Bell state-based two-party quantum key negotiation method and system
A quantum key agreement and quantum technology, applied in the field of Bell state-based two-party quantum key agreement methods and systems, can solve problems such as difficulty in fair communication, and achieve the effects of easy deployment and reduced hardware costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
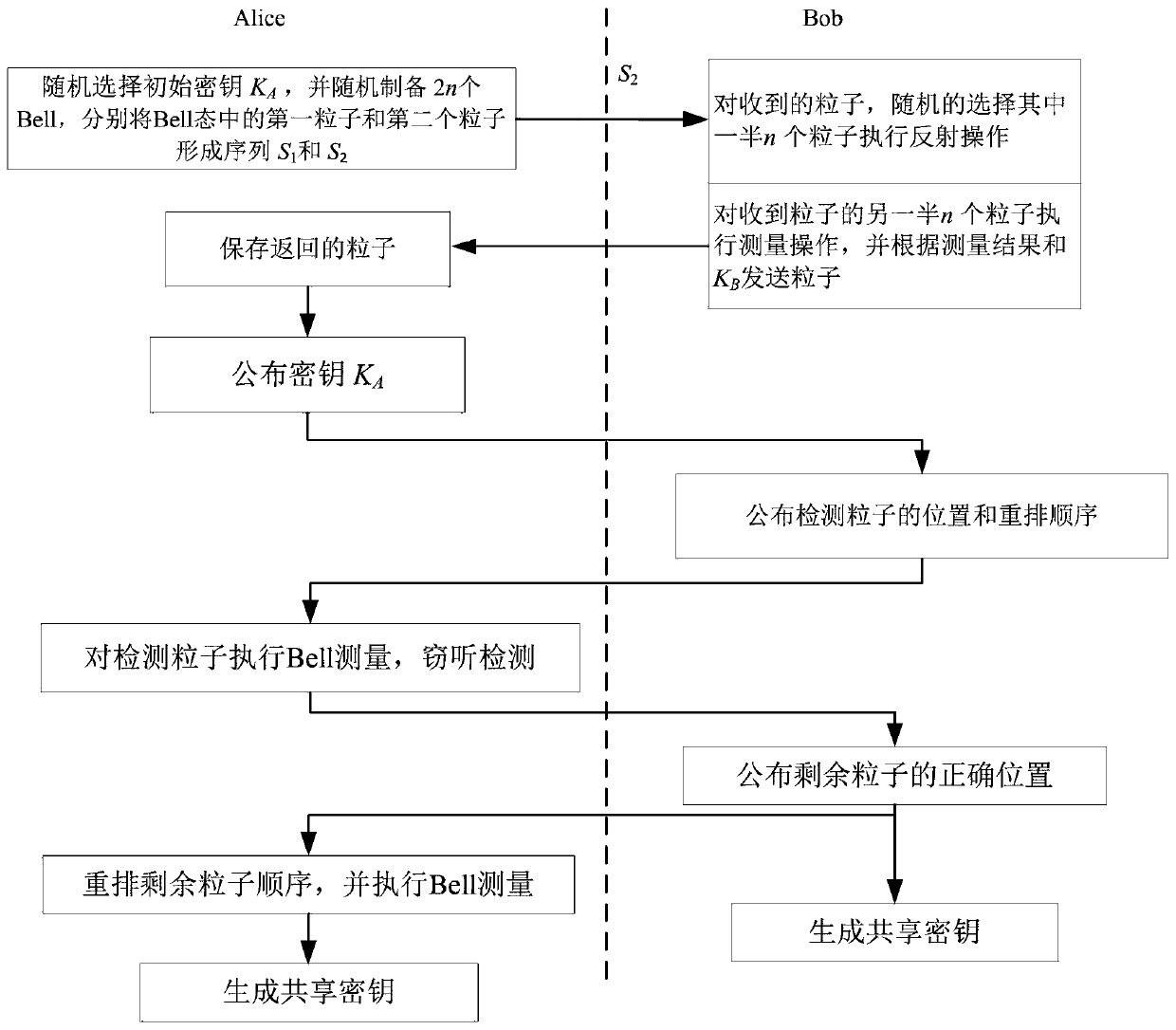
[0051] like figure 1 As shown, this embodiment includes two parties, Alice and Bob, negotiating a key.
[0052] Alice sends the sequence of particles to Bob, who randomly performs the measurement and reflection operations.
Embodiment 2
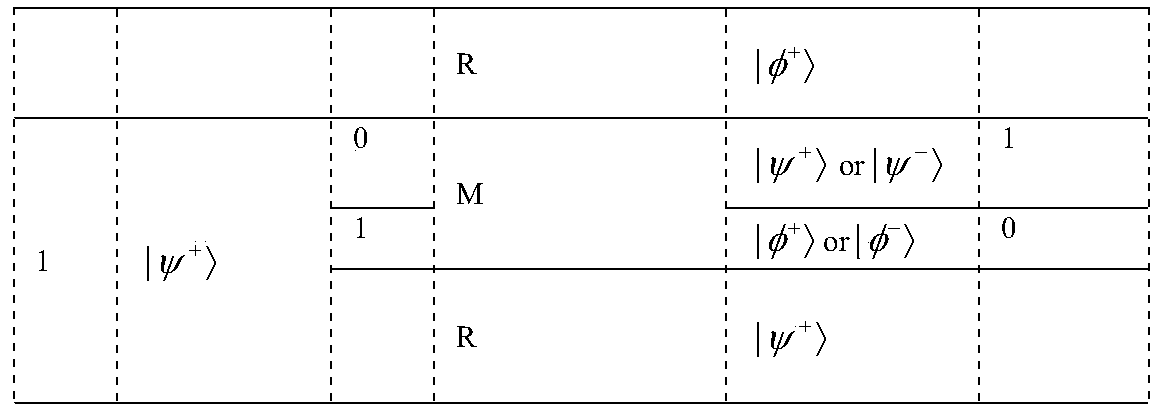
[0054] As shown in the protocol listening detection and key generation process of the present invention in table 1, it includes the following steps:
[0055] Detect particles for listening. Bob performs the reflection operation, and Alice discovers the eavesdropper by performing the Bell measurement combined with the prepared initial state.
[0056] For the particle used to generate the key, Bob performs the measurement operation, and Alice calculates K by performing the Bell measurement, combining the measurement result and the initial state of the prepared quantum B , and generate the final shared secret.
[0057] Table 1 shows the protocol monitoring detection and key generation process of the present invention.
[0058]
[0059]
[0060] The present invention will be further described in terms of security analysis of the protocol from two aspects of external attack and internal attack.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com