Encrypted data storage system and method based on remote storage of key
A storage system and technology for encrypting data, applied in the fields of information transmission and storage and information security, can solve the problems of safe separation and storage of encryption keys and ciphertext data, achieve unconditional security, low power consumption, and improve data security protection level Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
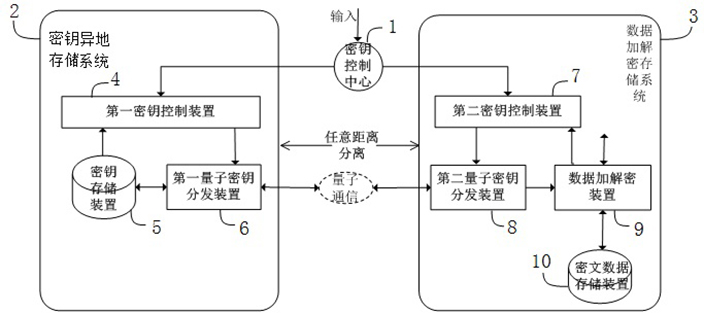
[0096] Example 1: see figure 2 , figure 2 Only the basic structure of the key off-site storage system 2 and the data encryption and decryption storage system 3 in the database system application is illustrated, that is, the basic security principles for establishing database encryption storage and access, and database security backup are illustrated, and the key-based off-site storage is completed. The encrypted data storage system in the database system is combined with various security control devices in the database system to improve the security of the data. The specific structure is as follows.
[0097] The encrypted data storage system based on key off-site storage is in the database application system, the database application system refers to a structured database application system, or an unstructured database application system, or a cloud storage application system. Key offsite storage system 2 , data encryption and decryption storage system 3 , data security sto...
Embodiment 2
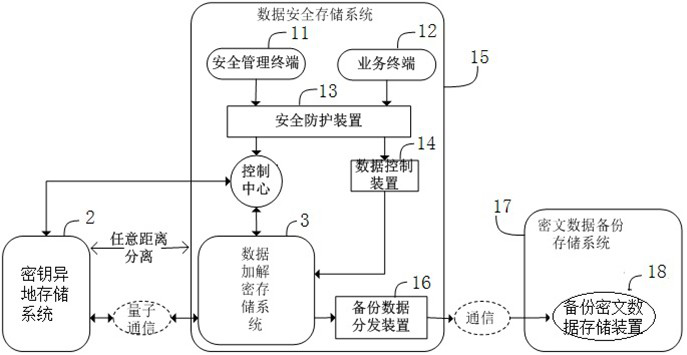
[0101] Example 2: see image 3 , image 3 Only the basic structure and principle of the encrypted data storage system based on key off-site storage in the database active-active application is shown, and the combination of the encrypted data storage system based on key off-site storage and the database active-active system encryption device is completed, which greatly improves the database. The security of the active-active system and the high reliability guarantee of the active-active database application are improved. The specific structure is as follows.
[0102] The database active-active system of the encrypted data storage system based on key off-site storage, wherein the database application system can be a structured database application system, an unstructured database application system, or an active-active or multi-active database system of a cloud storage application system , the system structure includes a control center, an off-site key storage system 2 , a firs...
Embodiment 3
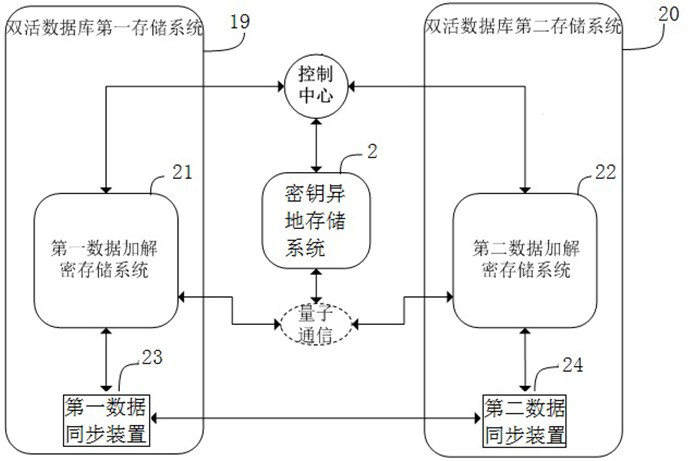
[0105] Embodiment 3: see Figure 4 , Figure 4 It only illustrates the basic structure and principle of the application of the dual-key remote storage system 2 based on the encrypted data storage system stored in different places, which realizes multiple remote storage of keys and improves the efficiency and security of key storage. The dual-key off-site storage system 2 includes a key control center 1, a data security storage system 15, a first key off-site storage system 25, and a second key off-site storage system 26; the data security storage system 15 includes a data encryption and decryption storage system 3;
[0106] The key control center 1 controls the data encryption and decryption storage system 3, the first key remote storage system 25 and the second key remote storage system 26 to work, and the specific encryption method and decryption method are the same as figure 1 The encryption method and decryption method in the structure are basically the same, the differe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com