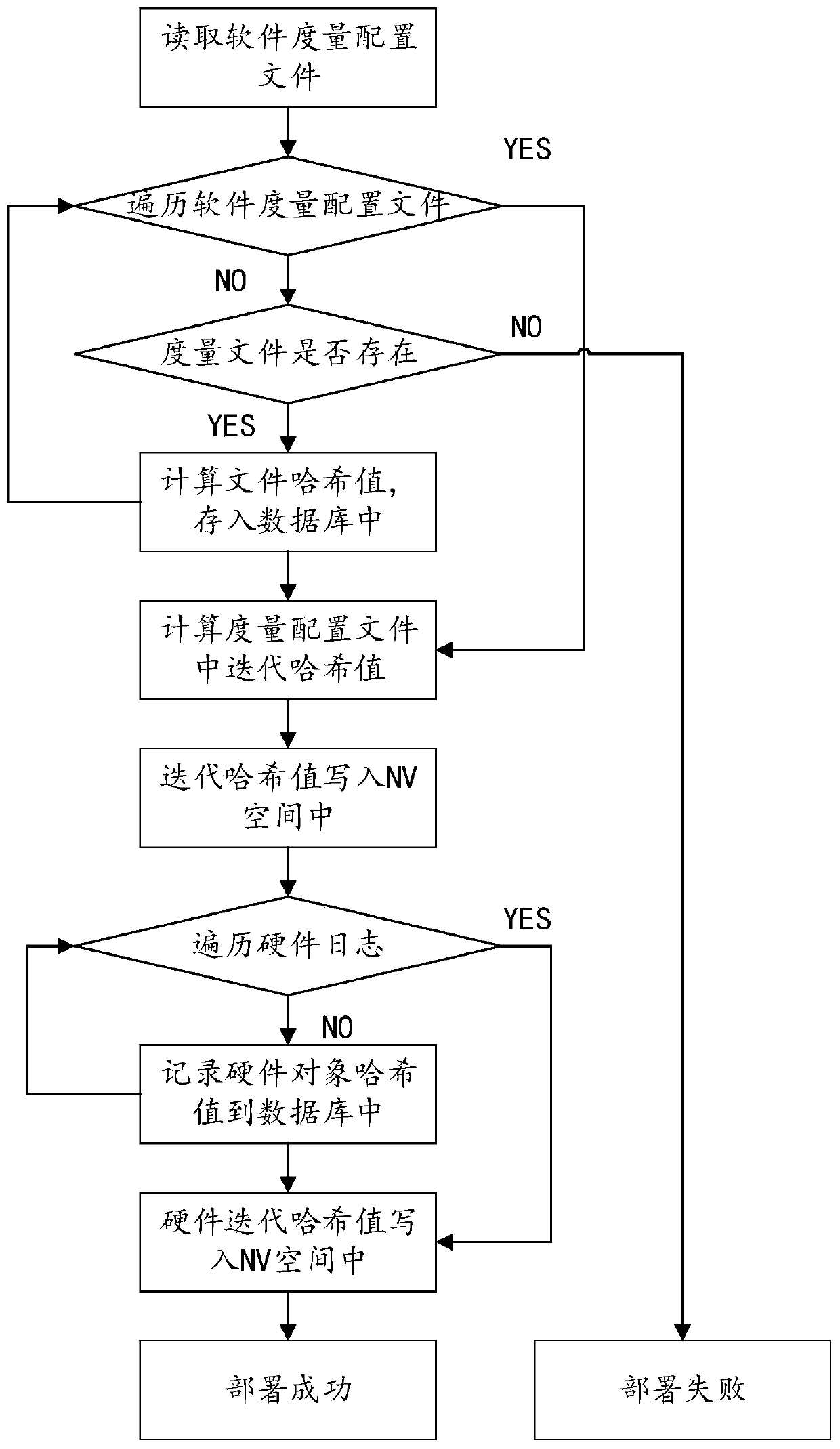
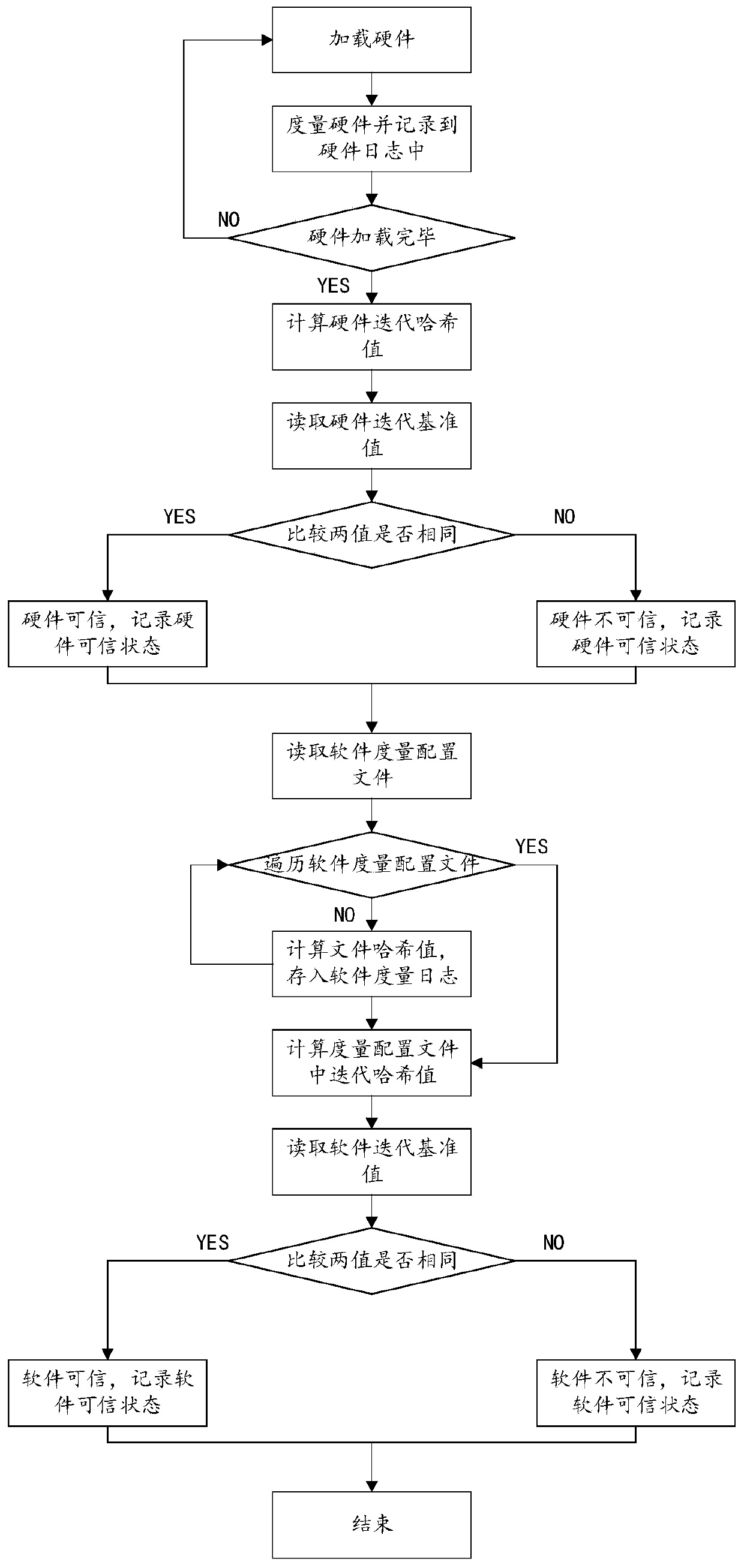
The invention provides a method and a system for protecting the integrity of a host based on a self-checking mechanism. Based on an integrity measurement technology in trusted computing, the measurement reference value of the protected object is stored into an NV space in a TPM chip of a host; hardware and software of a host in the starting process of the host are measured in real time through trusted guidance, the real-time measurement value of a protected object is obtained, the integrity state of the host is judged by comparing a measurement reference value with the real-time measurement value, an incomplete object list is found based on an integrity report, and safe visual management is provided. According to the self-checking mechanism, the integrity of the host can be protected basedon an integrity measurement technology in a trusted computing system without a remote challenge party and a privacy PCA, the security of the host is improved, and the security of hardware and software of the host can be conveniently protected.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Fish-skin collagen peptide compound product capable of enhancing immunity and preparation method of fish-skin collagen peptide compound product
ActiveCN104041830AImprove product qualityProtect IntegrityFood ingredient functionsFood preparationPeptideSolubility
The invention relates to a fish-skin collagen peptide compound product capable of enhancing the immunity and a preparation method of the fish-skin collagen peptide compound product. The fish-skin collagen peptide compound product consists of the following ingredients by weight percent: 40 to 70 percent of deep sea fish-skin collagen peptide, 2 to 12 percent of a ginseng extract, 2 to 12 percent of cordyceps militaris and 15 to 40 percent of a filler. The fish-skin collagen peptide compound product has the advantages that the ocean polypeptide is combined with traditional Chinese herb extract polysaccharide, all the components supplement, the effect for enhancing the immunity is good, the product solubility and stability are good, the taste is good, and the convenience in taking is realized.
