Method and device for identity authentication, terminal and storage medium
An identity authentication and mobile terminal technology, applied in the field of security authentication, can solve the problems of inaccurate detection, low precision, low applicability, etc., and achieve the effect of improving accuracy and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
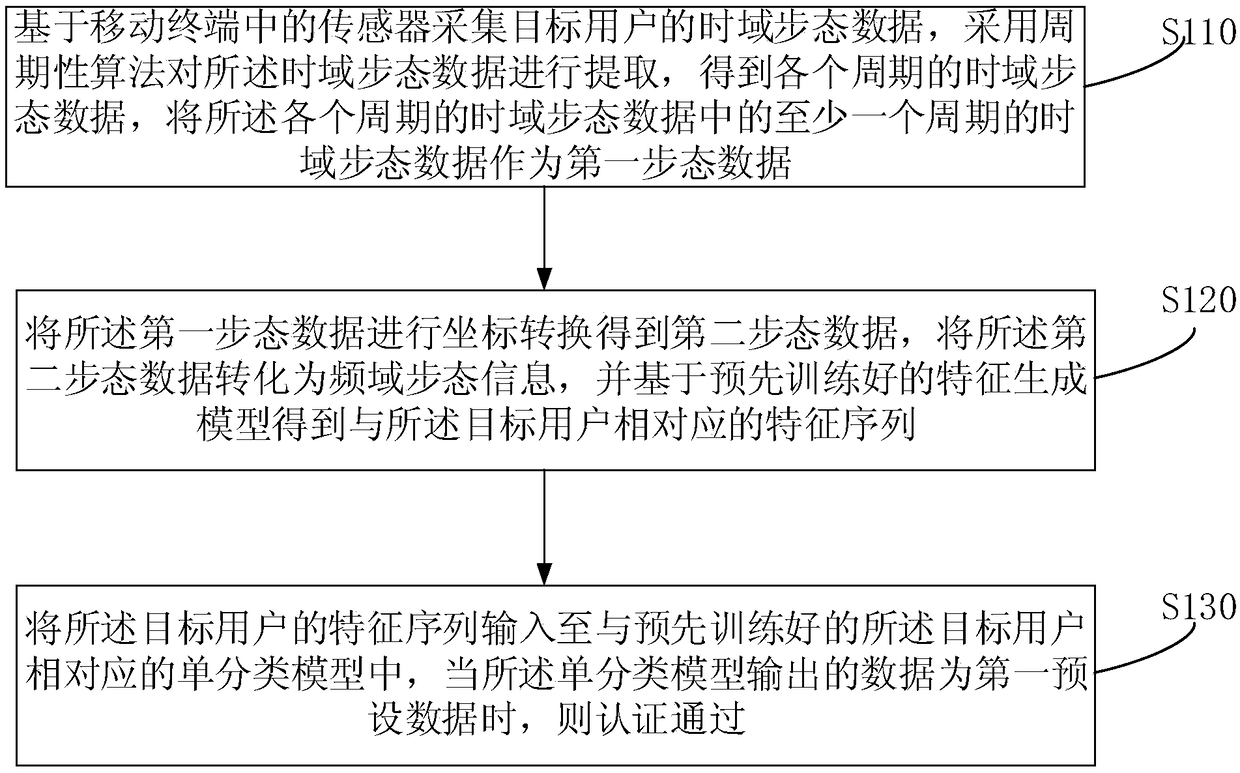
[0027] figure 1 It is a schematic flow chart of an identity authentication method provided by Embodiment 1 of the present invention. The embodiment of the present invention is applicable to the situation of authenticating the user's identity. The method can be executed by an identity authentication device, which can use software and / or or in the form of hardware.
[0028] Such as figure 1 Described, the method of the present embodiment comprises:
[0029] S110. Collect the time-domain gait data of the target user based on the sensor in the mobile terminal, use a periodic algorithm to extract the time-domain gait data, obtain the time-domain gait data of each cycle, and extract the time-domain gait data of each cycle Time domain gait data of at least one period in the domain gait data is used as the first gait data.
[0030] Wherein, a mobile terminal refers to a computer device that can be used on the move, such as a mobile phone, a tablet computer, and the like. A sensor ...
