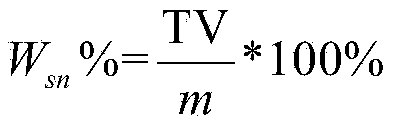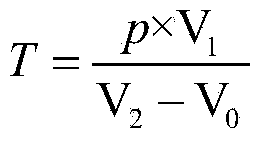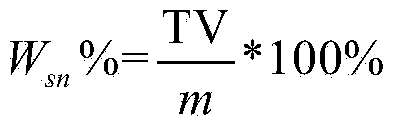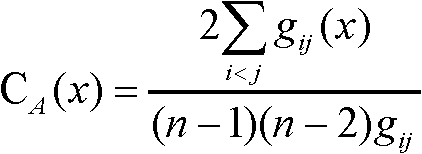Patents
Literature
31results about How to "Thorough analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Cytotherapeutics, cytotherapeutic units and methods for treatments using them
ActiveUS20070092497A1Uniform and effective therapeutic applicationMinimal numberBiocideSenses disorderAssayTreatment use
The present invention provides cytotherapeutic units comprising predetermined numbers of selected types of potent cells. Assurance of the nature and identities of such cells is achieved through assay and certification of said numbers and identities. Therapeutic modalities are provided. Libraries of cell preparations with assayed and preferably certified populations are preferred and the preparation of cell preparations tailored to specific patients or disease states are provided.
Owner:CELULARITY INC
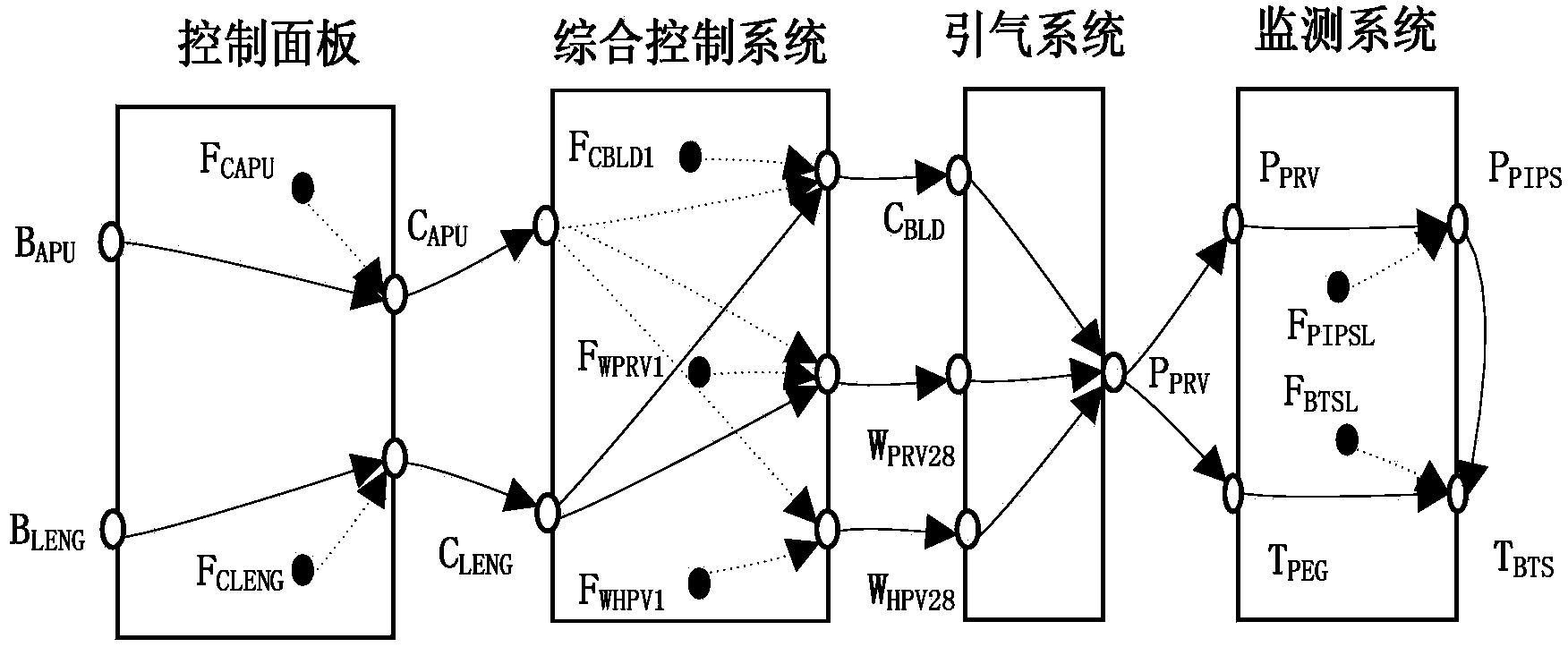
System and method for sensing torque on a rotating shaft
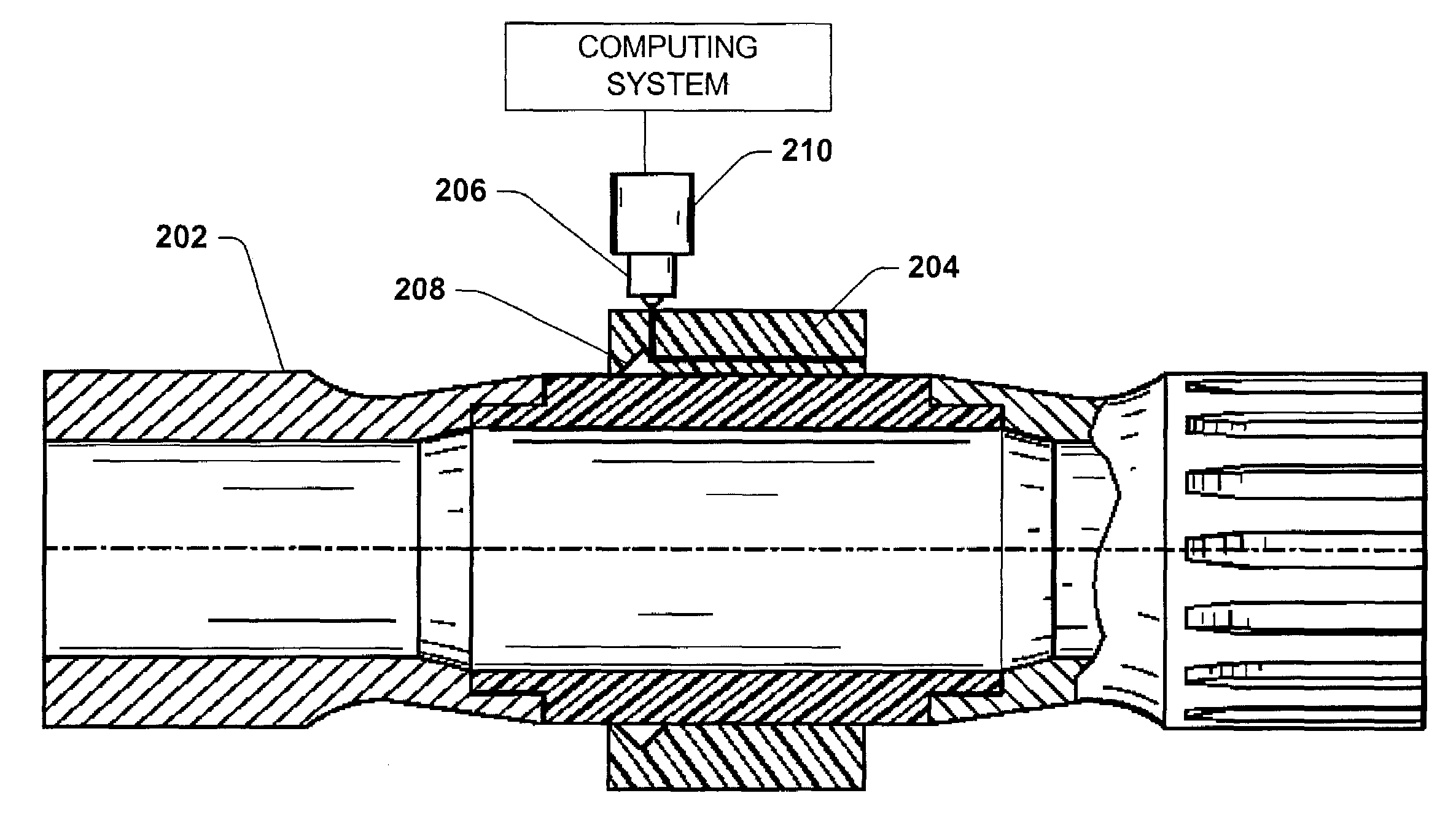
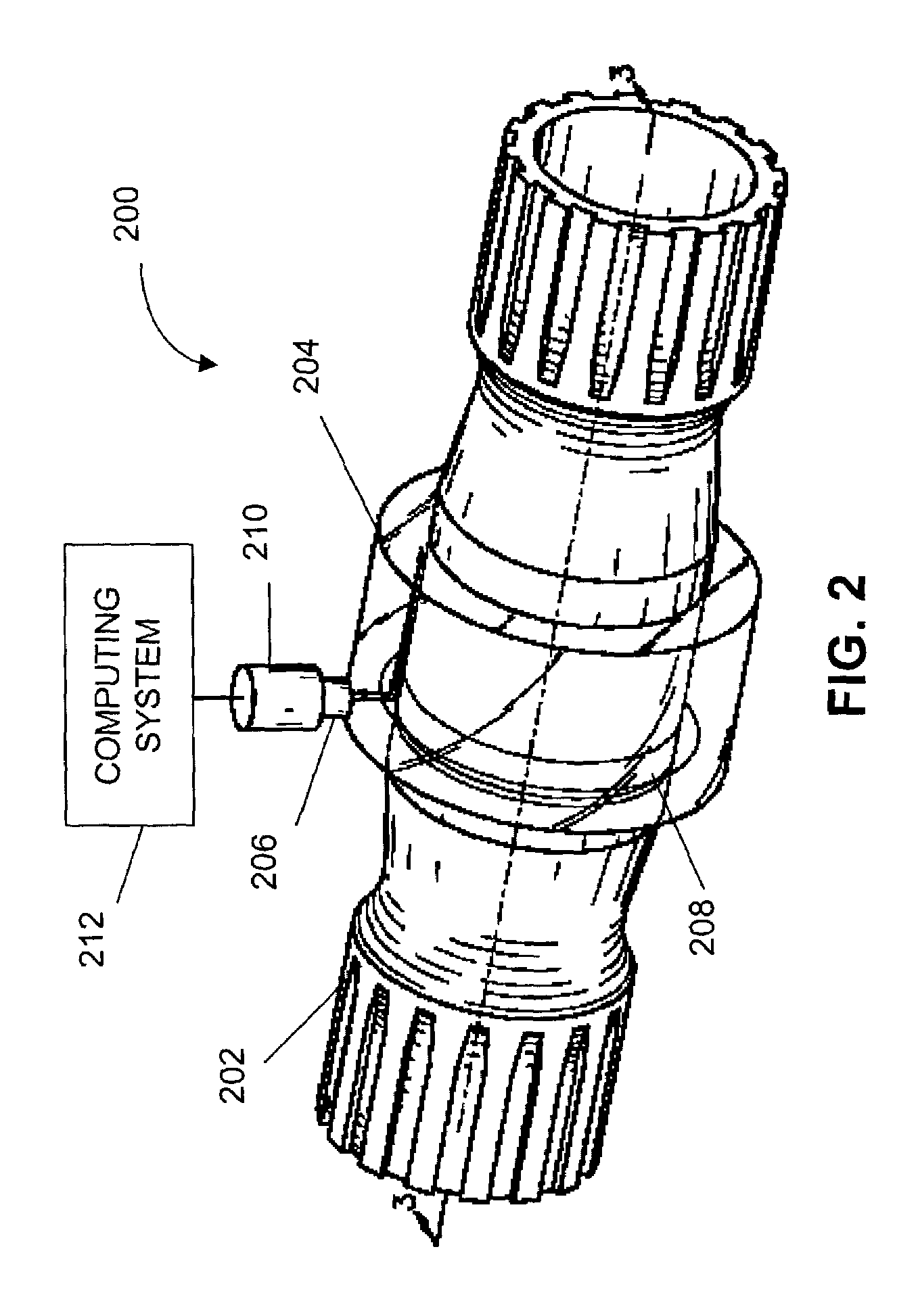
InactiveUS6948381B1Effective methodLow costForce measurement by measuring optical property variationWork measurementComputing systemsEngineering
A system and method relating to the measuring of torque in a rotating shaft is provided. An optical torque sensing system comprises a rotating shaft, wherein a sleeve of photo-elastic material overlays a portion of the shaft. A light emitting component delivers light into the photo-elastic material, wherein the light delivered by the light emitting component is directed through the photo-elastic material along an axis of the rotating shaft. A capturing component captures the light that exits the photo-elastic material. The exiting light comprises fringe pattern data, and a computing system computes torsion strain of the shaft based at least in part on the fringe pattern information.
Owner:ROCKWELL AUTOMATION TECH
Web vulnerability protection method and apparatus
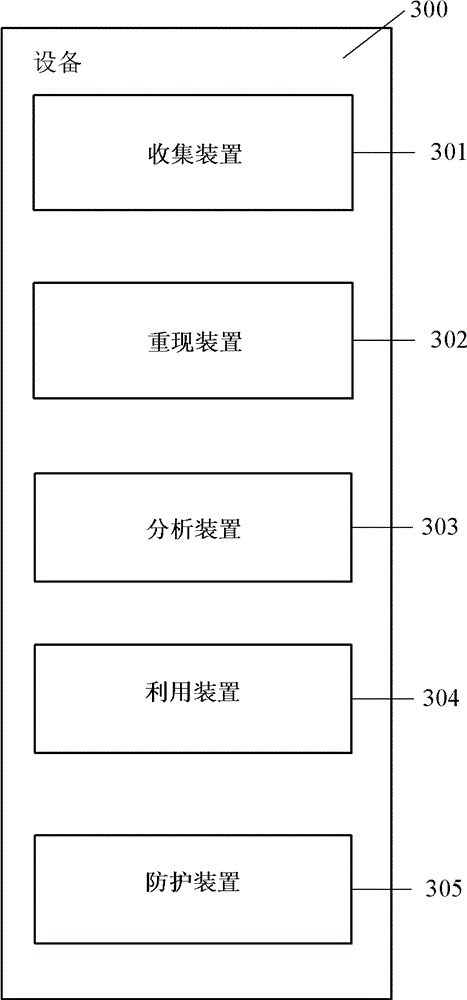
InactiveCN104065645AImprove timelinessImprove accuracyPlatform integrity maintainanceTransmissionData miningComputer science
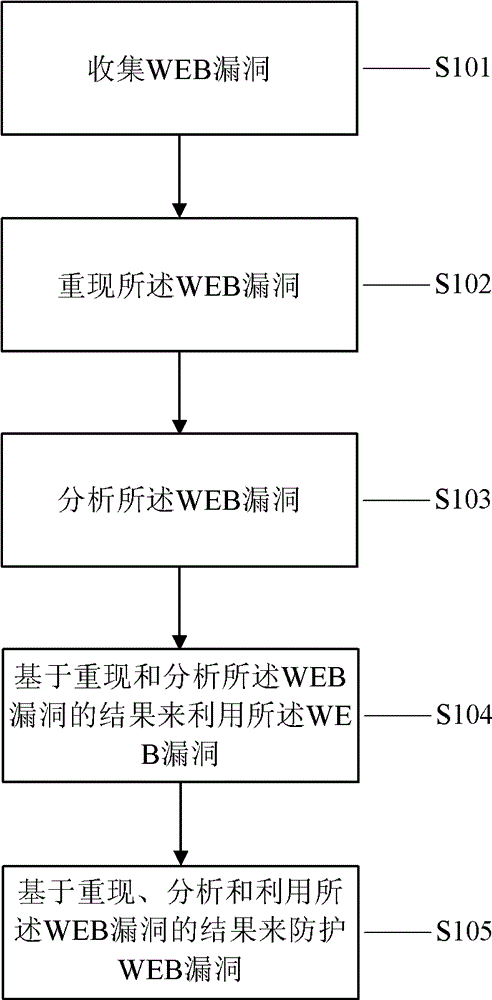
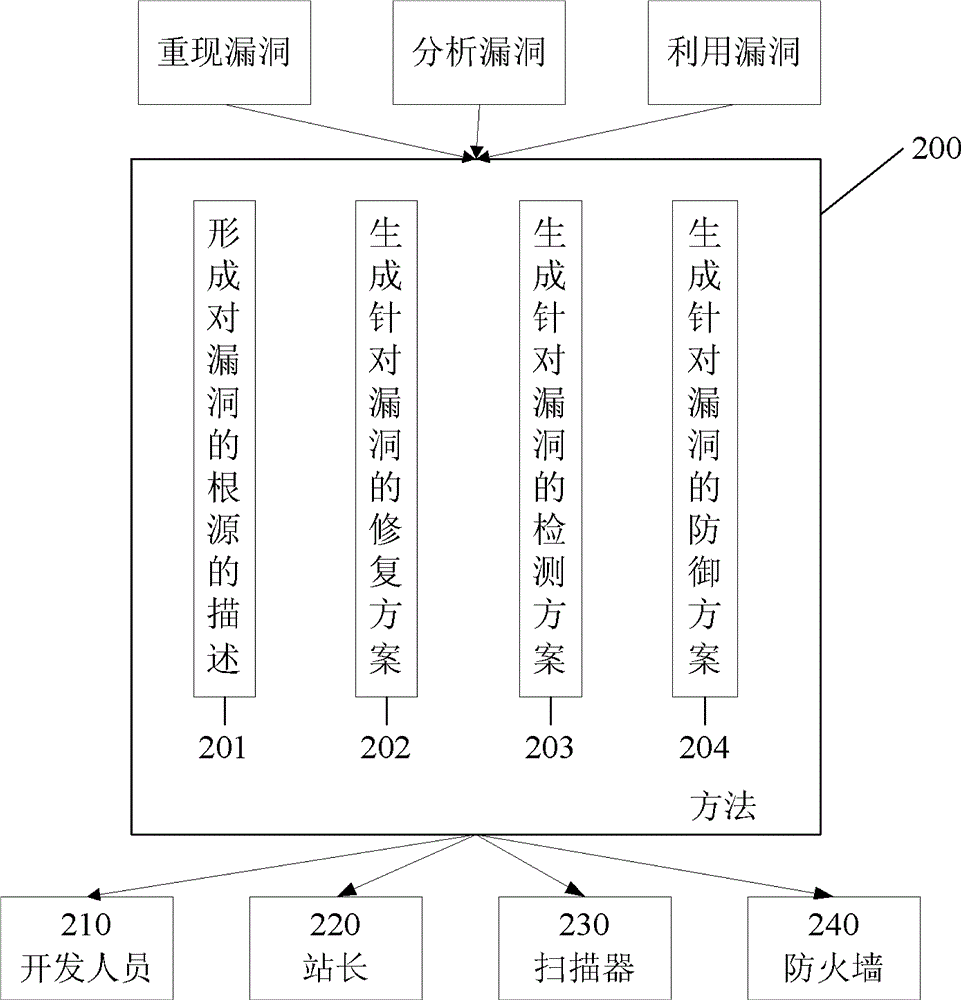
The invention discloses a web vulnerability protection method and apparatus. The web vulnerability protection method includes collecting web vulnerabilities; reproducing the web vulnerabilities; analyzing the web vulnerabilities; utilizing the web vulnerabilities according to the reproduction and analysis results of the web vulnerabilities; protecting the web vulnerabilities according to the reproduction, analysis and utilization results of the web vulnerabilities.
