A method for quickly realizing file identification under a host white list mechanism
A whitelist and file technology, applied in the field of rapid file identification under the host whitelist mechanism, can solve the problems of slowing down system response speed, multi-tasking preemption, poor user experience, etc., to improve identification ability and security , reduce the effect of HASH value calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. The method of the present invention comprises the following steps:
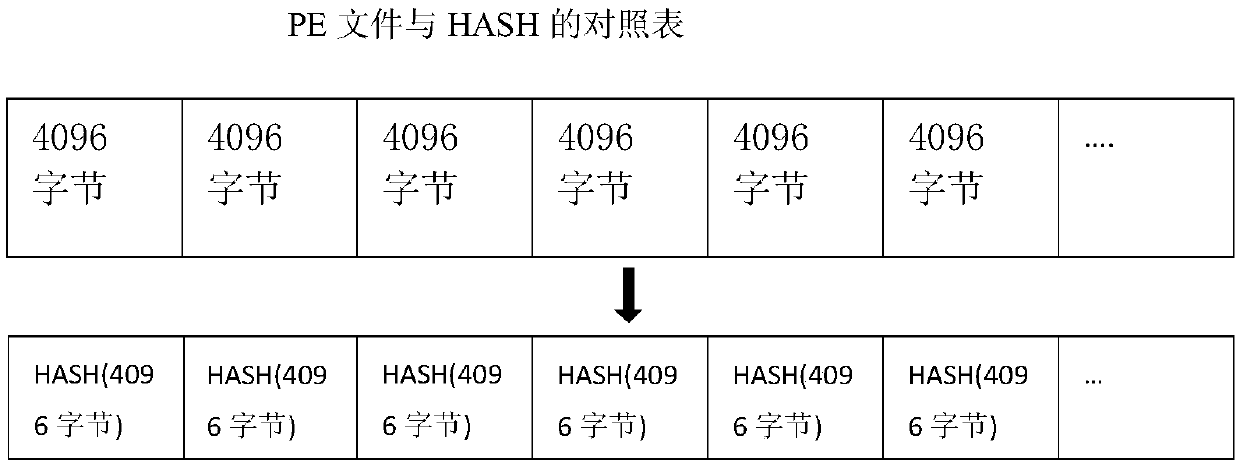
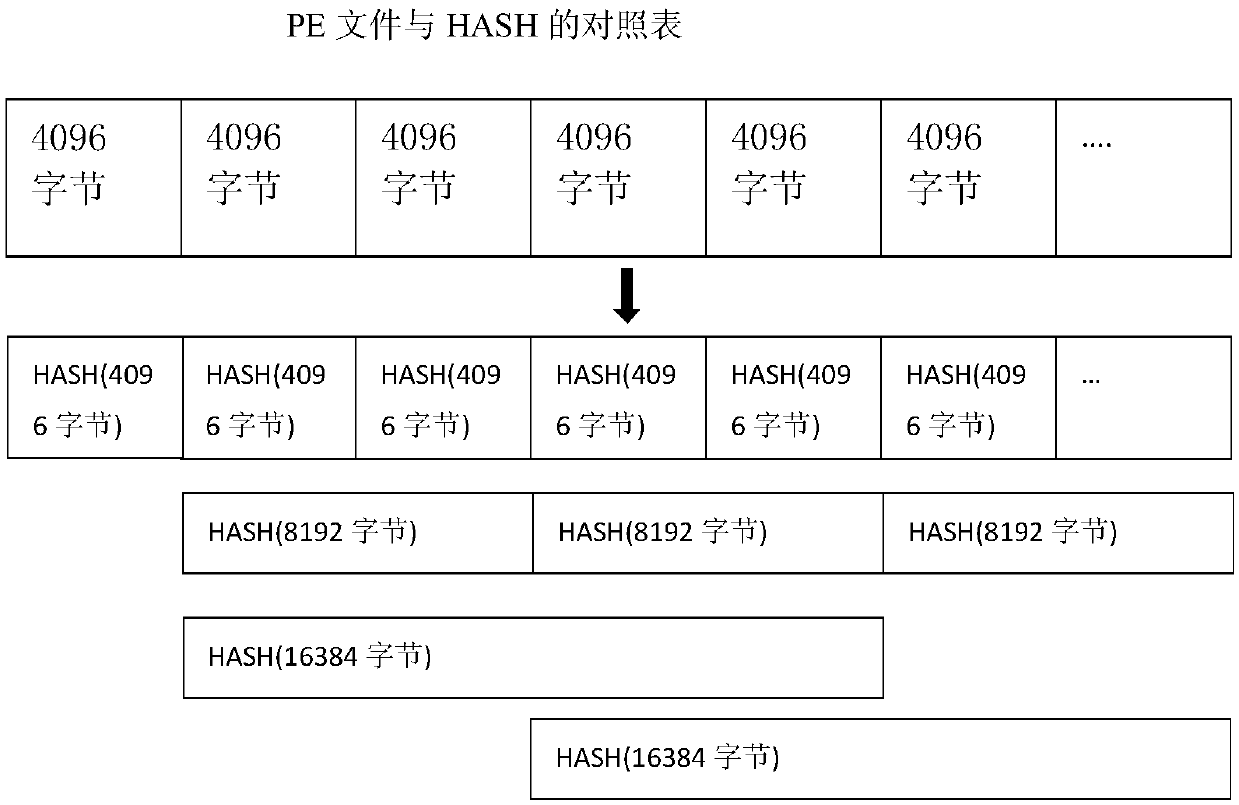
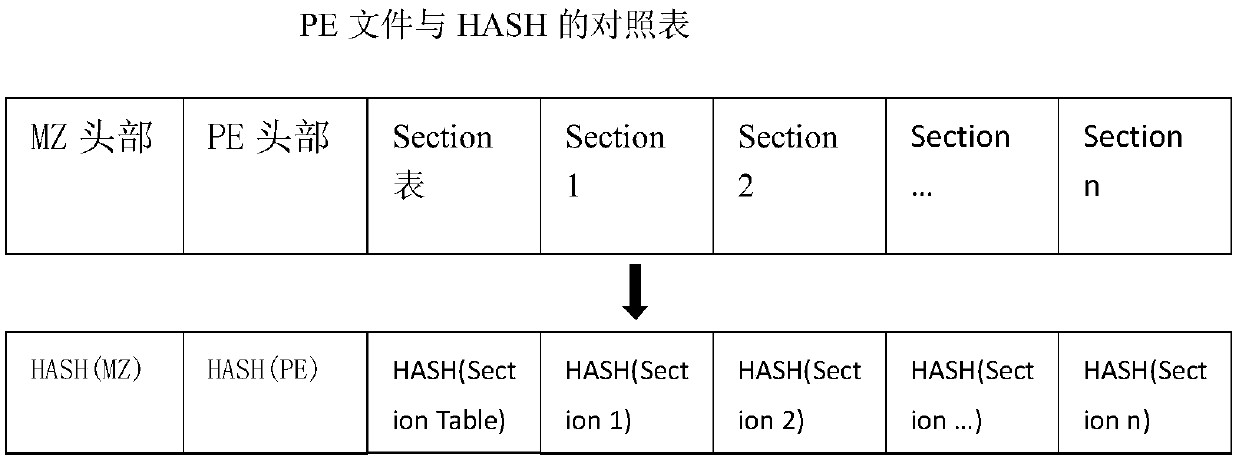
[0074] Step 1. Fragmentation Algorithm 1: Segment in sequence according to the fixed size and calculate the HASH value in turn and record it in the database, such as figure 1 Shown:
[0075] Step 1.1, in the preparatory stage, determine the fragment size according to the operating system version, number of digits, and file system, and the default is 4096 bytes;
[0076] Step 1.2, establishing and learning the whitelist stage: read the target PE file, and divide the complete file into several segments according to the unit of 4096 bytes;
[0077] Step 1.3, calculate its HASH value for each segment, and store the file name, serial number, offset position, data length, and HASH value into the structured database;
[0078] Step 1.4, for the data whose tail is less than 4096 bytes, use pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com