Owner:青岛琛蓝生物营养技术有限公司
System-level packaging process for radio frequency chip
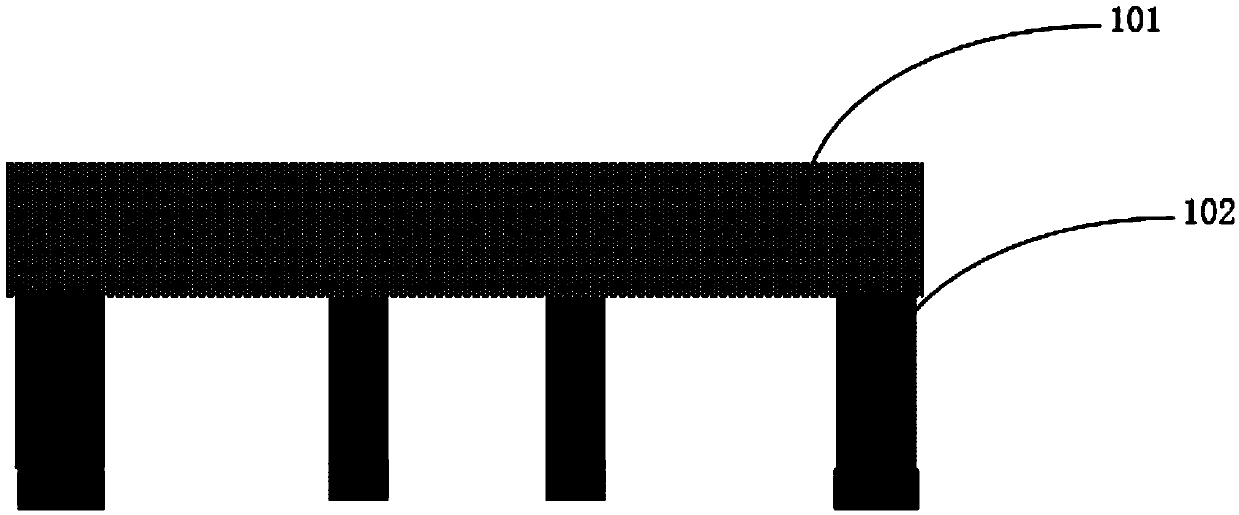
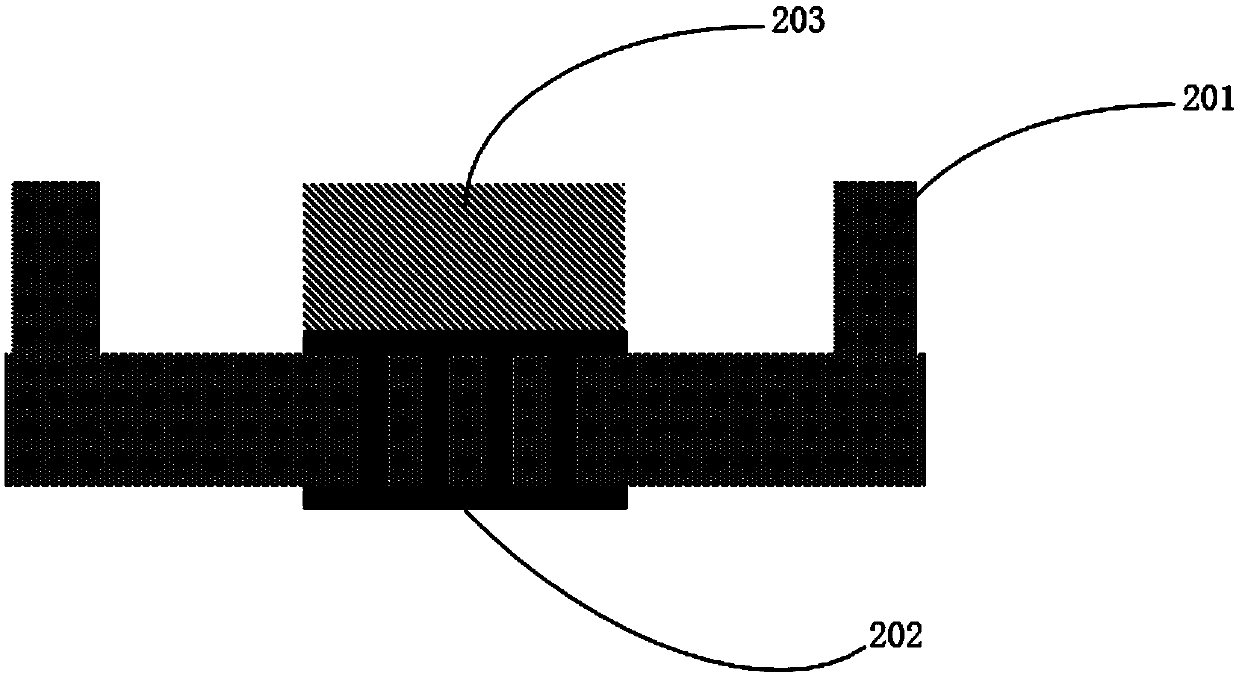
ActiveCN110010502ASimple processProtect IntegritySemiconductor/solid-state device detailsSolid-state devicesRadio frequencyHigh frequency
The invention discloses a system-level packaging process for a radio frequency chip. The process comprises the following steps of (101) base processing, (102) cover plate processing, and (103) packaging. The present invention provides the system-level packaging process for the radio frequency chip, different structures are separately made on different adapter boards, the process is simplified, andthe integrity of a high-frequency signal is protected.
