Trojan file tracing method, system and equipment
A Trojan horse and file technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as inability to effectively identify features, simple detection methods, and backward traceability methods, and achieve the goal of improving speed and efficiency, expanding analysis dimensions, accurate judgment, and traceability capabilities. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
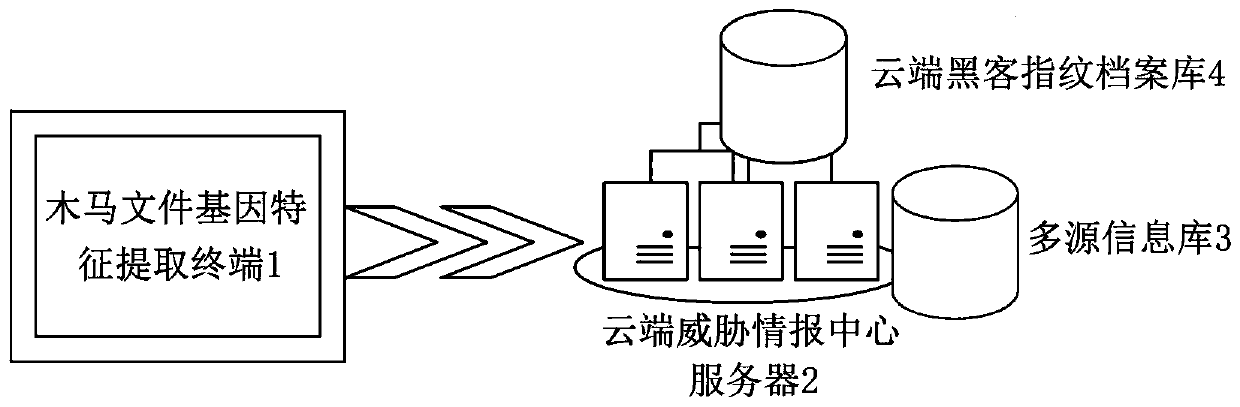
[0034] refer to figure 1 A Trojan file traceability device proposed in an embodiment of the present invention includes: a Trojan file gene feature extraction terminal 1, a cloud threat intelligence center server 2, a multi-source information library 3, and a cloud hacker fingerprint archive library 4; wherein, the cloud threat