Patents
Literature
32 results about "Secure File Transfer Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A network protocol designed to move files securely between a computer and a host over a TCP network, such as the Internet.
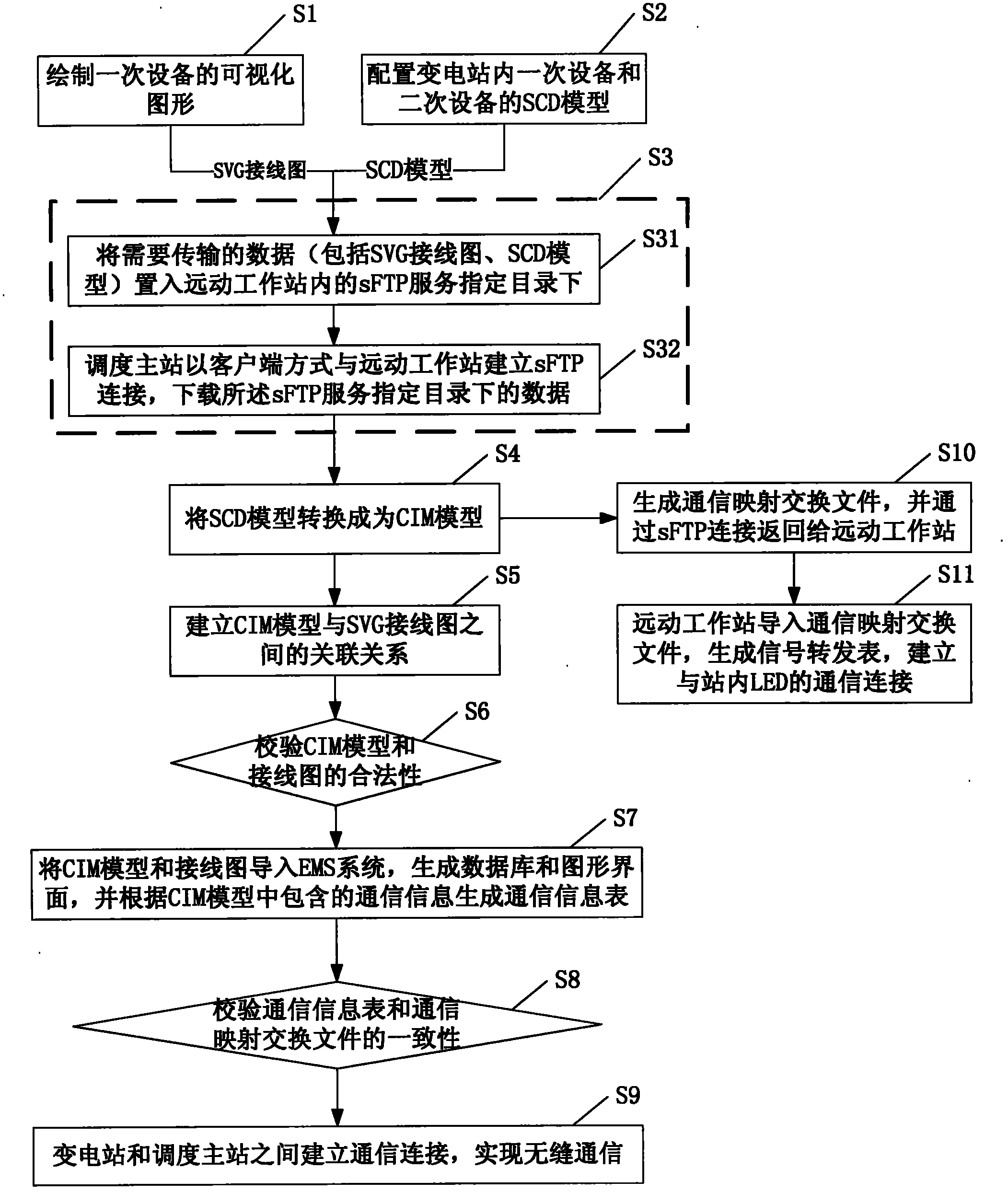
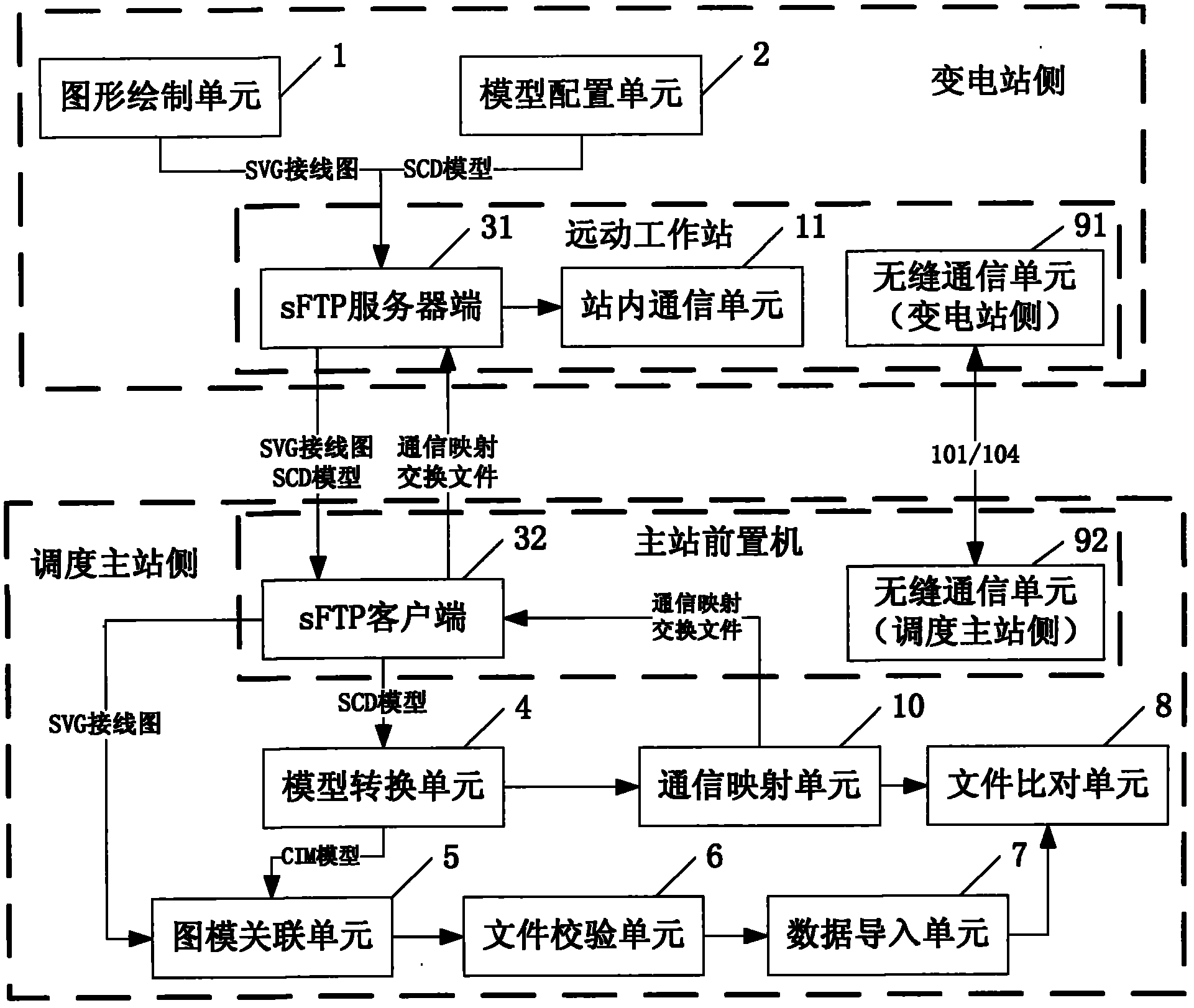
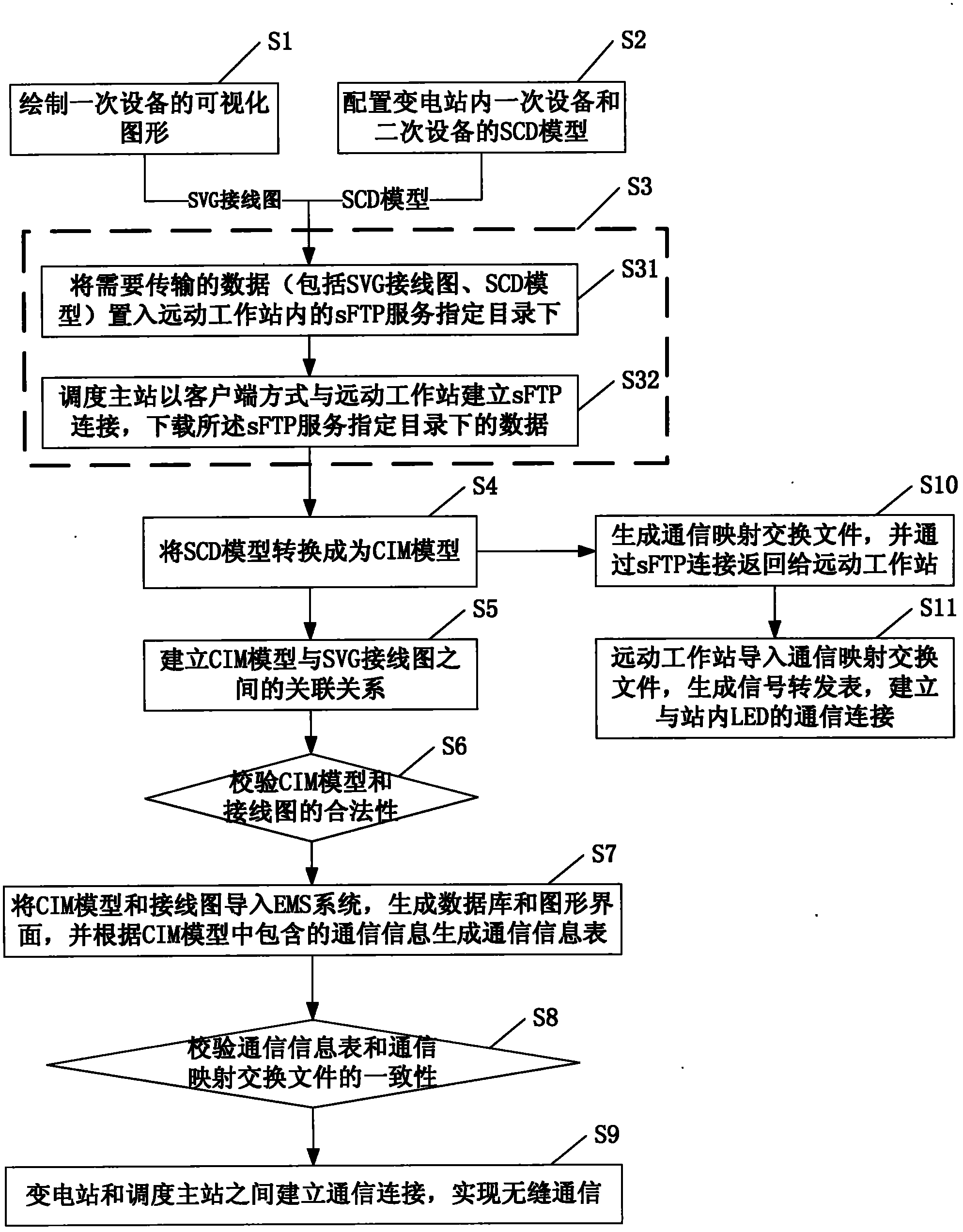
Method and system for realizing seamless communication between master scheduling station and substation of power grid
The invention discloses a method for realizing seamless communication between a master scheduling station and a substation of a power grid. The method comprises: a model configuration step of establishing an international electrotechnical commission (IEC)-61850-standard-format-based whole-station unified configuration model file comprising a primary equipment model and a second equipment model in the substation; a secure file transfer protocol (sFTP) file transmission step of uploading data comprising the whole-station unified configuration model file to the master scheduling station through sFTP connection by using a telecontrol workstation in the substation; a model conversion step of converting the whole-station unified configuration model file into an IEC-61970-standard-format-based common information model comprising communication information; and a seamless communication step of establishing seamless communication connection between the master scheduling station and the substation. The invention also discloses a corresponding system for realizing the seamless communication between the master scheduling station and substation of the power grid. By the method and the system, the seamless communication between the digital substation and the master scheduling station can be realized under the condition of avoiding influence on the conventional substation and the master scheduling station as much as possible.
Owner:广东电网公司深圳供电局
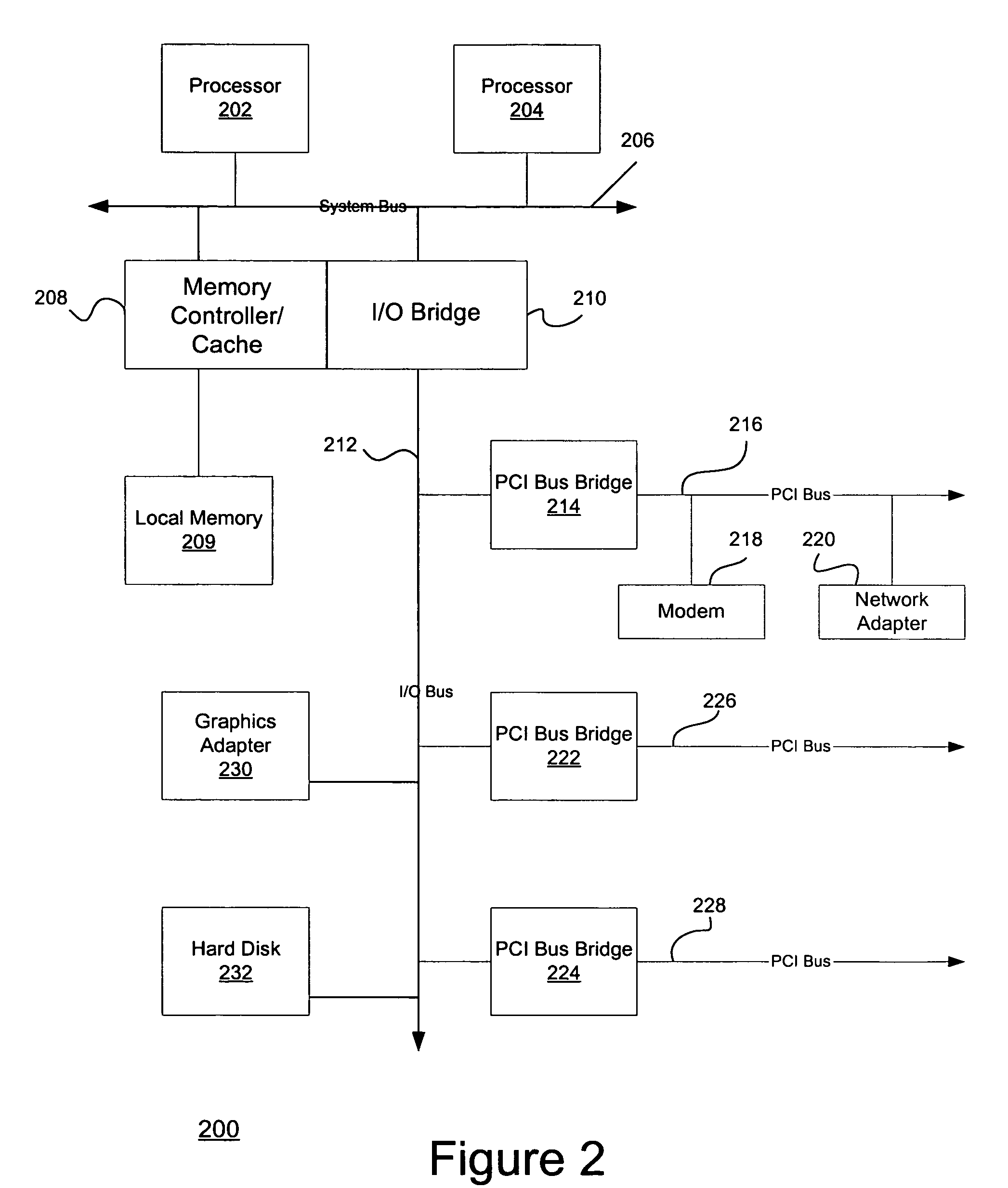
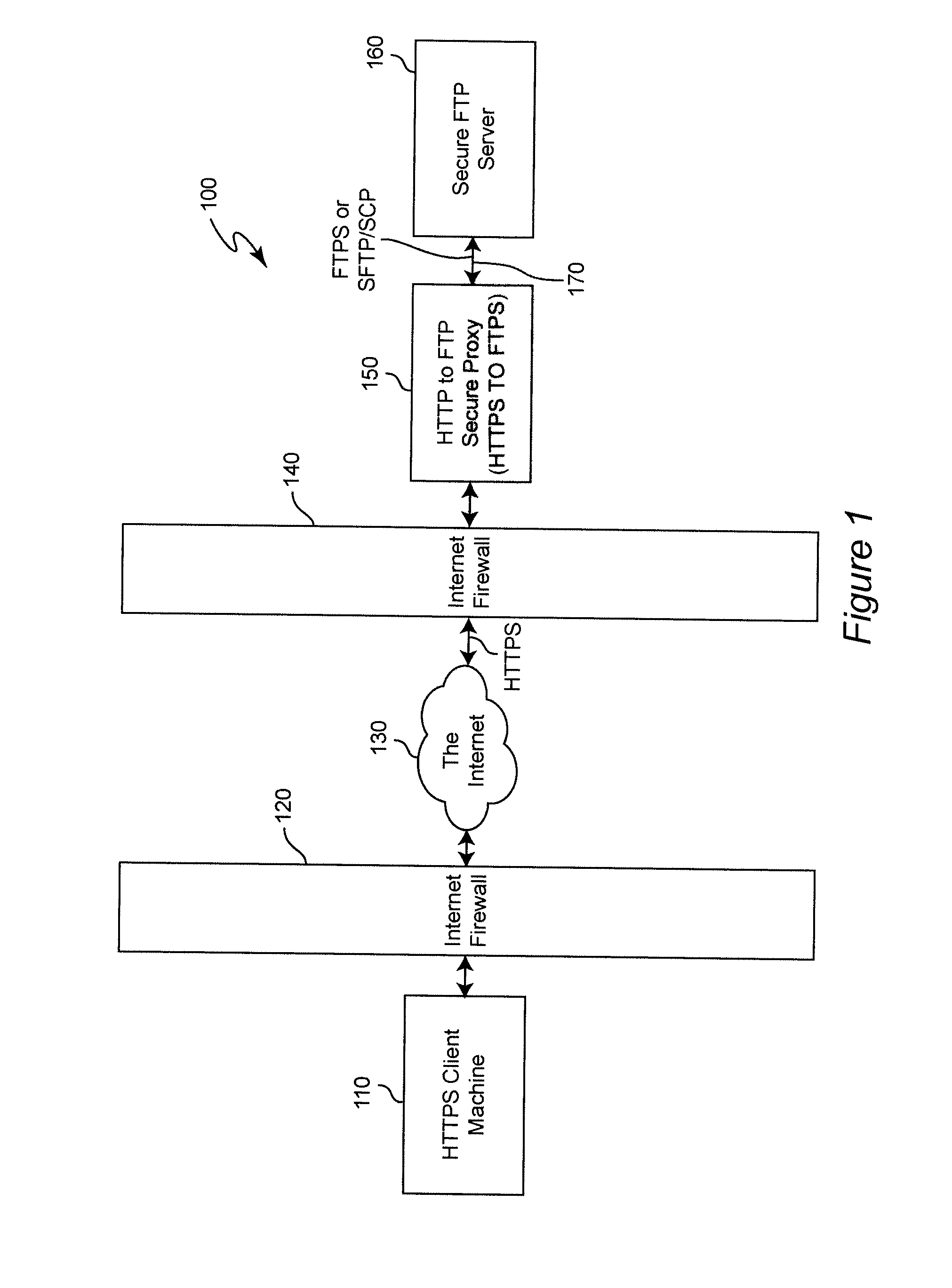
Secured FTP architecture
ActiveUS7308710B2Improve securityDigital data processing detailsMultiple digital computer combinationsPrivate networkIp address
A system for providing secured file transfer protocol (“FTP”) services between a passive FTP client system coupled to a private network and a FTP server coupled to a public communication network, such as the Internet. The passive FTP client system requests a communication session with a first proxy server that is coupled to the private network. The passive FTP client system submits to the first proxy server the uniform resource locator (“URL”) of a desired FTP server. The first proxy server initiates an outbound request from the private network, through a single port on a firewall, to a second proxy server that is coupled to the public communication network. The first proxy server submits the URL to the second proxy server. The second proxy server uses the URL to establish a FTP session with the desired FTP server. Upon receiving an identified socket provided by the FTP server for the data channel, the first proxy server changes the received data packets from the FTP server by substituting its own IP address for the FTP server's IP address, thus identifying a new socket on the first proxy server. The passive FTP client system transmits a FTP data request to the new socket on the first proxy server. The first proxy server forwards the data request to the FTP server via the outbound connection established with the second proxy server. All FTP data flows through a single port on the firewall.
Owner:JPMORGAN CHASE BANK NA
Configurable secure FTP
A method, system, and computer program product for providing automatic reconfigurable secure File Transfer Protocol (sFTP) software for sFTP transfers for clients is provided. In one embodiment, a property file is created, wherein the property file contains configuration information, such as, for example, destination host, port, user ID, password, pickup directory, destination directory, and encryption public key, for each client. Software component parameters used for sending and receiving files via a FTP and for encrypting the files prior to sending the files and decrypting the files after receiving the files are configured based on the configuration information in the property file. The property file is monitored for changes and the software components for a client are automatically reconfigured if the property file changes to reflect the new configuration information.
