IPv6 (Internet Protocol Version 6) network node identity security protecting method
A technology for security protection and ipv6 network, applied in the field of IPv6 network, can solve the problem that the identity security of IPv6 network nodes has not been effectively solved, and achieve the effect of protecting privacy and network security and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The following is based on Figure 1 to Figure 4 The specific embodiment of the present invention is further described:
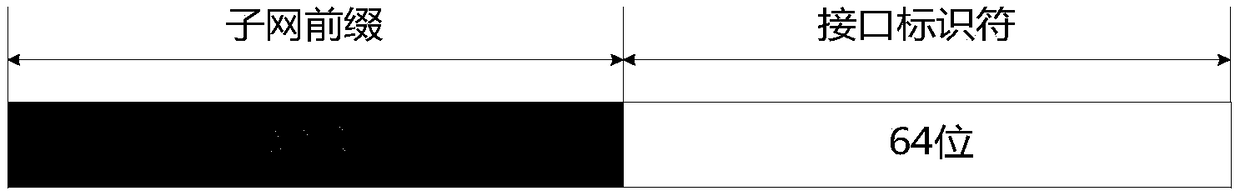
[0040] figure 1 It is an IPv6 network unicast IP address structure. The IP address has 128 bits, the first 64 bits are the subnet prefix, which will change when accessing different subnets; the last 64 bits are the interface identifier, generally according to the physical address of the node device generate.
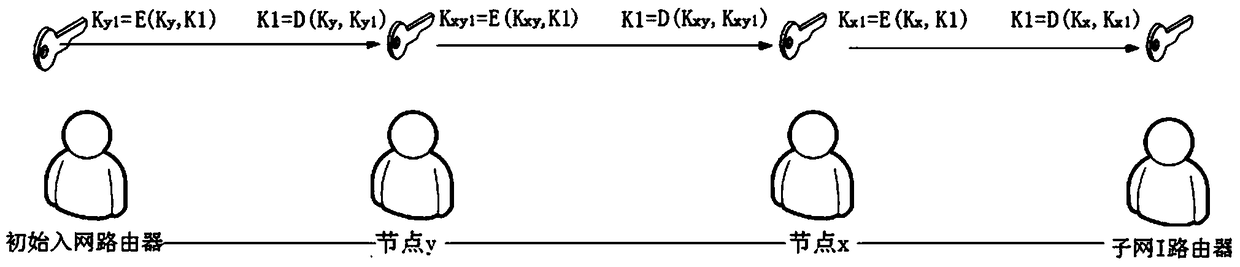
[0041]In view of the identity concealment requirement of the unicast IP address of the network node, this embodiment uses the combined operation of MAC+PIN+KEY to generate the last 64 bits of the unicast address (where KEY is the random number below), on the premise of strictly ensuring the identity information of the node Under normal circumstances, it does not affect normal data communication, and it also allows regulatory authorities to identify nodes with authorization.
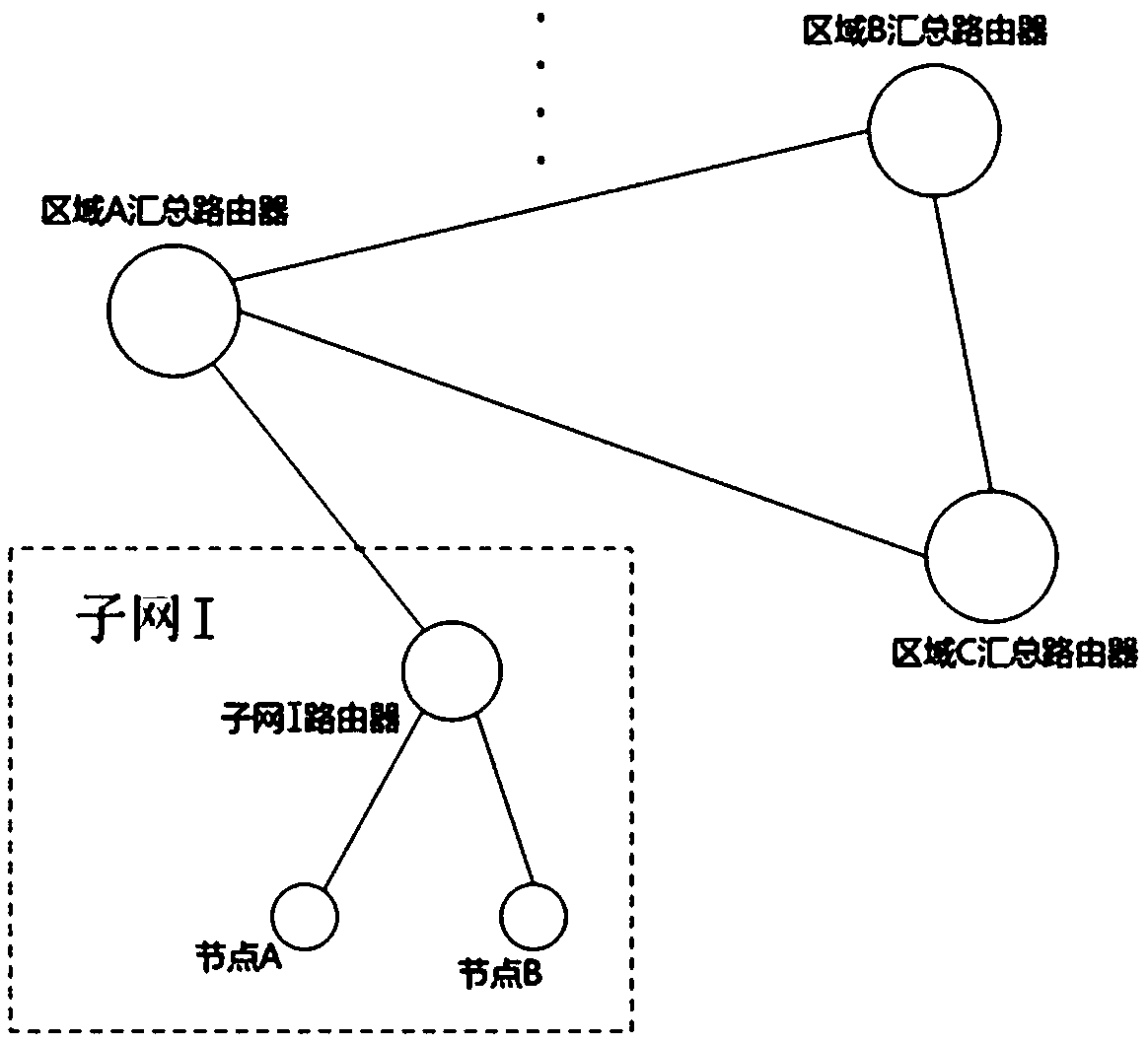
[0042] see figure 2 , figure 2 Represents a node network connec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com