Patents
Literature
80 results about "Computer Point" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
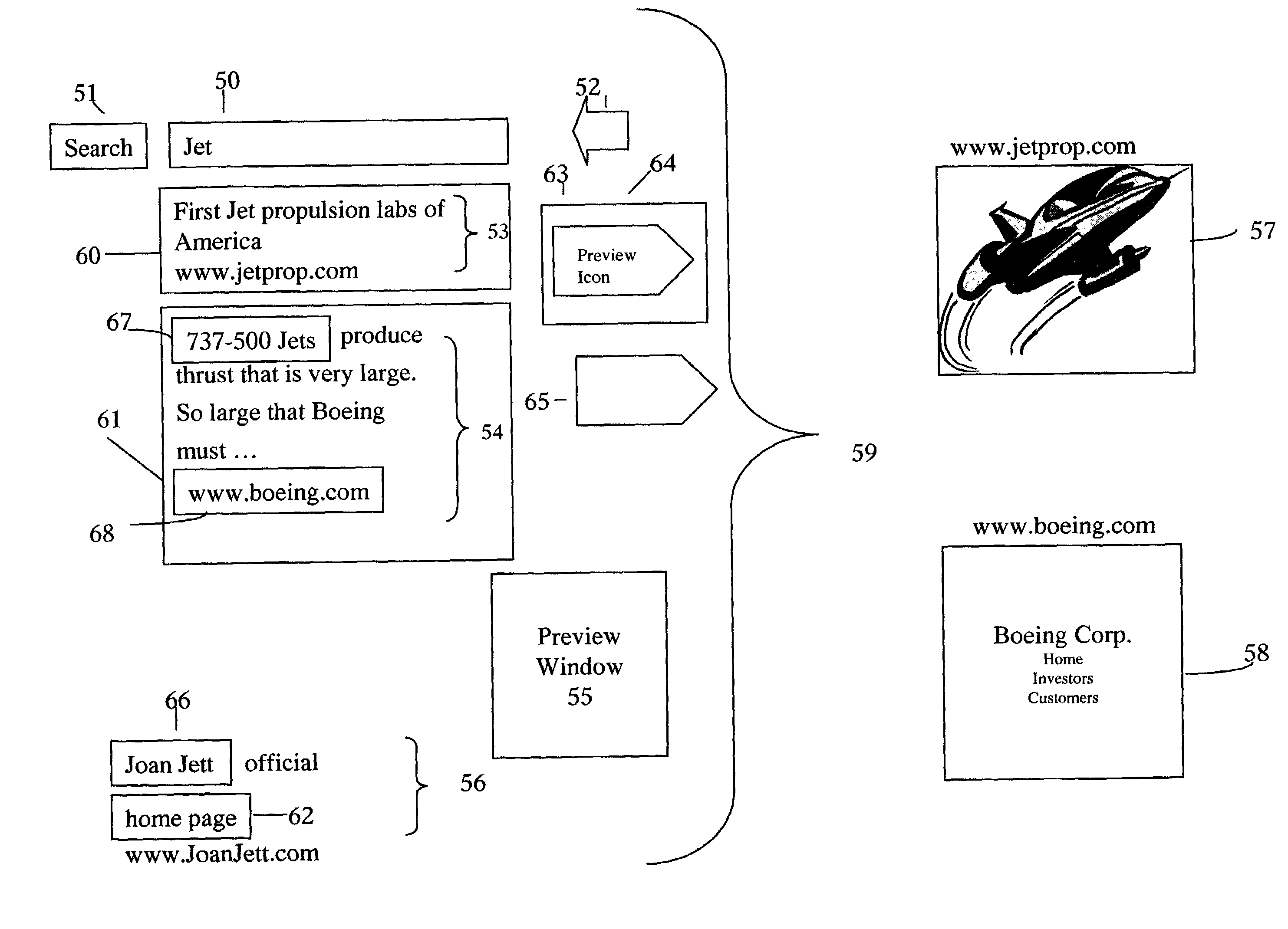
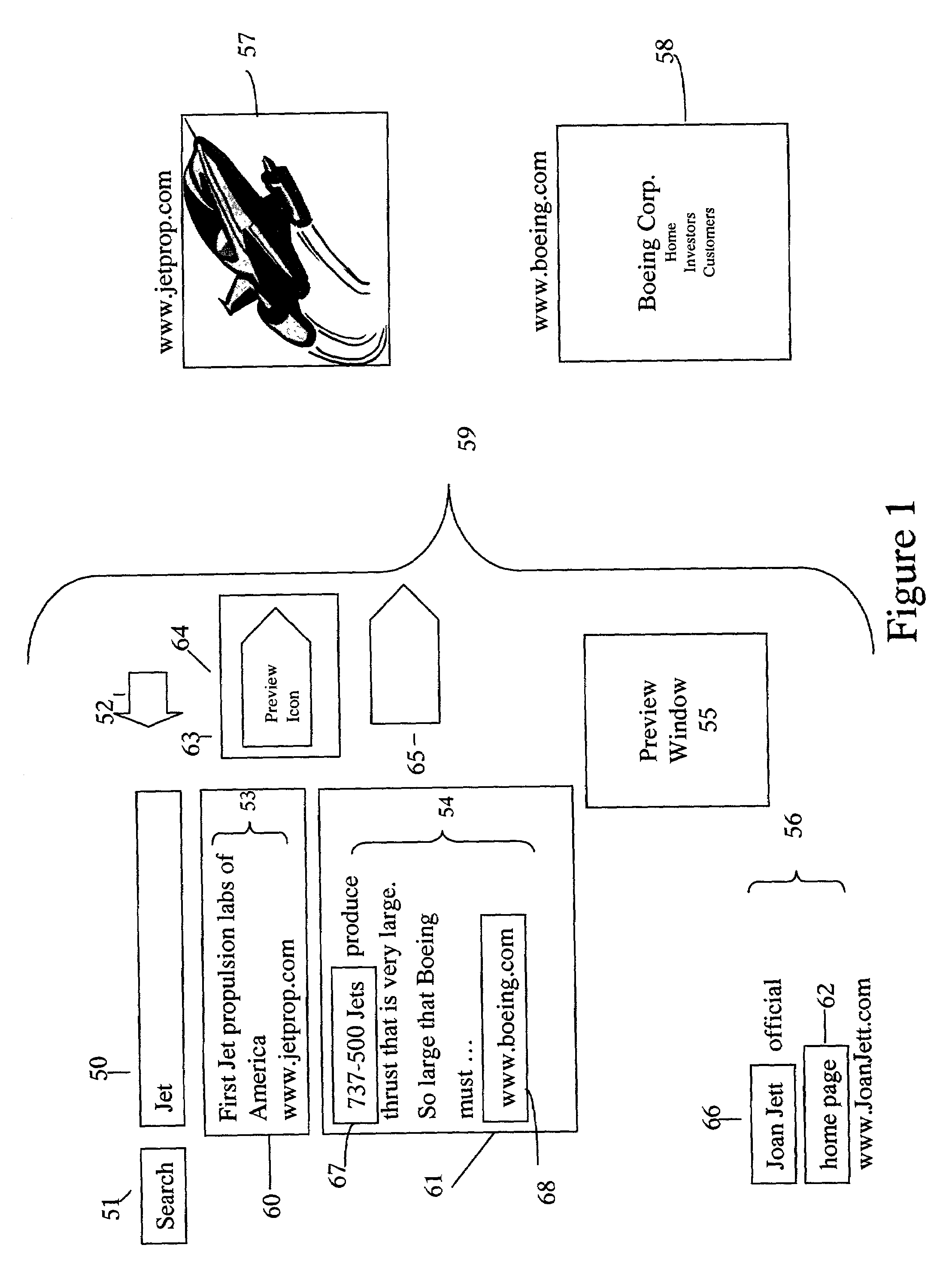
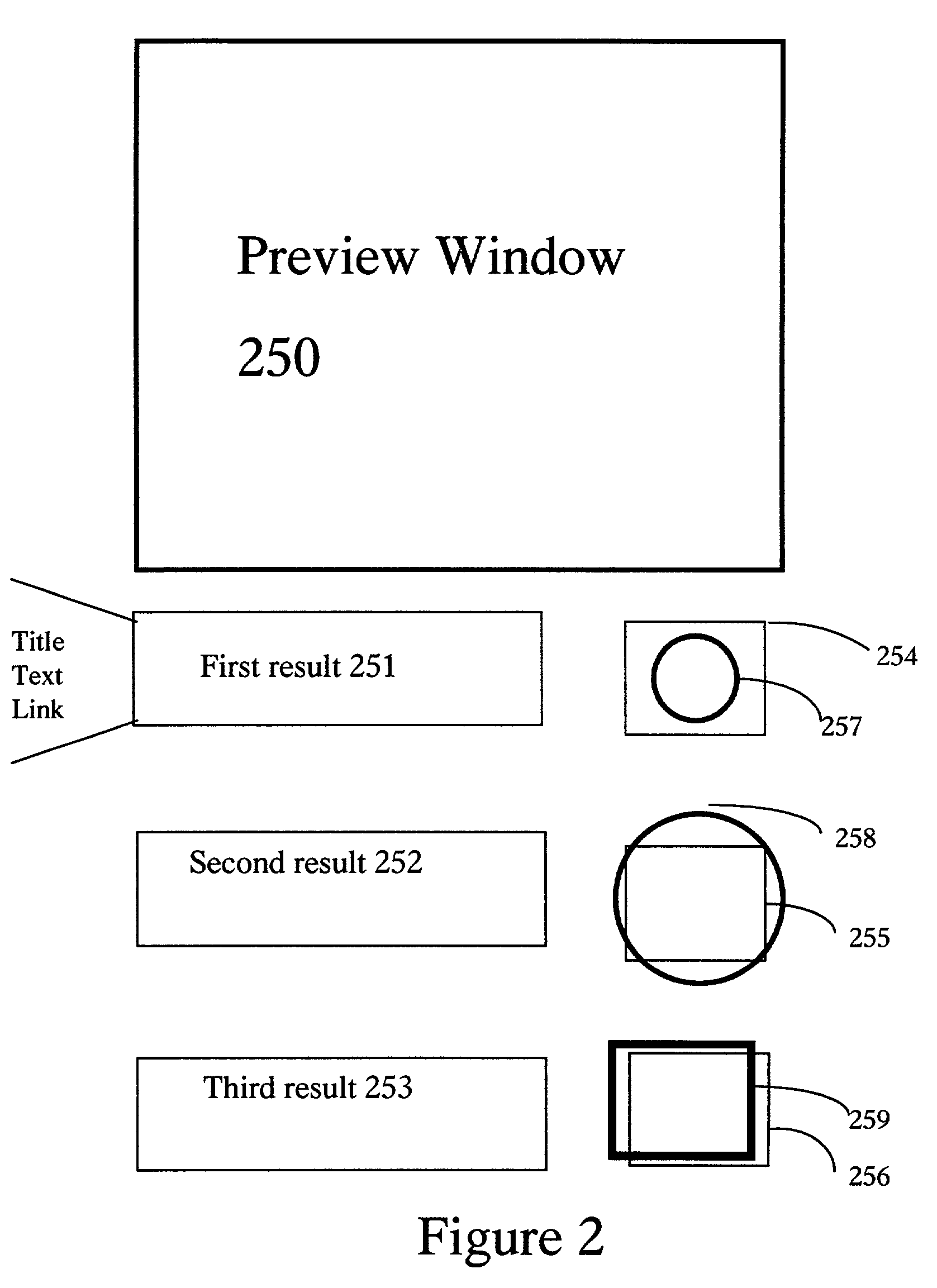
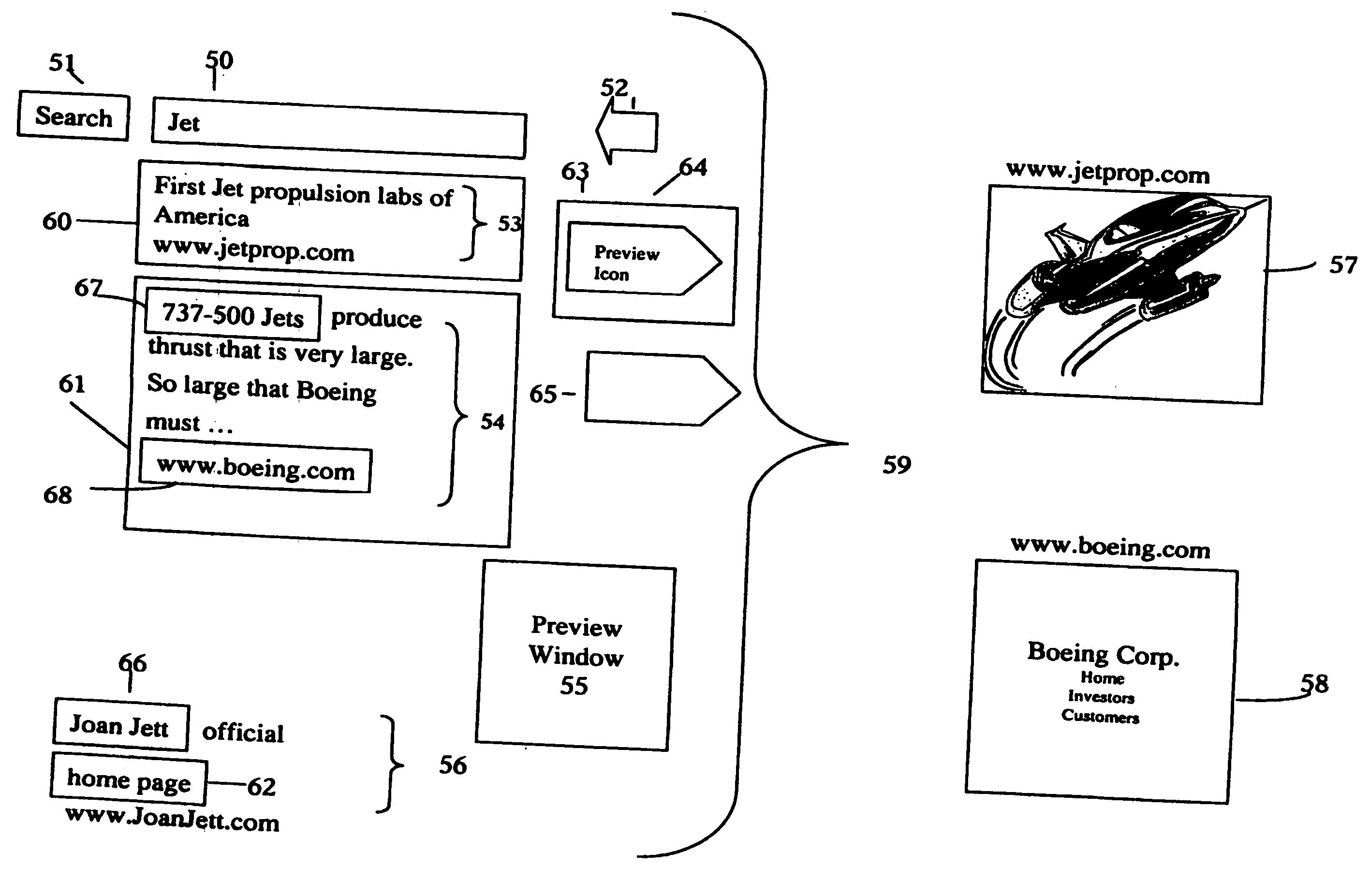
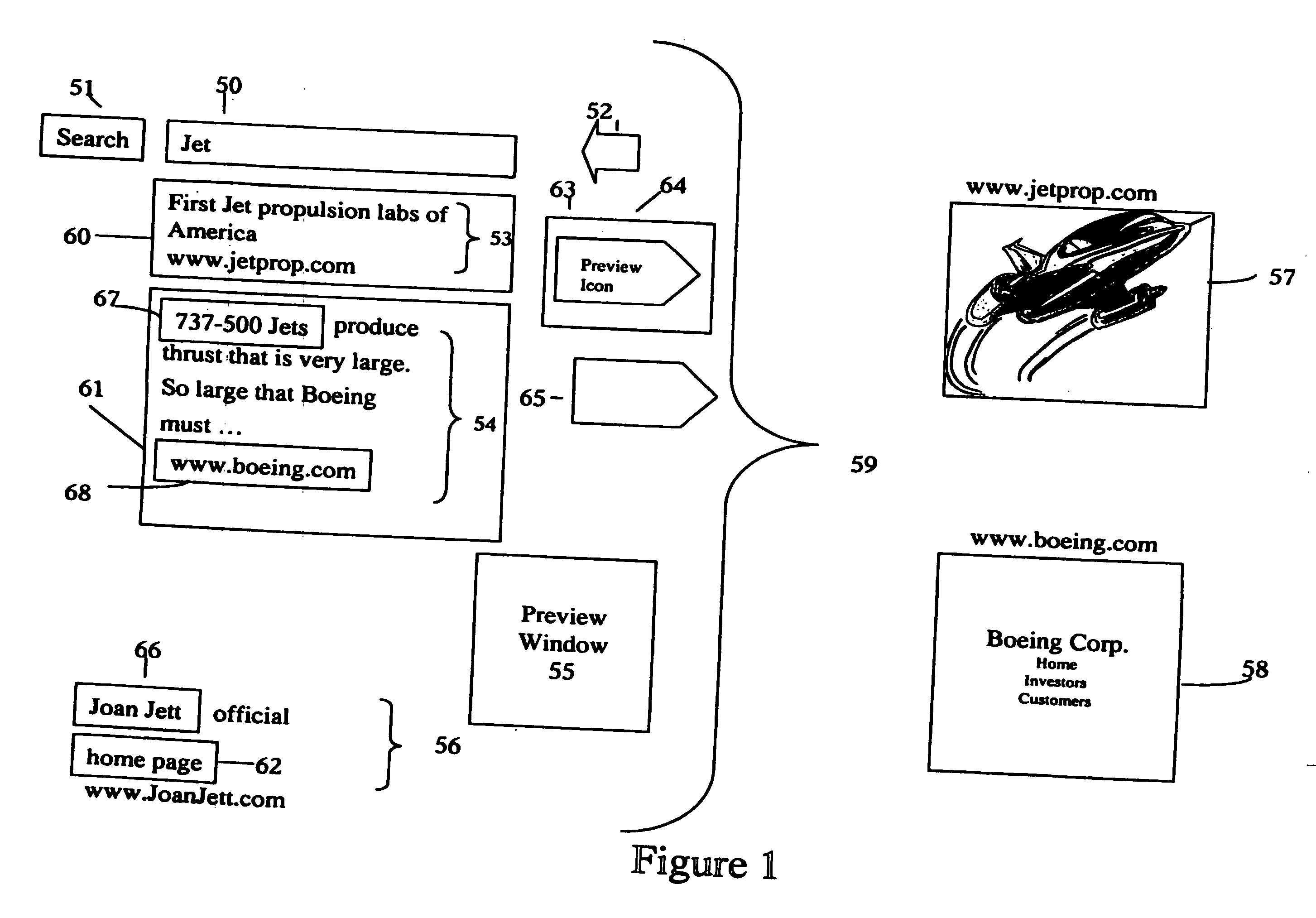
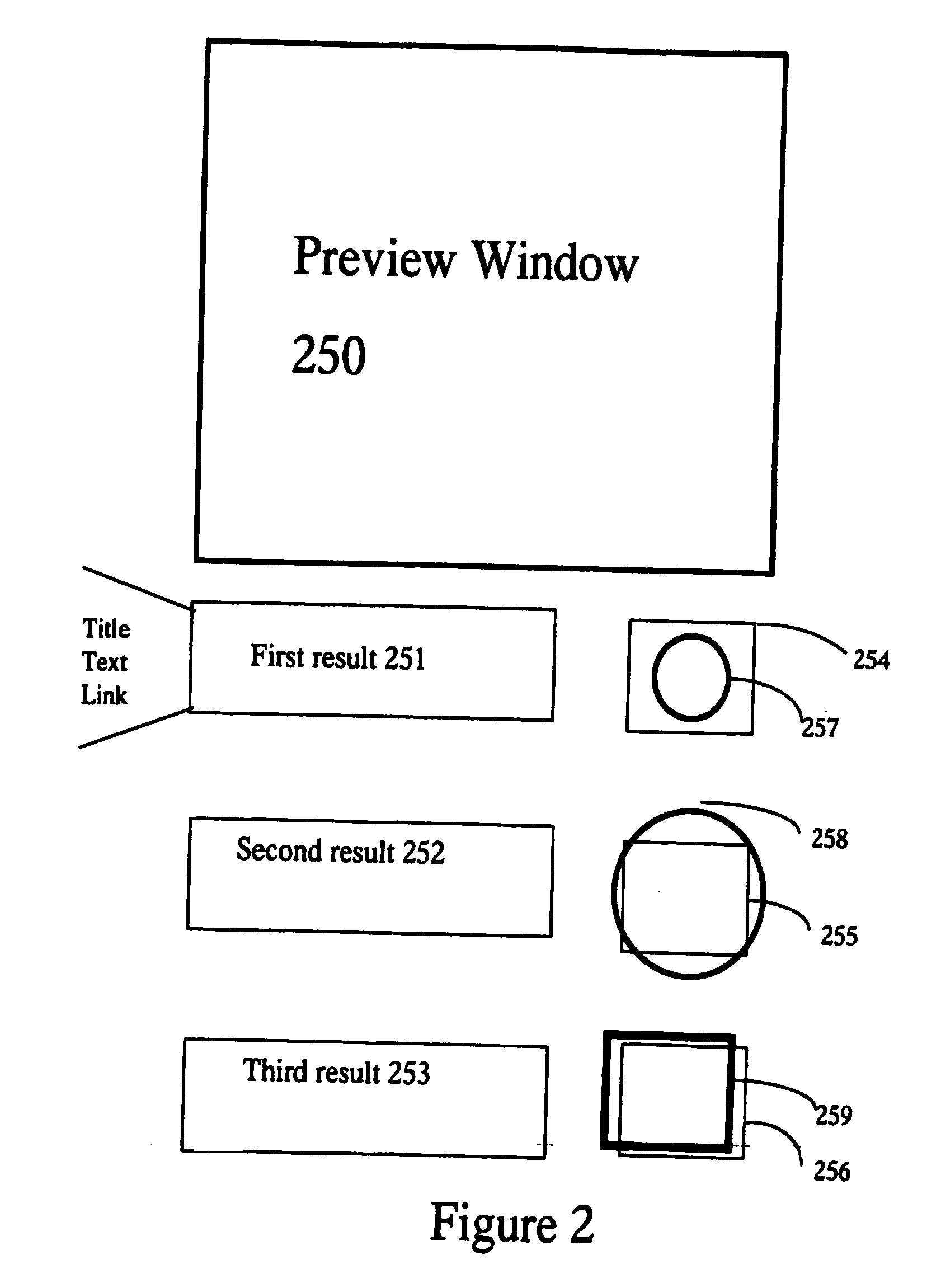
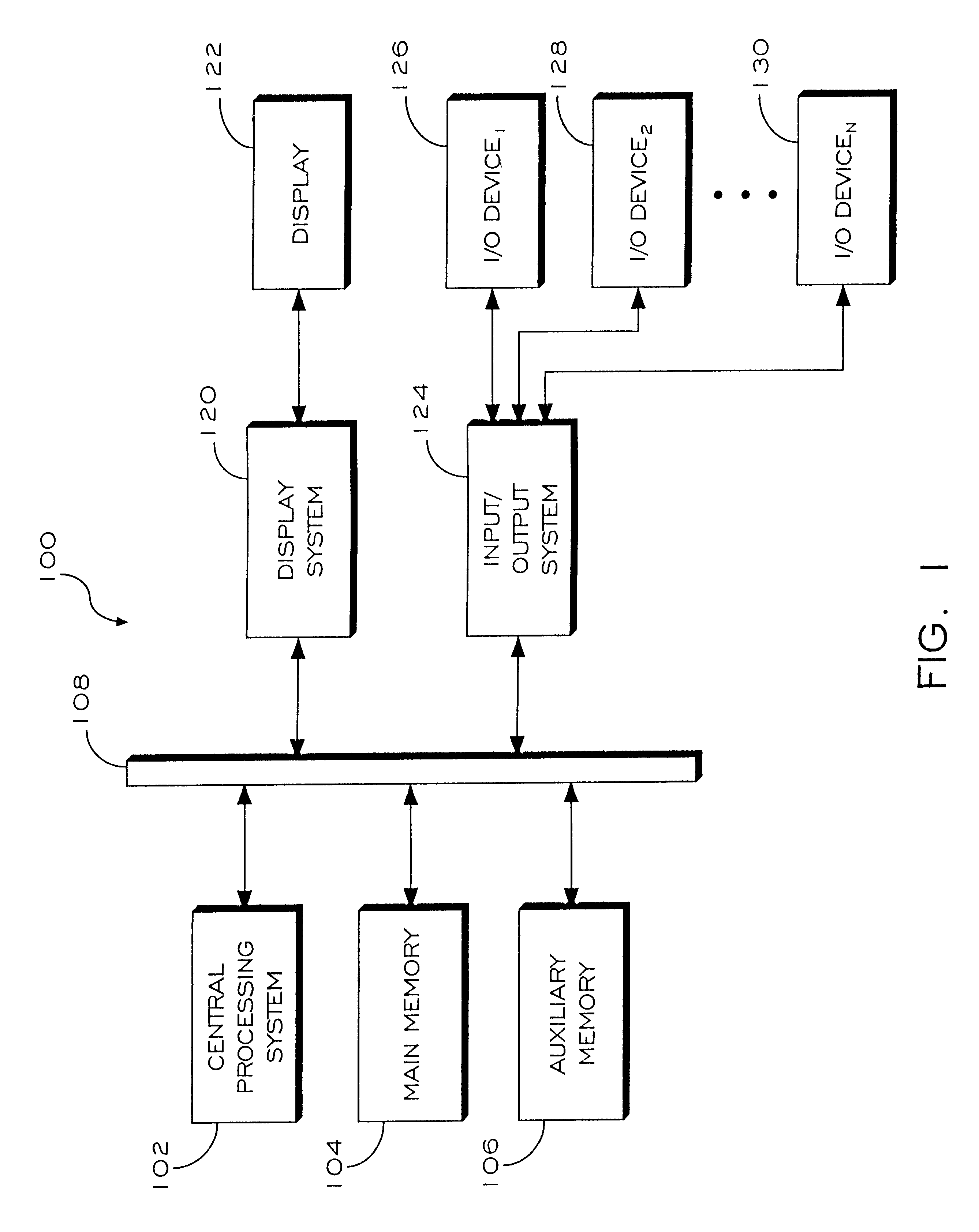
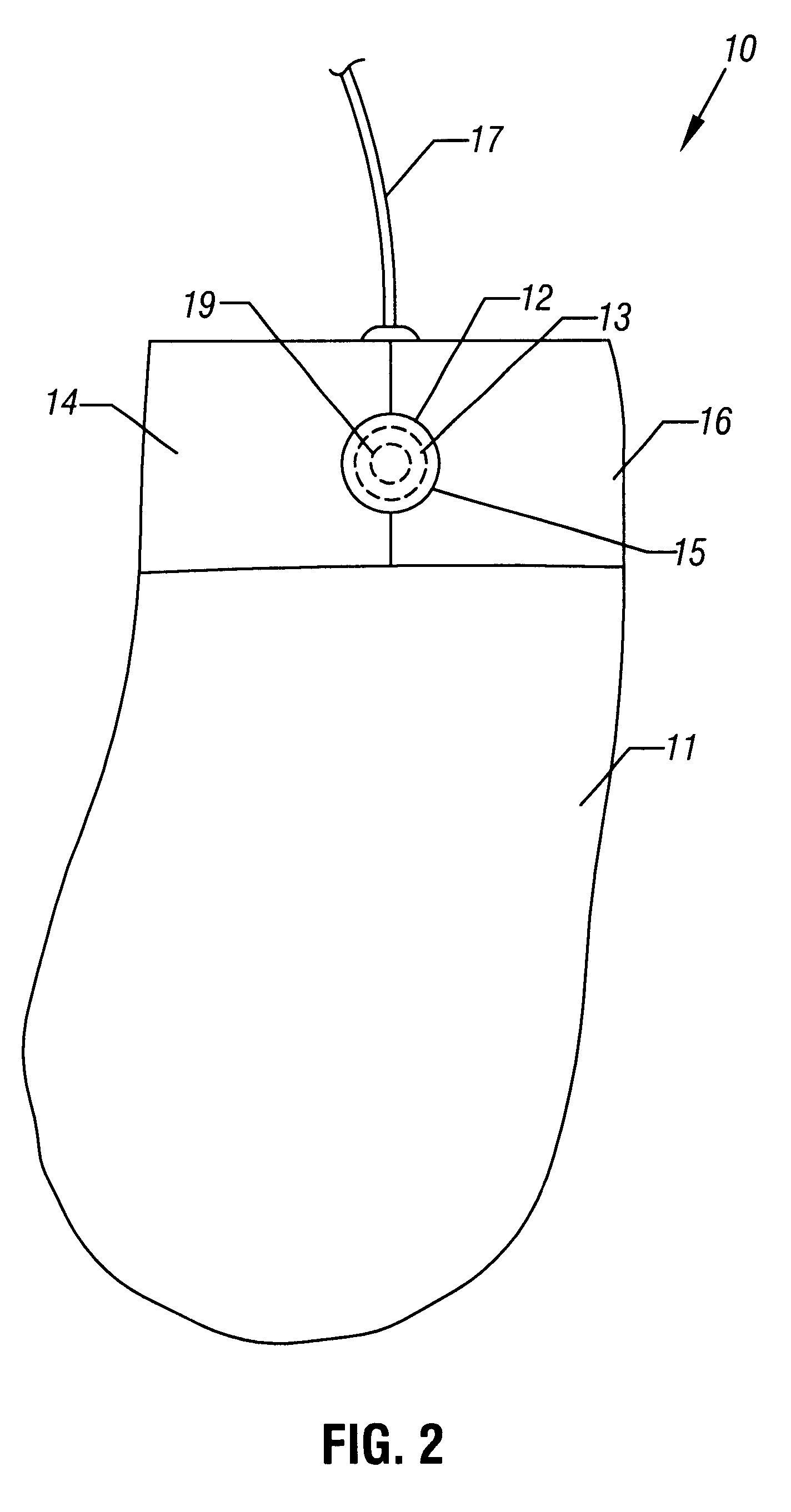
Methods and apparatus for mouse-over preview of contextually relevant information
InactiveUS7047502B2Mitigate challengeReduce problemsDigital data information retrievalCathode-ray tube indicatorsRelevant informationMouseover
Challenges to the analysis of search results may be mitigated by offering preview information when users navigate a computer-pointing device over pre-designated areas of a search result page. A separate icon in the pre-designated area enhances the advantages by providing intuitive preview ability with seamless and natural control over a variety of preview options, such as the type of preview information and the manner in which it is presented. In addition, while operating a preview-enabled search result page, users' behavior provides data and attributes, which may be re-incorporated into the searching algorithm to improve the relevancy of search results.
