Outsourcing data ownership checking and updating method based on alliance chain
A technology for outsourcing data and data owners, applied in the field of information security, to resist tampering attacks, avoid computing power consumption, and eliminate mutual distrust
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
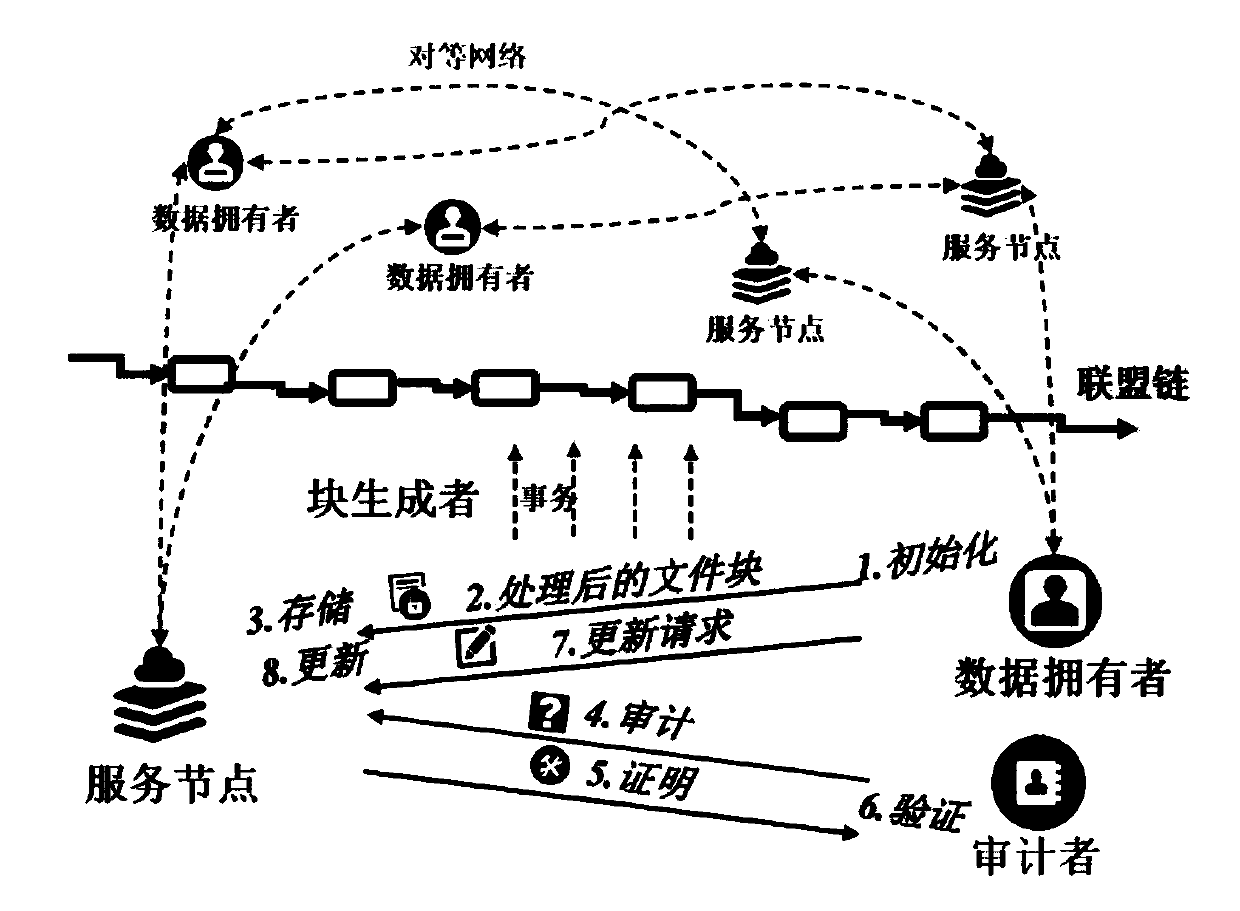
[0042] This embodiment provides a scheme for checking and updating the ownership of outsourced data based on alliance chains. The scheme flow chart is as follows figure 1 As shown, there are four types of stakeholders: data owners, service nodes, auditors, and block generators;
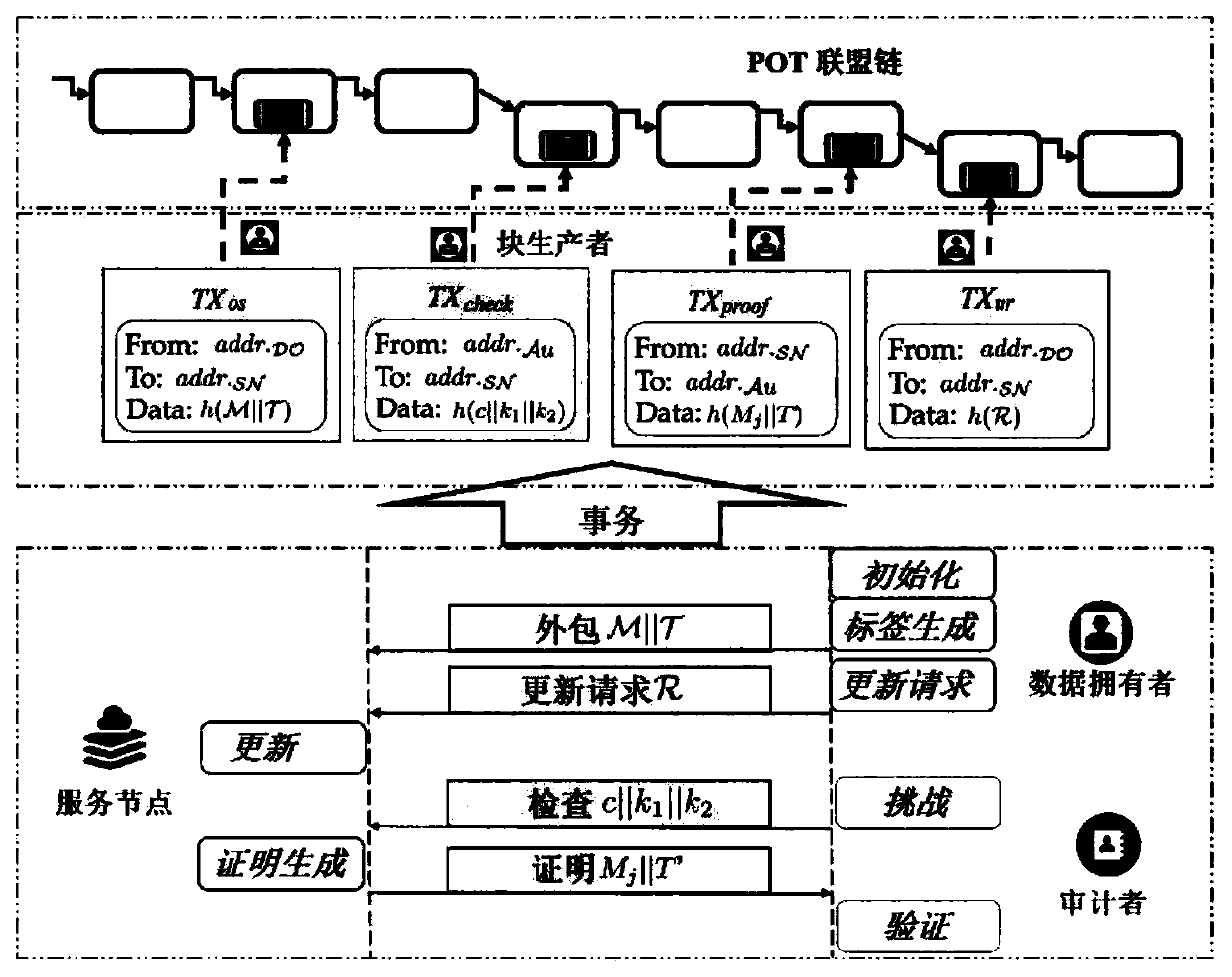
