An information security management system
A management system and information security technology, applied in the direction of computer security devices, electronic digital data processing, instruments, etc., can solve the problems of release risk, easy to be closed, and cannot be directly used, so as to eliminate dynamic security risks and avoid soft Risk, the effect of avoiding hard risk
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
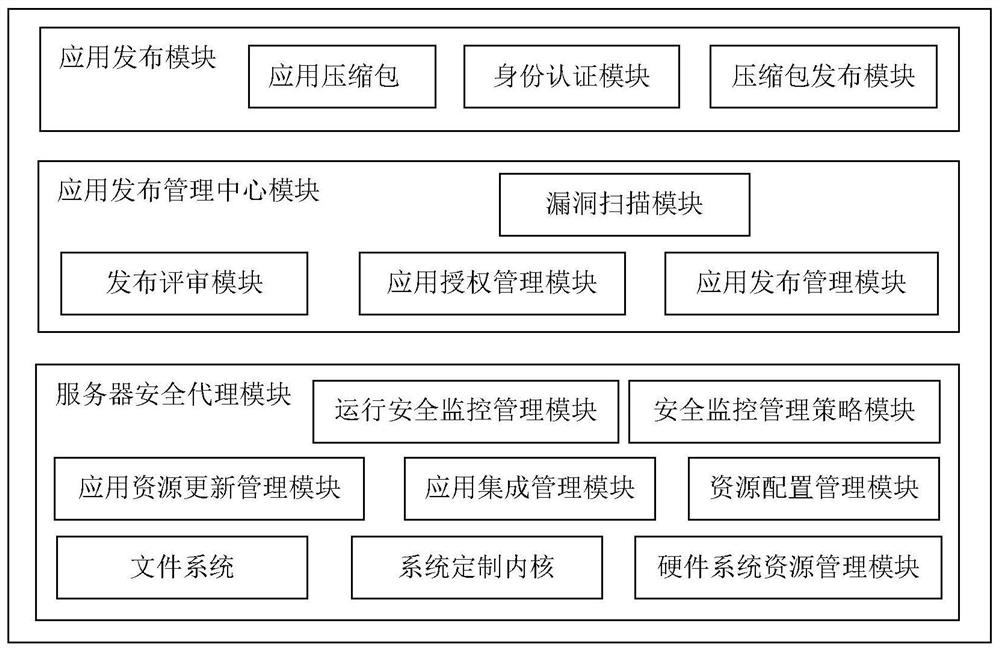
[0047] as attached figure 1 As shown, an information security management system includes an application release module, an application release management center module, a server security agent module, and an authorization management center.
[0048] The system isolates the server operating system and applications to form a cloud information system security protection model. Isolating a server operating system involves the following steps:
[0049] (1) The system kernel is cut, and only the basic driver and boot are reserved;
[0050] (2) Customize the file system;
[0051] (3) Customize the system boot loading area, that is, the MBR loading process;
[0052] (4) Integrated system kernel, file system and boot program;
[0053] (5) Integrated system resource management, application integration management and other sub-modules;
[0054] (6) Customize the initialization process of the operating system, shield all ports except ports 80 and 443; replace the login module of the ...
Embodiment 2
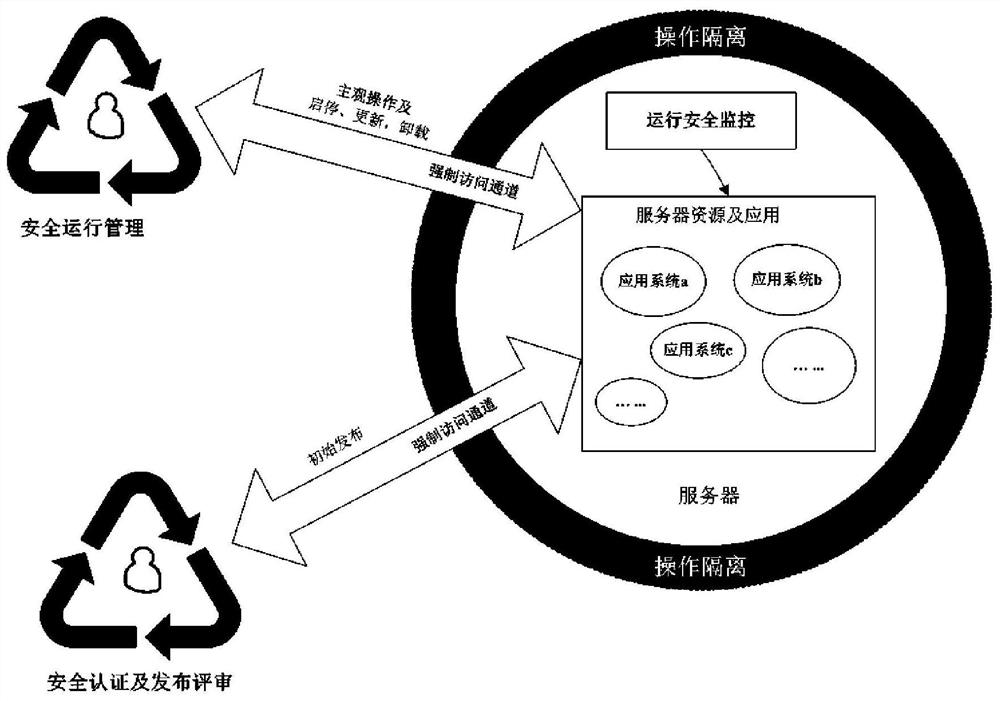
[0071] This embodiment is carried out on the basis of Embodiment 1, and the same parts will not be repeated. It mainly introduces the operation process of the information security management system, as shown in the attached Figure 4 As shown in the figure, it is the flow chart of