high-hiding network agent method and system based on an HTTP protocol
An HTTP protocol and network proxy technology, applied in the field of high-secrecy network proxy methods and systems, can solve the problems of weak concurrency and easy identification of traffic, and achieve low cost, efficient proxy services, and reduced computing and occupancy rates. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the following specific embodiments are described in detail in conjunction with the accompanying drawings.
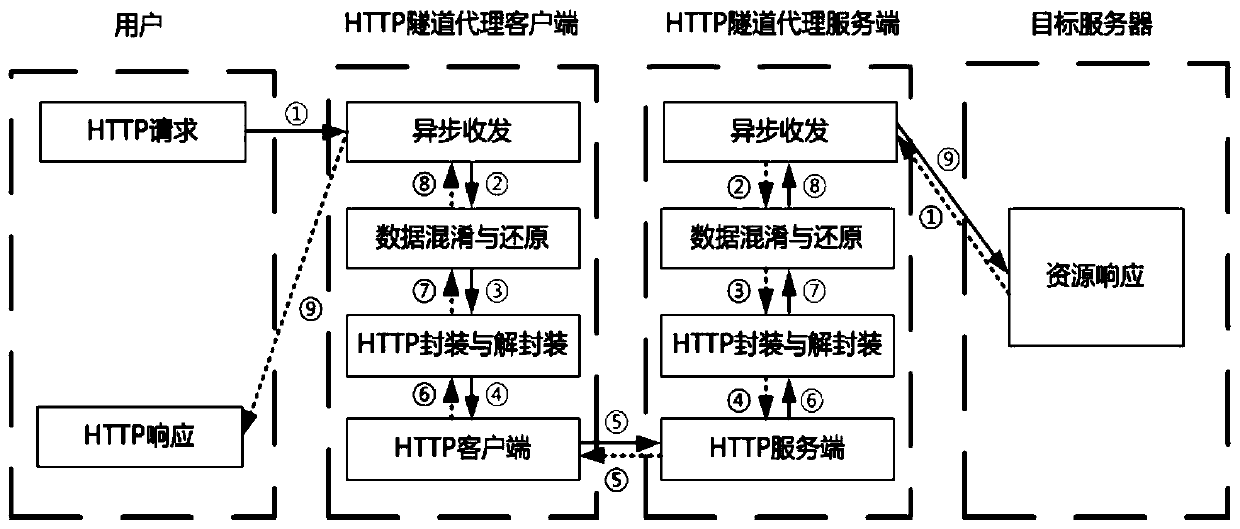
[0065] The present embodiment provides a highly hidden network proxy system based on the HTTP protocol, such as figure 1 shown. A complete HTTP request forwarding process requires the joint participation of the user, the tunnel proxy client, the tunnel proxy server and the target server to complete. The whole process can be divided into two parts, the process in which the user sends an HTTP request to the target server and the server returns a resource response. The specific instructions are as follows:
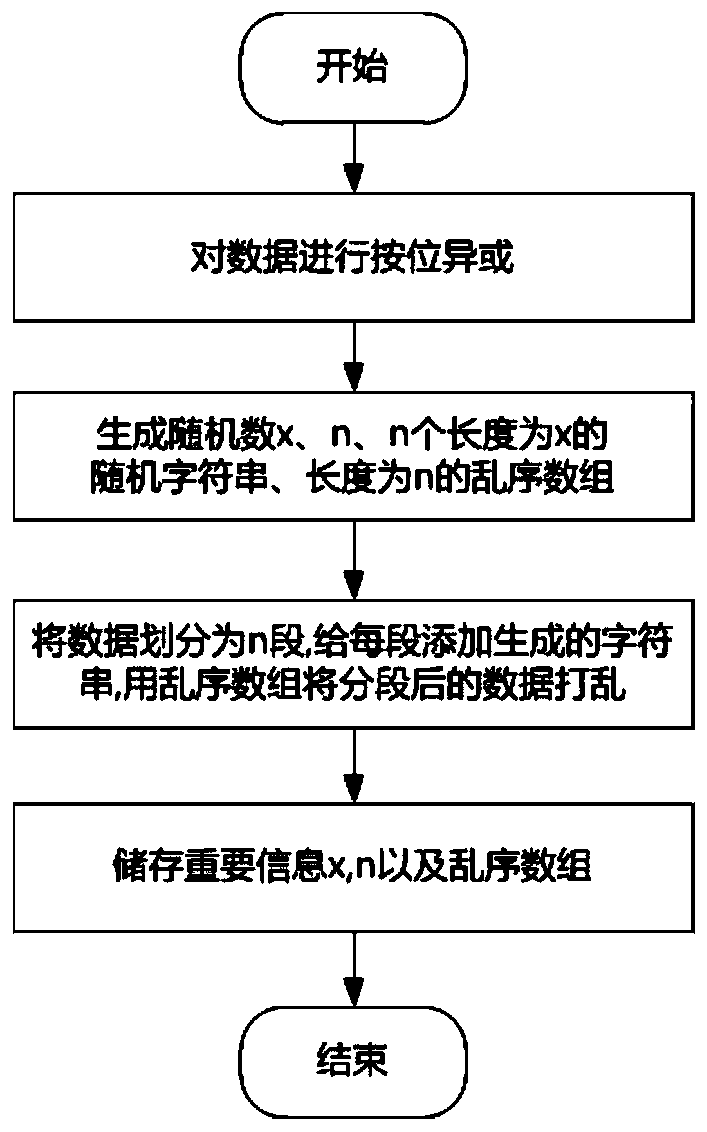
[0066] (1) The tunnel proxy client listens on the corresponding port. Whenever the user sends an HTTP request (GET, POST, PUT or CONNECT, etc.) to the server in the Internet, a TCP connection will be established with the user. After the connection is esta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com