Owner:IAC SEARCH & MEDIA
To a combined fingerprint acquisition and control device
The present invention combines the functionality of a computer pointing device with a fingerprint authentication system, In the preferred embodiment, by regularly scanning fingerprints acquired from the pointing device touch pad, fingerprint features may be extracted and compared to stored data on authorized users for passive authentication. Furthermore, calculations based upon the acquired fingerprint images and associated features allows the system to determine six degrees of freedom of the finger, allowing the user to control a variety of functions or to manipulate a three-dimensional model or virtual reality system.
Owner:SYNAPTICS INC
Computer mouse peripheral
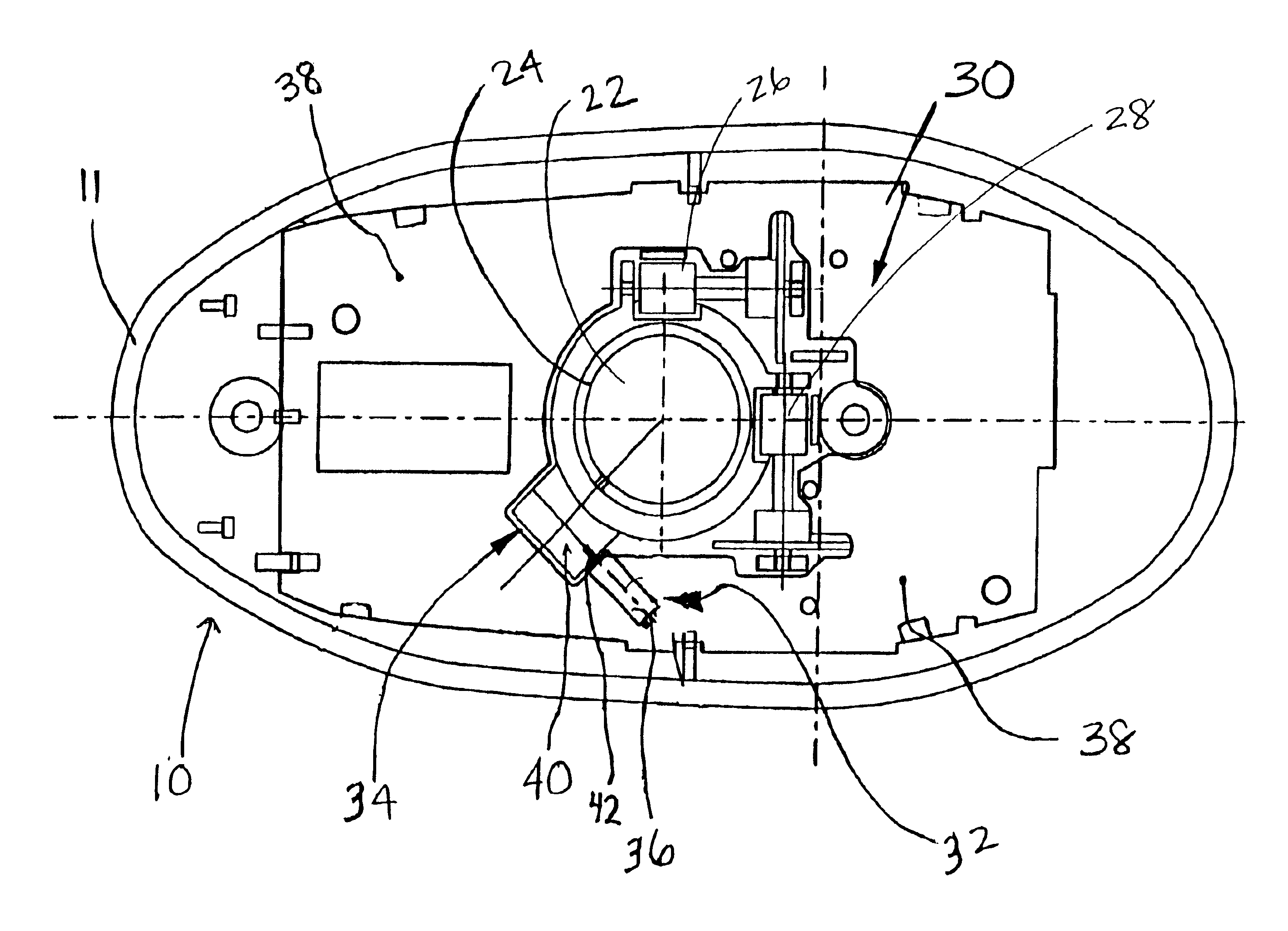
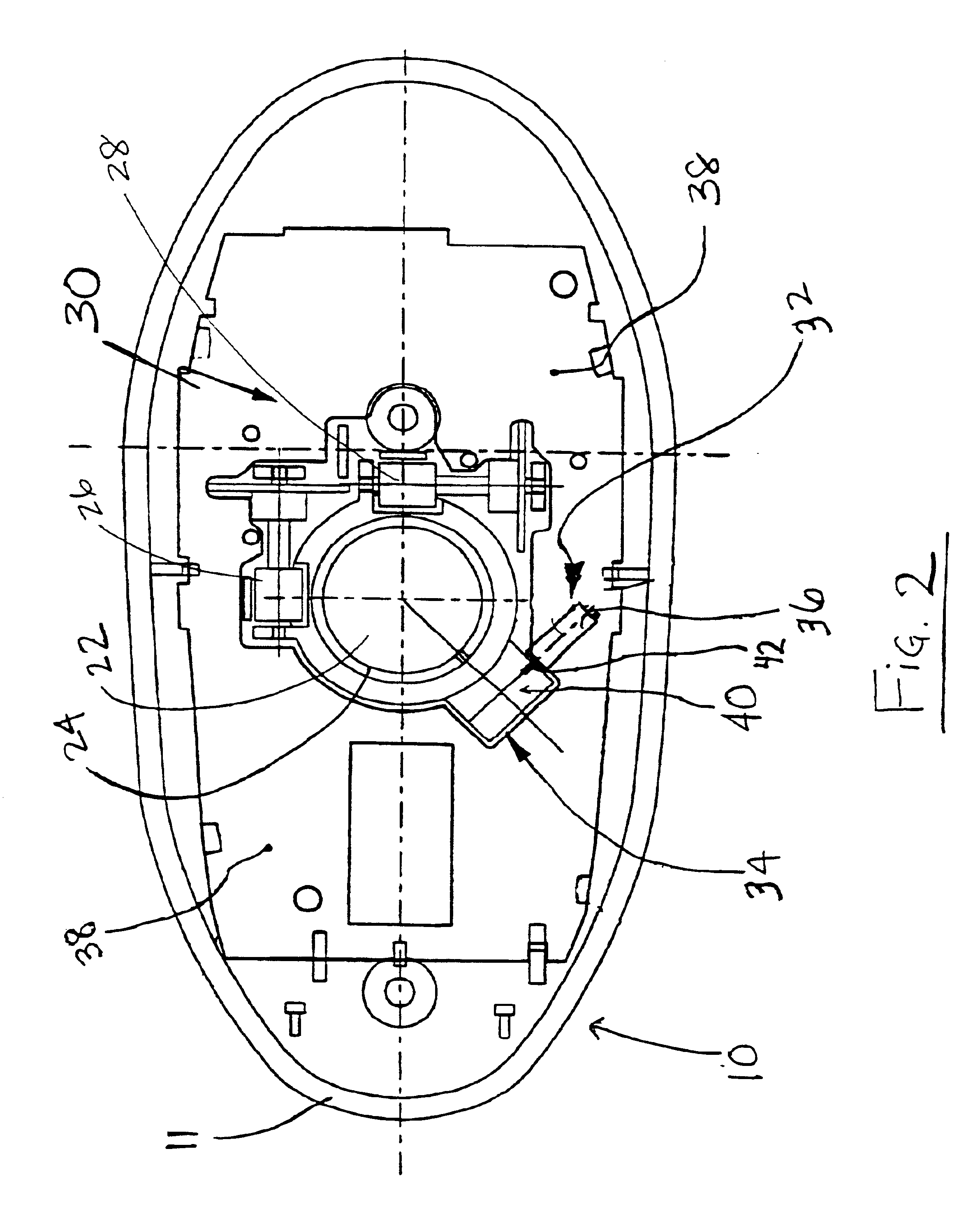
InactiveUS20090231275A1Easy to rememberGreat degree of comfortCathode-ray tube indicatorsDetails for portable computersVirtual screenEngineering
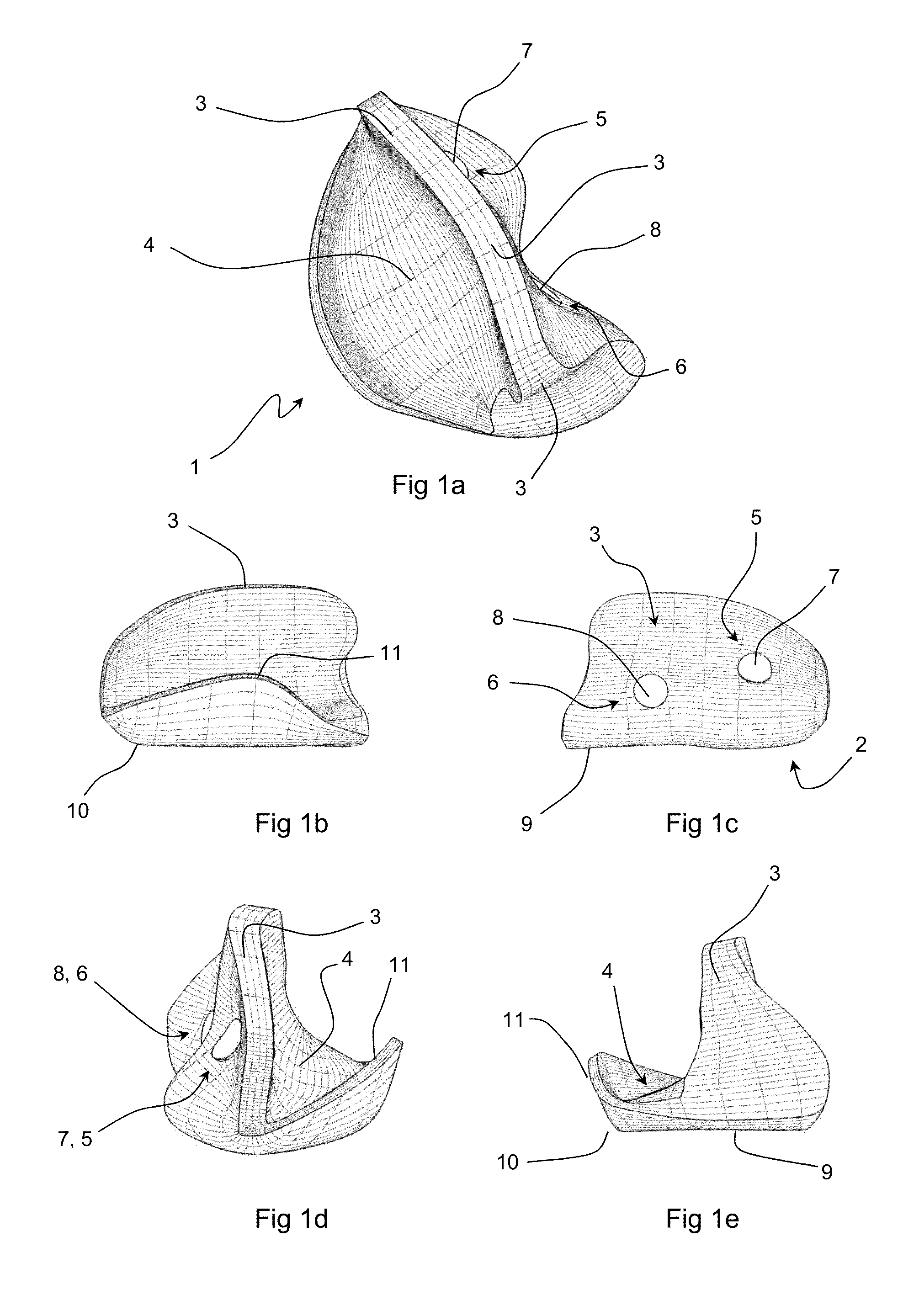
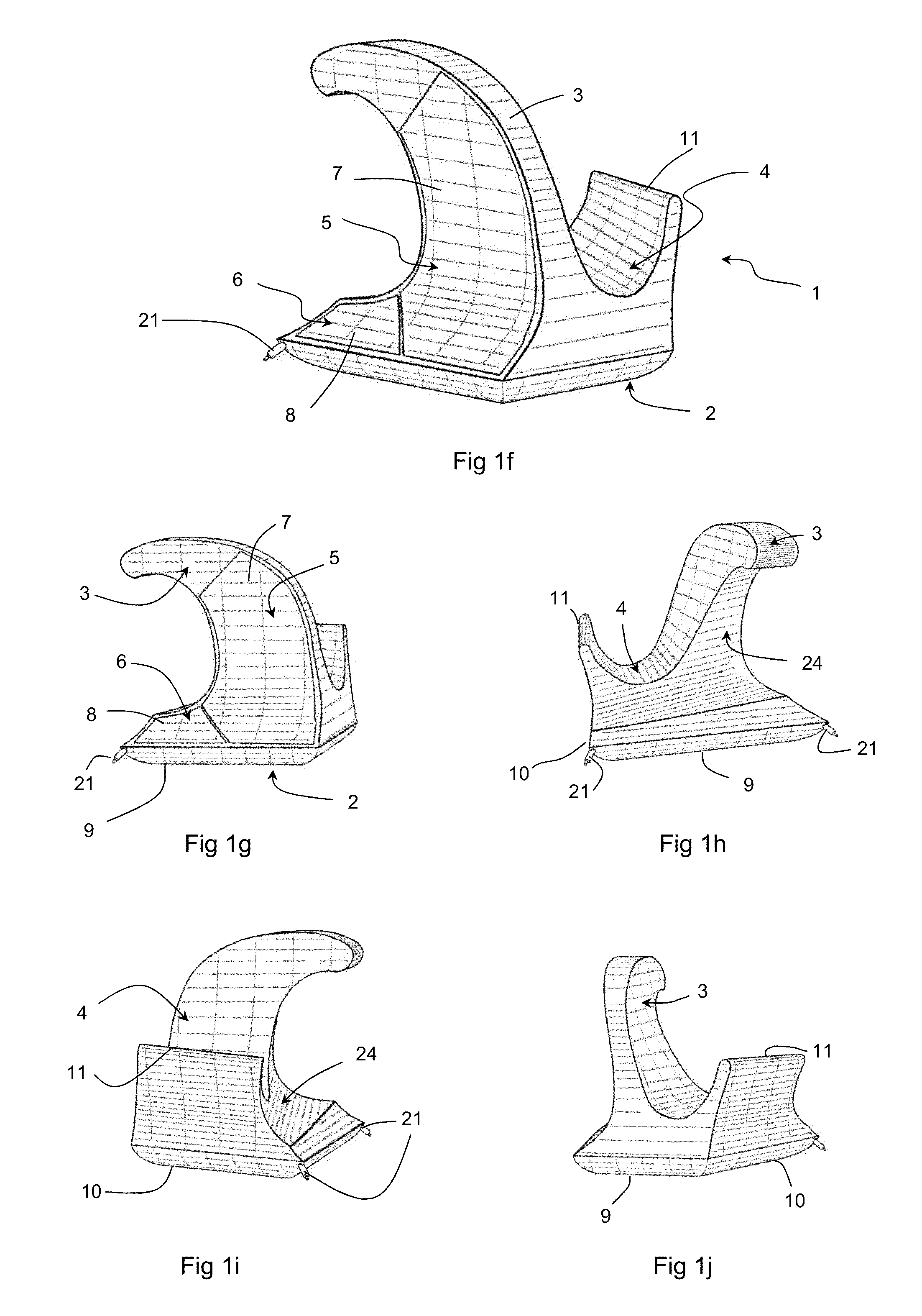
A computer pointing device including: a base portion with a lower surface adapted for sliding across a work surface, a spine portion, projecting substantially upward from said base portion and having a thumb-engaging surface on a first lateral side of the spine and at least fingertip-engaging surface on a second lateral side of the spine opposing said first lateral side. A keyboard with an altered arrangement of function of keys, such as an enlarged or truncated appearance in accordance with keys being re-mapped to sensors on a pointing device. A keyboard with a virtual screen display, which may be made semi-transparent by activating a sensor on a pointing device. A computer with a recess capable of accommodating a mouse device. A locked scrolling or zooming means, using any pointing device, in which scrolling or zooming in a defined direction is proportional to the distance travelled by the device, irrespective of direction of movement of the device.
Owner:SWIFTPOINT
Method, system and program product for augmenting an image of a scene with information about the scene
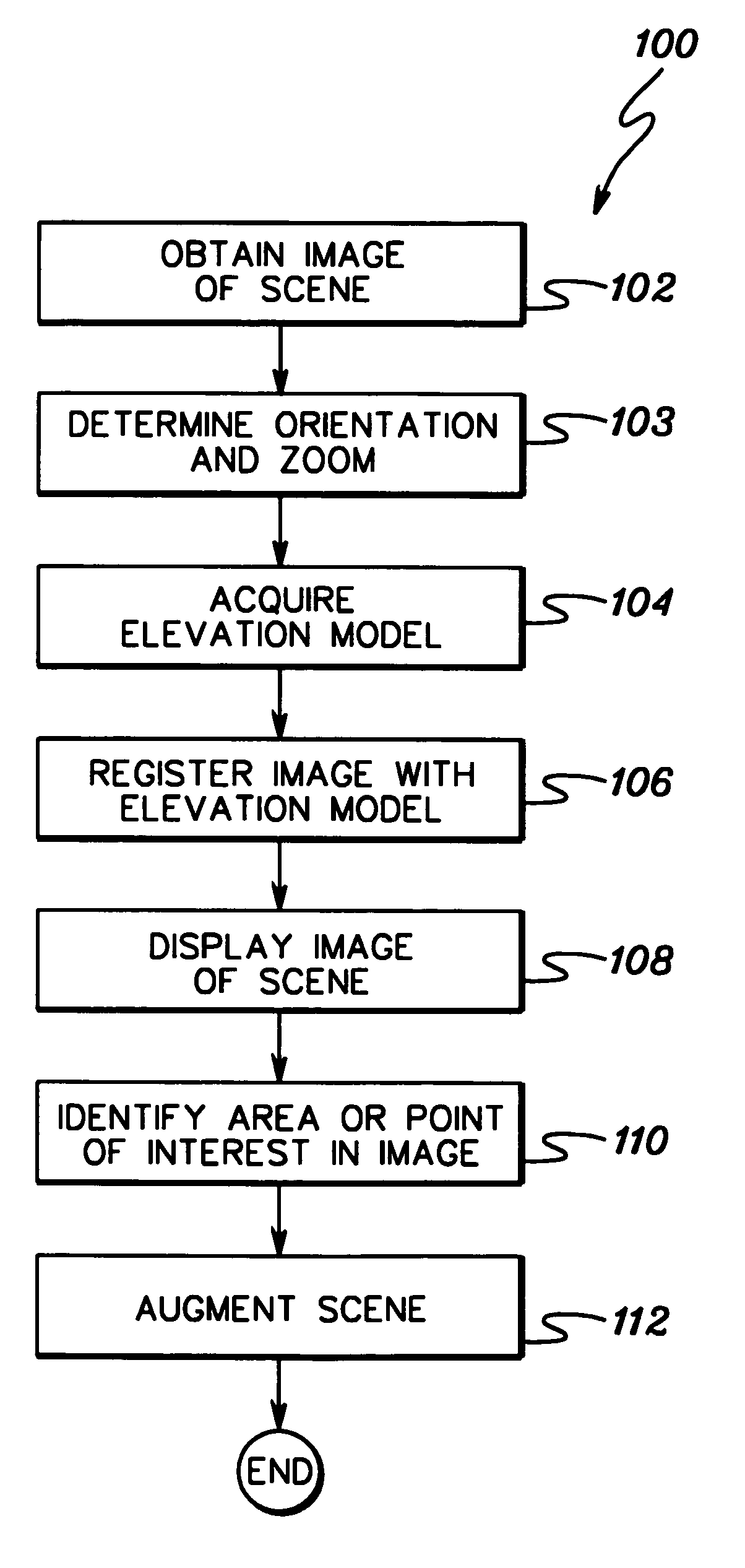
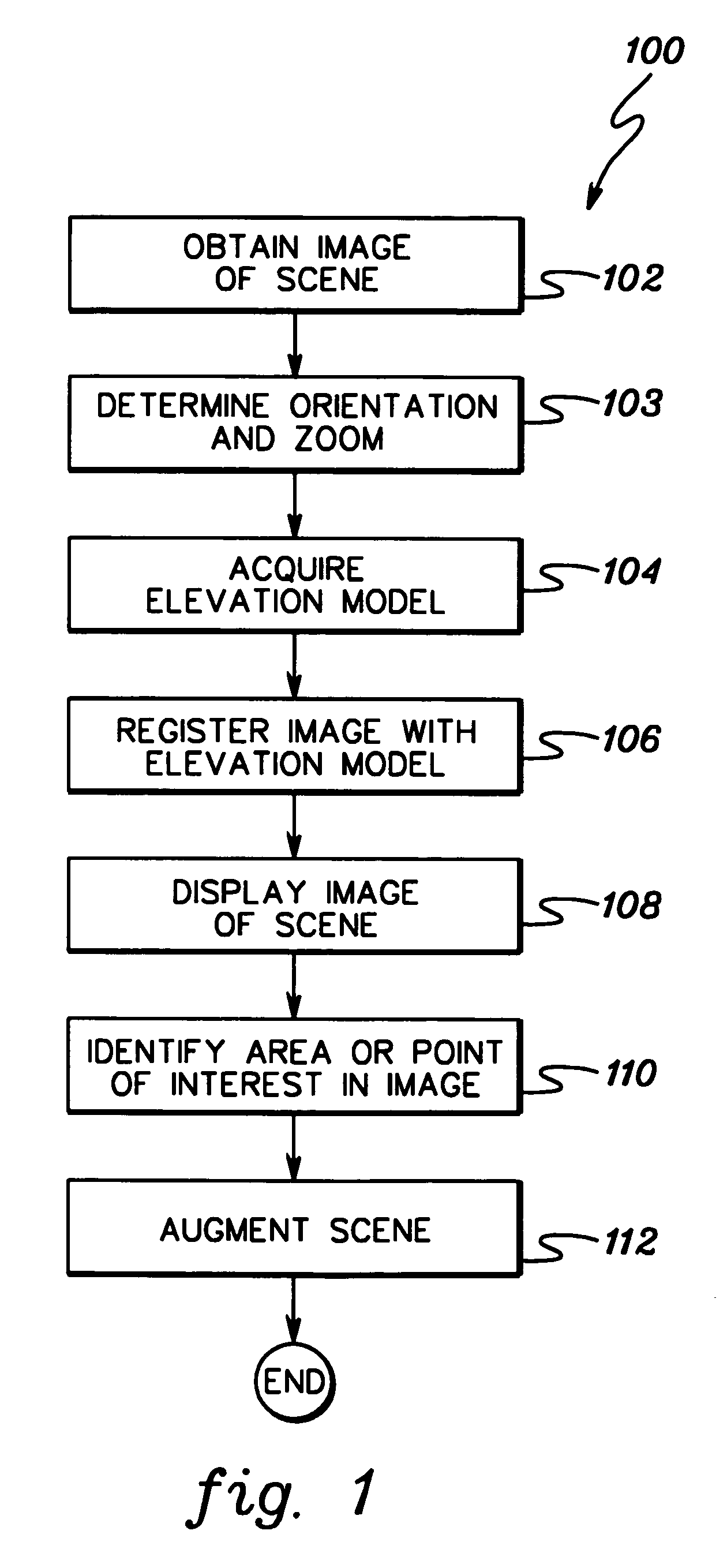
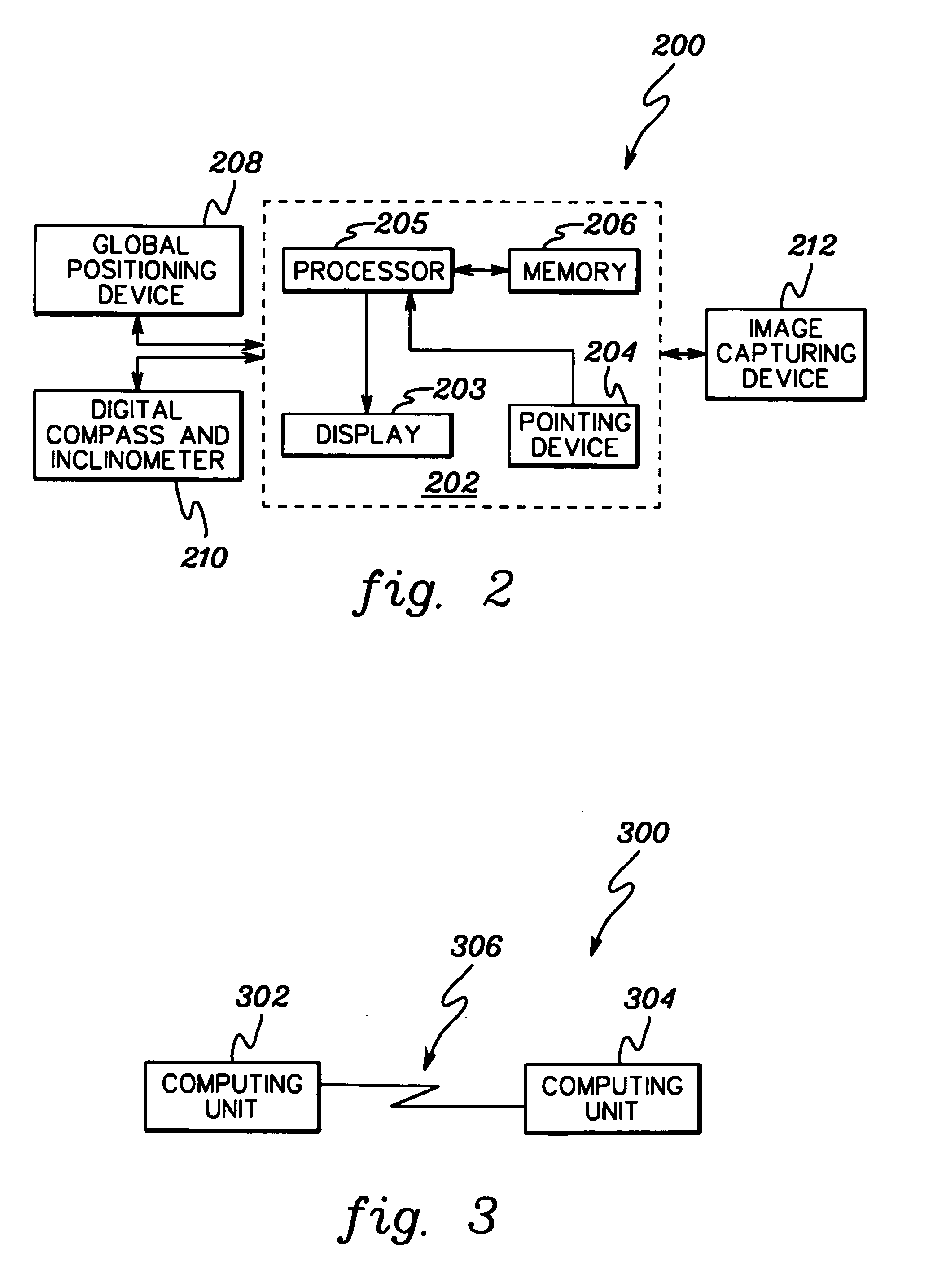
InactiveUS6930715B1Enhance the imageEasy to useTelevision system detailsNavigation by speed/acceleration measurementsComputer visionDigital image
A fixed or mobile image capturing device, coupled to a first computer, is remotely controlled over a global computer network by a second computer, and obtains a digital image of a scene. The first computer acquires a digital elevation model of the scene, which is data for creating a three-dimensional perspective model of the scene in two dimensions based on data corresponding, and registers the image with the digital elevation model. The registered digital image is provided to the second computer over the global computer network. When a user at the second computer points to an area of the registered image, the first computer augments the image provided with at least some information corresponding to the area pointed to.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Self-powered cordless mouse
InactiveUS6903725B2Extended operating timeIncorporated into computer-pointing devices inexpensivelyCathode-ray tube indicatorsInput/output processes for data processingEngineeringPointing device
A self-powered computer-pointing device includes a housing and a roller ball accommodated within the housing. At least a portion of the roller ball is exposed through an opening in the housing to allow the roller ball to contact a surface on which the computer-pointing device rests. Movement of the computer-pointing device across the surface imparts rotation of the roller ball. A sensing mechanism senses movement of the roller ball and generates x-y movement signals corresponding to movement of the computer-pointing device across the surface. The sensing mechanism conveys the x-y movement signals to a host computer. A power generating mechanism is coupled to the roller ball and converts rotational movement of the roller ball into electrical energy that is used as power by the computer-pointing device.
