DNS covert tunnel detection method based on deep learning
A deep learning and covert channel technology, applied in the field of network security, can solve the problems of inability to automatically learn abstract features and low efficiency, and achieve the effects of reducing labor costs, high application value, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
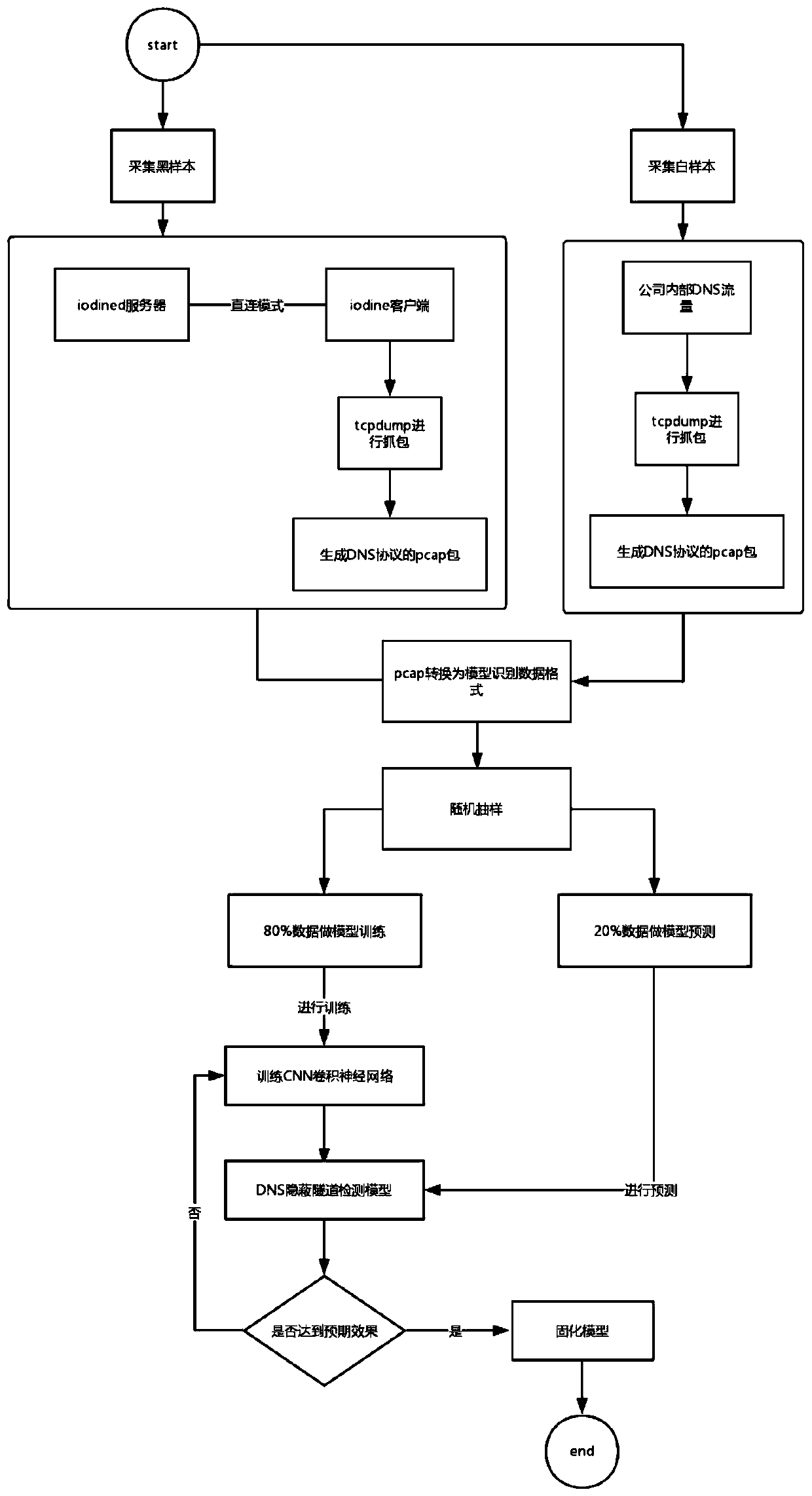
[0025] The DNS channel is a type of covert channel, and data transmission is performed by encapsulating other protocols in the DNS protocol. Since most firewalls and intrusion detection devices seldom filter DNS traffic, this provides conditions for DNS to be used as a covert channel, so that it can be used to achieve operations such as remote control and file transfer. DNS covert channels are also often used in botnets and APTs. play an important role in the attack.
[0026] DNS covert channels can be divided into two modes: direct connection and relay. Direct connection means that the Client directly connects to the designated target DNS Server (authorized NS server), and communicates by encapsulating data encoding in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com