Network system security vulnerability relevance modeling and analysis method
A network system and analysis method technology, which is applied in the field of network system security vulnerability correlation modeling and analysis, can solve the problem of inaccurate network harm degree measurement standards, and achieve the effect of thorough vulnerability analysis, comprehensive evaluation perspective and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
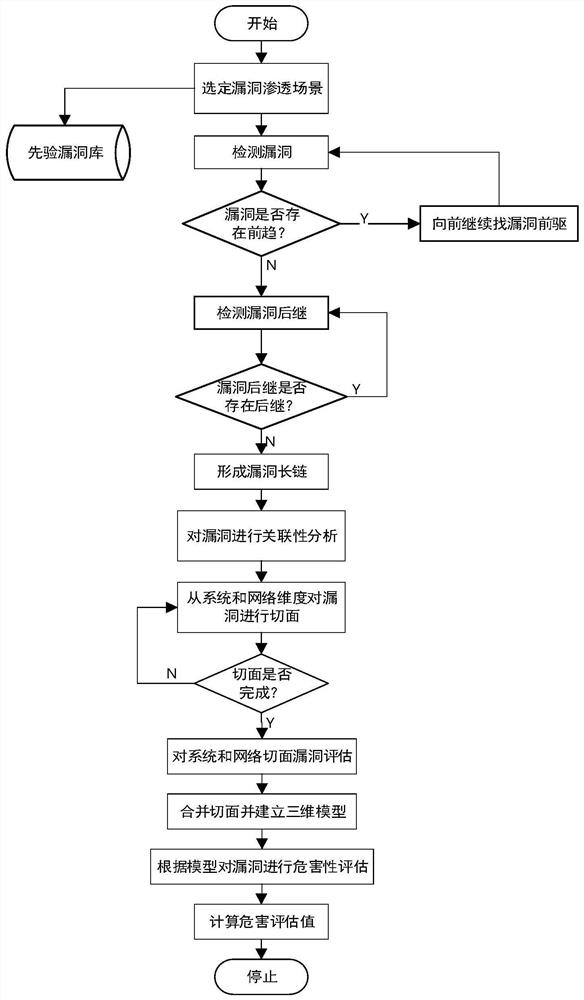
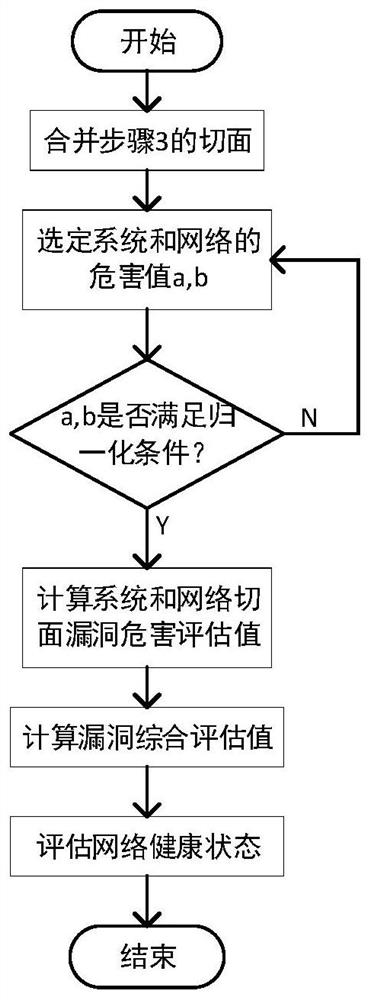
[0061] In the network system, the leakage of certain user information will activate system vulnerabilities and then be infiltrated. Some infiltration results can even be used again, step by step into the system, and obtain higher permissions. In order to cover up the infiltration behavior, the infiltrator Infiltration traces are erased, and infiltrators leave backdoors for the convenience of the next attack.
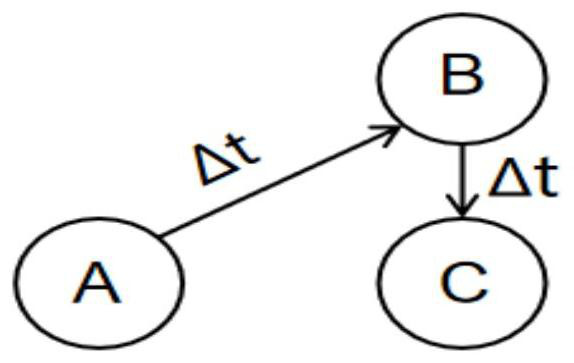
[0062] Record A as a vulnerability caused by a system version that is too low. The attacker uses this vulnerability to cause an overflow vulnerability B in the system. Through the overflow, the infiltrator can obtain the system shell, and then use the shell to trigger a privilege escalation vulnerability C. The infiltrator logs in through an ordinary user system, escalate privileges, obtain administrator information, log in to the background, make changes to the database or other information of the website, and finally the attacker successfully escalates privileges. Acco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com