Owner:NACSON SABATINO
Methods and apparatus for mouse-over preview of contextually relevant information
InactiveUS20060095424A1Mitigate challengeReduce problemsDigital data information retrievalSpecial data processing applicationsRelevant informationMouseover
Challenges to the analysis of search results may be mitigated by offering preview information when users navigate a computer-pointing device over pre-designated areas of a search result page. A separate icon in the pre-designated area enhances the advantages by providing intuitive preview ability with seamless and natural control over a variety of preview options, such as the type of preview information and the manner in which it is presented. In addition, while operating a preview-enabled search result page, users' behavior provides data and attributes, which may be re-incorporated into the searching algorithm to improve the relevancy of search results.
Owner:IAC SEARCH & MEDIA
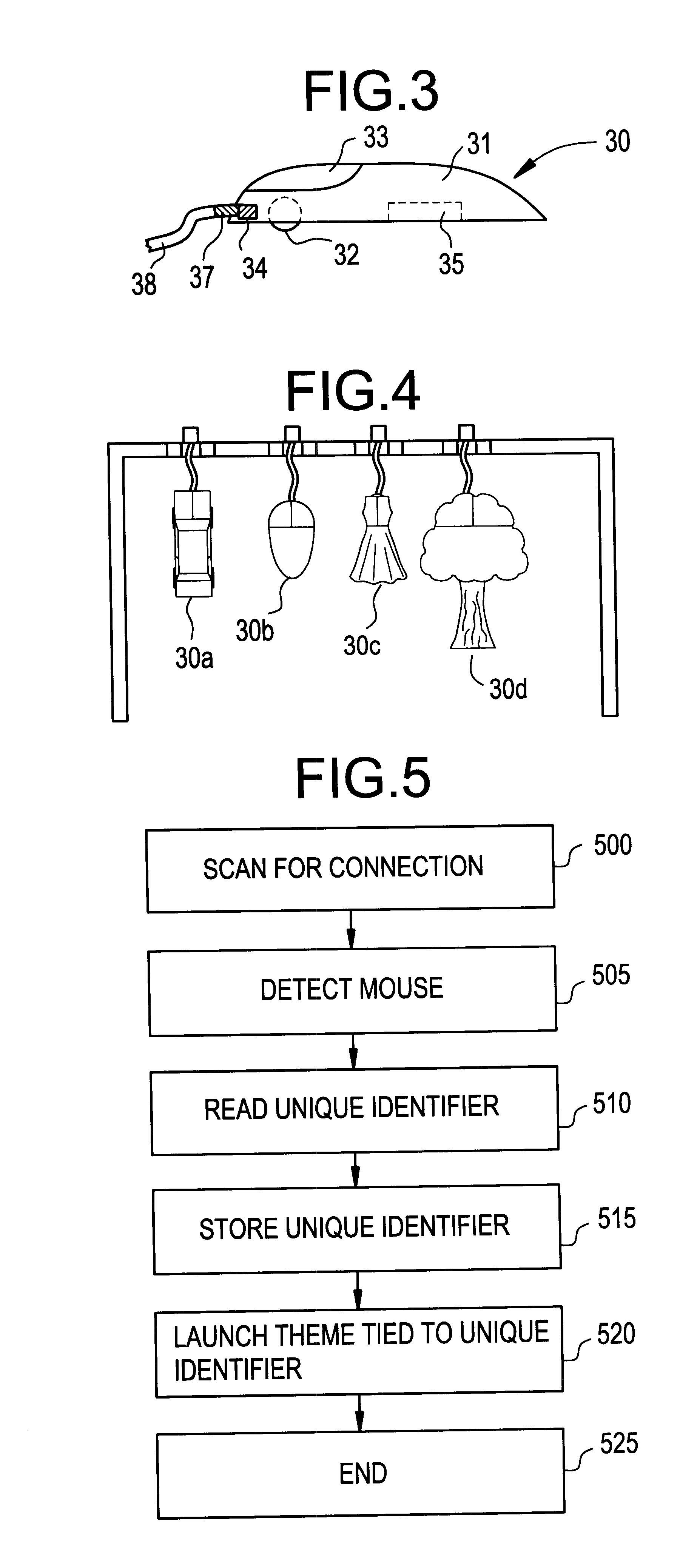
Computer pointing device having theme identification means
InactiveUS6392671B1Easy to removeEasy to replaceDigital data processing detailsCathode-ray tube indicatorsGraphicsGraphical user interface
A pointing device operable with a computer system having a graphical user interface. The pointing device includes a unique identifier that is associated with the pointing device, wherein a theme of the graphical user interface is automatically changed in accordance with the unique identifier. The theme may be a desktop theme. The unique identifier may also initiate a security protocol.
Owner:RED HAT
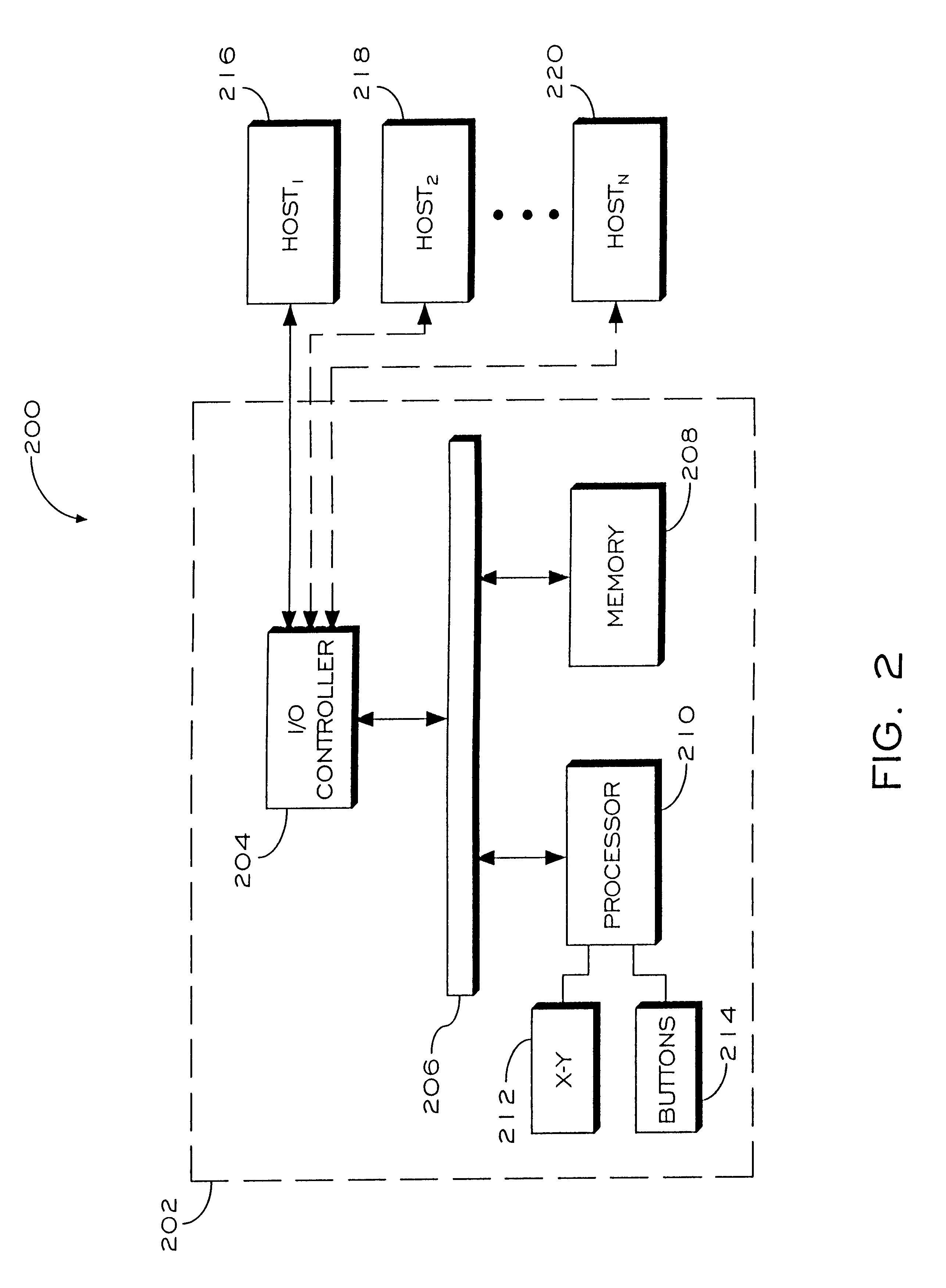
Hybrid presentation controller and computer input device
InactiveUS7061468B2Cathode-ray tube indicatorsInput/output processes for data processingUser inputHand held
An input device having a housing; a pointing device coupled with the housing having a plurality of buttons; a scrolling element coupled with the housing; and a module for detecting user input for operating the input device in at least a first mode and a second mode, where in the first mode, the input device operates as a tabletop computer pointing device, and where in the second mode, the input device operates as a hand-held presentation device used to control a computer-based presentation.
Owner:LOGITECH EURO SA
Computer pointing input device
InactiveUS20080180395A1Cathode-ray tube indicatorsInput/output processes for data processingDisplay deviceMobile device
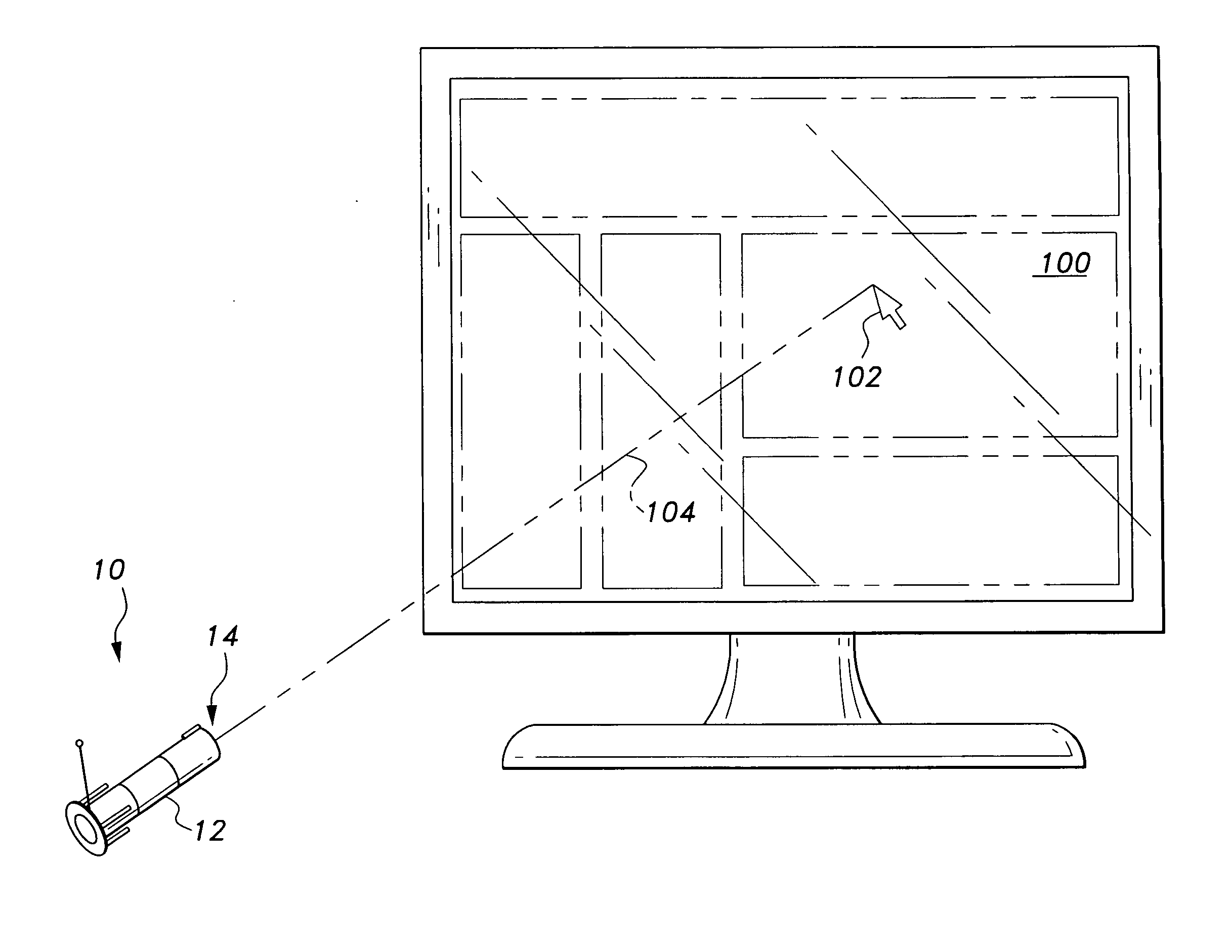
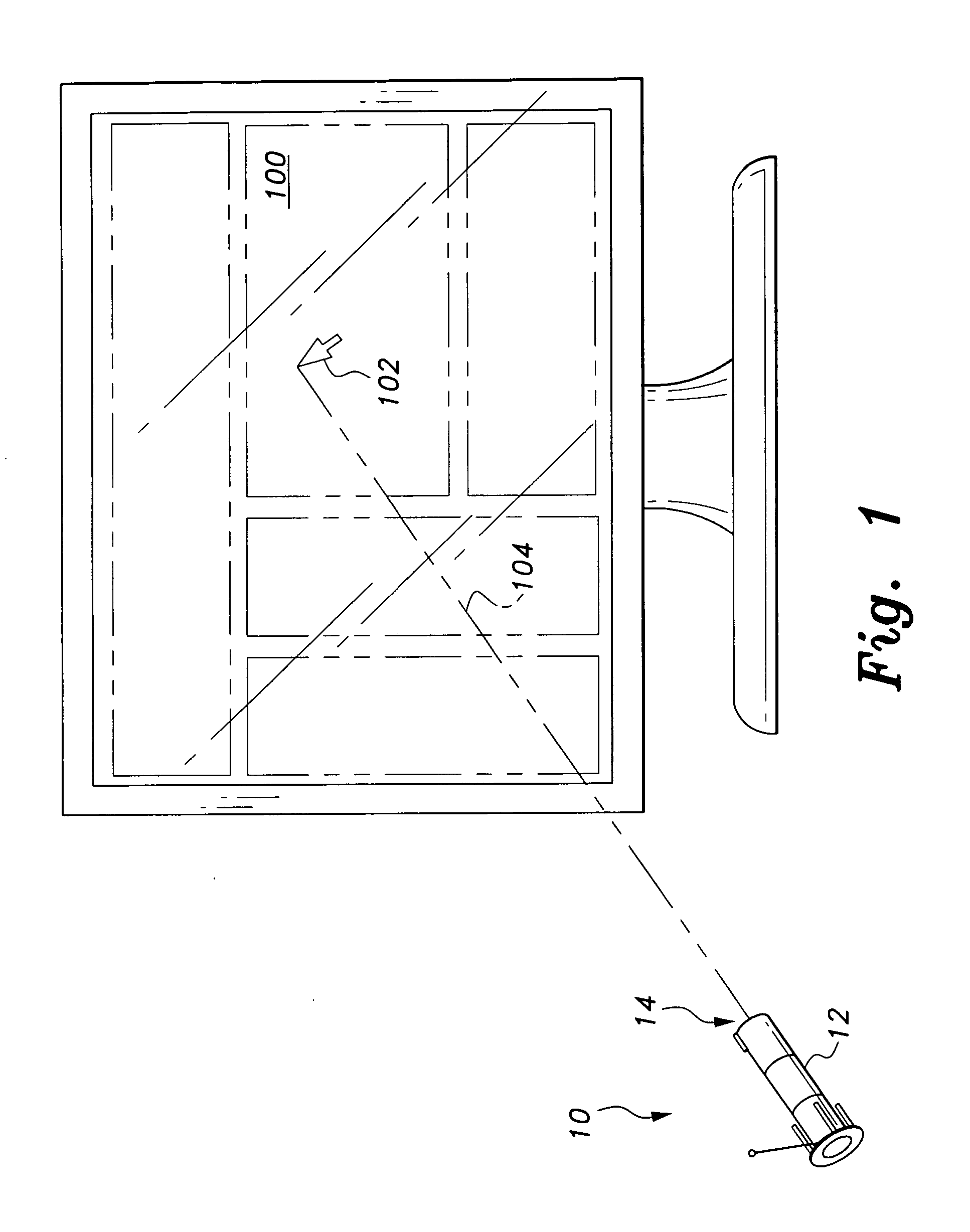
The computer pointing input device allows a user to determine the position of a cursor on a computer display. The position of the input device in relation to the display controls the position of the cursor, so that when a user points directly at the display, the cursor appears at the intersection of the display and the line of sight from of the input device. When the device is moved, the cursor appears to move on the display in exact relation to the input device. In addition, a cursor command unit allows the user to virtually operate the input device wherein changes in the position of the device allow the user to spatially invoke mouse functions. The computer pointing input device is designed to operate with a computer having a processor through a computer communication device.
Owner:NEW ERA IP
Pointing device with storage
InactiveUS6933919B1Simple methodInterprogram communicationCathode-ray tube indicatorsFloppy diskRemovable media
A computer pointing device employs memory for the storage of data allowing information to be copied from one computer to another without the need for a network or removable media such as a floppy disk. In a first aspect, the pointing device may be linked to multiple computers wherein the connection to the pointing device may be toggled from one computer to another. The connection method may be via a cabled interface or wireless interface, such as a radio frequency link. In a second aspect, the device may by physically moved from one computer to another. In a preferred embodiment, the pointing device is a universal serial bus device.
Owner:GATEWAY
Apparatus for entering data into a computer
InactiveUS6480184B1Cathode-ray tube indicatorsInput/output processes for data processingPointing deviceComputer Point
The invention, in one embodiment, is a computer pointing device that includes: (1) a housing; (2) a first depressible button supported by the housing which, when pressed, causes a first signal to be generated; (3) a second depressible button supported by the housing which, when pressed, causes a second signal to be generated; (4) a cable coupled to transmit the first signal and the second signal; and (5) a lever pivotably coupled to the housing at one end.
Owner:MICRON TECH INC
Computer mouse peripheral
InactiveCN101111817AInput/output for user-computer interactionDetails for portable computersPhysical medicine and rehabilitationVirtual screen
A computer pointing device including: a base portion with a lower surface adapted for sliding across a work surface, a spine portion, projecting substantially upward from said base portion and having a thumb-engaging surface on a first lateral side of the spine and at least one index fingertip and / or middle fingertip-engaging surface on a second lateral side of the spine opposing said first lateral side. A keyboard with an altered arrangement of function of keys, such as an enlarged or truncated or no spacebar or capable of an altered appearance in accordance with keys being re-mapped to sensors on a pointing device. A keyboard with a virtual screen display, which may be made semi-transparent by activating a sensor on a pointing device. A computer with a recess capable of accommodating a mouse device. A locked scrolling or zooming means, using any pointing device, in which scrolling or zooming in a defined direction is proportional to the distance travelled by the device, irrespective of direction of movement of the device.
Owner:SWIFTPOINT LTD
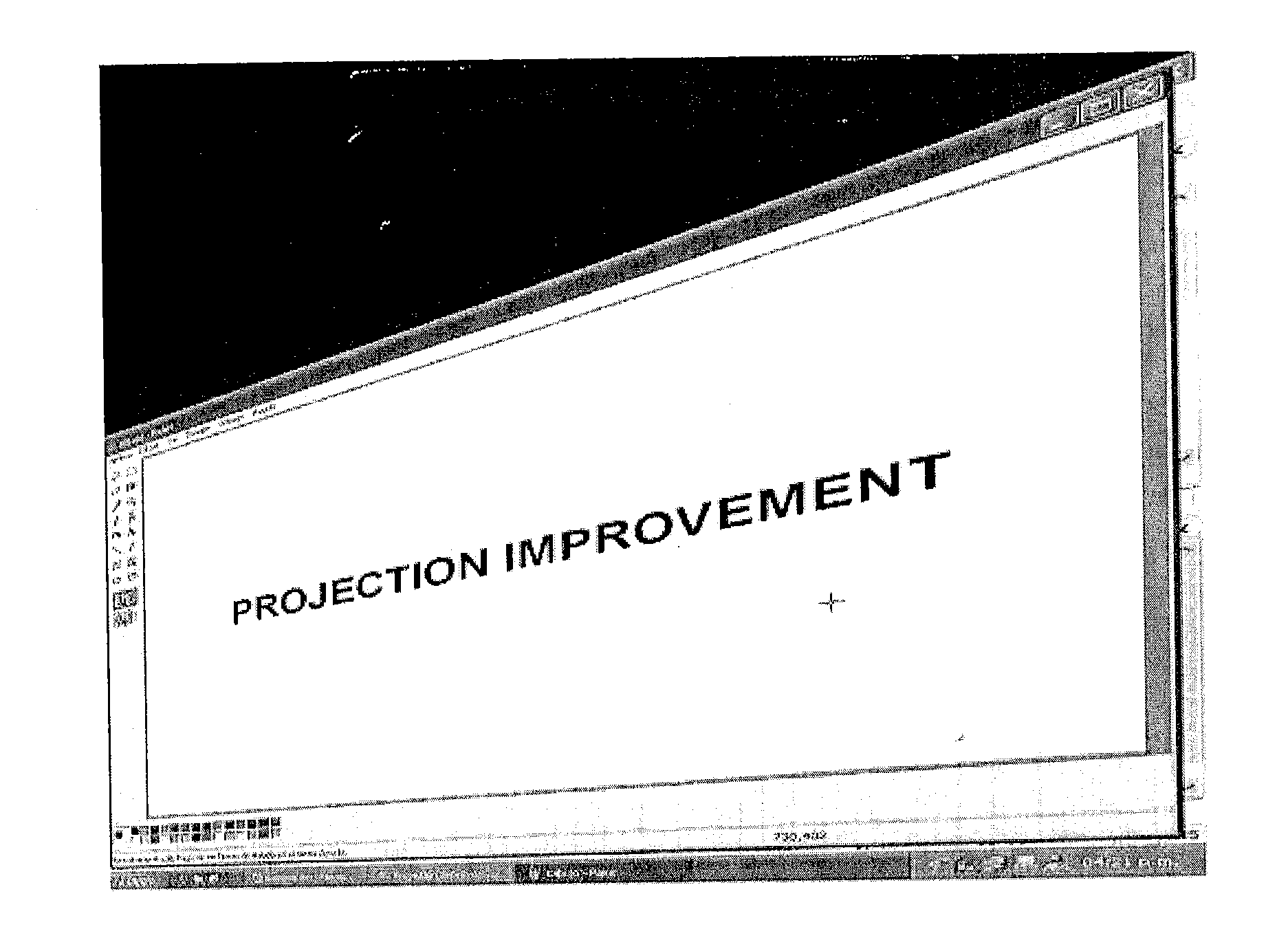
Manipulation of Projected Images
InactiveUS20070008344A1Reduce loadIncrease refresh rateTelevision system detailsGeometric image transformationRemote controlProjection image
Correction of distorted projections and other visual effects are displayed continuously for still and video images based on three-dimensional transformations that distort or overlay images projected in such a way that the displayed image manipulated. The technology used to remove the distortion is not hardware dependent, may be used with any display device, such as a projector, and is capable of interfacing with the user by remote control, a computer pointing device or any other input device capable of communicating commands to a processor for manipulation of an image.
