A method for anonymous user authentication in the Internet of Things based on crowd sensing based on chaotic maps
A technology of crowd sensing and user authentication, which is applied in user identity/authority verification, digital transmission systems, secure communication devices, etc., can solve the problems of high computing overhead or communication overhead, difficulty in resisting various typical attacks, etc., and reduce communication Comparing with computational overhead, the effect of good forward security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0024] Specific implementation mode 1: In this implementation mode, a method for anonymous user authentication of the Internet of Things based on crowd intelligence sensing based on chaotic mapping. The specific process is as follows:
[0025] 1 Mathematical model
[0026] The present invention establishes corresponding mathematical models for the one-way hash function, Chebyshev chaotic map and fuzzy extraction to be adopted in the proposed user authentication scheme.
[0027] 1.1 One-way hash function with anti-collision
[0028] One-way cryptographic hash function h:{0,1} * →{0,1} n , also known as one-way Hash function, hash function, is to input binary string q∈{0,1} of any length * Change into a fixed-length binary string, and the output string is called the hash value of the character. The anti-collision performance of the one-way hash function h( ) is as follows:
[0029] Definition 1 Collision resistance: The advantage probability that any attacker A has a collis...
specific Embodiment approach 2
[0070] Specific embodiment two: the difference between this embodiment and specific embodiment one is that the user is registered in the step one; the specific process is:
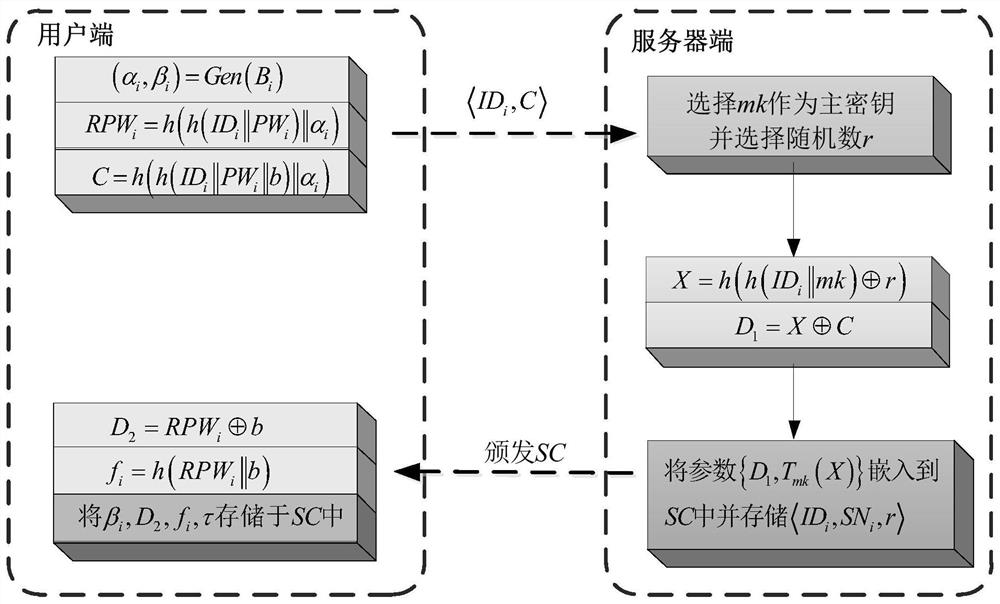
[0071] CMAUS first needs to be registered, and legal users can obtain their smart cards SC from the server S. u i Communication with S is carried out on a secure channel, the specific process is as follows figure 1 Shown:
[0072] Step 11. Any user U i Select user U i ID i , login password PW i , personal biometric B i and a 128-bit random number b;
[0073] Steps 1 and 2, using the probability generation process in fuzzy extraction, the user U i generating function (α i ,β i ) = Gen(B i ), for user U i ID i , login password PW i , personal biometric B i Encrypt with 128-bit random number b to obtain masked login password RPWi=h(h(ID i ||PW i )||α i ) and user U i The identity certificate C=h(h(ID i ||PW i ||b)||α i );
[0074] Among them, α i for user U i biometric private key, β ...
specific Embodiment approach 3
[0087] Specific embodiment three: the difference between this embodiment and specific embodiment one or two is that after the user registers in the step two, the user logs in; the specific process is:
[0088] User U i You need to log in to the system to access server S, the process is as follows:
[0089] Step 21. User U i Insert the smart card SC into the mobile client (such as mobile phone, computer, etc.), and enter the user U i ID i , login password PW i and personal biometric B' i ;
[0090] The user's smart card SC utilizes the stored β i , calculate α′ through deterministic recovery process i =Rep(B' i ,β i ), RPW′ i =h(h(ID i ||PW i )||α′ i ) and generate
[0091] In the formula, α' i is the personal biometric B' i private key, b' is the registration parameter to be verified; RPW' i is the masked login password;
[0092] Step 22. Based on step 1, the user's smart card SC calculates f' i =h(RPW' i ||b′), and verify f′ i = f i whether it is estab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com