Priority-considered multi-level backup blocking method for attack exception of an industrial control system
An industrial control system and priority technology, applied in the transmission system, branch remote connection/disconnection, electrical components, etc., can solve the hidden dangers of the safe and stable operation of the power grid industrial control system, cannot guarantee the reliability of attack exception blocking, attack and abnormality Identify problems such as low accuracy, and achieve the effect of promoting large-scale applications, reducing economic losses, and reducing management difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
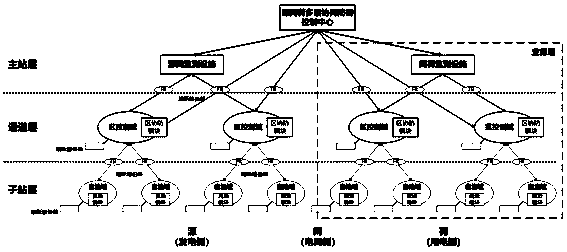
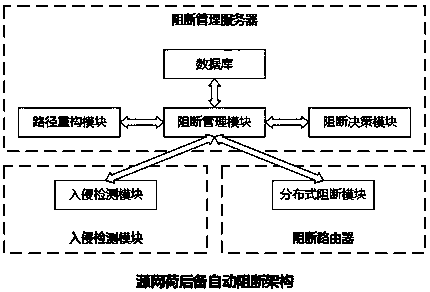
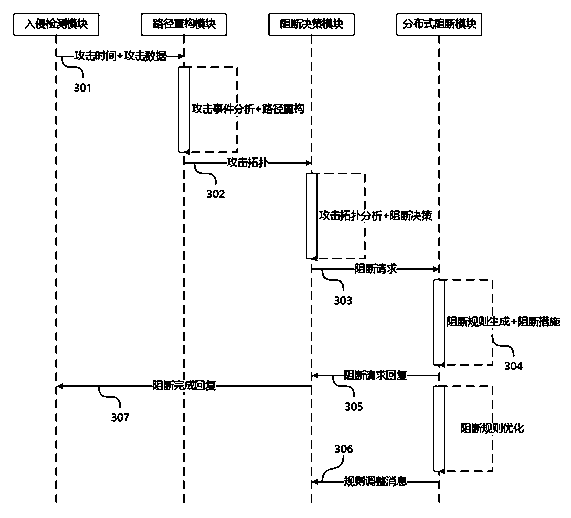
[0051] The priority-considered multi-level backup blocking method for an industrial control system attack abnormality in this embodiment, wherein the industrial control system includes an intrusion detection module, a path reconstruction module, a blocking decision-making module, a distributed blocking module, and a database.
[0052] Based on the source-network-load network architecture, it is generally divided into master station layer, communication layer, city aggregation, access layer and user terminal layer. The specific contents of each part are as follows:
[0053] 1. The master station layer includes the production control area and the management information area, in which the production control area includes the EMS application system and the load control quick response subsystem, and the management information area includes the power consumption information collection system;
[0054] 2. The communication layer is composed of routers, responsible for connecting the m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com