Owner:MEDINA GERMAN
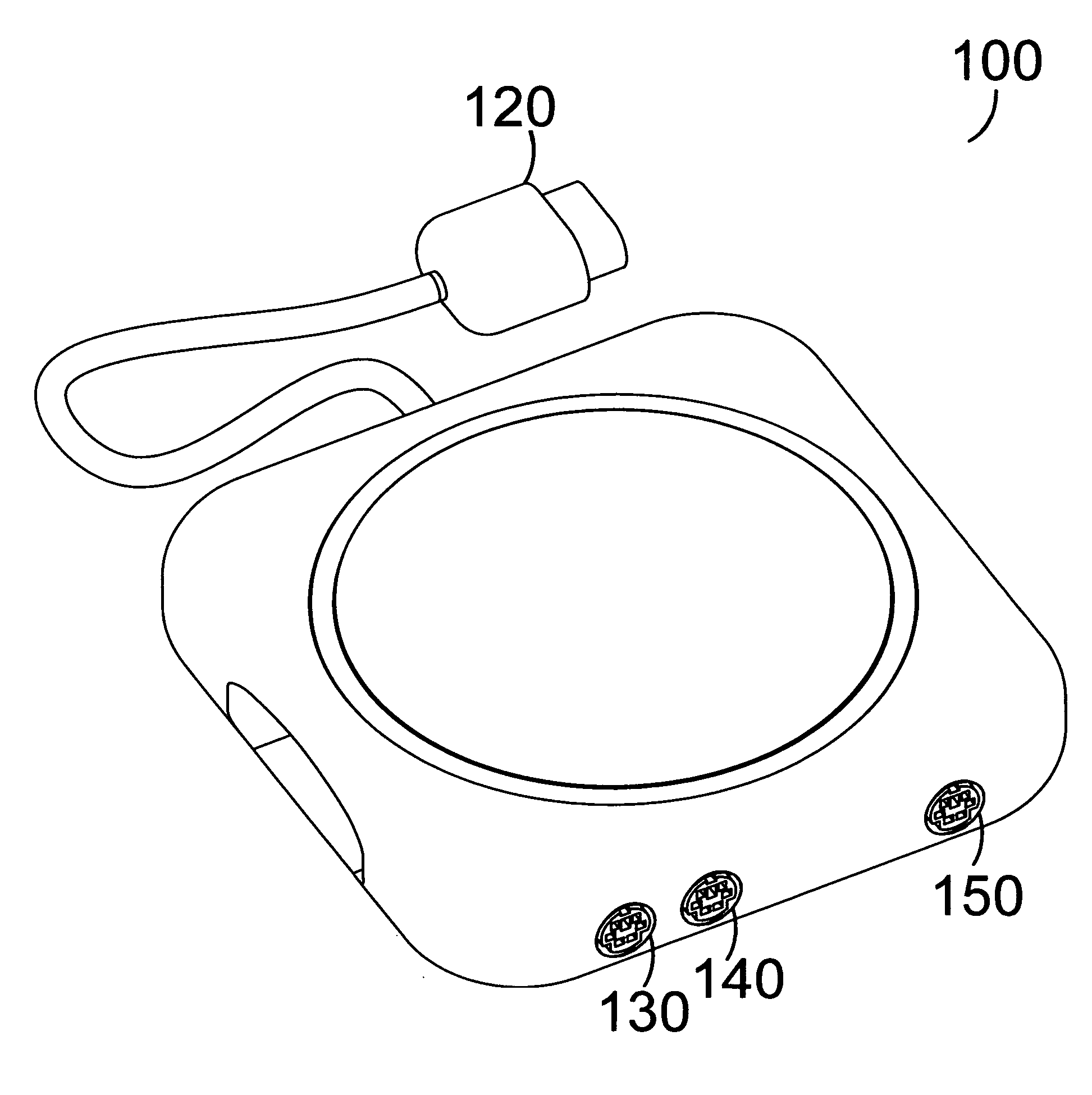
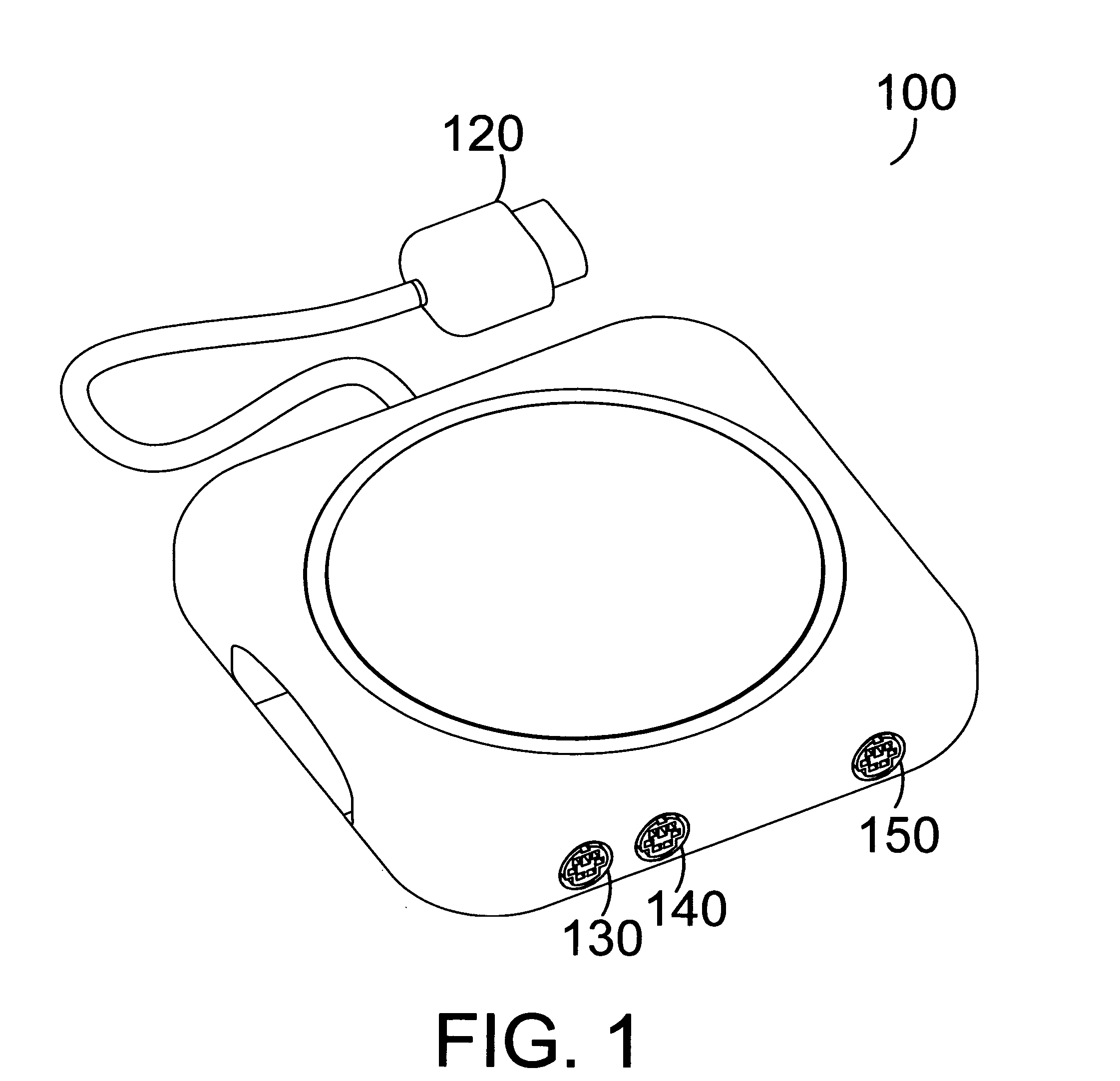
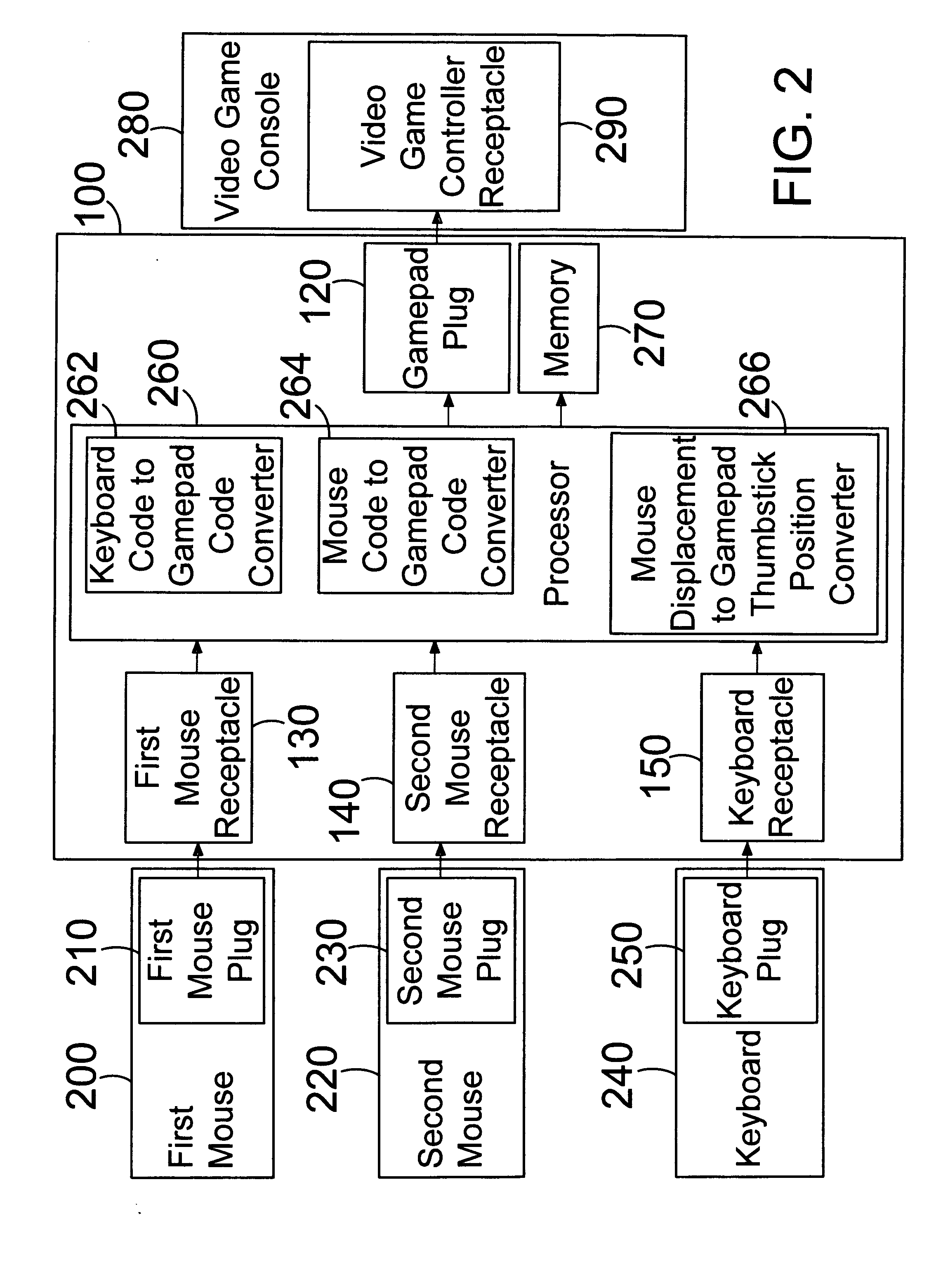
Method and apparatus for providing computer pointing device input to a video game console
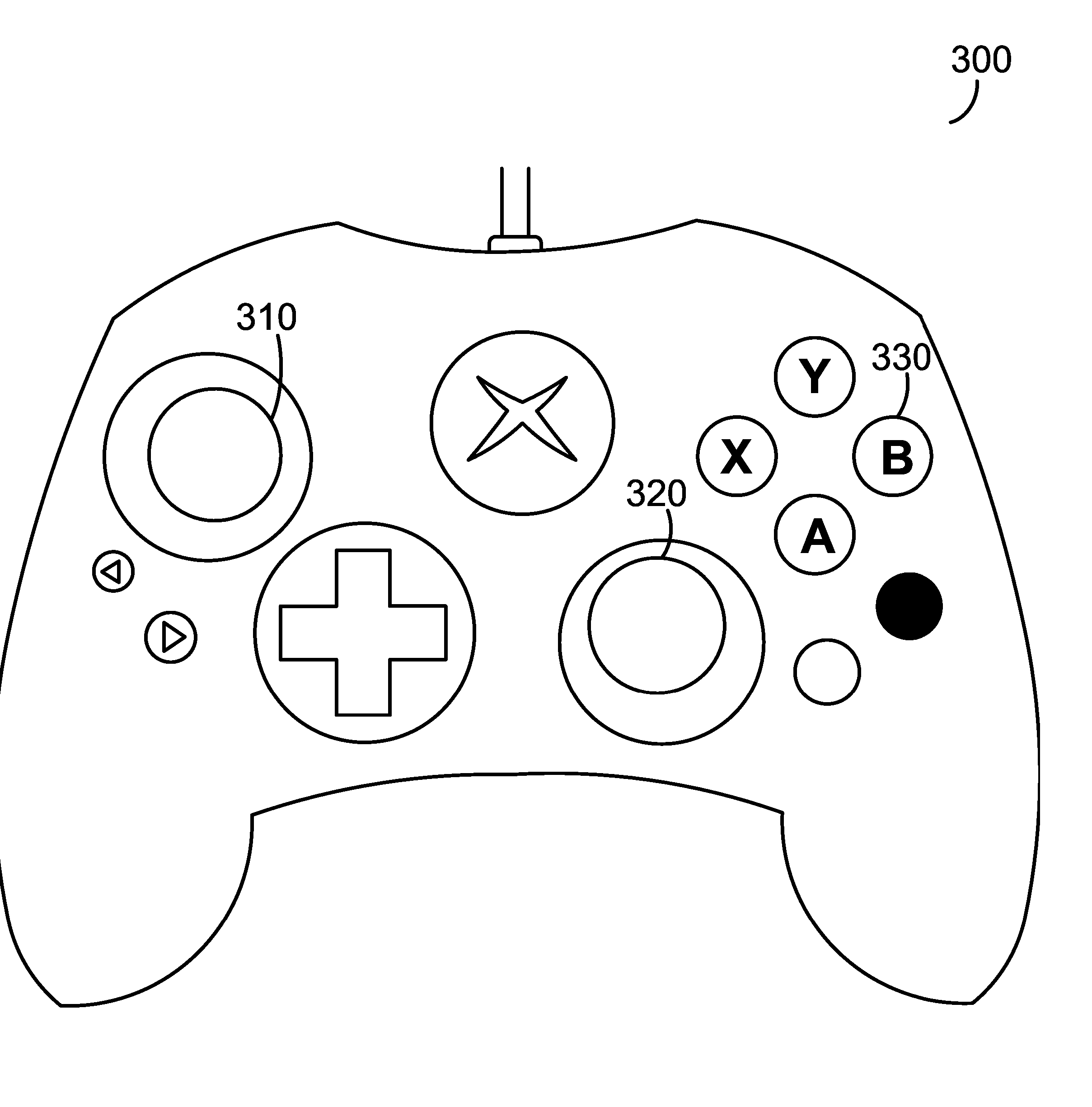
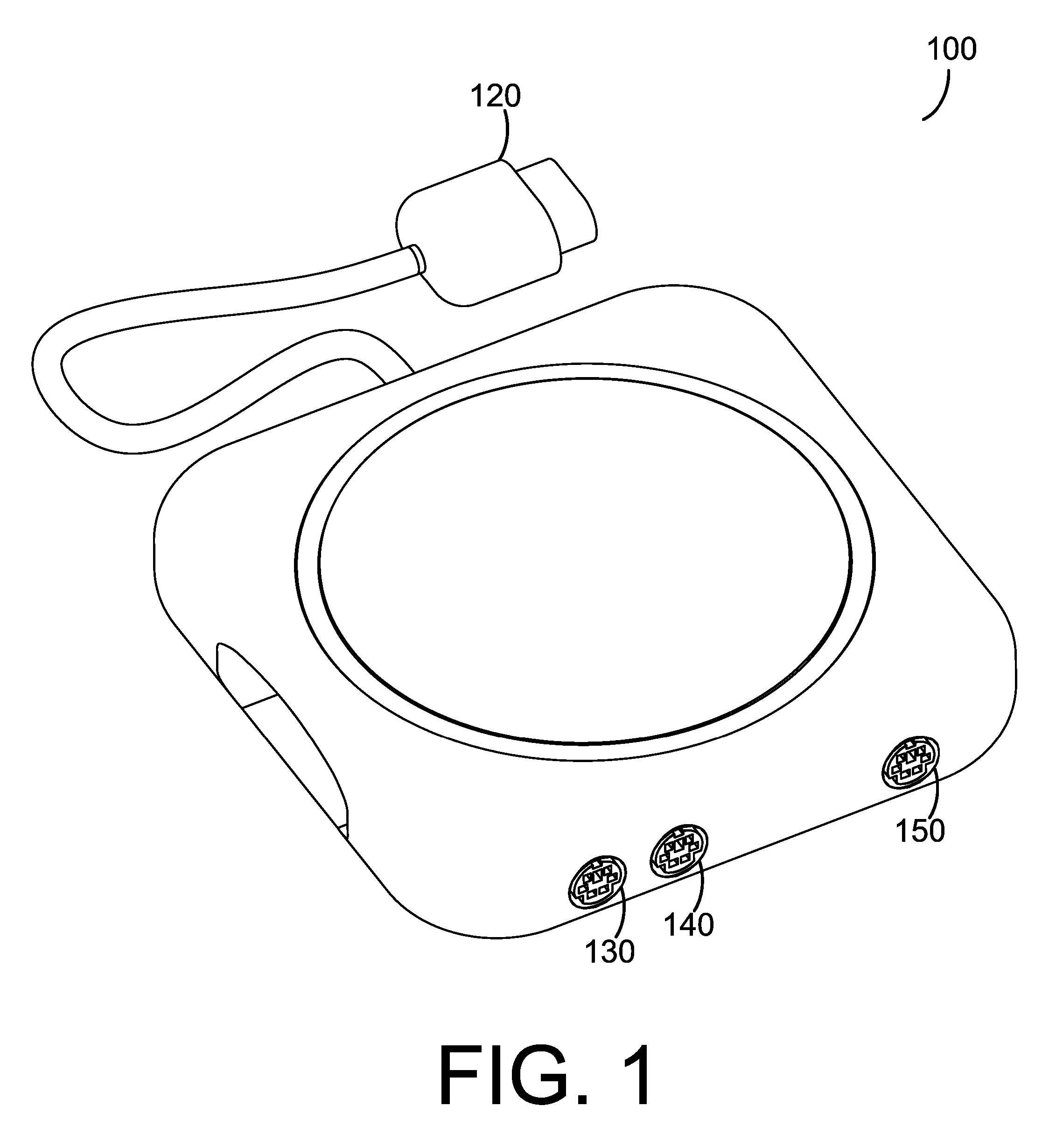
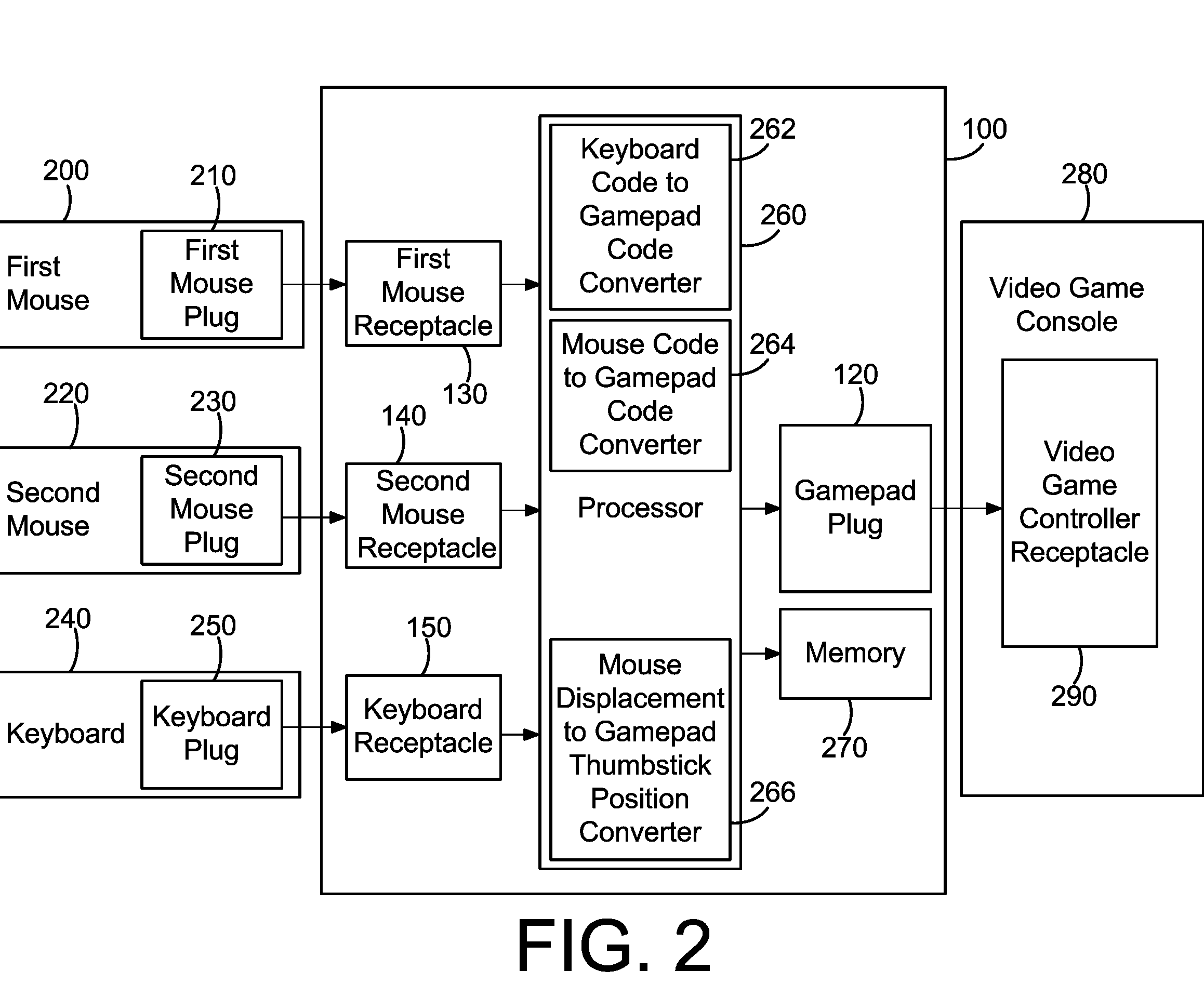
InactiveUS20050176505A1Smooth inputLess grainVideo gamesSpecial data processing applicationsPersonal computerPointing device
A method and apparatus for adapting a computer pointing device to a video game console. In one embodiment a mouse plugs into an adapter which has an output that plugs into an input of a console. The adapter receives motion data from one or more computer mice and translates this into a format compatible with a game controller for that console. This data is then output to the console which perceives the data as from a single game controller. Thus computer pointing device output, such as from a mouse, is adapted to a console such that the user can control games on that console using the mouse. Data from a computer pointing device can also be combined with data from a keyboard such that the user may play games on a console using a mouse and a keyboard, as is common on personal computers.
