A secure smart grid access control method and system resistant to differential attacks
An access control and smart grid technology, applied in key distribution, can solve the market environment that destroys fair competition, lack of fine-grained security data access control mechanism, and low differential privacy utility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0098] The present invention will be described in further detail below in combination with the accompanying drawings, and specific implementation methods will be given.
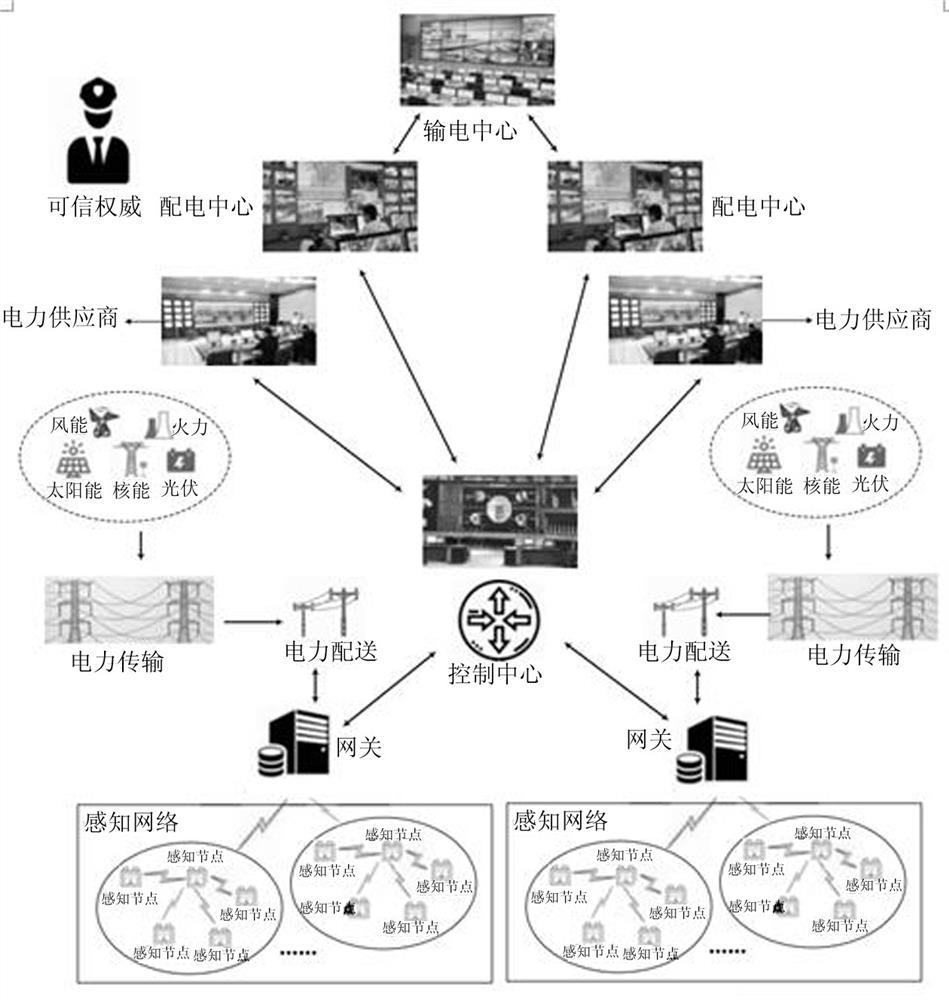
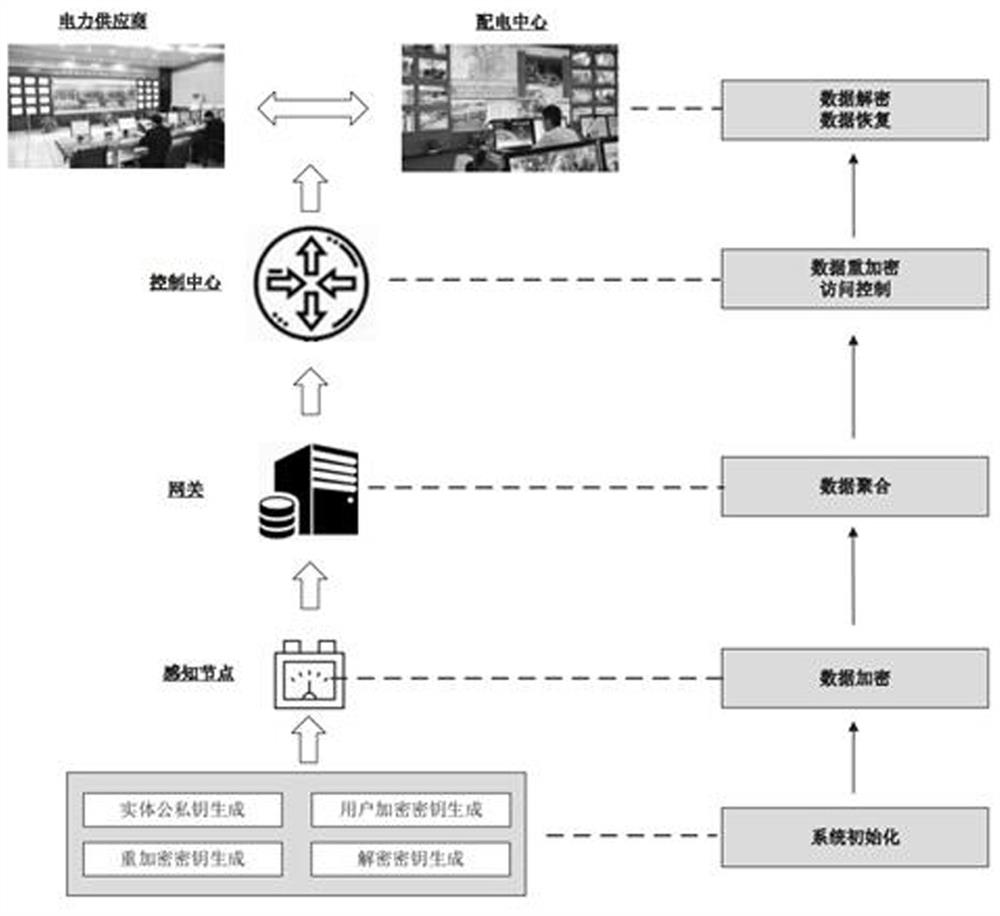
[0099] A secure smart grid access control method that resists differential attacks. The method is based on a typical smart grid communication system application scenario. The overall system architecture is as follows: figure 1 As shown, it includes the following seven participants: trusted authority: responsible for managing and distributing secret information of all other entities in the system, which has high reliability and super computing power; control center: responsible for integrating, processing and analyzing electrical energy Periodic time series power consumption data of all users in the consumption side network, providing comprehensive and reliable intelligent services; power transmission center: used to manage the transmission network, which is responsible for aggregated power consumption informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com