Owner:浙江集迈科微电子有限公司
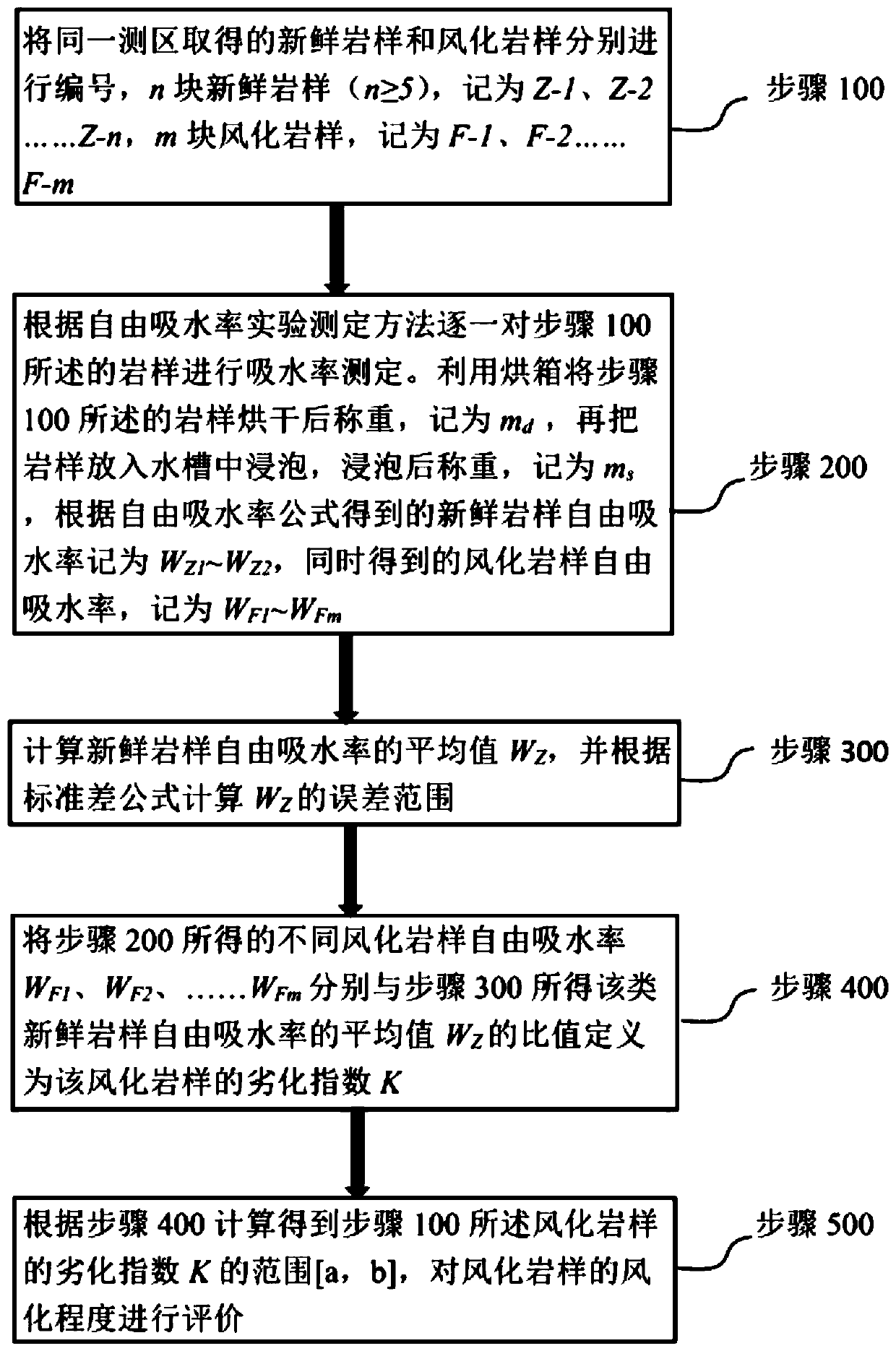
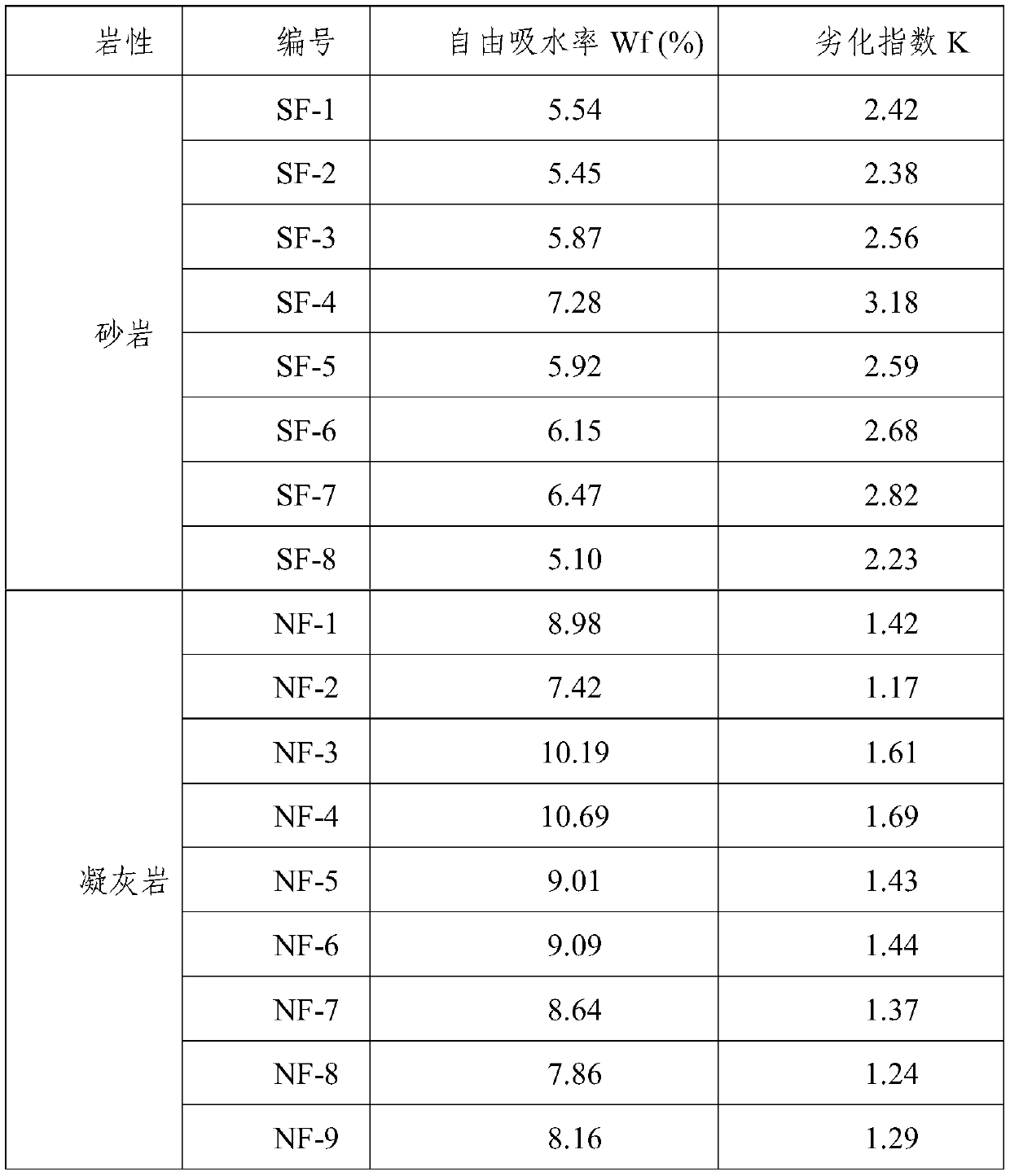
Method for quickly evaluating weathering degree of stone cultural relics
InactiveCN110927000AProtect IntegrityEasy to getWeighing by absorbing componentChemistrySoil science
The invention discloses a method for quickly evaluating the weathering degree of stone cultural relics. The method comprises the following steps: drying and weighing a weathered rock sample and a fresh rock sample in a drying oven; soaking the rock sample in water and weighing, and calculating the free water absorption rate of the rock sample; defining the ratio of the free water absorption of theweathered rock sample to the average value of the free water absorption of the fresh rock sample as the degradation index of the weathered rock sample; and determining the weathering degree grade ofthe weathered rock sample according to the degradation index range. The method is convenient to operate, and a quick, accurate and quantitative evaluation method for the weathering degree of the stonecultural relics is provided.