Owner:BEIJING KNOWNSEC INFORMATION TECH
Complex network clustering method based on key influence of nodes
InactiveCN102571954AReflect the clustering processThorough analysisTransmissionFunctional networkComputer science
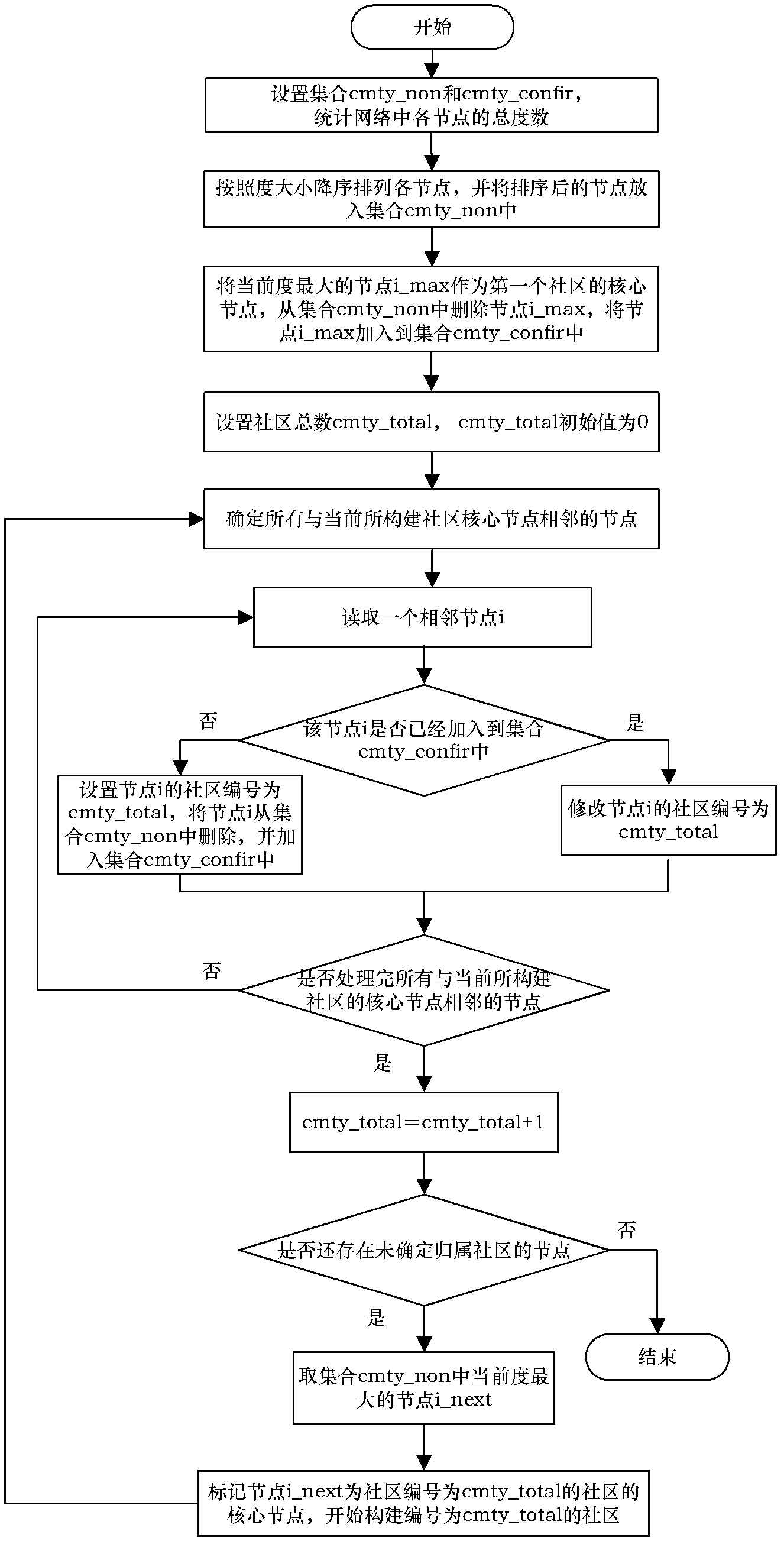
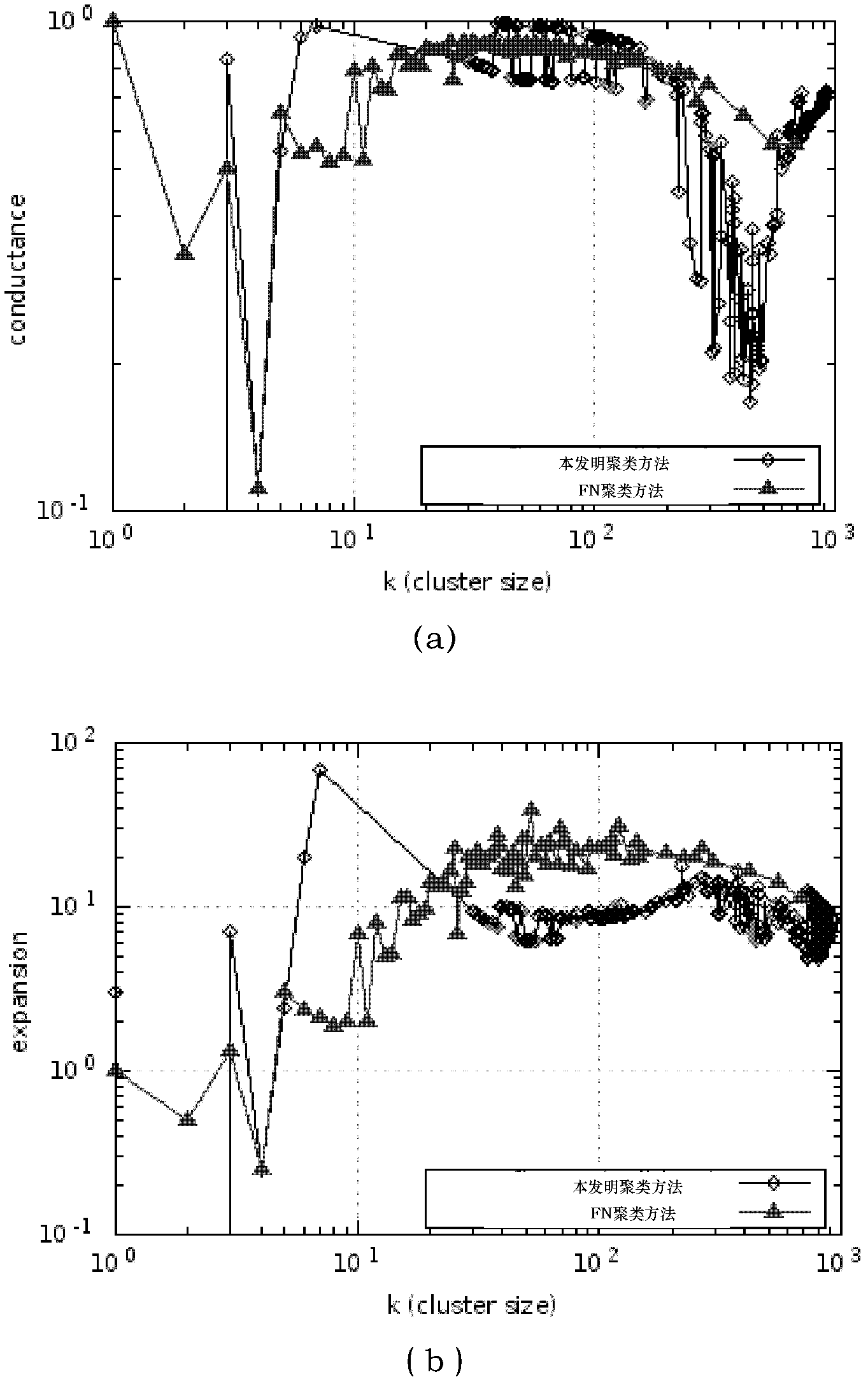
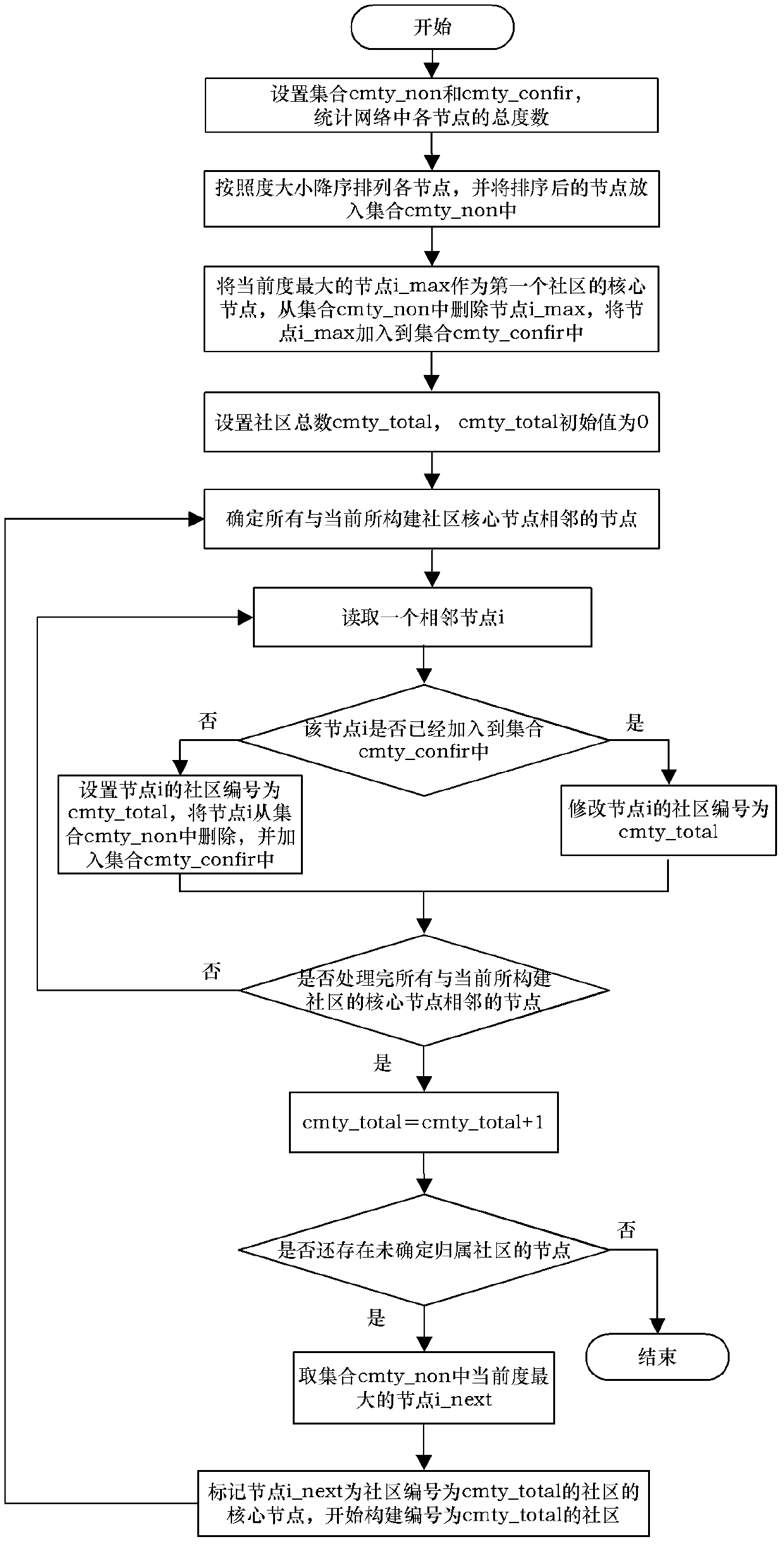
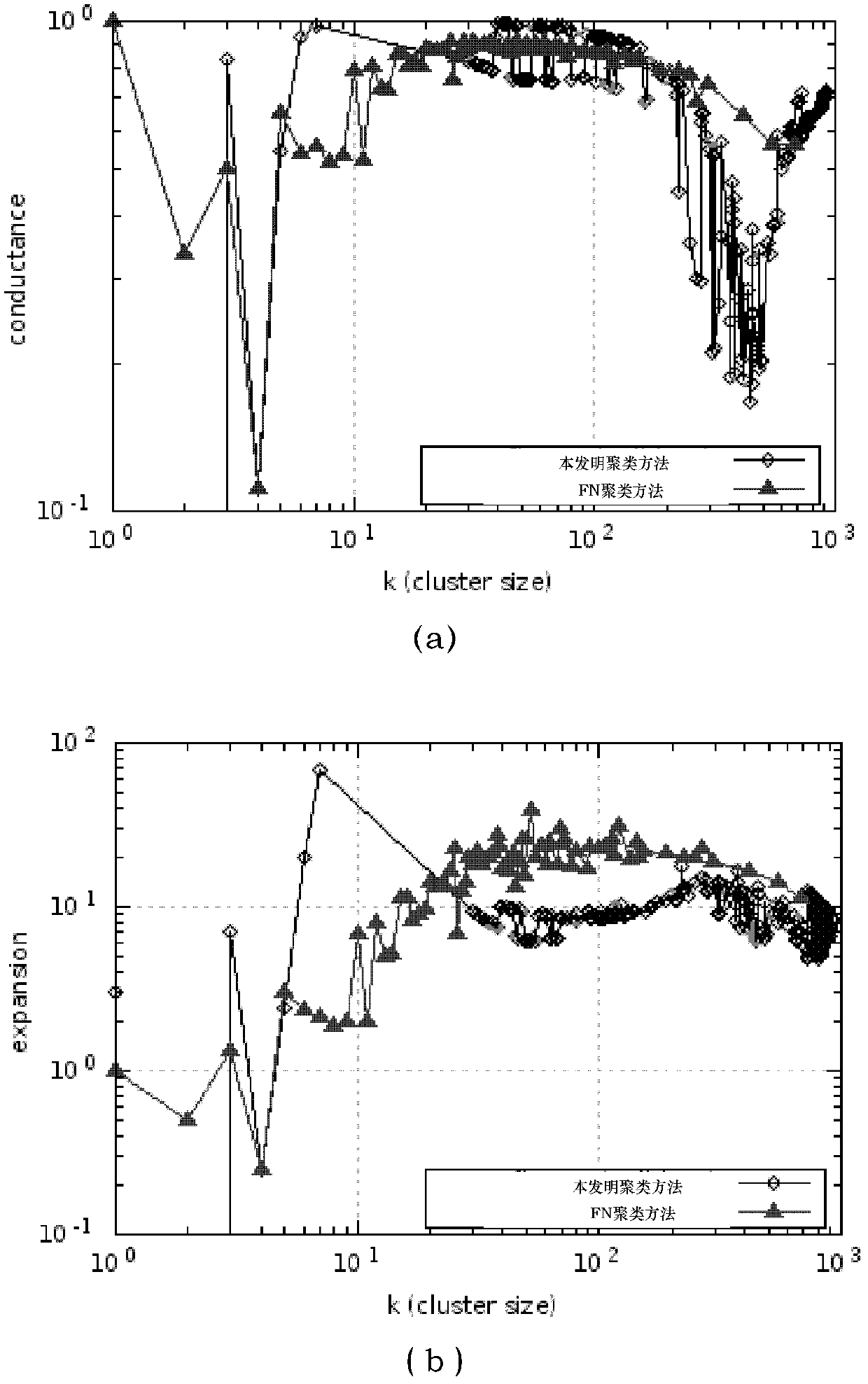
The invention discloses a complex network clustering method based on the key influence of nodes, which comprises the following steps: sequencing nodes in a complex network according to the size of degree, wherein the subordinate community of each initial node is not determined; taking a node (the subordinate community thereof is not determined) with the largest degree as a core node of a community; beginning to build the community; determining the subordinate community of a node adjacent to the core node; after the community is completely built, taking a node (the subordinate community thereof is not determined) with the largest degree as a core node of a community; beginning to build a community; and repeatedly performing a process of community building until the subordinate communities of all nodes in the network are determined, thereby obtaining a final network cluster structure. By using the method disclosed by the invention, a clustering precision in the complex network is superior to that obtained by using a FN (functional network) clustering method; and the method plays a positive role in carrying out fine-grained reveal on a real cluster structure of the complex network.
Owner:臻睿(北京)信息技术有限公司
Production data management information system
InactiveCN103745311AImprove real-time performanceImprove effectivenessResourcesManufacturing computing systemsWork periodProgram planning
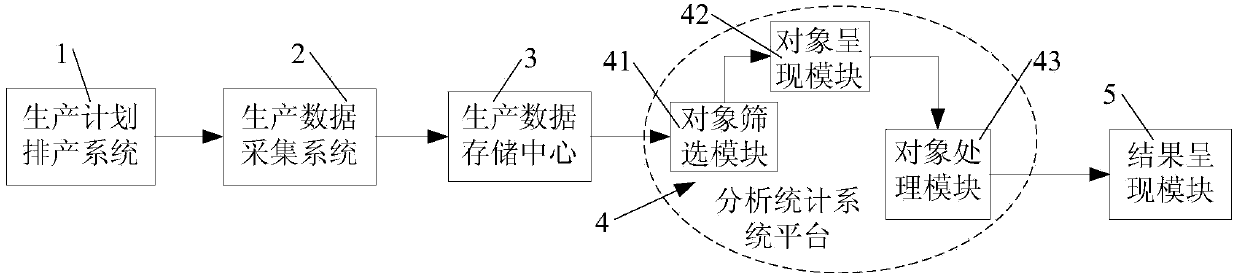
The invention discloses a production data management information system. The system comprises a production plan scheduling system, a production data acquisition system, a production data storage center, an analytical and statistical system platform and a result presentation module. The production data management information system utilizes the production plan scheduling system to schedule production plans, utilizes the production data acquisition system to product according to the production plans, records actual production information and stores actual production information in the production data storage center, and then, utilizes the analytical and statistical system platform to process the actual production information according to a preset strategy to obtain a production statement, thus, the statistical efficiency of production efficiency can be improved, production efficiency analysis is relatively thorough, a large amount of working time of plan management personnel used in paper file statistics of production efficiency is released, the efficiency of generating the production statement is high, the work efficiency of plan management personnel can also be improved, in addition, the production statement is presented through the result presentation module in the form of characters or graphs, and the readability is high.
