UMA service method, device and system based on human-certificate integration
A witness and server technology, applied in the UMA service field based on the integration of witnesses and witnesses, can solve the problems of being unable to verify the real identity of the registrant, unable to authorize other users, and requiring high security protection capabilities of smart terminals, so that it is not easy to forge and tamper , improve safety and convenience, and improve the effect of the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
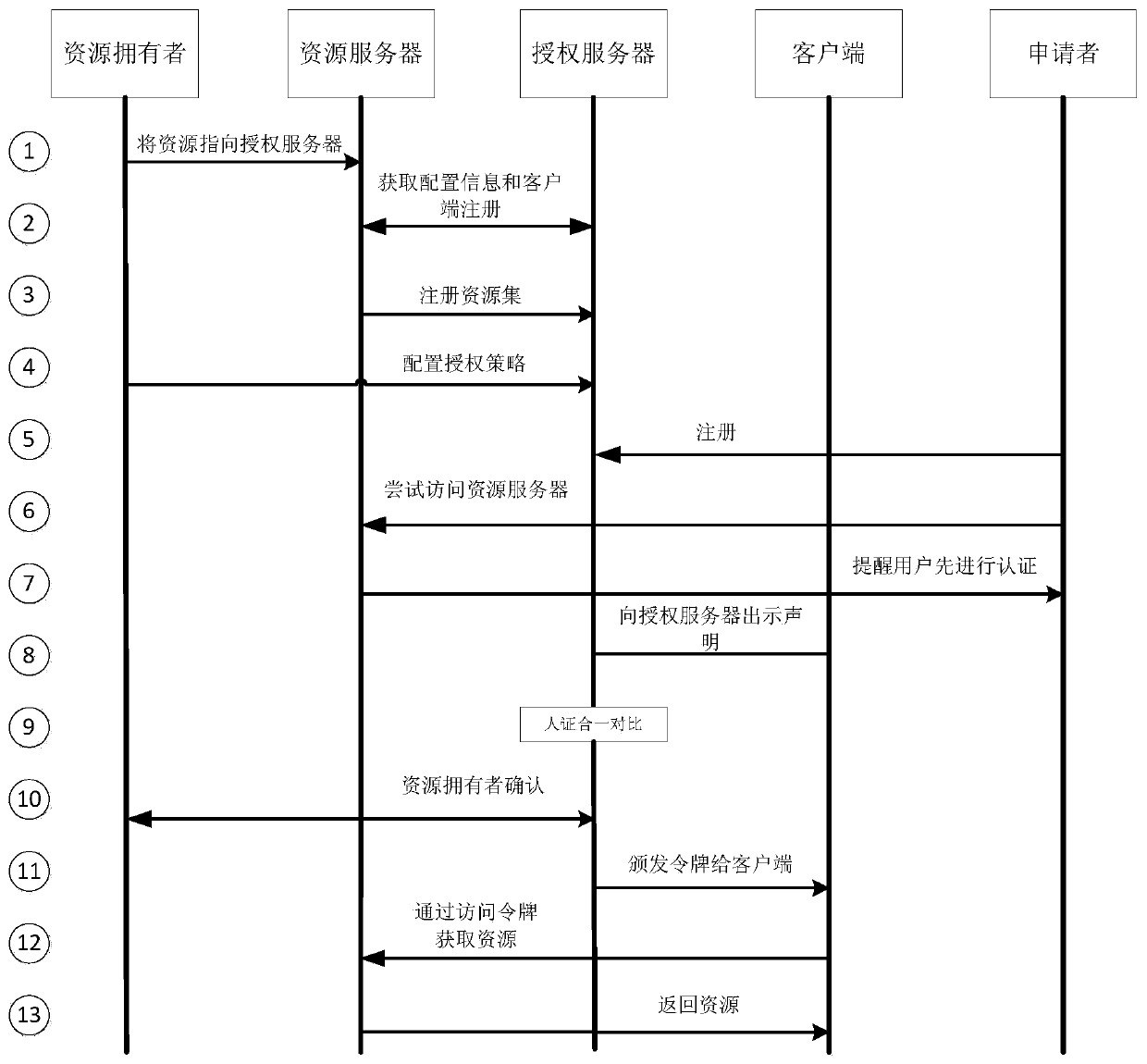
[0050] A UMA service system based on the integration of human and certificate, including resource server, authorization server and terminal equipment;
[0051] The resource server is used to save the resources uploaded by the resource owner, and the resources include visible resources such as documents or authorization credentials;
[0052] The authorization server provides services that meet the requirements of the UMA protocol for user registration, user verification, resource server and resource registration, and access token generation.