Owner:CHINA UNIV OF GEOSCIENCES (BEIJING)
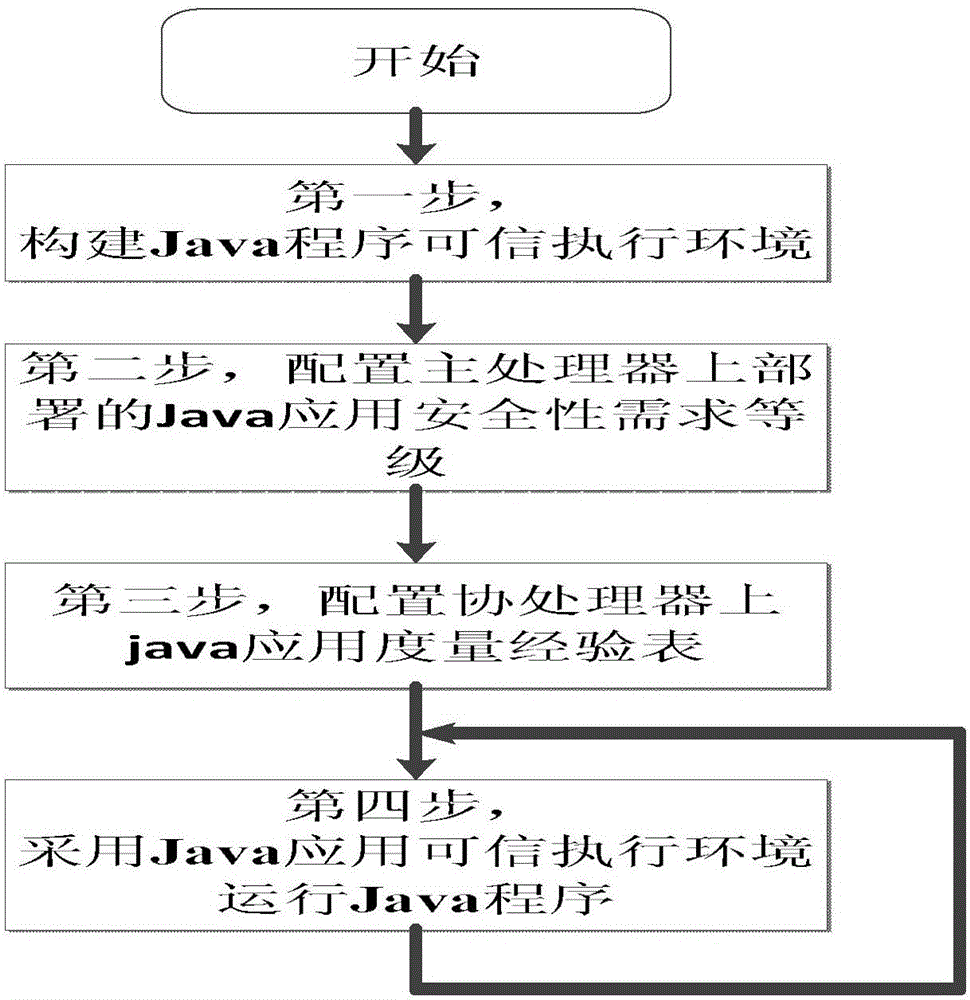
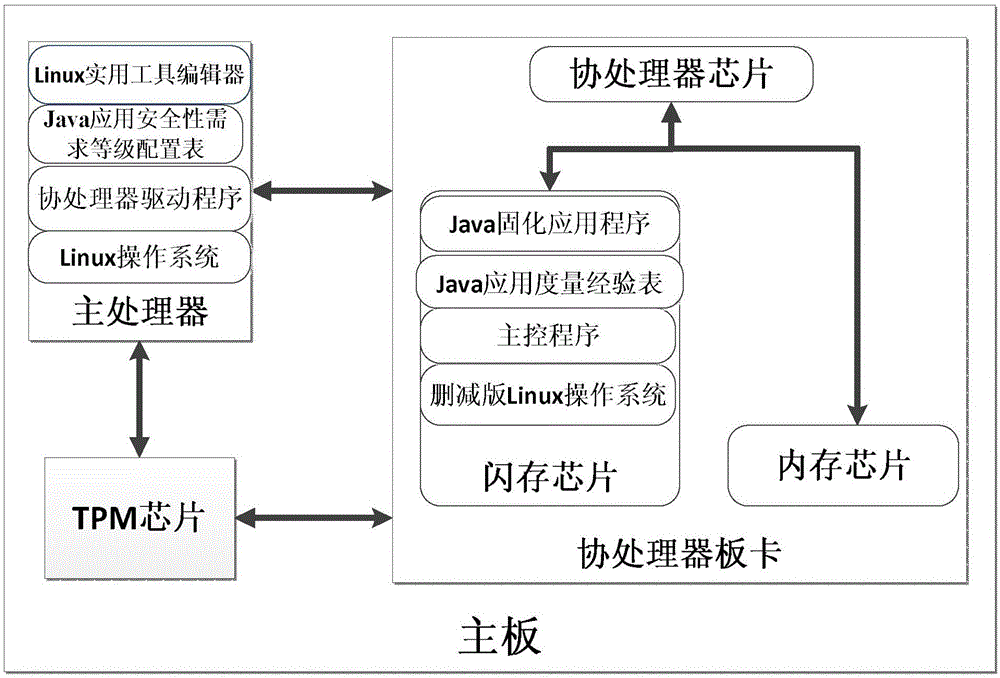
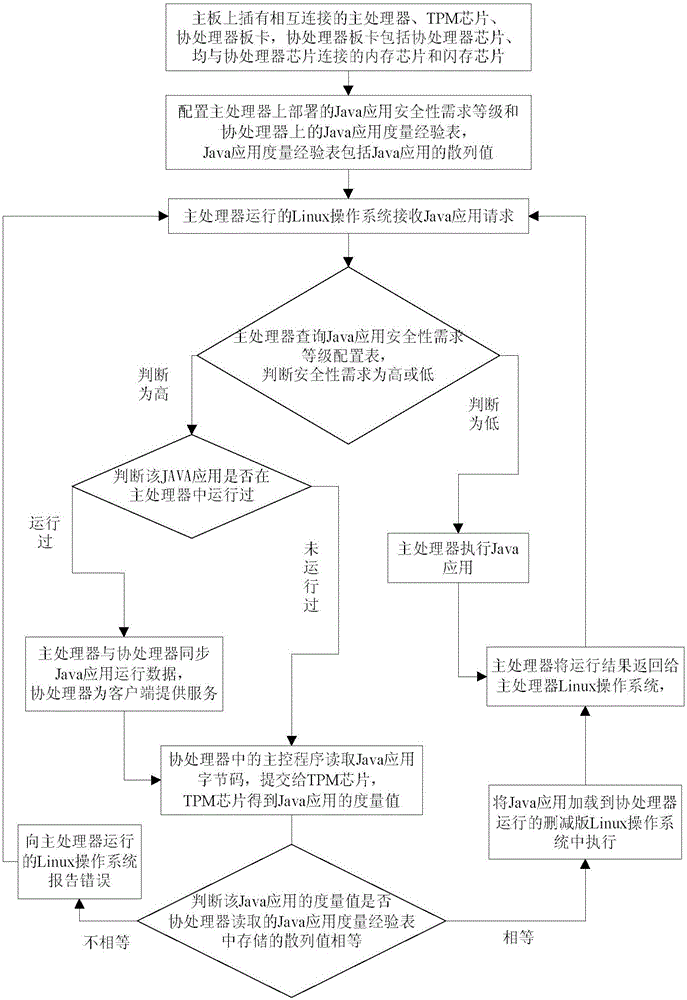
Construction method and system for Java program trusted execution environment
ActiveCN106778249AProtect IntegrityImprove securityPlatform integrity maintainanceMeasurement and VerificationApplication software
The invention provides a construction method for a Java program trusted execution environment. The method comprises the steps that a coprocessor board card is constructed, and the coprocessor board card is connected with a mainboard, wherein the coprocessor comprises a coprocessor chip, a memory chip and a flash chip; a main processor and a TPM chip are inserted into the mainboard, and the main processor, the coprocessor board card and the TPM chip are mutually connected; a person fills the security requirement level of each Java application in a Java application security requirement level configuration table, wherein the Java application name and hash value are written into a Java application measurement experience table of the coprocessor board card flash chip, and processing is conducted separately according to the security level. Accordingly, the Java trusted execution environment is constructed under the support of the TPM chip and the coprocessor board card, a high security Java application is executed in an isolated mode in a coprocessor transparent to a user, measurement and verification are conducted on a coprocessor drive program and a Java application program through the TPM chip, and the security of executing the Java application is greatly strengthened.
Owner:湖南文盾智链科技有限公司
Mouse-tail DNA (deoxyribose nucleic acid) extraction kit applicable to the genotype of laboratory mouse and application thereof
ActiveCN102329791ASimplify the routine extraction processProtect IntegrityMicrobiological testing/measurementDNA preparationDeoxyriboseProteases
The invention discloses a simple, economic and reliable mouse-tail DNA (deoxyribose nucleic acid) extraction kit, which is applicable to accurate identification of the genotype of a laboratory mouse. The kit comprises liquid A and liquid B, wherein the liquid A consists of NaOH solution with the final concentration being 0.025N and EDTA (ethylene diamine tetraacetic acid) solution with the final concentration being 2mM; and the liquid B is Tris solution with the final concentration being 40mM and pH being 7.6. The application of the kit comprises the following steps of: taking 0.2-0.5cm tissue of the tail tip of the mouse, and putting the tail tip into a 1.5ml EP (eppendorf) tube; adding 180muml of liquid A, and putting the EP tube in a trace thermostat with the temperature being 100 DEG C for 30 minutes; and then carrying out ice bath for 2 minutes, then adding 180mul of liquid B, fully mixing to be uniform, and obtaining the tissue DNA which can be used for genotype identification in the next step. In the kit, the preparation method is simple, the components of the liquid A and the liquid B are conventional biochemical reagents respectively, the whole process does not need the reagents such as protease K, phenol / chloroform and the like to participate in and does not have fuzzy steps such as multiple centrifugation and the like as well, and the operation time is not more than1 hour, so that the invention has the advantages of fastness, economy and high cost performance, and is especially suitable for being used in laboratories for identifying the mouse genotype in a long-term, numerous and frequent manner.