Owner:HEWLETT PACKARD DEV CO LP
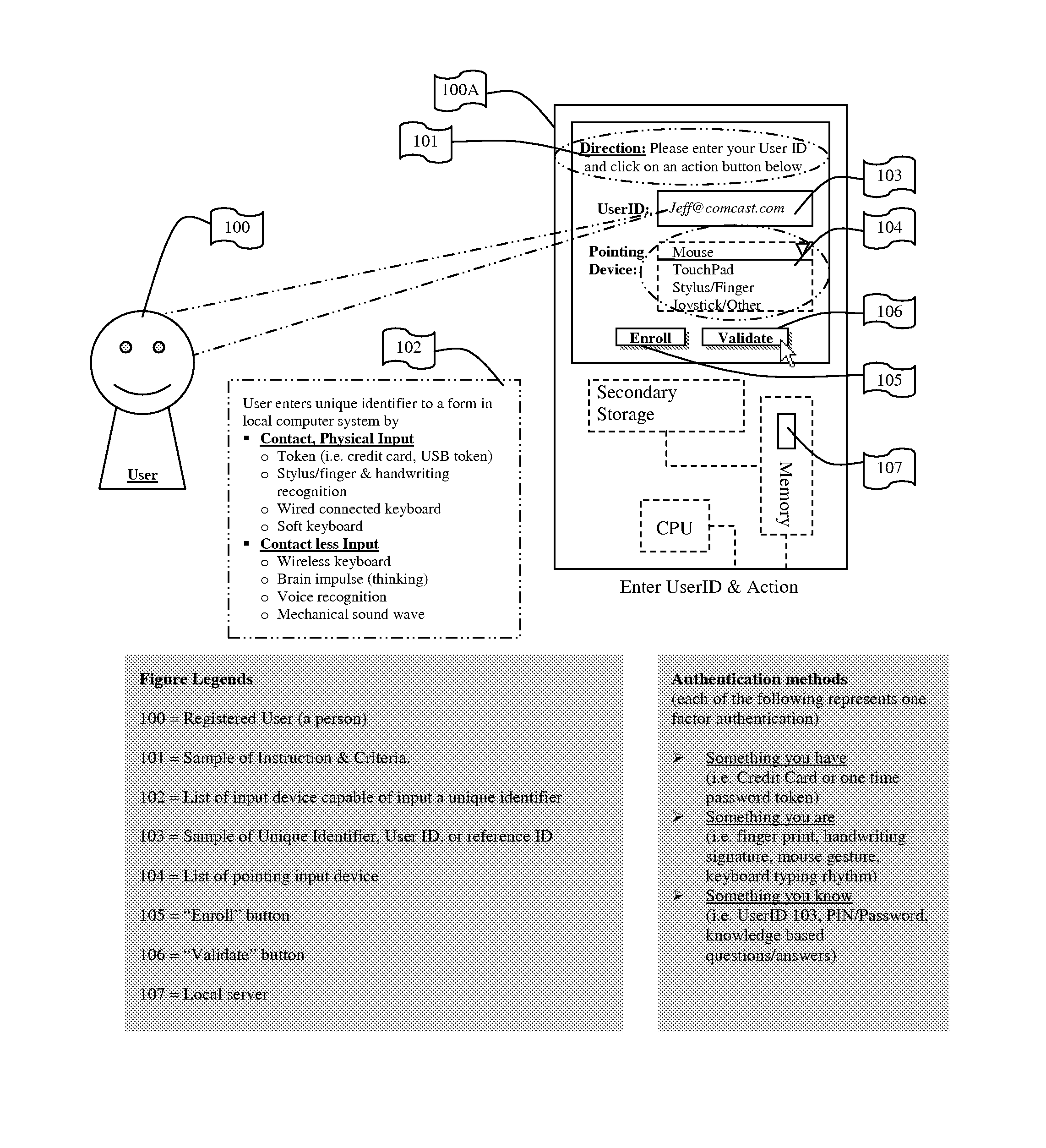
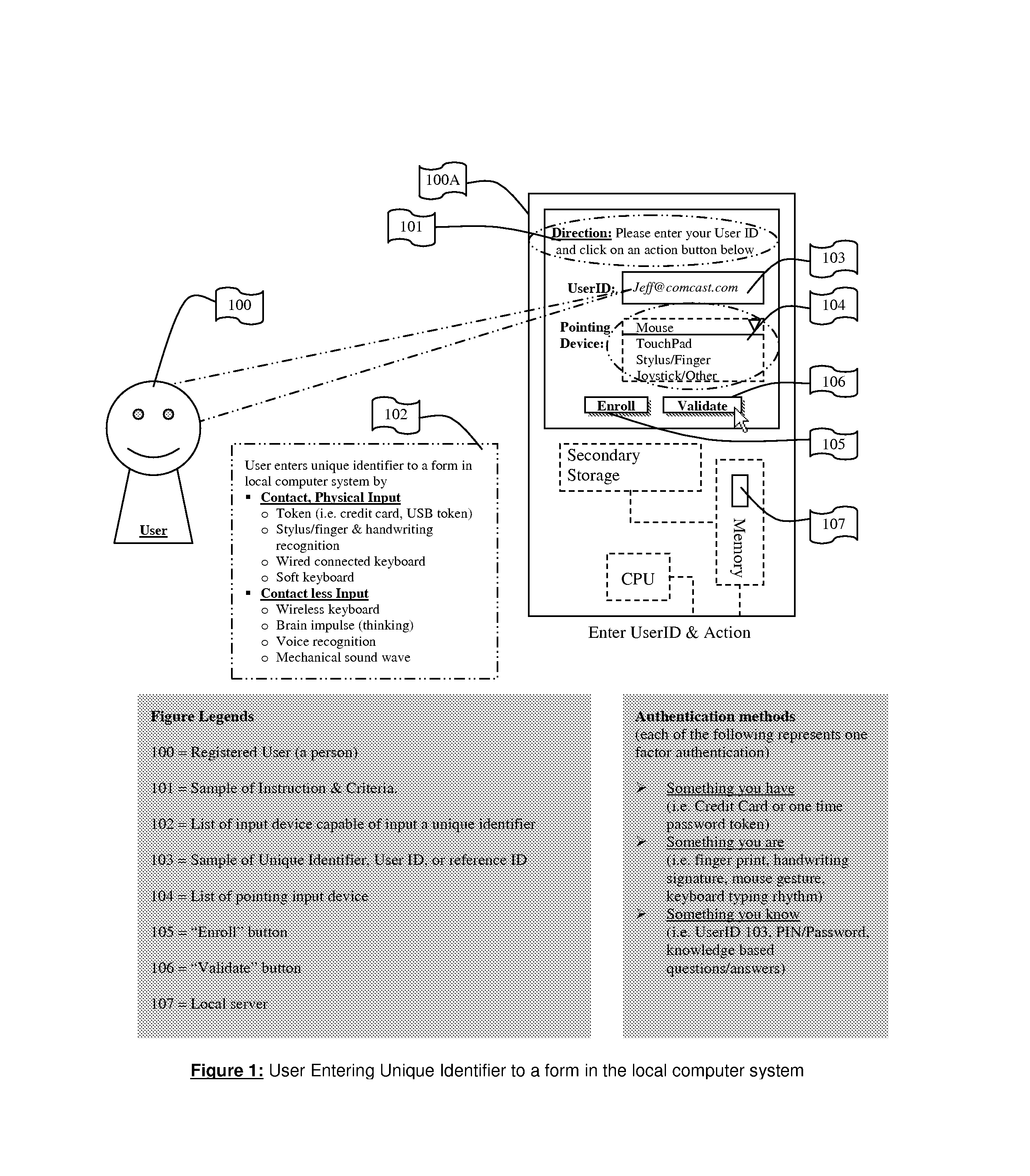
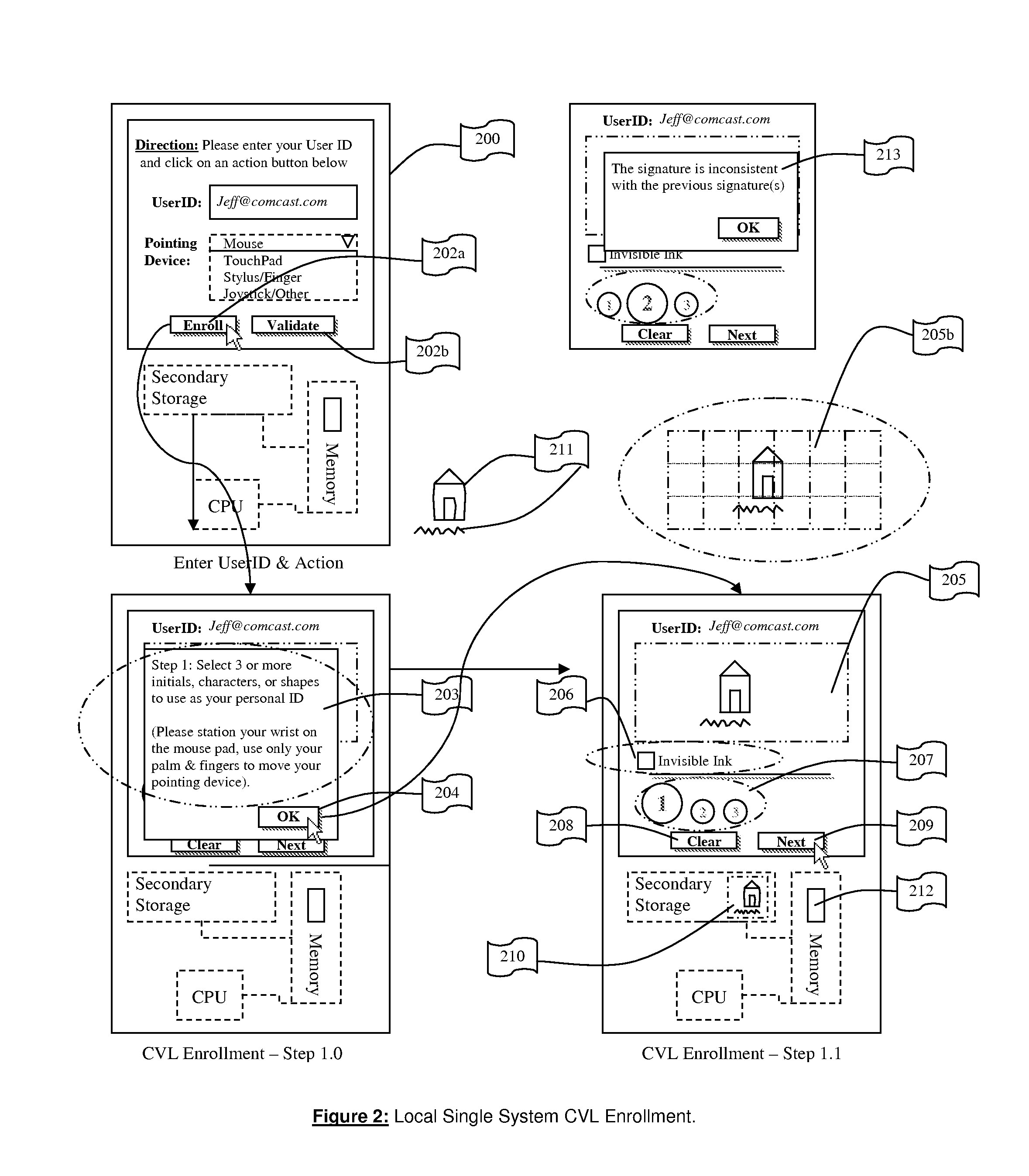
System for and Methods of Storing and Comparing Computer Generated Continuous Vector Lines through a Non-Secure or a Secure Communication Channel
ActiveUS20070236453A1Character and pattern recognitionCathode-ray tube indicatorsTerm memoryPointing device
The present invention includes a system for and methods of storing and comparing computer generated vector lines through an insecure or a secure communication channel. A continuous vector line (CVL) identifier includes from an ordered collection of 2 or more points. Using an input device (such as computer keyboard, finger, soft keypad, or any other input from body movements or input from electrical current or impulses, or input from human or mechanical sound waves) to a physical machine, or through a token (such as credit card, USB token, which can be carried around by user), a user enters and sends their unique identifier and reference code (such as a personal identification number (PIN), and / or password or other secret code) to the physical machine by making a contact or contact-less to the computer system. As part of the enrollment process the user inscribes a pre-determined set of continuous vector lines (CVLs). The CVLs include data points that are collected from any computer pointing device, such as a mouse, stylus or a digitizer tablet, in a specific format, using a push down anatomical technique and are sent to local active content (such as a library, or a program, or an add-on to the Internet browser such as ActiveX) or a remote server for further analysis of the two CVL's. A user should go through an Enrollment and Verification process to capture the data points and this process uses a two factor authentication and a verification scheme. The collected data points that represent a CVL profile made previously is kept in a database, registry, or memory that can be encrypted and accessed by using a reference number or other unique identifier. Access is either locally or remotely through any wired or wireless medium such as the Internet, Secure File Transfer Protocol (SFTP) server, cellular network or other communication connection to enable the comparison of a newly generated CVL identifier to the CVL profile generated previously.
Owner:JCLADS
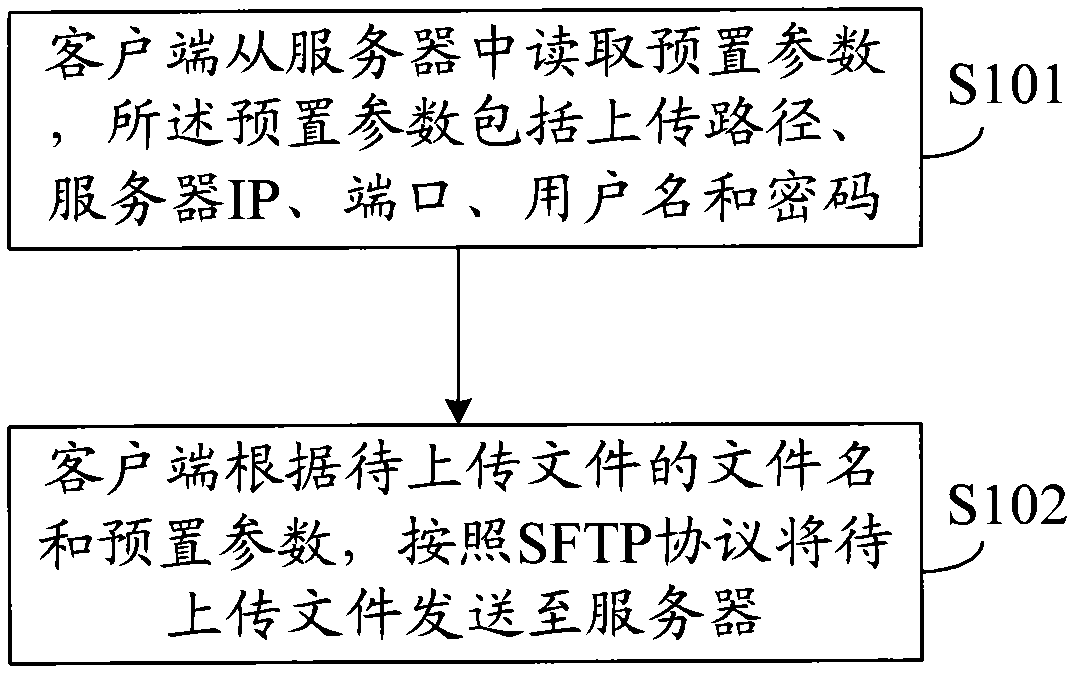
File uploading and downloading methods, system and related equipment based on SFTP (Secure File Transfer Protocol)
ActiveCN102231742ARealize automatic identificationEliminate potential safety hazardsTransmissionSecure File Transfer ProtocolPassword
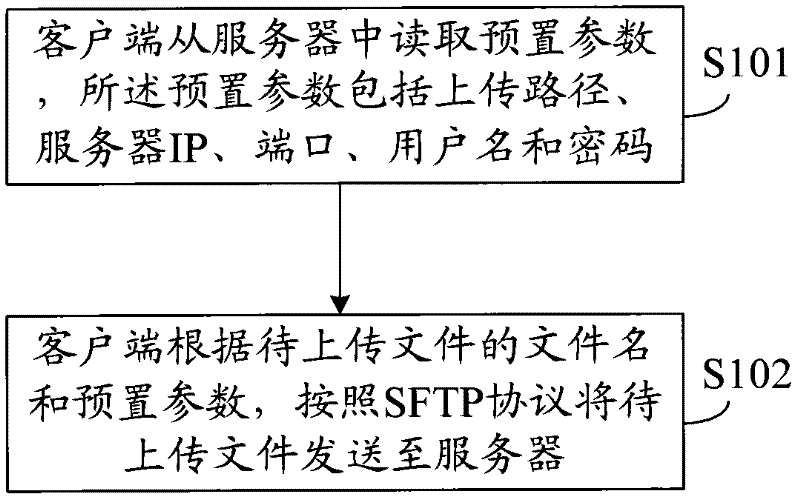
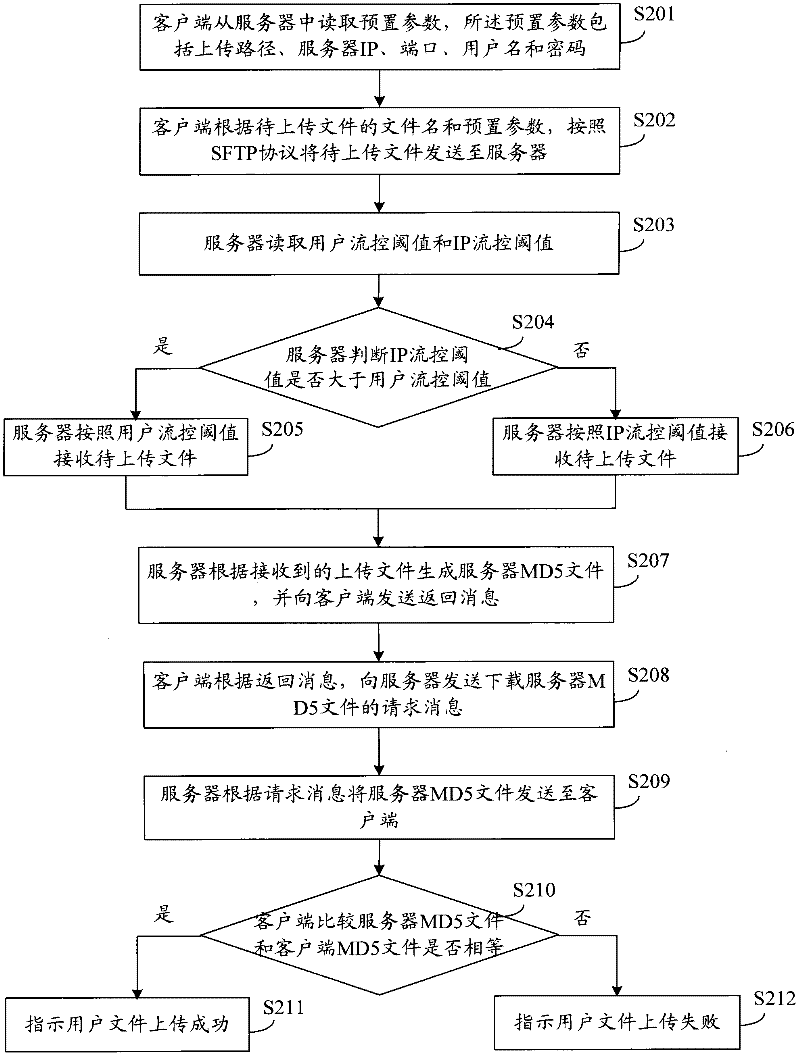
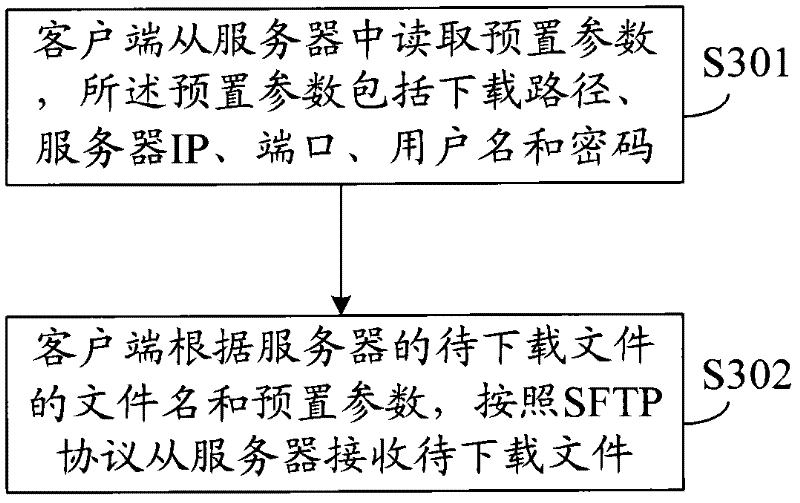
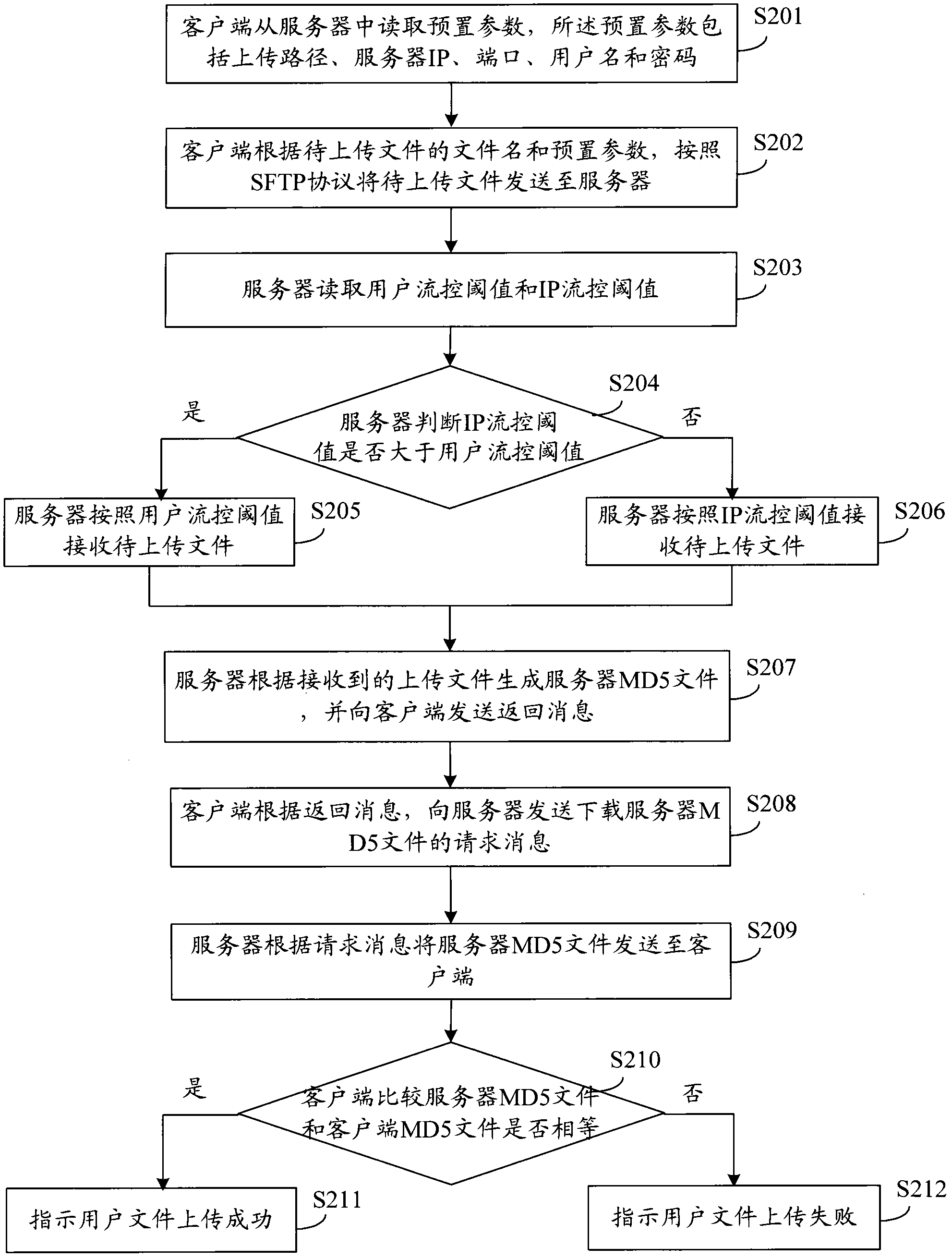
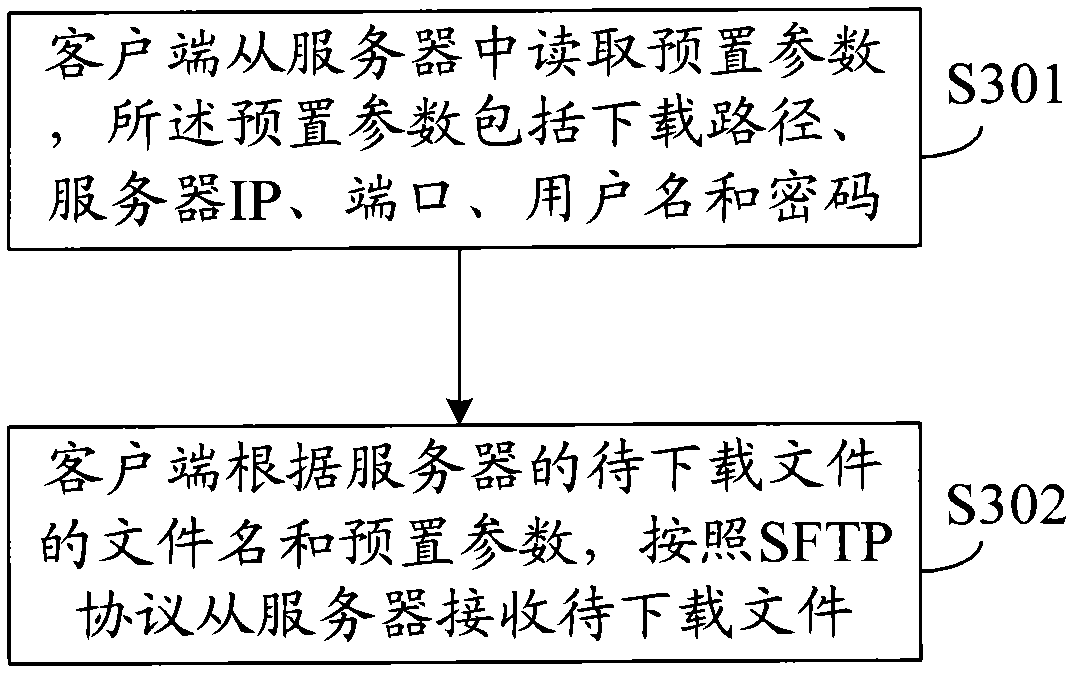
The invention discloses a file uploading and downloading methods based on an SFTP (Secure File Transfer Protocol), wherein the file uploading method comprises the following steps: a client reads preset parameters from a server, wherein the preset parameters comprise an uploading path, a server IP (Internet Protocol), ports, a user name and passwords; and the client sends a file to be uploaded to the server in accordance with the SFTP according to the file name of the file to be uploaded and the preset parameters. The file downloading method comprises the following steps: the client reads preset parameters from the server, wherein the preset parameters comprise a downloading path, the server IP, the ports, the user name and the passwords; and the client receives the file to be downloaded in accordance with the SFTP according to the file name of the file to be downloaded of the server and the preset parameters. Correspondingly, the invention also discloses the client and the server. In the invention, the file transmission is carried out according to the preset parameters by storing the preset parameters in advance and the catalog of a local disk does not need to be operated manually, thereby improving the safety and stability of the client and the server.
