Asymmetric cryptographic terminal based on quantum random number, communication system and method
An asymmetric cryptography and quantum random number technology, applied in the field of communication encryption, can solve the problems of short development history, slow encryption/decryption speed, and complex equipment structure, and achieve the effect of simple algorithm, improved security, and simplified deployment process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
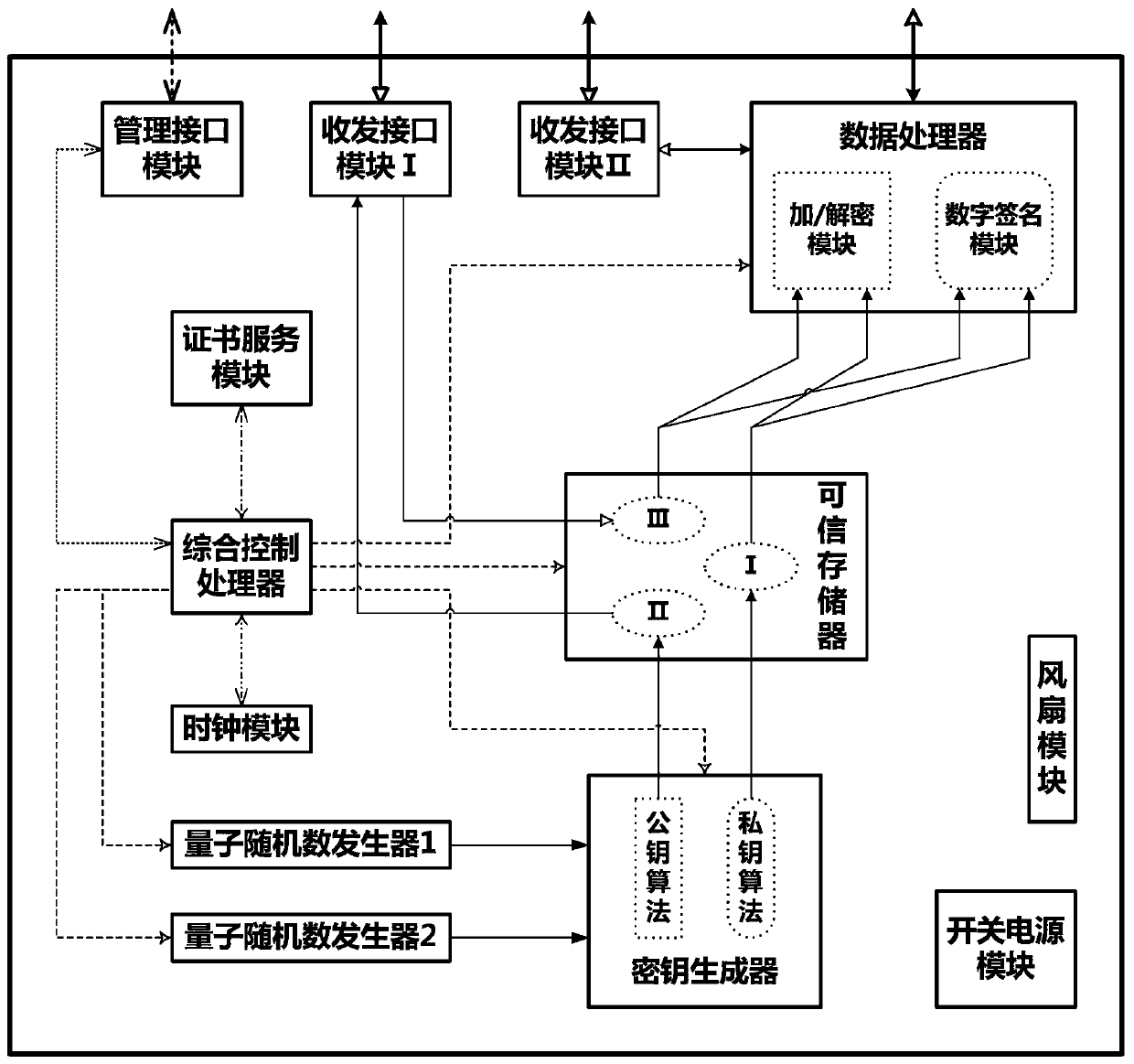
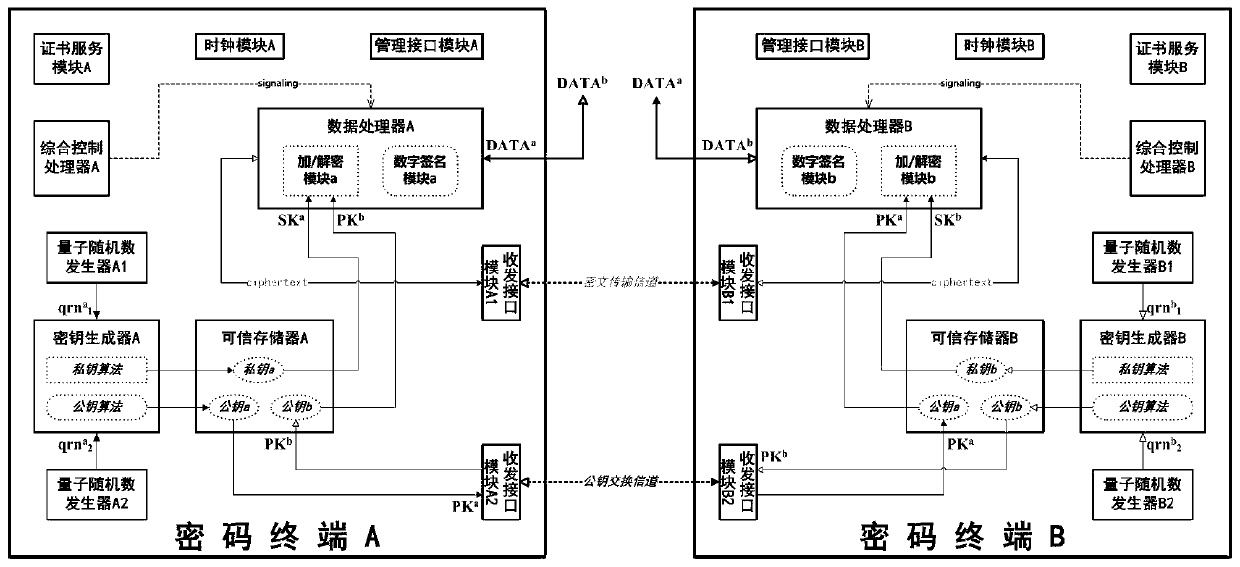
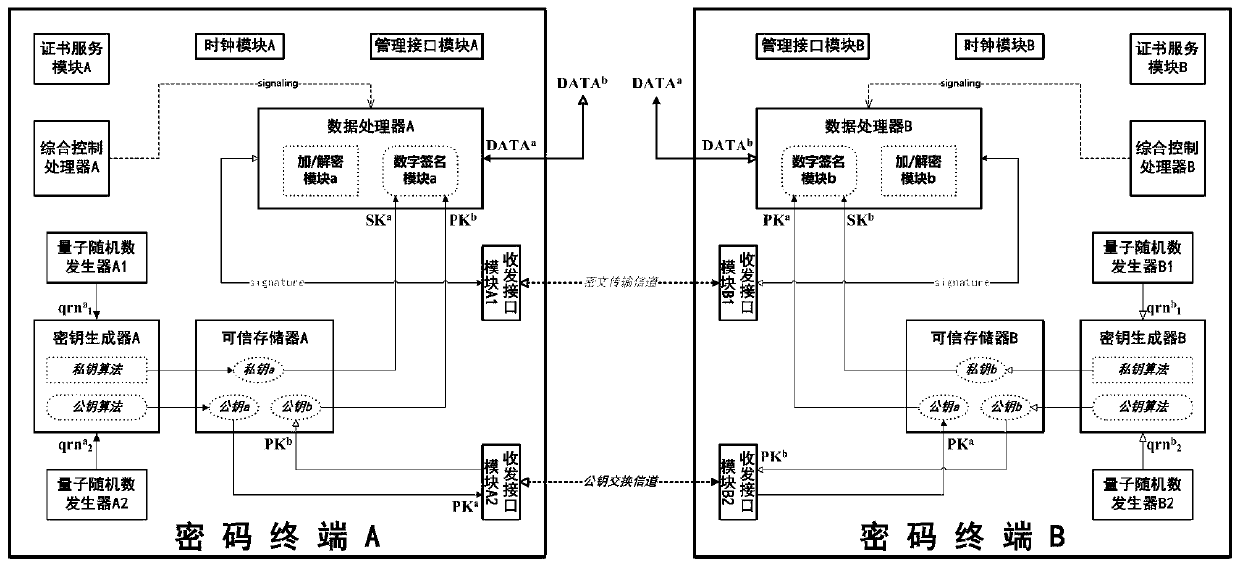
[0049] This embodiment discloses an asymmetric cryptographic terminal based on quantum random numbers, refer to figure 1 As shown, the cryptographic terminal includes a quantum random number generator, a key generator, a trusted memory, a data processor, a transceiver interface module I, a transceiver interface module II and an integrated control processor.
[0050] The above-mentioned quantum random number generator utilizes the uncertainty of the nature of quantum phenomena to continuously output ultra-long chains of true random numbers (or "quantum random numbers") at high speed through signal acquisition from physical sources and digitization technology. Each true random number The number is a binary string containing infinite bits, and whether the character on each bit is 1 or 0 is completely random. Unlike pseudo-random numbers generated on computers through algorithmic complexity, true random numbers will not be successfully predicted even with infinite computing resour...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com