Owner:THE THIRD AFFILIATED HOSPITAL OF THIRD MILITARY MEDICAL UNIV OF PLA
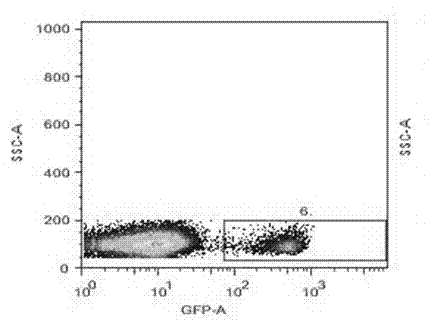
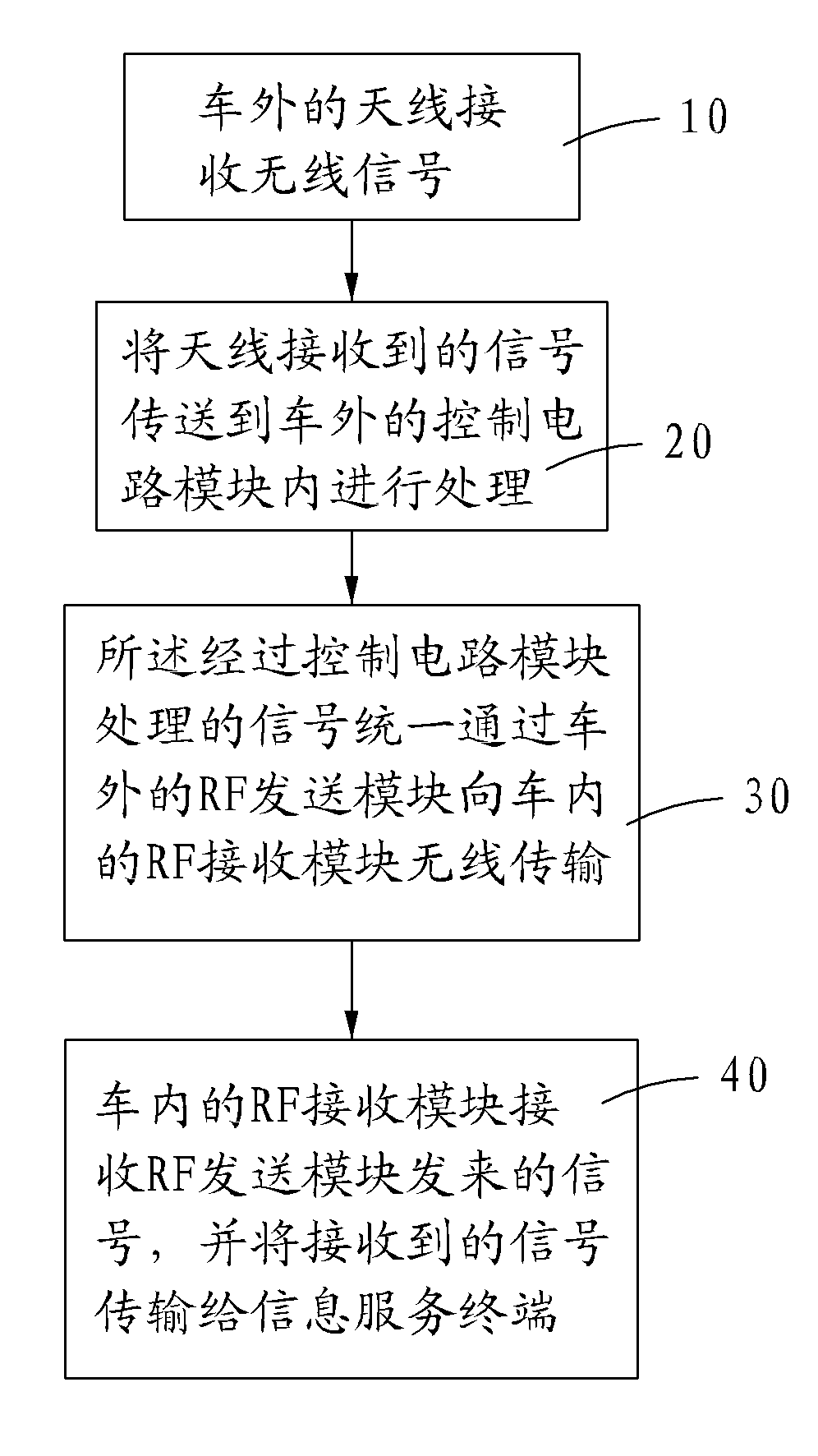
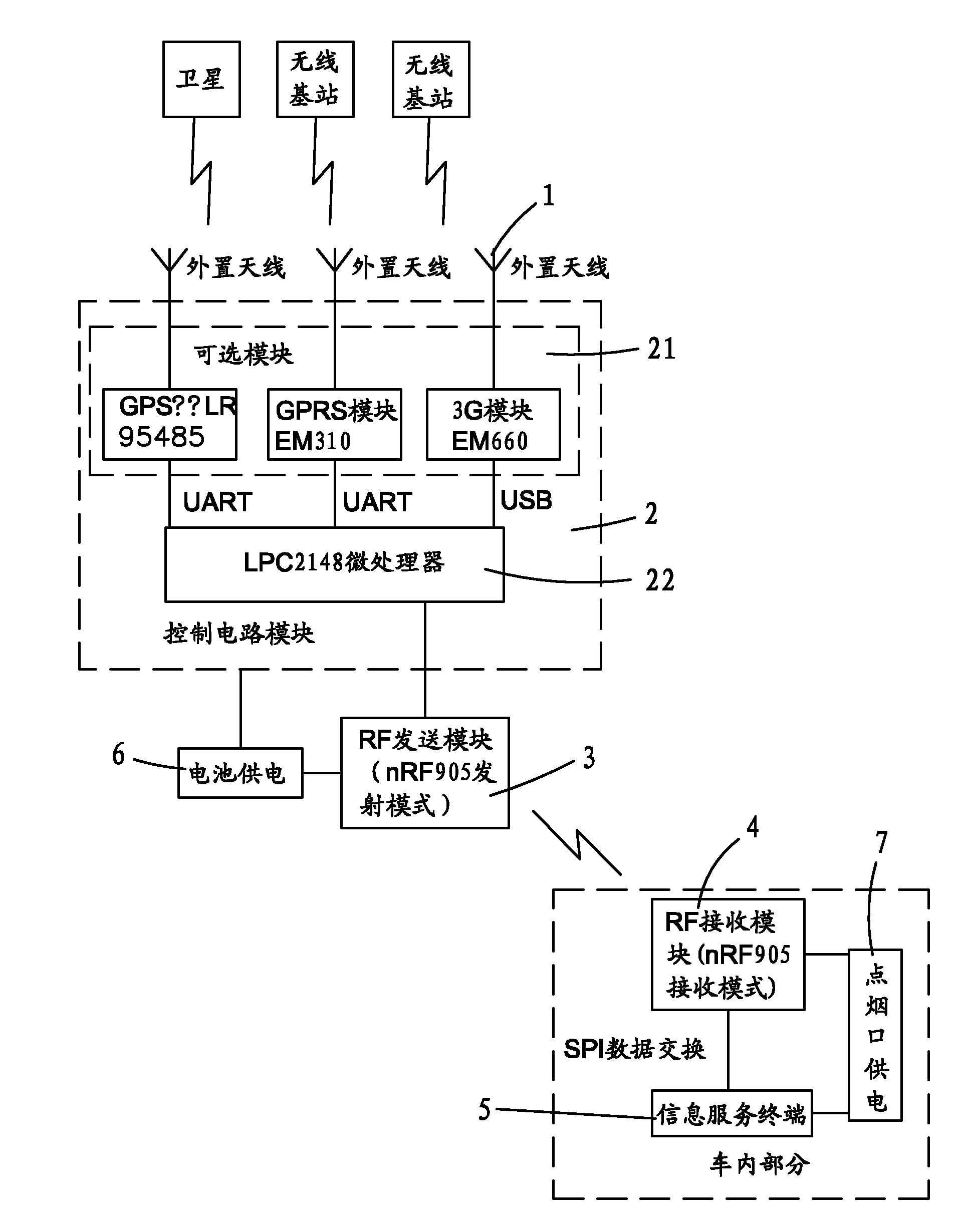
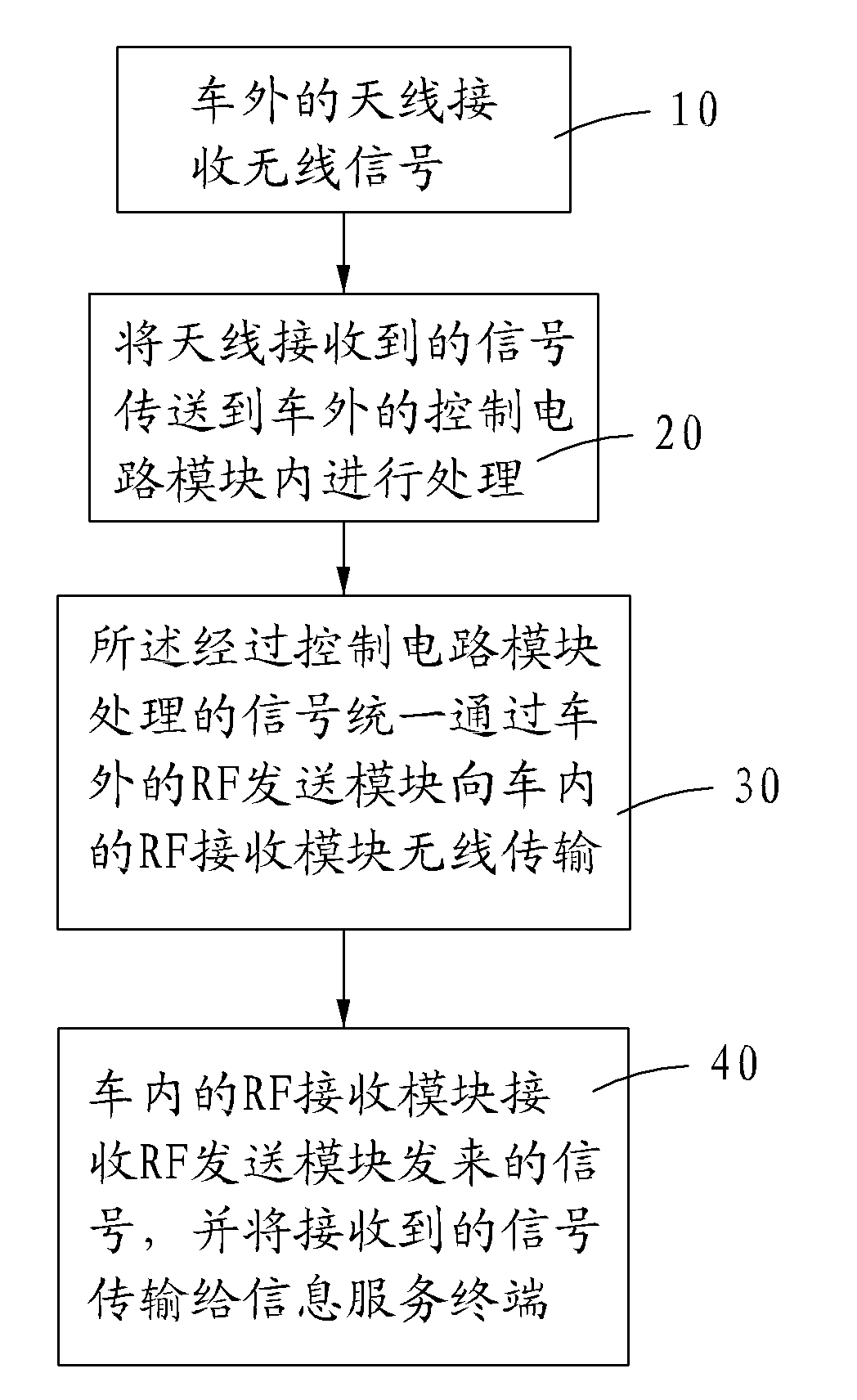
Signal receiving method of vehicle-mounted antenna
The invention provides a signal receiving method of a vehicle-mounted antenna, which concretely comprises the following steps of: a step 10: receiving a radio signal by an antenna outside a vehicle; a step 20: conveying the signal received from the antenna into a control circuit module outside the vehicle for processing; a step 30: uniformly transmitting a signal processed by the control circuit module to a RF (Radio Frequency) receiving module in a vehicle through an RF sending module outside the vehicle; and a step 40: receiving the signal sent by the RF sending module by the RF receiving module in the vehicle and transmitting the received signal to an information service terminal. The method can avoid wire connection of external antennas, the signals are stable, multi-channel signals are received according to demands and the signals are made to pass through the vehicle so that the whole vehicle is covered by the information.
Owner:FUJIAN UNIV OF TECH
Microecological traditional Chinese medicine preparation for prevention and control of chicken coccidiosis and preparation method thereof
InactiveCN105233275AProtect IntegrityEnhance immune functionPeptide/protein ingredientsBacteria material medical ingredientsLactobacillus acidophilusHerb
The invention relates to a pharmaceutical composition for prevention and control of chicken coccidiosis and a preparation method of the pharmaceutical composition for prevention and control of chicken coccidiosis. The pharmaceutical composition comprises active Chinese herbal medicinal ingredients, probiotics and glucose oxidase; the active Chinese herbal medicinal ingredients are composed of radix dichroae, radix sophorae flavescentis, sweet wormwood herb, radix astragali and angelica sinensis; the probiotics include one or more of saccharomycetes, lactobacillus acidophilus, lactobacillus plantarum, bacillus subtilis and bacillus licheniformis. The pharmaceutical composition is applicable to control of chicken coccidiosis and has the advantages of accurate curative effects, preparation stability, simplicity and feasibility in process and suitableness for industrial production.
Owner:RINGPU TIANJIN BIOLOGICAL PHARMA
Practical electromagnetic hot pot table
The present invention relates to a practical electromagnetic hotpot table, which comprises a tabletop board and a supporting table cabinet. The central position of the tabletop board is located on the supporting table cabinet. A hollow groove is arranged inside the supporting table cabinet, and the tabletop board corresponds to the hollow groove. A port is opened; a hot pot and an electromagnetic heating furnace are arranged sequentially from top to bottom in the hollow tank; the hot pot is placed on the electromagnetic heating furnace, and the electromagnetic heating furnace is driven up and down by a cylinder arranged below it ; There is a leftover trash can on the bottom of the desktop, and a small drawer and a mobile phone drawer are arranged on the customer seating area corresponding to the edge of the desktop.
