A blockchain-based trust service architecture and method
A block chain and architecture technology, applied in the direction of secure communication devices, payment architecture, instruments, etc., can solve problems such as failure to effectively realize information security, loss of user privacy, infrastructure disasters, etc., to achieve trust transfer and simplify authentication The effect of the process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
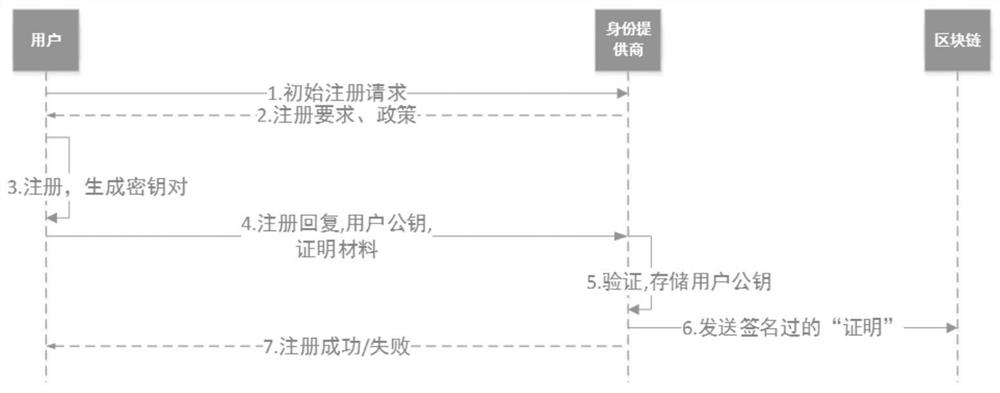
[0042] As mentioned above, such as figure 2 As shown, the specific application process of registration is as follows:
[0043] ① The identity provider receives the registration application initiated by the user through the terminal application;
[0044] ②The identity provider selects the registration requirements and relevant policies for this registration and sends them back to the user;
[0045] ③The user's terminal generates a new pair of public and private keys, which are unique to the user, identity provider, and blockchain;
[0046] ④ The user selects the required attributes, his own public key and other freely selected attributes according to the policy requirements and sends them back to the identity provider, and presents relevant certification materials;
[0047] ⑤The identity provider verifies the user's certification materials, and saves the user's public key and associated users after passing the verification, but does not save the user data locally, but hashes...
Embodiment 2
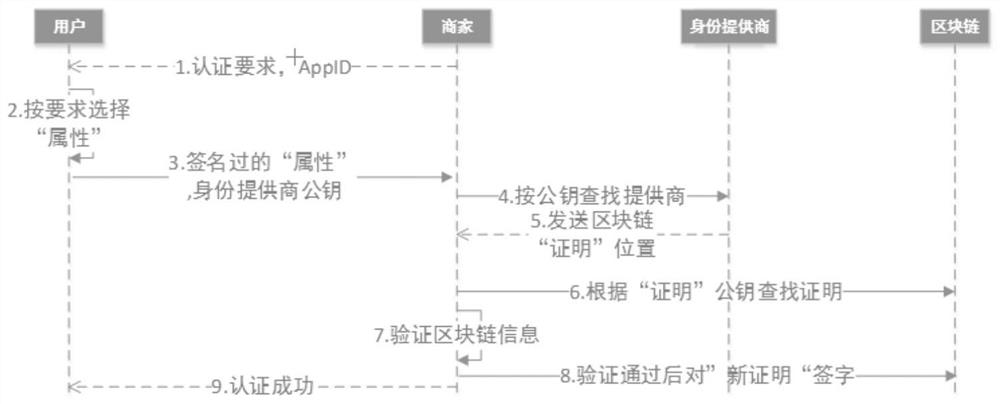
[0051] As mentioned above, such as image 3 and Figure 4 As shown, the specific application process of certification is as follows:
[0052] ①The merchant sends a random number challenge to the user, requiring the user to authenticate the required data according to the policy;
[0053] ② The data attributes authenticated by the identity provider when the user registers before the terminal selection according to the policy required by the authentication;
[0054] ③The user signs the challenge value, encrypts the attribute materials required by the merchant with the public key, and provides the public key and associated information of the identity provider to send to the merchant;
[0055]④ According to the identity provider information provided, the merchant goes to the identity provider to find the user's public key, associated information, and blockchain "proof" location information;
[0056] ⑤ The identity provider returns the information requested by the merchant;
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com