Owner:CHINA CONSTRUCTION BANK
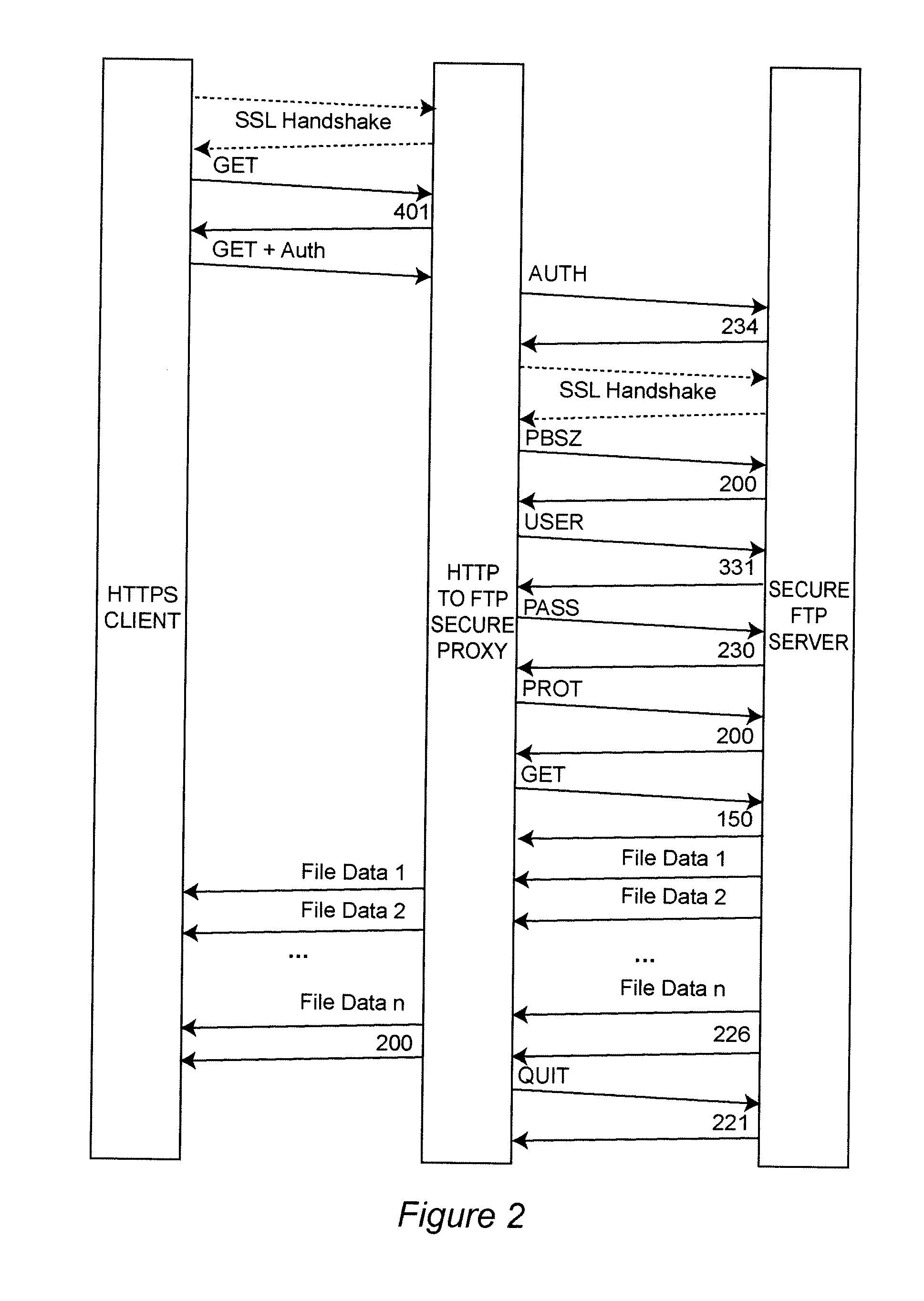
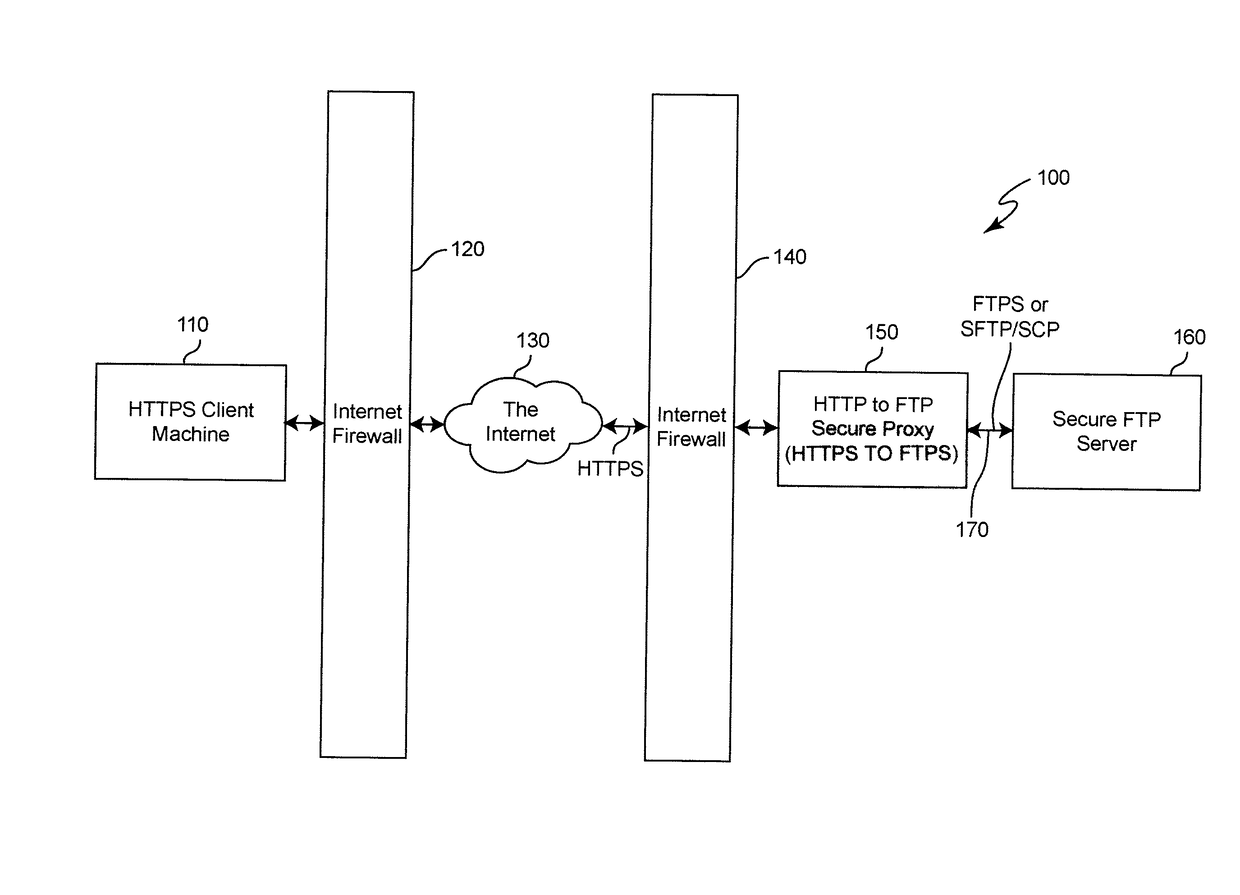
Method and System for Pervasive Access to Secure File Transfer Servers
ActiveUS20090199289A1Computer security arrangementsMultiple digital computer combinationsSecure communicationSecure File Transfer Protocol
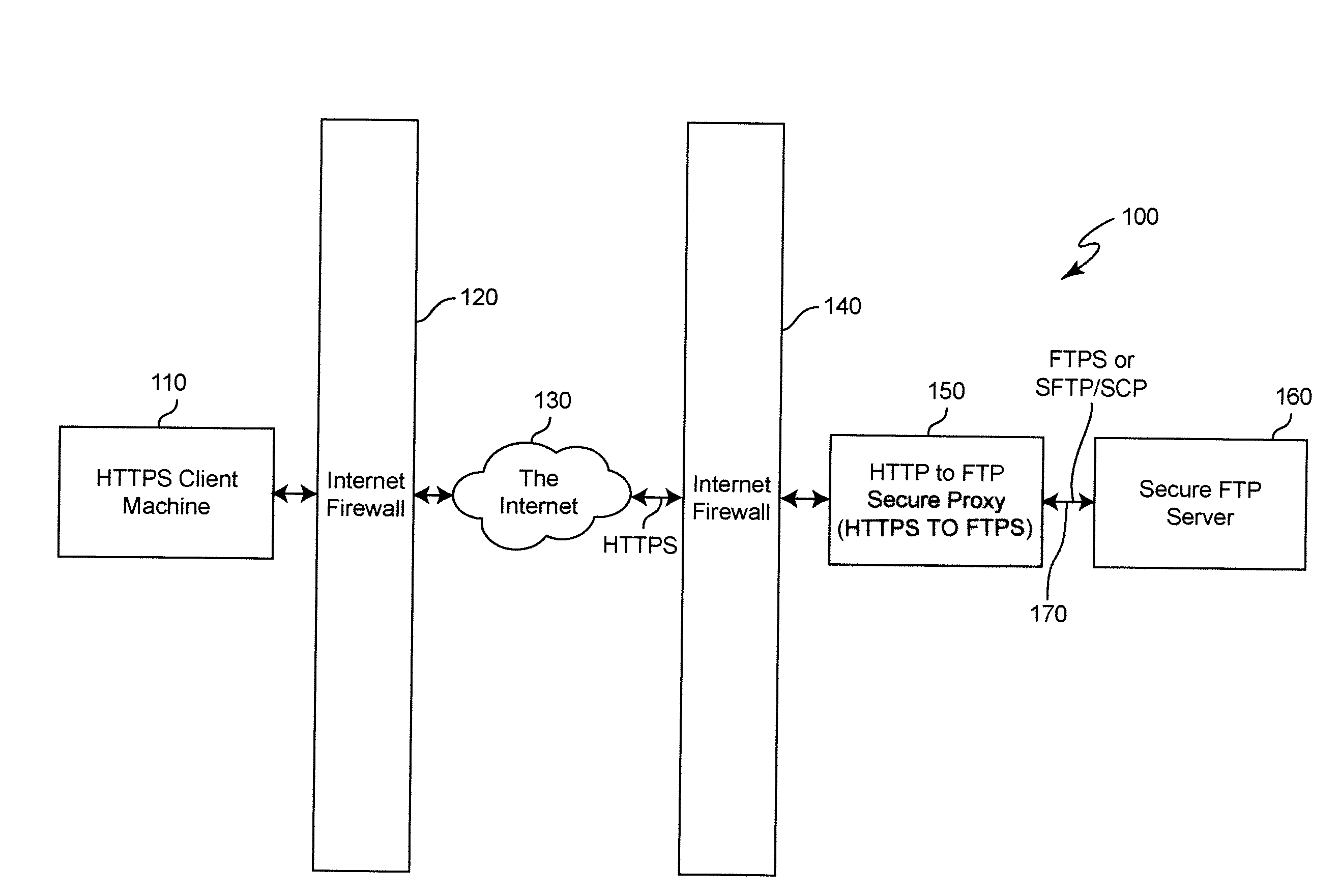
End-to-end file transfer security for file transfer is provided over a network such as the Internet between a client, using a secure communication protocol which is pervasively available, such as HTTPS, to a secure file server which is accessible only through a secure file transfer protocol which is not pervasively available by using a secure proxy for accessing the secure file server rather than providing a protocol break merely for traversing a firewall. The secure proxy is arranged to provide a protocol conversion between the pervasively available secure protocol and the communication protocol through which the server is accessible and which is not pervasively available. By doing so, the secure proxy inherits secure functions of the secure server which thus need not be separately or independently provided in the secure proxy.
Owner:IBM CORP
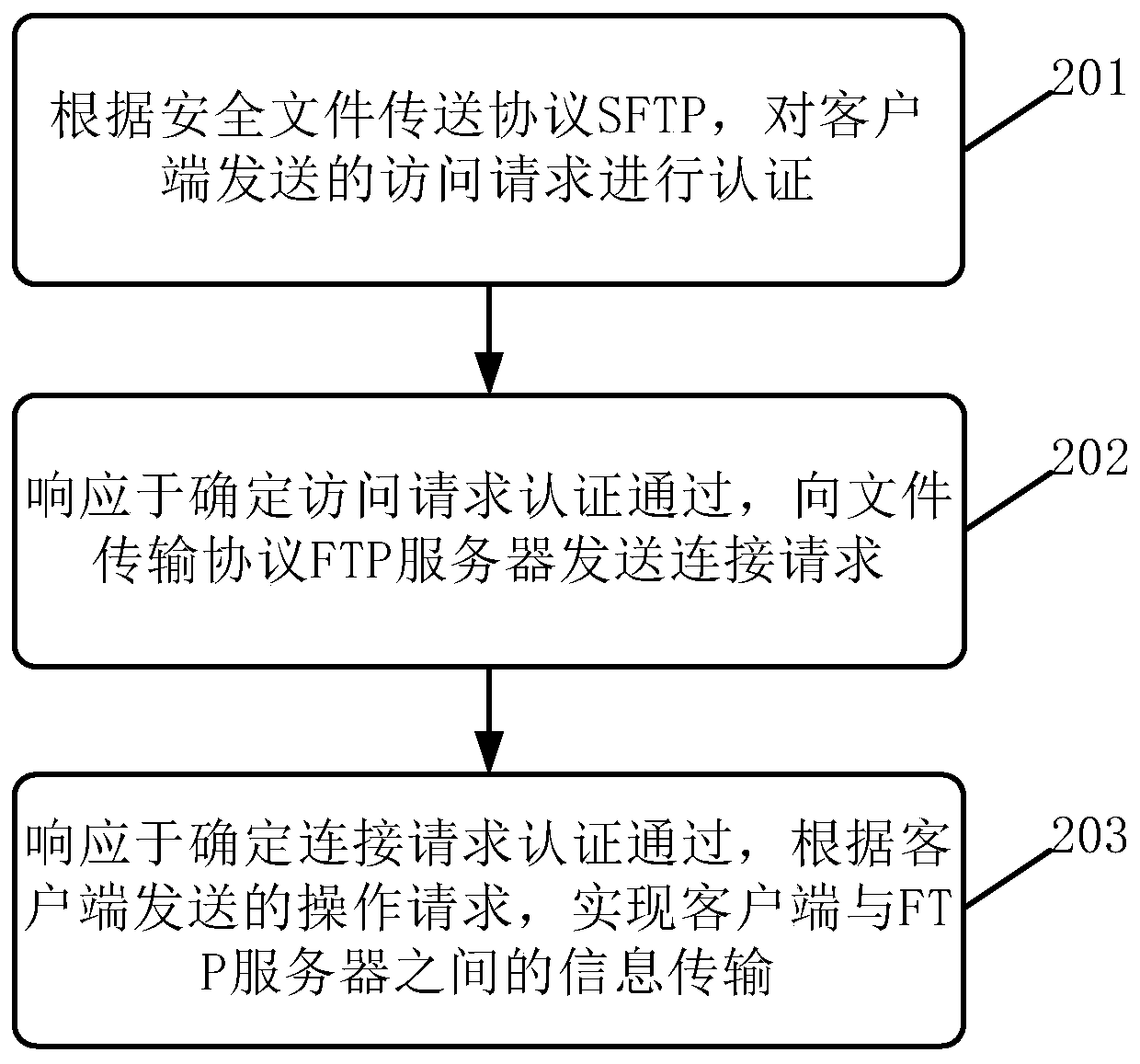
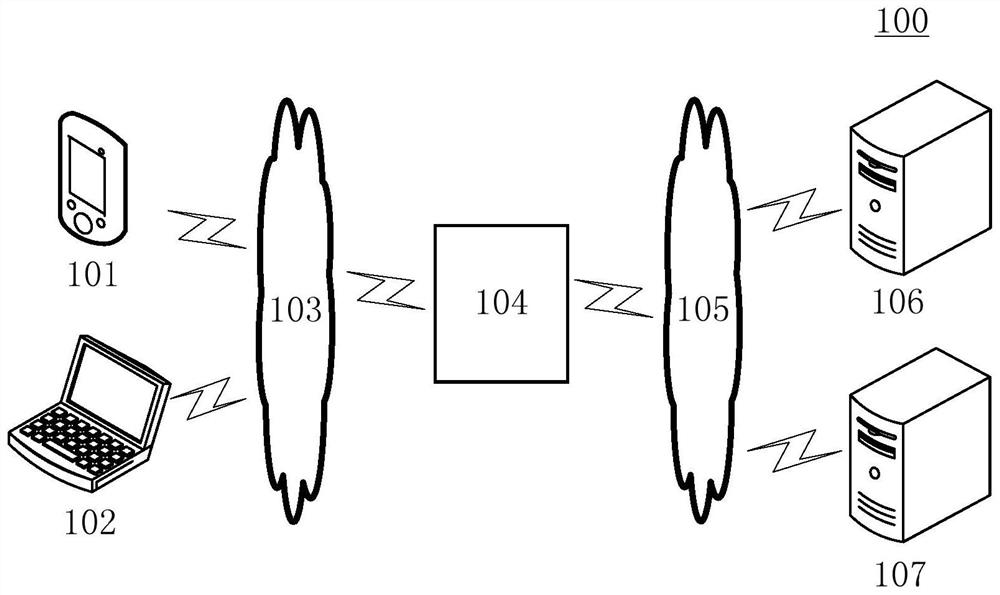
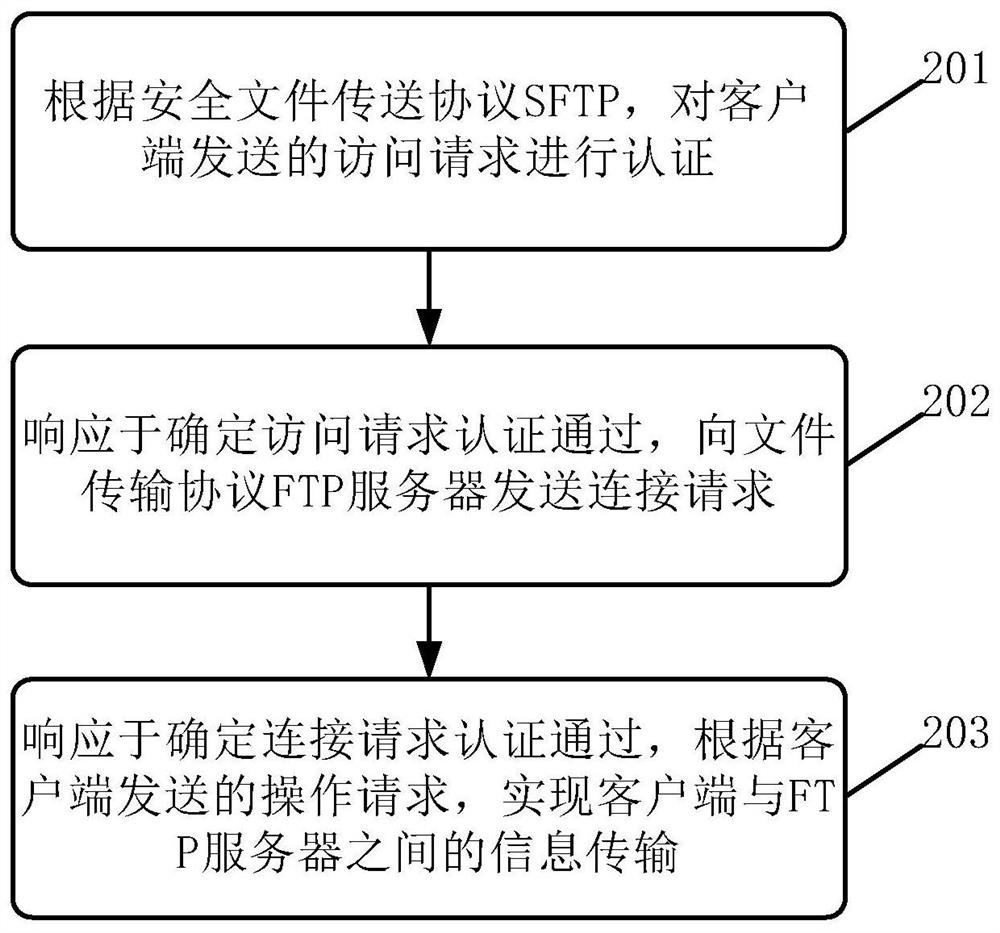
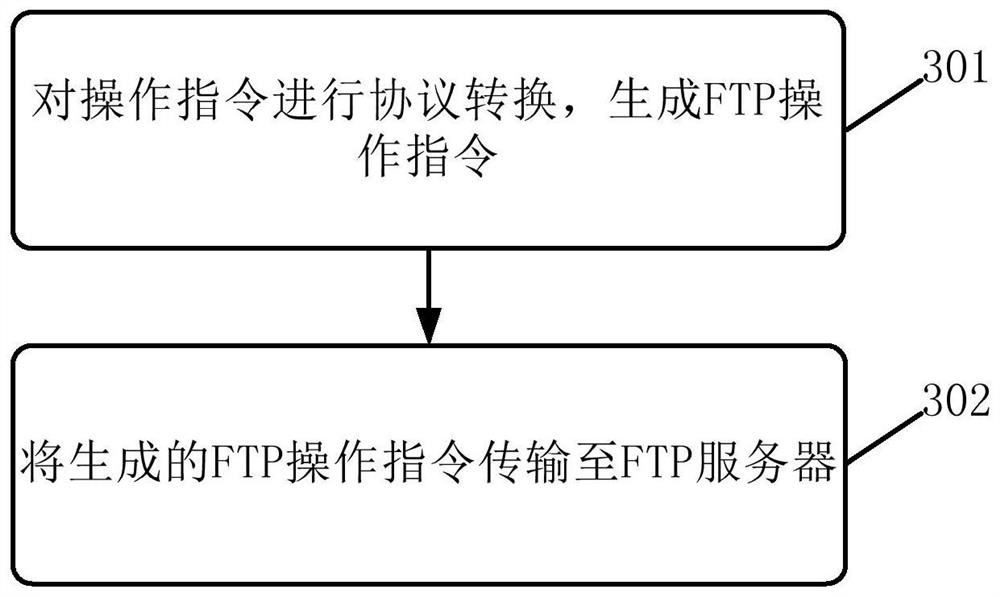
Information transmission method and device, electronic equipment and computer readable medium
ActiveCN109861973ARealize transmissionImplement encrypted transmissionTransmissionTransmission protocolInformation transmission
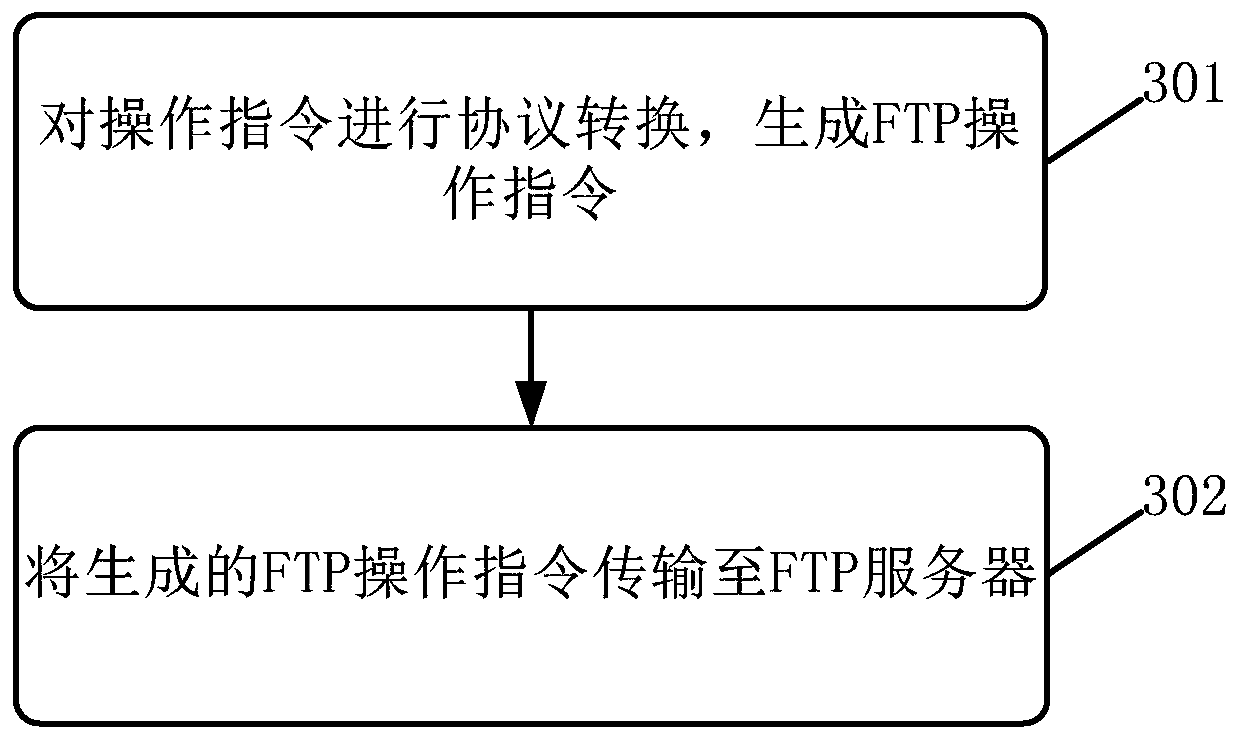
The embodiment of the invention discloses an information transmission method and device, electronic equipment and a computer readable medium. A specific embodiment of the method comprises the following steps: authenticating an access request sent by a client according to a secure file transfer protocol SFTP; In response to determining that the access request passes the authentication, sending a connection request to a file transfer protocol FTP server; And in response to determining that the connection request passes the authentication, realizing information transmission between the client andthe FTP server according to an operation request sent by the client. According to the embodiment, the FTP transmission protocol with the client is converted into the SFTP transmission protocol, so that encrypted transmission of information can be realized. In this way, the safety of information transmission is improved, and information leakage is prevented.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Method and system capable of remotely testing smart cards
InactiveCN104484275AImprove automated testingUniqueness guaranteedSoftware testing/debuggingSecure File Transfer ProtocolApplication server
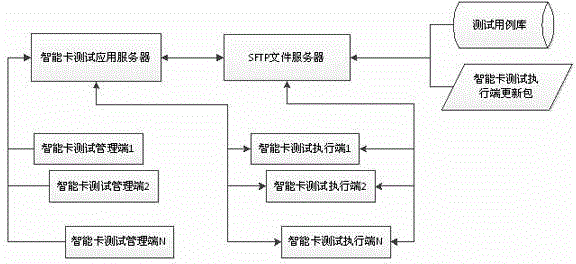
The invention provides a system capable of remotely testing smart cards. The system comprises a smart card testing application server, an SFTP (Secure File Transfer Protocol) file server, a test case library, a plurality of smart card testing management terminals, a plurality of smart card testing execution terminals and a smart card testing execution terminal updating package, wherein the SFTP file server is used for storing files, such as the smart card test case library, test logs, test reports and the smart card testing execution terminal updating package, and the smart card testing execution terminals interact with the SFTP file server by SFTP, so as to provide a guarantee for data security; the smart card testing management terminals are used for managing and monitoring an entire testing process and providing statistic and analysis functions; the smart card testing execution terminals are used for getting testing tasks, then, executing the testing tasks, generating the test logs and the test reports after execution is completed, and submitting the test logs and the test reports to the testing application server and the SFTP file server. The system can be used for carrying out automated test on the smart cards in a local area network or wide area network environment.