Owner:STANLEY MARK JOSEPH
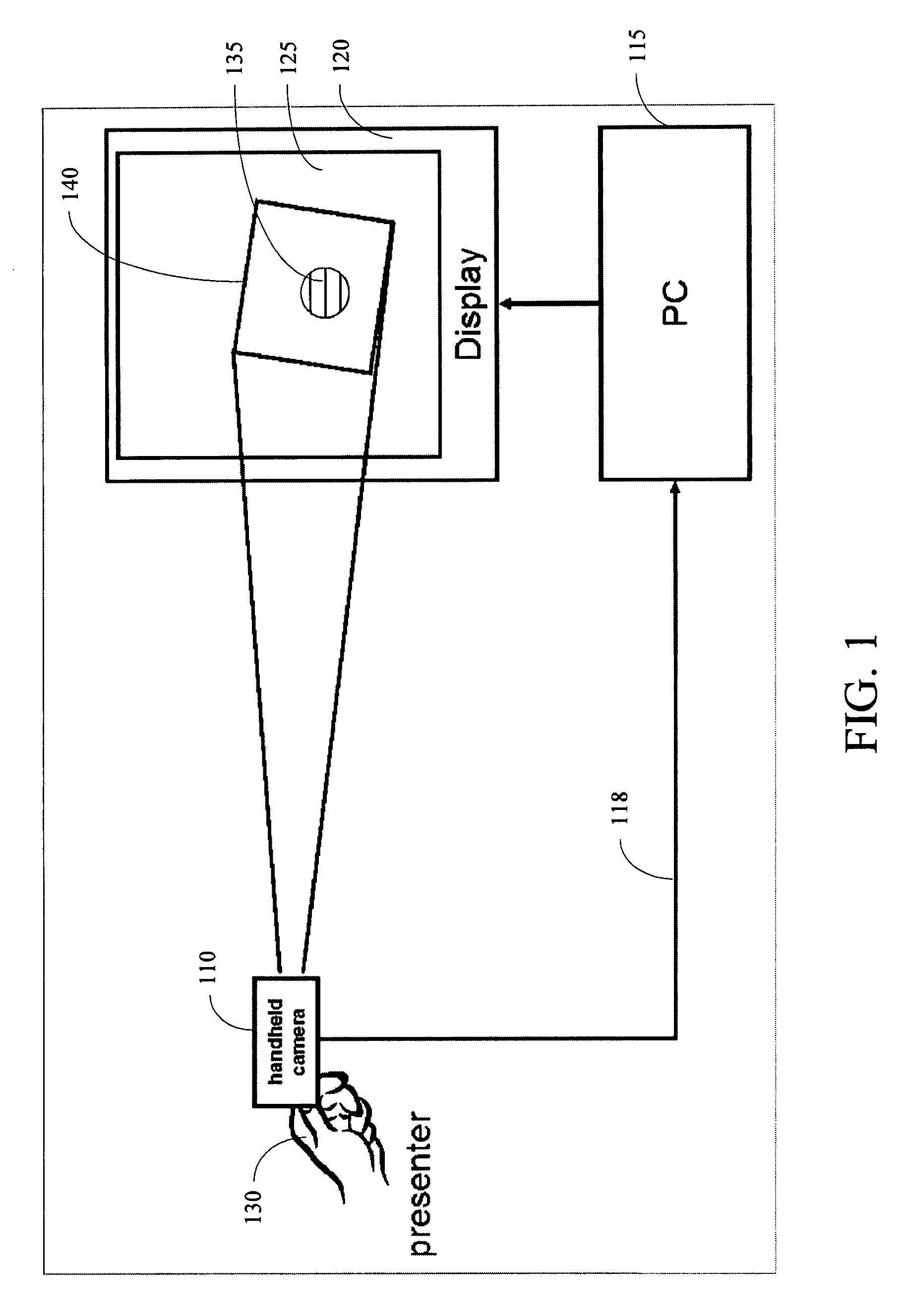
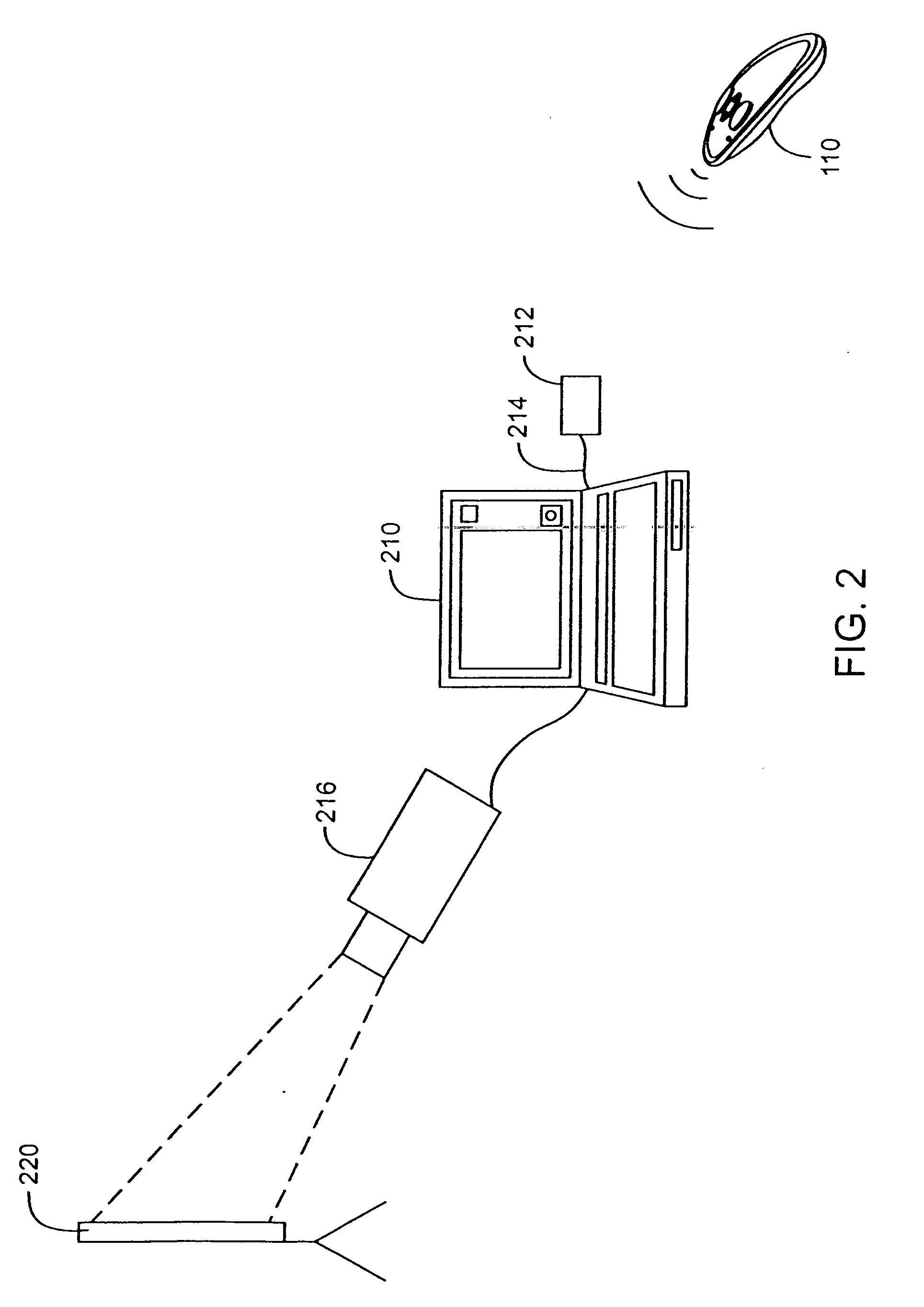
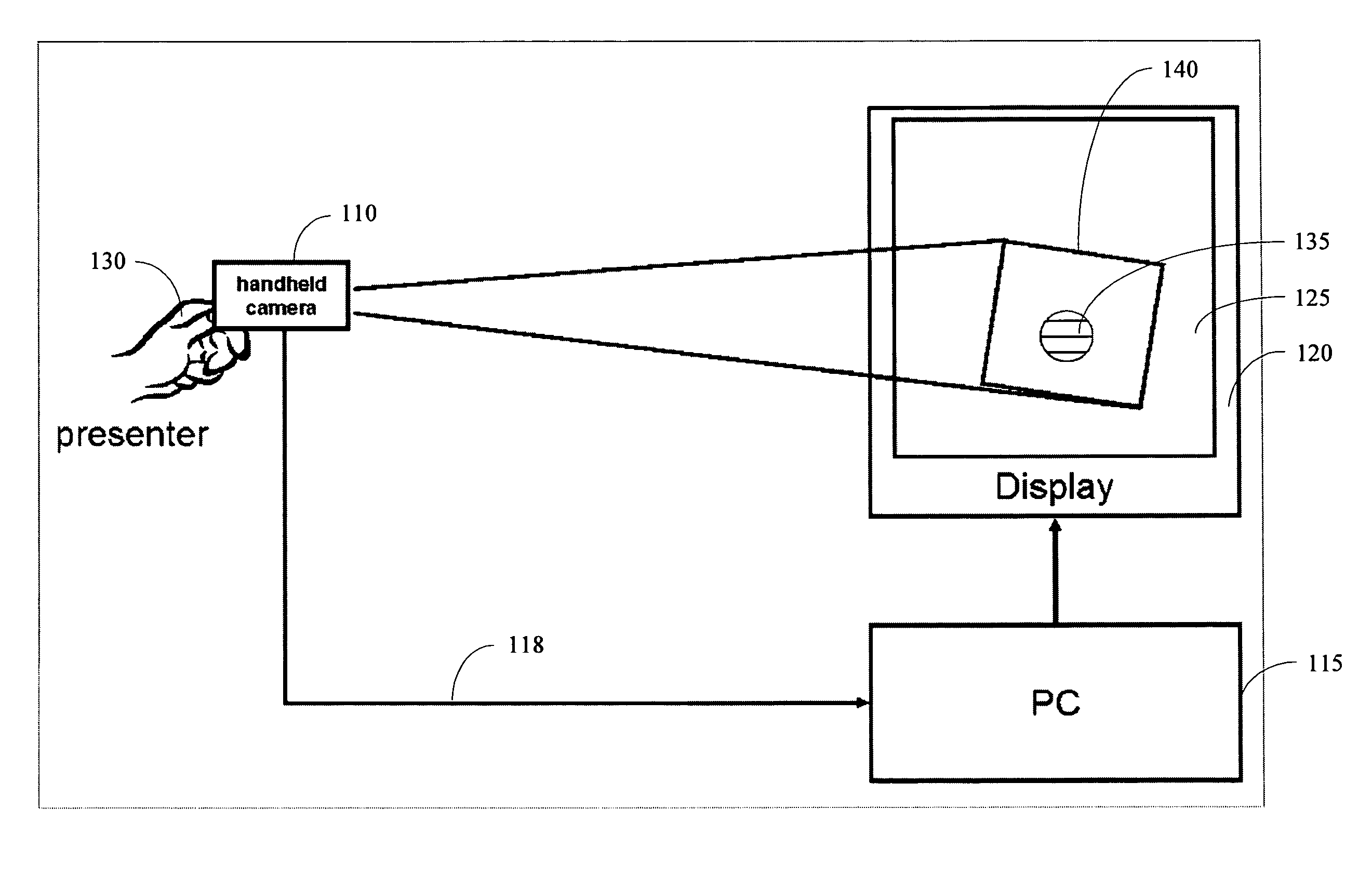
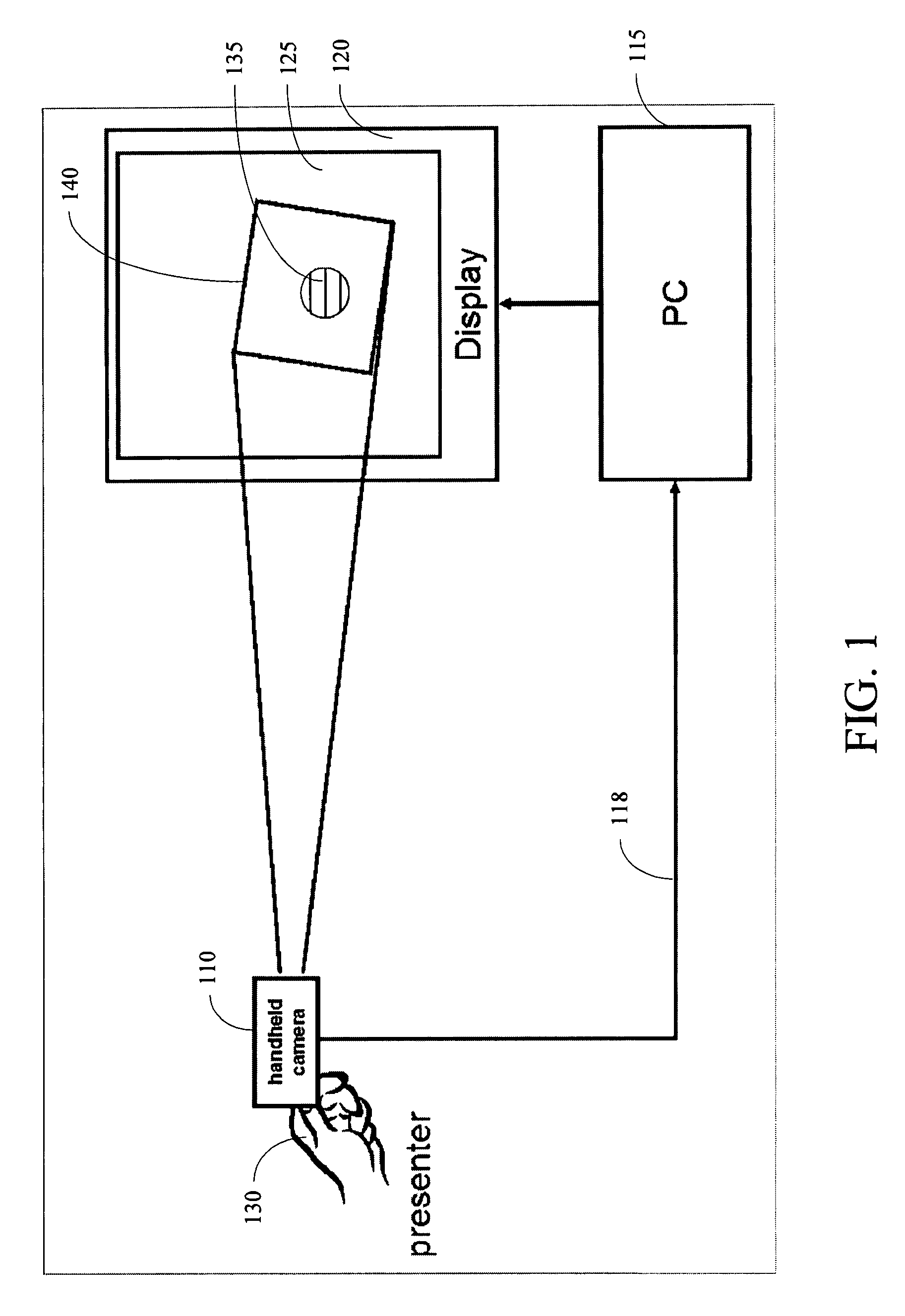
Dynamically Controlling a Cursor on a Screen when Using a Video Camera as a Pointing Device
InactiveUS20090046061A1Cathode-ray tube indicatorsInput/output processes for data processingPointing deviceOn-screen display
A system provides for controlling a cursor on a screen automatically and dynamically when using a video camera as a pointing device. A computer displays static or dynamic content to a screen. A video camera connected to the computer points at the screen. As the video camera films the screen, frames captured by the video camera are sent to the computer. A target image is displayed by the computer onto the screen and marks the position of the screen cursor of the video camera. Frames captured by the video camera include the target image, and the computer dynamically moves the target image on the screen to ensure that the target image stays in the center of the view of the video camera.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Modular assembly for a self-indexing computer pointing device
InactiveUS20050110754A1Easy to understandCathode-ray tube indicatorsInput/output processes for data processingModularityPointing device
A pointing device having a puck sub-assembly and a base sub-assembly is disclosed. The puck sub-assembly includes a moveable puck having a user sensor that detects the interaction of a user and the puck. The puck is confined to move within a puck field of motion. The puck sub-assembly includes a support member having an opening therein that determines a boundary for the puck field of motion. The base sub-assembly includes a base surface over which the puck moves, a position detector that measures the position of the puck in the puck field of motion, and an attachment mechanism. The attachment mechanism connects the base sub-assembly to the puck sub-assembly such that the puck sub-assembly is easily removed. The base surface is accessible when the puck sub-assembly is separated from the base assembly. The puck sub-assembly can also include a restoring mechanism that returns the puck to a predetermined area.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
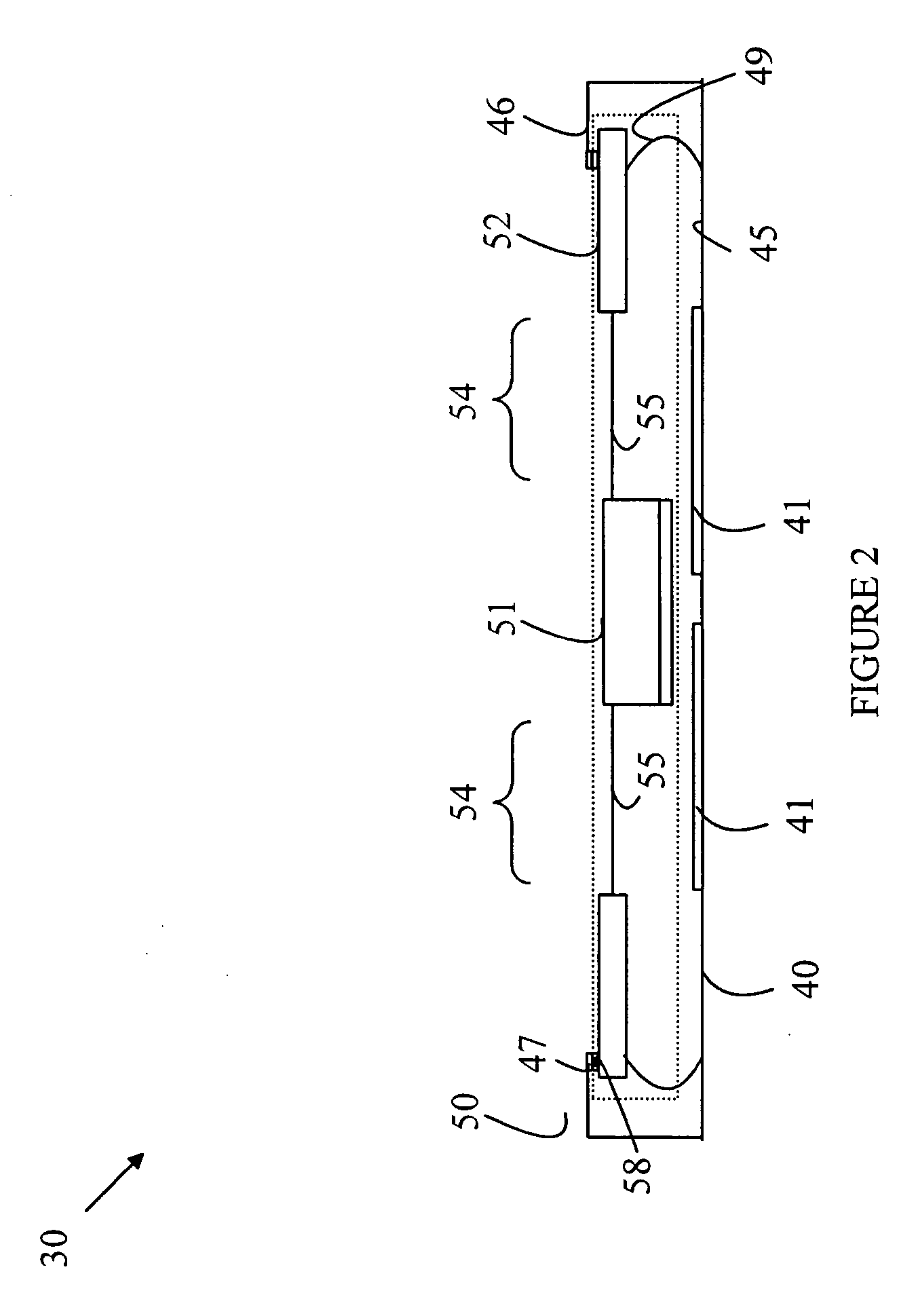
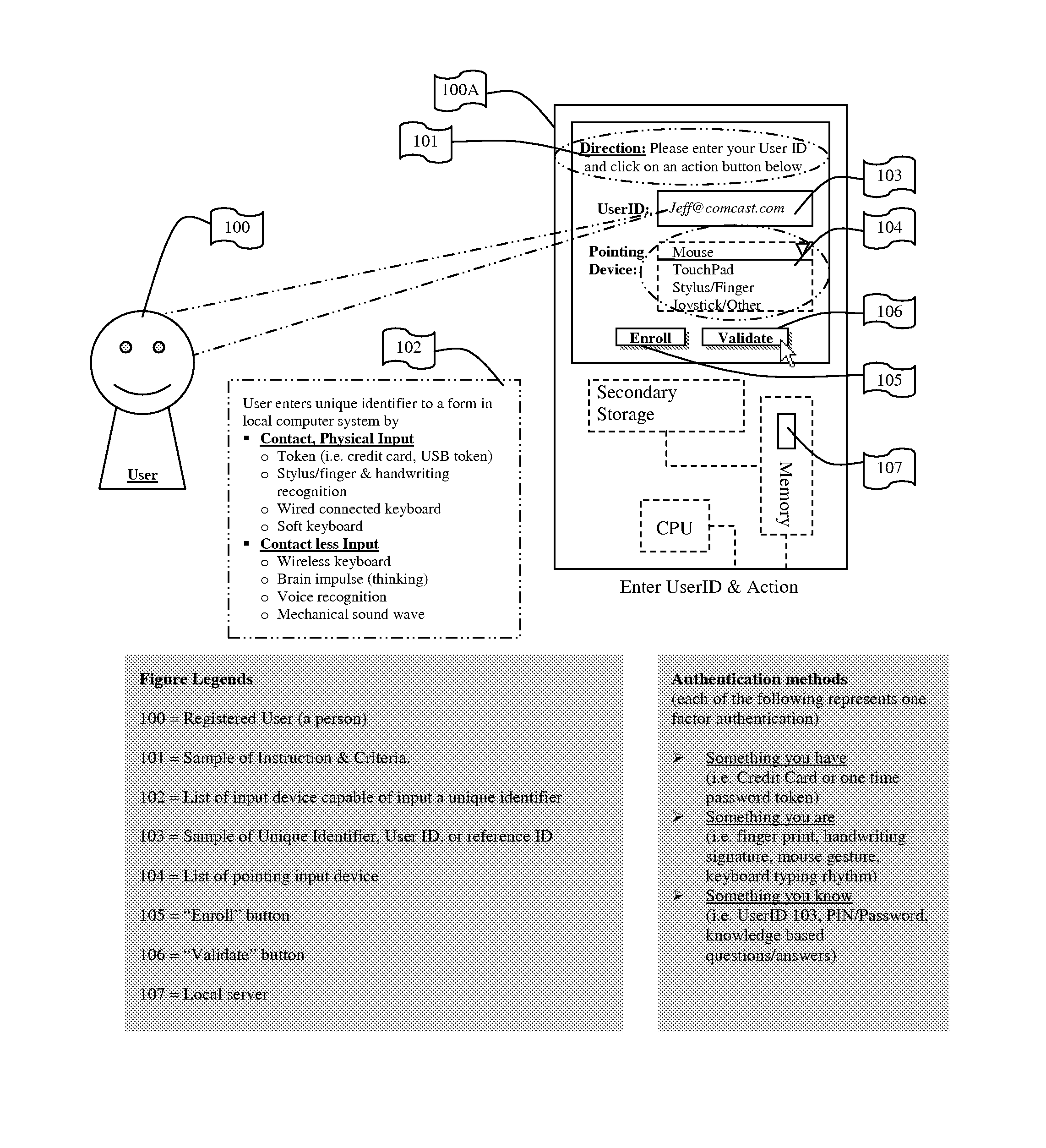
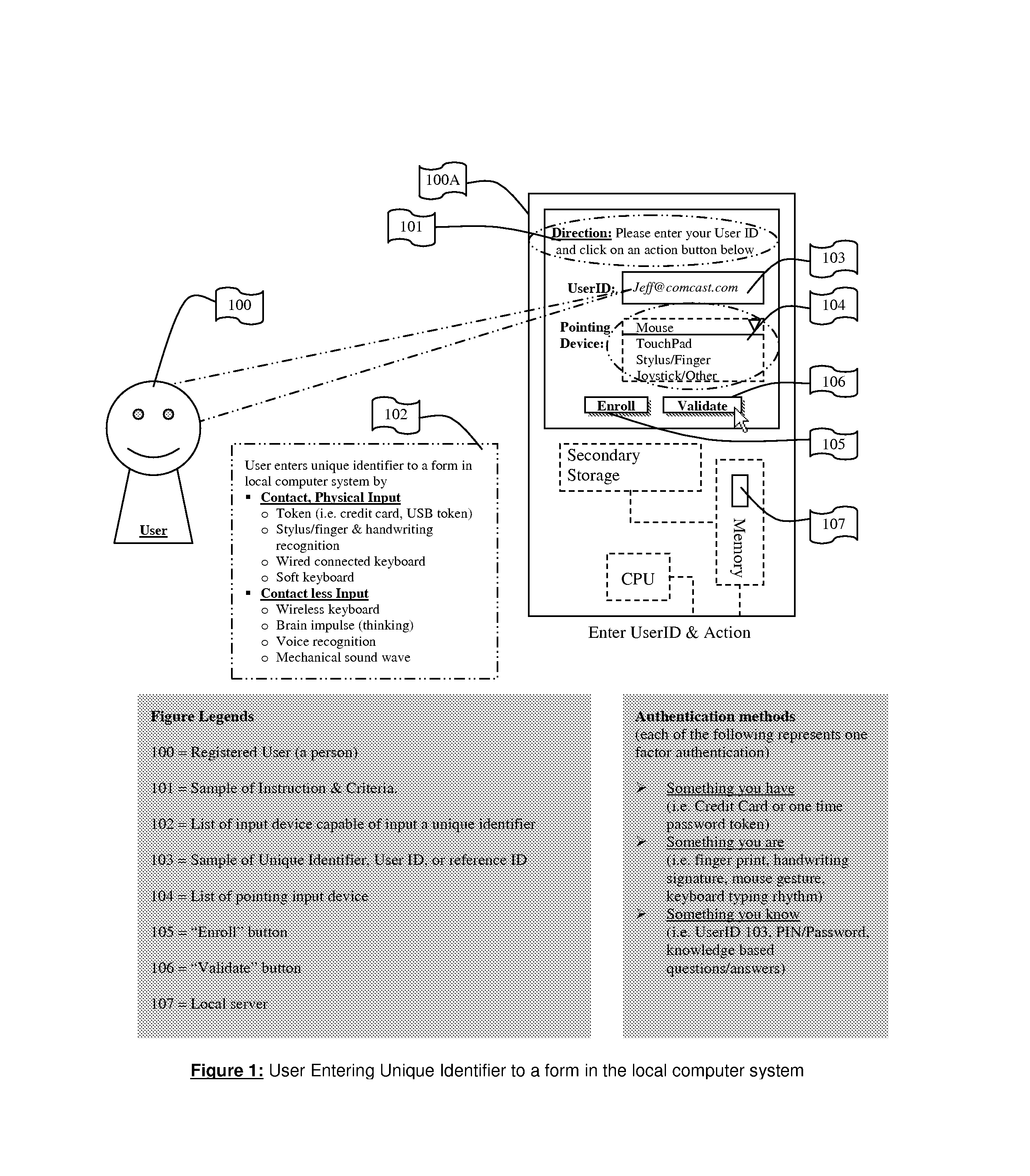
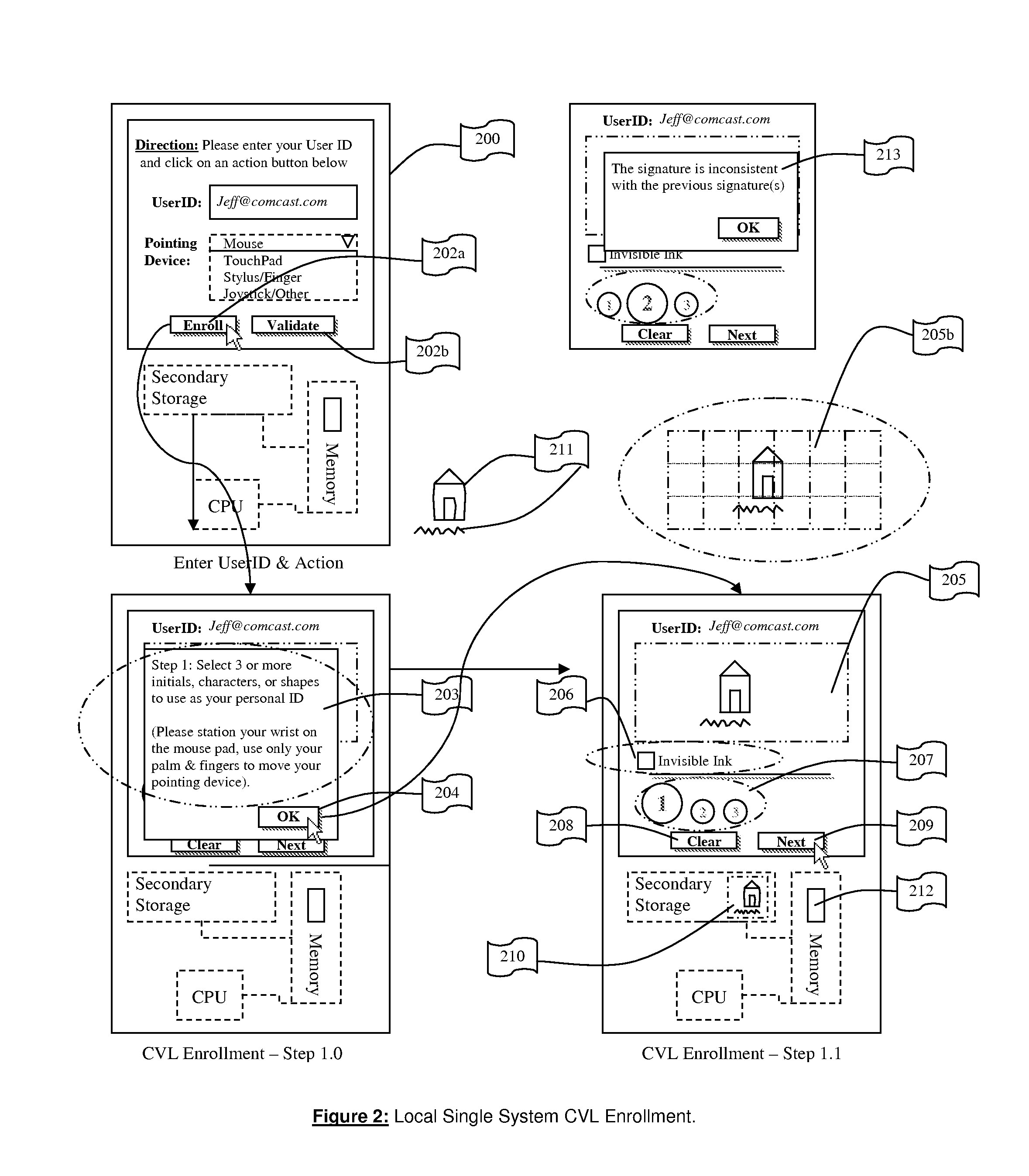
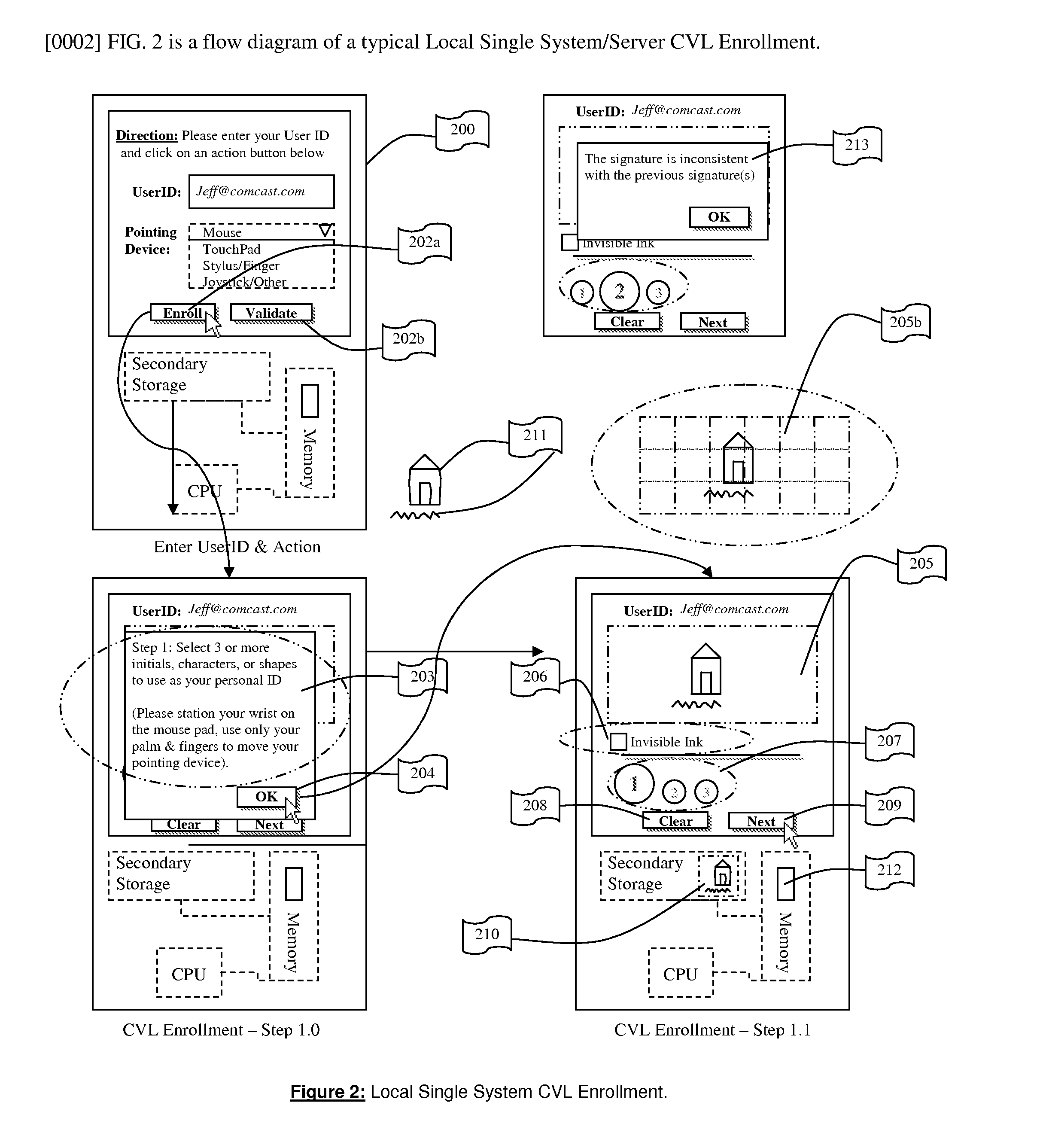
System for and Methods of Storing and Comparing Computer Generated Continuous Vector Lines through a Non-Secure or a Secure Communication Channel
ActiveUS20070236453A1Character and pattern recognitionCathode-ray tube indicatorsTerm memoryPointing device
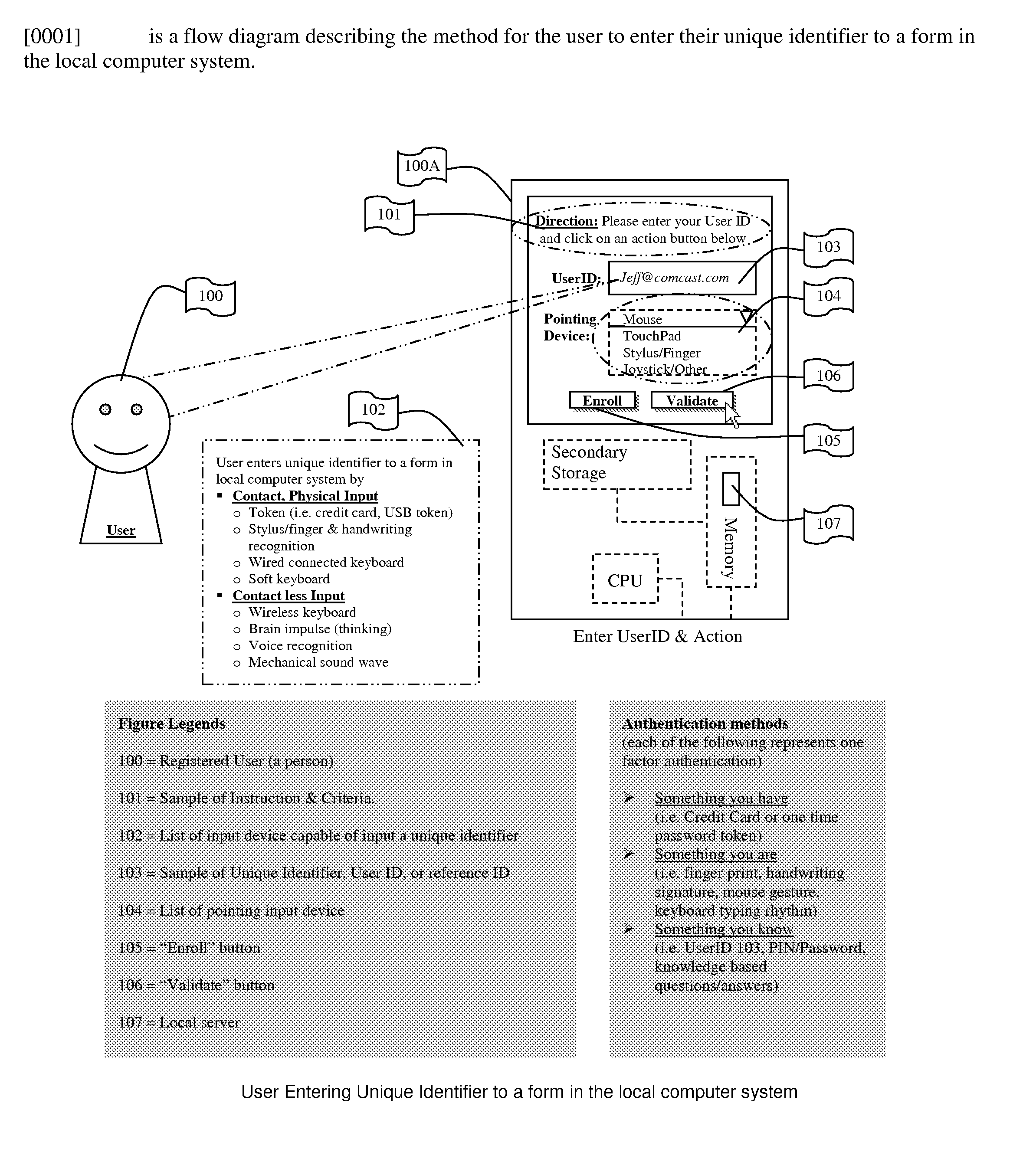
The present invention includes a system for and methods of storing and comparing computer generated vector lines through an insecure or a secure communication channel. A continuous vector line (CVL) identifier includes from an ordered collection of 2 or more points. Using an input device (such as computer keyboard, finger, soft keypad, or any other input from body movements or input from electrical current or impulses, or input from human or mechanical sound waves) to a physical machine, or through a token (such as credit card, USB token, which can be carried around by user), a user enters and sends their unique identifier and reference code (such as a personal identification number (PIN), and / or password or other secret code) to the physical machine by making a contact or contact-less to the computer system. As part of the enrollment process the user inscribes a pre-determined set of continuous vector lines (CVLs). The CVLs include data points that are collected from any computer pointing device, such as a mouse, stylus or a digitizer tablet, in a specific format, using a push down anatomical technique and are sent to local active content (such as a library, or a program, or an add-on to the Internet browser such as ActiveX) or a remote server for further analysis of the two CVL's. A user should go through an Enrollment and Verification process to capture the data points and this process uses a two factor authentication and a verification scheme. The collected data points that represent a CVL profile made previously is kept in a database, registry, or memory that can be encrypted and accessed by using a reference number or other unique identifier. Access is either locally or remotely through any wired or wireless medium such as the Internet, Secure File Transfer Protocol (SFTP) server, cellular network or other communication connection to enable the comparison of a newly generated CVL identifier to the CVL profile generated previously.
