A method, device and equipment for identifying abnormal transaction behavior
An anomaly recognition and transaction technology, applied in the computer field, can solve problems such as user resource loss, achieve the effect of avoiding resource loss and improving effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
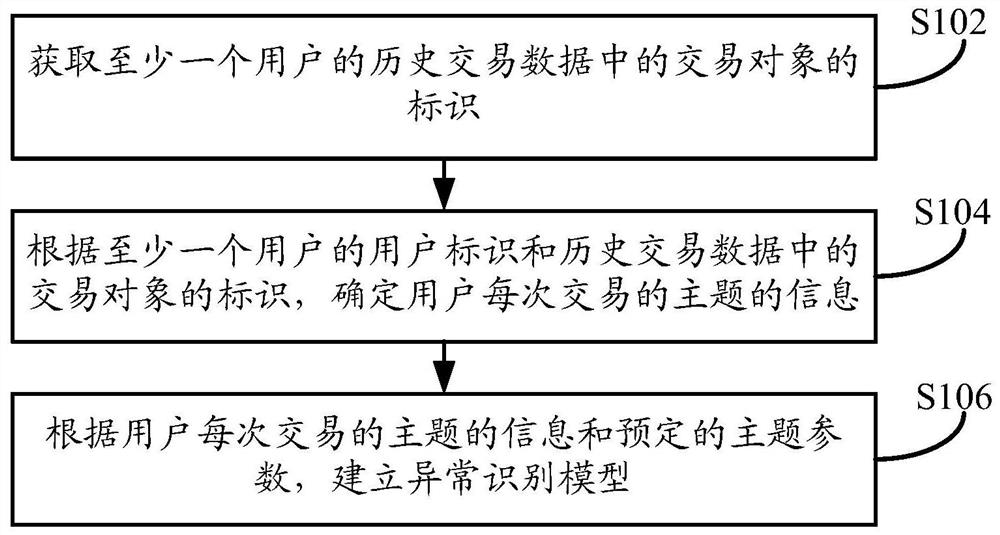
[0068] like figure 1 As shown, the embodiment of this specification provides a method for establishing an abnormality recognition model. The execution subject of the method may be a terminal device or a server, wherein the terminal device may be a personal computer or other mobile phone or a tablet computer. A terminal device, the terminal device may be a terminal device used by a user. The server can be an independent server, or a server cluster composed of multiple servers, and the server can be the background server of a certain business, or the background of a certain website (such as an online shopping website or payment application, etc.) server etc. In order to improve the efficiency of establishing an abnormality identification model, this embodiment takes the execution subject as a server as an example for illustration. For the case of a terminal device, it can be handled according to the following relevant content, and will not be repeated here. The method specific...
Embodiment 2
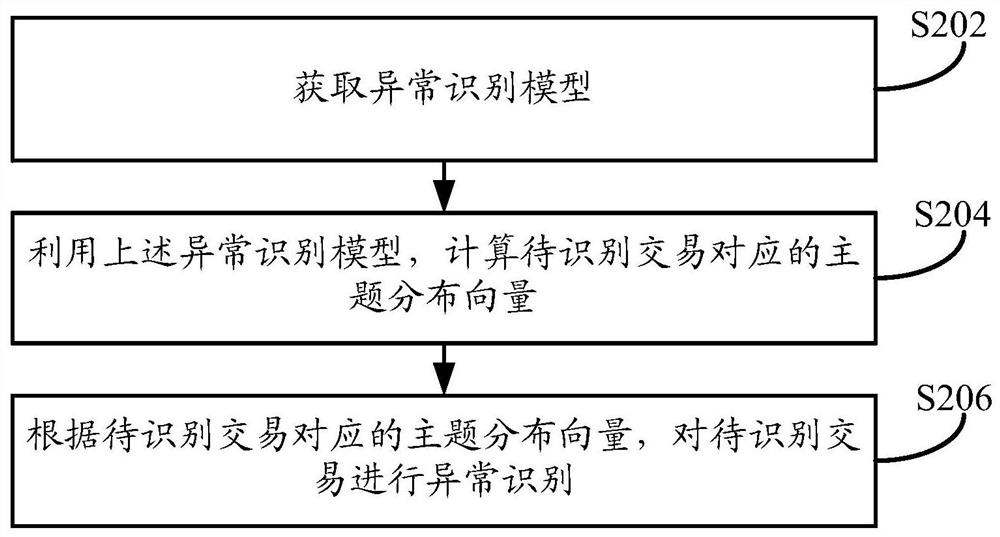
[0089] like image 3 As shown, the embodiment of this specification provides a method for identifying abnormal transaction behavior. The execution subject of the method may be a terminal device or a server, wherein the terminal device may be a personal computer or other mobile phone or tablet computer. A terminal device, the terminal device may be a terminal device used by a user. The server can be an independent server, or a server cluster composed of multiple servers, and the server can be the background server of a certain business, or the background of a certain website (such as an online shopping website or payment application, etc.) server etc. This method can create an identification model for identifying abnormal transactions, and identify abnormal transaction lines. In order to improve the identification efficiency of abnormal transactions, this embodiment takes the execution subject as the server as an example for illustration. For terminal equipment In the case of...
