Secure protection method for container service and data processing method, device and equipment
A security protection and container technology, applied in the computer field, can solve problems such as the inability to fundamentally contain attacks, the inability of the cluster to provide services, and the unavailability of the control center to avoid the impact.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
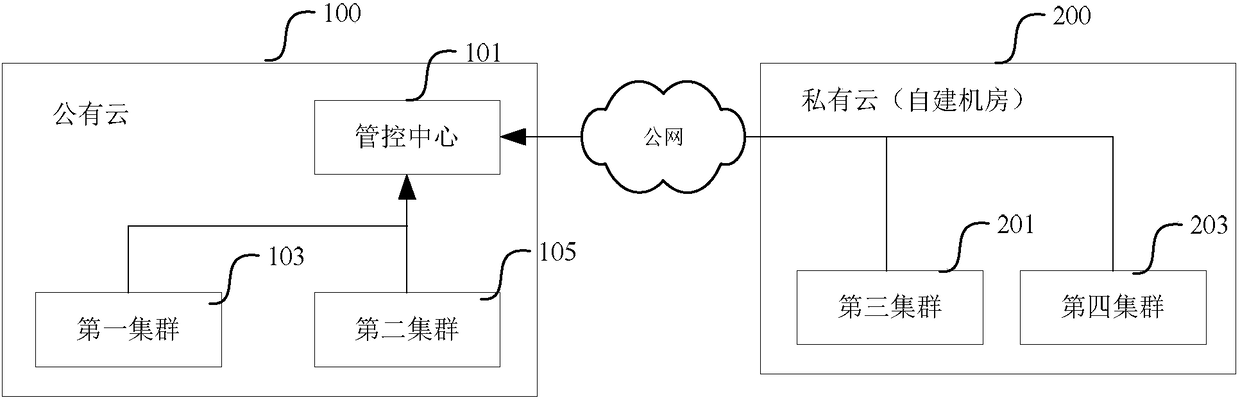
[0046] This embodiment provides a security protection method for container services, such as figure 2 shown, including:
[0047] Step 110, the management and control center receives traffic of clusters in the external network through multiple access portals, and different access portals are used to receive traffic from different clusters or cluster groups;
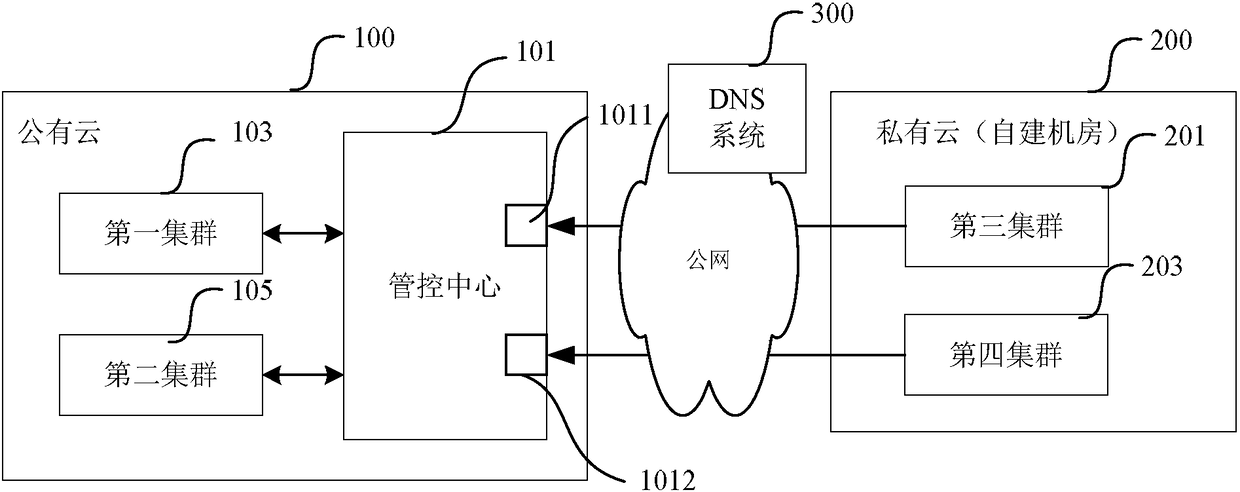
[0048] In this application, the access portal has an IP address of the public network, and is an interface provided by the management and control center for accepting public network access. An access portal is usually represented by the IP address of the access portal or the domain name corresponding to the IP address.