Owner:天通精电新科技有限公司
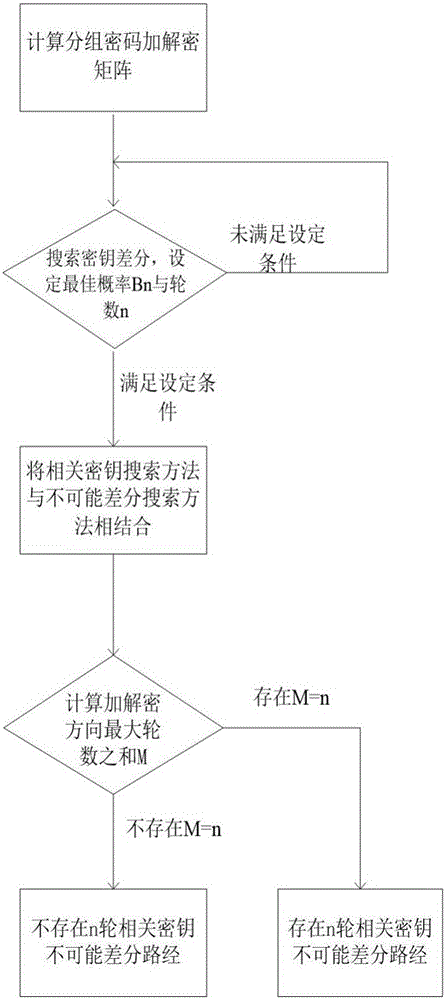
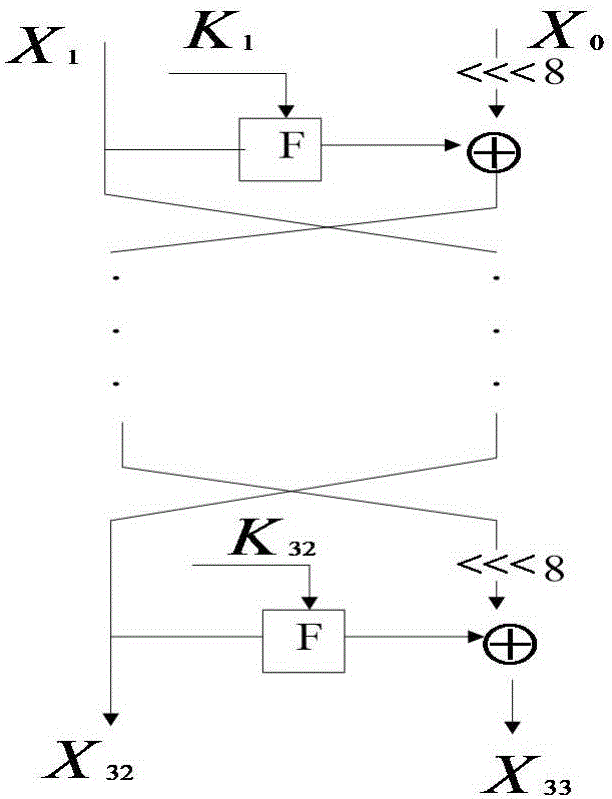
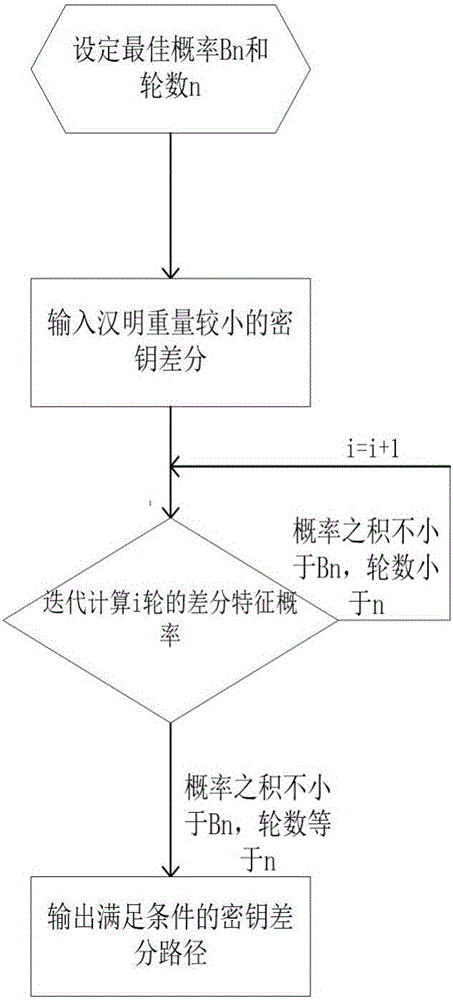
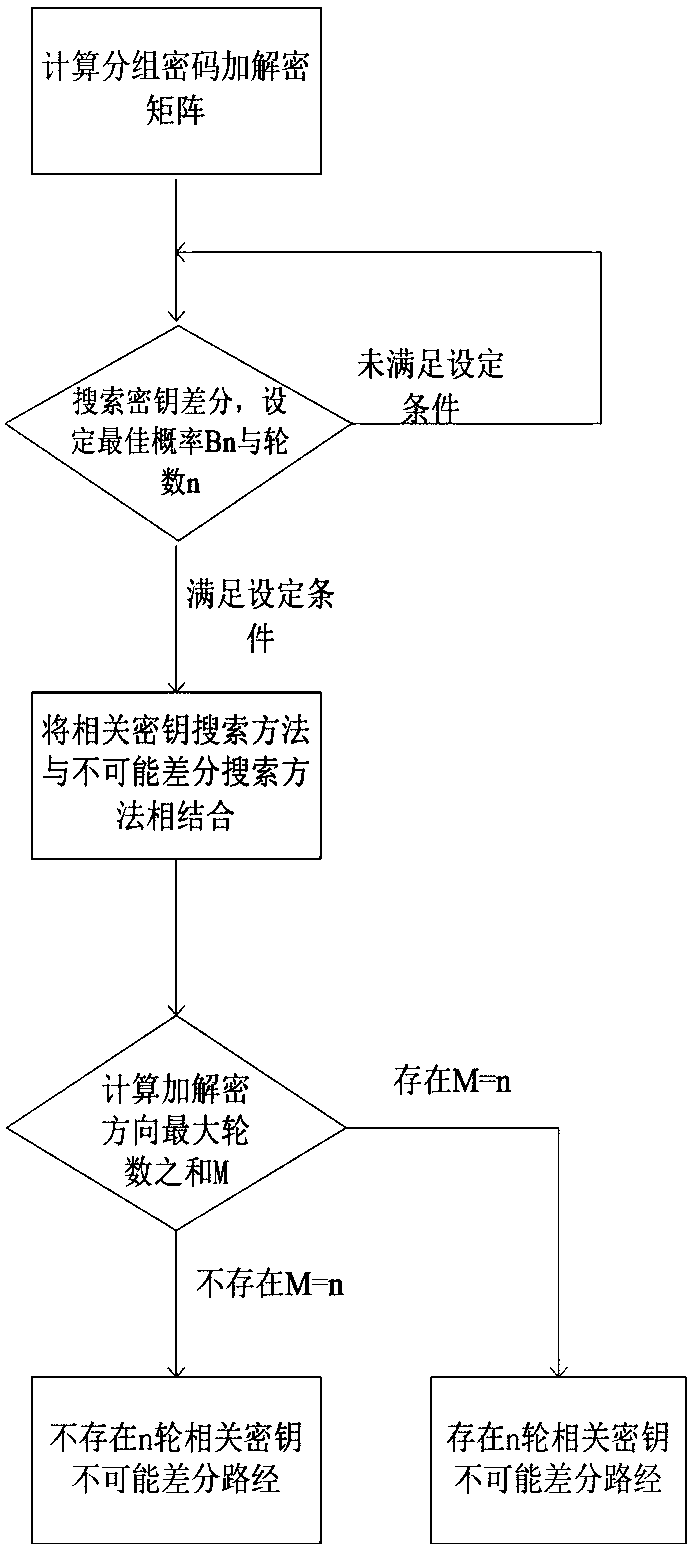
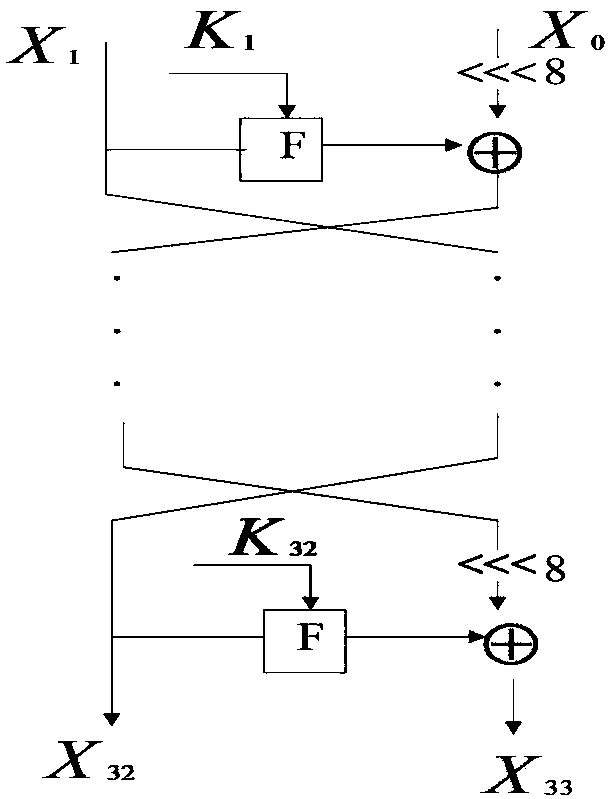
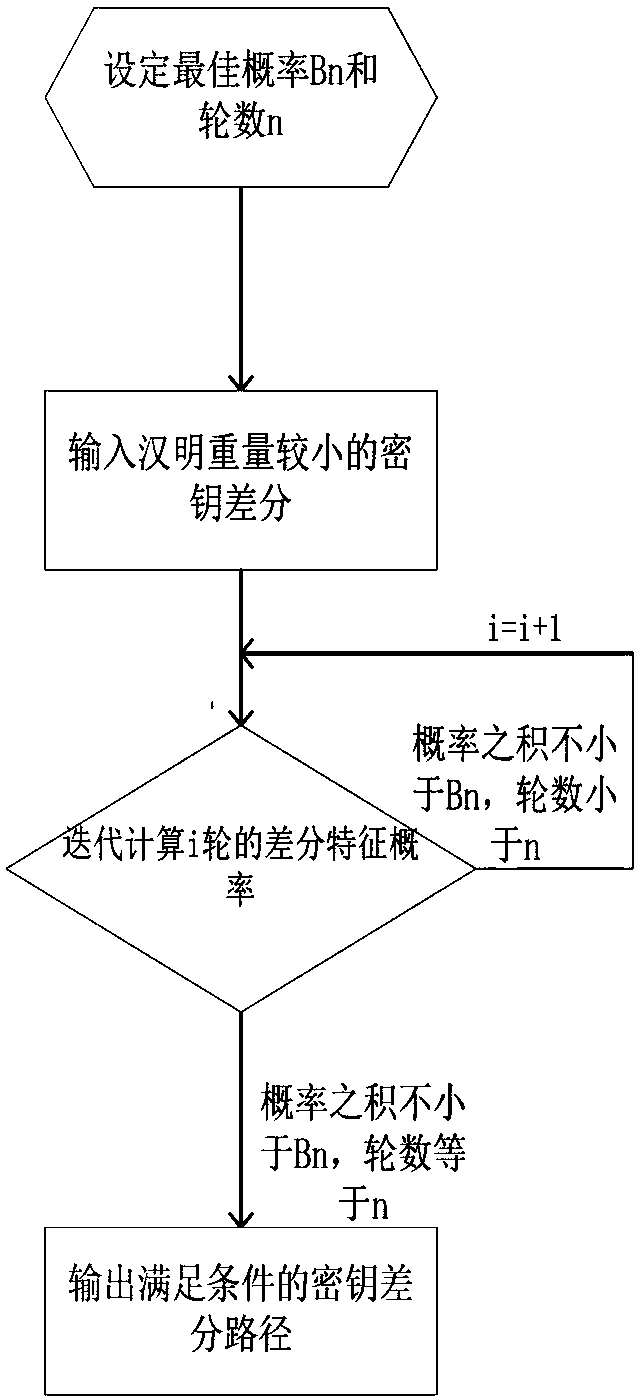
Searching method for impossible differential path of related key of block cipher
ActiveCN106027226ASolve the problem of findingIn-depth analysisEncryption apparatus with shift registers/memoriesRelated-key attackTheoretical computer science
The invention discloses a searching method for an impossible differential path of a related key of a block cipher. As an impossible differential attack method and a related key attack method are combined, the problems of automatic searching of the impossible differential path of the related key and searching of a longest analysis path in cryptanalysis are solved, and deeper and more thorough analysis for a cryptographic algorithm can be carried out. According to the searching method for the impossible differential path of the related key of the block cipher, the method for searching the impossible differential path of the related key is upgraded from the traditional manual analysis to computer automatic searching, the disadvantages that an existing manual analysis method is fussy and error-prone when being used for analyzing the cryptographic algorithm are avoided, the maximum length of the impossible differential path of the related key of the block cipher algorithm can be calculated rapidly and accurately, and the cryptanalysis efficiency is improved. The searching method for the impossible differential path of the related key of the block cipher realizes transformation of the cryptographic algorithm from a non-generalized Feistel structure to a generalized Feistel structure, can be widely applied to automatic search of the impossible differential paths of related keys of various cryptographic algorithms in different structures.
Owner:XIDIAN UNIV
Method and device for researching chlorophyll fluorescence characteristic of Jiuzhaigou Valley aquatic plants
InactiveCN106770142AImprove working environmentImprove work efficiencyFluorescence/phosphorescenceStudy methodsBiology
The invention relates to a method and a device for researching the chlorophyll fluorescence characteristic of Jiuzhaigou Valley aquatic plants, relates to research on photosynthesis characteristic of aquatic plants and relation between the aquatic plants and a water environment, and belongs to G01 type. The device consists of a pulse modulation chlorophyll luminoscope capable of being controlled remotely and an electric remote control catamaran with an underwater robot. The method comprises four parts of chlorophyll fluorescence characteristic measurement, photosynthetic active radiation intensity and water temperature measurement, chlorophyll content measurement and data analysis. By the device and the method, remote real-time sampling, monitoring and experiment are realized, the working environment of scientific research personnel is greatly improved, and the working efficiency is improved; and the device is maneuverable, data is detailed and accurate, the method is reasonable, analysis is complete, graphs are attractive, and great scientific research theoretical and practical significance is achieved.