Owner:FUZHOU PINXING TECH DEV
Processing method of small-leaved Kuding tea
InactiveCN109007080AProtect IntegrityImprove qualityPre-extraction tea treatmentAntipyreticDiuresisLost Weight
The invention discloses a processing method of small-leaved Kuding tea. The method comprises steps of green tea picking, withering, stir-frying, steaming, rolling and drying. The bitterness of tea isreduced through stir-frying, a micro roller fixation machine is used for stir-frying, the integrity of tea is protected to the greatest extent in the stir-frying process, few tea fragments exist, andthe tea quality is improved. Phyllantus emblica powder is scattered before tea withering, fresh fruits of phyllantus emblica taste bitter and then sweet, the bitterness is removed after the phyllantusemblica is processed into powder, after the phyllantus emblica powder is added to Kuding tea, the sweetness of tea can be improved during brewing, besides, the phyllantus emblica powder has sweet aftertaste, so that the tea is sweet and mellow and popular among consumers. The tea is safe and non-toxic, has multiple effects of clearing heat, removing toxins, improving eyesight, clearing heat fromthe liver, moistening the throat, relieving cough, benefiting the throat, moistening the lung, producing saliva to slake thirst, promoting diuresis, strengthening heart, reducing pressure, losing weight, inhibiting and preventing cancer, resisting aging, activating blood vessels and the like and has better efficacy on hepatitis B, hyperlipidemia, hypertension, hyperglycemia, stomach cancer and thelike.
Owner:XINGYI LYVYUAN TCM MATERIALS PLANTING FARMERS SPECIALIZED COOP
Multifunctional in-situ rock and soil body torsional shear specimen device
PendingCN109870370AGuaranteed in situProtect IntegrityStrength propertiesTorsional ForcesElectric machinery
The invention provides a multifunctional in-situ rock and soil body torsional shear specimen device, which comprises a support platform, a servo motor and a hydraulic jack, wherein the servo motor andthe hydraulic jack are arranged at the upper end of the support platform; a telescopic rod and a push rod are arranged at the lower end of the support platform; the upper end of the telescopic rod passes through the support platform to be connected with a transmission shaft of the servo motor; the upper end of the push rod passes through the support platform to be connected with the hydraulic jack; the lower end of the telescopic rod is fixedly provided with a gear A; the push rod is connected with a specimen sleeve through a connecting element; a gear B is connected onto the specimen sleevein a sleeving way; and the gear B is engaged with the fixed gear A. A torsional shear mechanical test instrument uses a force sensor, so that the normal pressure exerted by the hydraulic jack is controlled; the normal tension exerted by the hydraulic jack can also be controlled; through the cooperation of the servo motor and the jack, the normal pressure (tension) and lateral torsional force can be exerted onto the specimen at the same time; and the pressure (tension) torsional shear mechanical experiments of the field specimen can be performed, so that the mechanical performance study on thefield specimen becomes possible.