Owner:EASTCOMPEACE TECH
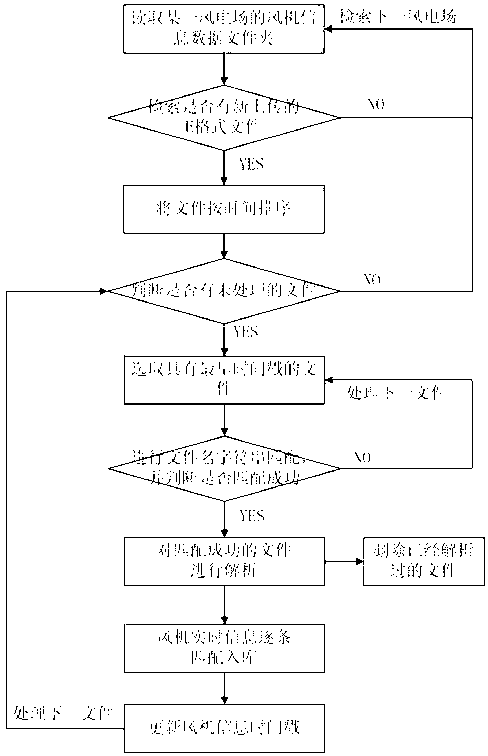
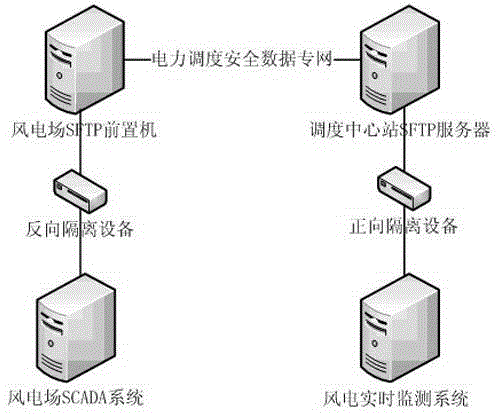
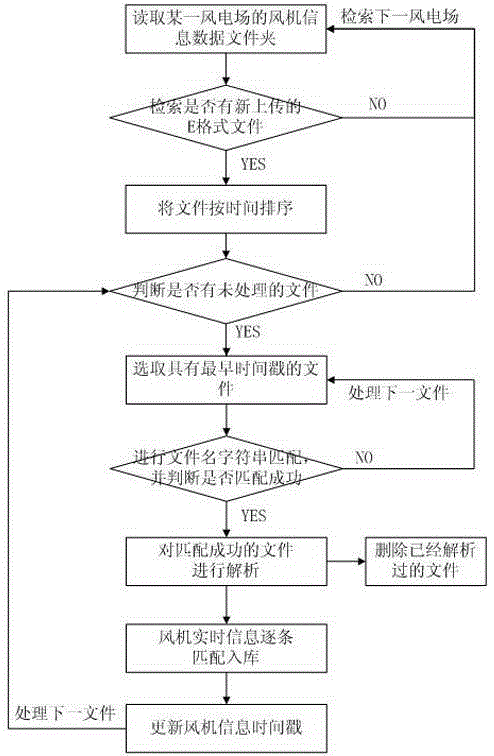
Real-time operating information monitoring method for multi-million kilowatt-level wind power base fan
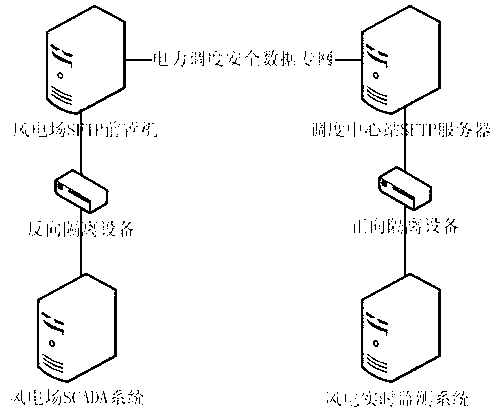
The invention discloses a real-time operating information monitoring method for a multi-million kilowatt-level wind power base fan. The real-time operating information monitoring method includes steps of acquiring fan operation data through an SCADA (supervisory control and data acquisition) system; writing the acquired fan operation data into E files line by line, transmitting the completed E-file data into an SFTP (secure file transfer protocol) prepositive server and a dispatch center station SFTP server of a wind power plant through an isolation equipment and storing the same in a real-time wind power monitoring server, and analyzing E-format files. The fan operation data are acquired through the SCADA system, stored according to the fixed formats, and transmitted to a database to store through the servers and the isolation equipment, and operation conditions of the fan can be checked according to the analyzed results of the stored data, thereby the purpose of accurately monitoring the multi-million kilowatt-level wind power base fan in real time is achieved.
Owner:STATE GRID CORP OF CHINA +2
Data transmission method and system
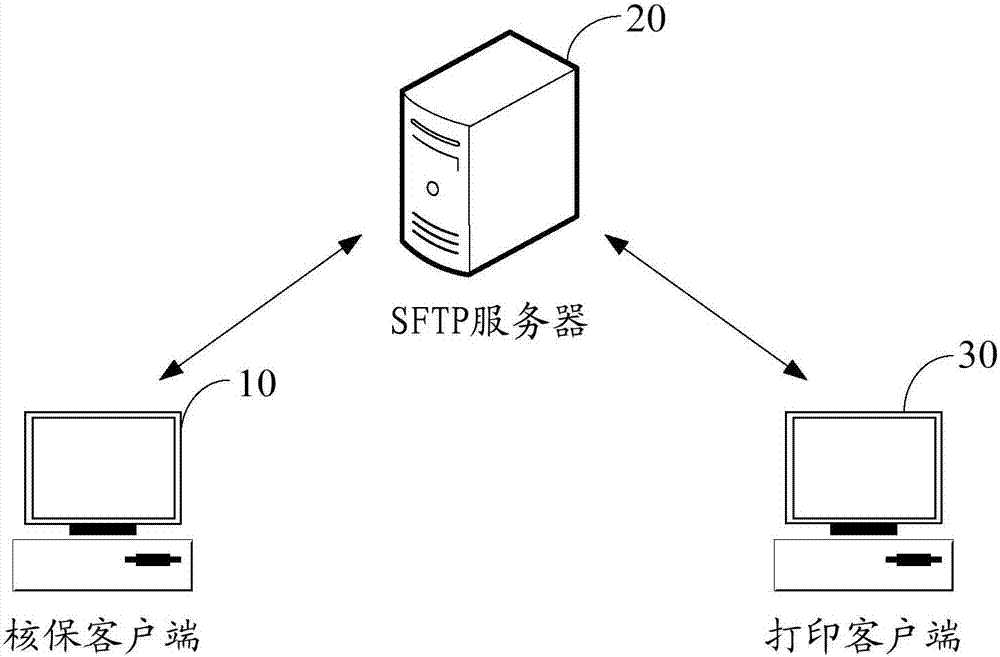
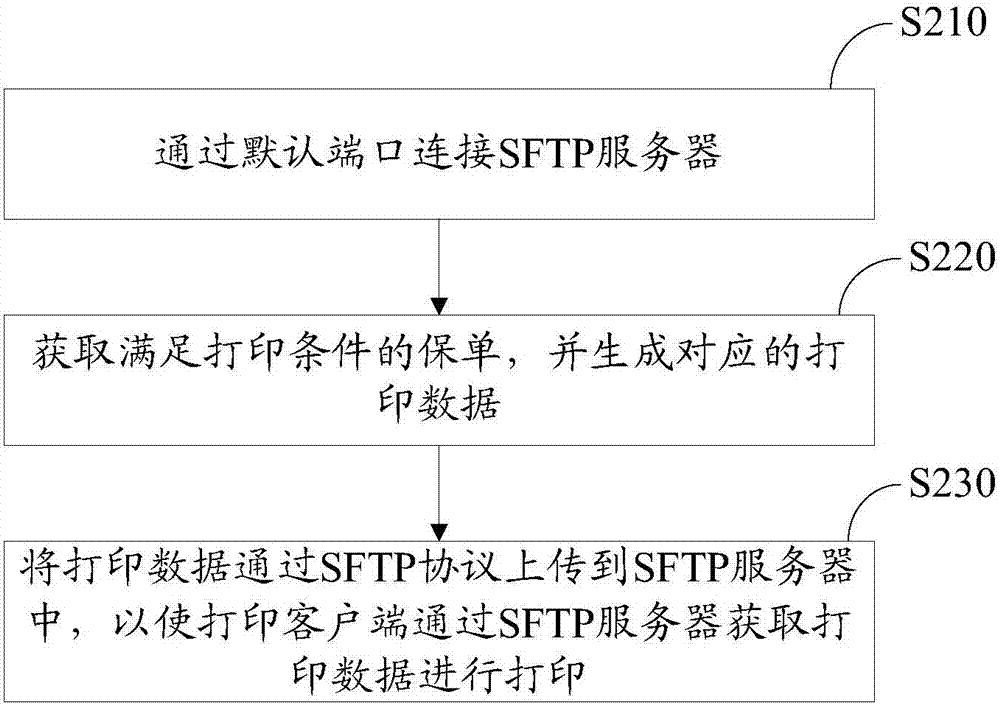
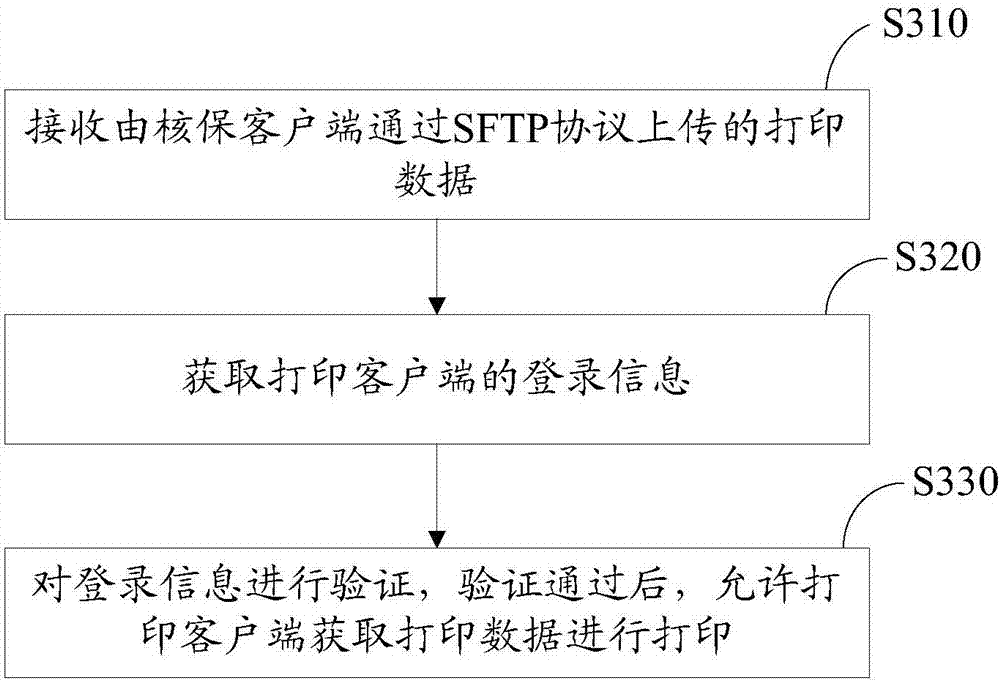
InactiveCN107239239APrevent tamperingPrevent loss and other problemsTransmissionDigital output to print unitsSecure File Transfer ProtocolTransfer procedure
The invention relates to a data transmission method and system. The above method comprises the following steps that: through a default port, connecting with an SFTP (Secure File Transfer Protocol) server; obtaining an insurance policy which meets a printing condition, and generating corresponding printing data; and uploading the printing data to the SFTP server through an SFTP protocol to enable a printing client side to obtain the printing data through the SFTP server and print the printing data. By use of the data transmission method and system, the printing client side directly obtains the printing data from the SFTP server, the problem that the printing data is tampered or lost in a transmission process can be avoided, the printing data is subjected to encryption transmission through the SFTP protocol, and therefore, the transmission process of the printing data is safe.
Owner:PING AN TECH (SHENZHEN) CO LTD