Embodiment 3
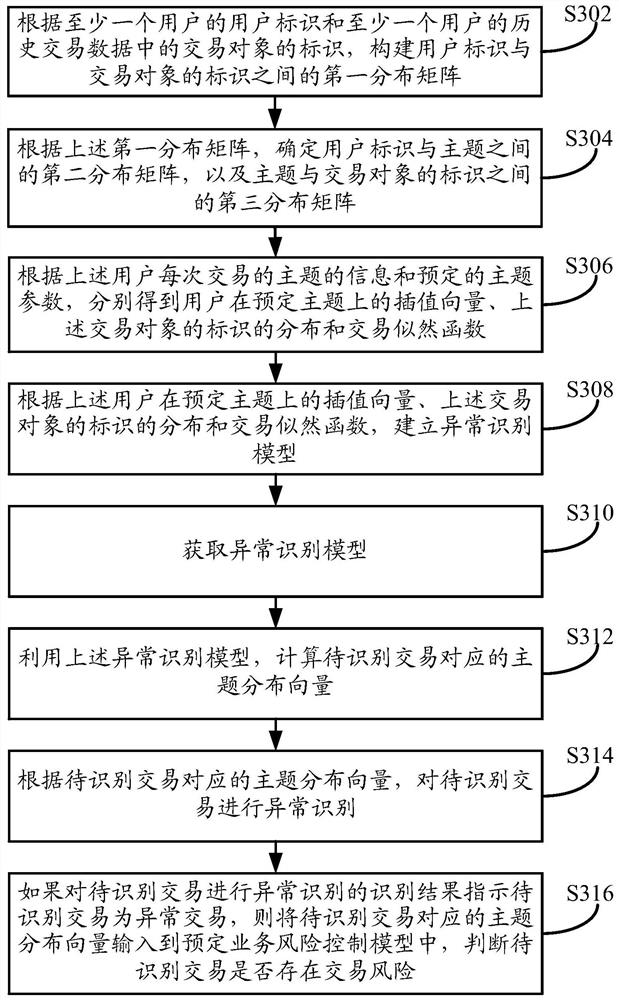
[0131] The above is the identification method for abnormal transaction behavior provided by the embodiment of this specification. Based on the same idea, the embodiment of this specification also provides an identification device for abnormal transaction behavior, such as Figure 5 shown.
[0132] The identification device for abnormal transaction behavior includes: a model acquisition module 501, a vector calculation module 502 and an identification module 503, wherein:
[0133] A model acquisition module 501, configured to acquire an abnormality recognition model, wherein the abnormality recognition model is established according to the user identifier of at least one user and the identifier of the transaction object in the historical transaction data of the at least one user, and the abnormality recognition model uses It is used to calculate the topic distribution vector in user transactions;
[0134] A vector calculation module 502, configured to use the abnormality ident...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com