Owner:CHINA THREE GORGES UNIV
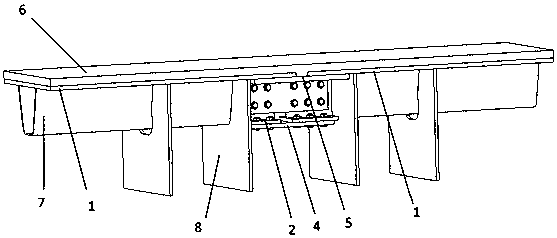
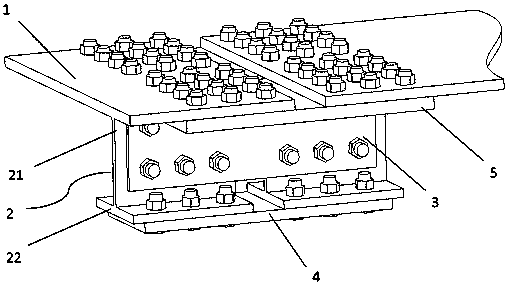
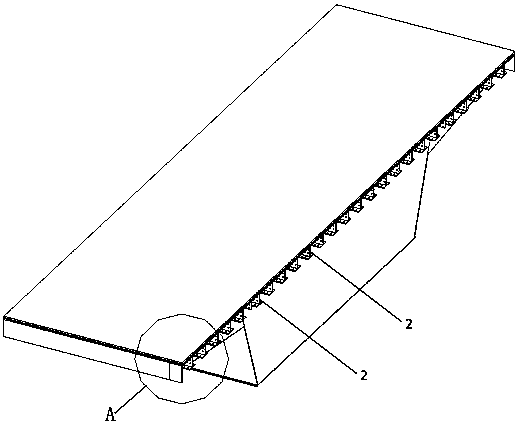
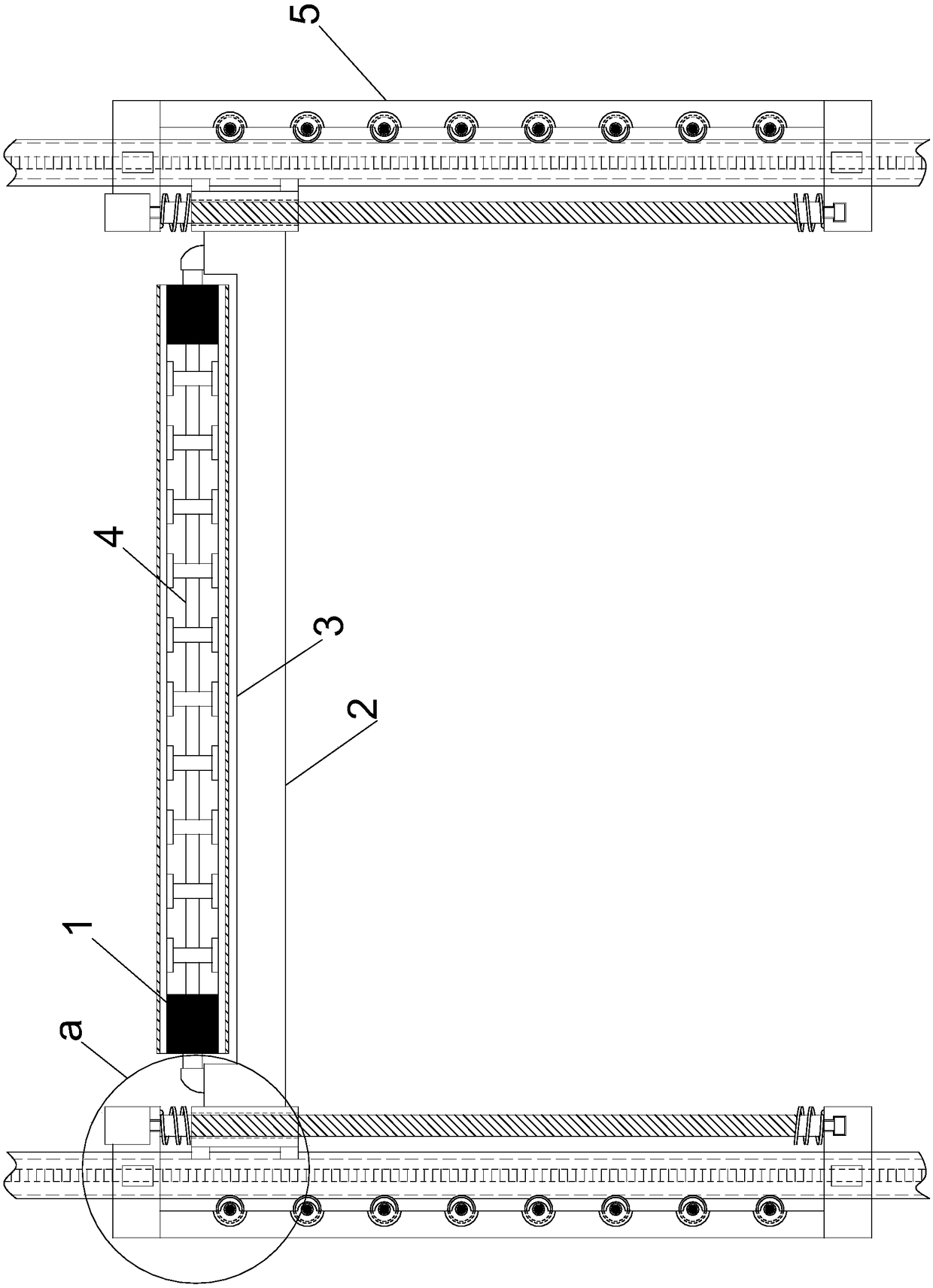
Steel-super high toughness concrete lightweight combined beam pier top bridge surface continuous structure and construction method thereof
PendingCN107653779AProtect IntegrityRepair is simple and convenientBridge structural detailsBridge materialsSurface plateBox girder
The invention discloses a steel-super high toughness concrete lightweight combined beam pier top bridge surface continuous structure. The steel-super high toughness concrete lightweight combined beampier top bridge surface continuous structure is arranged between adjacent steel box beam bridge surface plates, combines the adjacent bridge surface plates together to form a continuous whole, and comprises inverted-T ribs, inverted-T rib web connecting plates, inverted-T rib bottom plate connecting plates and top plate connecting plates. The multiple inverted-T ribs are transversely arranged on the bottom surface of the joint of the two bridge surface plates at intervals, and the inverted-T ribs on the two bridge surface plates are in one-to-one correspondence. Webs of the two corresponding inverted-T ribs are connected through the corresponding inverted-T rib web connecting plate; bottom plates of the two corresponding inverted-T ribs are connected through the corresponding inverted-T rib bottom plate connecting plate; and between the adjacent inverted-T ribs, the two bridge surface plates are connected through the top plate connecting plates. According to the continuous structure, adjacent box beams are connected as a whole through the inverted-T ribs and the connecting plates, under the effect of an earthquake, the damage mode of the continuous structure is that bolts are sheared off, in restoration after the earthquake, only the sheared-off high-strength bolts need to be replaced, and STC is partially repaired, so that repair is easy and convenient.
