Single-step quantum key distribution post-processing method and system based on polarization code, medium and equipment
A technology of quantum key distribution and polar code, which is applied in the post-processing field of single-step quantum key distribution based on polar code, can solve the problem of increasing bit overhead, reducing the practicability of quantum key distribution system, and affecting the generation of security keys Speed and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
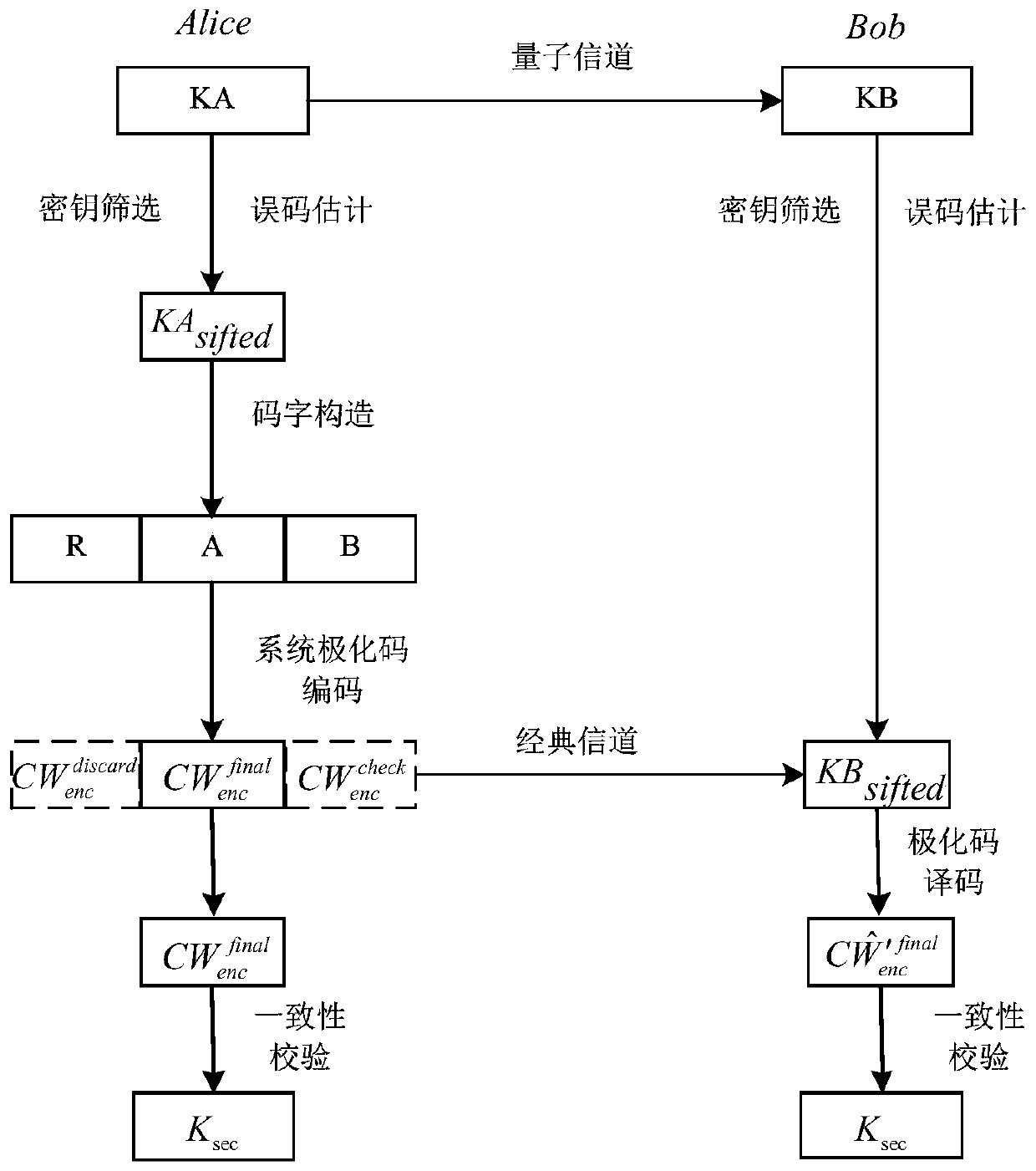
[0070] Such as figure 1 As shown, this embodiment provides a polar code-based single-step quantum key distribution post-processing method, including the following steps:
[0071]S1. Alice at the sending end and Bob at the receiving end respectively obtain a series of original keys KA and KB of equal length through quantum channel transmission, and then Alice at the sending end discloses all the modulation bases when preparing qubits, and at the same time Bob at the receiving end discloses his measurement All measurement bases when qubits are used; when Alice and Bob receive the base information of the other party and compare it with their own base information, they discard the original keys with different bases and keep the original keys with the same base, thus completing Key screening to obtain the screened key of equal length;
[0072] S2. After completing the key screening, Alice at the sending end and Bob at the receiving end select some of the screened keys for public c...