Owner:成都学院
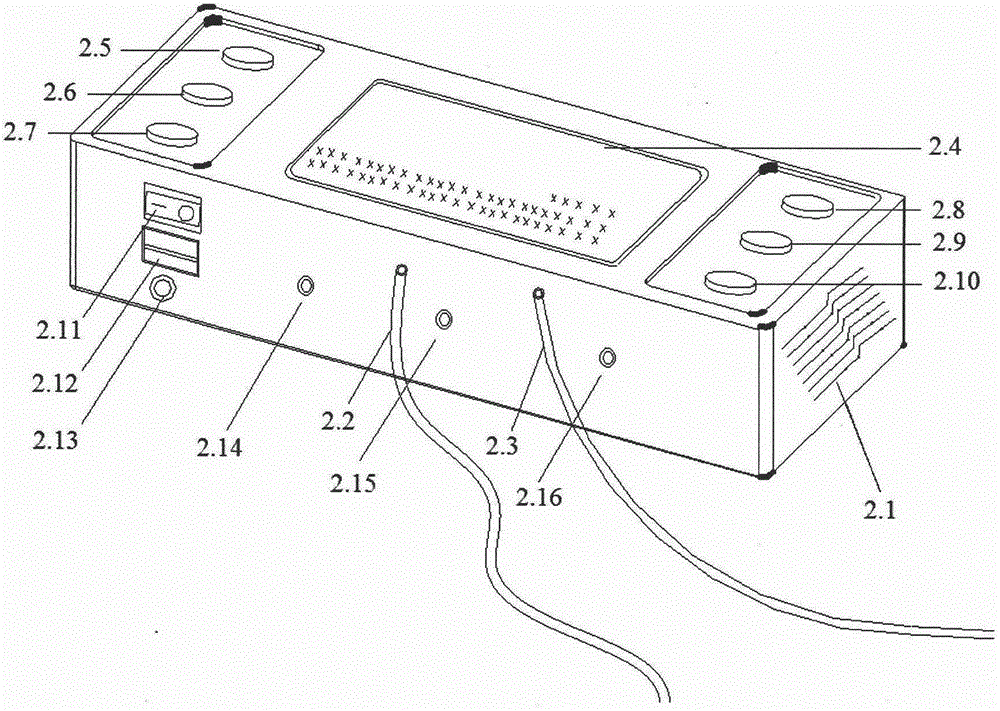
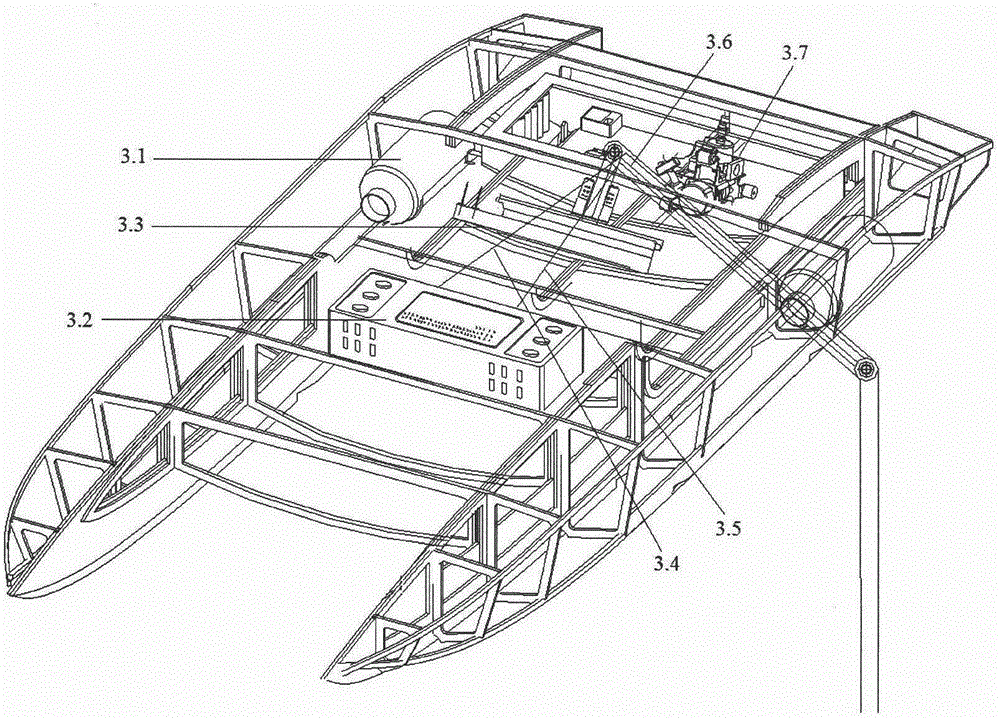
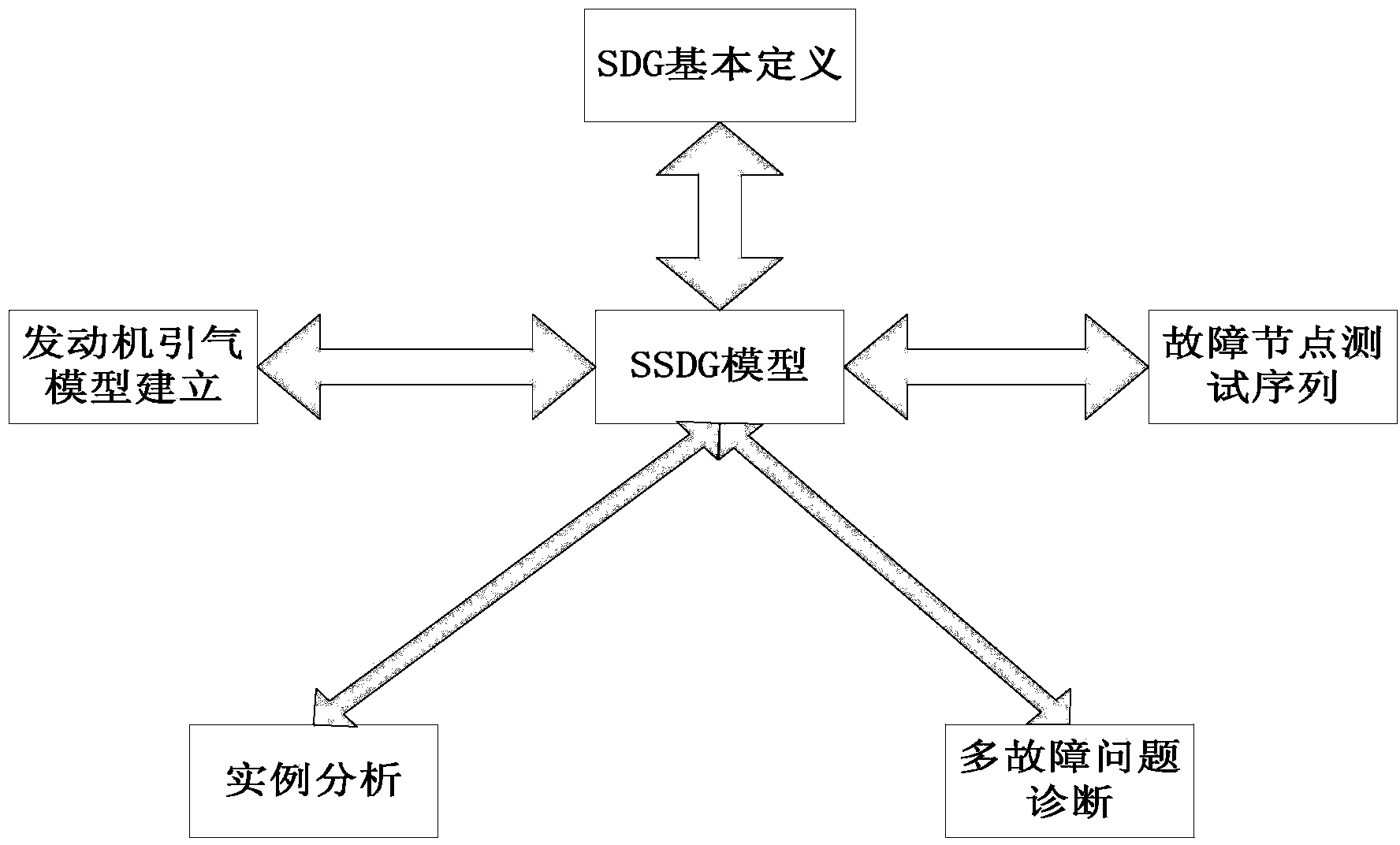
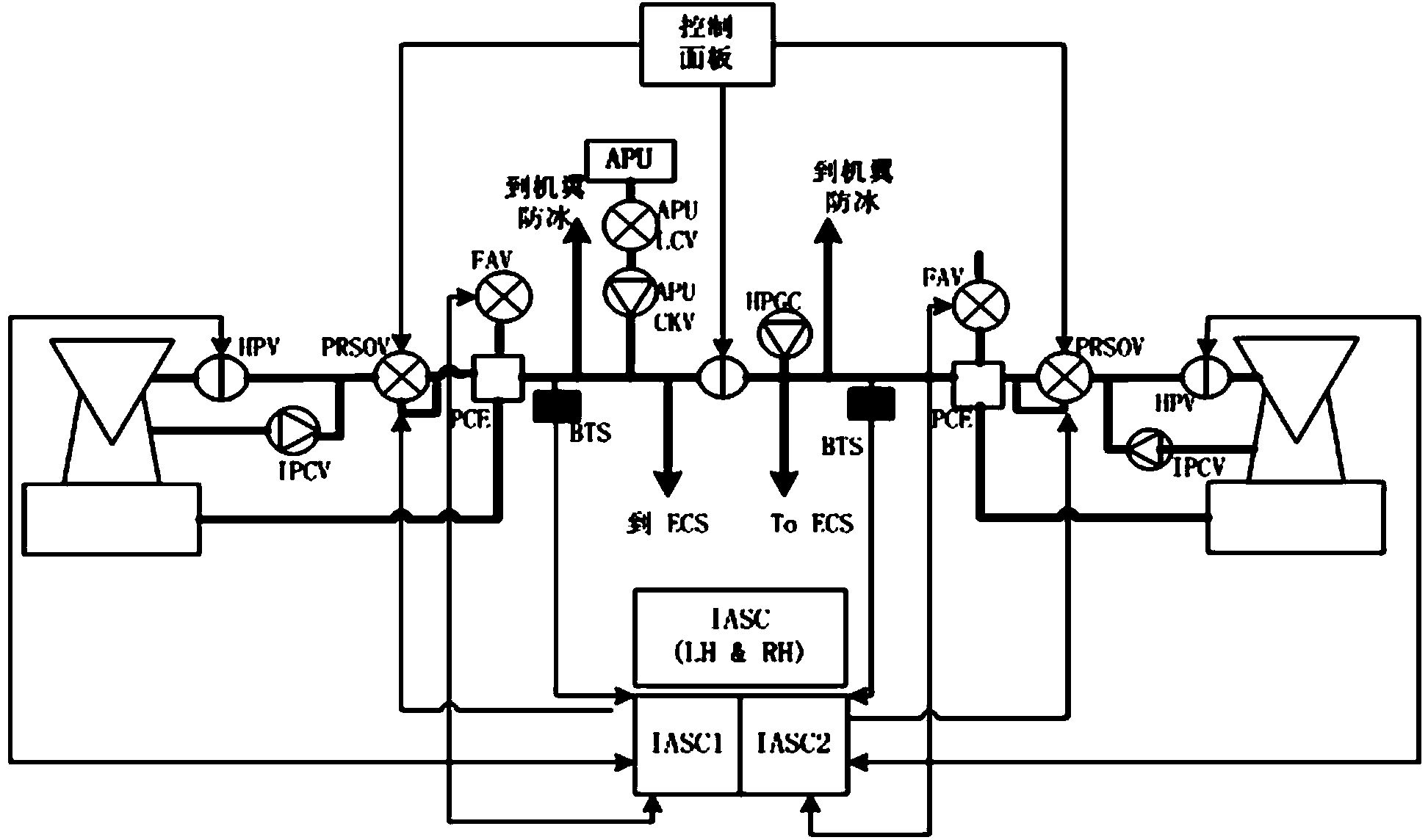
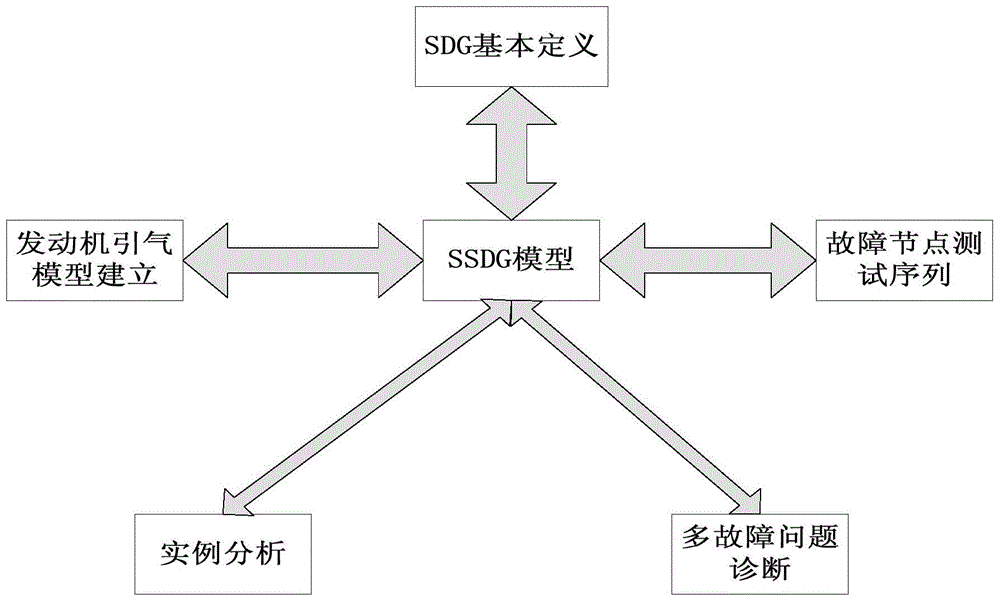
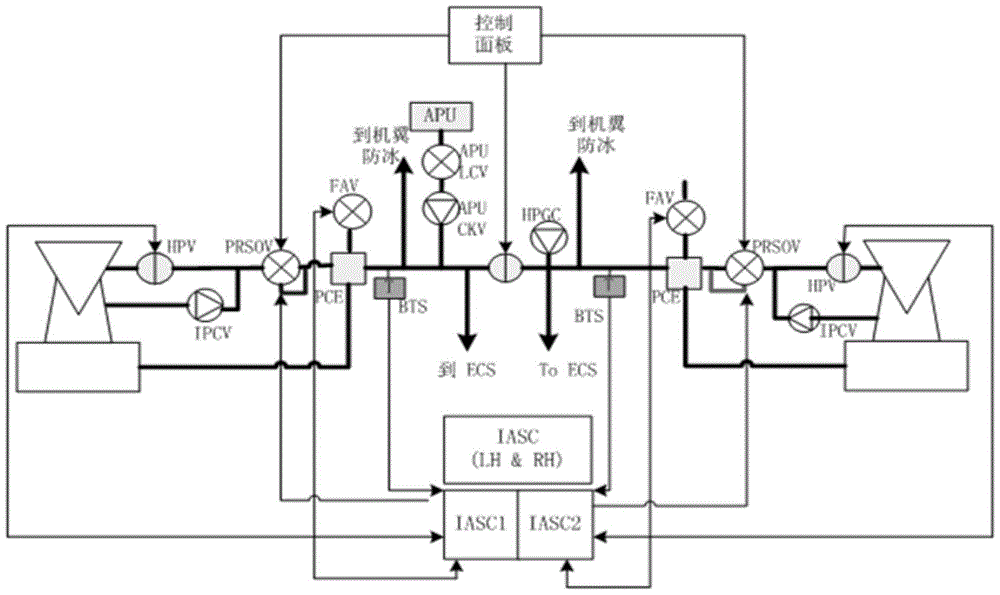
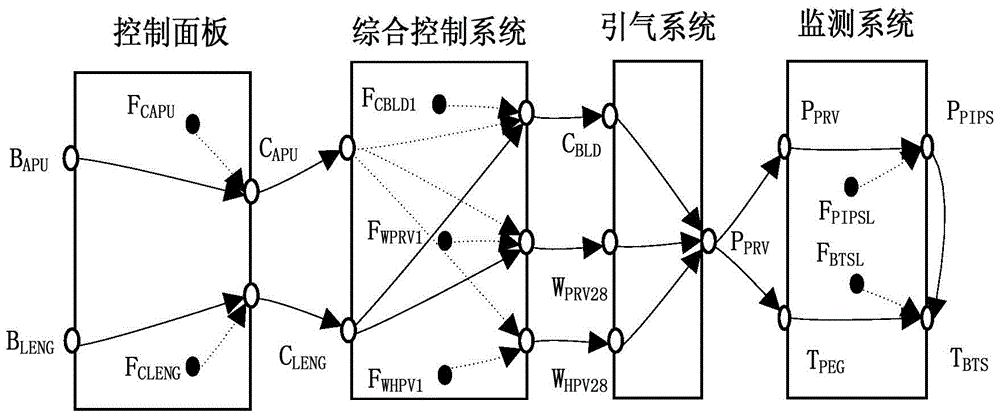
Multi-fault diagnosis method based on improved SDG
InactiveCN104050371AThorough analysisMultiple fault diagnosis is accurateSpecial data processing applicationsSequence analysisDiagnosis methods
The invention discloses a multi-fault diagnosis method based on an improved SDG, and belongs to the field of fault problem diagnosis. The multi-fault diagnosis method based on the improved SDG mainly comprises the step of establishing an engine entraining model, the step of establishing an SSDG model, the step of diagnosing a multi-fault problem, and the step of analyzing a fault node measuring sequence. According to the multi-fault diagnosis method, the multi-source fault source searching detection can be carried out, and the fault diagnosis can be more accurate. The fault of a large system is analyzed on the background of manufacturing a large airplane, and the fault source is found out. According to the multi-fault diagnosis method based on the improved SDG, the fault diagnosis is carried out with the SDG method, the method can carry out the analysis more thoroughly compared with an event tree method and an accident tree method, the defect that according to a traditional SDG method, only the single-fault source can be found out is overcome, the multi-fault source searching can be carried out with the multi-fault diagnosis method, and the fault diagnosis is more accurate.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
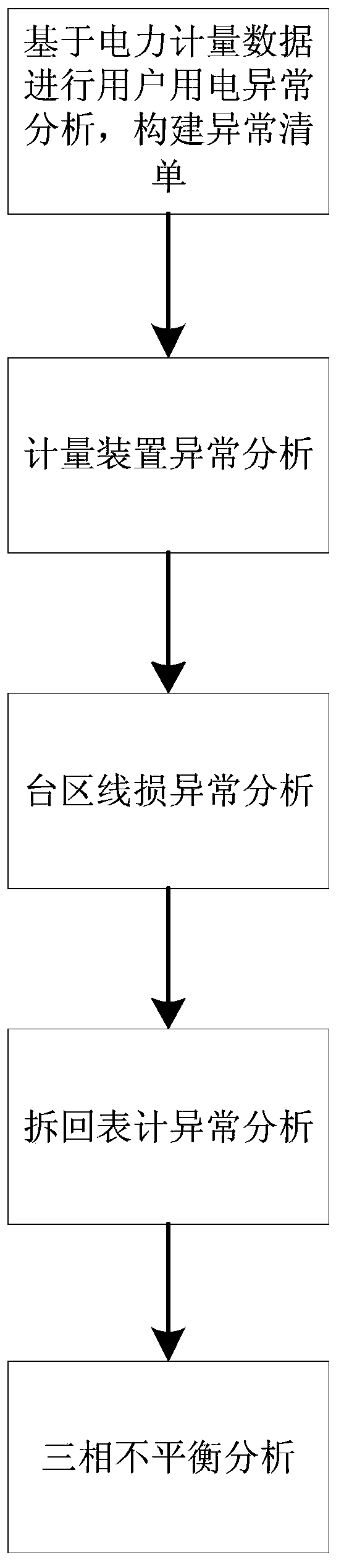
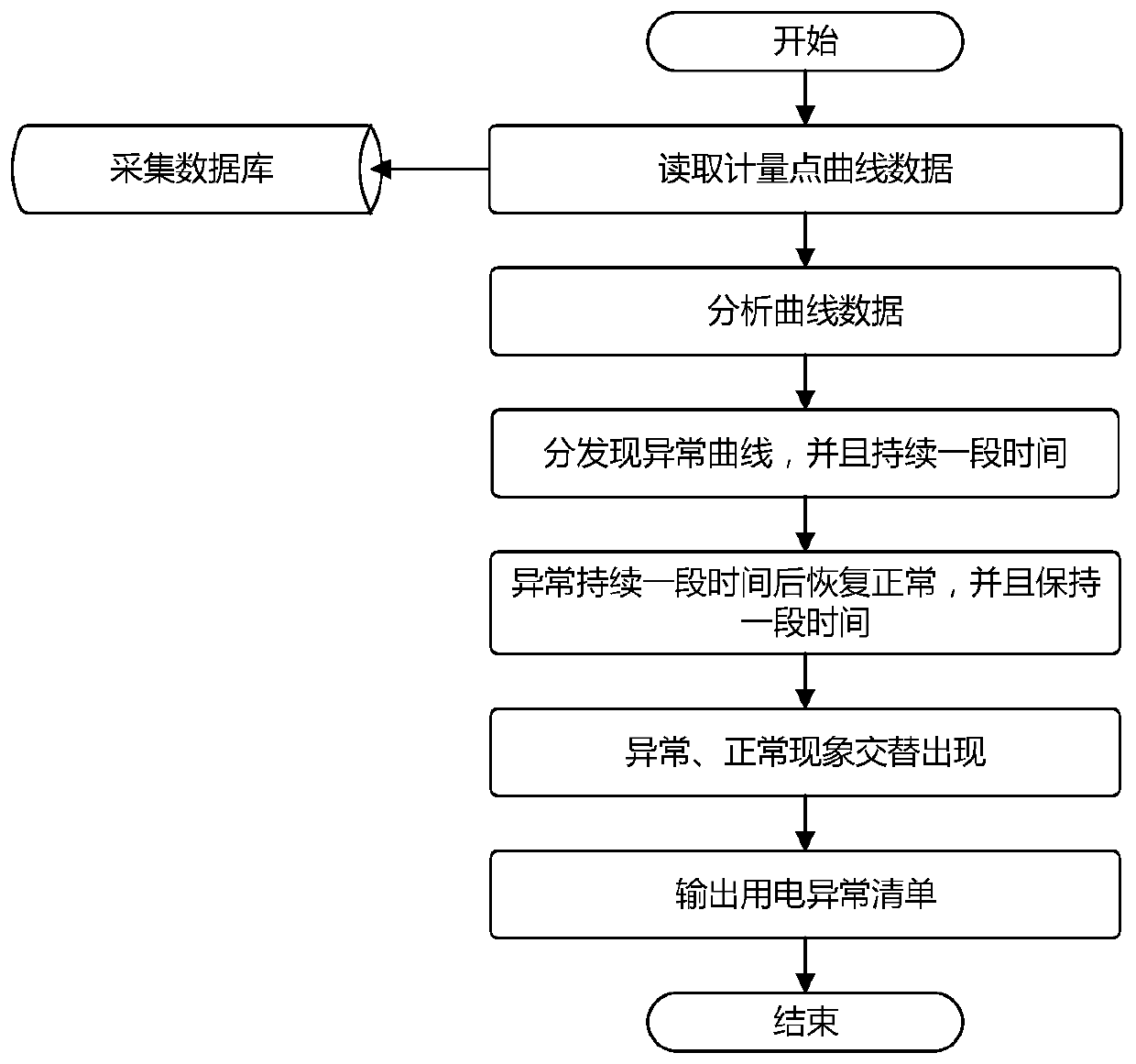
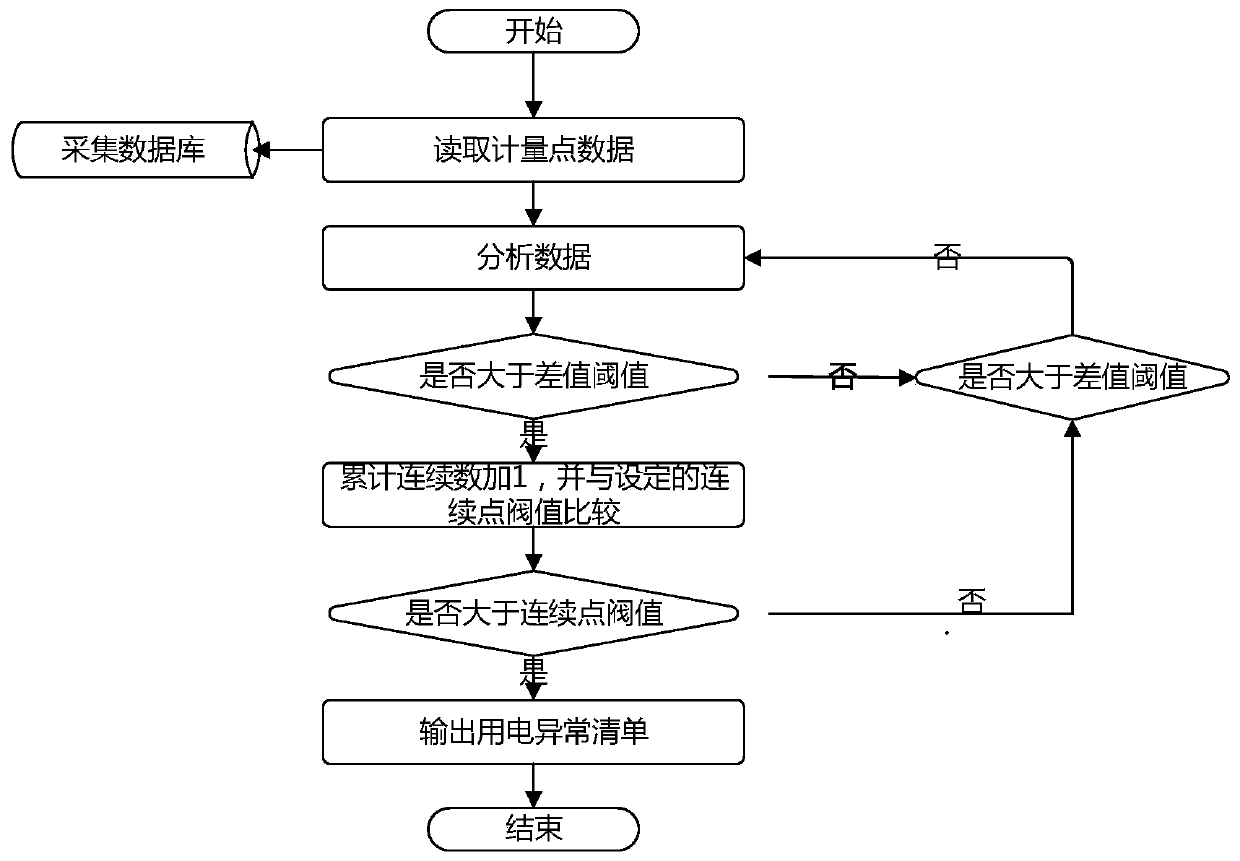
Power consumption abnormity analysis method and system for large power consumers
The invention discloses a power consumption abnormality analysis method for a large power consumer, and the method comprises the steps: carrying out the user power consumption abnormality analysis based on power measurement data, and constructing an abnormality list; and performing metering device anomaly analysis, transformer area line loss anomaly analysis, meter dismounting anomaly analysis andthree-phase imbalance analysis on elements in the anomaly list to obtain a user anomaly result list. The invention further discloses a corresponding system. According to the invention, the exceptionlist is constructed based on the metering data, metering device exception analysis, transformer area line loss exception analysis, meter dismounting exception analysis and three-phase imbalance analysis are carried out on all elements in the exception list, exception results of all users in the exception list are obtained, and compared with a traditional analysis method, the method does not dependon personnel experience, and analysis is more thorough.
