Micro public key encryption method based on finite plum type group decomposition problem
A public key encryption, limited technology, applied to the encryption device with shift register/memory, key distribution, to achieve the effect of resisting attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the examples.
[0028] The present invention proposes a miniature public key encryption method based on the non-commutative decomposition problem of finite Lie group, and the specific description is given below.
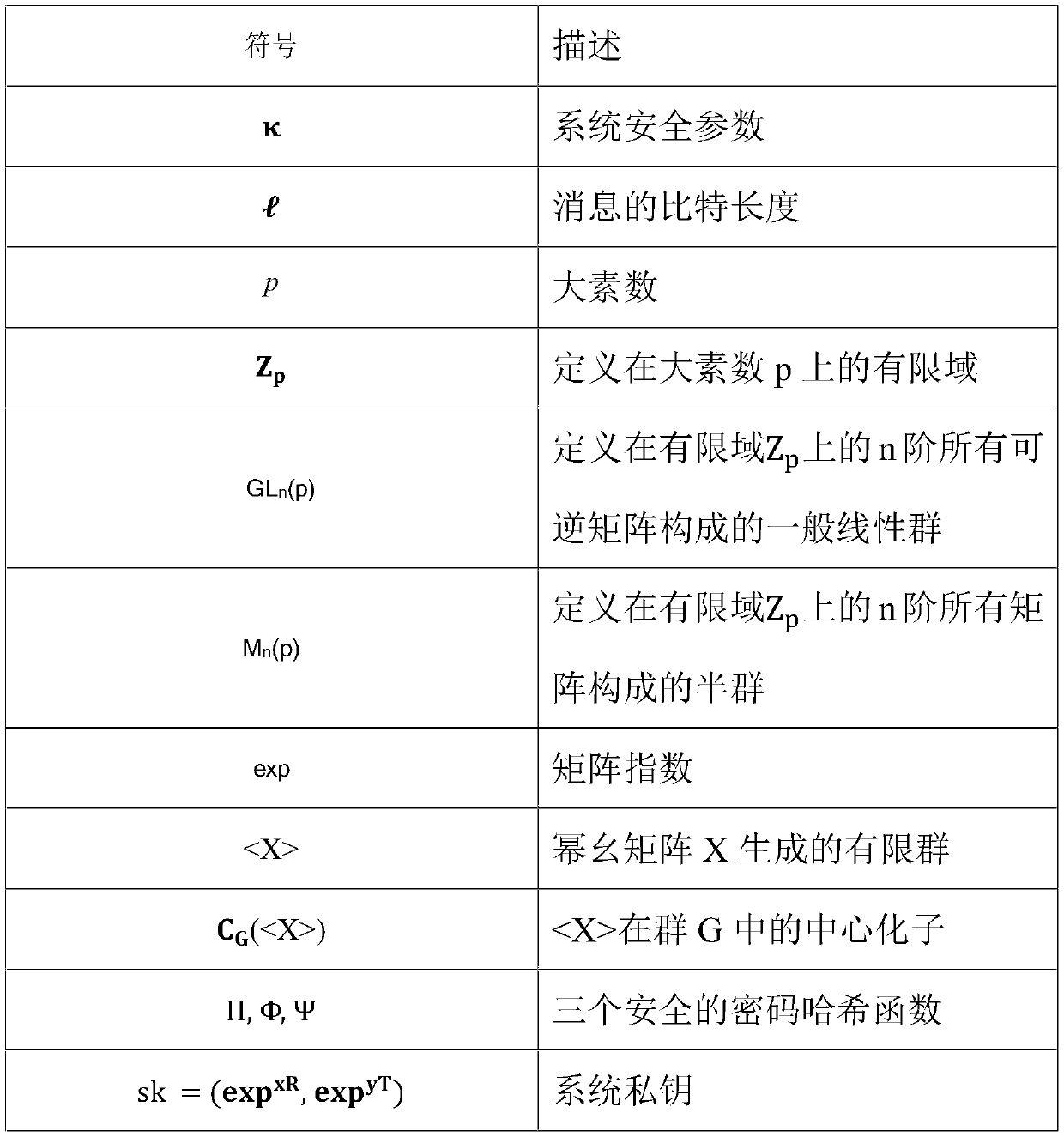
[0029] Symbols and definitions
[0030]
[0031]
[0032] The specific steps of this embodiment are as follows:
[0033] 1. System establishment: input security parameter k, KGC (Key Generation Center) selects a large prime number p, Z p Two random elements x and y and two nilpotent matrices R, T∈M=Mn(p), satisfy C G (R) = R and C G (T)=T, calculate the private key of user B: sk=(exp xR , exp yT ); define three cryptographic hash functions as: Π: {0, 1} l → Z p × Z p , Φ: G → {0, 1} l , Ψ: G×G → {0, 1} l , l is the bit length of the message, calculate the public key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com