A malicious code homology analysis method based on system call control flow graph
A technology of homology analysis and control flow graph, which is applied in the field of network security, can solve the problems of poor homology analysis ability of malicious code variants, etc., and achieve the effects of avoiding confusion, good abstraction, and simplifying the amount of data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
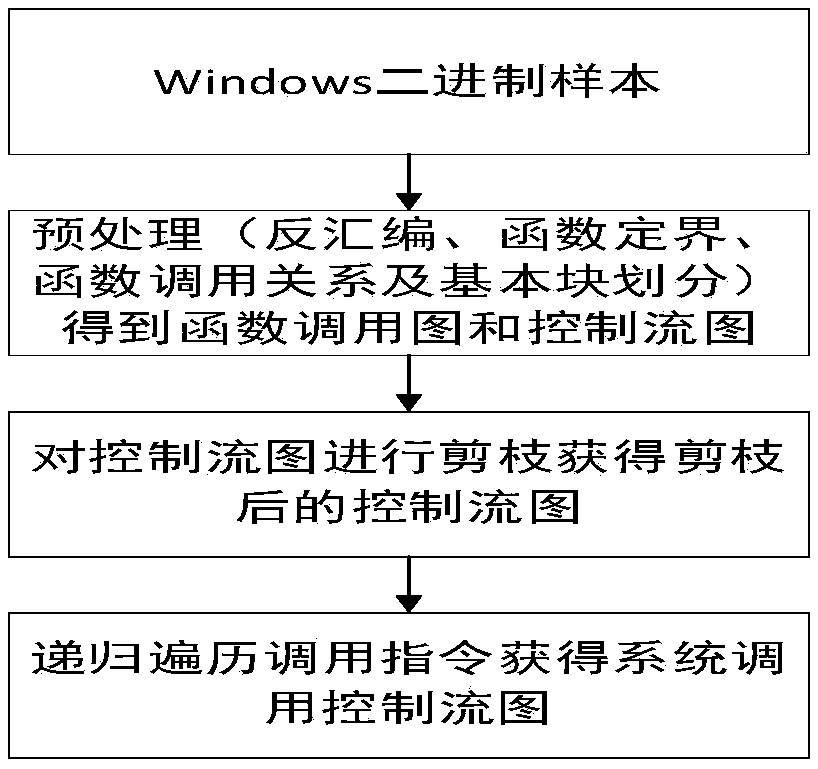
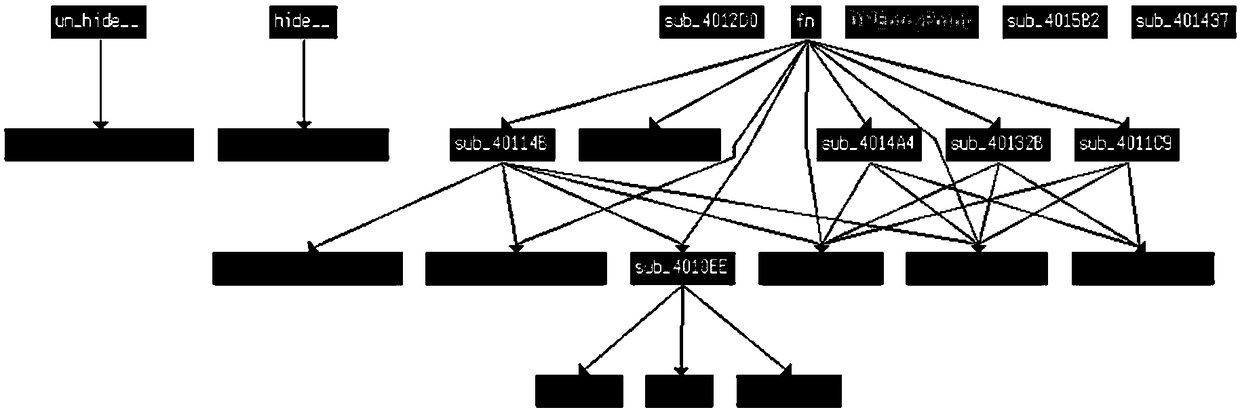
[0045] In the homology analysis of malicious code variants, the internal logic of malicious code processed by obfuscation techniques such as deformation and polymorphism may be disrupted, and the control flow graph of instruction blocks extracted through static analysis can be used with little value; while dynamic analysis Expenses are high. In addition, the function call graph can obtain the calling relationship between functions, but there is no timing relationship.