intelligence center server 2 is respectively connected to the Trojan horse file gene feature extraction terminal 1 and the cloud hacker fingerprint archive 4 through wired or wireless network communication, and the cloud threat intelligence center server 2 is connected to the multi-source information library 3 through wired or wireless network communication or the cloud threat intelligence center server 2 is embedded with a multi-source information base 3 .
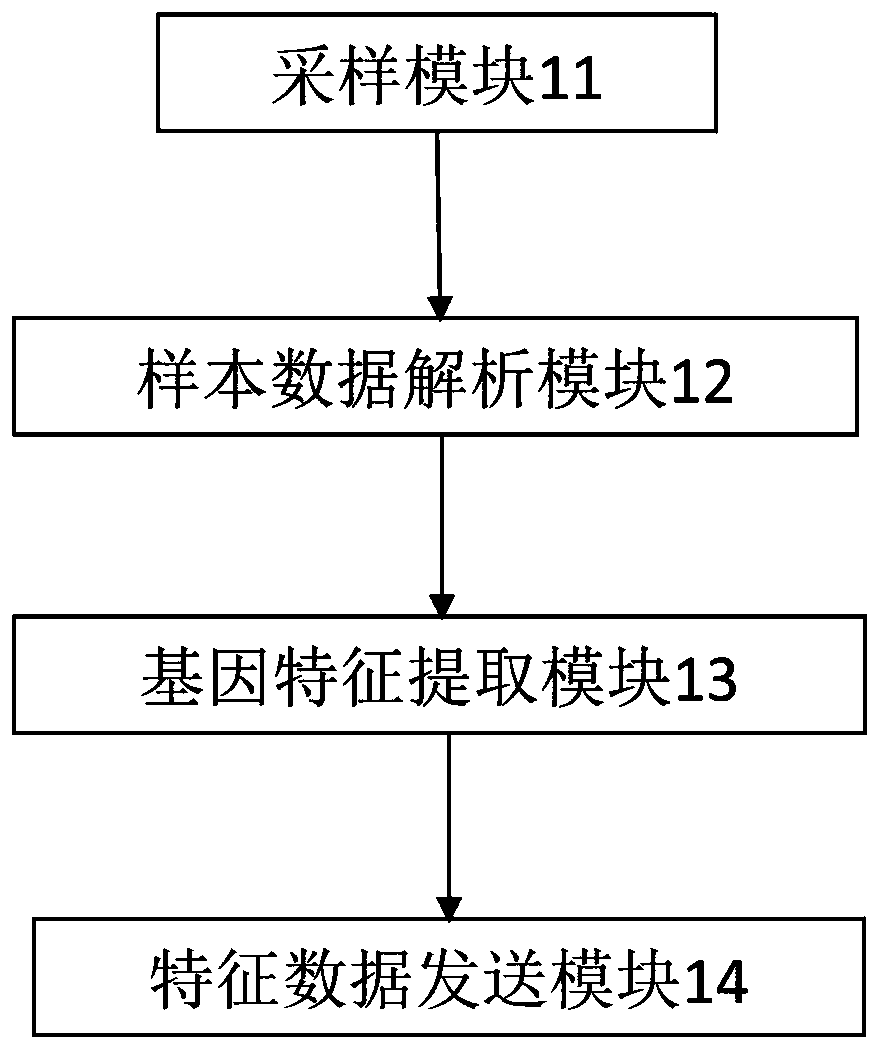
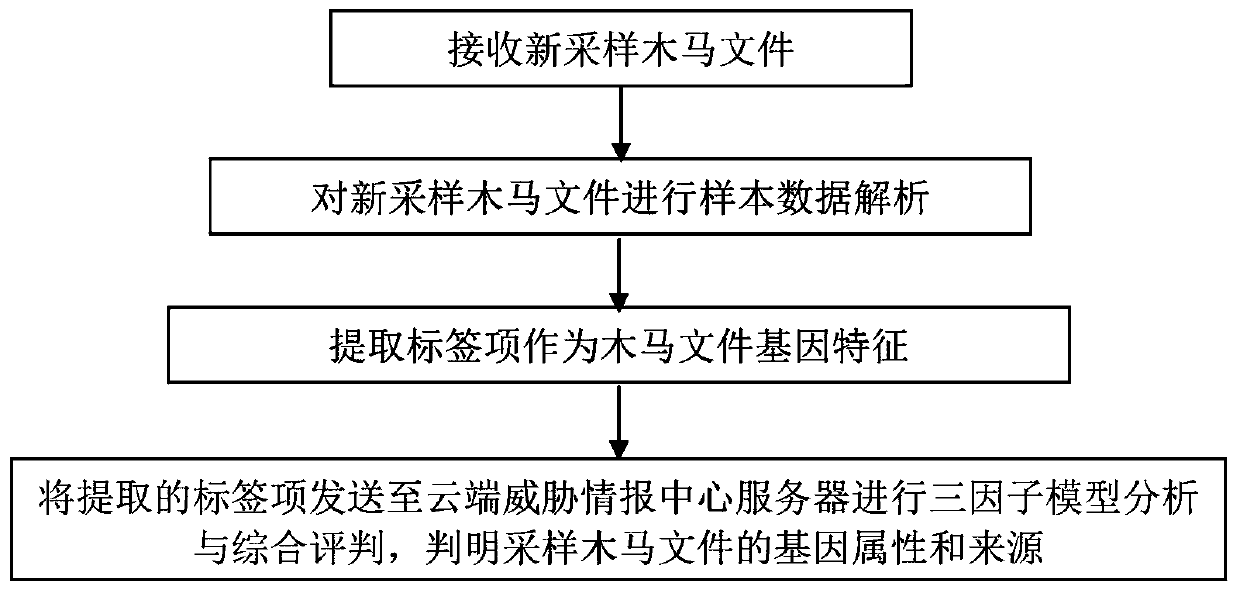
[0035] Trojan horse file gene feature extraction terminal 1 stores computer program instructions, a kind of Trojan horse file traceability system applied to Trojan horse file gene feature extraction...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com