Owner:JCLADS
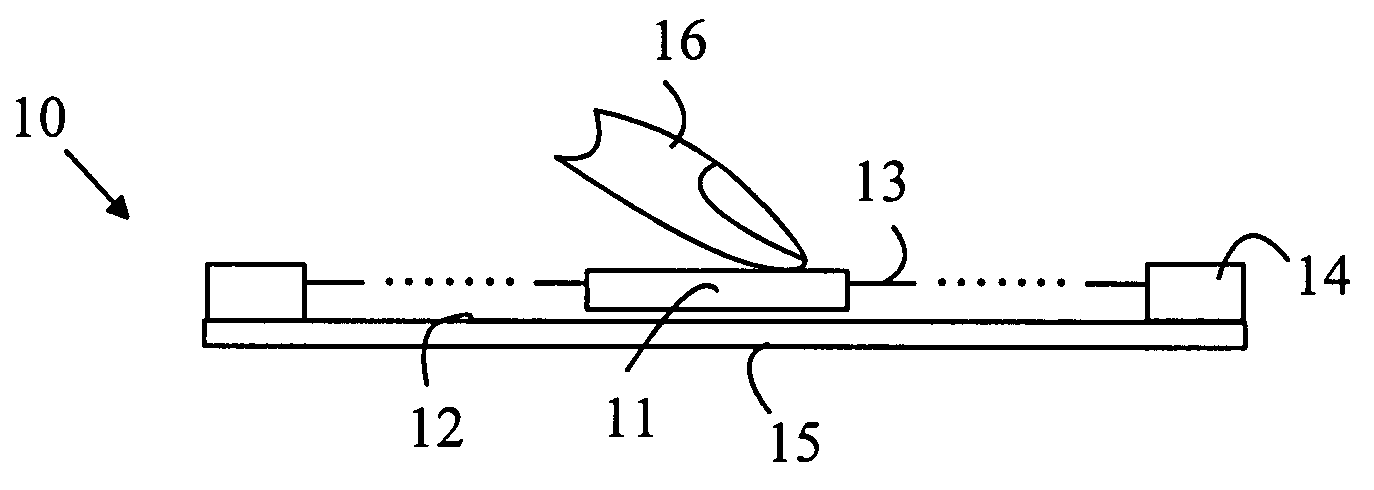
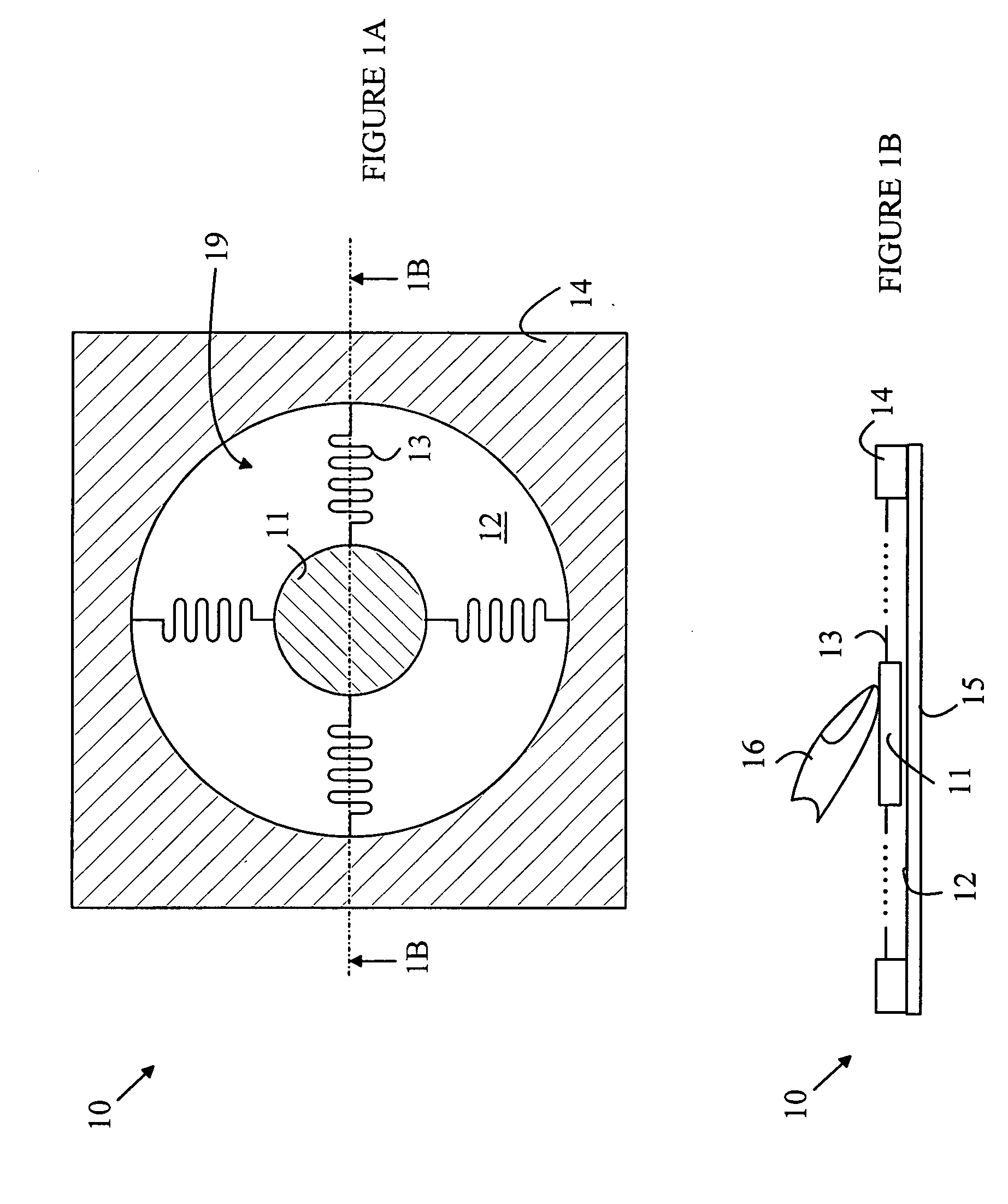
Thumb-actuated computer pointing-input device
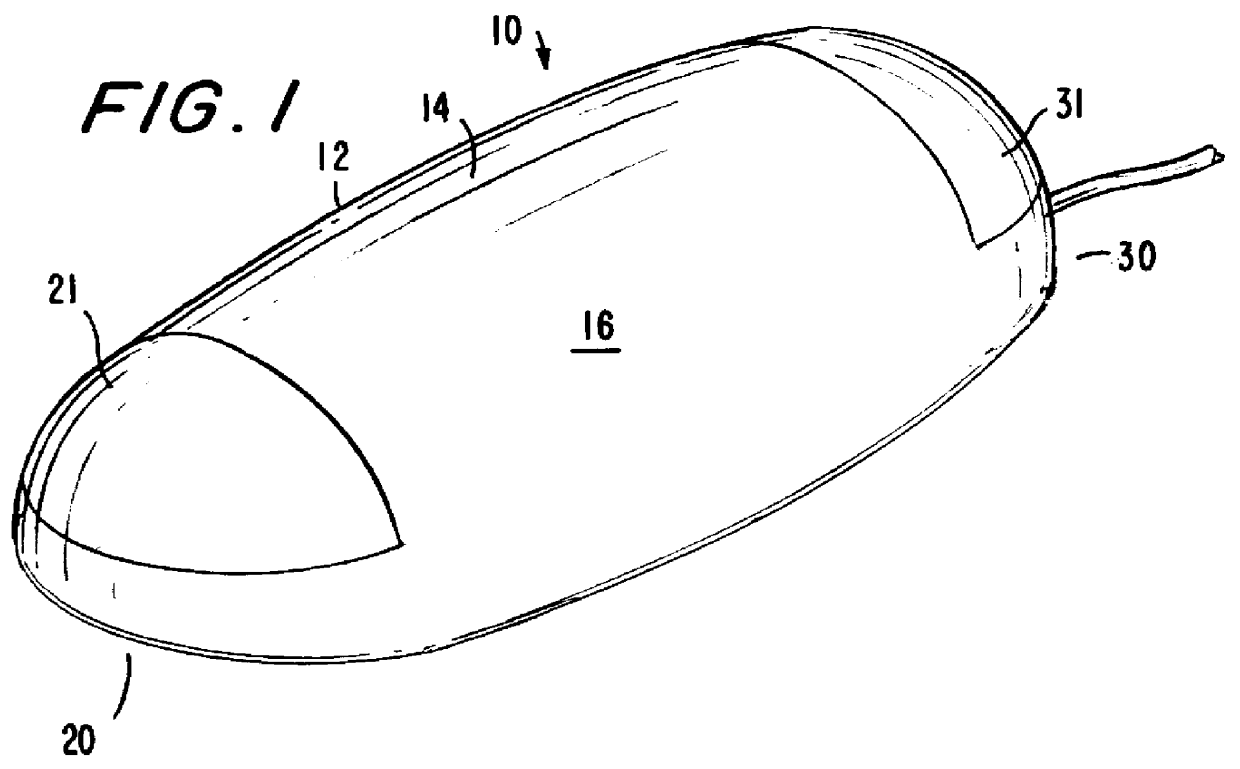
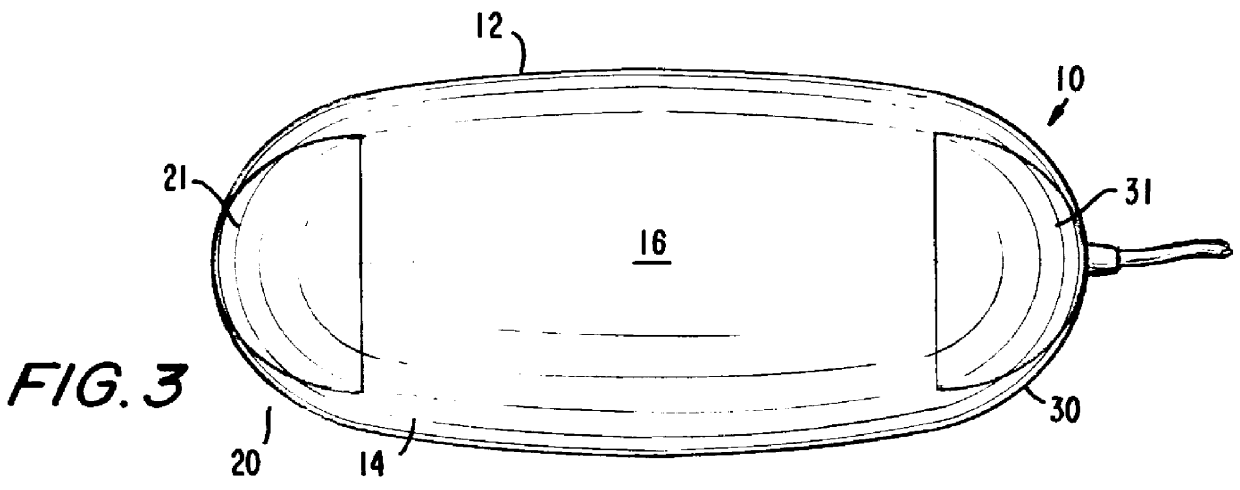
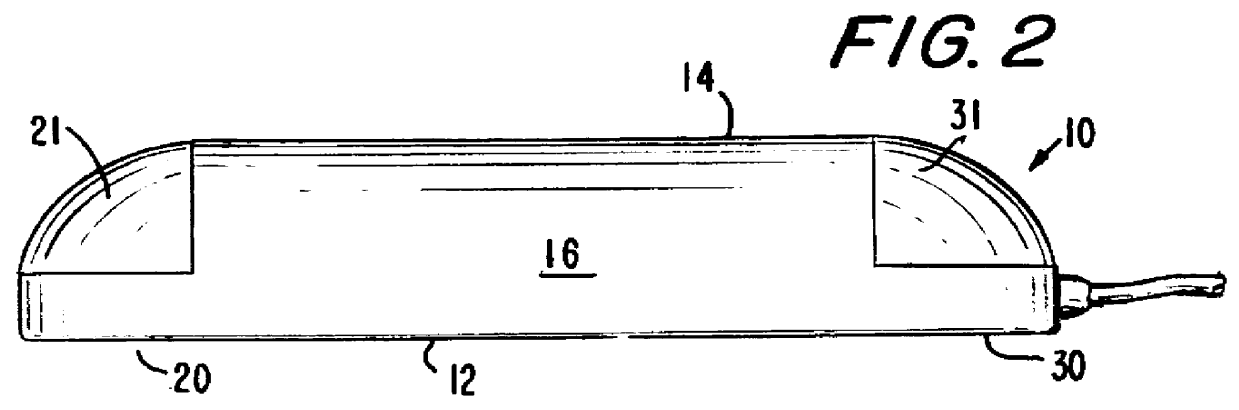
InactiveUS6104383ACathode-ray tube indicatorsInput/output processes for data processingCTS - Carpal tunnel syndromeStress syndrome
A computer pointing-input device has a low risk of inducing Repetitive Stress Syndrome and Carpal Tunnel Syndrome in a user by providing thumb and hand actuated controls. A main body (16) of the device is held laterally in a hand of the user with the thumb of the hand resting on a thumb switch (21). The palm of the hand rests on the main body (16) and an outer edge of the palm of the hand rests on a hand switch (31). The thumb switch (21) is operable by a downward pressure from the user's thumb, and the hand switch (31) is operable by downward pressure from the outer side of the user's palm.
Owner:SHIPMAN DALE HOWARD
Three state icon for operations
InactiveUS20050091614A1Reduce stepsInput/output processes for data processingPointing deviceHuman–computer interaction
A three state icon for a computer is disclosed. The icon prevents inadvertent starting of an operation on a computer. The icon has a first state which conceals a second state. Upon selection of the first state with a computer pointing device (i.e., mouse), the icon will change to the second state. Upon selecting the icon in the second state, the operation on the computer will start. Accordingly, only upon selecting the icon in the first state and then the second state, the operation will commence on the computer thereby preventing accidental startup of the operation. Once the second state has been selected, the icon will change to a third state which indicates that the operation is proceeding on the computer.
Owner:APPLE INC
Hybrid presentation controller and computer input device
InactiveUS20060197744A1Cathode-ray tube indicatorsInput/output processes for data processingUser inputHand held
Owner:LOGITECH EURO SA
Dynamically controlling a cursor on a screen when using a video camera as a pointing device
InactiveUS8144123B2Cathode-ray tube indicatorsInput/output processes for data processingPointing deviceOn-screen display
A system provides for controlling a cursor on a screen automatically and dynamically when using a video camera as a pointing device. A computer displays static or dynamic content to a screen. A video camera connected to the computer points at the screen. As the video camera films the screen, frames captured by the video camera are sent to the computer. A target image is displayed by the computer onto the screen and marks the position of the screen cursor of the video camera. Frames captured by the video camera include the target image, and the computer dynamically moves the target image on the screen to ensure that the target image stays in the center of the view of the video camera.
