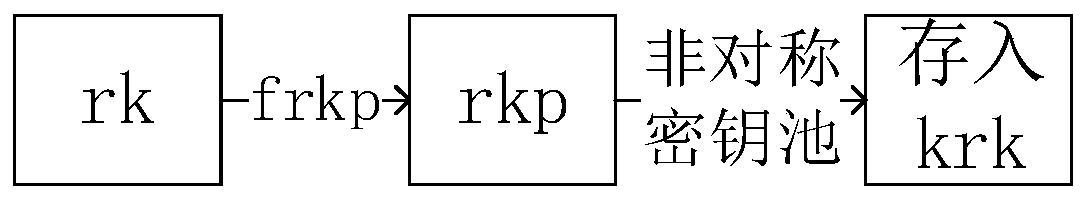Anti-quantum computing intelligent household quantum cloud storage method and system based on quantum key card
A smart home and quantum computing technology, applied in quantum computers, calculations, computing models, etc., can solve problems such as cracking, stealing information, malicious software or malicious operation theft, so as to prevent the use of secure clouds, improve security, and reduce cracking risk effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
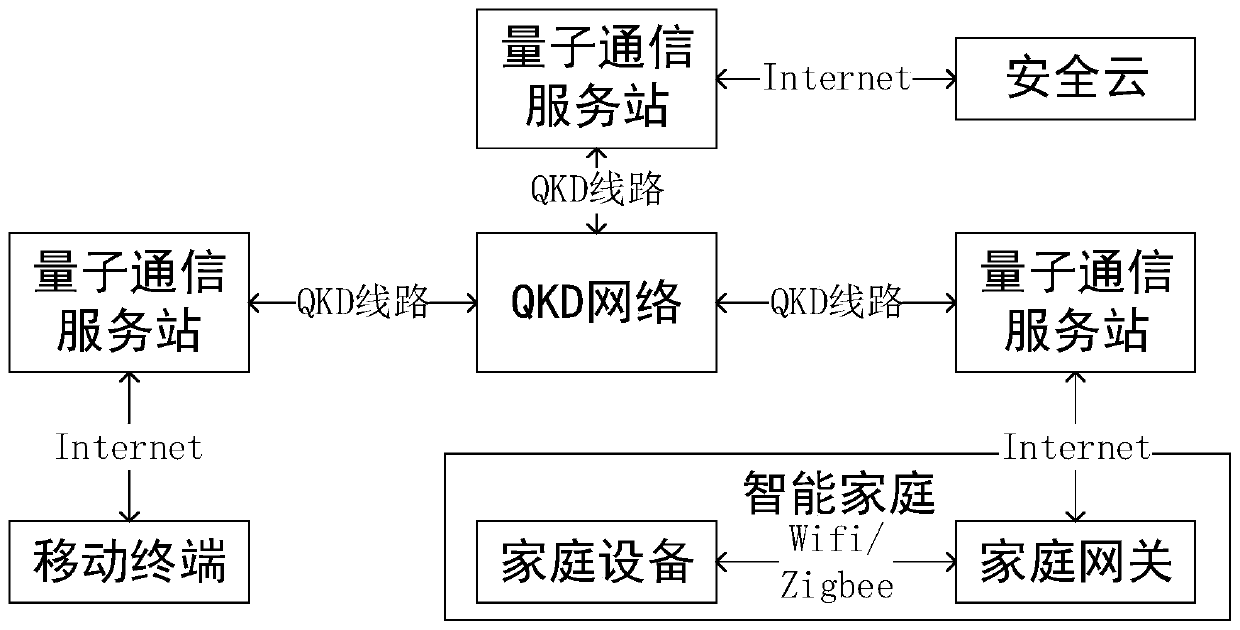
[0093] In this embodiment, smart family members upload files to the security cloud. The uploading of files by smart family members to the security cloud is divided into the following three situations: mobile terminal M uploads files to the security cloud, home gateway S uploads files to the security cloud, and home device C uploads files to the security cloud. files to the secure cloud.
[0094] Case 1: The mobile terminal uploads files to the secure cloud. like figure 1 As shown, the mobile terminal uploads files to the secure cloud through the quantum communication service station.
[0095] Step 1.1.1: The mobile terminal sends the file to the quantum communication service station.