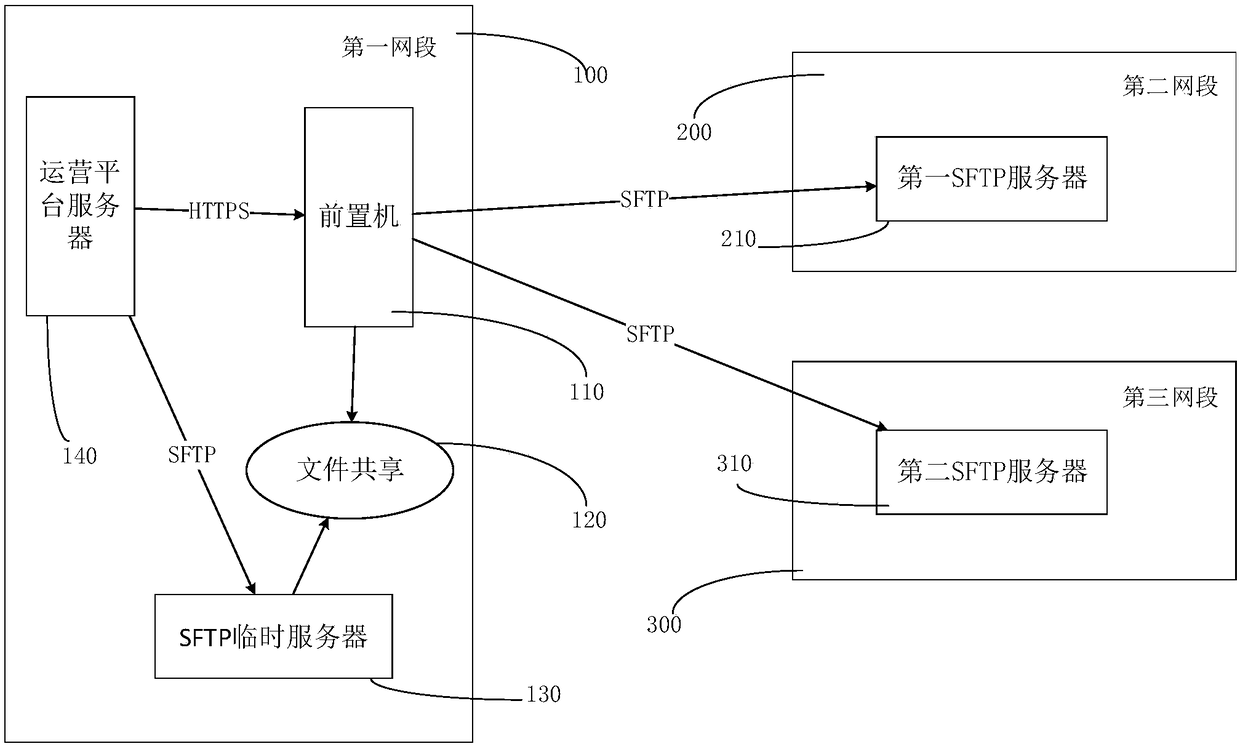
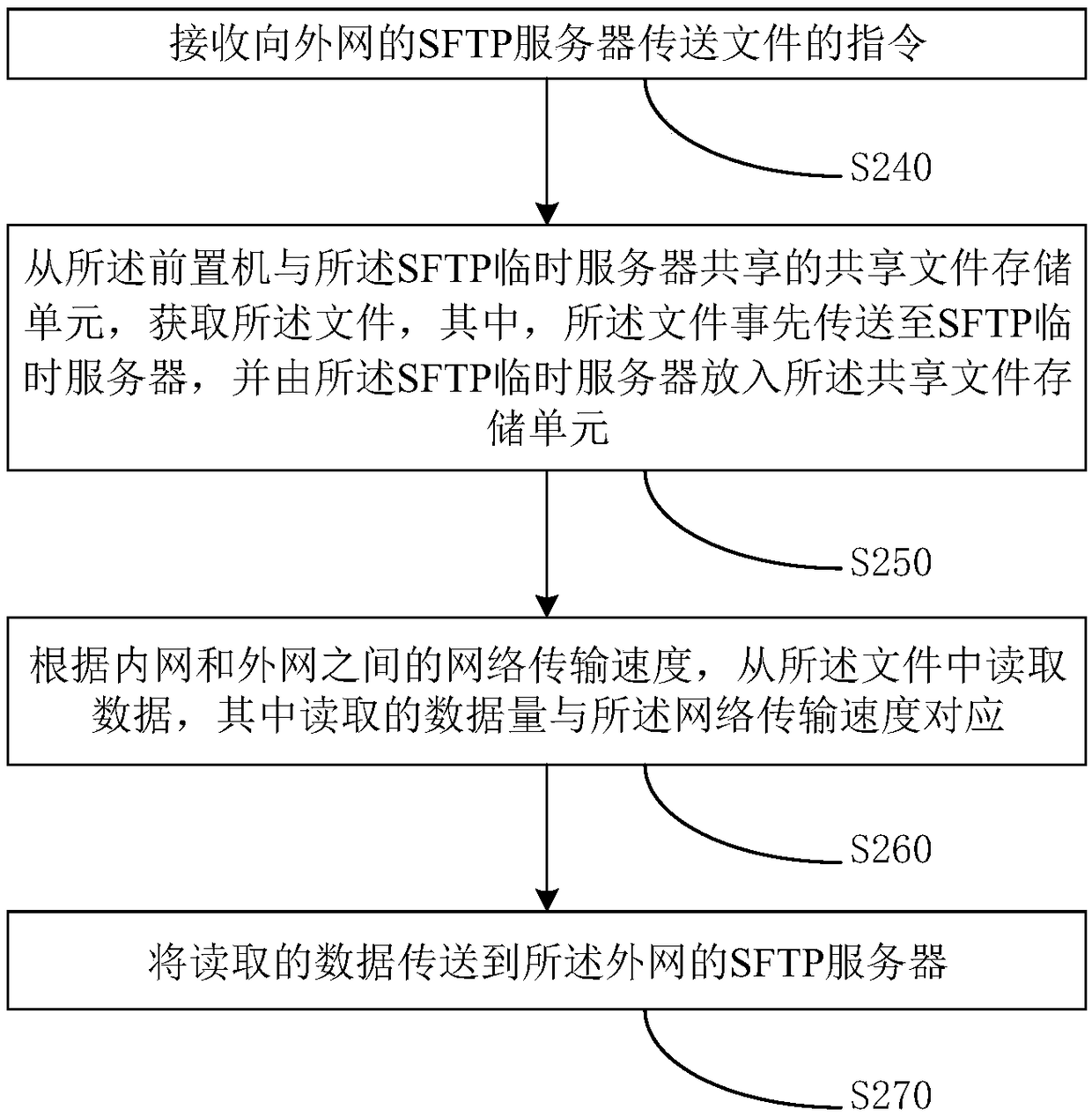
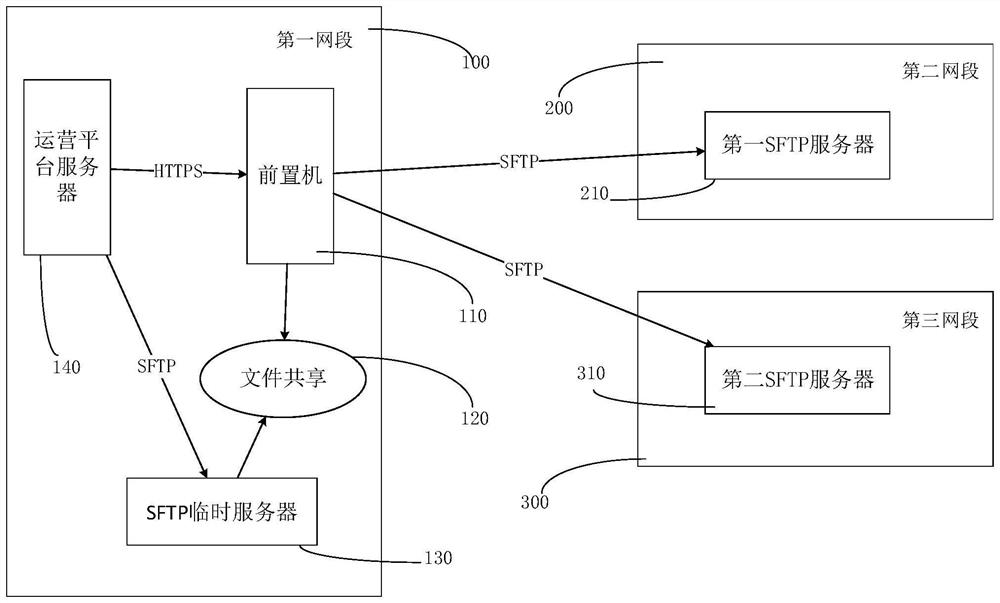
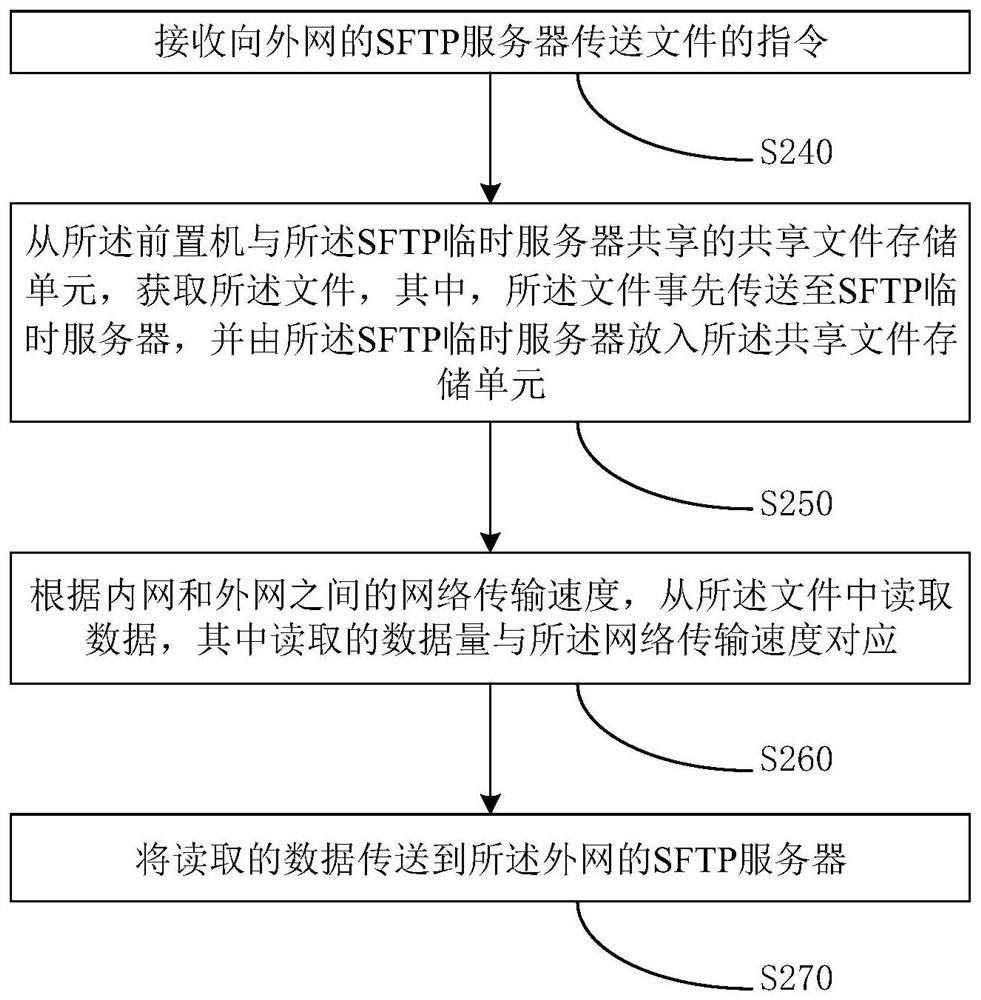
File transfer method based on SFTP and related device
ActiveCN109391694AImprove securityImprove transmission efficiencyTransmissionSecure File Transfer ProtocolProtocol for Carrying Authentication for Network Access
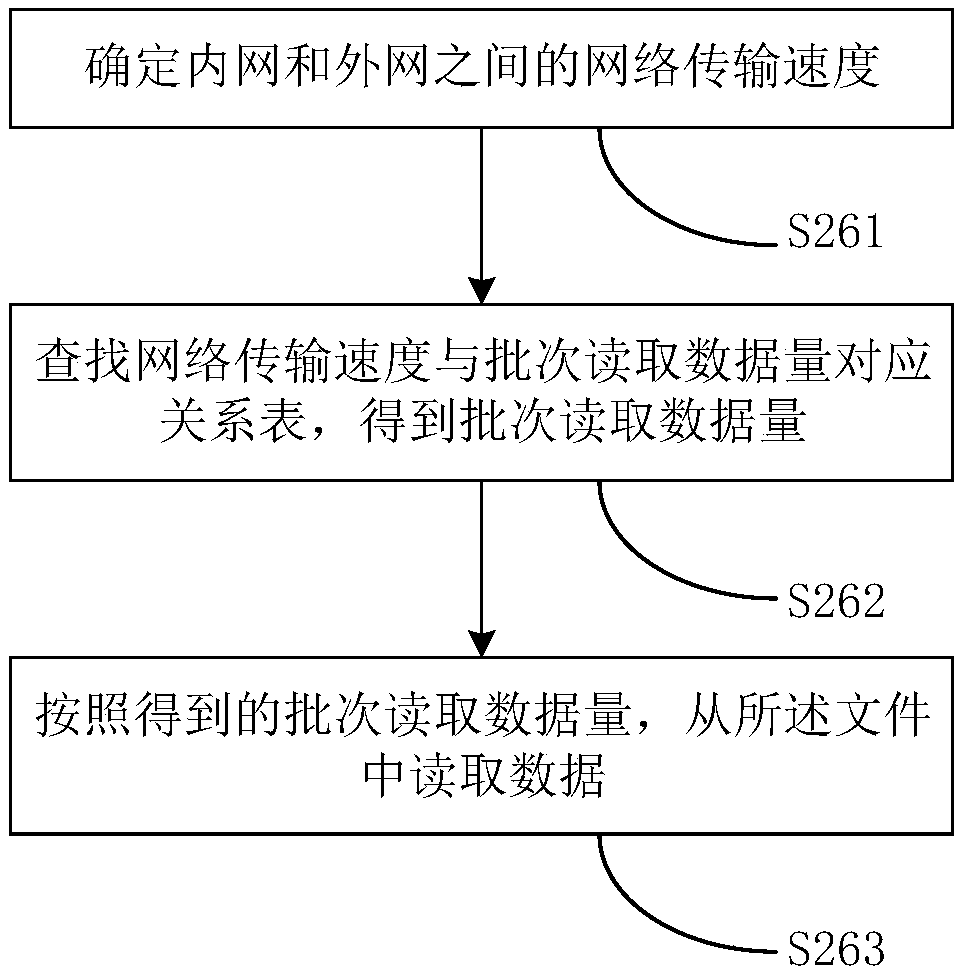
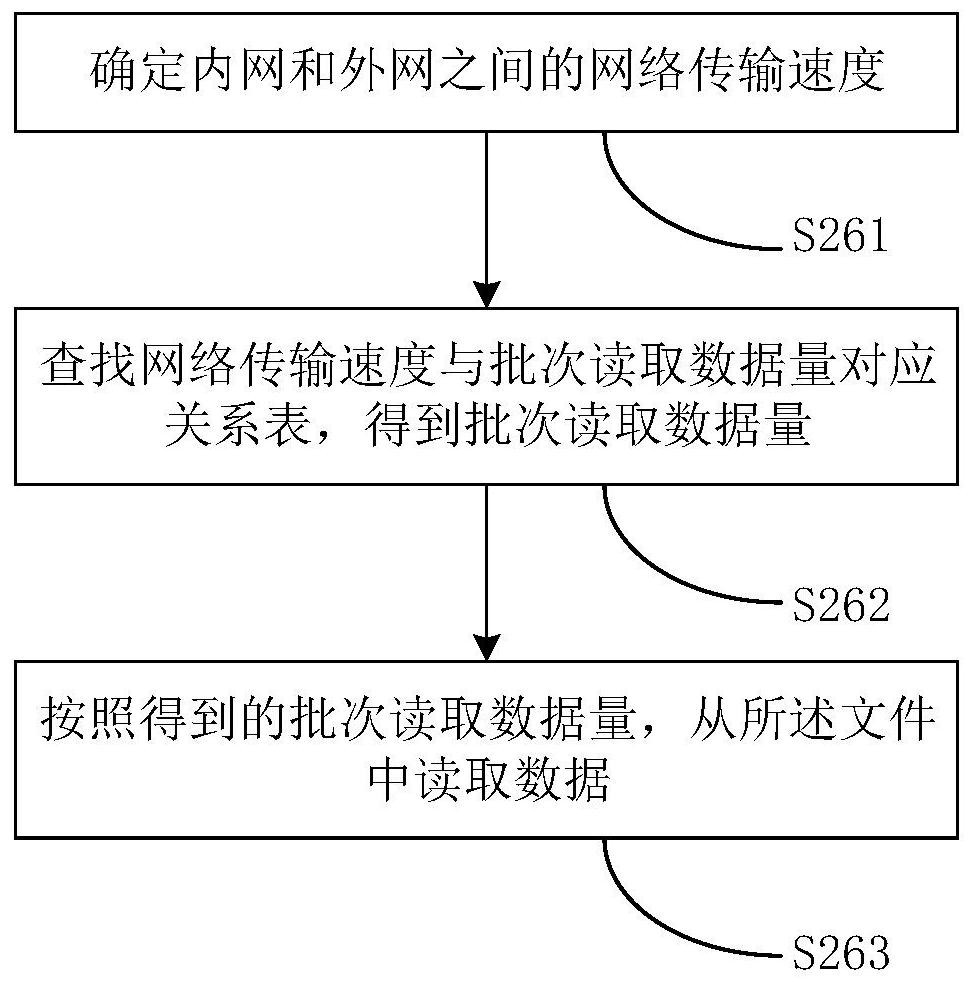
The invention discloses a file transfer method based on a secure file transfer protocol (SFTP), a device, a computer device and a storage medium, and belongs to the technical field of data transmission. The method comprises: in response to trigger of transferring a file to an SFTP server of an external network, a shared file storage unit shared by a front-end processor and a SFTP temporary serveracquiring the file, wherein the file is transmitted to a SFTP temporary server in advance and is placed in the shared file storage unit by the SFTP temporary server; reading data from the file according to network transmission speed between an internal network and the external network, wherein the read data amount is corresponding to the network transmission speed; and transmitting the read data to the SFTP server of the external network. Thus, security of data transmission among SFTP servers is improved, disconnection is reduced, transmission efficiency is improved, and network security is ensured.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
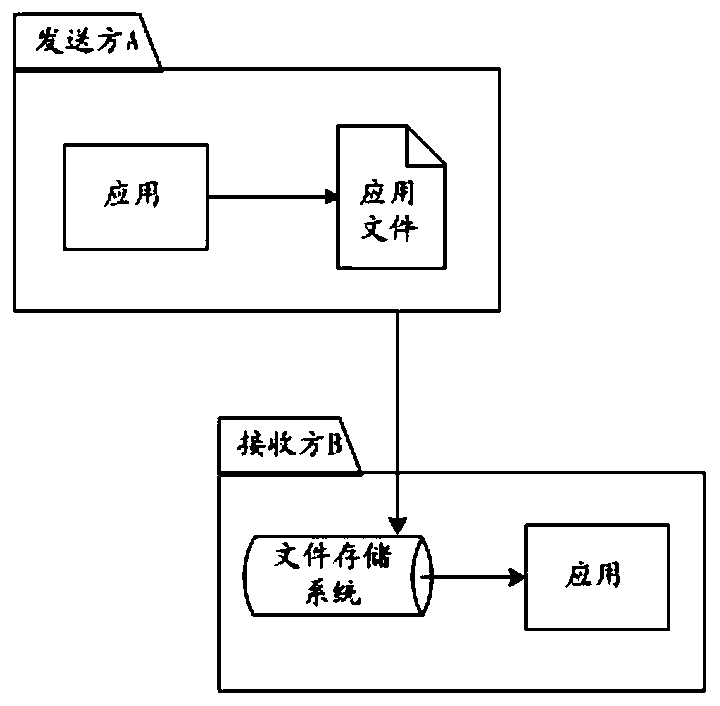
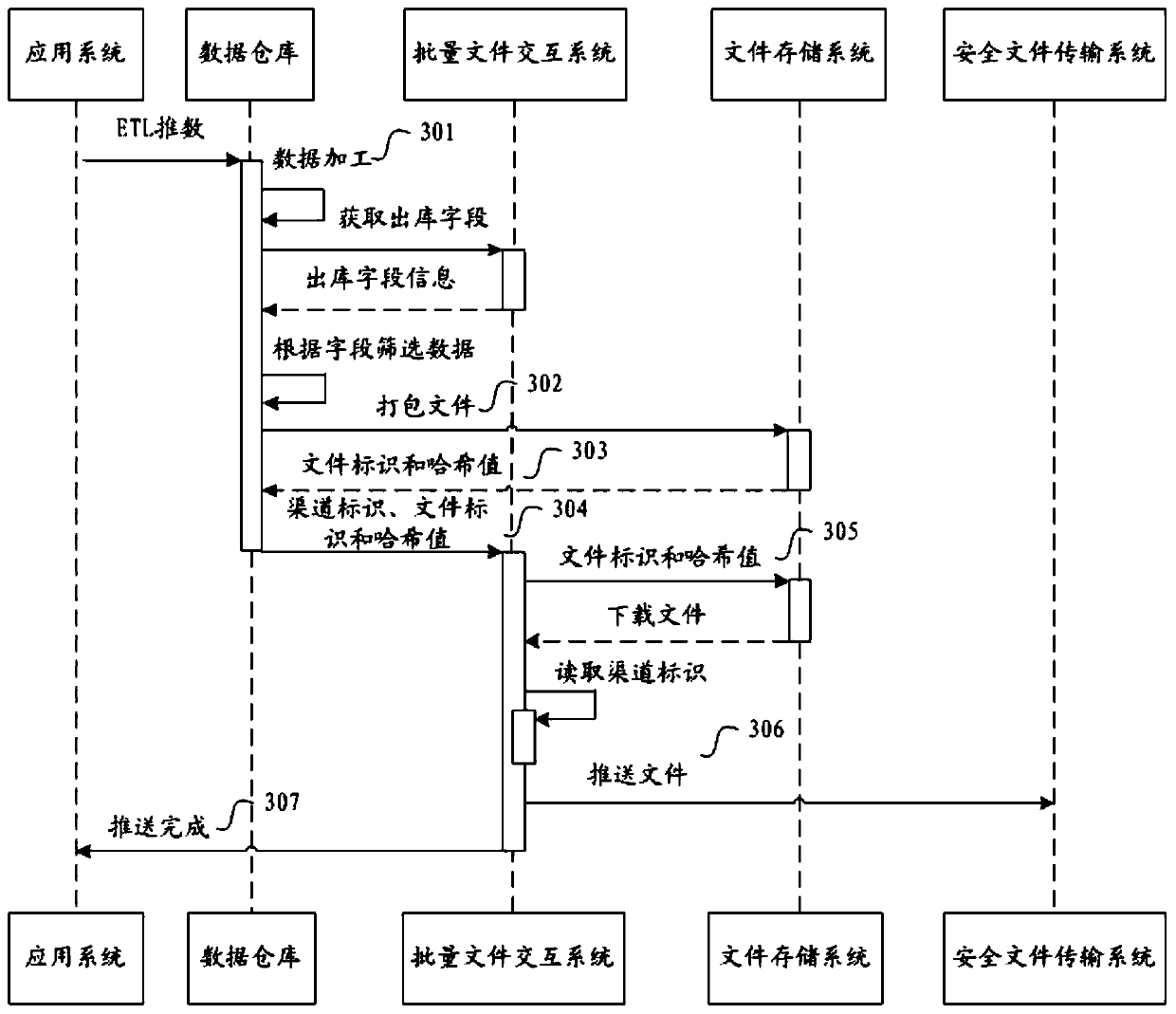
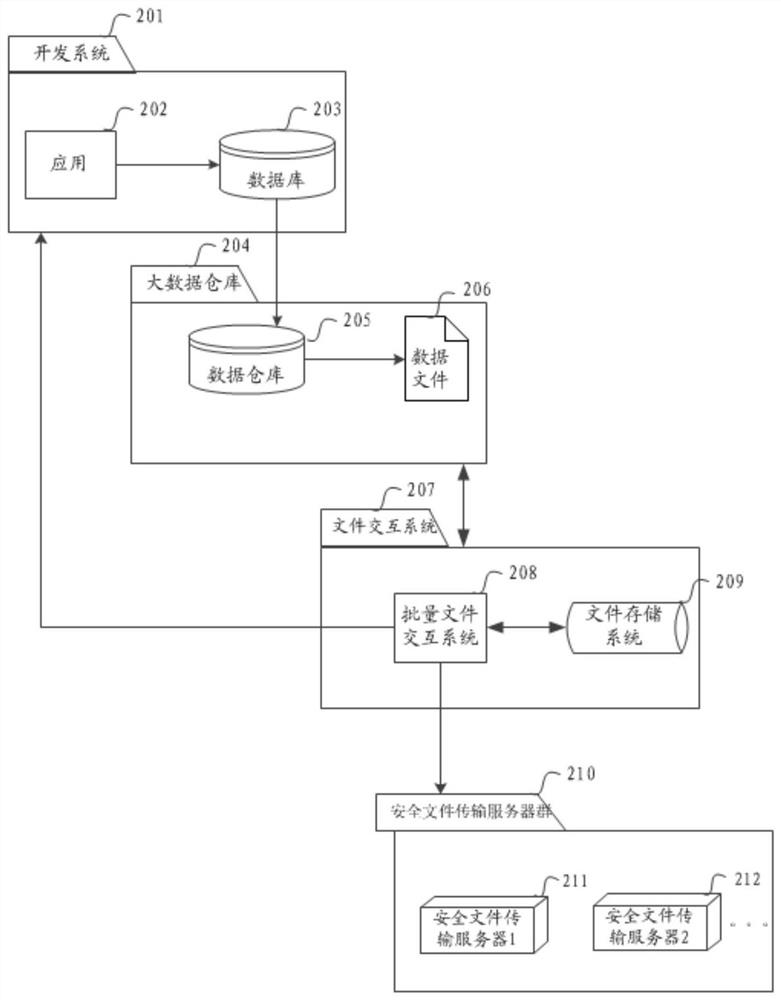
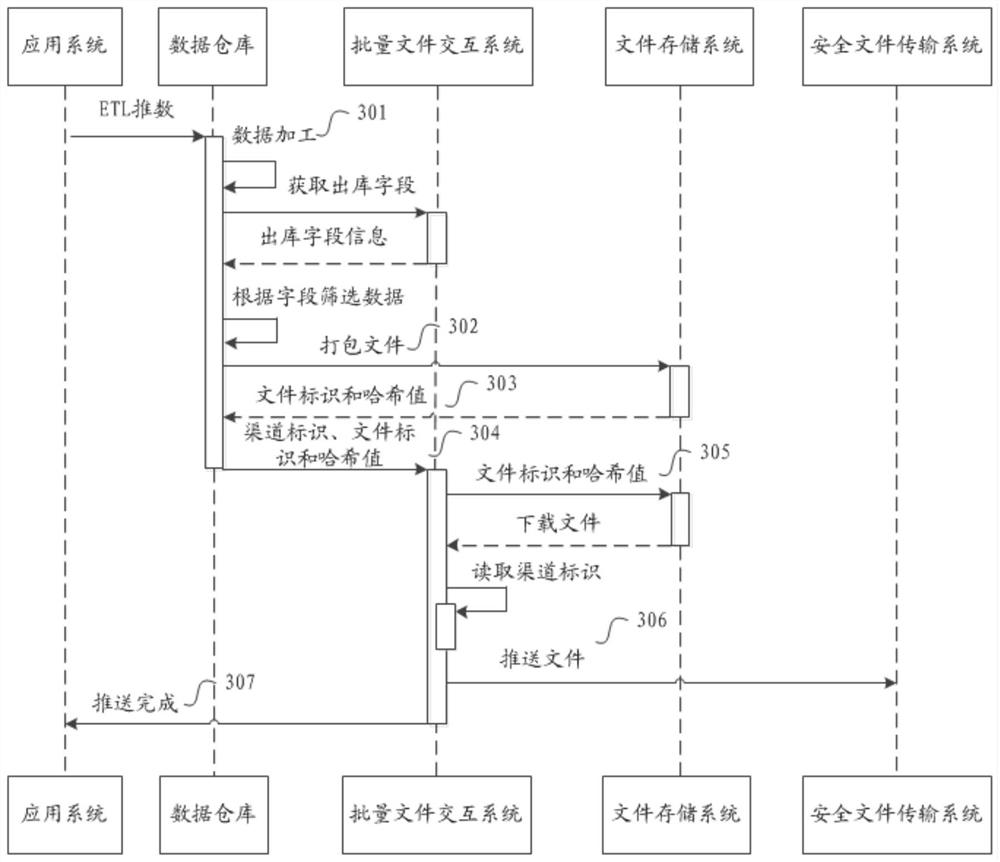
File interaction processing method, device and system
ActiveCN110177154AImplement configurationAchieve separationUser identity/authority verificationFile transmissionSecure File Transfer Protocol
The invention discloses a file interaction processing method, device and system, and relates to the field of file transmission, and the method comprises the steps: obtaining a first channel identifier, a first file identifier of a first file, and a first hash value of the first file; wherein the first channel identifier is used for indicating a secure file transfer protocol SFTP server corresponding to a first file receiver; downloading the first file from a file transfer protocol FPS server according to the first file identifier of the first file and the first hash value of the first file; and storing the first file to an SFTP server corresponding to the first channel identifier according to the first channel identifier. The method can be applied to the finance technology (Fintech).
