Automatic intelligent mining method for network security vulnerabilities of broadcast television key information infrastructure
A technology of infrastructure network and key information, applied in the field of automatic intelligent mining of network security vulnerabilities of key information infrastructure of radio and television, which can solve problems such as misconfiguration, insecure default setting applications, and leakage of sensitive information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
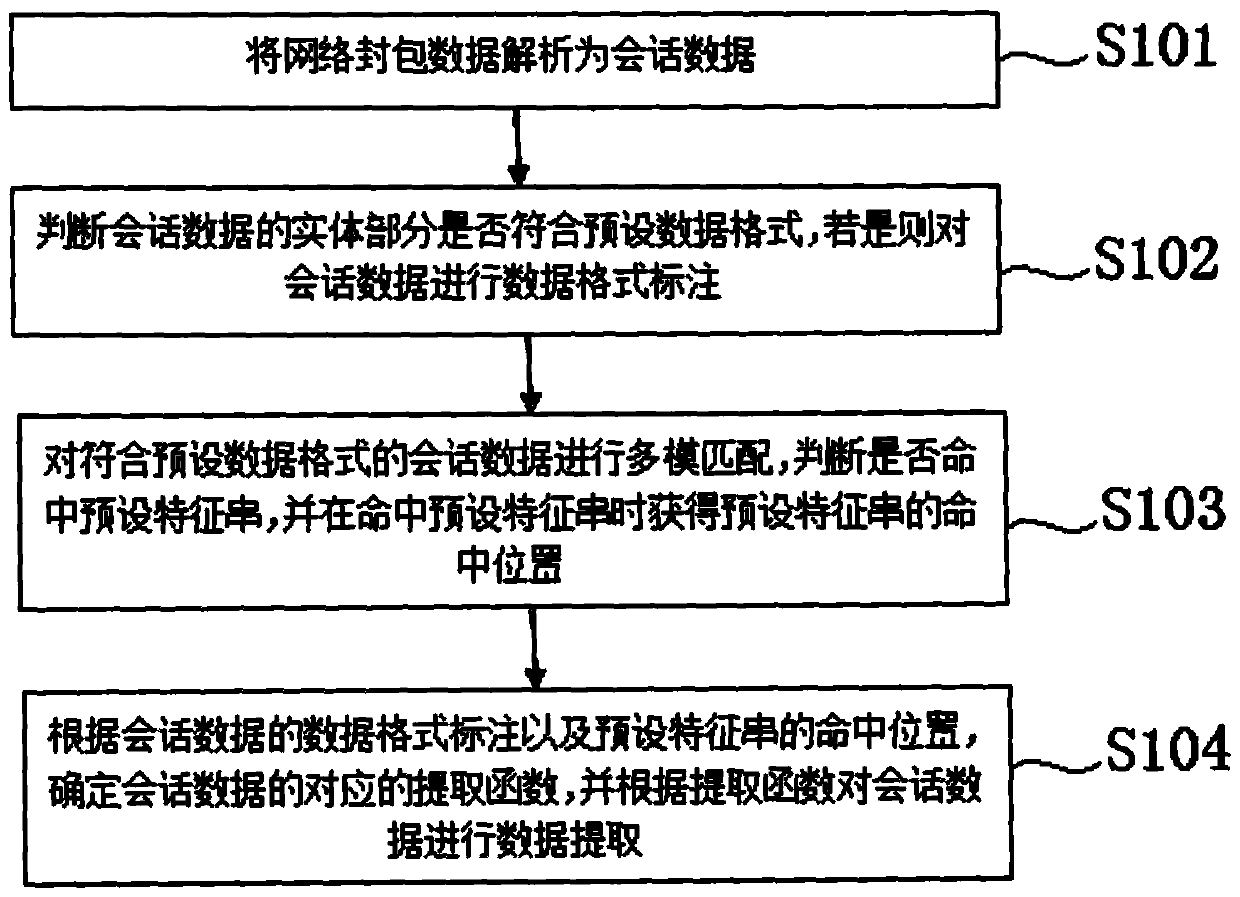
[0021] Such as figure 1 As shown, the present invention is an automatic intelligent mining method for network security loopholes in key information infrastructure of radio and television, comprising the following steps,
[0022] Step S101: Parse the network packet data into session data. In this step, the data communicated by various protocols can be extracted, and the following takes Hyper Text Transfer Protocol (Hyper Text Transfer Protocol, HTTP) data as an example to describe in detail. Firstly, the network packet data obtained from the data source is parsed into session data in text format. For HTTP protocol data, the HTTP protocol stack is used to parse it into HTTPPOST session data. The parsed session data includes HTTP header and HTTP entity part. To parse and restore HTTP POST session data according to the HTTP protocol stack, it is necessary to first build a Transmission Control Protocol (TCP) stream, and then parse according to the HTTP session. For example, use ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com