A camouflage attack detection method based on a DQL algorithm in fog computing
A detection method, fog computing technology, applied in security devices, electrical components, wireless communication, etc., can solve the lack of research on the randomness of wireless channel movement, without considering the application of physical layer security technology, masquerading attacks by malicious users in fog computing networks, etc. problems, to achieve the effect of improving overestimation problems, enhancing security protection capabilities, and solving threshold problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
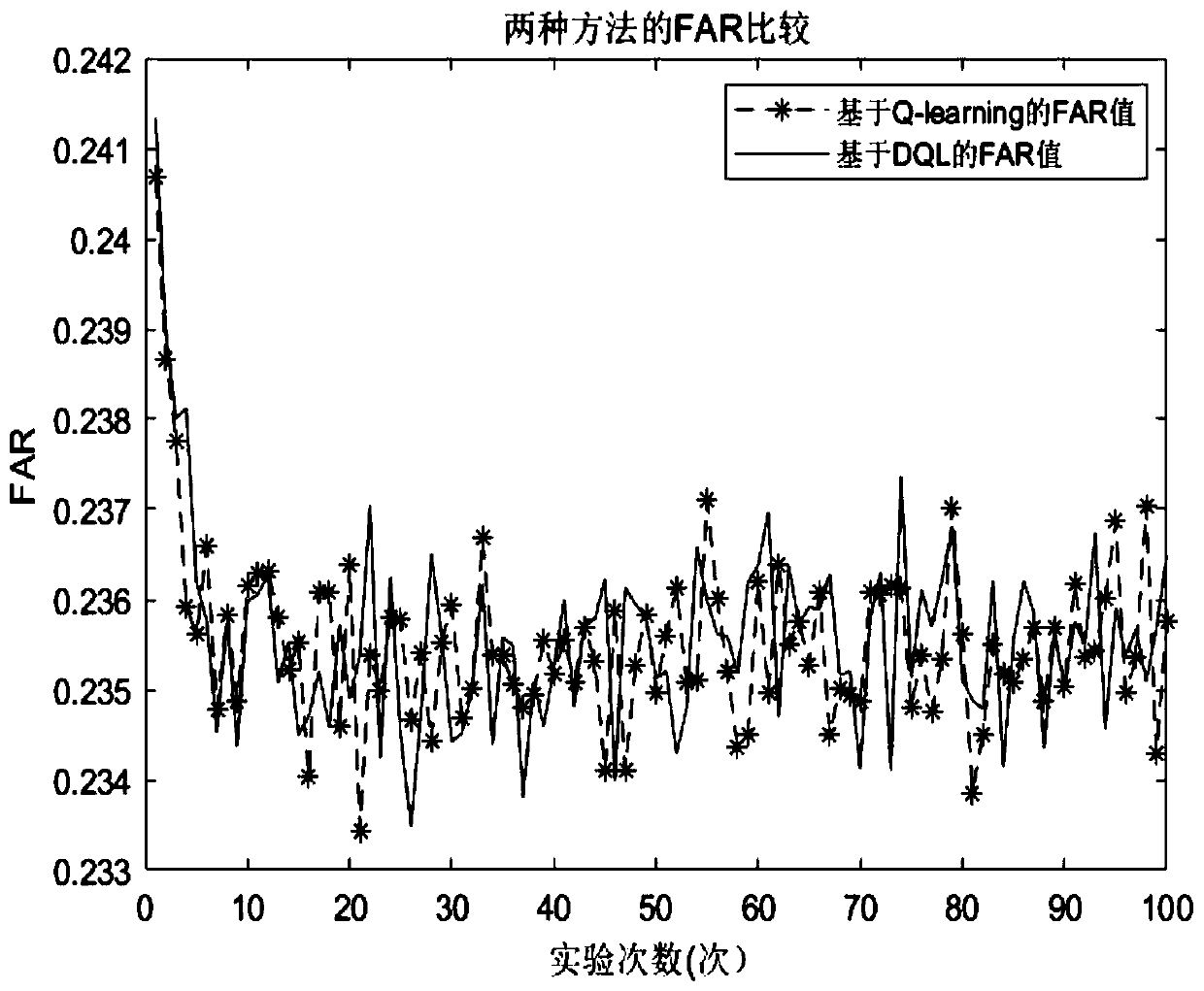
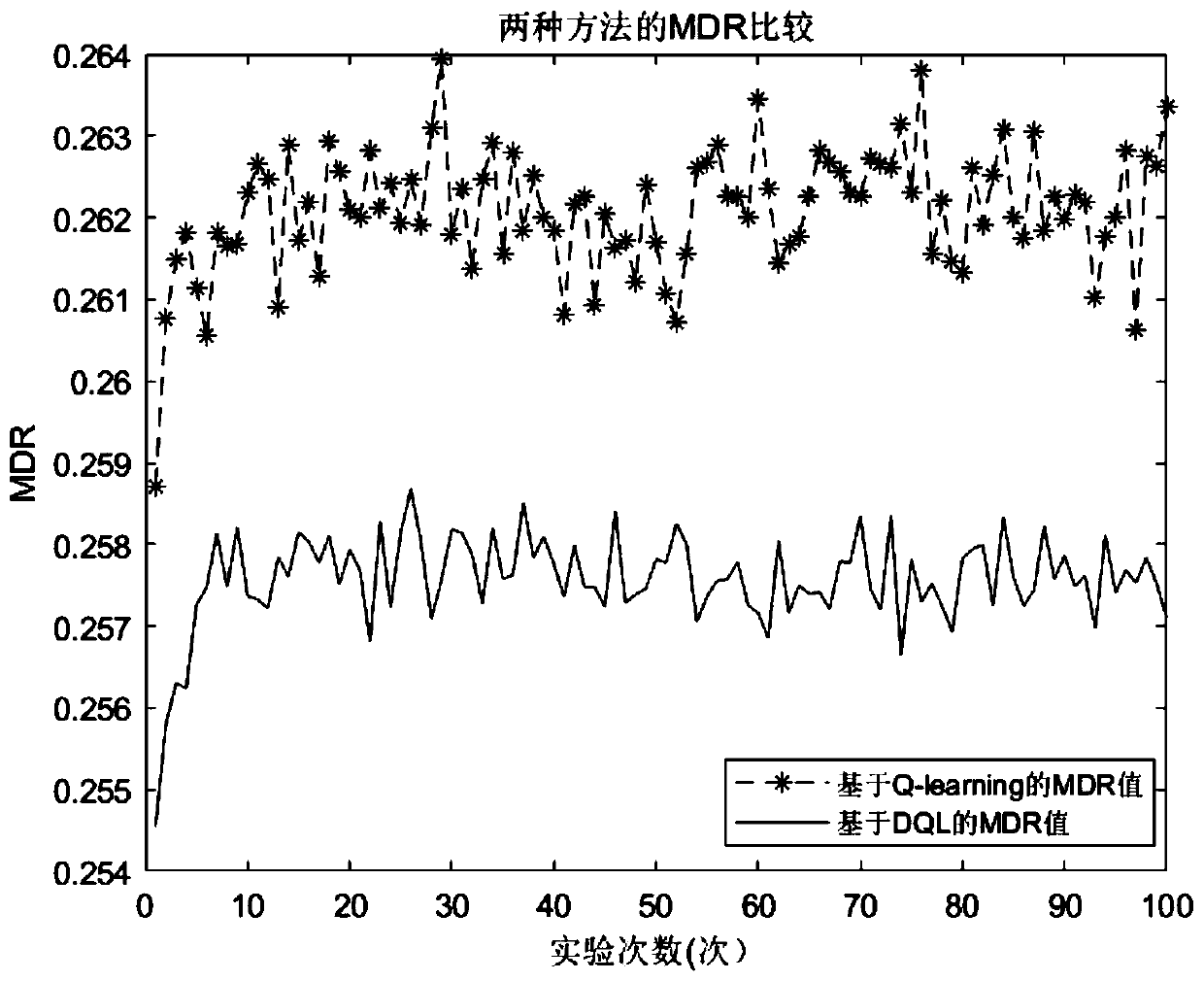
[0075] The present invention obtains a fog computing masquerading detection method based on the DQL algorithm, designs a masquerading attack security model in fog computing, and