Owner:WEBANK (CHINA)
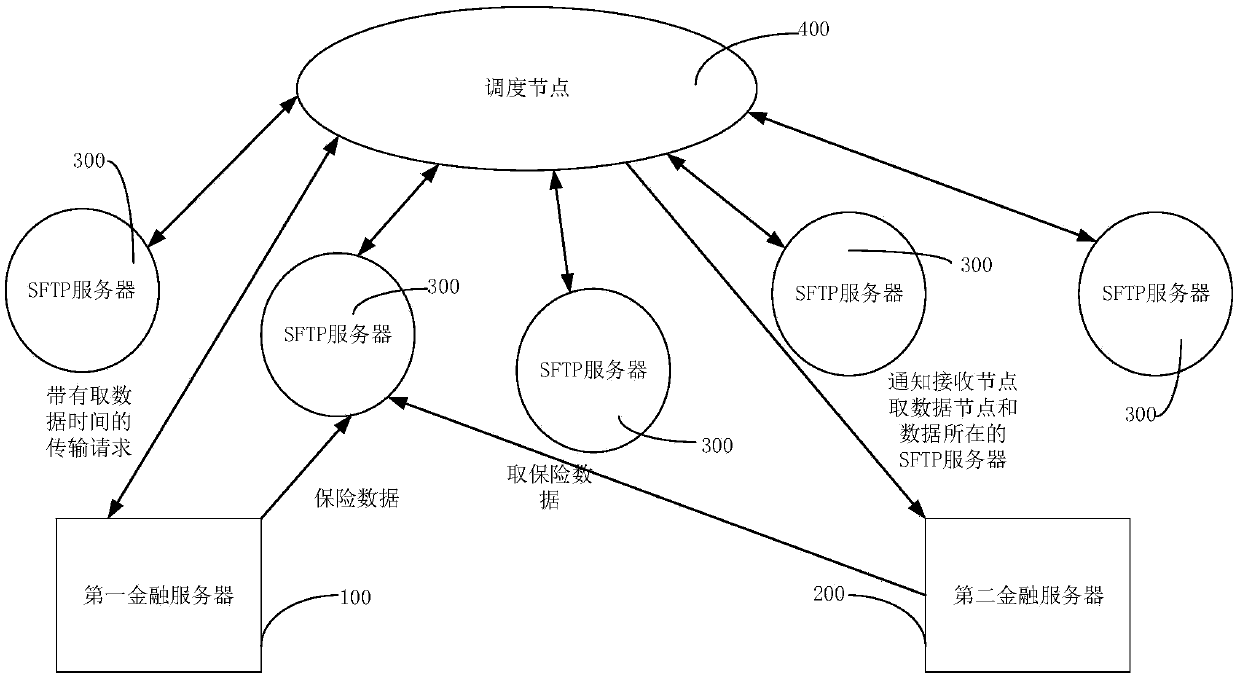
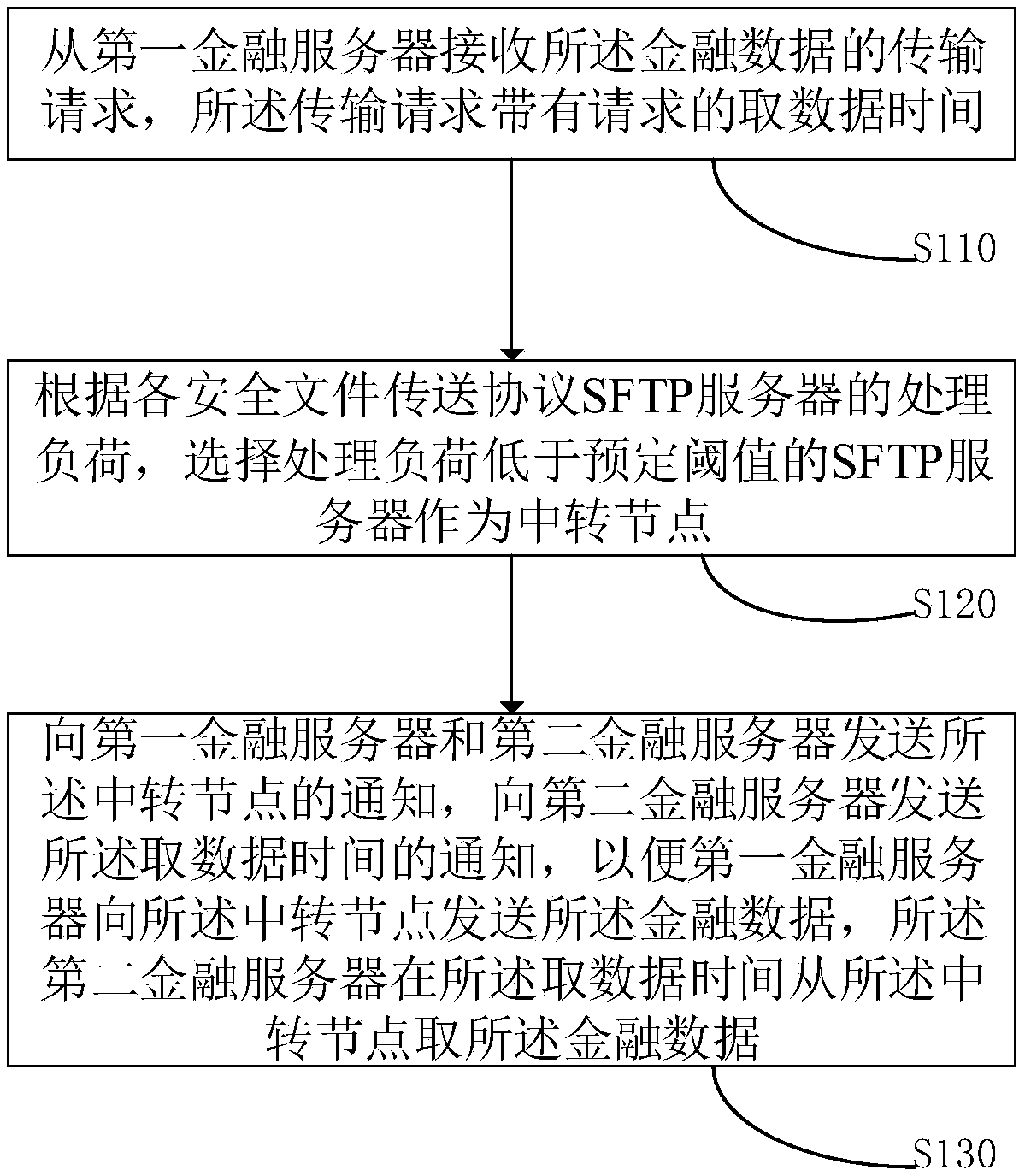
Method and device for transmitting financial data, computer equipment, and storage medium
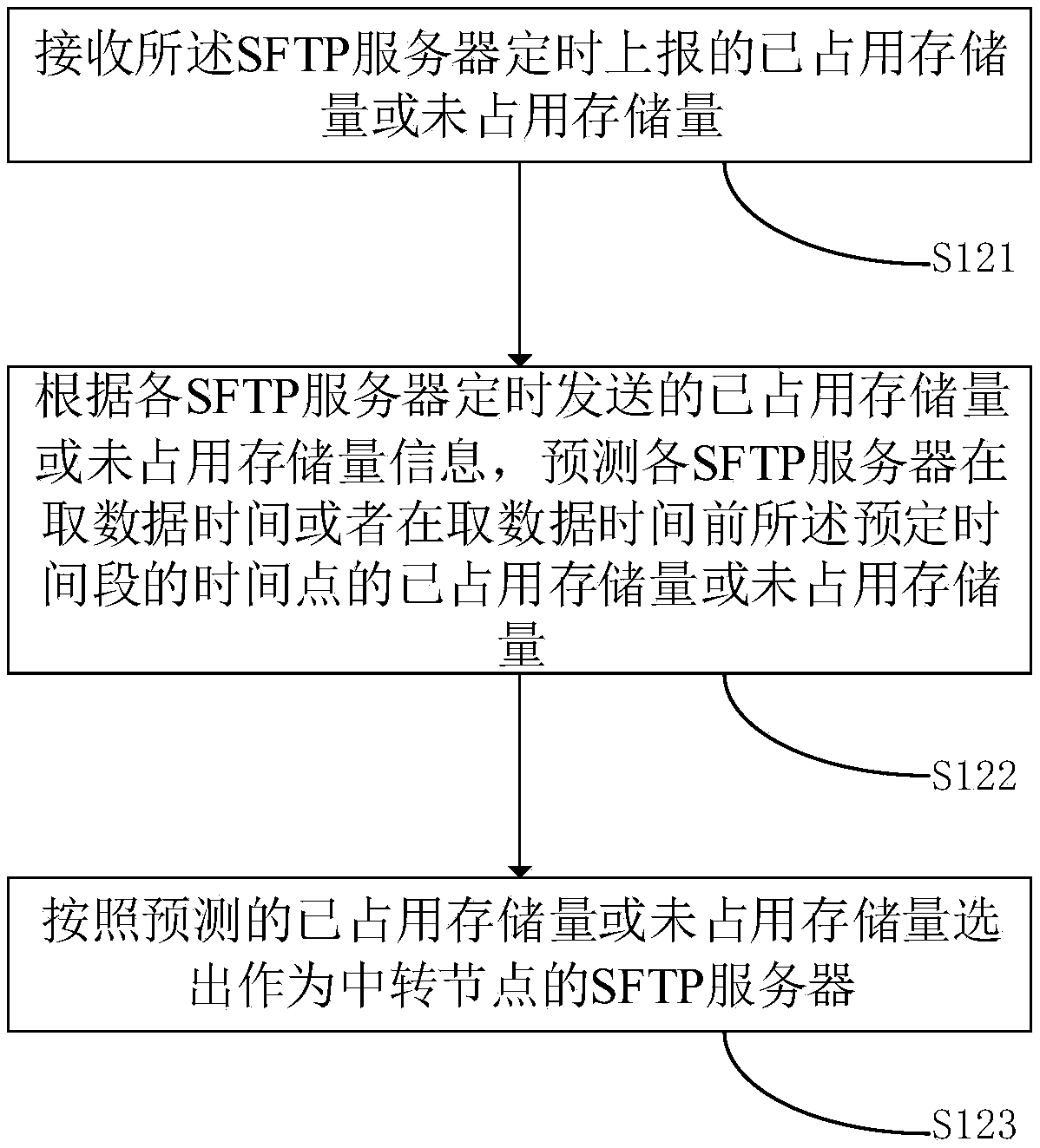
ActiveCN109688190AAvoid overburdened paralyzing problemsAvoid paralysisTransmissionSecure File Transfer ProtocolCloud storage
The invention discloses a method and device for transmitting financial data by a server, computer equipment, and a storage medium, belonging to the technical field of cloud storage. The method comprises the following steps: receiving a transmission request of the financial data from a first financial server, wherein the transmission request carries a requested data fetching time; selecting an SFTPserver whose processing load is lower than a predetermined threshold as a transit node according to the processing load of each secure file transfer protocol SFTP server; transmitting the notification of the transit node to the first financial server and a second financial server, and transmitting the notification of the data fetching time to the second financial server so that the first financial server sends the financial data to the transit node, wherein the second financial server fetches the financial data from the transit node at the data fetching time, which avoids the problem of crashcaused by that insurance data is fixed on an SFTP server to bring excessive burdens, and can handle urgent matters in time.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Method for securely transmitting U disk file on counter of financial network and file transmission system
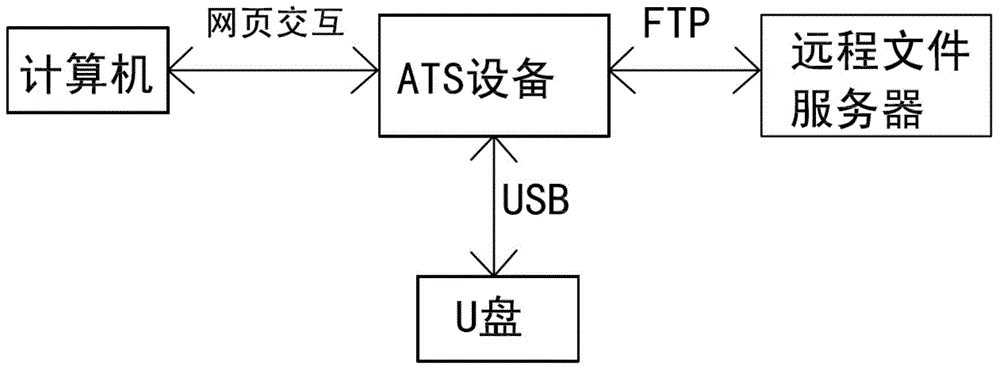
InactiveCN102497366AImplement file transferAvoid runnabilityFinanceFile/folder operationsSecure File Transfer ProtocolFile server
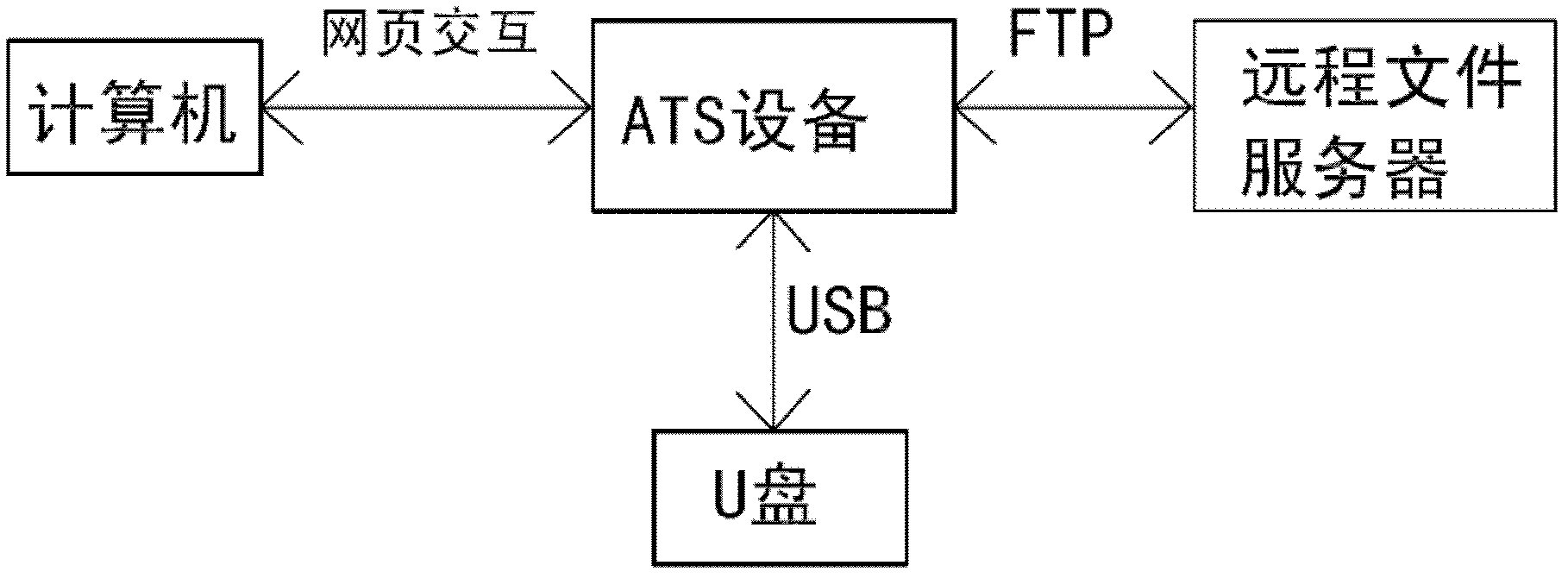
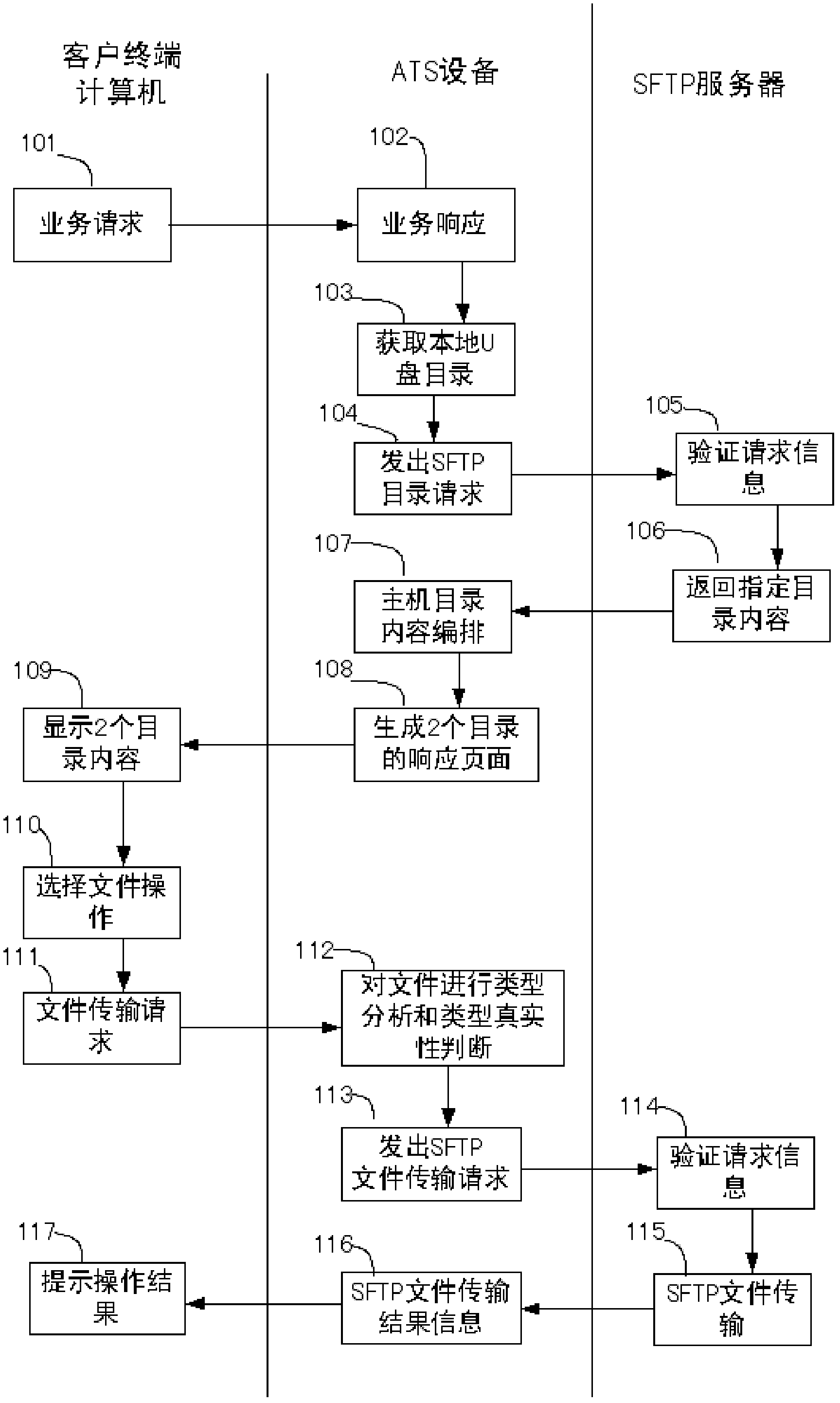
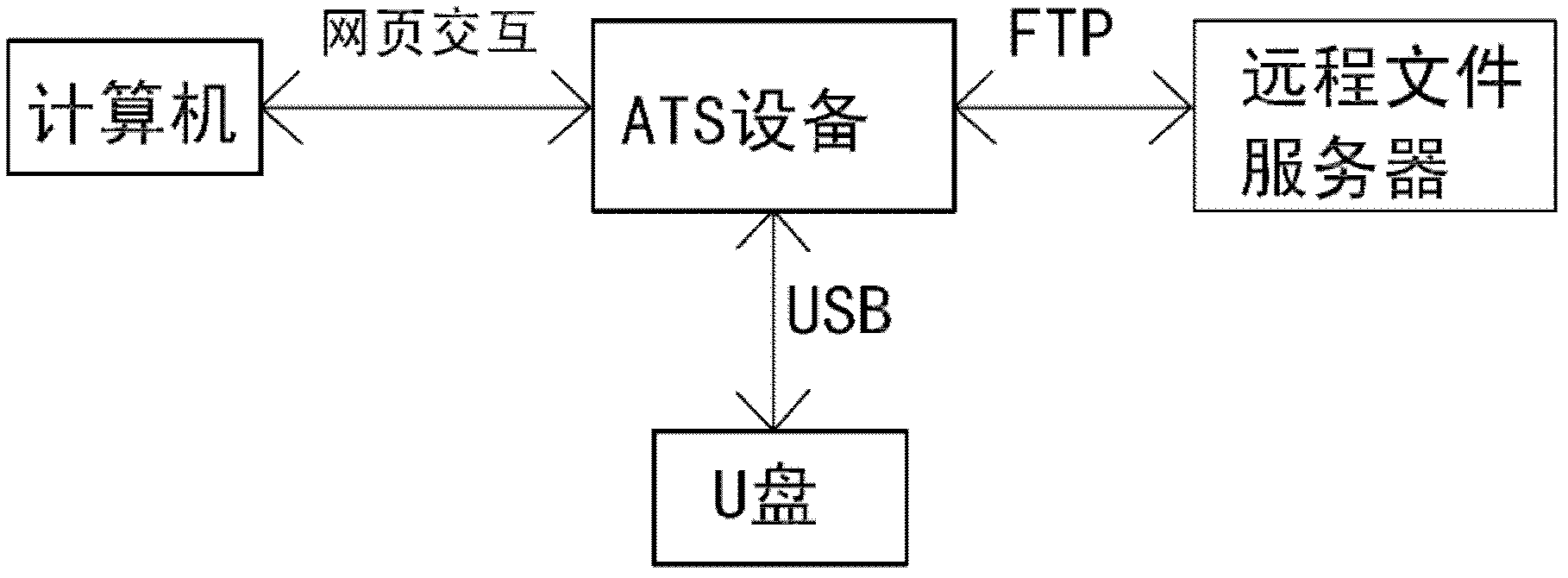
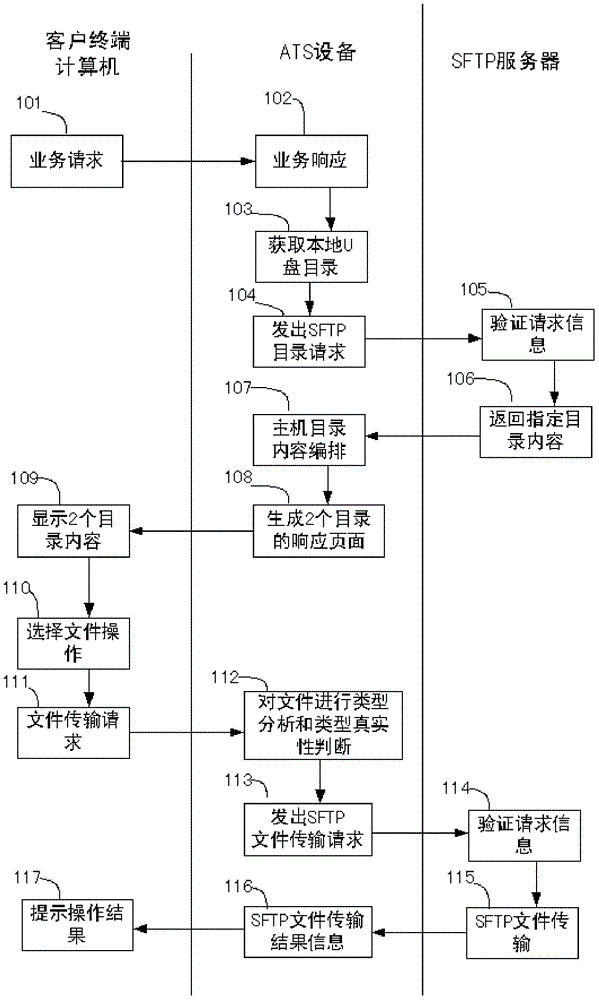
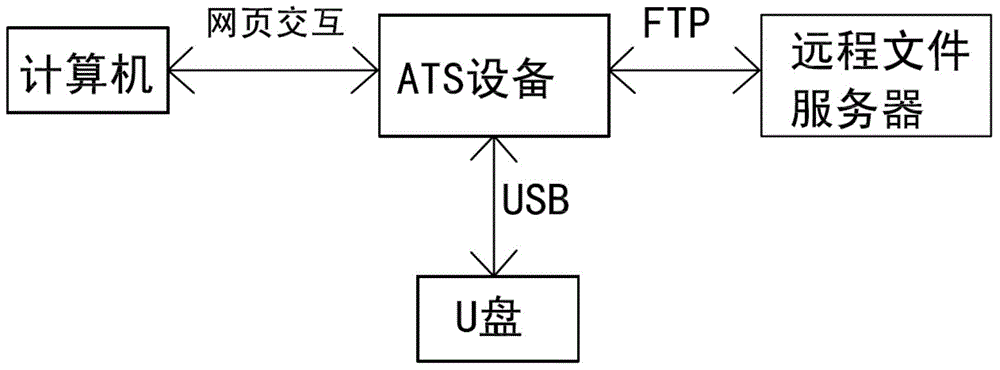
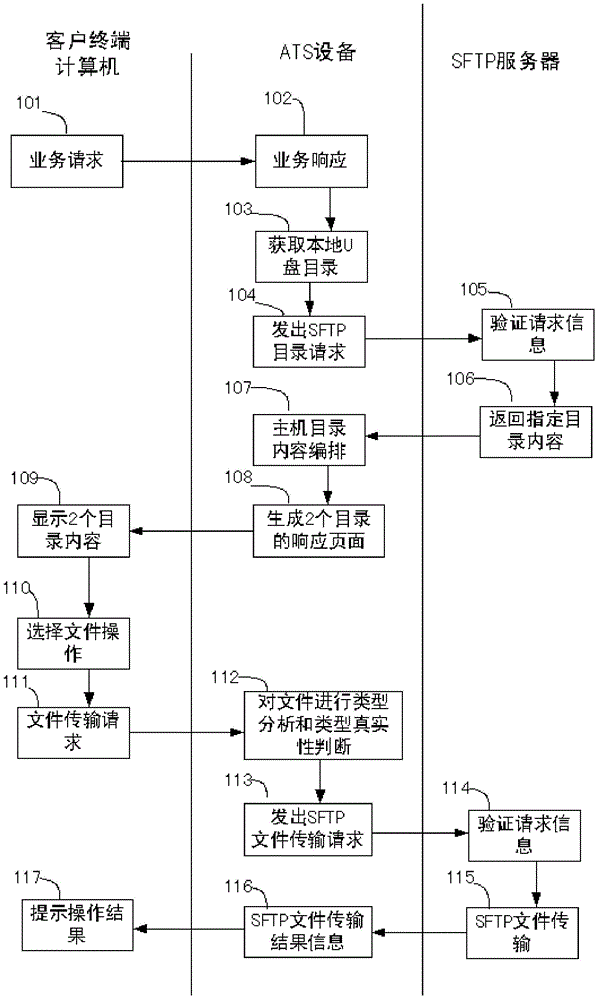
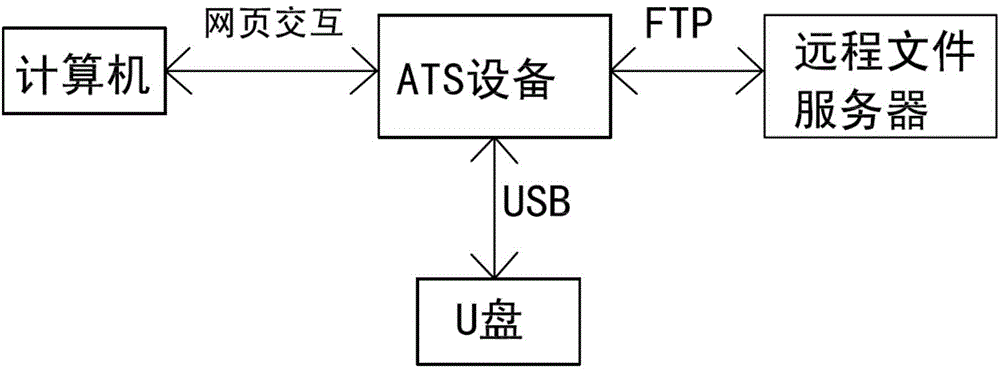
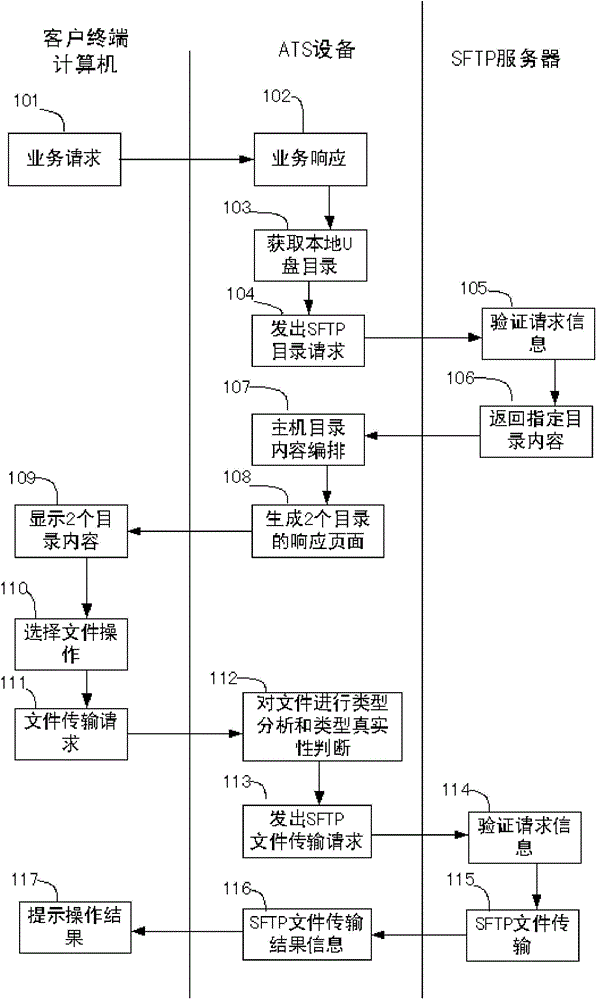
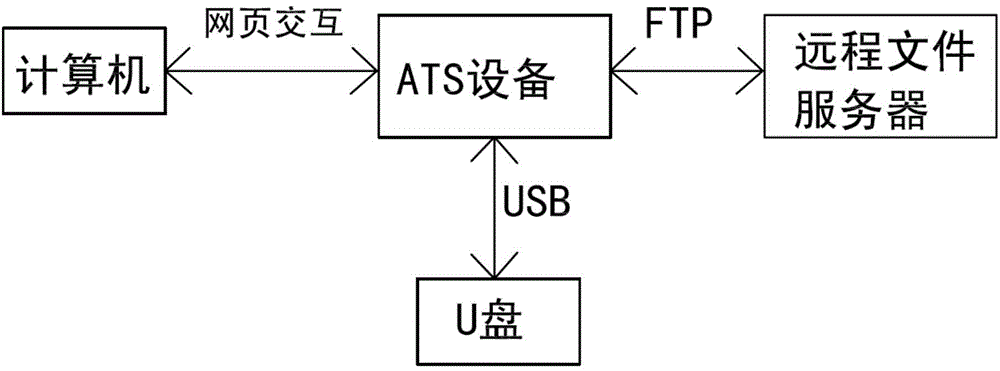
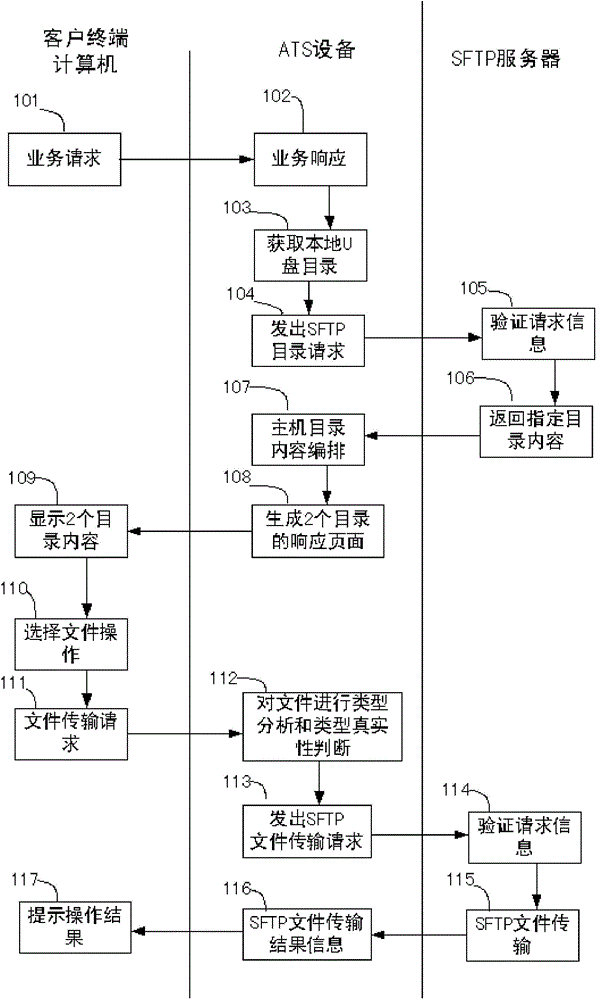
The invention relates to a method for securely transmitting a U disk file on a counter of a financial network. The method comprises the following steps: a user remotely accesses ATS equipment through a browser on a computer and obtains a file list in the U disk connected with the ATS equipment; meanwhile, the user remotely accesses a remote file server through the ATS equipment by use of the browser on the computer, and obtains a file list on the remote file server; then the file list in the U disk and the file list on the remote file server are displayed on the browser at the same time; and finally, the user controls to transmit a file or file folder through ftp (file transfer protocol) between the U disk and the remote file server in the browser. In the process, the transmitted file data does not contact the operator, thereby preventing the user data from being tampered and ensuring the file security. In order to improve the security, the ftp is the common sftp (secure file transfer protocol), namely the securely encrypted ftp.
