Encrypted solid state disk capable of being automatically authorized and automatic authorization method
A technology of solid-state hard disk and automatic authorization, which is applied in the direction of instruments, digital data authentication, electronic digital data processing, etc., can solve the problems of poor safety and reliability, high cost, low security, etc., achieve high security, meet application requirements, reduce The effect of unlock time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in more detail below in conjunction with the accompanying drawings and embodiments.
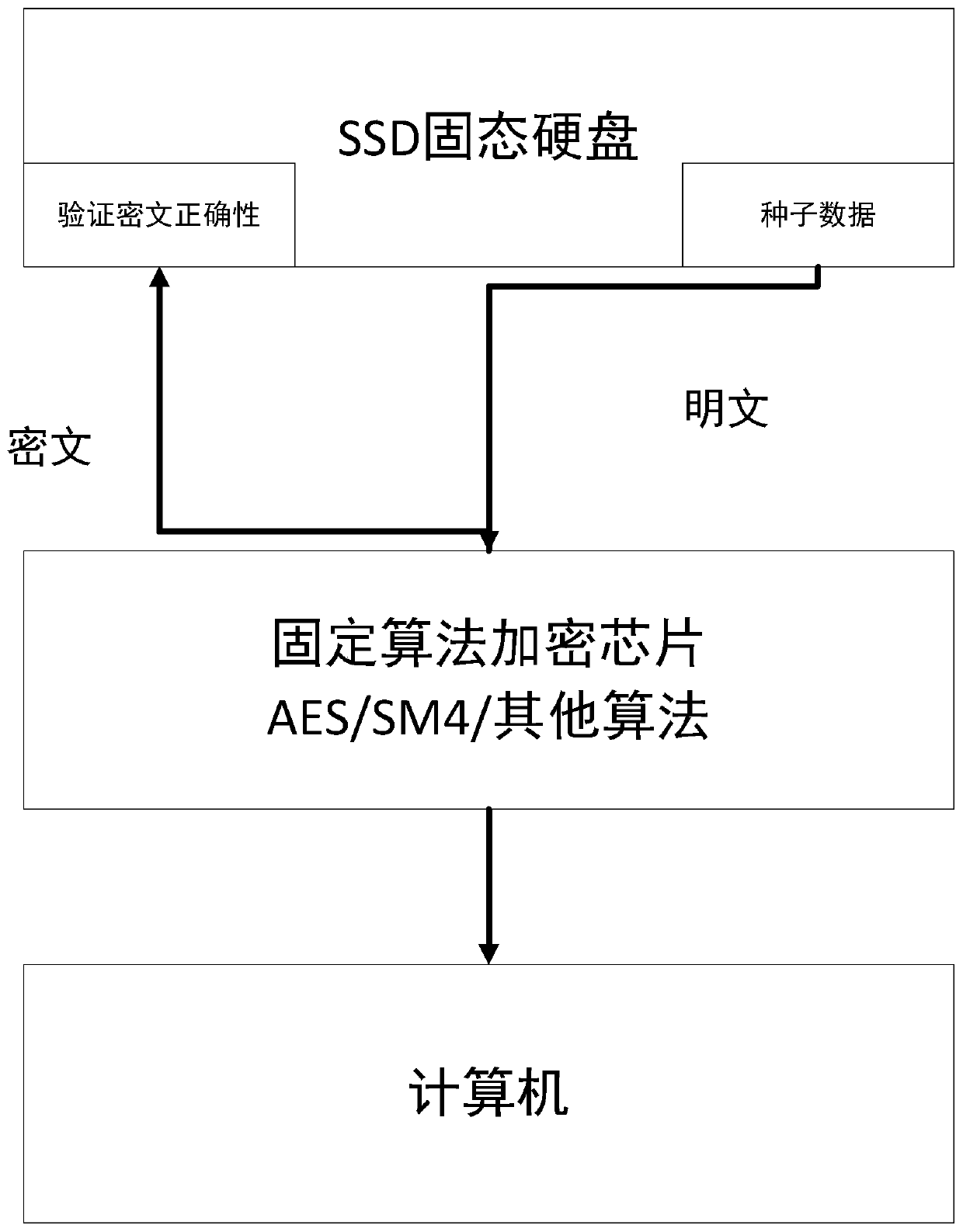
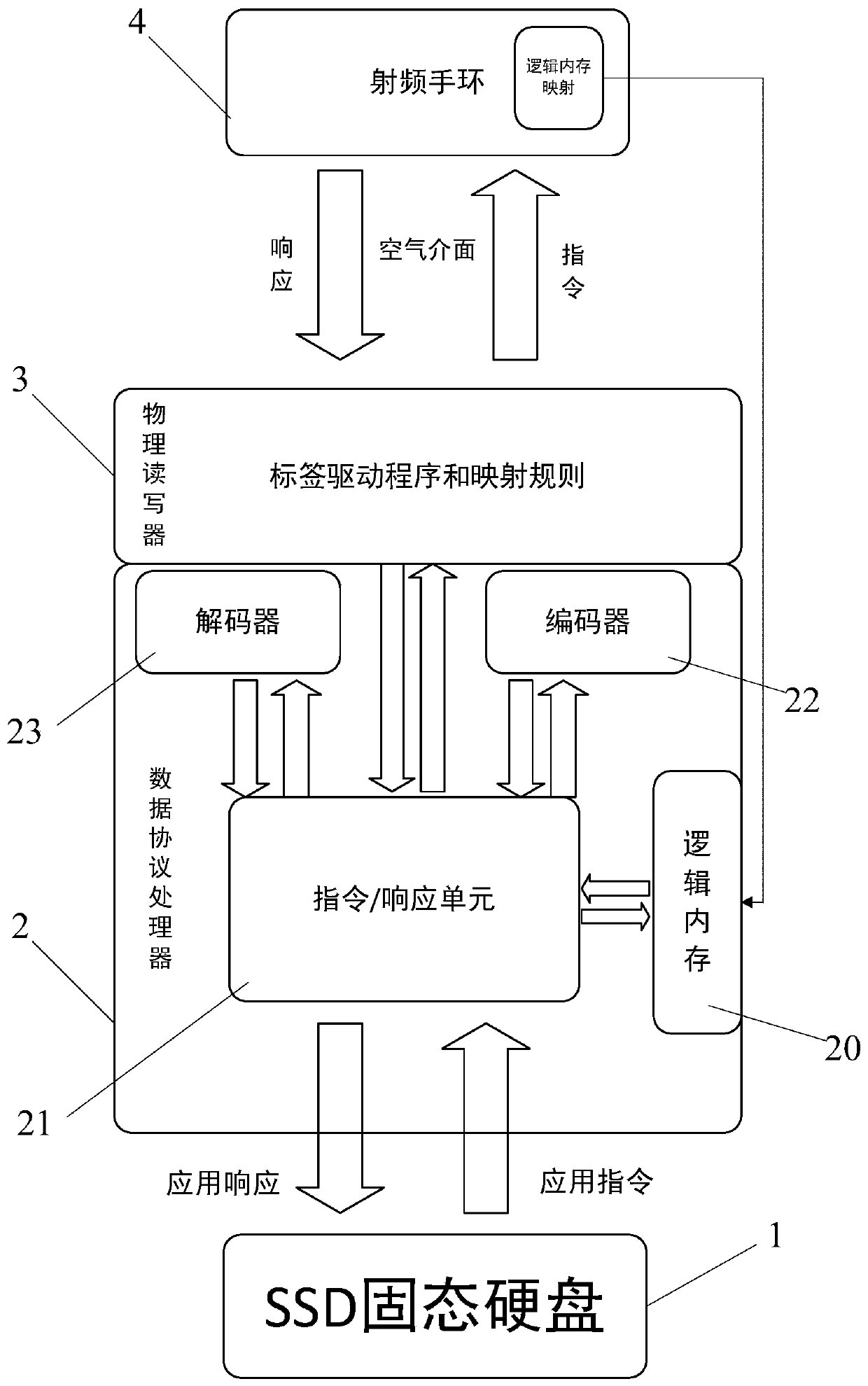
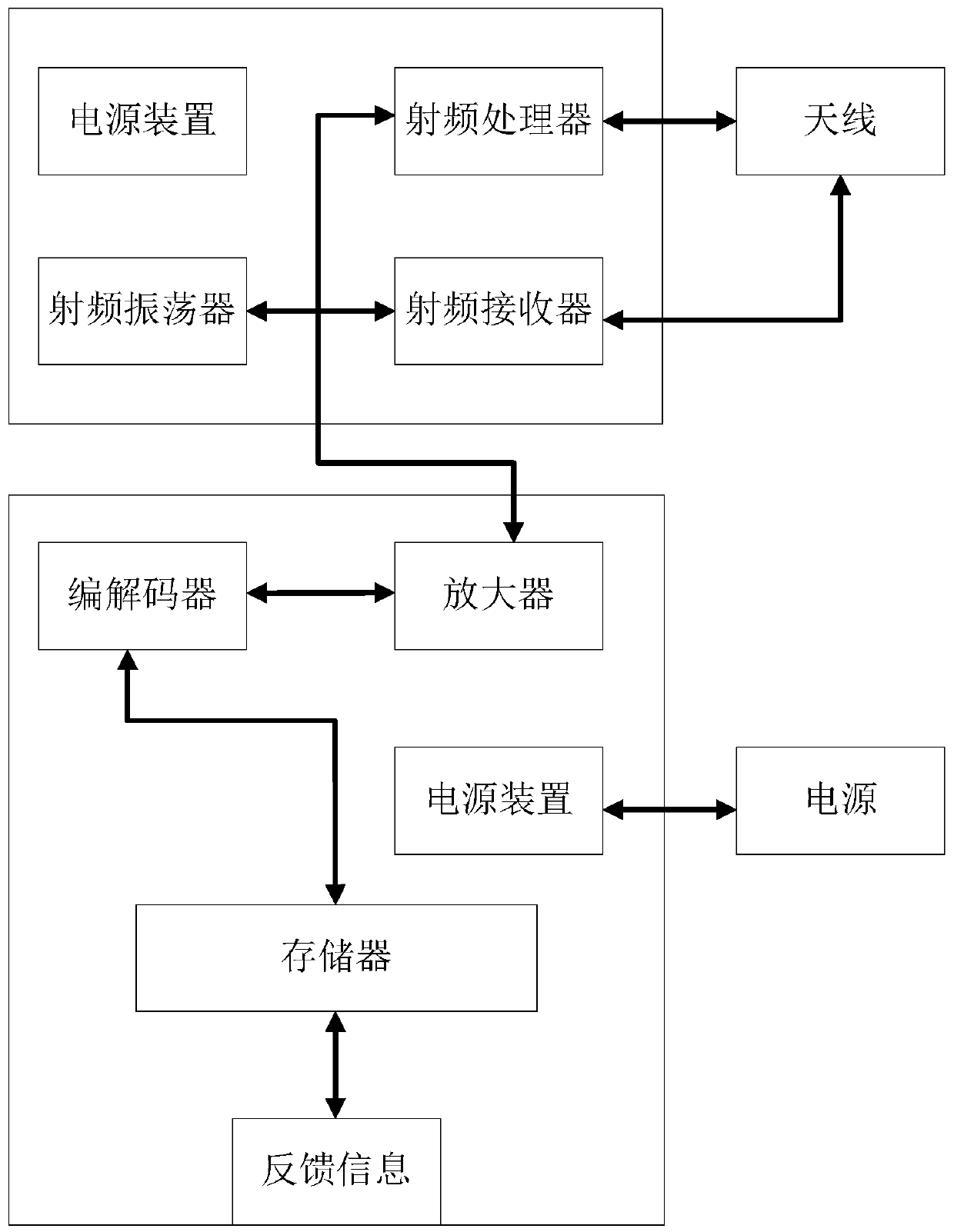
[0021] The invention discloses an encrypted solid-state hard disk capable of automatic authorization, which combines figure 2 with image 3 As shown, it includes a hard disk body 1, a data protocol processor 2, a radio frequency read-write module 3 and a radio frequency transponder 4, and the hard disk body 1, the data protocol processor 2 and the radio frequency read-write module 3 are connected in sequence, wherein:
[0022] The radio frequency transponder 4 is used to store identity information;
[0023] The radio frequency reading and writing module 3 is used to establish radio frequency communication with the radio frequency transponder 4, and then read the identity information stored in the radio frequency transponder 4;
[0024] The data protocol processor 2 is used to receive the identity information read by the radio frequency read-wr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com