Owner:JIANGSU FRONTIER ELECTRIC TECH
Method for determining content of tin in tungsten concentrate
InactiveCN104215634AReduce lossesSolve insensitive problemsMaterial analysis by observing effect on chemical indicatorPreparing sample for investigationPotassium iodineMaterials science
The invention discloses a method for determining the content of tin in a tungsten concentrate. The method comprises the following steps: smelting a tungsten concentrate sample through a composite smelting agent consisting of anhydrous borax, boric acid and zinc powder, leaching through thick hydrochloric acid, oxidizing leachate, filtering and separating to obtain a tin-containing solution, reducing the tin-containing solution through iron powder, titrating a reaction solution to an endpoint through a potassium iodate standard solution by taking a starch-potassium iodide solution as an indicator, and calculating the mass percentage of tin in the tungsten concentrate according to the titration result. The determination method is simple in process, low in cost, and capable of fast and accurately determining the content of tin in the tungsten concentrate and overcoming the defects of conventional methods for determining tin in the tungsten concentrate in the prior art, for instance, a potassium iodate volumetric method is complicated in determination process and inaccurate in determination, and an atomic absorption spectrometry method needs expensive advanced instruments and is large in testing cost.
Owner:HUNAN NONFERROUS METALS XINTIANLING WOLFRAM MINE
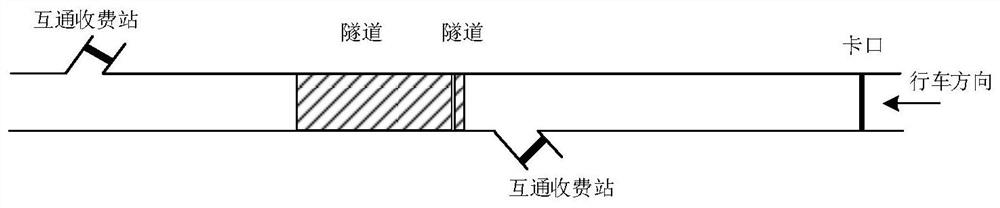
Highway traffic jam detection method based on toll data and checkpoint data
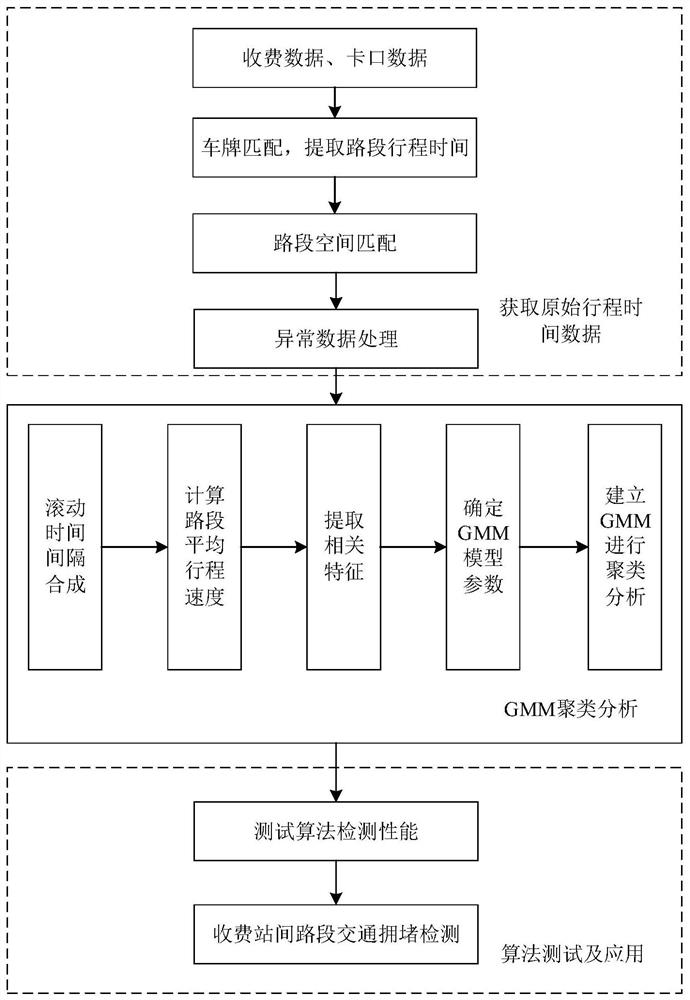
ActiveCN111724592AHave diversitySolving problems with less dataDetection of traffic movementCharacter and pattern recognitionCluster algorithmData Origin
The invention discloses a highway traffic jam detection method based on toll data and checkpoint data. According to the method, the traffic jam is predicted by comprehensively utilizing the toll dataand the checkpoint data, data sources are diversified, the toll data is supplemented by utilizing the checkpoint data, the problem of less data between adjacent intercommunication toll stations can bewell solved, and the prediction is more accurate; and the road running state is analyzed by adopting the Gaussian mixture clustering algorithm, the consideration is comprehensive, different traffic forms of the road can be comprehensively simulated and analyzed, and scientificity and comprehensiveness are higher.
Owner:CHONGQING UNIV
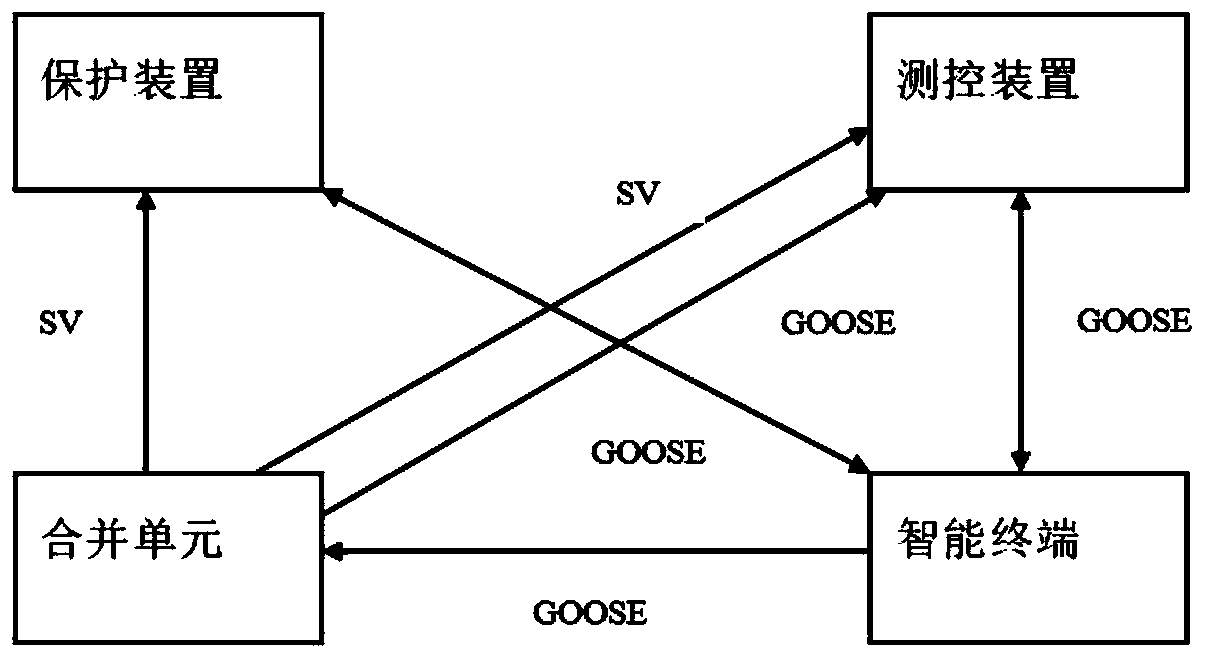
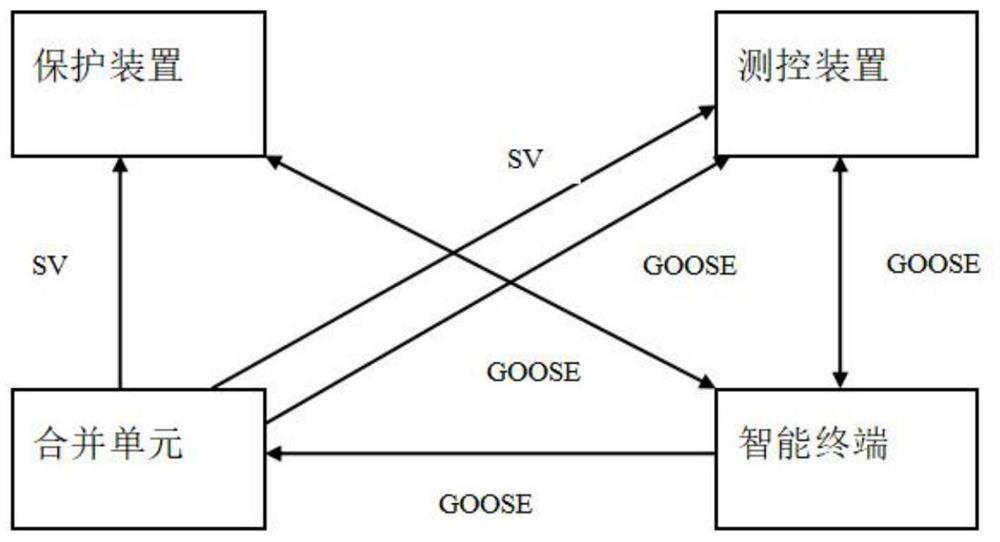
A method and a tool for automatically checking correctness of a secondary virtual loop of an SCD file
ActiveCN109728976AImprove parsing speedEasy to understandCircuit arrangementsData switching networksVirtual terminalPower grid
The invention relates to a method and a tool for automatically checking correctness of a secondary virtual loop of an SCD file, and belongs to the field of power grids. According to the method, SCD analysis can be carried out, and correctness inspection can be carried out on the secondary virtual loop of the SCD file. By analyzing the SCD file, information is displayed according to categories in graphical forms such as graphs, tables and the like, such as secondary equipment tables, IED instance configurations, communication configuration information, GOOSE / SV configurations and IED virtual terminal connection relationships, so that a convenient and visual viewing means is provided for on-site analysis. In addition, after the SCD is analyzed, the content of the SCD file can be stored locally in a json text format, a special interface is designed, text information is obtained and stored in an inspection tool memory, real-time SCD correctness inspection and analysis are carried out, andan analysis result is displayed.
Owner:GUIZHOU POWER GRID CO LTD
Process for improving SO2 desorption efficiency of desulfurization absorbent
ActiveCN112452109AReduce loadImprove desorption efficiencyGas treatmentDispersed particle separationThermodynamicsPhysical chemistry
The invention discloses a process for improving SO2 desorption efficiency of a desulfurization absorbent. The process comprises the following steps: a, heating amine-rich liquid absorbing SO2 gas, andfeeding the heated amine-rich liquid into a low-pressure desorption tower for pre-desorption; b, feeding the pre-desorbed secondary lean amine solution into a high-pressure desorption tower for desorption; c, reducing SO2 contained in the lean amine output after desorption of the high-pressure desorption tower to be belower than 5g / L, or increasing the total desorption efficiency of SO2 in the amine-rich liquid input in the step a to be greater than 90%; pressurizing the high-pressure desorption steam output by the high-pressure desorption tower, and adopting as a heat source of steam required by steam stripping of SO2 in the desorption amine-rich liquid of the low-pressure desorption tower. According to the invention, a double-tower double-effect and low-pressurization two-time deep desorption process is adopted, the content of SO2 contained in the output lean amine liquid is less than 5g / L or the total desorption efficiency of SO2 in the amine-rich liquid is more than 90%, the operation is stable, the power consumption is low, the live steam consumption is saved by 30-50%, the desorption efficiency is improved by 4-12%, and the investment operation comprehensive cost is reducedby 20-40%; and ultra-low emission of desulfurization can be realized.
Owner:双盾环境科技有限公司
Complex network clustering method based on key influence of nodes
InactiveCN102571954BReflect the clustering processThorough analysisTransmissionFunctional networkComputer science
The invention discloses a complex network clustering method based on the key influence of nodes, which comprises the following steps: sequencing nodes in a complex network according to the size of degree, wherein the subordinate community of each initial node is not determined; taking a node (the subordinate community thereof is not determined) with the largest degree as a core node of a community; beginning to build the community; determining the subordinate community of a node adjacent to the core node; after the community is completely built, taking a node (the subordinate community thereof is not determined) with the largest degree as a core node of a community; beginning to build a community; and repeatedly performing a process of community building until the subordinate communities of all nodes in the network are determined, thereby obtaining a final network cluster structure. By using the method disclosed by the invention, a clustering precision in the complex network is superior to that obtained by using a FN (functional network) clustering method; and the method plays a positive role in carrying out fine-grained reveal on a real cluster structure of the complex network.
Owner:臻睿(北京)信息技术有限公司
Rapid planning and configuration method for engineering pipelines of urban underground comprehensive pipe gallery
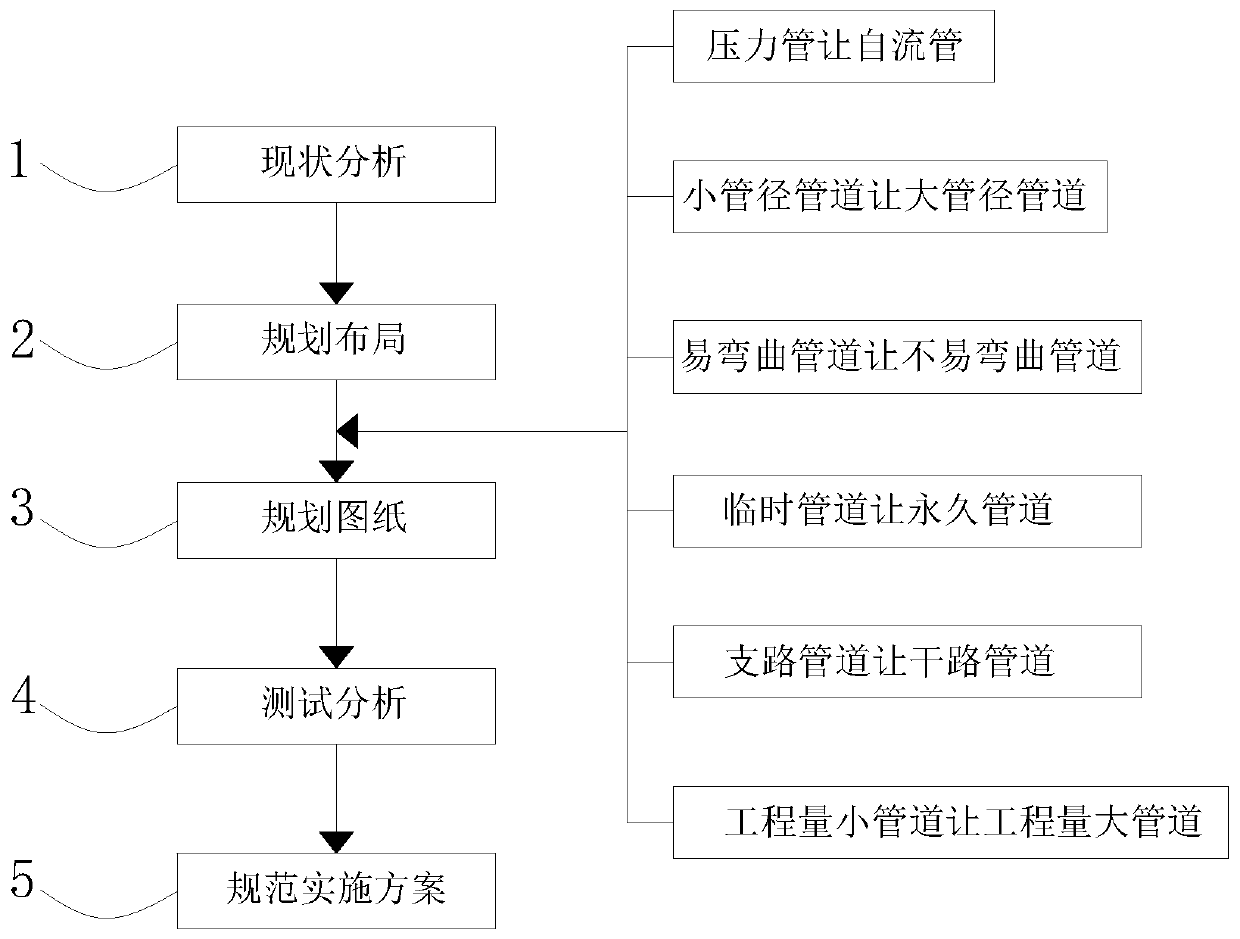
PendingCN110837671AThorough analysisEasy to planGeometric CADForecastingLayout planningTest analysis
The invention belongs to the technical field of urban underground comprehensive pipe gallery pipeline planning, and particularly relates to a rapid planning and configuration method for engineering pipelines of an urban underground comprehensive pipe gallery. The method comprises the following steps, s1: performing present situation analysis, wherein the scale, the layout, the framework and otherinformation of the urban underground comprehensive pipe gallery are understood, problems faced by the urban underground comprehensive pipe gallery are analyzed and summarized, and a preliminary data analysis model is established; S2, integrating the conclusions and solutions obtained in the S1, and carrying out reasonable planning and layout, S3, planning drawings, planning an engineering pipelinecomprehensive overall planning plane graph and an engineering pipeline comprehensive road standard cross section graph, and S4, carrying out test analysis. According to the method, the analysis of the current situation of the urban underground comprehensive pipe gallery is enhanced, so that the analysis is more thorough, the planning and layout rationality are optimized, the layout is uniform, the problem of disordered layout is solved, and the planning efficiency is improved.