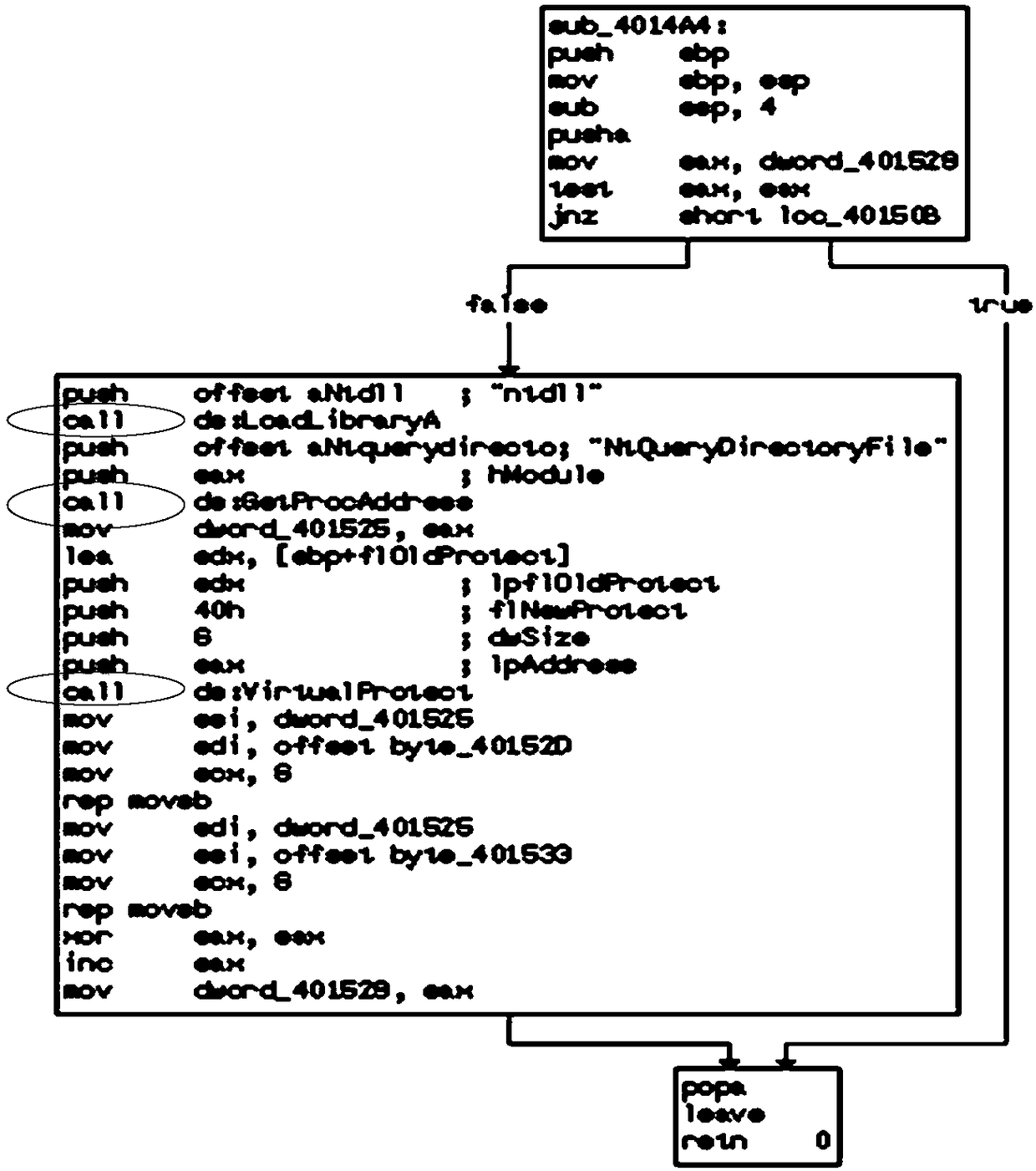
[0046] The present invention considers constructing a system call control flow graph, the control flow graph is a directed and unweighted graph composed of system call nodes, and the direction of the edges represents the sequential relationship of system call execution, which retains the timing relationship between system calls. Here, "system call" means that a program running in user space requests a service from the operating system kernel that requires higher privileges to run. System calls provide the inte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com