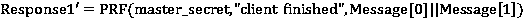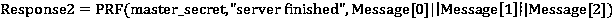Bidirectional self-authentication method based on identification password
A technology for identifying passwords and authentication methods, applied in the field of computer network security, can solve the problems of attackers forging or stealing tokens, inability to perform double authentication, and management pressure, etc., to increase defense capabilities, simple and efficient two-way authentication, and simple implementation. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
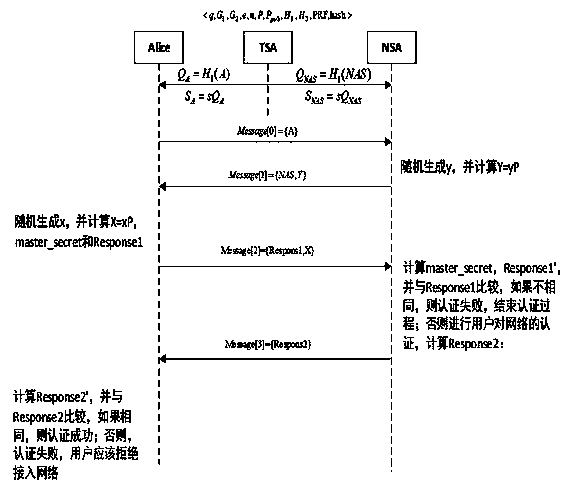
[0029] The present invention will be described in detail below in conjunction with the accompanying drawings. The description in this part is only exemplary and explanatory, and should not have any limiting effect on the protection scope of the present invention. In addition, those skilled in the art can make corresponding combinations of features in the embodiments in this document and in different embodiments according to the descriptions in this document.
[0030] The terms "first", "second", "third", "fourth", etc. (if any) in the description and claims of the present invention and the above drawings are used to distinguish similar objects and not necessarily Describe a particular order or sequence. It is to be understood that the data so used are interchangeable under appropriate circumstances such that the embodiments of the invention described herein, for example, can be practiced in sequences other than those illustrated or described herein. Furthermore, the terms "co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com