Successive verification type safe scanning chain device and method based on logic encryption
A technology of security scanning and scan chain, applied in the field of successive verification type security scan chain structure, can solve the problem of chip security, malicious attack of scan chain, etc., and achieve the effect of ensuring testability and security, and resisting attack methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
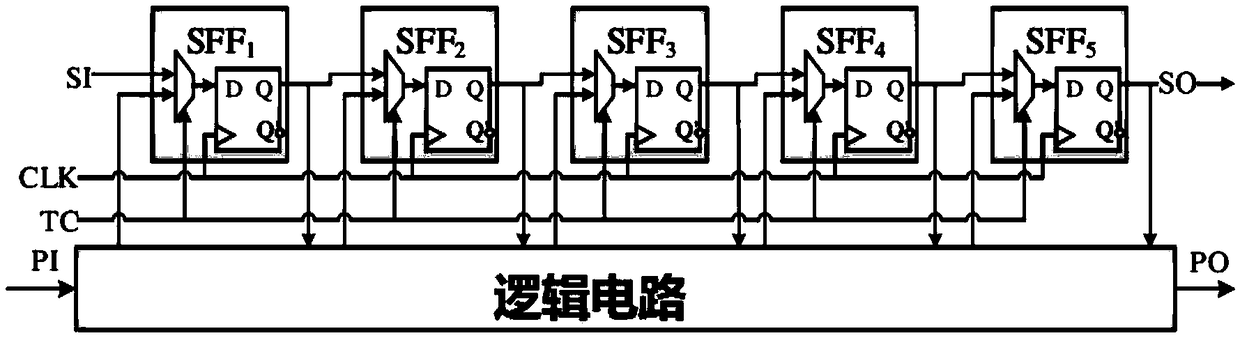
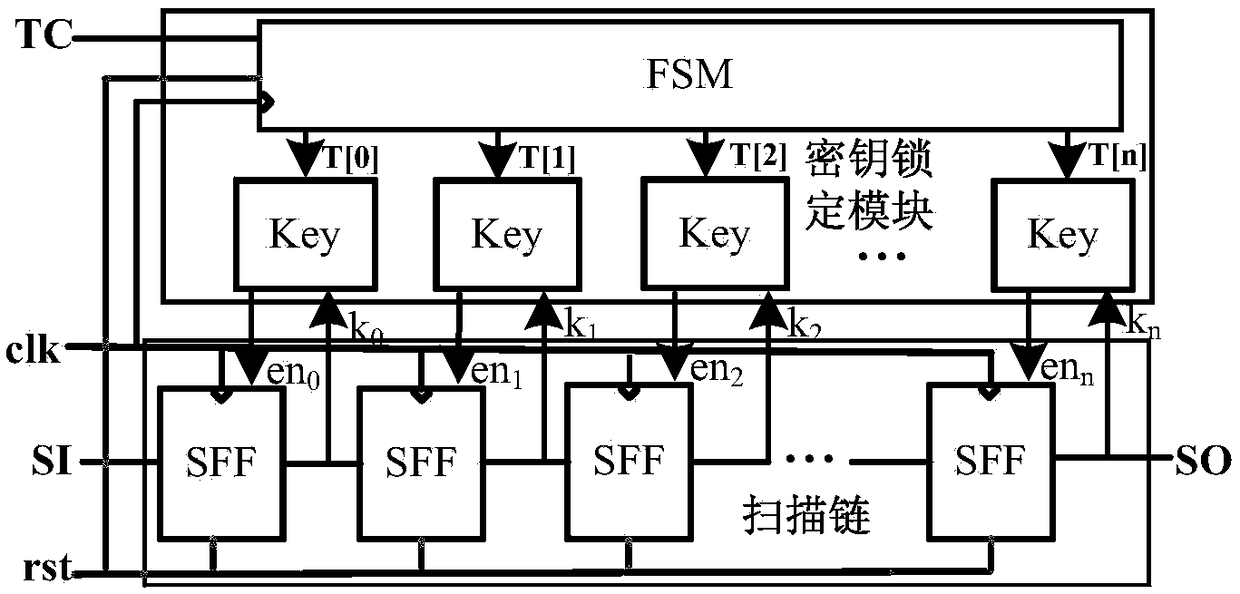
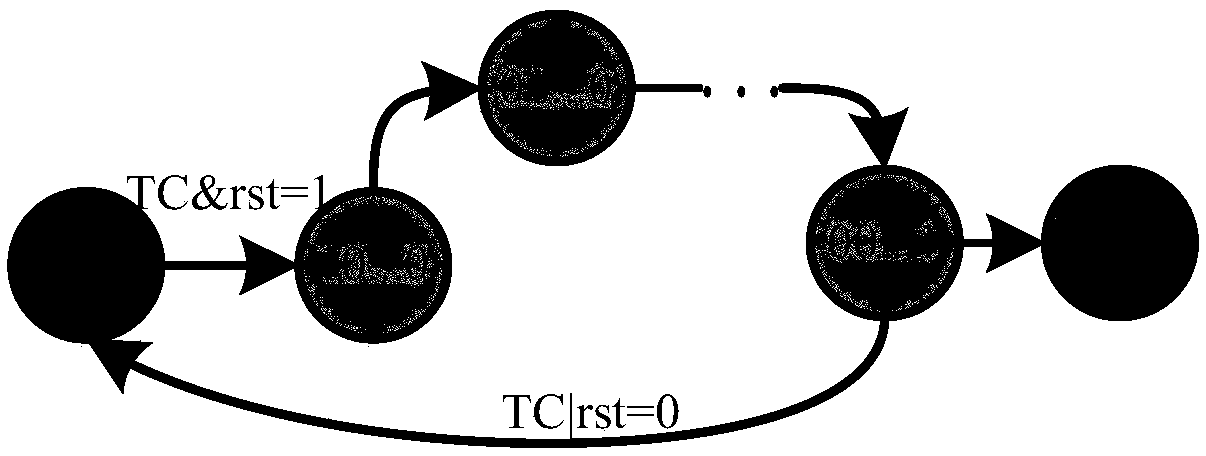
[0022]The present invention proposes a sequentially verified security scan chain structure based on logic encryption, uses logic encryption technology to encrypt the traditional scan chain to prevent malicious attackers from reading the internal information of the circuit, and uses logic camouflage technology to camouflage the security scan chain , to prevent reverse analysis of the security logic chain structure. The security scan chain structure adds an identification and verification structure. When entering the test work mode, a certain password needs to be entered to scan input and output. If the attacker does not know the preset password in advance, the security scan chain structure cannot be effectively used. On the basis of ensuring the observability and controllability of the chip, the security scanning structure greatly improves the security level of the scan chain, effectively preventing the risk of leakage of chip information in private areas such as communication a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com