Owner:JIANGSU I FRONT SCI & TECH CO LTD
Cytotherapeutics, cytotherapeutic units and methods for treatments using them
Owner:CELULARITY INC
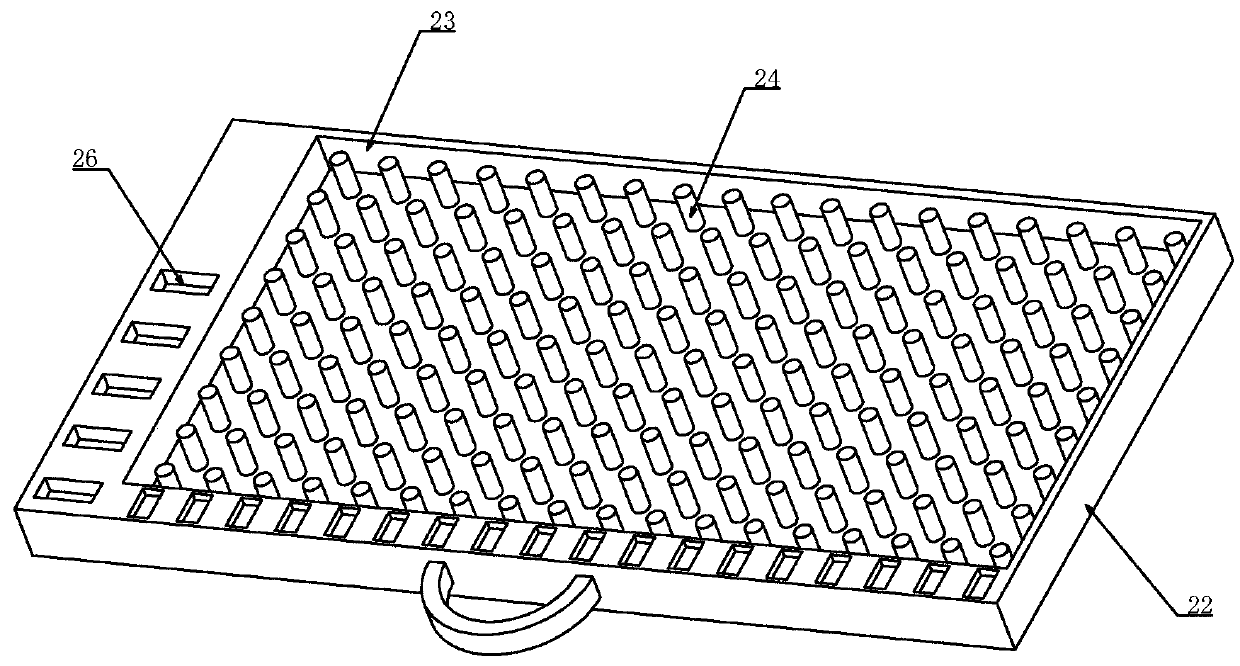
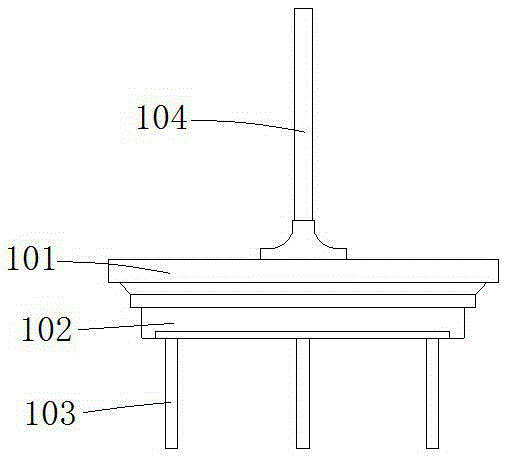
Multifunctional test platform
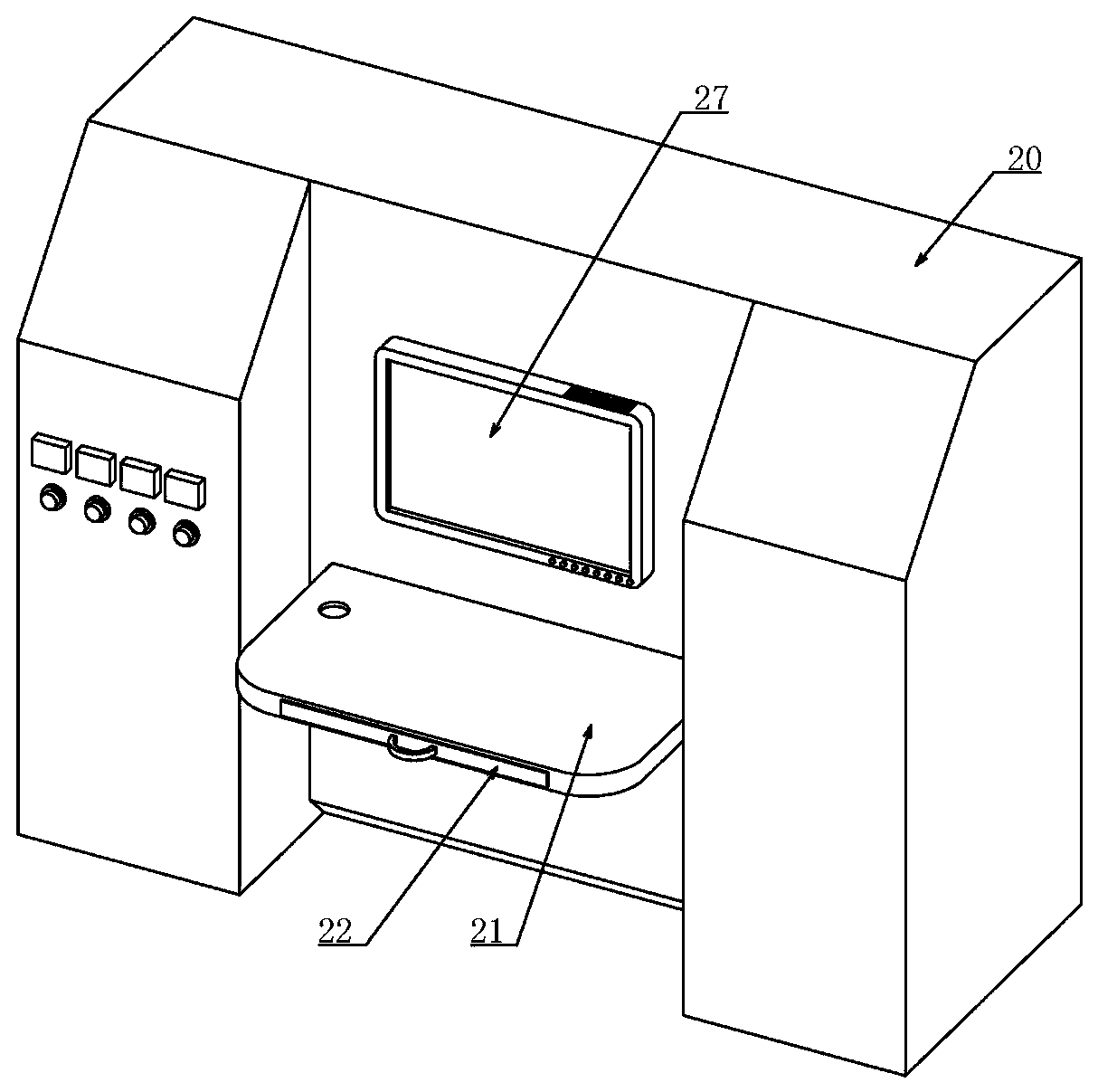
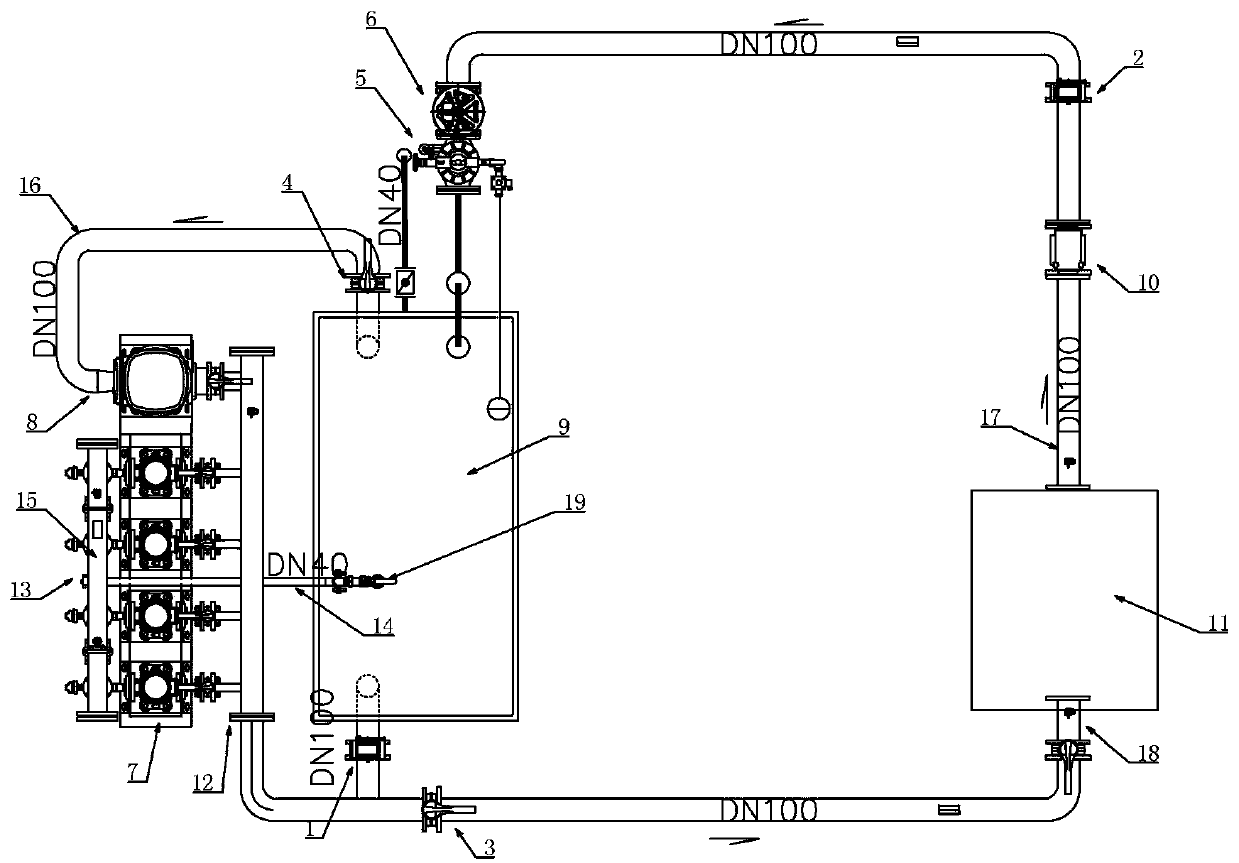
PendingCN111238841ASmall footprintBeautiful appearanceMachine valve testingElectric testing/monitoringFrequency changerWater use
The invention relates to a multifunctional test platform. In order to adjust the water consumption in the urban peak period and the urban low peak period, the invention provides an intelligent high-low-peak-adjusting water utilization scheme. A series of matched test platforms are used for testing the performance of each parameter proposed in the scheme so as to be better applied to urban water supply. The test platform comprises a water pump unit part and a valve test part. The water pump unit part is provided with five water pumps, wherein four groups of water pumps are used for simulating field water pump operation, and one water pump is used for simulating municipal pipe network water supply through a frequency converter so as to test all parameters of the non-negative pressure controlcabinet under different conditions, and the test bench is electrically connected with the test platform and has three parameters for testing all functions under different modes and pressure values infront of and behind a valve piece at a corresponding position. The test platform is small in occupied area and attractive in appearance, various parameters are intelligently read through the sensor,the parameters are accurate and comprehensively analyzed, and comparison, recording and analysis are facilitated.
Owner:河南慧水科技有限公司
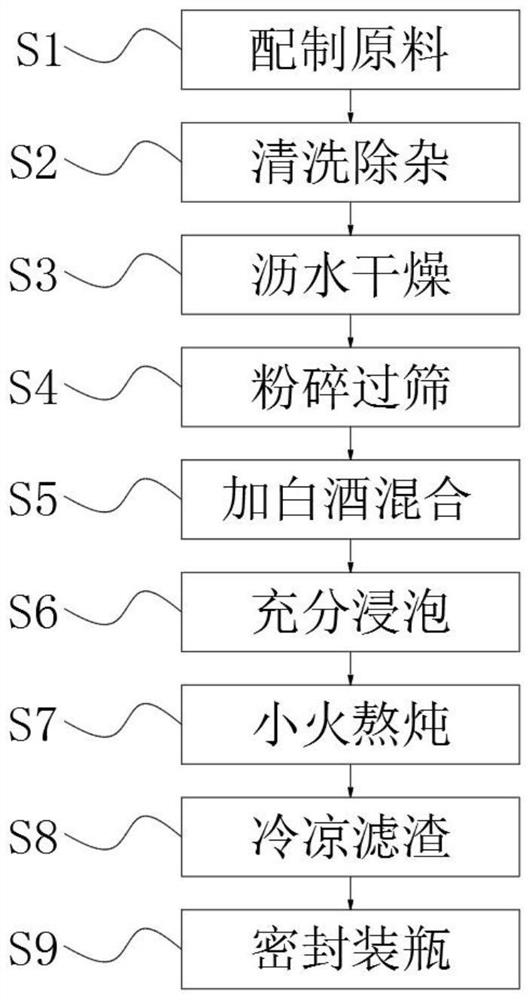
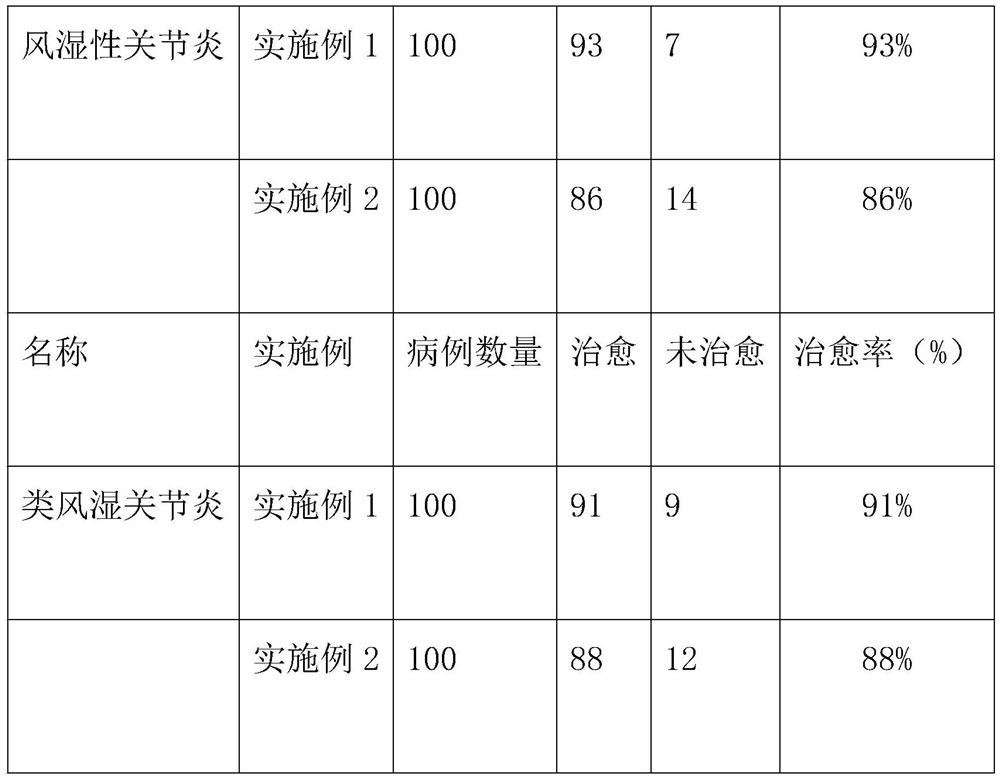
Medicinal liquor for conditioning waist and leg arthralgia and preparation method thereof
PendingCN114306455AScientific and reasonable structureSafe to useAntibacterial agentsHydroxy compound active ingredientsZanthoxylum chalybeumAching pain
The invention discloses medicinal liquor for conditioning waist and leg arthralgia, which is prepared from 20 parts of high-alcohol-content white spirit, 40 parts of folium artemisiae argyi and 40 parts of pepper, the high-alcohol-content white spirit is used as a main material, and the folium artemisiae argyi and the pepper are used as auxiliary materials, the medicinal liquor prepared by the invention consists of the folium artemisiae argyi and the pepper which are common in life, and the folium artemisiae argyi and the pepper are lower in cost compared with an existing medicinal liquor formula and are easy to obtain; compared with the traditional complex traditional Chinese medicine composition, the prepared medicinal liquor is more suitable for people to use and convenient to popularize and use, meanwhile, the folium artemisiae argyi and the pepper are used as auxiliary materials of the medicinal liquor, effective components of the folium artemisiae argyi and the pepper can be effectively absorbed in cooperation with the high-degree baijiu, the high-degree baijiu is applied to the pain spot, and the pain spot cannot be affected. The active ingredients of the folium artemisiae argyi and the pepper are conveniently and deeply substituted into the pain of a patient through the high-degree white spirit, so that the active ingredients of the medicine permeate the skin and directly reach tendons and vessels, germs are killed, and the purposes of relieving pain and removing cold-dampness are achieved.