Owner:CHINA HIGHWAY ENG CONSULTING GRP CO LTD +1
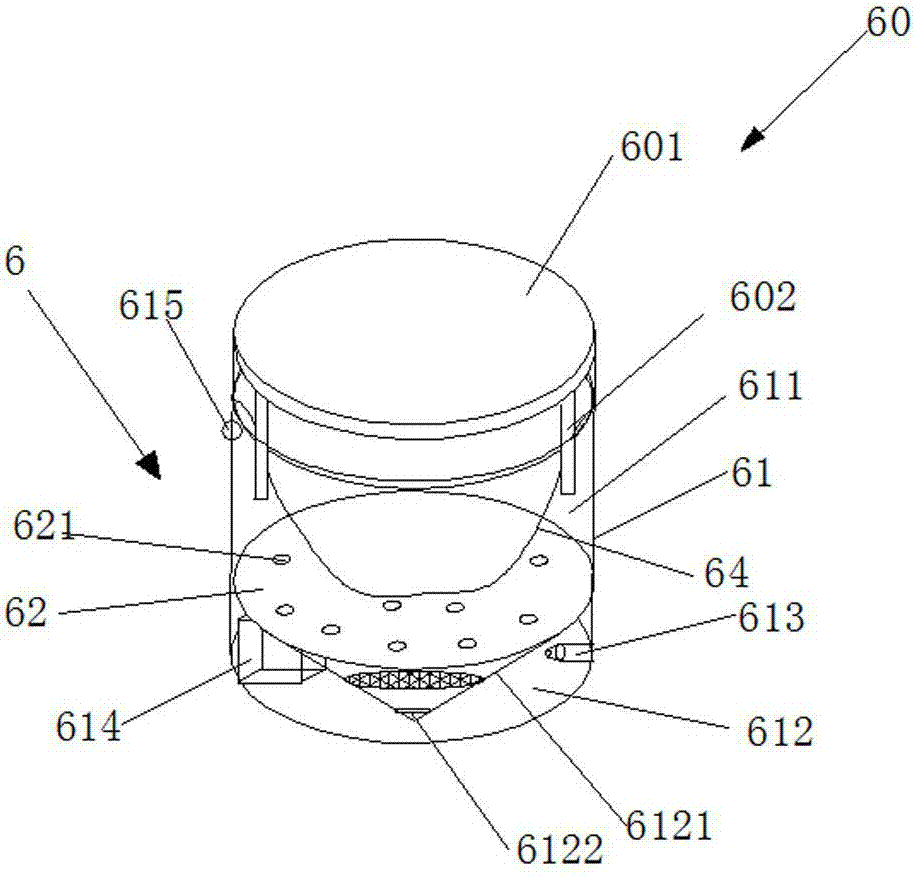
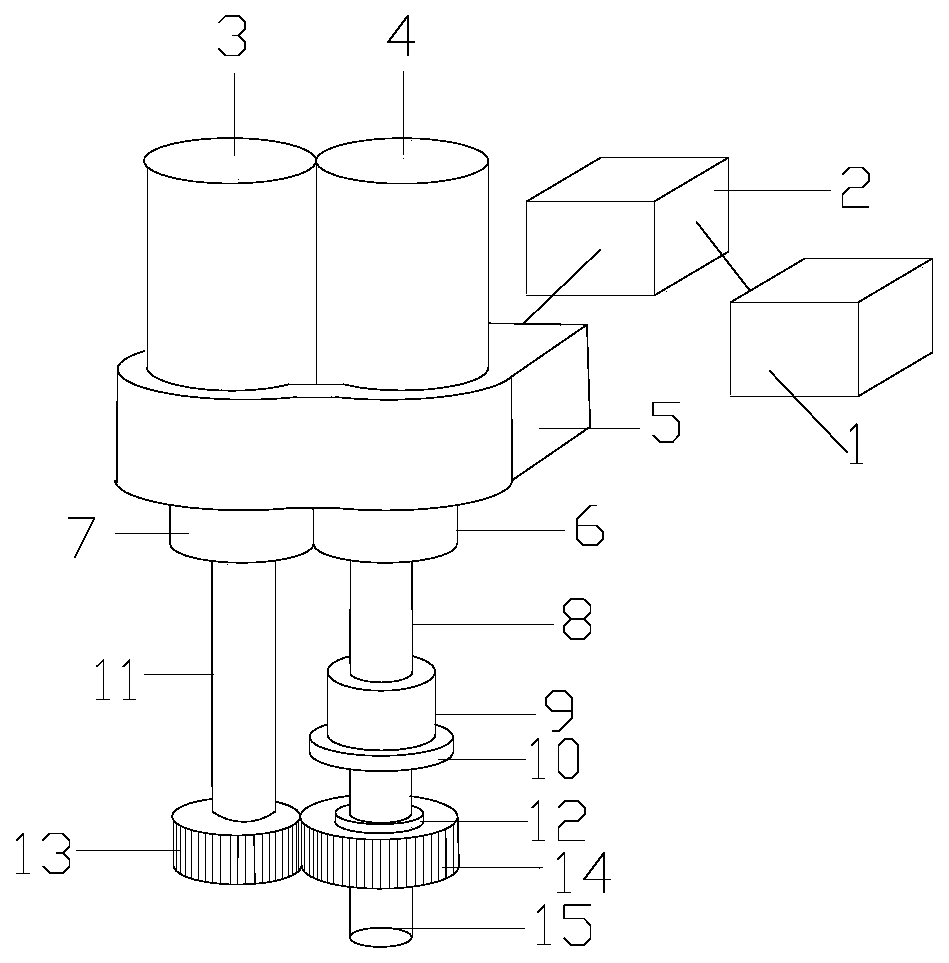
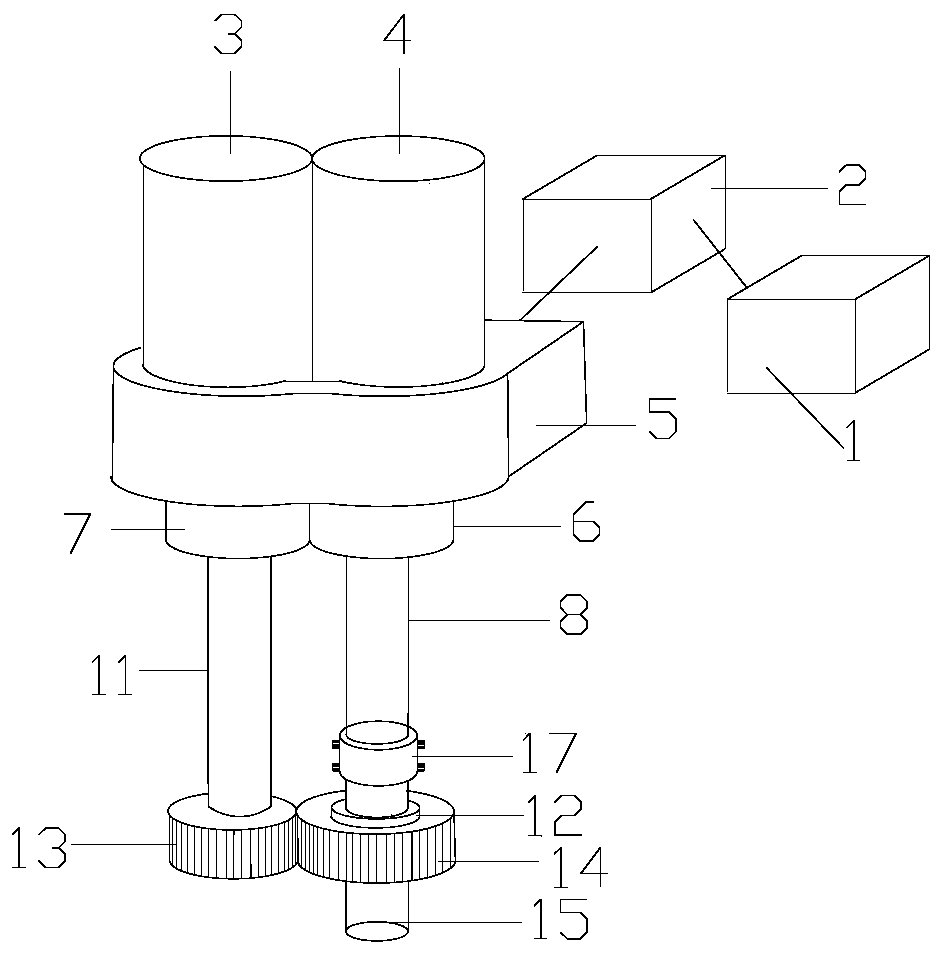
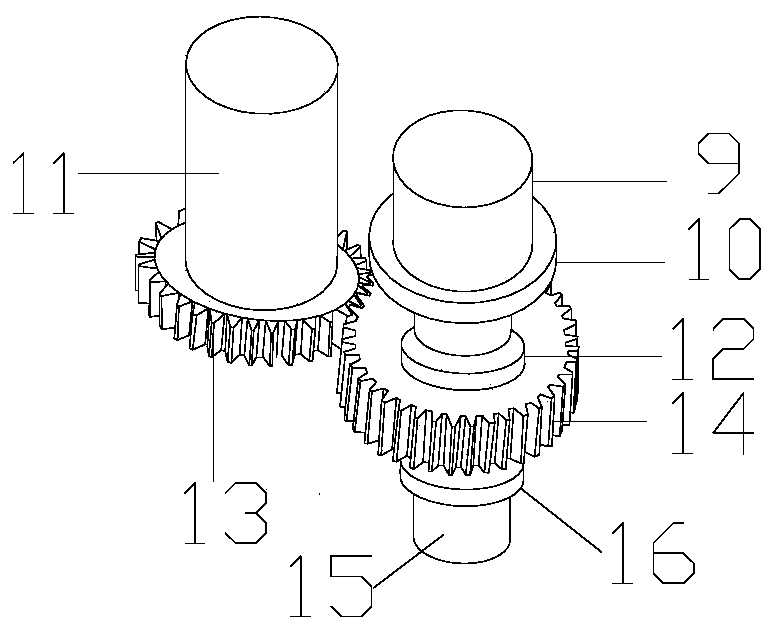
Follow-up stable lifting device for storage
Owner:ZHANJIANG POWER SUPPLY BUREAU OF GUANGDONG POWER GRID CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com