adopts this method to detect masquerading attacks; through detection by this method, the detection threshold can be optimized, solving the problem The threshold problem of detecting masquerading attacks improves the accuracy of detection; at the same time, it enhances the security protection capability of the fog computing network.
[0076] The present invention adopts following technical scheme and implementation steps:
[0077] 1. Masquerade Attack Security Model in Fog Computing
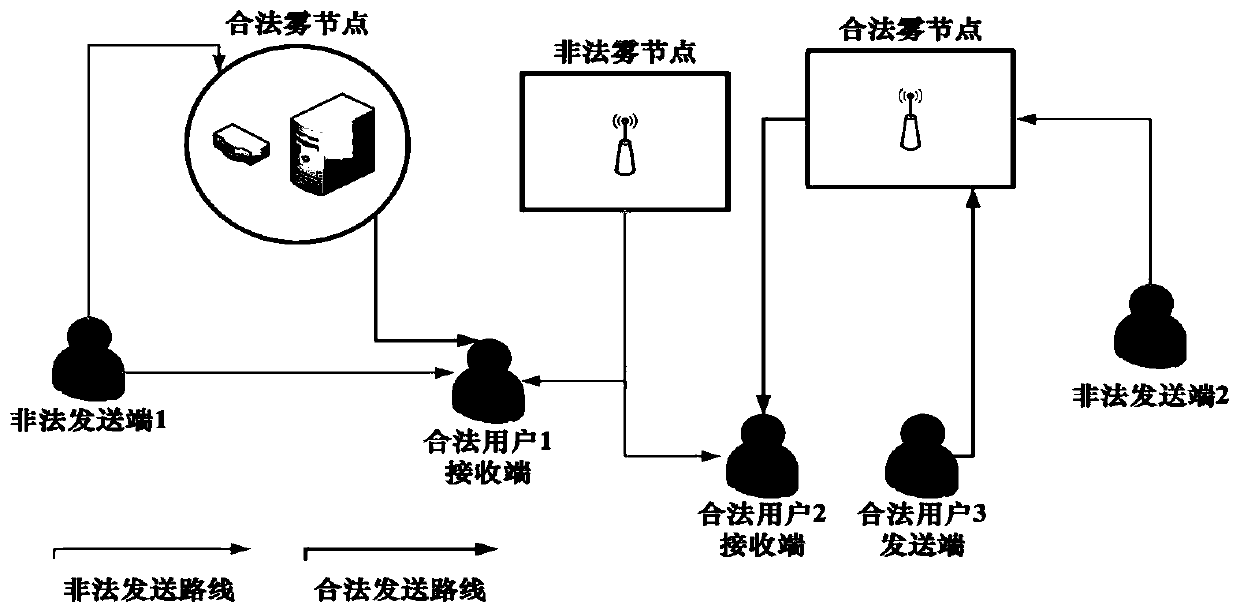
[0078] The security model of the present invention is oriented to fog nodes and end users, and considers the wireless network between fog nodes and end users. Suppose there are a sending end, r receiving end, h legal nodes and i illegal nodes, among which:
[0079]
[0080]
[0081] like figure 1 shown. A rogue n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com