Owner:CHANGZHOU YINGBEITONG INFORMATION TECH
File transmission verification method and device, computer equipment and storage medium
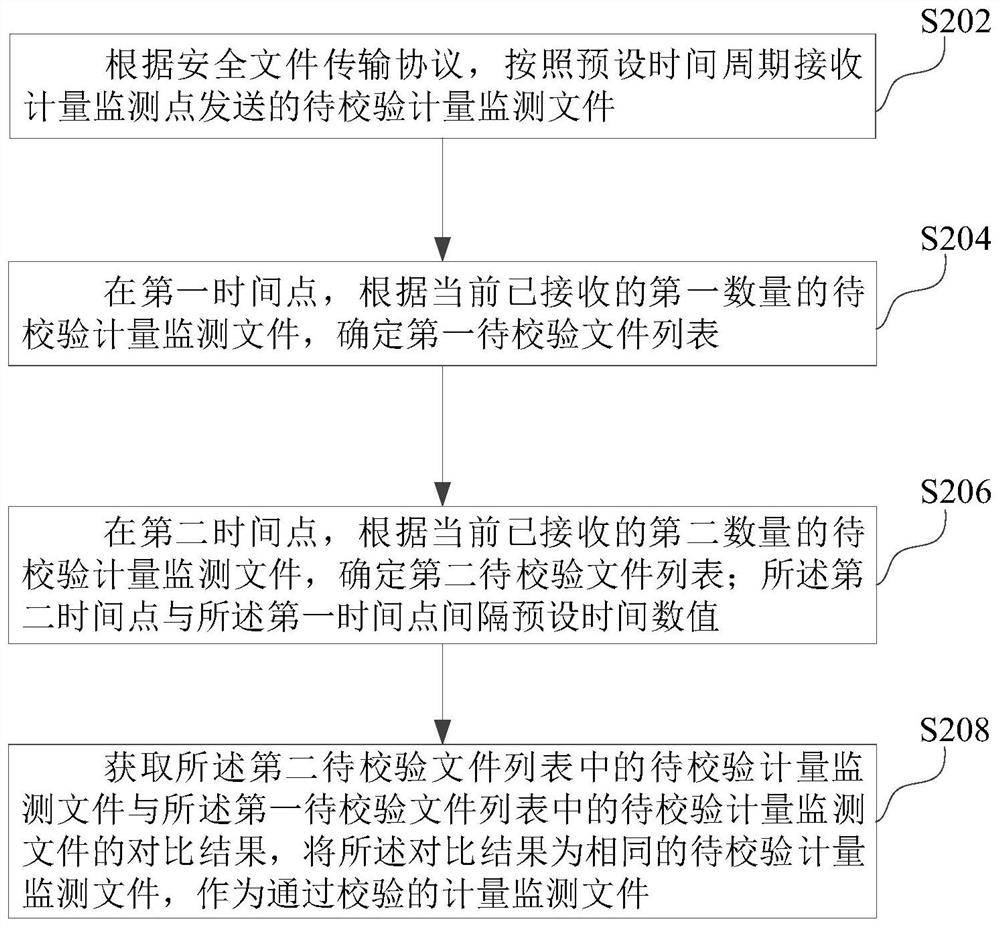
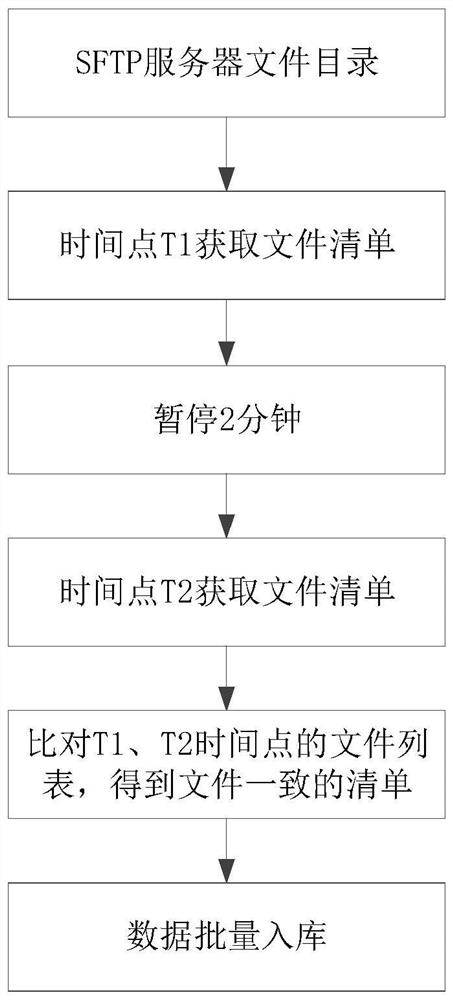
PendingCN114513498AImprove verification efficiencySecuring communicationComputer hardwareMonitoring site
The invention relates to a file transmission verification method and device, computer equipment, a storage medium and a computer program product. The method comprises the following steps: receiving a to-be-verified metering monitoring file sent by a metering monitoring point according to a preset time period through a security file transfer protocol, determining a first to-be-verified file list at a first time point according to the currently received metering monitoring file, and determining a second to-be-verified file list at a second time point after a preset time interval according to the currently received metering monitoring file, and determining a second to-be-verified file list, and comparing the first to-be-verified file list with the second to-be-verified file list to obtain the same to-be-verified metering monitoring file as the verified metering monitoring file. Compared with a traditional mode of independently checking each file, the scheme has the advantages that the file lists are respectively formed based on the received files at the two time points, and the intersection of the to-be-checked metering monitoring files in the two lists obtained by comparison is used as the metering monitoring file passing the checking, so that the checking efficiency of the metering files is improved.
Owner:GUANGZHOU POWER SUPPLY BUREAU GUANGDONG POWER GRID CO LTD
Method for securely transmitting file on counter of financial network, and transmission system
InactiveCN104935586AImplement file transferAvoid spreadingFinanceFile/folder operationsSecure File Transfer ProtocolSecure transmission
The invention relates to a method for securely transmitting a U disk file on a counter of a financial network. The method comprises the following steps: a user remotely accesses ATS equipment through a browser on a computer and obtains a file list in the U disk connected with the ATS equipment; meanwhile, the user remotely accesses a remote file server through the ATS equipment by use of the browser on the computer, and obtains a file list on the remote file server; then the file list in the U disk and the file list on the remote file server are displayed on the browser at the same time; and finally, the user controls to transmit a file or file folder through ftp (file transfer protocol) between the U disk and the remote file server in the browser. In the process, the transmitted file data does not contact the operator, thereby preventing the user data from being tampered and ensuring the file security. In order to improve the security, the ftp is the common sftp (secure file transfer protocol), namely the securely encrypted ftp.
Owner:丁雪强
Viral transmission prevention method for safely transmitting USB flash disk file on financial network counter
InactiveCN104935645AImplement file transferAvoid spreadingFinanceData switching by path configurationSecure File Transfer ProtocolUSB
The invention relates to a method for securely transmitting a U disk file on a counter of a financial network. The method comprises the following steps: a user remotely accesses ATS equipment through a browser on a computer and obtains a file list in the U disk connected with the ATS equipment; meanwhile, the user remotely accesses a remote file server through the ATS equipment by use of the browser on the computer, and obtains a file list on the remote file server; then the file list in the U disk and the file list on the remote file server are displayed on the browser at the same time; and finally, the user controls to transmit a file or file folder through ftp (file transfer protocol) between the U disk and the remote file server in the browser. In the process, the transmitted file data does not contact the operator, thereby preventing the user data from being tampered and ensuring the file security. In order to improve the security, the ftp is the common sftp (secure file transfer protocol), namely the securely encrypted ftp.
Owner:丁雪强
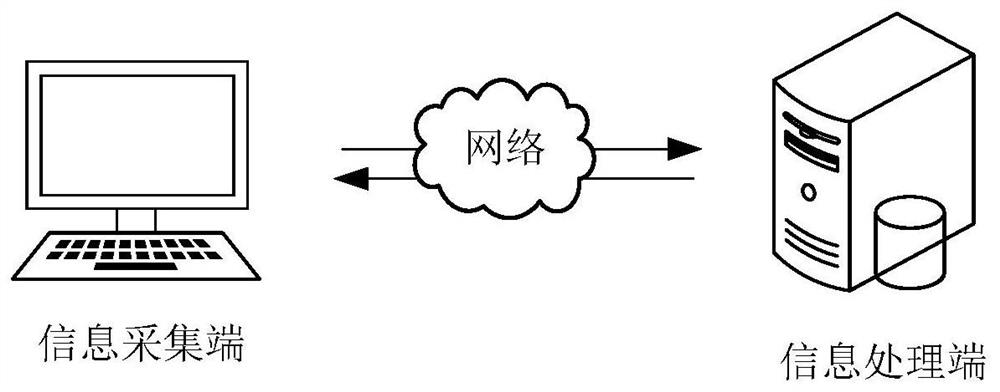
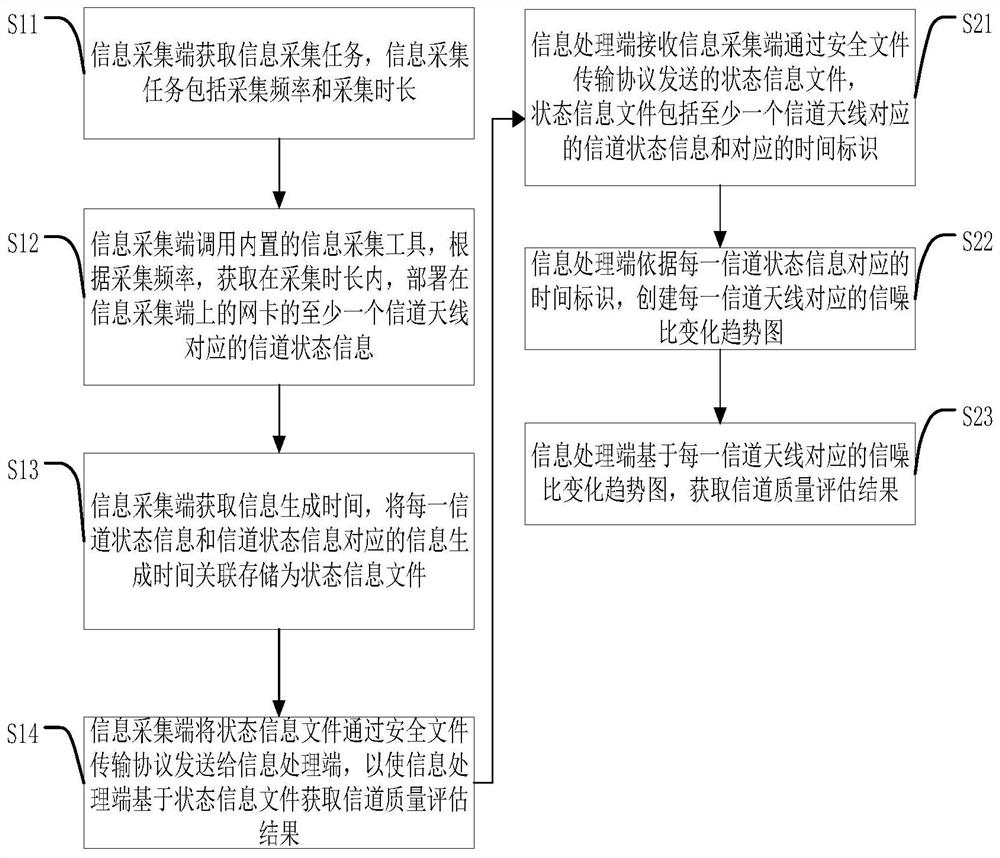
Information transmission method and device, computer device and storage medium
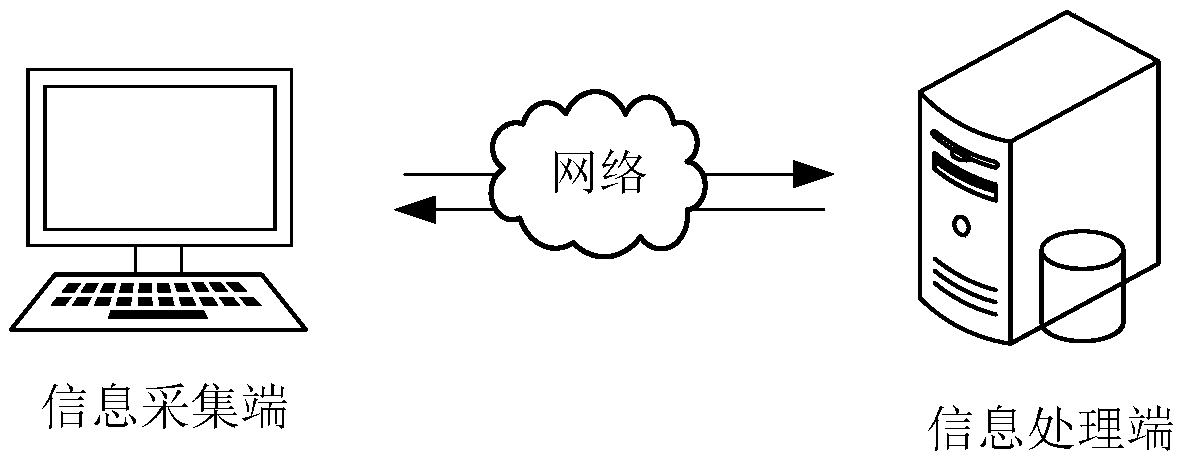
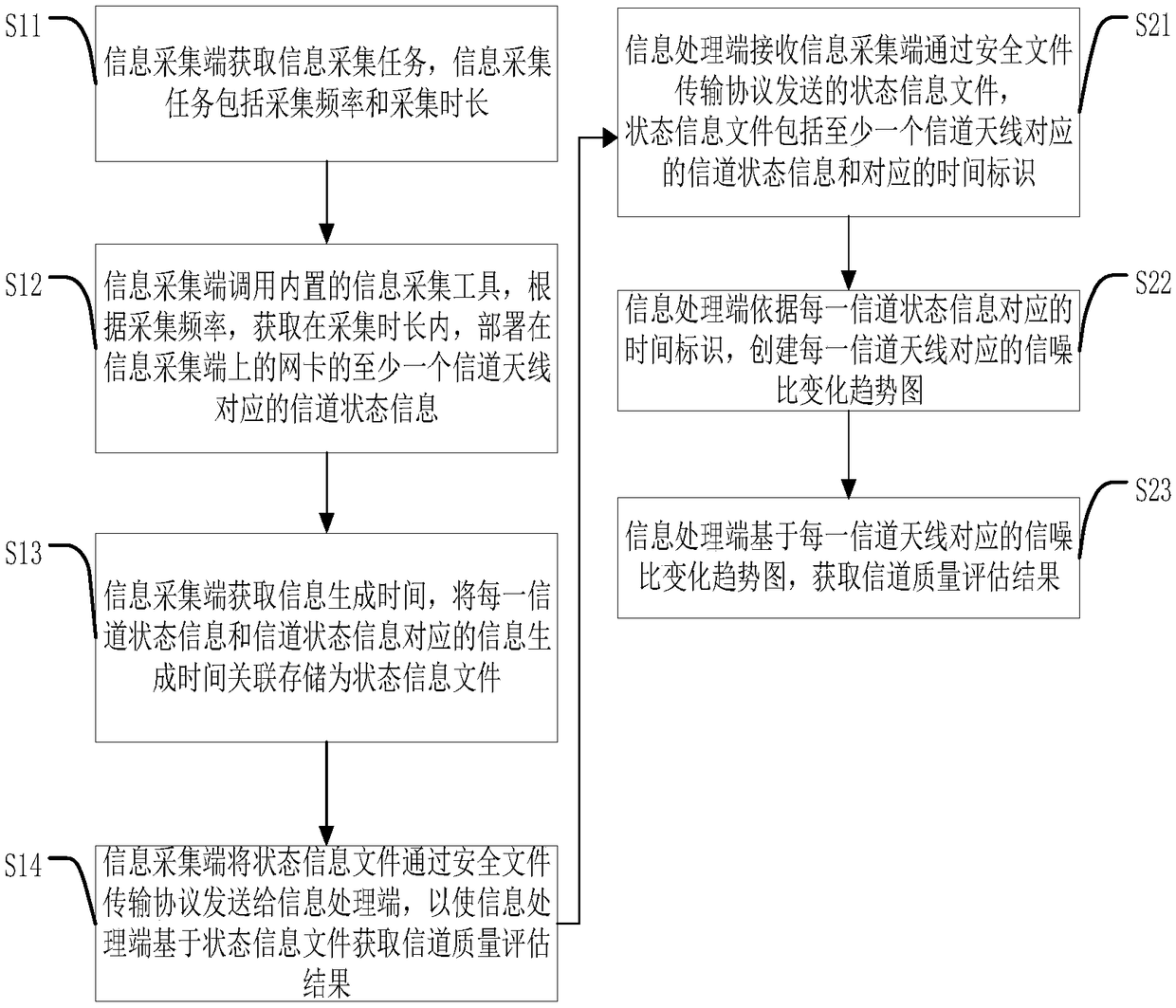
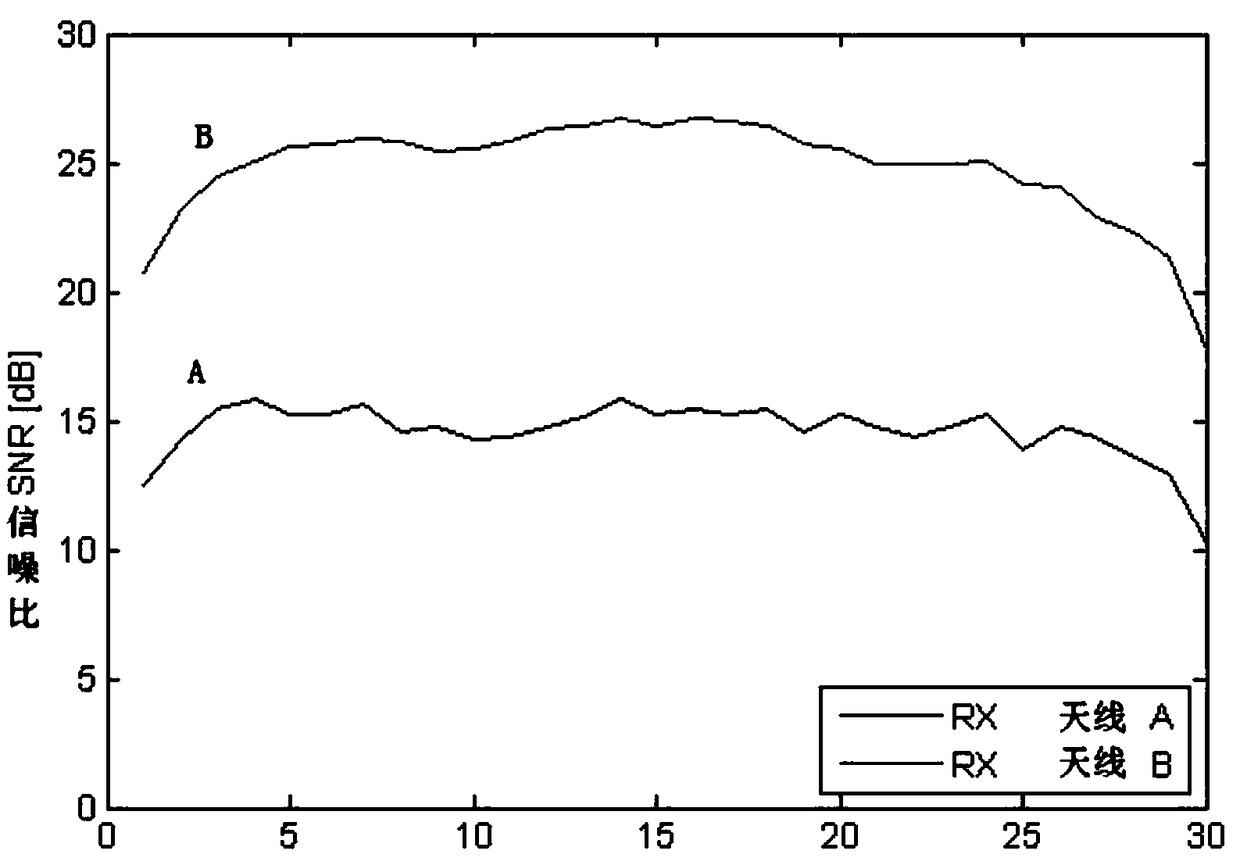
ActiveCN109194416AImprove transmission efficiencyRealize automatic transmissionTransmission monitoringHigh level techniquesInformation processingTelecommunications link
The present invention discloses an information transmission method and device, a computer device and a storage medium. The method comprises the following steps, executed by an information collection terminal, of: obtaining an information task; transferring a built-in information collection tool; according to a collection frequency, obtaining channel state information corresponding to at least onechannel antenna of a network card deployed on the information collection terminal in the collection duration; obtaining information generation time, performing association storage of each channel state information and the information corresponding to the channel state information as a state information file; and sending the state information file to an information processing terminal through a safety file transmission protocol. The information transmission method sends the channel state information collected by the information collection terminal through a communication link to the informationprocessing terminal to achieve automatic transmission of the channel state information and improve the efficiency of information transmission.
Owner:PING AN TECH (SHENZHEN) CO LTD
Real-time monitoring method of wind turbine operation information in 10-million-kilowatt wind power base
The invention discloses a real-time operating information monitoring method for a multi-million kilowatt-level wind power base fan. The real-time operating information monitoring method includes steps of acquiring fan operation data through an SCADA (supervisory control and data acquisition) system; writing the acquired fan operation data into E files line by line, transmitting the completed E-file data into an SFTP (secure file transfer protocol) prepositive server and a dispatch center station SFTP server of a wind power plant through an isolation equipment and storing the same in a real-time wind power monitoring server, and analyzing E-format files. The fan operation data are acquired through the SCADA system, stored according to the fixed formats, and transmitted to a database to store through the servers and the isolation equipment, and operation conditions of the fan can be checked according to the analyzed results of the stored data, thereby the purpose of accurately monitoring the multi-million kilowatt-level wind power base fan in real time is achieved.