Owner:FUJIFILM BUSINESS INNOVATION CORP
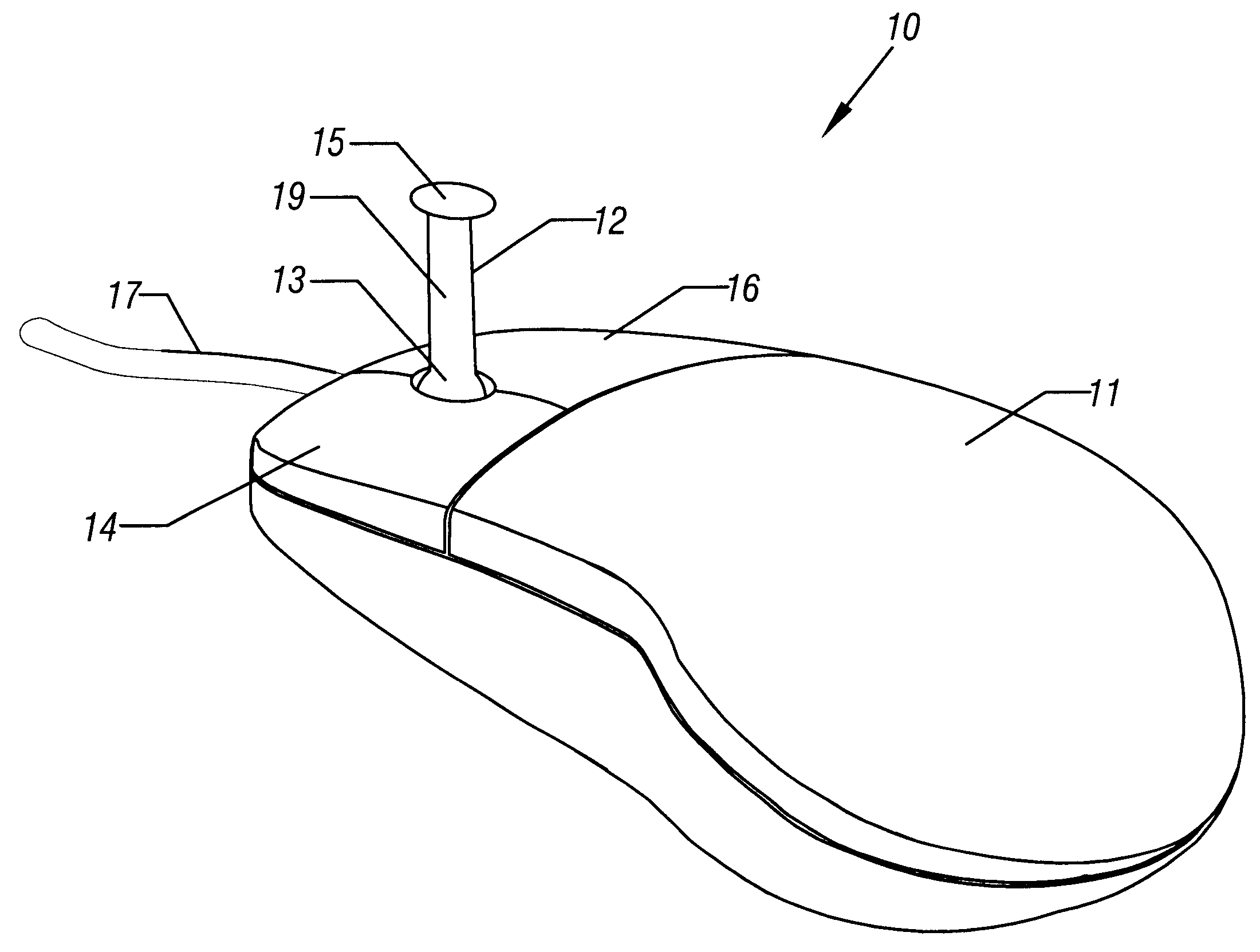
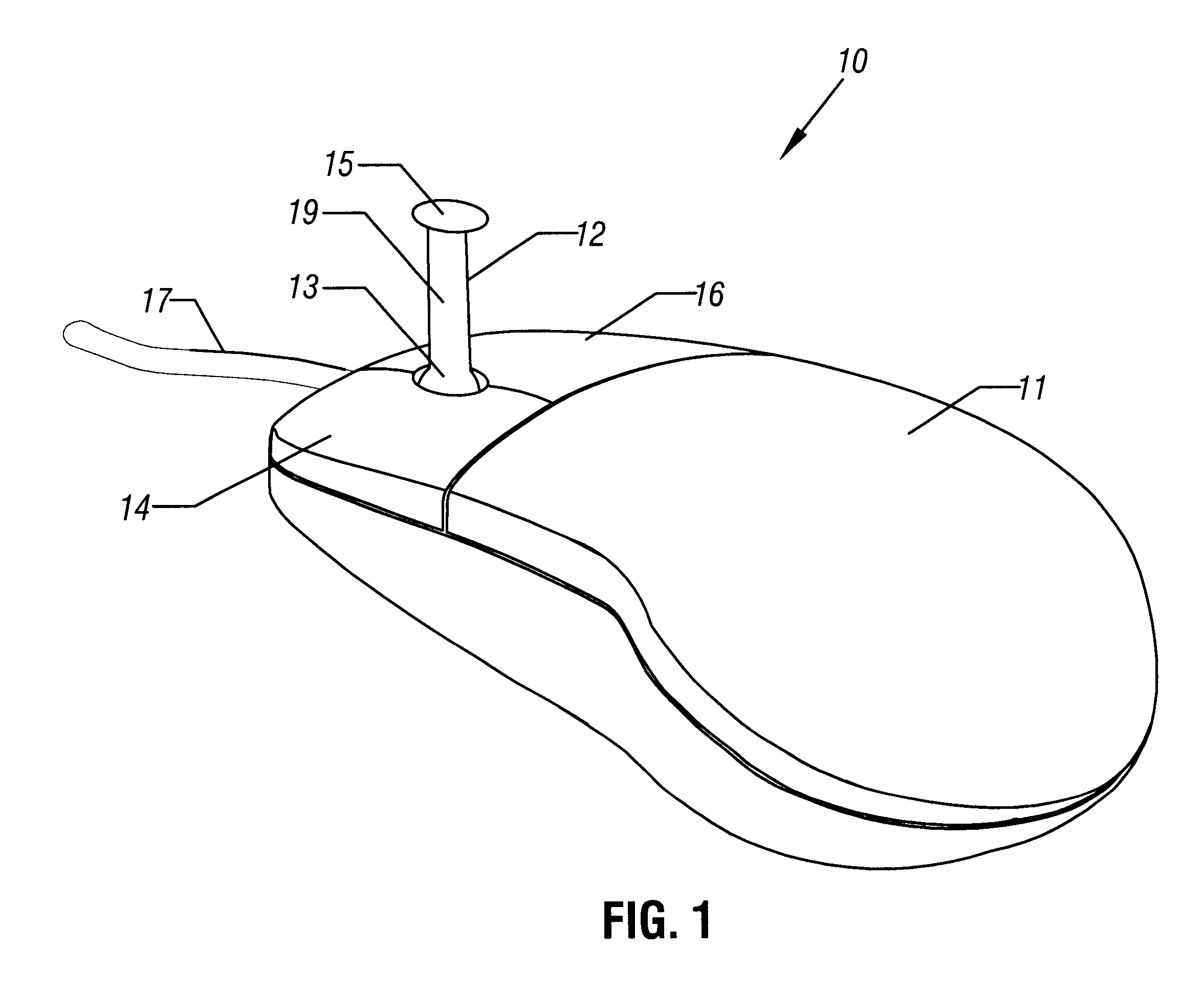
Computer pointing device and method of use
InactiveUS6229527B1Lessen biomechanical stressReducing overall biomechanical stressCathode-ray tube indicatorsInput/output processes for data processingBiomechanical stressPointing device
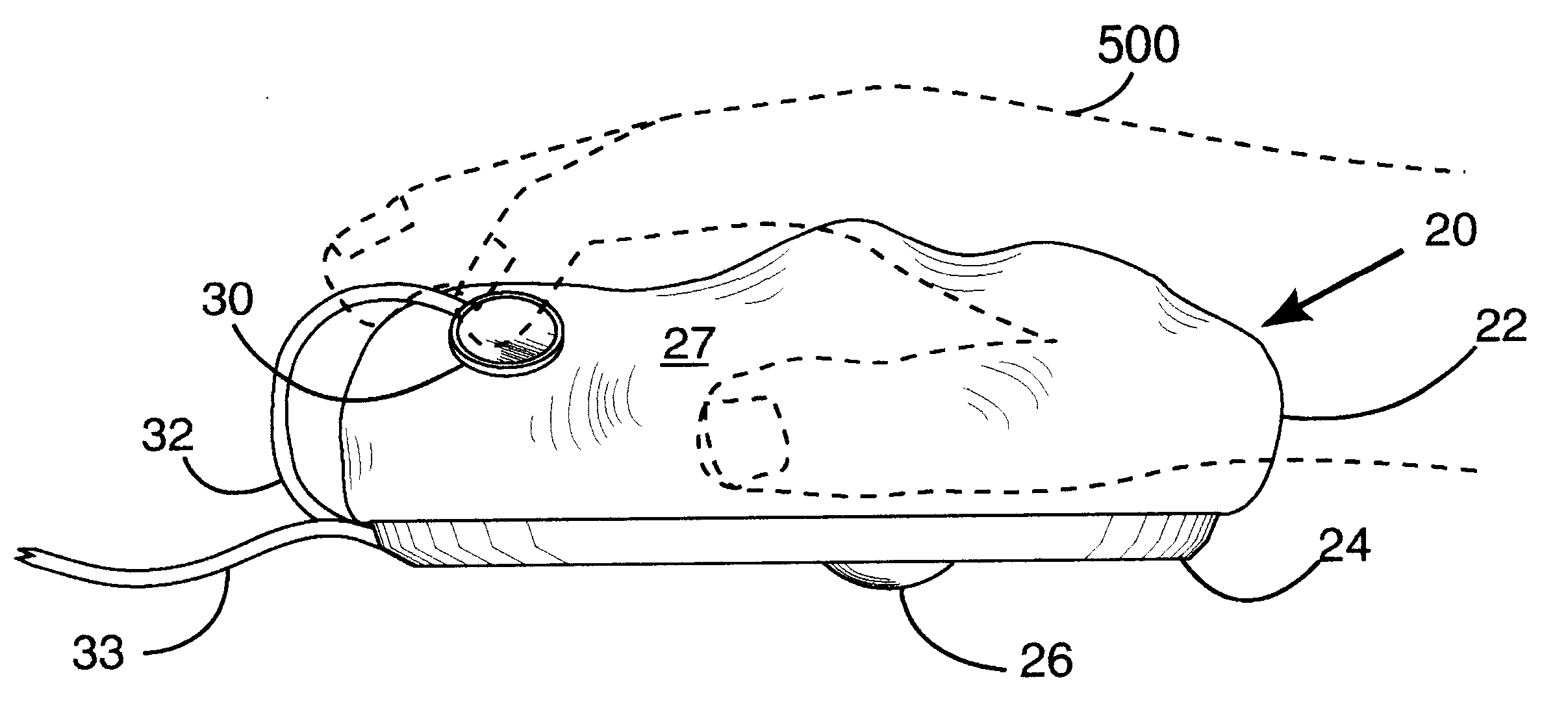
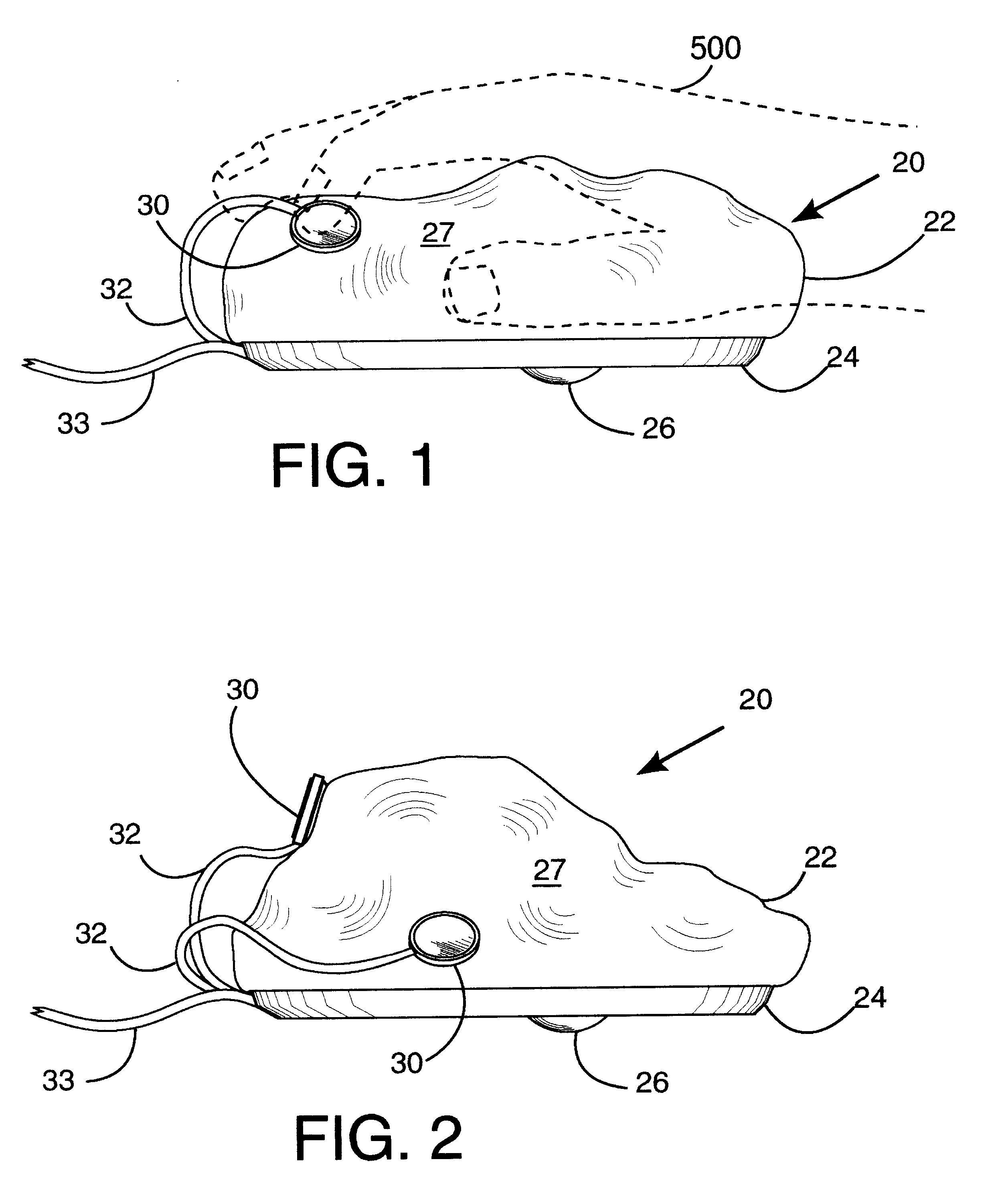
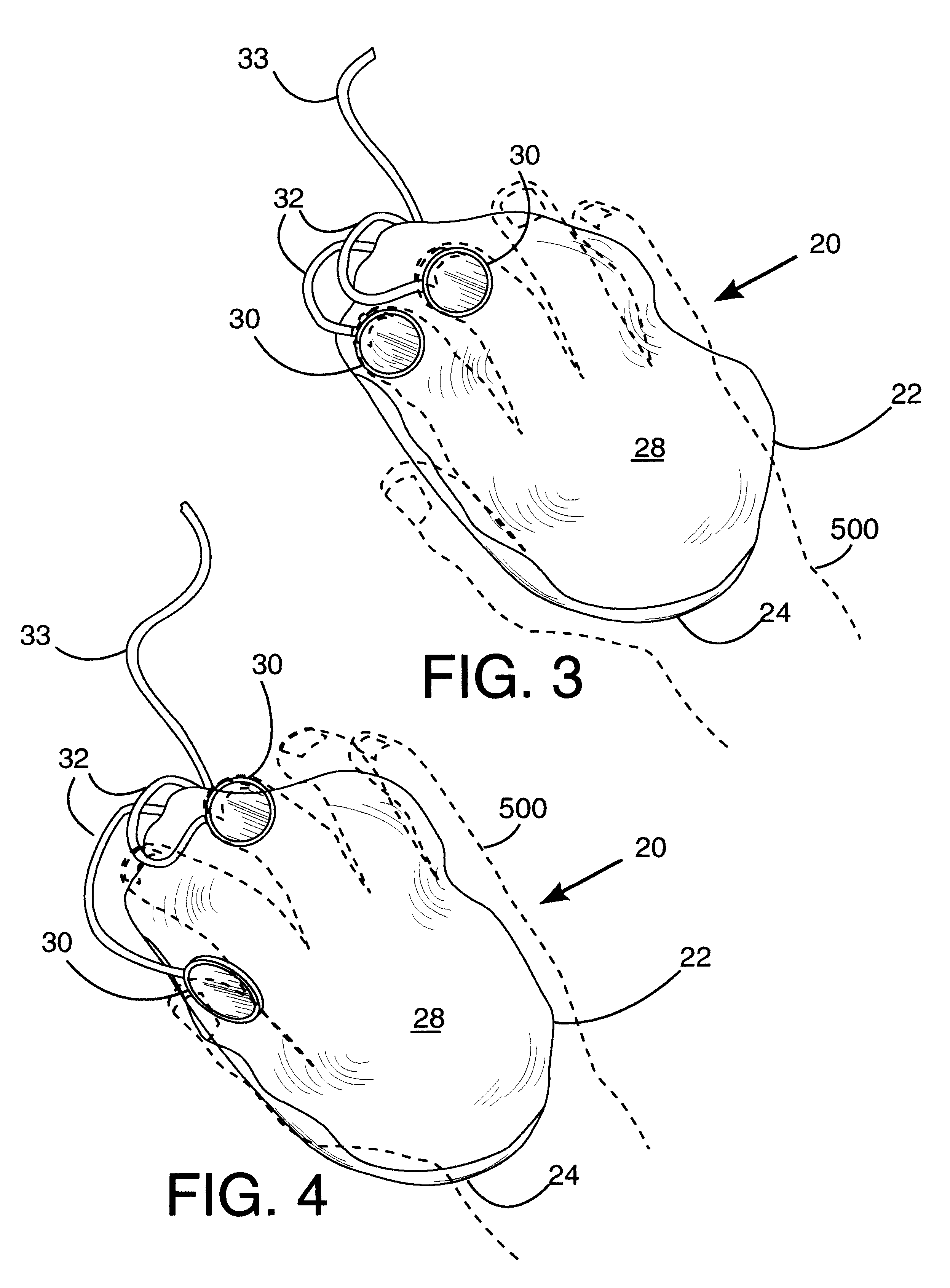
A hand operated computer pointing device (120) such as a "mouse" includes at least one control button (130) which is selectively positionable to a plurality of desired locations on the surface (127) of the body (122) of the computer point device (120). A user may selectively position the control button(s) (130) to any desired location upon the surface (127) of the body (122) in order to (a) best fit the hand (500) and fingers of the user, and (b) to reduce biomechanical stress. The body of the computer pointing device (120) may be of conventional firm construction (122), or alternatively may be moldable (22) by the user into a plurality of desired shapes.
Owner:SHEARN PATRICK M
Computer pointing system
InactiveUS20010045936A1Increase speedEfficient workCathode-ray tube indicatorsInput/output processes for data processingLow speedVideo image
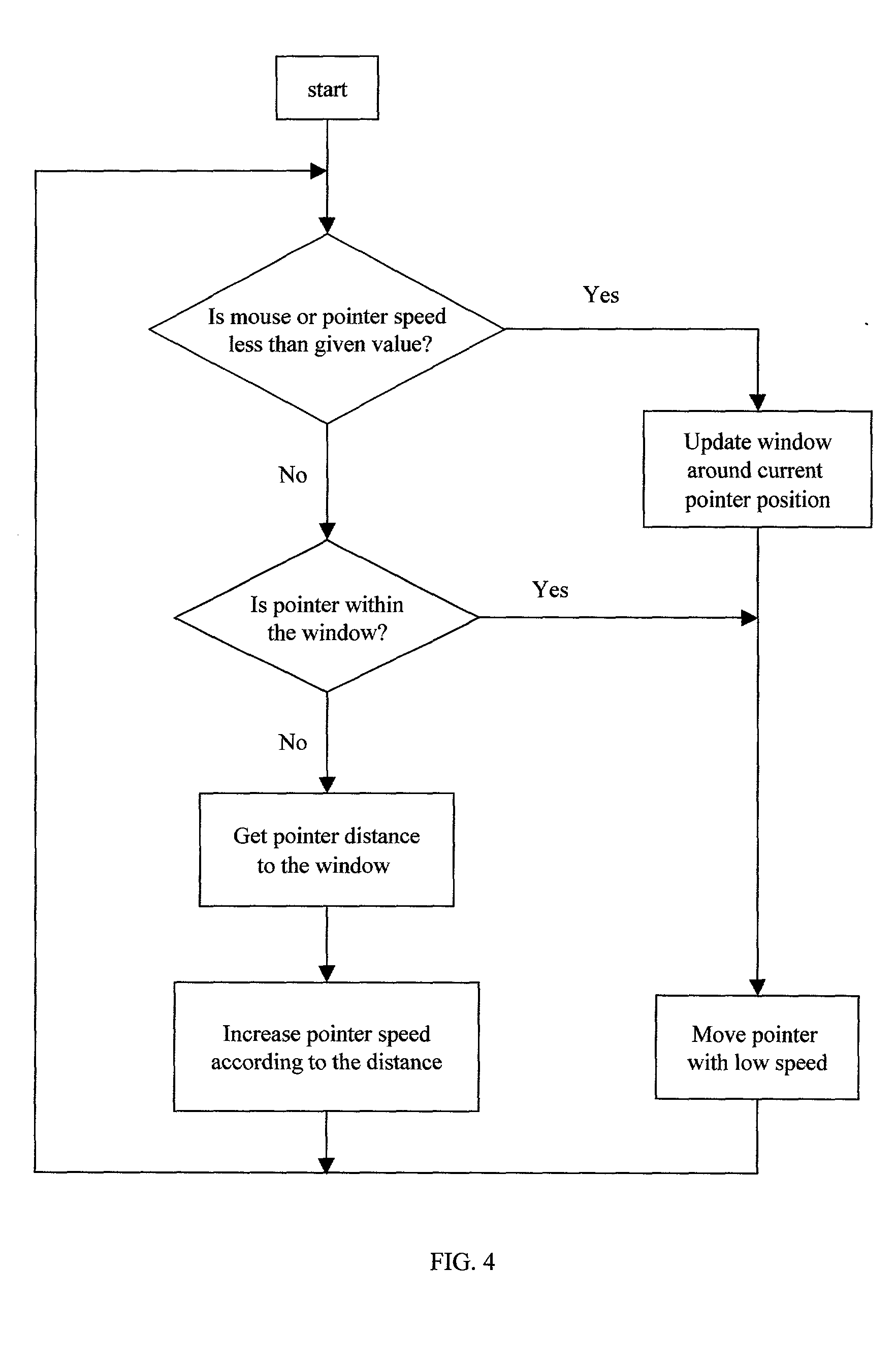
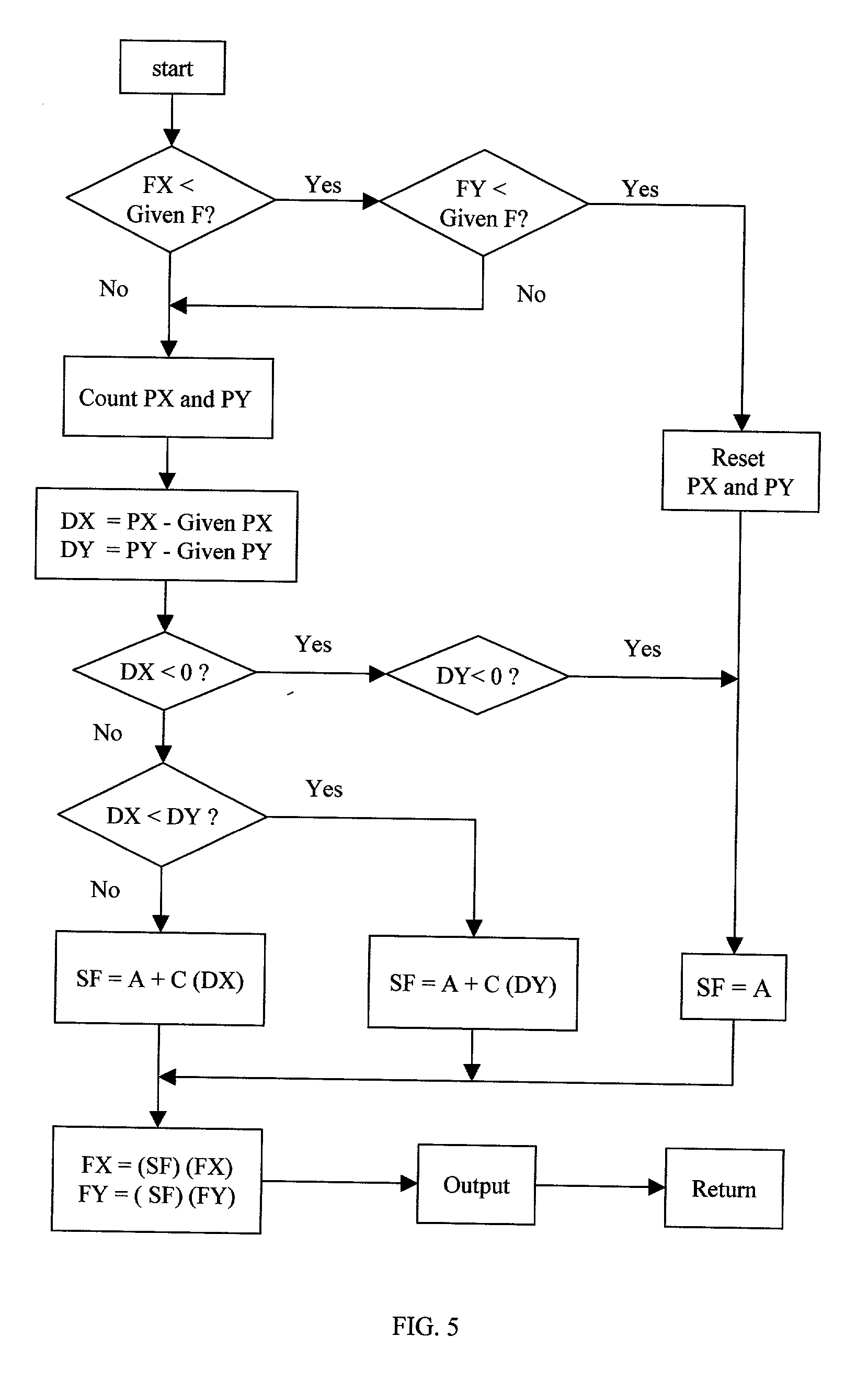
In a computer having a processing unit, a coordinate input device such as a mouse and a display screen, a video image of a cursor or pointer can be moved and positioned on the screen by moving the mouse. The speed of the pointer is changed according to the amount of movement or travel distance of the mouse or pointer. As the mouse or pointer is moved farther from an initial position, the speed of the pointer is increased. When the mouse is stopped or its speed is reduced below a given value, the process stops and restarts with the next movement of the mouse. In one embodiment, the pointer moves at a low speed in fixed relation with the mouse for a first part of the movement of the mouse or pointer. The increase in pointer speed starts after the completion of the first part of the movement. In another embodiment, the speed of the pointer is increased gradually or stepwise form the beginning of the movement of the mouse or pointer.
Owner:RAZZAGHI MAHMOUD
Method for carrying out laser-micro-engraving marking anti-counterfeiting identification code on inner surface of transparent or translucent container
The invention discloses a method for carrying out laser-micro-engraving marking anti-counterfeiting identification code on the inner surface of a transparent or translucent container. In the method, laser-micro-engraving and a computer point cloud software system are utilized to carry out point cloud process on an anti-counterfeiting identification code; a computer marking software system controls a vibrating mirror and the10ns grade laser beam of a 532nm green laser to act on the surface of a transparent or translucent container according to a point cloud file so that the anti-counterfeiting identification code is marked on the inner surface of the transparent or translucent container, wherein the laser beam of the 532nm green laser has high pulse peak value power and high frequency of pulse laser beam. An anti-counterfeiting identification code is internally engraved on the surface of a glass winebottle, so the laser-micro-engraving marking anti-counterfeiting identification code is never worn. The invention has simple and compact structure, high laser-micro-engraving speed, is suitable for various transparent and colorful glass winebottles, and can be widely applied to laser-micro-engraving marking of winebottles in production lines of distilled spirit, red wine or beer industries.