[0049]In this embodiment, among the plurality of access entries, different access entries have different IP addresses and domain names; the domain name system is configured with the mapping relationship between the IP addresses and domain names of the plurality of access entries, which can be in the exter...
Embodiment 2
[0078] This embodiment provides a container service cluster configuration method, such as Figure 6 shown, including:
[0079] Step 210, when the management and control center with multiple access entrances configures clusters or cluster groups in the external network, it assigns different access entrances to different clusters or cluster groups;
[0080] Step 220, the management and control center sends the allocated address information of the access entry to the corresponding cluster or cluster group.
[0081] In this embodiment, the address information is the domain name of the management and control center; the management and control center may perform the above configuration when creating a new cluster or cluster group in the external network.
[0082] This embodiment also provides a management and control center for container services, including:
[0083] Multiple access entries for receiving traffic from the cluster;
[0084] The cluster configuration module is used ...
Embodiment 3
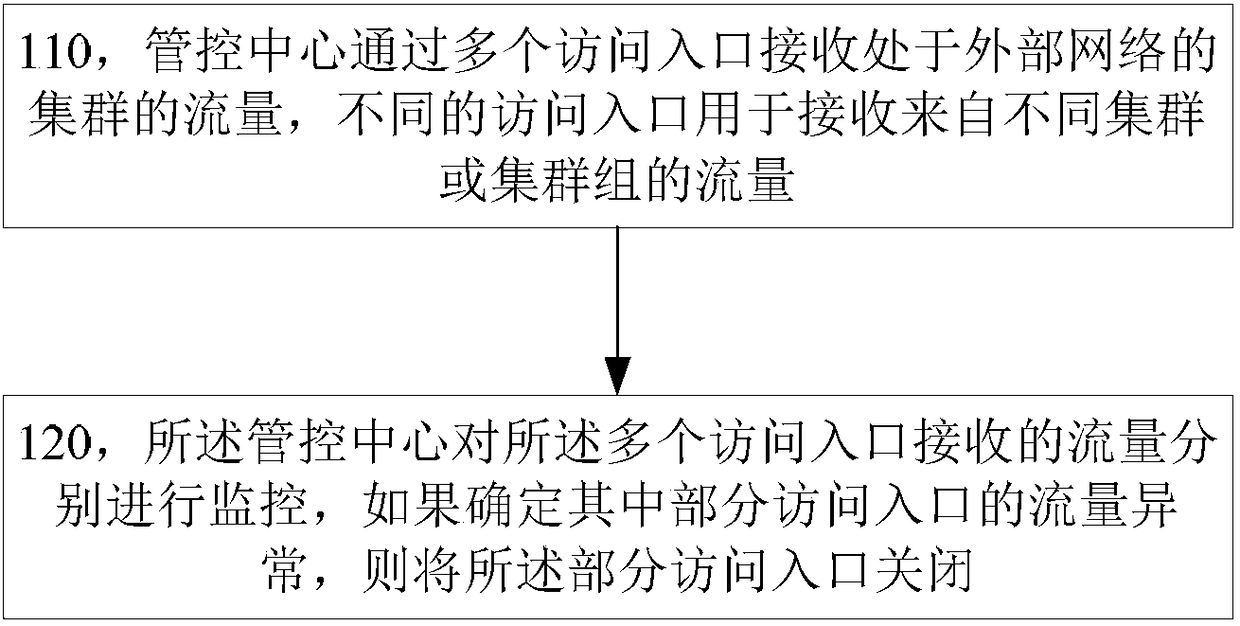
[0091] This embodiment provides a data processing method, such as Figure 7 shown, including:
[0092] Step 310, the first computing device of the public cloud receives access traffic through multiple access portals, wherein different access portals are used to receive traffic from different computing devices outside the public cloud;
[0093] Step 320, determining that the access traffic of at least one access entry in the plurality of access entries is abnormal;
[0094] Step 330, closing the access flow of the at least one access entry.
[0095] In this embodiment, the first computing device may be any device in the public cloud that can receive access traffic through multiple access portals, including but not limited to the management and control center of the public cloud. In this embodiment, the first computing device is also used for traffic monitoring, and when the traffic is abnormal, the corresponding access portal is closed. Stream processing; it may also be to n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com