Embodiment 2
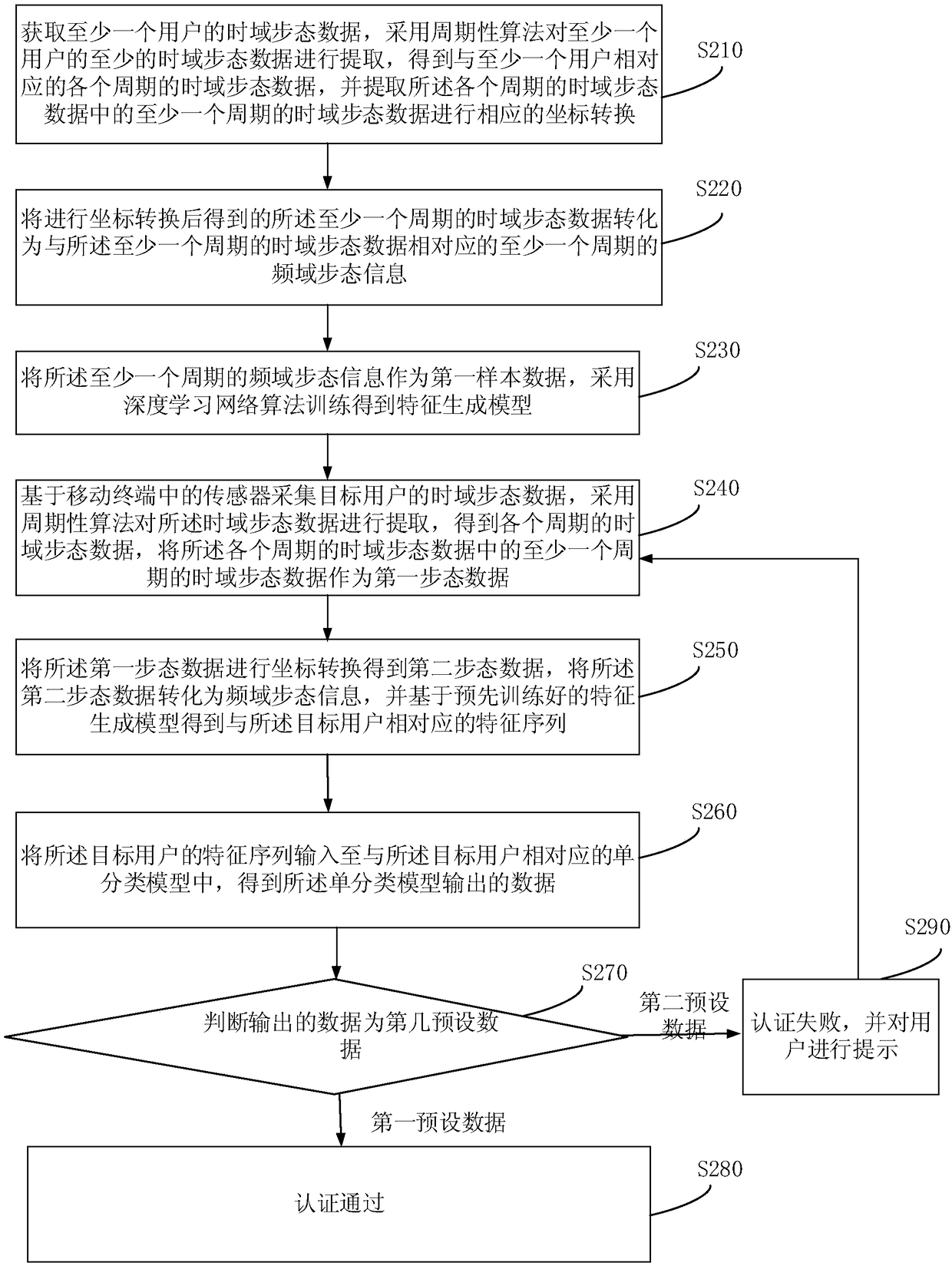
[0071] Before collecting the current time-domain action information of the target user based on the sensor in the mobile terminal, it is necessary to obtain a feature generation model, so that each user can obtain a feature sequence corresponding to each user through the feature generation model, so that a single classification vector machine can be used The algorithm trains the acquired feature sequence to obtain a single classification model, and the single classification model can also determine whether the current user is the target user according to the feature sequence input by the user. figure 2 It is a schematic flowchart of an identity authentication method provided by Embodiment 2 of the present invention, as shown in figure 2 Described, the method of the embodiment of the present invention comprises:
[0072]S210. Acquire time-domain gait data of at least one user, extract at least time-domain gait data of at least one user by using a periodic algorithm, and obtai...