Owner:WUHAN LEAD LASER
Braille computer pointing words input system, device and method thereof
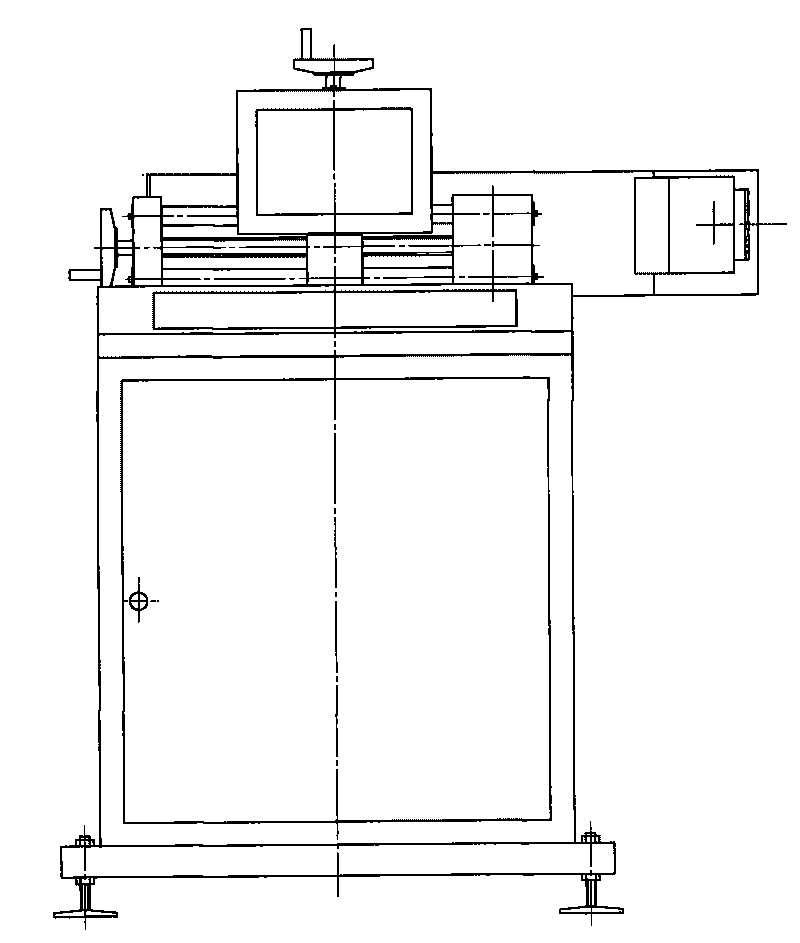
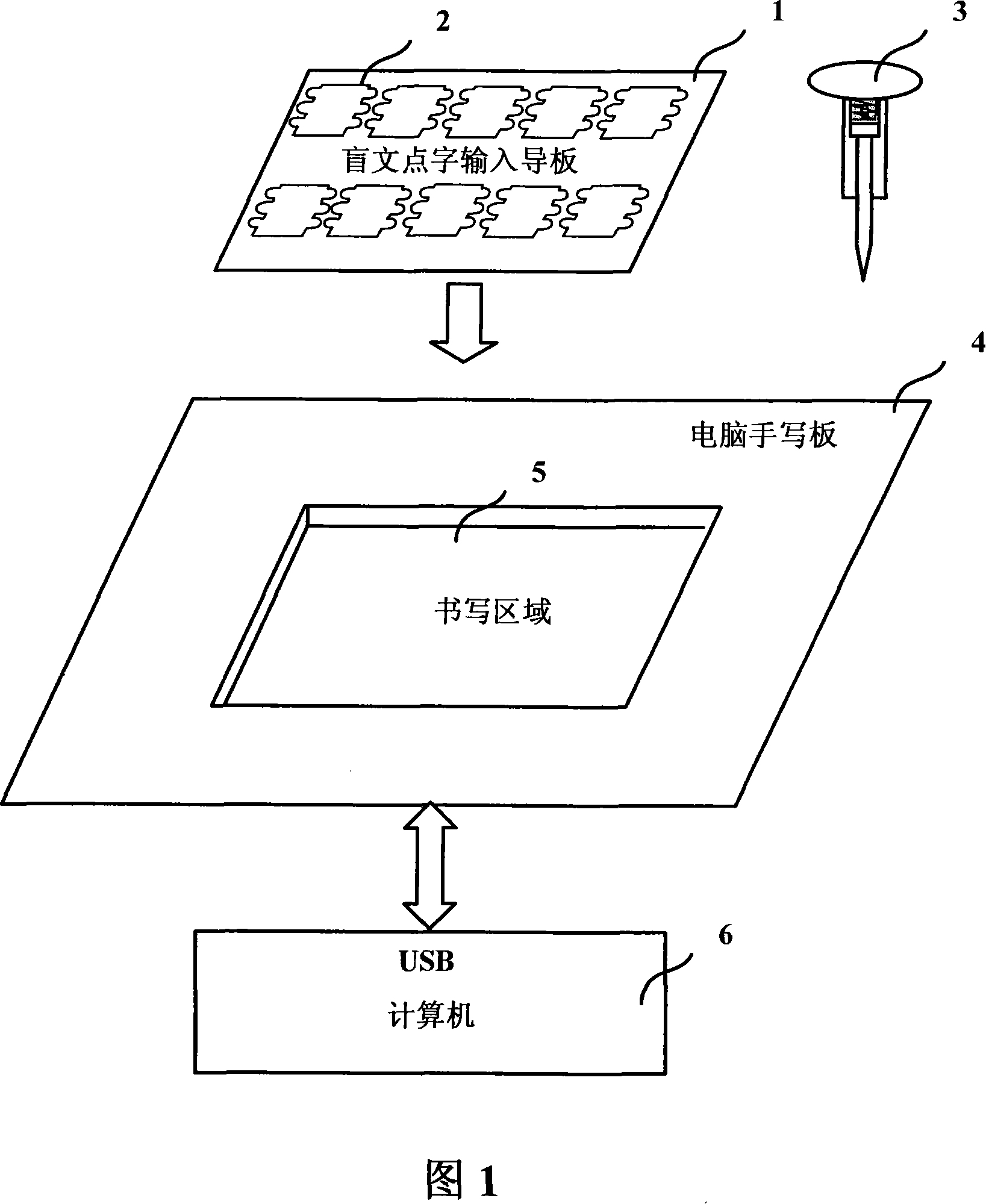
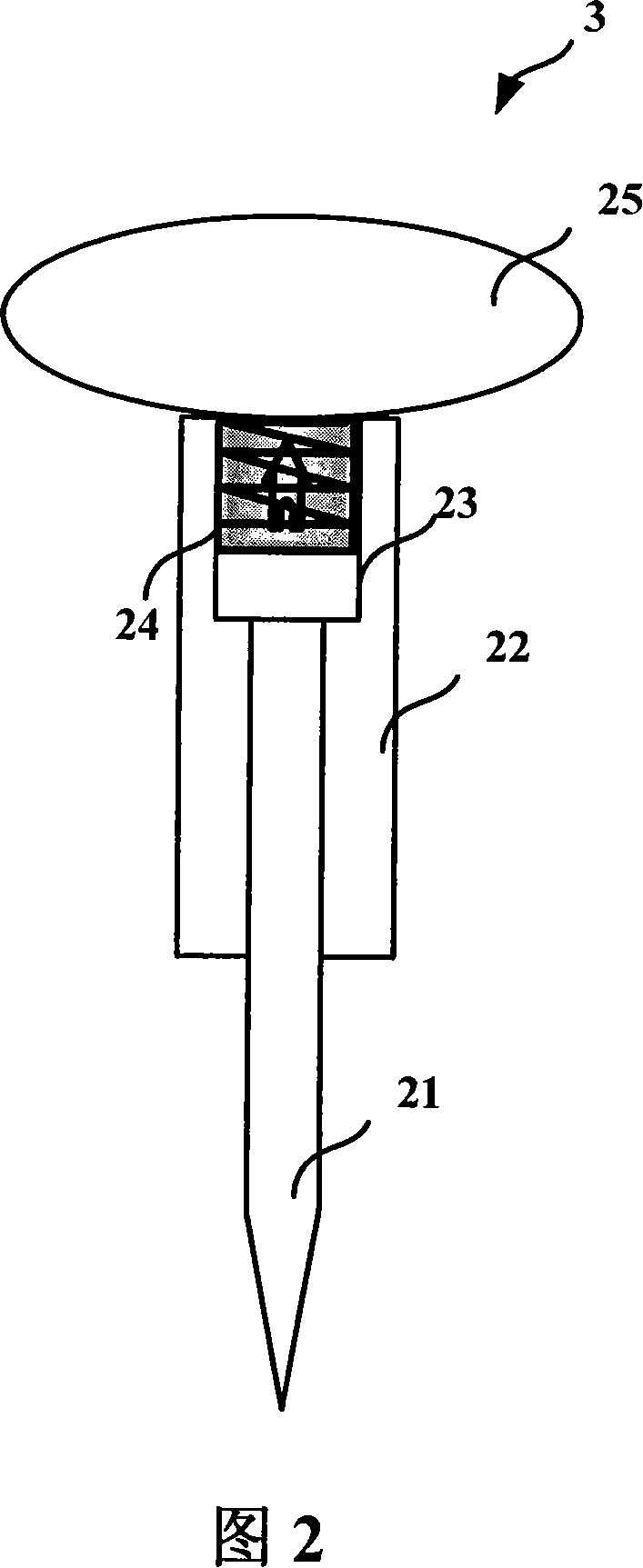
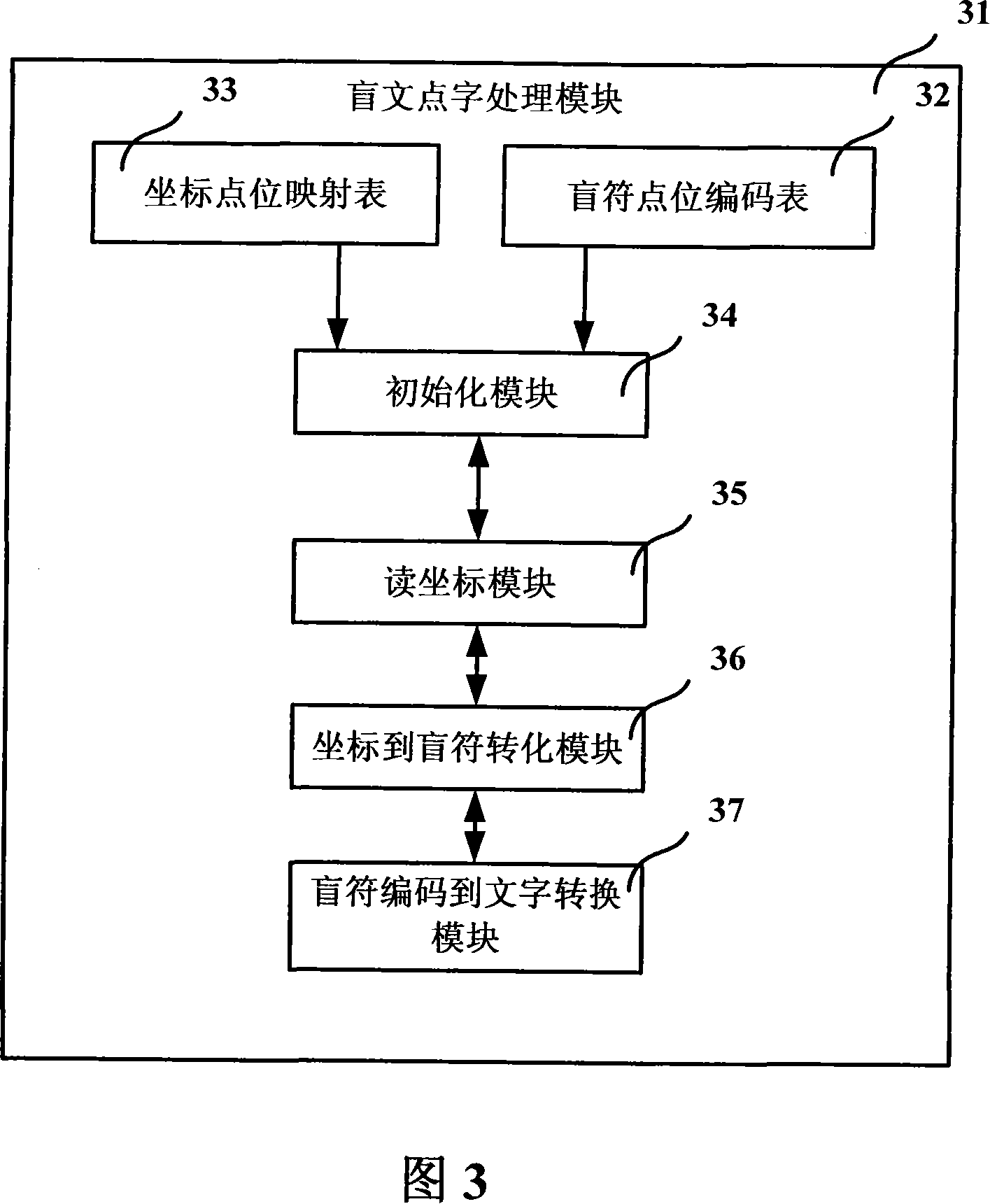
ActiveCN101135940ARealize Braille input functionMeet usage habitsInput/output for user-computer interactionHandwritingComputer Point
The system comprises: a handwriting board, a computer, a braille input guide board, a braille pen and a braille processing module. Said braille input guide board has a same size with the writing area of the handwriting board and is mounted on the surface of the handwriting board; said handwriting board is connected to said computer through an interface; said braille processing module is used for processing the braille input signals from the handwriting board when user uses the braille pen and braille input board to make input on the handwriting board.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
System and method for remote control coal mine evacuation working face advance detection and forecasting
ActiveCN101798923AAvoid harmComply with the requirements of the Safety RegulationsSurveyMining devicesControl systemRemote control
The invention discloses a system and method for remote control coal mine evacuation working face advance detection and forecasting, which comprises a remote control system, a firing device, a blasting excitation system, a blasting receiving system and an anti-explosion geological advance detector host, and is characterized in that the remote control system comprises an anti-explosion computer, a remote controller master computer and a remote control slave computer; the anti-explosion computer and the remote control master computer are connected to realize duplex communication; the remote controller master computer is connected with the remote controller slave computer point to point through a cable; the remote controller slave computer is connected with the anti-explosion geological advance detector master computer to realize duplex communication; the remote control coal mine evacuation working face advance detection and forecasting system also comprises a synchronous signal detectionbox; and the output end of the firing device is connected with the synchronous signal detection box, the firing device outputs excitation signals to the blasting excitation system through the synchronous signal detection box, thereby preventing an operator from harm.
Owner:CHINA COAL TECH & ENG GRP CHONGQING RES INST CO LTD
System for and methods of storing and comparing computer generated continuous vector lines through a non-secure or a secure communication channel
ActiveUS8004491B2Character and pattern recognitionCathode-ray tube indicatorsCredit cardThe Internet
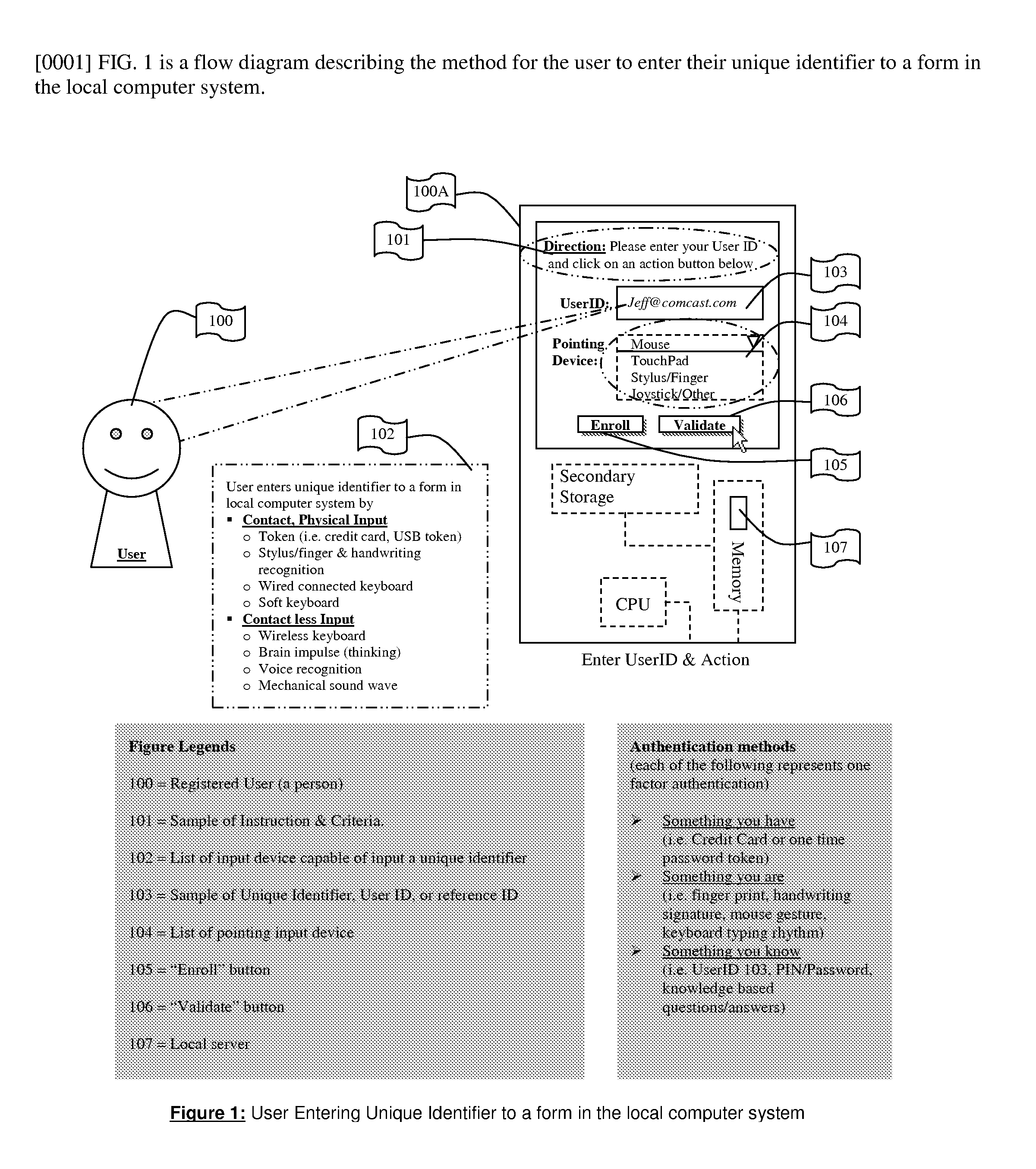
A system / method to store and compare computer generated vector lines through an insecure or a secure communication channel. Using an input device (i.e. computer Keyboard, finger, soft keypad, or any other input from body movements, electrical current, or impulses, or input from human or mechanical sound waves) to a physical machine, or through a token (i.e. credit card, USB token, which can be carried around by user), a user enters and sends their unique identifier and reference code (i.e. PIN, password, other secret code) to the physical machine by making a contact or contact-less to the computer system. As part of the enrollment process the user inscribes a pre-determined set of continuous vector lines (CVLs). The CVLs include data points that are collected from any computer pointing device in a specific format, using a push down anatomical technique and are sent to local active content (i.e. a library, or a program, or an add-on to the internet browser i.e. ActiveX) or a remote server for further analysis of the two CVLs. A user should go through an Enrollment and Verification process to capture the data points and this process uses a two factor authentication and a verification scheme. The collected data points that represent a CVL profile made previously is kept in a database, registry, or memory that can be encrypted and accessed (locally or remotely) by using a reference number or other unique identifier to enable the comparison of a newly generated CVL identifier to the previously generated one.
Owner:JCLADS
Connecting structured data sets
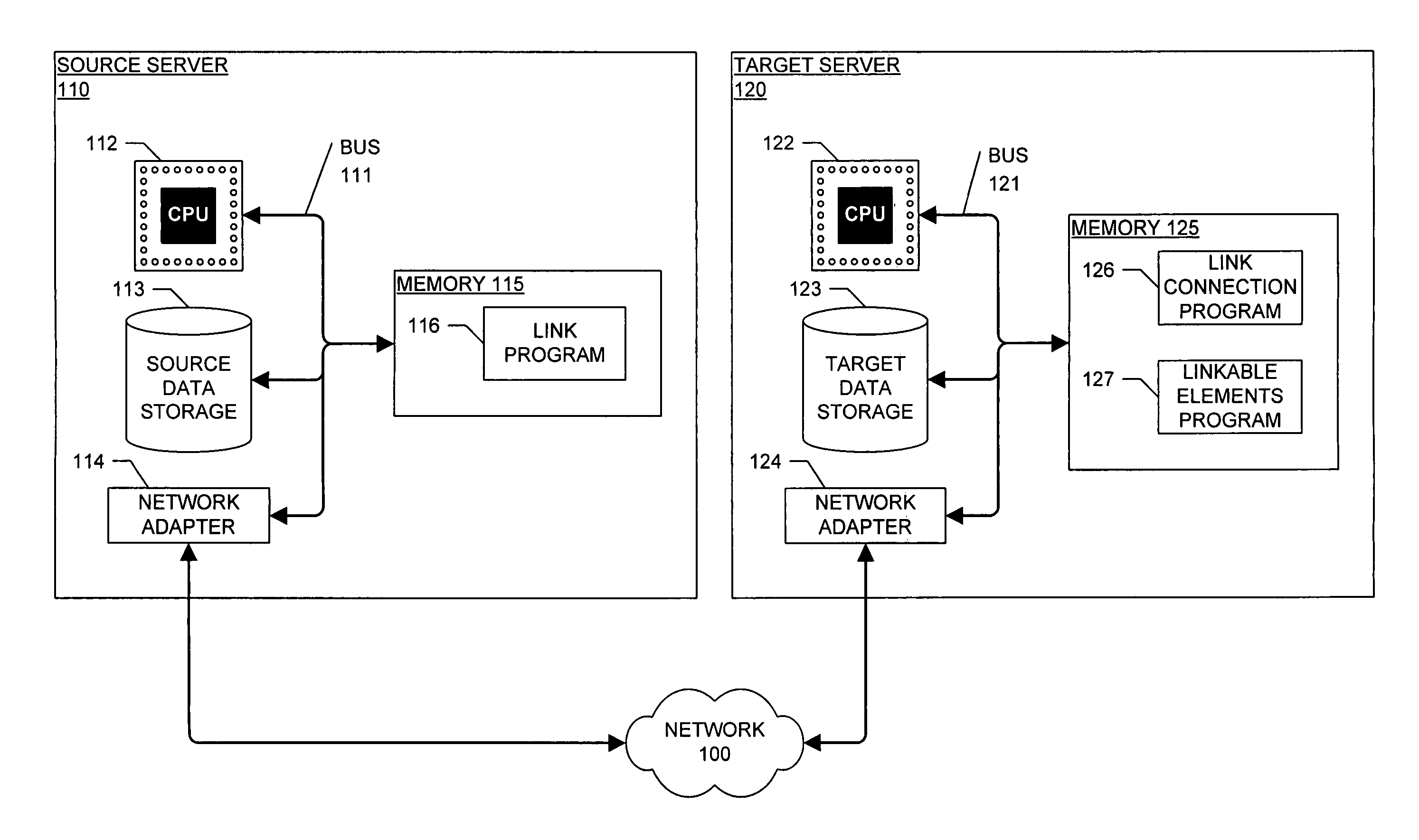
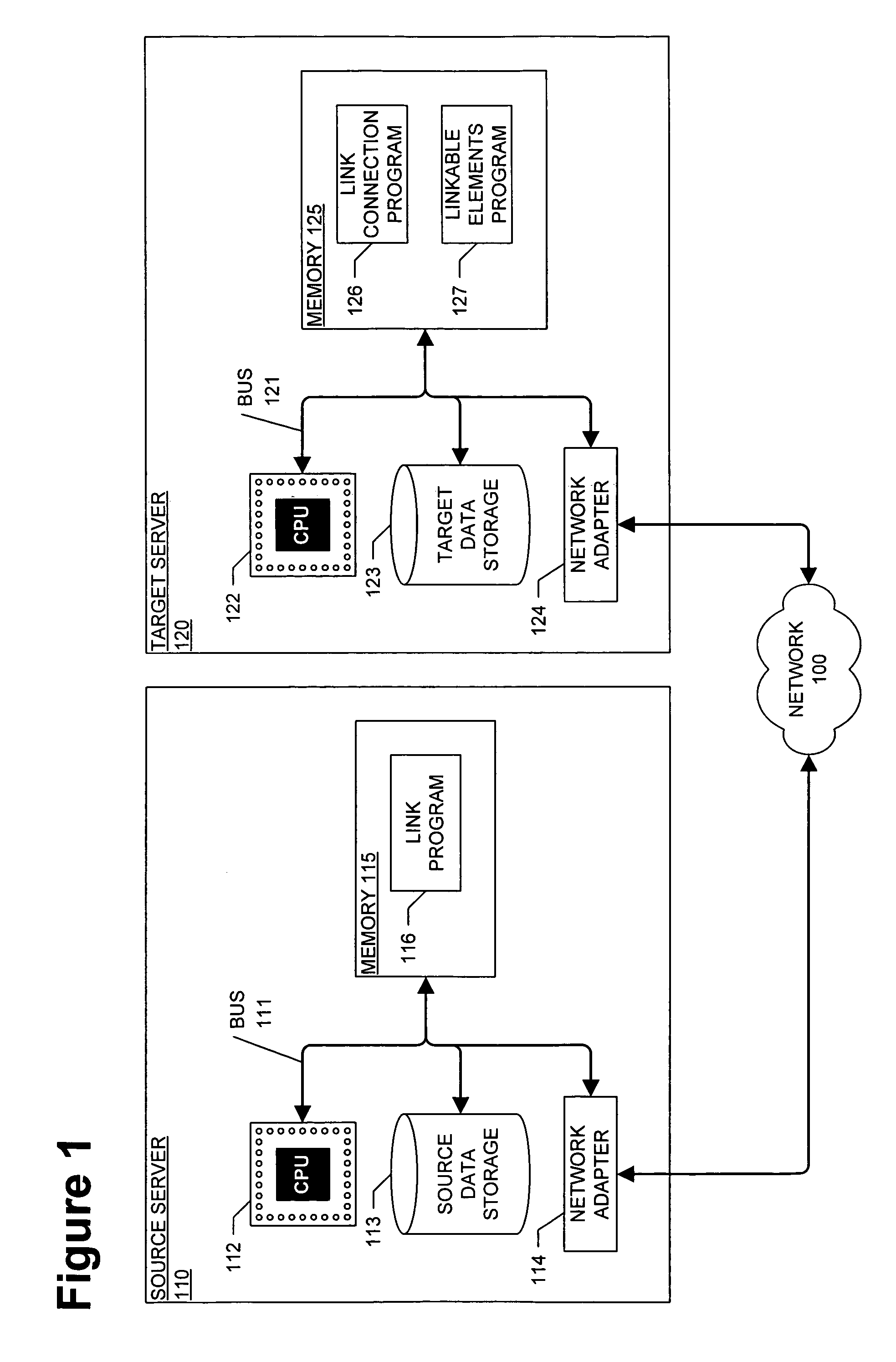
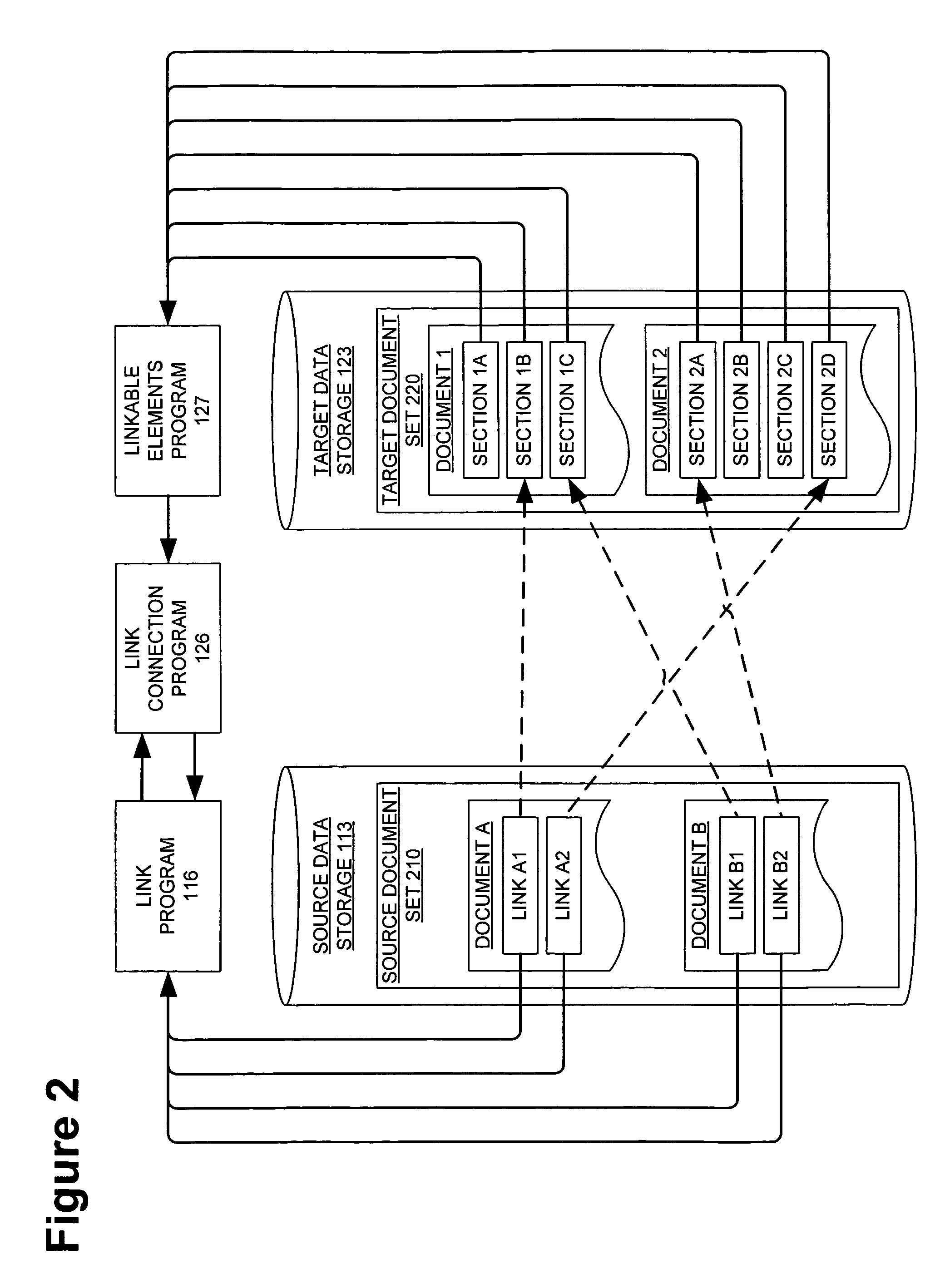
InactiveUS20060271839A1Digital data information retrievalDigital computer detailsData setDocumentation
A method and computer device for connecting structured documents stored on a source computer to structured documents stored on a target computer. The method identifies links in the structured documents on the source computer and linkable elements in the structured documents on the target computer. Each link on the source computer points to a linkable element on the target computer. The method transmits the links from the source computer to the target computer and associates each link with one of the linkable elements. The method determines changes to the links in the structured documents on the source computer based on changes to the structured documents on the target computer. The method transmits the link changes to the source computer which updates the links based on the link changes.
Owner:IHS GLOBAL
Method and apparatus for providing computer pointing device input to a video game console
InactiveUS20050176504A1Smooth inputLess grainVideo gamesSpecial data processing applicationsPersonal computerPointing device
A method and apparatus for adapting a computer pointing device to a video game console. In one embodiment a mouse plugs into an adapter which has an output that plugs into an input of a console. The adapter receives motion data from one or more computer mice and translates this into a format compatible with a game controller for that console. This data is then output to the console which perceives the data as from a single game controller. Thus computer pointing device output, such as from a mouse, is adapted to a console such that the user can control games on that console using the mouse. Data from a computer pointing device can also be combined with data from a keyboard such that the user may play games on a console using a mouse and a keyboard, as is common on personal computers.
Owner:STANLEY MARK JOSEPH
Computer mouse peripheral
InactiveUS20130194183A1Aid correct positioning and retentionEasy to controlCathode-ray tube indicatorsDetails for portable computersVirtual screenEngineering
A computer pointing device including: a base portion with a lower surface adapted for sliding across a work surface, a spine portion, projecting substantially upward from said base portion and having a thumb-engaging surface on a first lateral side of the spine and at least one index fingertip and / or middle fingertip-engaging surface on a second lateral side of the spine opposing said first lateral side. A keyboard with an altered arrangement of function of keys, such as an enlarged or truncated or no spacebar or capable of an altered appearance in accordance with keys being re-mapped to sensors on a pointing device. A keyboard with a virtual screen display, which may be made semi-transparent by activating a sensor on a pointing device. A computer with a recess capable of accommodating a mouse device. A locked scrolling or zooming means, using any pointing device, in which scrolling or zooming in a defined direction is proportional to the distance travelled by the device, irrespective of direction of movement of the device.
Owner:SWIFTPOINT LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com