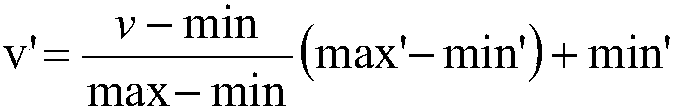FCM-GASVM-based industrial control system intrusion detection method
An industrial control system, intrusion detection technology, applied in general control systems, control/regulation systems, adaptive control and other directions, can solve problems such as loss, inability to detect attacks, inability to effectively reduce system security risks, and reduce training time, The effect of improving classification accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be further described in detail below in conjunction with the examples.
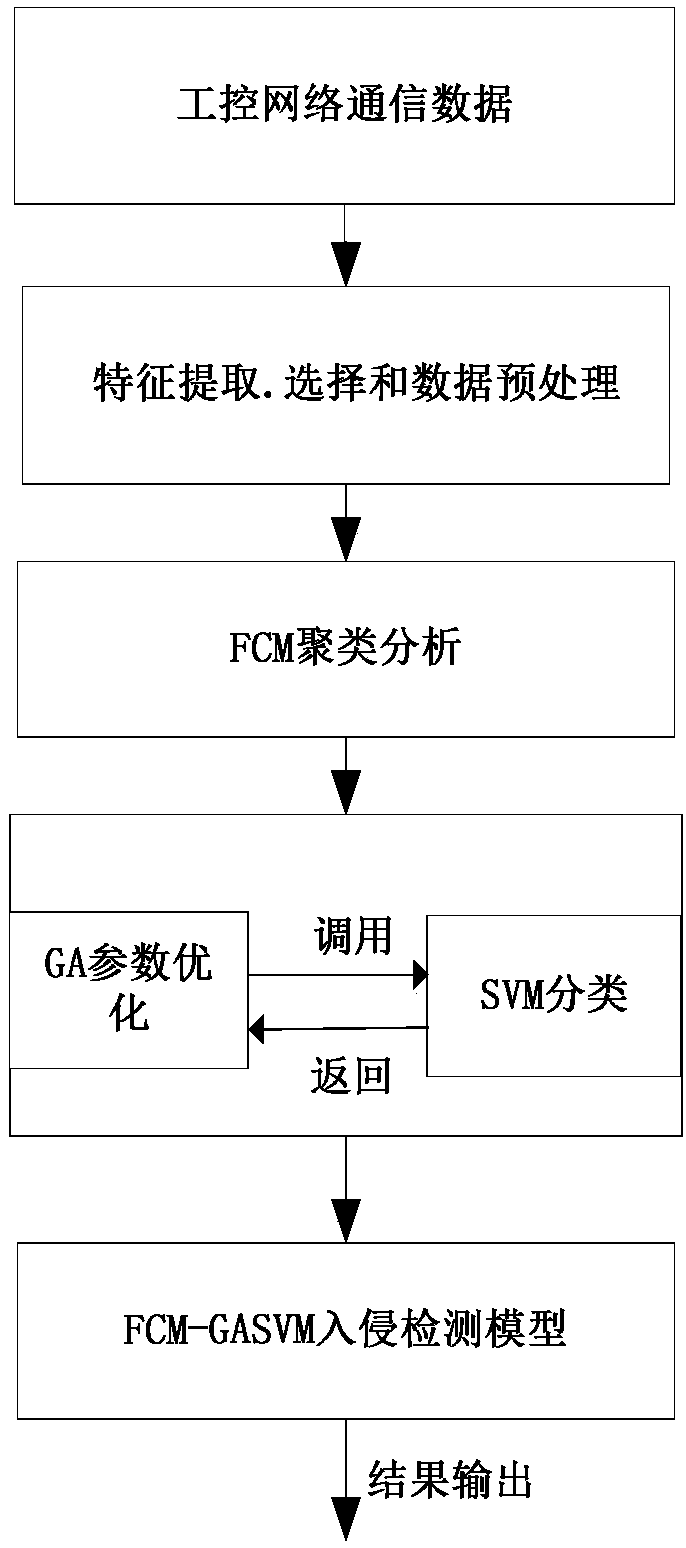
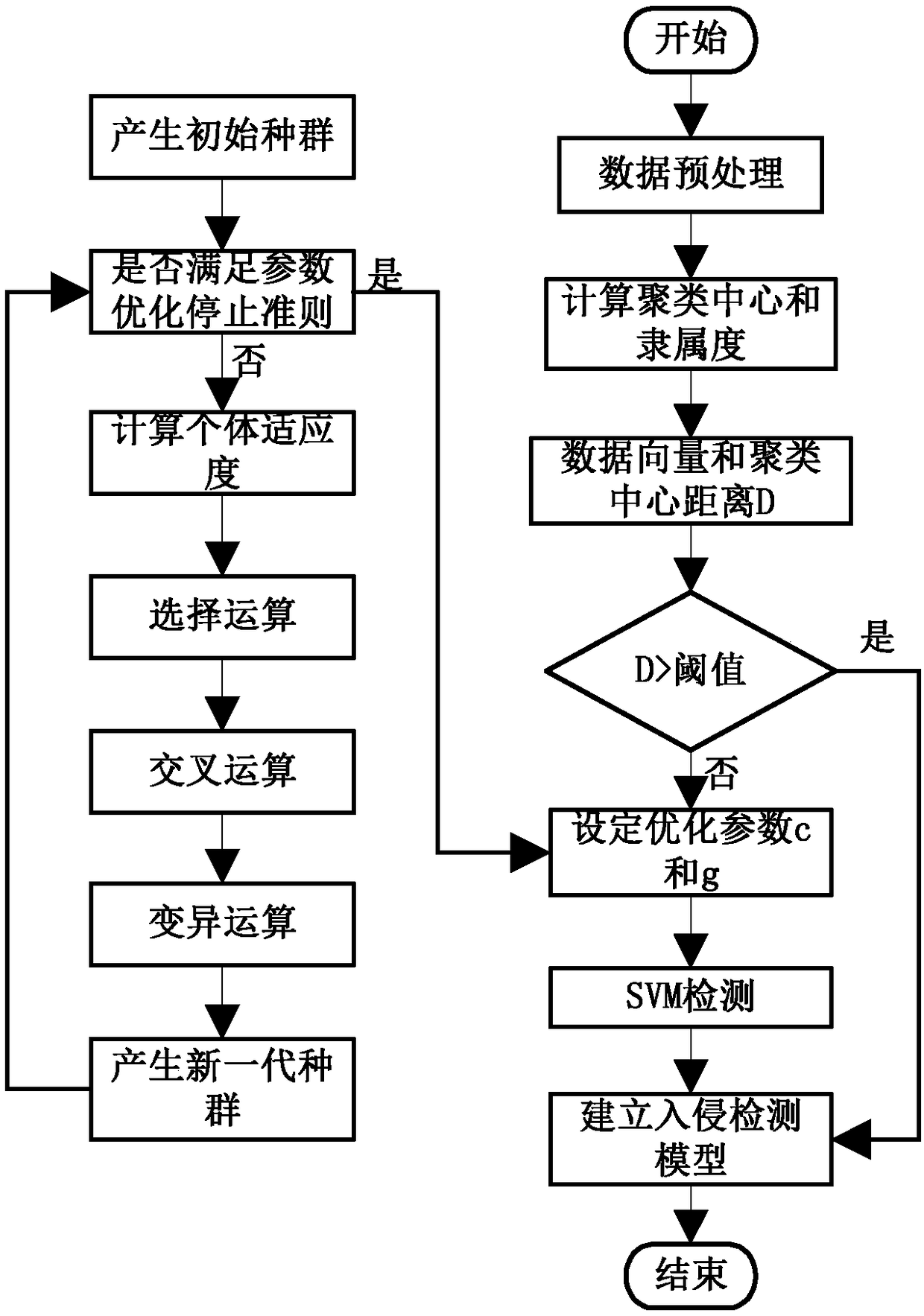
[0053] The industrial control intrusion detection method based on FCM-SVM includes the following steps:
[0054] Step 1: First, use wireshark to capture the Modbus / TCP communication traffic data packets. There are multiple attributes for each ModbusTCP / IP protocol, and extract the attributes that best reflect the data characteristics.
[0055] Step 2: According to the intrusion mode, construct the basic characteristics of the industry, the number of function code requests within 10 seconds, the number of visits to the address within 20 seconds, and the number of connections to the same device within 10 seconds.
[0056] Step 3: Sort the extracted and constructed data packets in chronological order, randomly divide them into different sequences, remove redundant data, normalize the data, and use the minimum and maximum normalization method to normalize the data of differen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com