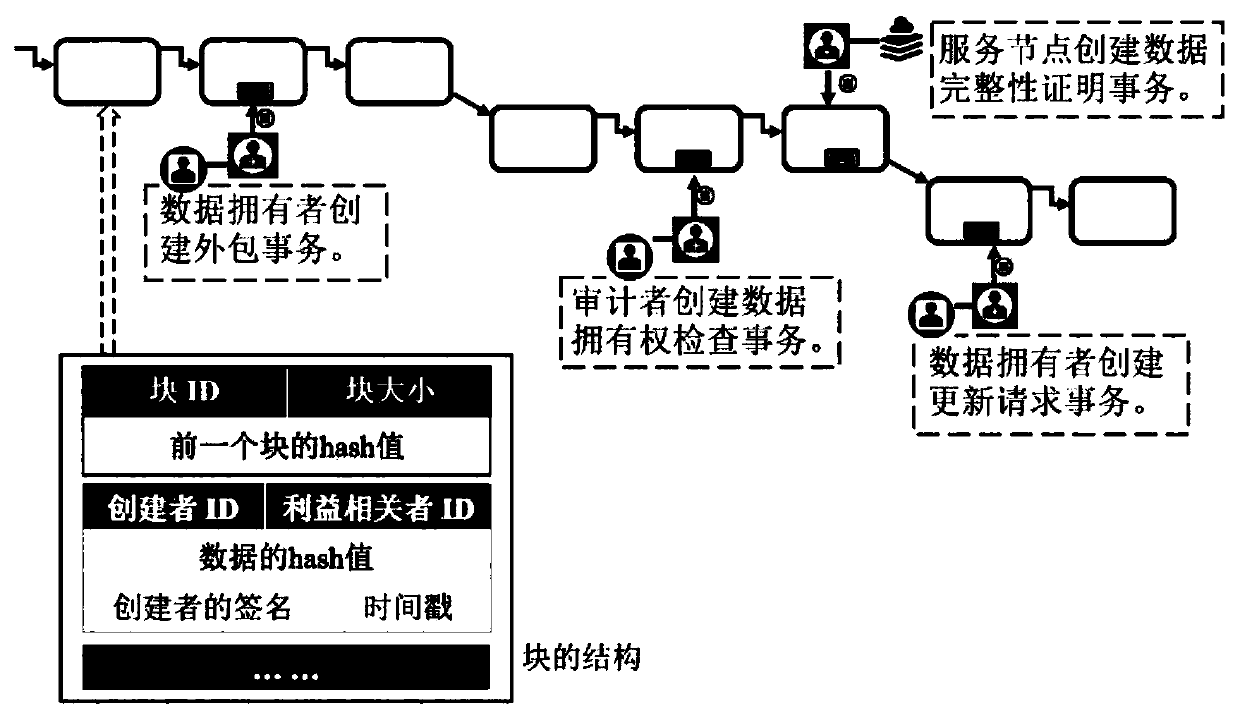
[0043] The implementation flow chart is as follows figure 2 As shown, including 7 algorithms:
[0044] initialization:
[0045] According to the security parameters, the data owner runs the initialization algorithm to select a secure hash function h:{0,1}*→G, a bilinear map e:G×G→G T , two pseudorandom functions f 1 : and f 2 : a random number as the private key s random numbers α 1 ,α 2 ,...,α s ∈G, and calculate the public key pk=g corresponding to the private key sk sk ∈G, where G, G T Both are groups, q is the order of G, g is a raw member of G, is a cyc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com