Owner:陈雪飞
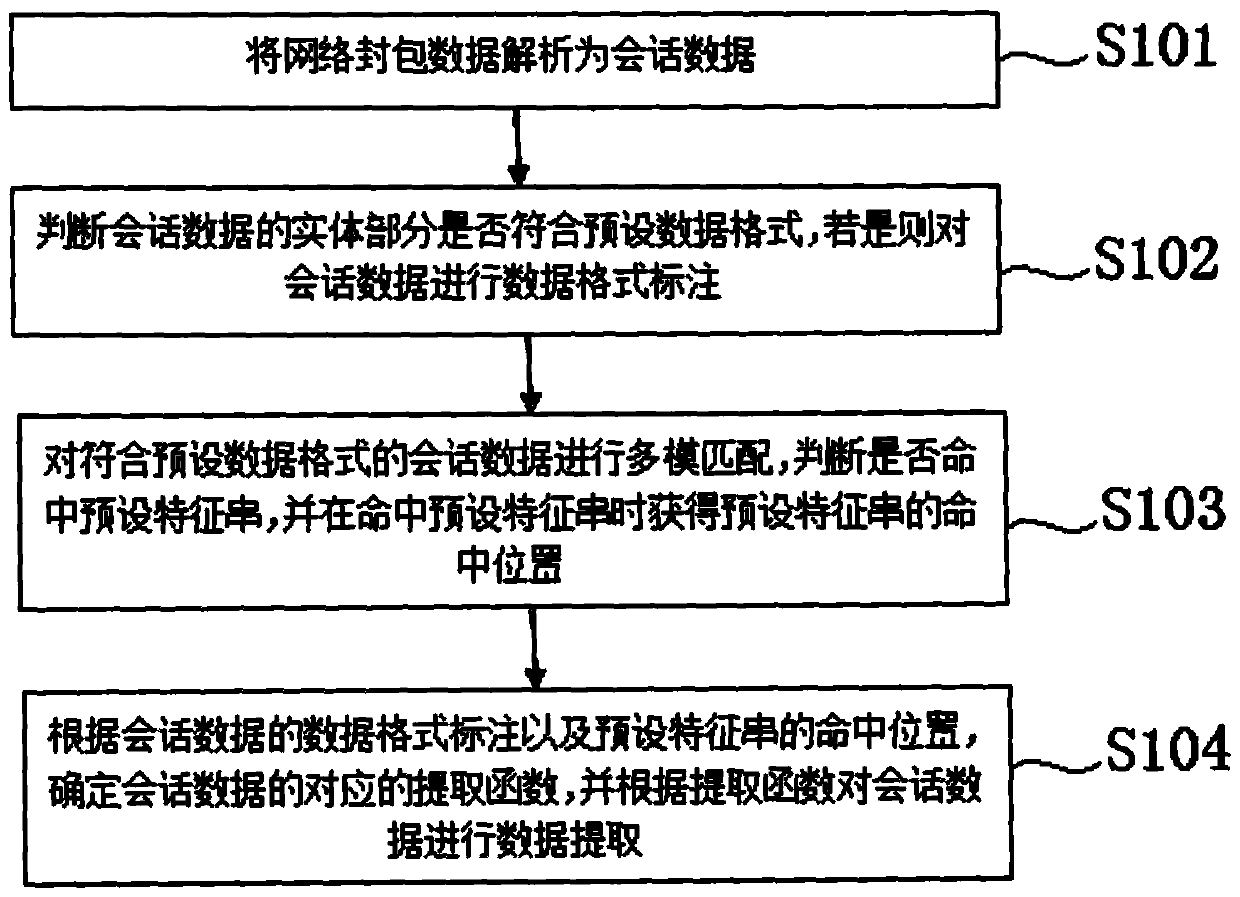
Automatic intelligent mining method for network security vulnerabilities of broadcast television key information infrastructure
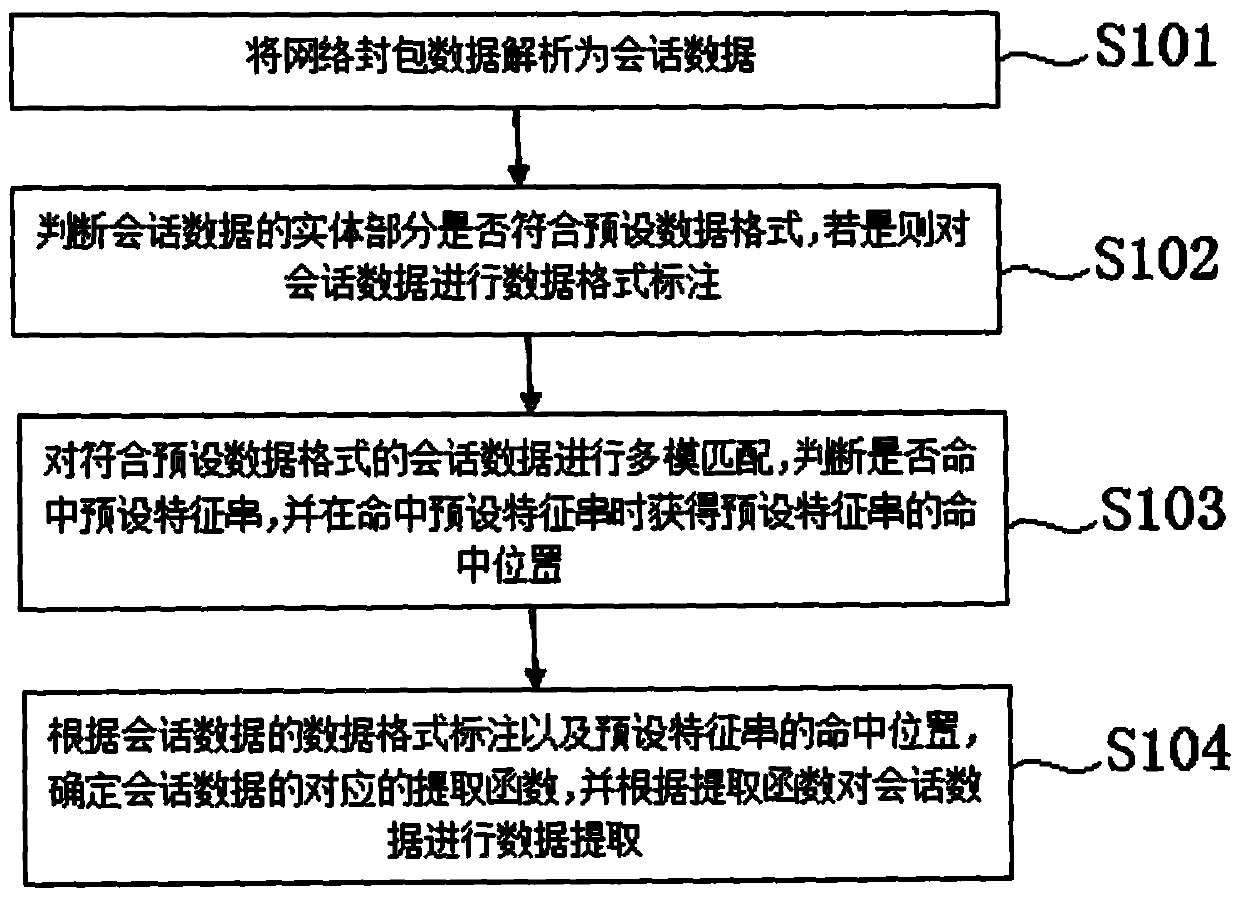
PendingCN109981563AReduce extraction timeImprove securityTransmissionCritical information infrastructureBroadcasting
The invention relates to the technical field of network security vulnerabilities, in particular to an automatic intelligent mining method for network security vulnerabilities of broadcast television key information infrastructure, which comprises the following steps of: step S101, analyzing network packet data into session data; step S102, judging whether the entity part of the session data conforms to a preset data format or not; step S103, performing multi-mode matching on the session data meeting the preset data format; and step S104, labeling according to the data format of the session data and the hit position of a preset feature string. After the method is adopted, the invalid data which do not conform to the preset data format can be filtered out by judging the preset data format ofthe analyzed session data, so that the data extraction time is shortened; besides, the Web application security vulnerability analysis is more thorough, the source of vulnerability generation can bepointed out, and the whole vulnerability triggering process is analyzed, so that the network security of the broadcast television key information infrastructure is greatly enhanced.
Owner:国家广播电视总局广播电视规划院
A kind of improving desulfurization absorbent desorption so 2 efficient process
ActiveCN112452109BReduce loadImprove desorption efficiencyGas treatmentDispersed particle separationPhysical chemistryProcess engineering
The invention discloses a method for improving the desorption of SO by a desulfurization absorbent 2 efficient process, the process steps are: a, absorb SO 2 The rich amine liquid of the gas is sent to the low-pressure desorption tower for pre-desorption after being heated; b. The sub-lean amine liquid after pre-desorption is sent to the high-pressure desorption tower for desorption; c. The SO contained in the lean amine liquid output after the high-pressure desorption tower is desorbed 2 To below 5g / L or in the rich amine solution input in step a, SO 2 The total desorption efficiency is greater than 90%; and the high-pressure desorption steam output from the high-pressure desorption tower is pressurized and used as a low-pressure desorption tower to desorb SO in the rich amine liquid 2 Heat source for steam required for stripping. The present invention adopts double-tower double-effect + low pressurization twice deep desorption process, and the SO contained in the output lean amine liquid 2 To below 5g / L or rich amine solution SO 2 The total desorption efficiency is greater than 90%, the operation is stable and the power consumption is low, the raw steam consumption is saved by 30%-50%, the desorption efficiency is increased by 4-12%, and the comprehensive cost of investment and operation is reduced by 20%-40%; it can achieve ultra-low emission of desulfurization.
Owner:双盾环境科技有限公司
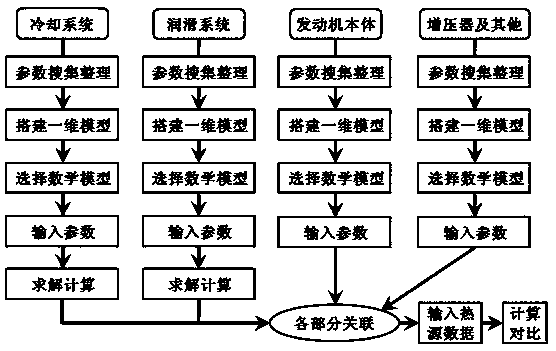
A one-dimensional integrated thermal management simulation method for automobile engine
ActiveCN104732009BRealize associative simulationRealize what-if analysisSpecial data processing applicationsDimensional simulationHeat management
The invention relates to a one-dimensional integrated thermal management simulation method of an automobile engine, which is characterized in that: one-dimensional simulation of the engine cooling system; one-dimensional simulation of the engine lubrication system; one-dimensional modeling of engine body components; and engine-related systems or modules One-dimensional modeling; correlating the simulation models of the aforementioned systems and components for integrated simulation.
Owner:CHERY AUTOMOBILE CO LTD
A Multiple Fault Diagnosis Method Based on Improved SDG
InactiveCN104050371BThorough analysisMultiple fault diagnosis is accurateSpecial data processing applicationsDiagnosis methodsSystem failure
The invention discloses a multi-fault diagnosis method based on an improved SDG, and belongs to the field of fault problem diagnosis. The multi-fault diagnosis method based on the improved SDG mainly comprises the step of establishing an engine entraining model, the step of establishing an SSDG model, the step of diagnosing a multi-fault problem, and the step of analyzing a fault node measuring sequence. According to the multi-fault diagnosis method, the multi-source fault source searching detection can be carried out, and the fault diagnosis can be more accurate. The fault of a large system is analyzed on the background of manufacturing a large airplane, and the fault source is found out. According to the multi-fault diagnosis method based on the improved SDG, the fault diagnosis is carried out with the SDG method, the method can carry out the analysis more thoroughly compared with an event tree method and an accident tree method, the defect that according to a traditional SDG method, only the single-fault source can be found out is overcome, the multi-fault source searching can be carried out with the multi-fault diagnosis method, and the fault diagnosis is more accurate.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
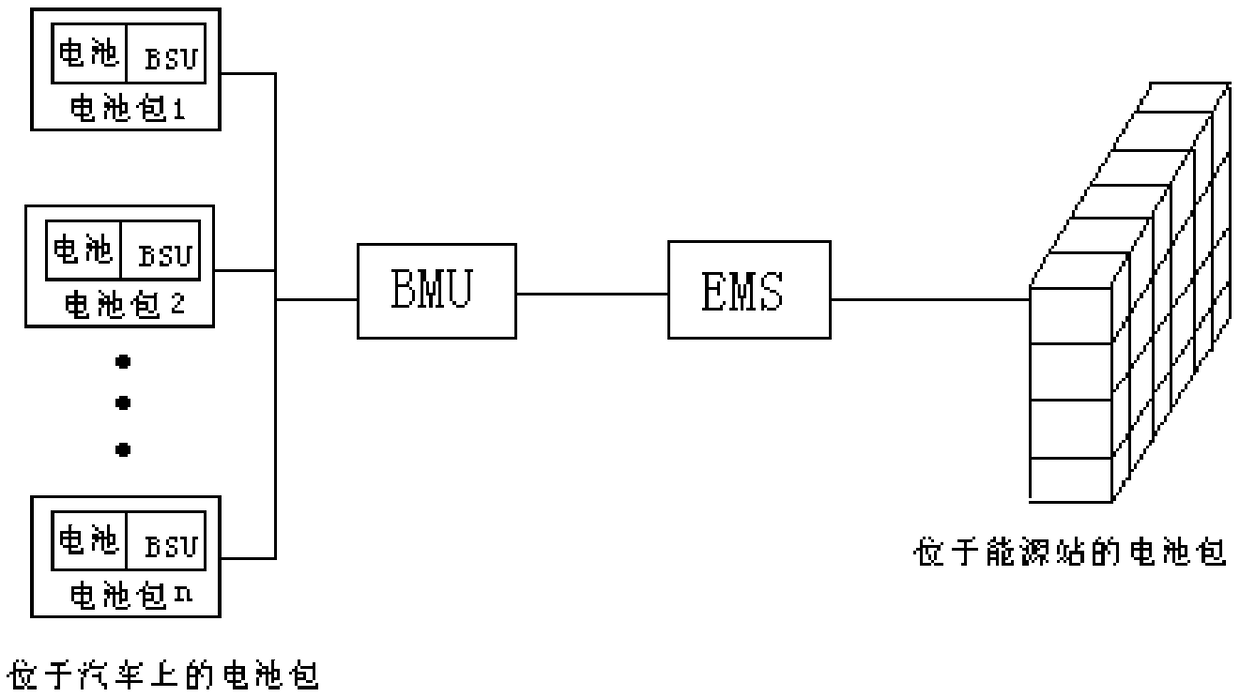
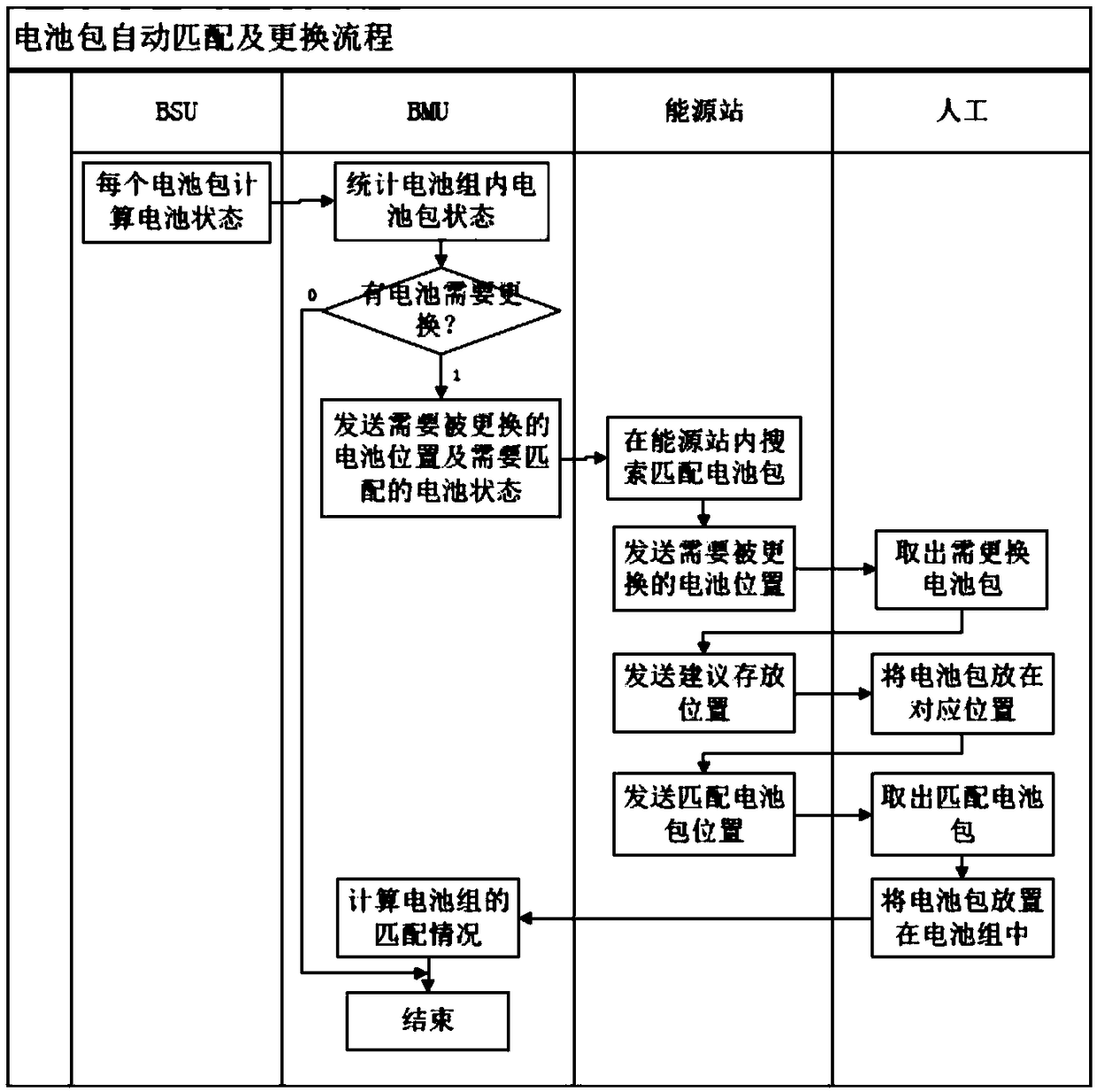
A battery pack automatic matching system
ActiveCN106356577BComprehensive dataThorough analysisCells structural combinationElectrical batteryEngineering
The invention provides an automatic battery pack matching system. The system comprises a plurality of battery packs located on an automobile, a vehicle-mounted battery pack controller, an energy source station controller and a plurality of battery packs located on an energy source station, wherein one controller is arranged in each battery pack and the controller is used for acquiring state information of the corresponding battery pack in real time; the vehicle-mounted battery pack controller is used for receiving and analyzing the state information of the plurality of battery packs on the automobile in real time; when the battery packs need to be replaced, the vehicle-mounted battery pack controller is used for sending the state information of the battery packs needing to be replaced to the energy source station controller; the energy source station controller is used for calculating the state information to obtain the battery packs which can mostly meet the requirements of the energy source station. According to the automatic battery pack matching system provided by the invention, automation of battery matching and replacing can be realized and workers can be guided to replace the battery packs, so that the battery pack matching and replacing efficiency is extremely improved.
