Network space vulnerability merging platform system
A cyberspace and vulnerability technology, applied in transmission systems, electrical components, etc., can solve problems such as hidden dangers, impact, control and destruction of Internet security, and achieve the effect of improving detection capabilities, improving industry standards, and improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
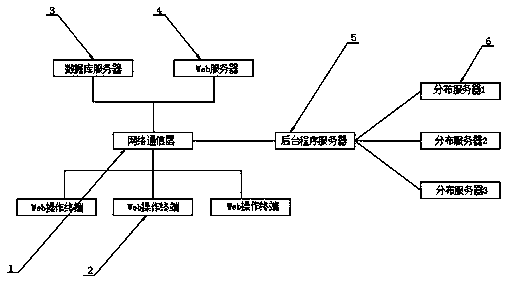
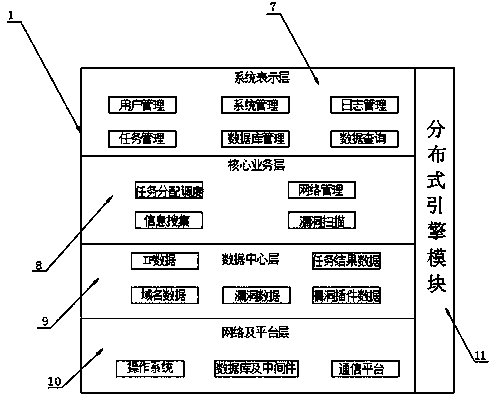
[0033] Refer to the attached Figure 4 and Figure 5 : First, the administrator / executor logs in to the web to submit the task; then the distribution node controls the background, and the task will be automatically assigned to the idle node; again, the node will analyze the task process (information collection->IP range / domain name arrangement- >Vulnerability scanning), and store the collected information, vulnerabilities, and services in the database; finally, the node still sends a notification to the administrator’s mailbox, reporting the completion of the task scanning and whether there is a vulnerability report and vulnerability level, and completes the entire detection report process , the program will automatically assign tasks to each distribution node, and use the distribution nodes to perform some tedious tasks such as information collection, vulnerability analysis, and report output for the target task, which can greatly save personnel usage and time, and the automa...
Embodiment 3
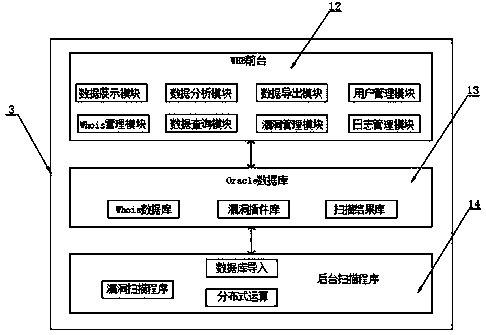
[0035] Refer to the attached Figure 6 : Administrators or executives can view the vulnerability distribution map of the areas or tasks under their management through the web operation terminal 2, and can clearly view the key areas of vulnerabilities and safe areas (visual display of the distribution of vulnerability areas), which can facilitate emergency response and ensure Network security.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com