[0053] The terminal equipment is COTS equipment (Commercial Off-The-Shelf, commercial off-the-shelf or technology, refers to the software or hardware products that can be purchased with an interface defined by an open standard, which can save cost and time. For example, a mobile phone or a tablet is a A COTS device), an APP running on the terminal device is used to collect ID photos and face avatars and receive UMA service push information (when...
Embodiment 2
[0056] A UMA service method based on the integration of human and evidence includes the following steps:
[0057] Step 1. Perform traditional information registration and ID card registration on the authorization server that provides UMA services, and the authorization server encrypts and saves user registration information;
[0058] Traditional information registration, traditional information registration includes user name / password, gender, hometown, contact information, etc., and automatically generates a unique user ID (identity identification number) number for the user. The user name and password can be used as login credentials for UMA services or as User authentication information required by low security level;
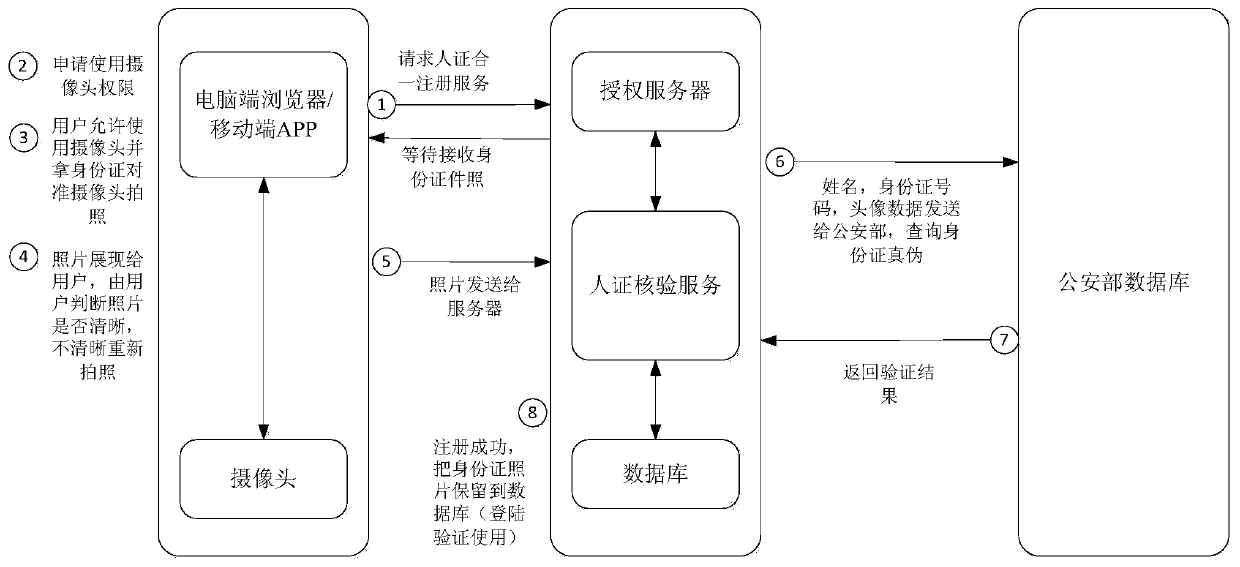
[0059] ID photo registration, collect ID photo through COTS equipment camera, verify whether the ID photo is true and valid, mainly check whether the ID name and number are the same and the authenticity of the ID image; if the ID card is confirmed to be true and va...