Owner:SICHUAN ENERGY INTERNET RES INST TSINGHUA UNIV
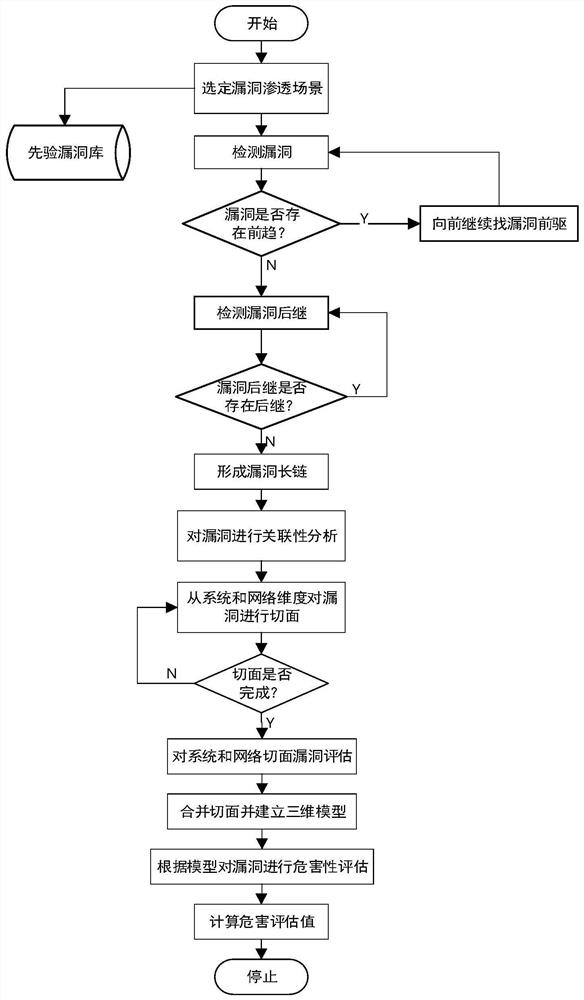
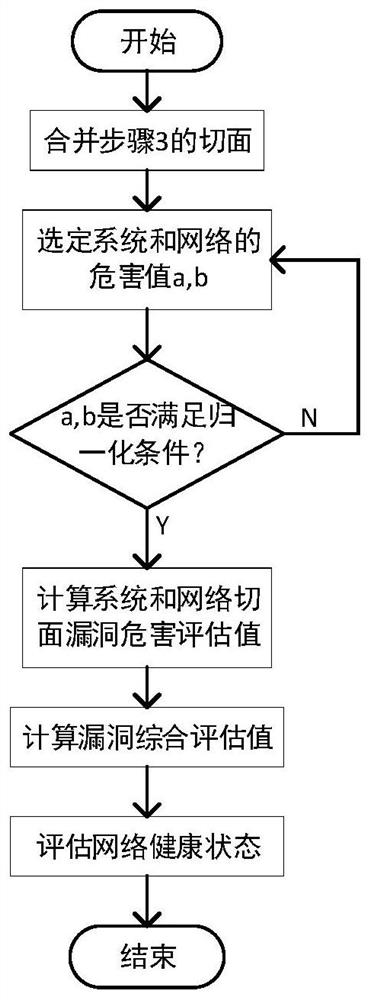
Network system security vulnerability relevance modeling and analysis method
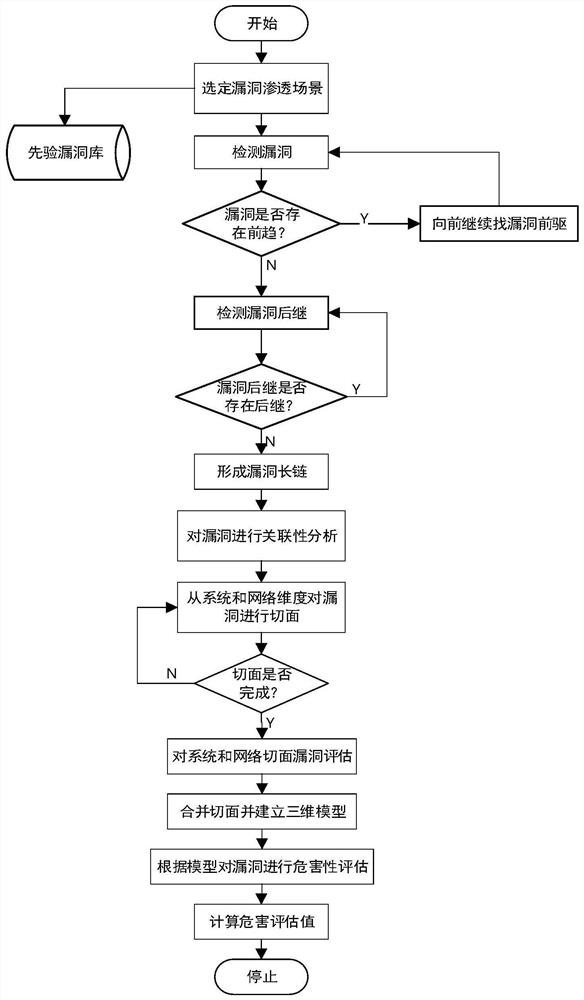
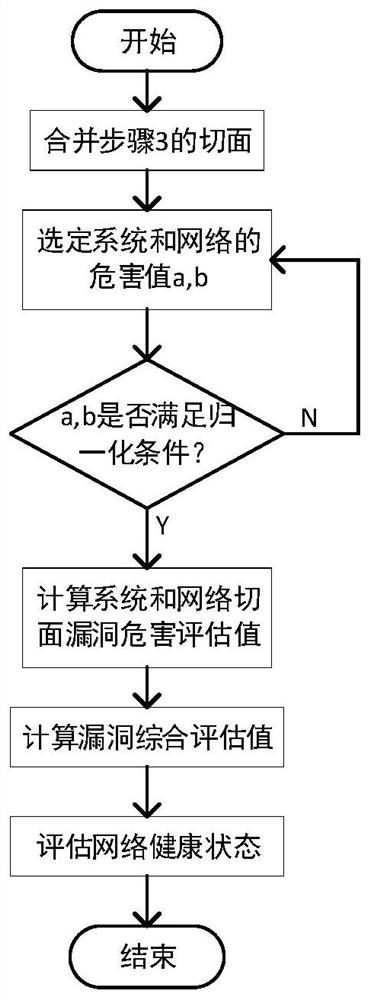
ActiveCN113259334AImprove accuracyComprehensive assessment perspectiveData switching networksNetworked systemCorrelation analysis
The invention discloses a network system security vulnerability relevance modeling and analysis method, which is specifically implemented according to the following steps: 1, selecting a network scene, and detecting network vulnerabilities existing in the specific network scene; 2, performing correlation analysis on the vulnerabilities obtained in the step 1, and cutting the vulnerabilities in two dimensions of a system level and a network level; 3, combining a system section and a network section, adding vulnerability hazards as a third dimension, and establishing a three-dimensional evaluation model; and 4, analyzing the model in the step 3, and establishing a vulnerability hazard degree assessment mechanism to assess the health state of the system. The problem that in the prior art, the network hazard degree measurement standard is not accurate enough is solved.
Owner:XIAN UNIV OF TECH
Medical system
PendingUS20200054258A1Reduce in quantityEasy to predictHealth-index calculationInertial sensorsPharmacy medicineAnalyte
A medical system, an analyte measurement device, a medication device and a method for transcutaneously inserting an insertable element into a body tissue are disclosed. The medical system comprises:at least one electronics unit having at least one electronics component;at least one adhesive surface for attachment of the electronics unit to a skin site of a host;at least one first subsystem configured for being at least partially inserted into the host;at least one second subsystem, wherein the second subsystem comprises at least one secondary sensor, wherein the first subsystem and the second subsystem are operably connectable to the electronics unit,wherein the second subsystem is physically attachable to the medical system.
Owner:ROCHE DIABETES CARE INC
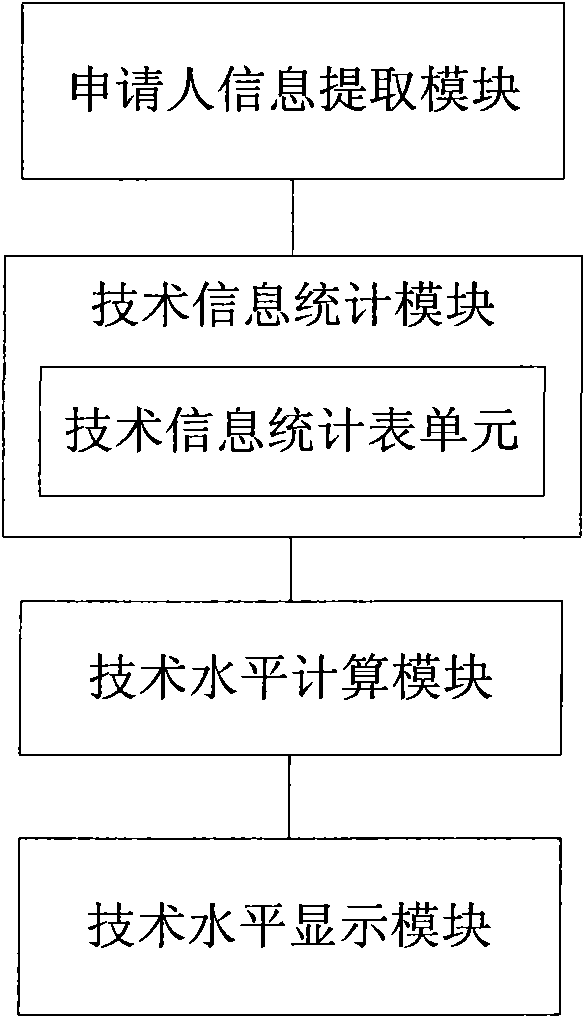
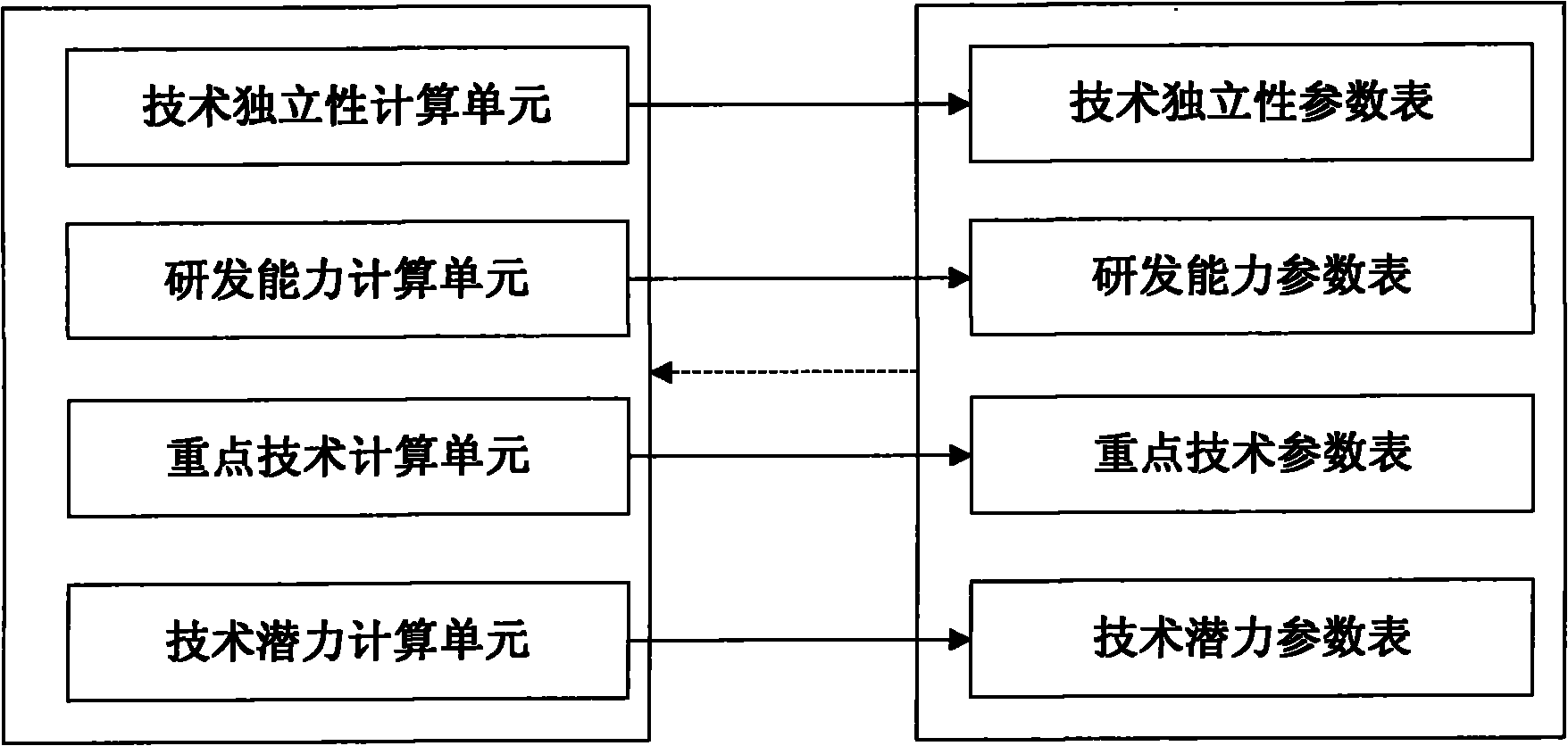
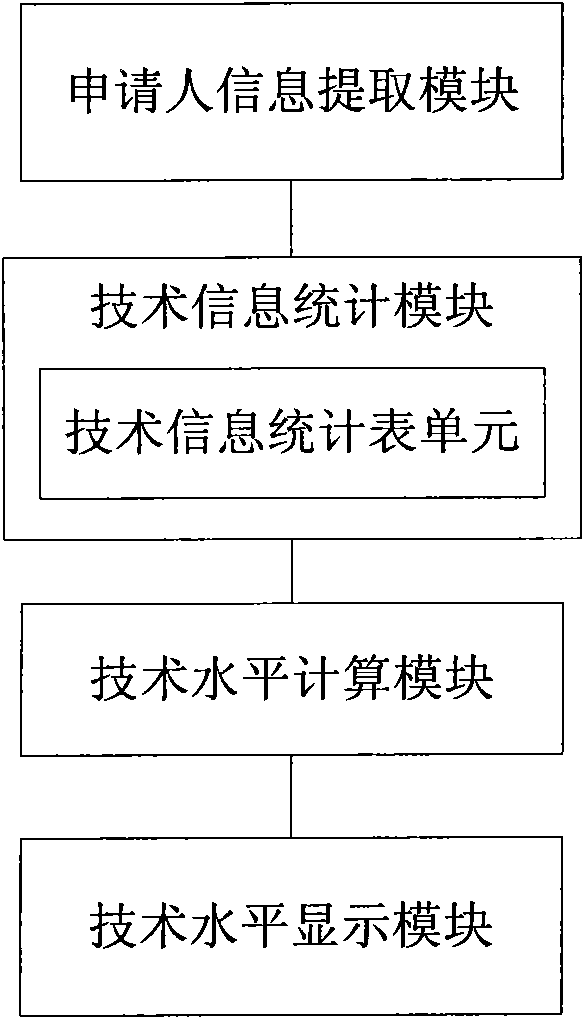
Analyzing system of technical level of patent applicant
InactiveCN101996220AThorough analysisAnalysis results are intuitive and easy to understandSpecial data processing applicationsRelevant informationLibrary science
The invention relates to an analyzing system of a technical level of a patent applicant, which comprises an applicant information extracting module, a technical information counting module, a technical level computing module and a technical level display module, wherein the technical information counting module comprises a technical information statistic table unit for counting each item of information obtained by the applicant information extracting module; the technical level computing module at least comprises a technology independence computing unit, a research and development capability computing unit, an emphasis technology analyzing unit and a technology potential computing unit and is used for reading the contents of the technical information counting module and computing each value of the technical level of the applicant according to a statistic result of the technical information counting module; and the technical level display module is used for displaying the technical level of the applicant according to the contents of the technical information counting module and the technical level computing module. The system has the advantages of discovering related information of the applicant deeply, comprehensively and thoroughly analyzing the technical level of the applicant, and simultaneously displaying the result in a more visual and easier mode.
Owner:J Z M C INTPROP DATA SCI & TECH
Biosensor dividing device
InactiveCN105259320AThe analysis is sound and comprehensiveThorough analysisMaterial analysisChemical reactionDisplay device
The invention discloses a biosensor dividing device. The device comprises a base, a reaction box, sensing devices and a fixed table, wherein the reaction box and the fixed table are installed on the top of the base, a plurality of detection ports are formed in the top of the chemicophysical reaction box, a plurality of telescopic booms are installed in an inner cavity of a collecting plate corresponding to the detection ports, and each sensing device is installed on the bottom of the corresponding telescopic boom. By the adoption of the multiple sensing devices, comprehensive physical and chemical reaction change data collection can be achieved during substance detection. Analysis of information in all aspects is achieved through a transcriber and a data analyzer. Through the arrangement of a first displayer, a second displayer and a third displayer, results in all aspects of substance detection can be displayed effectively and visually. Furthermore, through the arrangement of a plurality of reaction change data collectors, it is guaranteed that data can be collected more comprehensively.
Owner:ZHONGSHAN JIEXIN TECH SERVICES CO LTD
A Search Method for Impossible Differential Paths of Related Keys in Block Ciphers
ActiveCN106027226BSolve the problem of findingIn-depth analysisEncryption apparatus with shift registers/memoriesTheoretical computer scienceRelated-key attack
Owner:XIDIAN UNIV
A Modeling and Analysis Method for Network System Security Vulnerabilities Correlation
ActiveCN113259334BImprove accuracyComprehensive assessment perspectiveSecuring communicationNetworked systemCorrelation analysis
The invention discloses a method for modeling and analyzing the correlation of network system security loopholes, which is specifically implemented according to the following steps: Step 1, select a network scene, and detect the network loopholes existing in a specific network scene; Step 2, the obtained in step 1 Correlation analysis is performed on the vulnerabilities, and two dimensions of the vulnerability are cut at the system level and the network level; step 3, the system aspect and the network aspect are merged, and the vulnerability hazard is added as the third dimension, and a three-dimensional evaluation model is established; step 4, Analyze the model in step 3, and establish a vulnerability assessment mechanism to evaluate the health status of the system. The problem that the measurement standard of the degree of network harm existing in the prior art is not accurate enough is solved.
Owner:XIAN UNIV OF TECH
A method and tool for automatically checking the correctness of the secondary virtual loop of an SCD file
ActiveCN109728976BThorough analysisEasy to useCircuit arrangementsTransmissionVirtual terminalSoftware engineering
The invention relates to a method and a tool for automatically checking the correctness of a secondary virtual circuit of an SCD file, belonging to the field of power grids. The invention can not only analyze the SCD, but also check the correctness of the secondary virtual circuit of the SCD file. Through the analysis of the SCD file, the information is displayed by category in graphical forms such as diagrams and tables, such as secondary equipment tables, IED instance configurations, communication configuration information, GOOSE / SV configurations, IED virtual terminal connection relationships, etc. Analysis provides a convenient and intuitive means of viewing. In addition, after SCD analysis, the content of the SCD file can be stored locally in json text format, and a special interface can be designed to obtain the text information, store it in the memory of the inspection tool, perform real-time SCD correctness inspection and analysis, and display the analysis results.
Owner:GUIZHOU POWER GRID CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com