Owner:STATE GRID CORP OF CHINA +2
Information transmission method, apparatus, electronic device and computer readable medium
ActiveCN109861973BRealize transmissionImplement encrypted transmissionSecuring communicationTransmission protocolSecure File Transfer Protocol
The embodiments of the present application disclose an information transmission method, an apparatus, an electronic device, and a computer-readable medium. A specific implementation of the method includes: authenticating the access request sent by the client according to the secure file transfer protocol SFTP; in response to determining that the access request is authenticated, sending a connection request to the file transfer protocol FTP server; in response to determining that the connection request is authenticated Through, according to the operation request sent by the client, the information transmission between the client and the FTP server is realized. In this embodiment, the encrypted transmission of information can be realized by converting the FTP transmission protocol with the client to the SFTP transmission protocol. This helps to improve the security of information transmission and prevent information leakage.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
File upload and download method, system and related equipment based on sftp protocol
ActiveCN102231742BRealize automatic identificationEliminate potential safety hazardsTransmissionFile transmissionSecure File Transfer Protocol
The invention discloses a file uploading and downloading methods based on an SFTP (Secure File Transfer Protocol), wherein the file uploading method comprises the following steps: a client reads preset parameters from a server, wherein the preset parameters comprise an uploading path, a server IP (Internet Protocol), ports, a user name and passwords; and the client sends a file to be uploaded to the server in accordance with the SFTP according to the file name of the file to be uploaded and the preset parameters. The file downloading method comprises the following steps: the client reads preset parameters from the server, wherein the preset parameters comprise a downloading path, the server IP, the ports, the user name and the passwords; and the client receives the file to be downloaded in accordance with the SFTP according to the file name of the file to be downloaded of the server and the preset parameters. Correspondingly, the invention also discloses the client and the server. In the invention, the file transmission is carried out according to the preset parameters by storing the preset parameters in advance and the catalog of a local disk does not need to be operated manually, thereby improving the safety and stability of the client and the server.
Owner:CHINA CONSTRUCTION BANK
File transfer method, device, electronic device, and computer-readable storage medium
ActiveCN110557507BEnsure safetyImprove upload efficiencySubstation equipmentTransmissionComputer hardwareSecure File Transfer Protocol
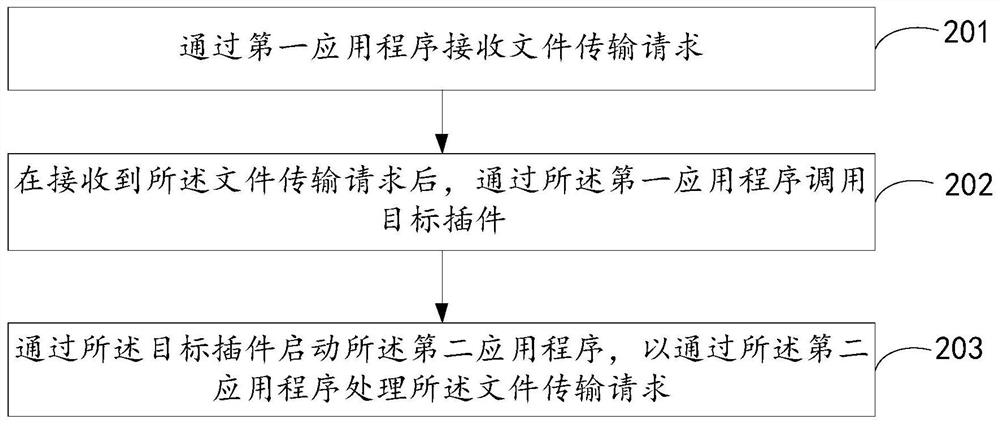
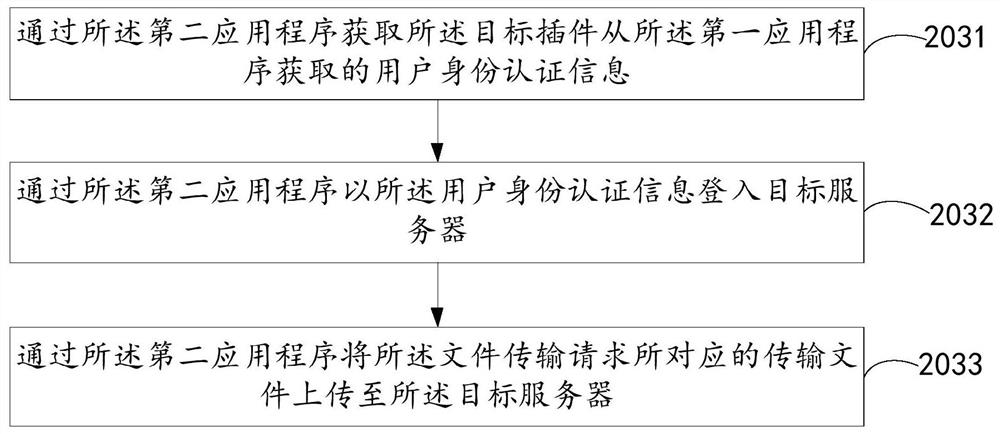
The present application provides a file transmission method, device, and electronic equipment, wherein the file transmission method is applied to electronic equipment, and the electronic equipment is installed with a first application program and a second application program, and the second application program uses The protocol is a secure file transfer protocol, and the file transfer method includes: receiving a file transfer request through a first application program; calling a target plug-in through the first application program after receiving the file transfer request; starting a second application program through the target plug-in program to The file transfer request is performed by the second application. According to the above method, the security of file transmission can be improved.
Owner:DAWNING INFORMATION IND BEIJING +1
File transfer protocol (FTP) data transmission method and system
InactiveCN102148845BImprove interoperabilityInterworking supportTransmissionSecure File Transfer ProtocolIp address
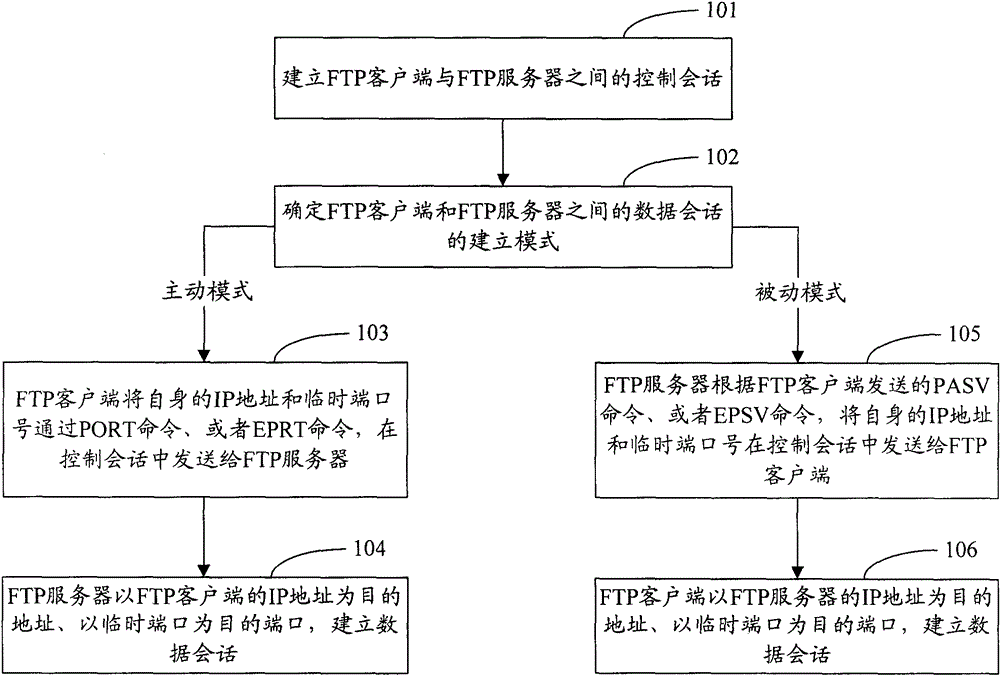
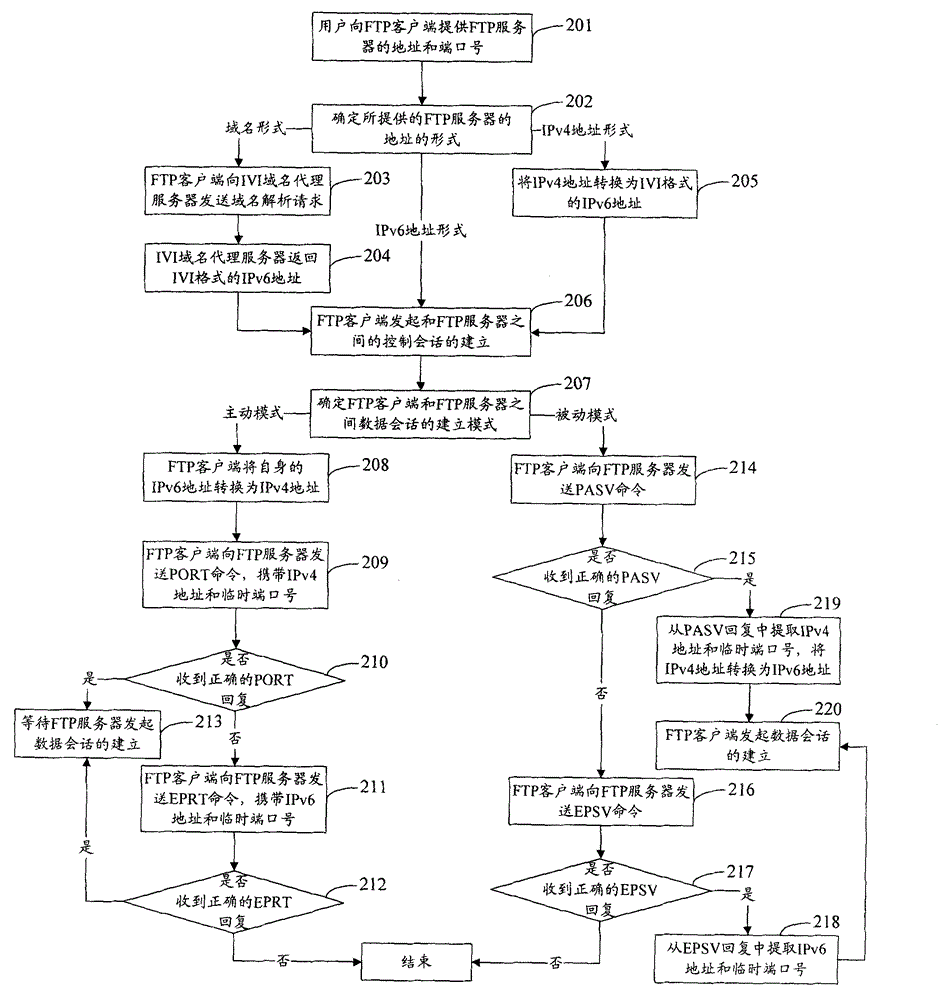
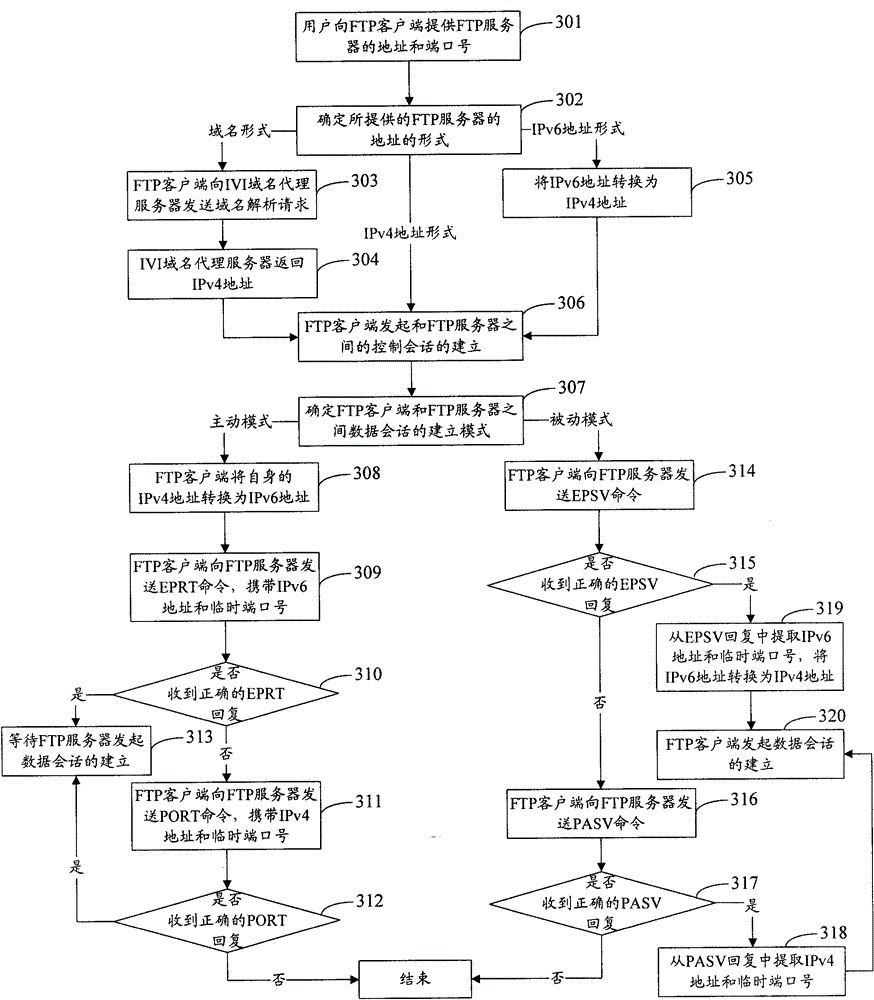
The invention discloses a file transfer protocol (FTP) data transmission method and an FTP data transmission system. If a data session creation mode is an active mode, an FTP client transmits own Internet protocol (IP) address and a temporary port number to an FTP server in a control session by a PORT command or an EPRT command for the data session creation of the FTP server. If the data creation mode is a passive mode, the FTP server transmits own IP address and the temporary port number to the FTP client in the control session by a PASV command or an EPSV command transmitted by the FTP client for the data session creation of the FTP client. By the method and the system, the communication of the FTP client and the FTP server between an Internet protocol Version 6 (IPv6) network and an IPv4 network can be realized under the condition of not adding an application layer gateway.
Owner:ZTE CORP
Method for preventing virus propagation and securely transmitting U disk file on counter of financial network
InactiveCN104935649AImplement file transferAvoid spreadingFinanceFile/folder operationsSecure File Transfer ProtocolSecure transmission
The invention relates to a method for securely transmitting a U disk file on a counter of a financial network. The method comprises the following steps: a user remotely accesses ATS equipment through a browser on a computer and obtains a file list in the U disk connected with the ATS equipment; meanwhile, the user remotely accesses a remote file server through the ATS equipment by use of the browser on the computer, and obtains a file list on the remote file server; then the file list in the U disk and the file list on the remote file server are displayed on the browser at the same time; and finally, the user controls to transmit a file or file folder through ftp (file transfer protocol) between the U disk and the remote file server in the browser. In the process, the transmitted file data does not contact the operator, thereby preventing the user data from being tampered and ensuring the file security. In order to improve the security, the ftp is the common sftp (secure file transfer protocol), namely the securely encrypted ftp.
Owner:丁雪强
Method for preventing virus propagation and securely transmitting file on counter of financial network
InactiveCN104935646AImplement file transferAvoid spreadingFinanceData switching by path configurationSecure File Transfer ProtocolSecure transmission
The invention relates to a method for securely transmitting a U disk file on a counter of a financial network. The method comprises the following steps: a user remotely accesses ATS equipment through a browser on a computer and obtains a file list in the U disk connected with the ATS equipment; meanwhile, the user remotely accesses a remote file server through the ATS equipment by use of the browser on the computer, and obtains a file list on the remote file server; then the file list in the U disk and the file list on the remote file server are displayed on the browser at the same time; and finally, the user controls to transmit a file or file folder through ftp (file transfer protocol) between the U disk and the remote file server in the browser. In the process, the transmitted file data does not contact the operator, thereby preventing the user data from being tampered and ensuring the file security. In order to improve the security, the ftp is the common sftp (secure file transfer protocol), namely the securely encrypted ftp.
Owner:丁雪强
sftp-based file transfer method and related equipment
ActiveCN109391694BImprove securityImprove transmission efficiencySecuring communicationServerComputer equipment
The invention discloses a file transmission method, device, computer equipment and storage medium based on the secure file transmission protocol SFTP, belonging to the technical field of data transmission. The shared file storage unit shared by the front-end machine and the SFTP temporary server, obtains the file, wherein the file is transmitted to the SFTP temporary server in advance, and is put into the shared file storage unit by the SFTP temporary server; According to the network transmission speed between the internal network and the external network, read data from the file, wherein the amount of data read corresponds to the network transmission speed; transmit the read data to the SFTP server of the external network . Thus, the security of data transmission between the SFTP servers is improved, the disconnection is reduced, the transmission efficiency is improved, and the network security is ensured.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
A file interactive processing method, device and system
ActiveCN110177154BImplement configurationAchieve separationUser identity/authority verificationTransmission protocolFile transmission
The invention discloses a file interaction processing method, device and system, and relates to the field of file transmission, wherein the method includes: acquiring a first channel identifier, a first file identifier of a first file, and a first hash value of the first file ; The first channel identifier is used to indicate the secure file transfer protocol SFTP server corresponding to the first file recipient; According to the first file identifier of the first file and the first hash value of the first file from the file downloading the first file from the transfer protocol FPS server; storing the first file to the SFTP server corresponding to the first channel identifier according to the first channel identifier. The method can be applied to financial technology (Fintech).
Owner:WEBANK (CHINA)
Information transmission method, device, computer equipment and storage medium
ActiveCN109194416BImprove transmission efficiencyRealize automatic transmissionTransmission monitoringHigh level techniquesComputer hardwareInformation processing
The invention discloses an information transmission method, device, computer equipment, and storage medium, wherein the information transmission method includes the following steps performed by an information collection end: obtaining information collection tasks; calling a built-in information collection tool, and according to the collection frequency, obtaining During the collection period, the channel state information corresponding to at least one channel antenna of the network card deployed on the information collection end; obtain the information generation time, and associate and store each channel state information and the information generation time corresponding to the channel state information as a state information file ; Send the state information file to the information processing terminal through the secure file transfer protocol. The information transmission method can send the channel state information collected by the information collection end to the information processing end through the communication link, so as to realize the automatic transmission of the channel state information and improve the efficiency of information transmission.
Owner:PING AN TECH (SHENZHEN) CO LTD
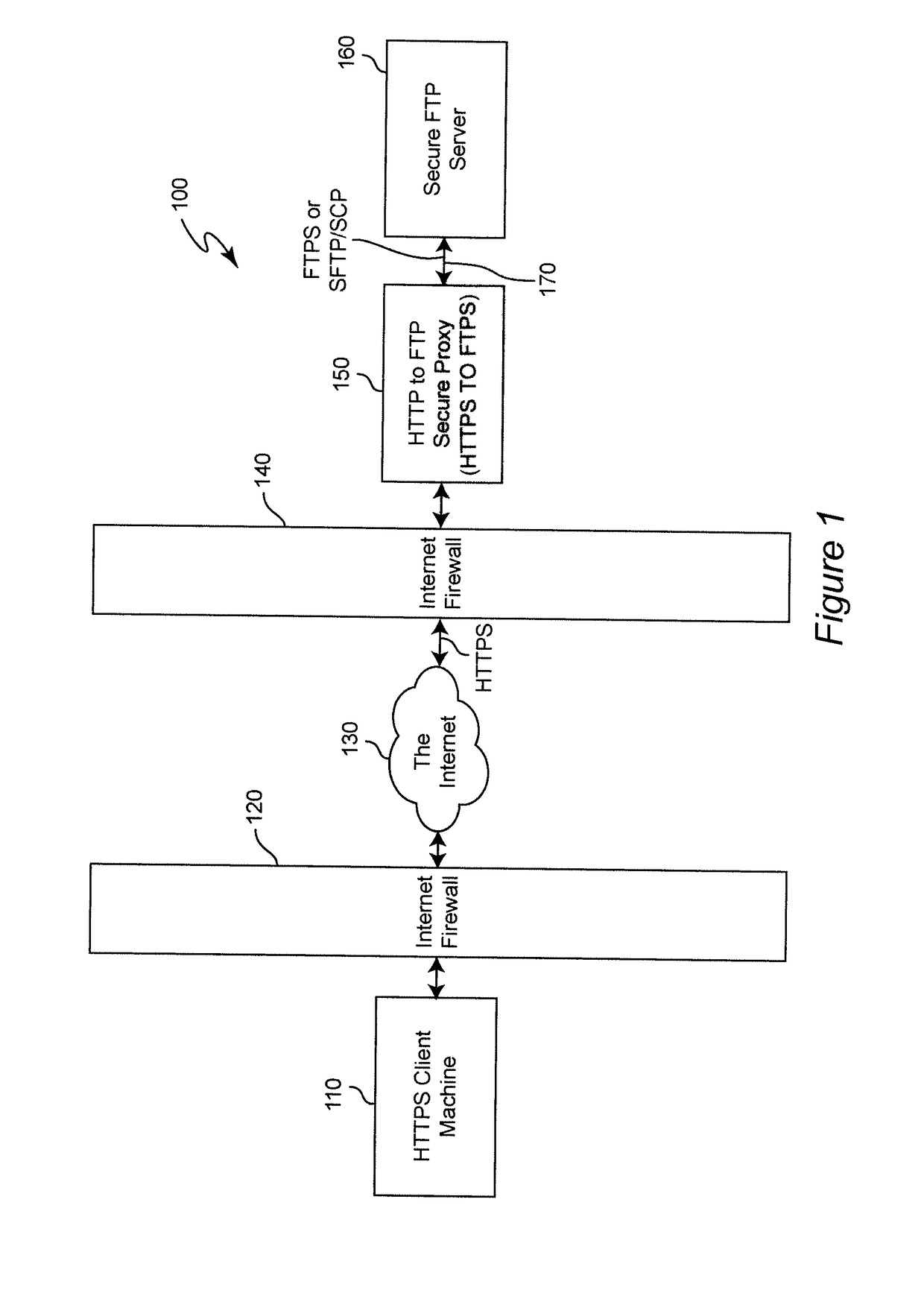
Method and system for pervasive access to secure file transfer servers
ActiveUS9800550B2Computer security arrangementsMultiple digital computer combinationsSecure communicationSecure File Transfer Protocol
End-to-end file transfer security for file transfer is provided over a network such as the Internet between a client, using a secure communication protocol which is pervasively available, such as HTTPS, to a secure file server which is accessible only through a secure file transfer protocol which is not pervasively available by using a secure proxy for accessing the secure file server rather than providing a protocol break merely for traversing a firewall. The secure proxy is arranged to provide a protocol conversion between the pervasively available secure protocol and the communication protocol through which the server is accessible and which is not pervasively available. By doing so, the secure proxy inherits secure functions of the secure server which thus need not be separately or independently provided in the secure proxy.
Owner:IBM CORP
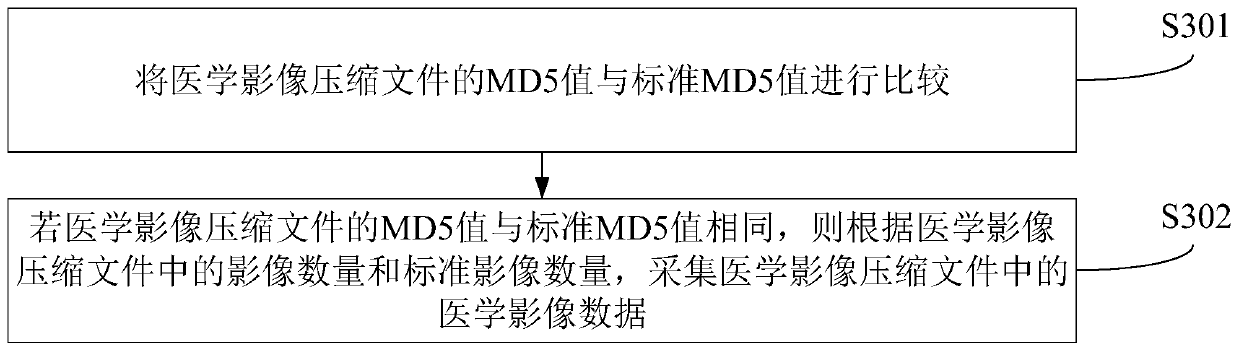
Medical image data acquisition method and device, computer equipment and storage medium
ActiveCN111403005AAcquisition is stable and efficientIntegrity guaranteedUser identity/authority verificationMedical imagesSecure File Transfer ProtocolMedical imaging data
The invention relates to a medical image data acquisition method and device, computer equipment and a storage medium. The method comprises the following steps: receiving an examination report sent bymedical image equipment through a secure file transfer protocol; searching for a compressed medical image file corresponding to the examination report in a target storage directory according to a preset field in the examination report, and acquiring an MD5 value of the compressed medical image file and the number of images in the compressed medical image file; and acquiring medical image data in the compressed medical image file according to the MD5 value of the compressed medical image file, the number of images in the compressed medical image file and the examination report. By adopting themethod, the medical image data in the medical image compressed file can be stably and efficiently acquired.
Owner:WUHAN UNITED IMAGING HEALTHCARE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com