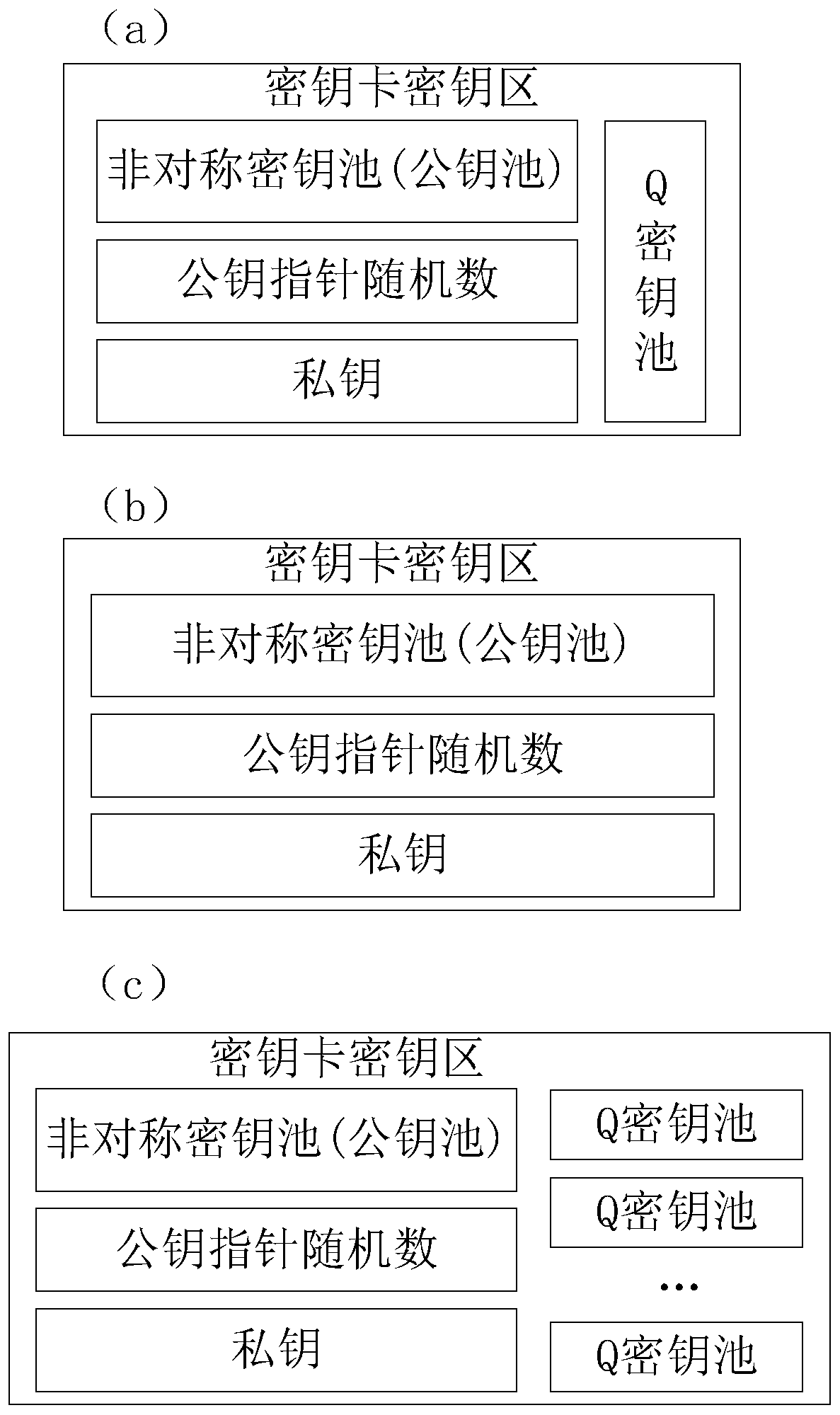
[0096] The mobile terminal M generates a true random number R according to the true random number generator in the matching quantum key fob M (hereinafter referred to as R M , and other similarities omit the Chinese character part as the abbreviation). R M Combining with a specific key ge...
Embodiment 2
[0130] In this embodiment, smart family members download files from the safe cloud, and the smart family members download files from the safe cloud into the following three situations: mobile terminal M downloads files from the safe cloud, home gateway S downloads files from the safe cloud, and home device C Download files from a secure cloud.
[0131] Case 1: The mobile terminal downloads files from the secure cloud.
[0132] Step 2.1.1: The mobile terminal sends a file download request to the security cloud.
[0133] The download file request sent by the mobile terminal to the security cloud is transferred through the quantum communication service station, and the request includes the MID of the mobile terminal.
[0134] Step 2.1.2: The quantum communication service station obtains and transmits files.
[0135] After receiving the request for downloading the file, Security Cloud SS will verify the MID, and if it exists in the legal user list, it will pass the verification....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com