Embodiment 3
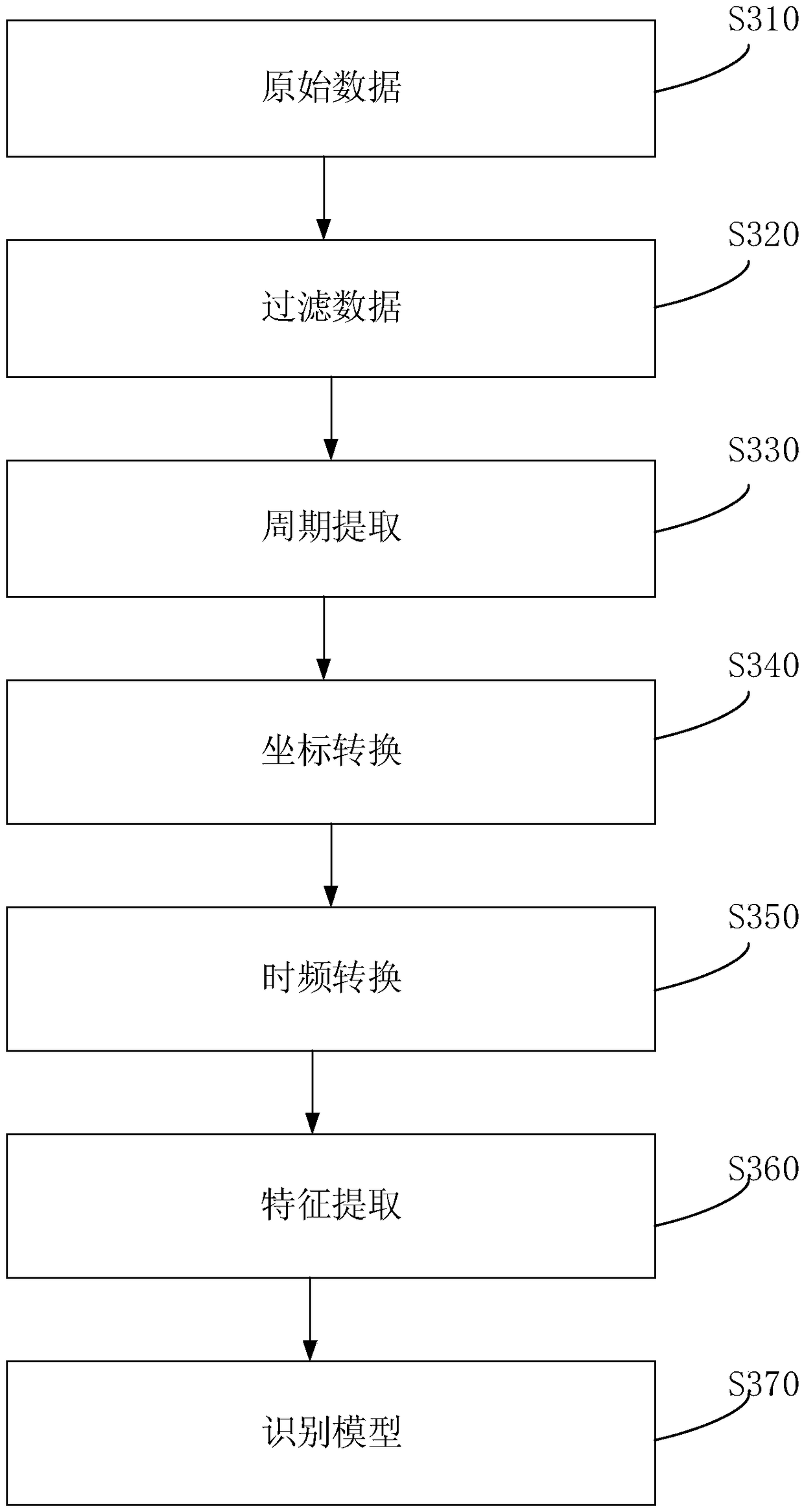
[0095] As a preferred embodiment of the above embodiment, image 3 It is a schematic flowchart of an identity authentication method provided by Embodiment 3 of the present invention, as shown in image 3 Described, the method of the embodiment of the present invention comprises:
[0096] S310. Raw data. The time-domain gait data of the target user is acquired through the built-in sensor of the mobile terminal, wherein the time-domain gait data may be the time-domain gait data of the current user walking at least three steps, optionally six steps, etc.
[0097] S320. Filter data.
[0098] The time-domain gait data obtained at this time has certain noise, and it needs to be de-noised. state data.
[0099] S330, period extraction.
[0100] In the process of walking, the user takes two steps and one cycle, which has a very strong periodicity. Therefore, basically one cycle (about 1 second) contains the gait characteristics of a user, and the time-domain gait data of more tha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com