Method for sensing abnormal behavior of passenger by wireless technology
A wireless technology, passenger technology, applied in wireless communication, location information-based services, instruments, etc., can solve problems such as inability to predict and identify in advance, low real-time performance, time-consuming and labor-intensive problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0063] Embodiment 2: When a suspicious user accesses an AP
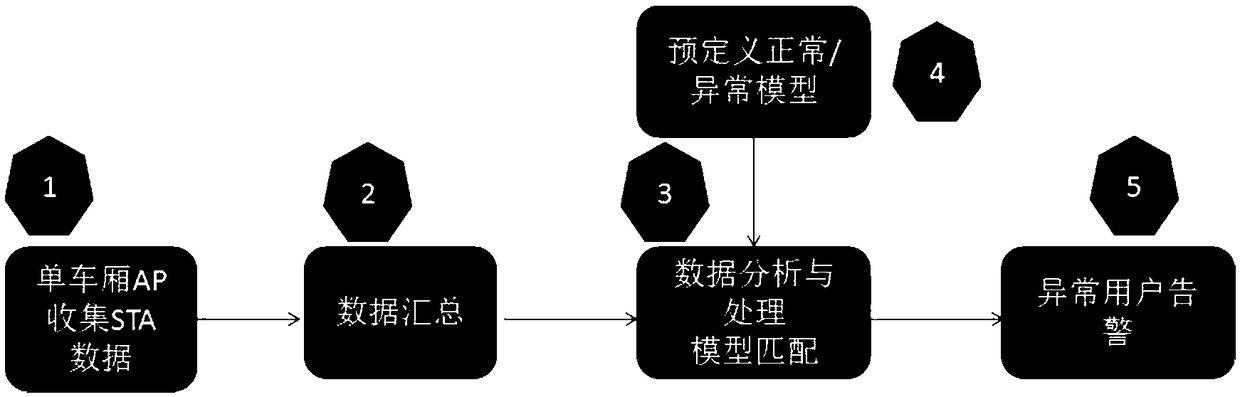
[0064] 1. On the train, one AP is installed in each carriage, and the whole train has a central control server to manage the AP equipment in each carriage
[0065] 2. Each carriage reports the connected STA information to the central server, and the central server gathers the AP ID numbers accessed by each passenger. The change of the passenger's location will lead to the change of the accessed AP ID (roaming)
[0066] 3. The data analysis of the central server is consistent with the scheme one.
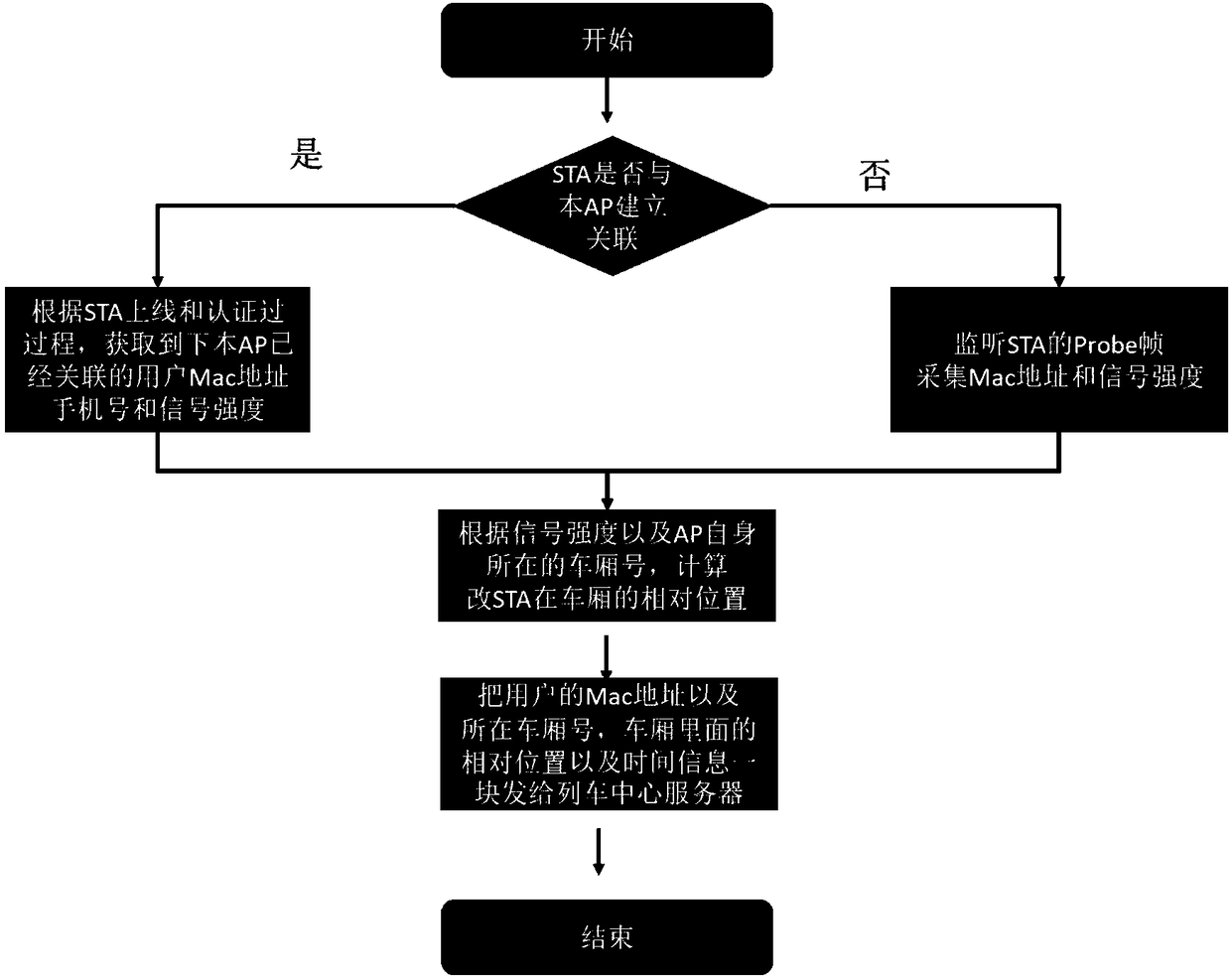
[0067] Among them such as Image 6 Three phases of wireless access process shown
[0068] Before the STA (workstation) starts initialization and begins to use the AP to transmit data frames, it needs to go through three stages before it can access (802.11MAC layer is responsible for the communication between the client and the AP, and its functions include scanning, access, authentication, encryption, features such as ro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com