the application release of this system. As shown in the figure, specifically, when the application release module releases the application, it first generates an installation (or upgrade) package, and logs in to the application release management center module for identity authentication. After passing, the installation package (or upgrade package) will be released to the application release management center module through the interface; the application release management center module will scan the installation package (or upgrade package) for security vulnerabilities, release review, authorization management, and generate a signed installation package (or upgrade package); the application publishin...
Embodiment 3
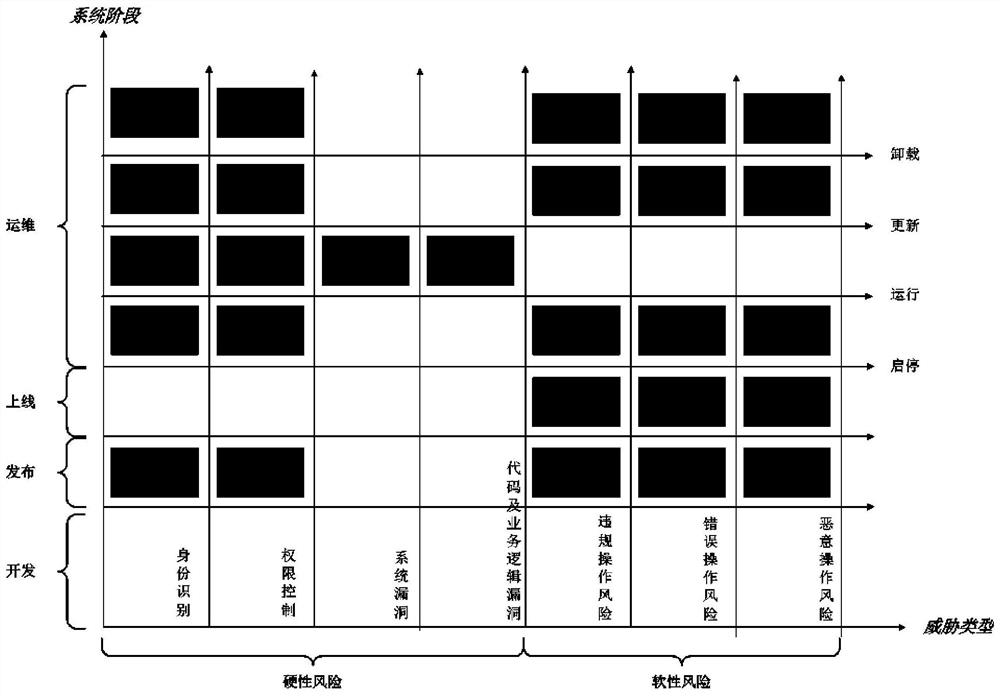
[0074] Based on the above-mentioned embodiment 1, the application publishing of this system includes the following steps:
[0075] (1) Register the name, version, and signature key of the application system to be released in the "Application Release Management Center", the list of "server security agents" who are allowed to obtain installation and operation authorization, and the list of preset system jury members;
[0076] (2) First, it is necessary to perform MD5 calculation on the xxx_yyy.tar installation package (binary compressed package) uploaded by the application publisher, and compare it with the MD5 value recorded in the xxx_yyy.config.ini file (configuration file) uploaded together. To determine the integrity of the installation package;
[0077] (3) Start the test container and automatically deploy the installation package;
[0078] (4) Start automatic vulnerability scanning, analyze and evaluate technical vulnerabilities and security risks;
[0079] (5) Generate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com