Embodiment 2
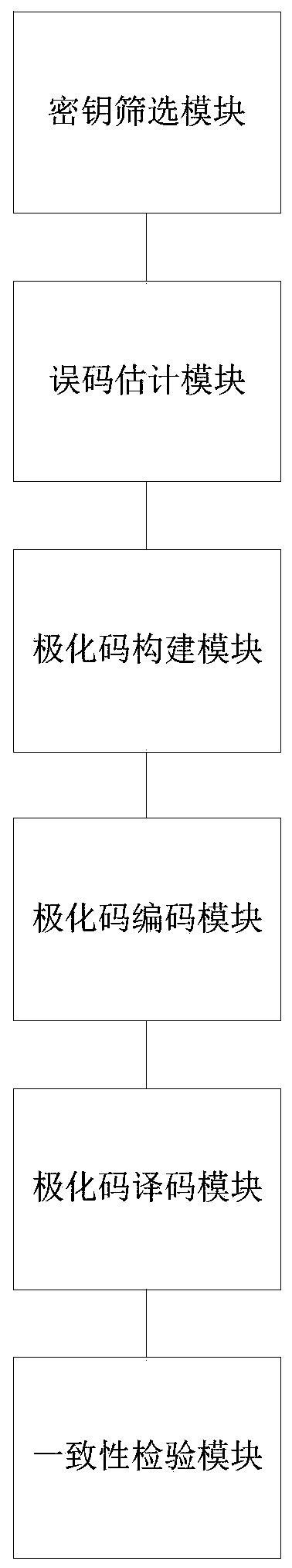
[0116] Such as image 3 As shown, this embodiment also provides a polar code-based single-step quantum key distribution post-processing system, including:
[0117] Key screening module: the sending end and the receiving end respectively obtain the original key of the sending end and the original key of the receiving end through quantum channel transmission, the sending end and the receiving end respectively disclose the modulation base and the measurement base, and discard the original key with different bases, The original key with the same base is retained, and both the sender and the receiver get a sieved key of equal length;
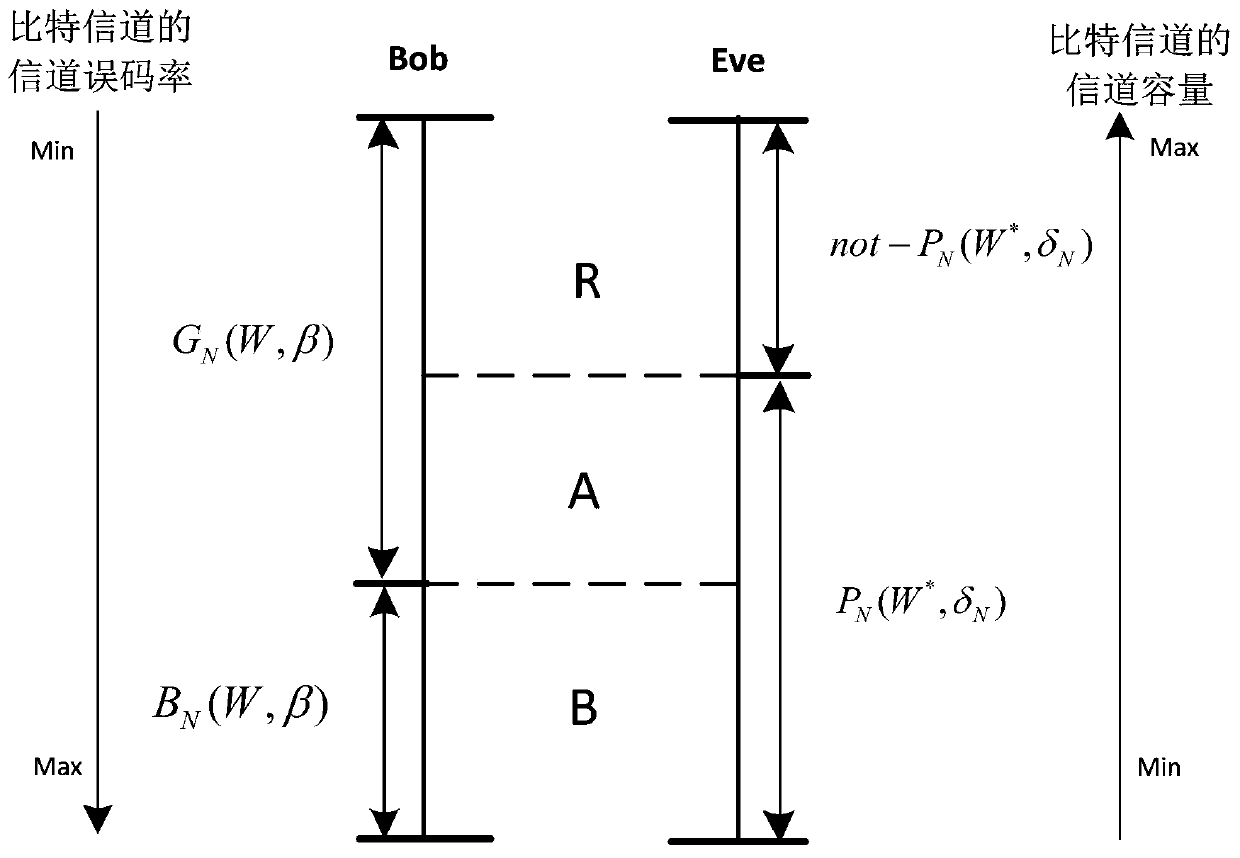
[0118] Bit error calculation module: select some keys in the sieved keys of the sending end and the receiving end for public comparison, and obtain the qubit bit error rate according to the comparison result. If the qubit bit error rate is higher than or equal to the set safety threshold, Abandon all the key bits of this transmission; if it is less ...
Embodiment 3
[0124] This embodiment also provides a storage medium, the storage medium can be a storage medium such as ROM, RAM, magnetic disk, optical disk, etc., and the storage medium stores one or more programs. When the programs are executed by the processor, the implementation of Embodiment 1 based on Post-processing method of single-step quantum key distribution of polar code:
[0125] S1: After the sending end and the receiving end transmit information through the quantum channel, the sending end and the receiving end obtain a series of original keys of equal length respectively, and then the sending end discloses the modulation base, and the receiving end discloses the measurement base; when the sending end and the receiving end Receive the base information of the other party and compare it with the base information held by yourself, discard the original keys with different bases, and keep the original keys with the same base, and both the sending end and the receiving end will get...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com