Embodiment 3
[0082] Such as figure 1 As shown, a UMA service method based on the integration of human and certificate includes the following steps:
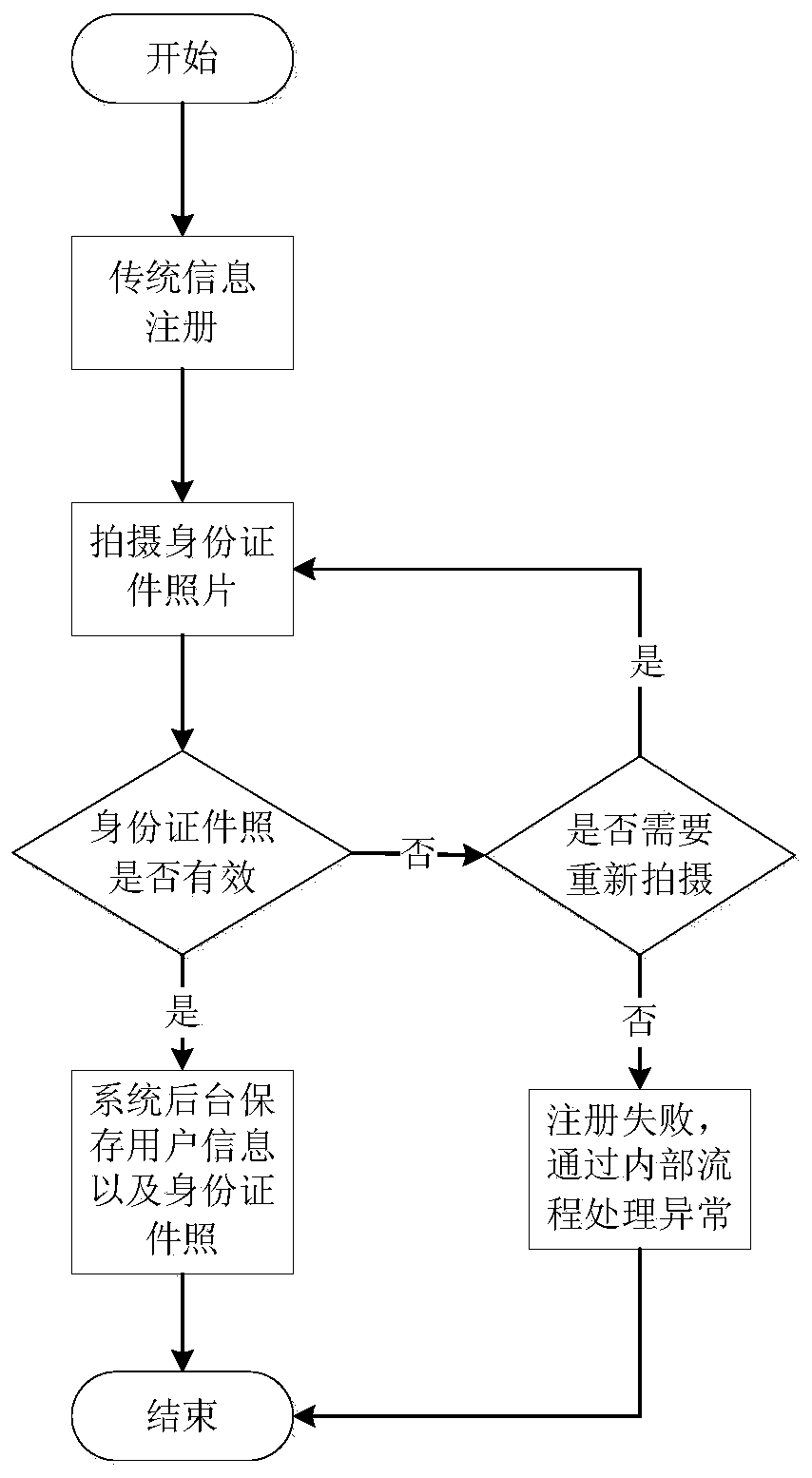
[0083] Step 1. The user registers on the authorization server that provides UMA services; figure 2 As shown, registration includes:
[0084] Traditional information registration, traditional information registration mainly includes user name / password, gender, hometown, contact information, etc., and automatically generates a unique ID number for the user. The user name and password can be used as login credentials for UMA services or as low security requirements. User authentication; such as figure 2 As shown,
[0085] ID photo registration, collect ID photo through COTS equipment camera, verify whether the ID photo is true and valid, mainly check whether the ID name and number are the same and the authenticity of the ID image; if the ID card is confirmed to be true and valid, the server is authorized Encrypted storage of user information, ID pho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com